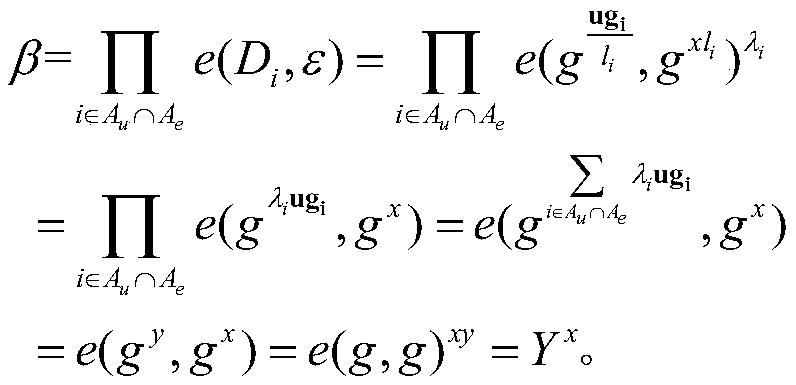A Provably Secure Attribute-Based Signcryption Method Under Standard Model
A standard model and attribute technology, which is applied to the public key of secure communication, secure communication device, and key distribution, and can solve problems such as inability to construct instances.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention is described in further detail below in conjunction with accompanying drawing:
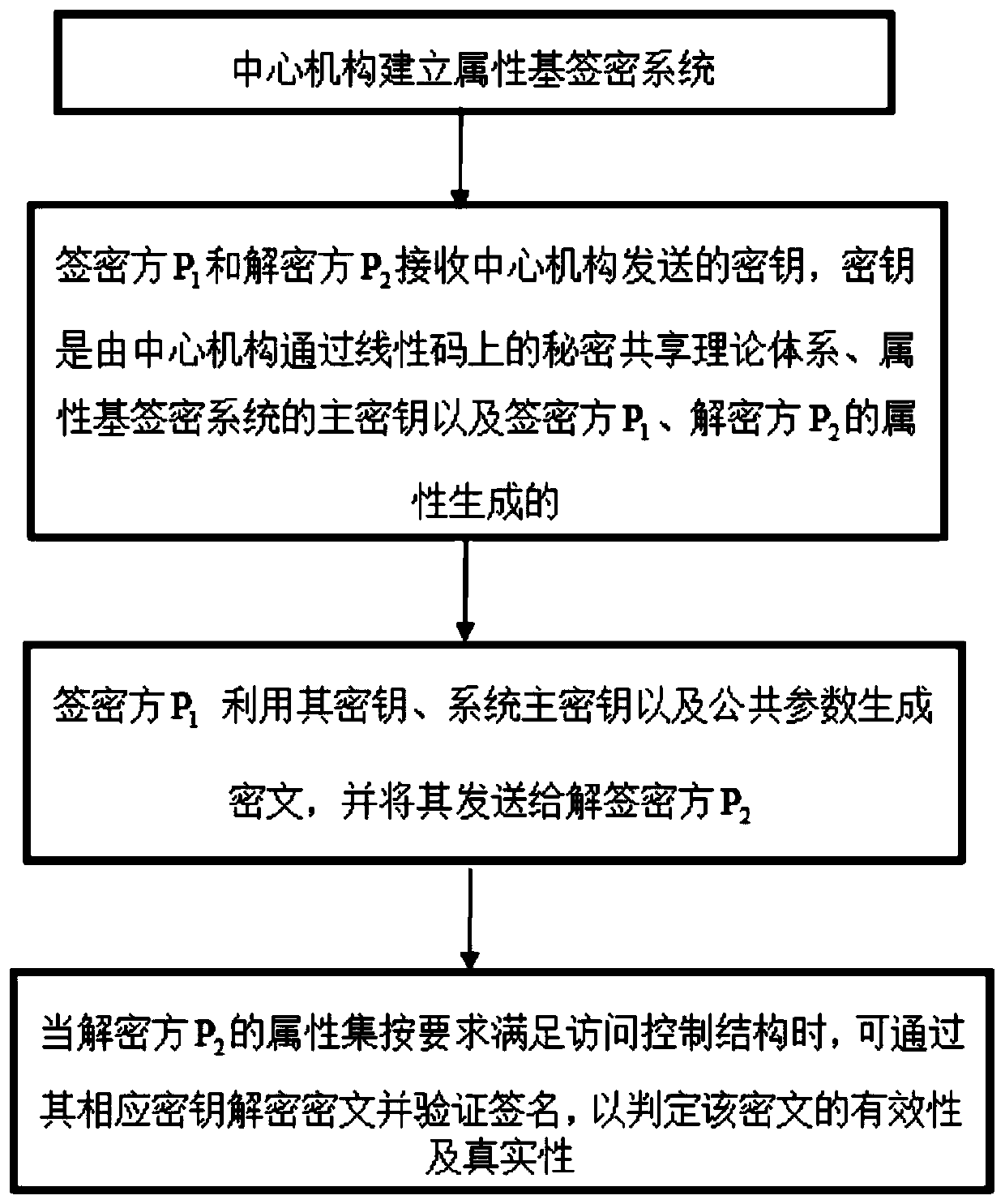
[0037] see figure 1 , 2 , the invention is a secure attribute-based signcryption method under the standard model. The signcryption is to simultaneously realize two functions of digital signature and encryption within one logical step. The signature means that the sender signