User authentication method and system
A user authentication and user technology, applied in the blockchain field, can solve problems such as low user authentication efficiency, central server vulnerability, data leakage, etc., achieve fast query and response speed, improve authentication efficiency, and improve system performance Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
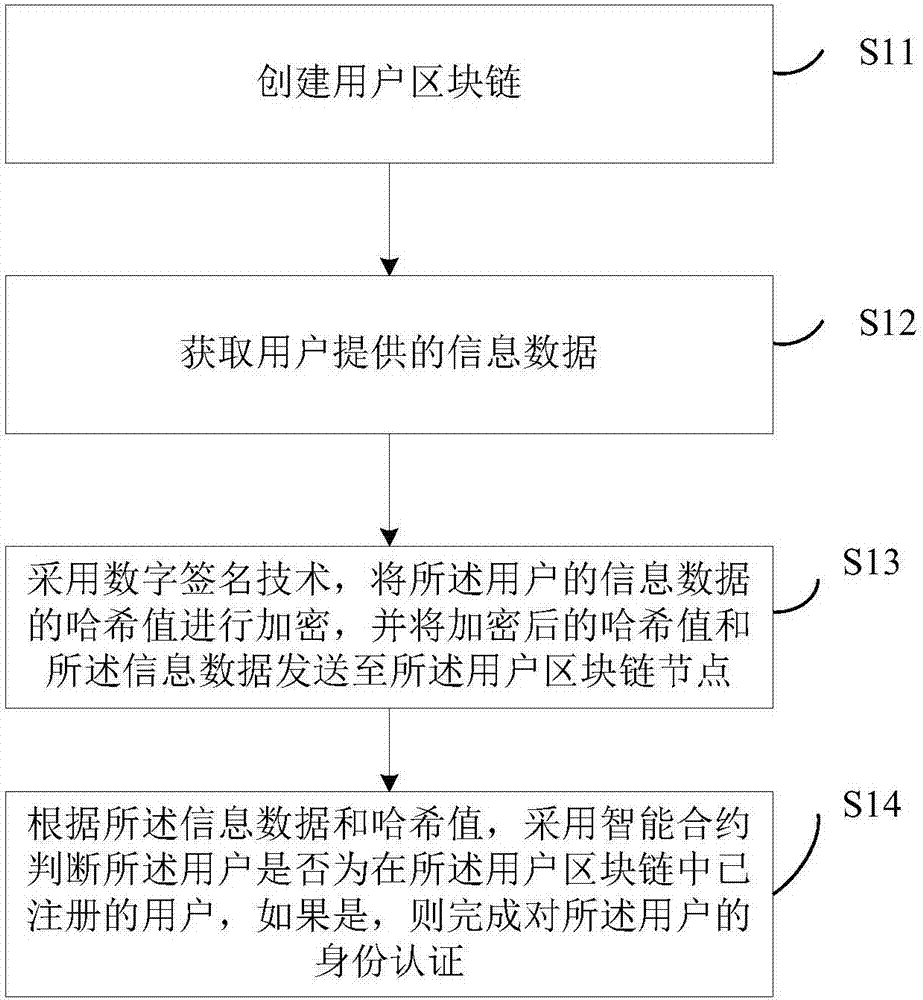
[0046] see figure 1 It is a schematic flowchart of a user authentication method provided by Embodiment 1 of the present invention, the method includes the following steps:
[0047] S11. Create a user blockchain;
[0048] Specifically, the purpose of creating the user blockchain is to store user account data, that is, user-related information data, separately from transaction data, so that user account data and transaction data are stored on different chains, making account query and response speed faster. Fast, improved system performance.
[0049] S12. Obtain information data provided by the user;
[0050] Specifically, when the user's information data is obtained through the user blockchain, all the user information data can be obtained, and then the hash value of the combined data can be used for authentication, and some key feature information data of the user can also be obtained. Authentication is performed by the hash value of the key characteristic information data....
Embodiment 2
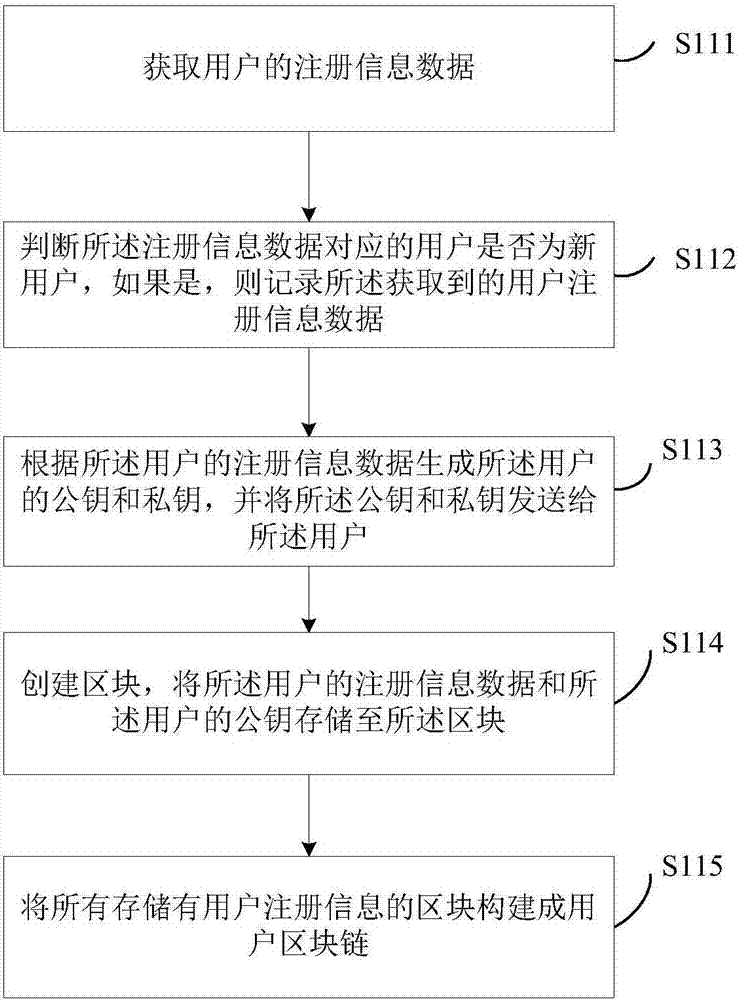
[0057] Referring to embodiment one of the present invention and figure 1 The specific process of steps S11 to S14 described in , and see figure 2 The schematic diagram of the process of creating a user block chain corresponding to the above, the steps of creating a user block chain specifically include:
[0058] S111. Obtain the registration information data of the user, wherein the registration information data includes the basic information of the user and the biometric information of the user;
[0059] Specifically, the user's registration information data includes user basic information and user biometric information. Among them, user basic information may include user name, ID number, unit and city, and user biometric information may include fingerprints, iris, DNA, etc. Information, behavioral feature information, face information and retinal information.
[0060] S112. Determine whether the user corresponding to the registration information data is a new user, and if...
Embodiment 3
[0076] Corresponding to the user authentication method disclosed in Embodiment 1 and Embodiment 2 of the present invention, Embodiment 3 of the present invention also provides a user authentication system, see Fig. Figure 4 A schematic structural diagram of a user authentication system provided by Embodiment 3 of the present invention, the system includes:
[0077] Create module 1 for creating user blockchains;
[0078] The obtaining module 2 is used to obtain the information data provided by the user;
[0079] The encryption module 3 is used to encrypt the hash value of the user's information data by using digital signature technology, and send the encrypted hash value and the information data to the user block chain node;
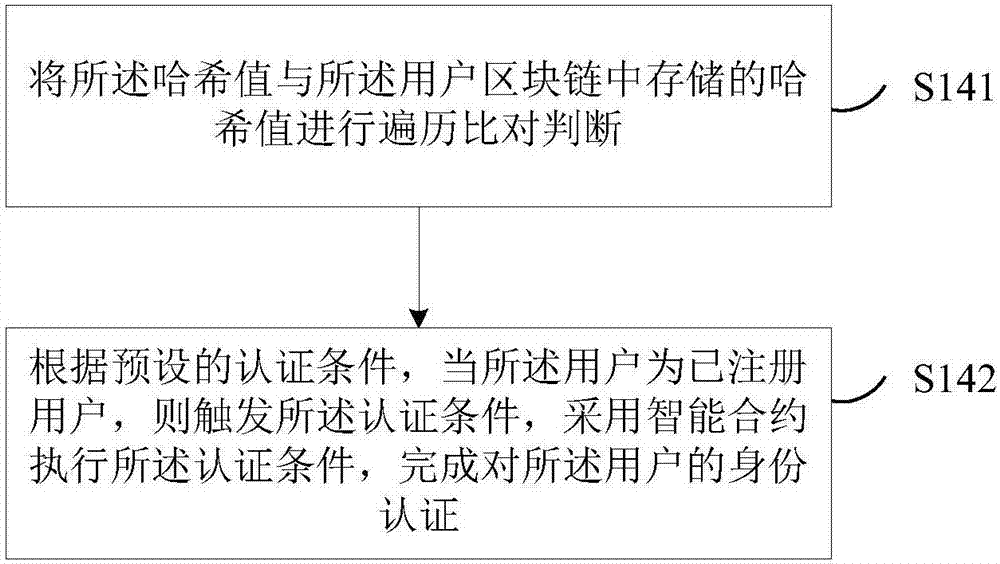
[0080] The authentication module 4 is used to judge whether the user is a registered user in the user block chain by using a smart contract according to the information data and the hash value, and if so, complete the identity authentication of the user...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com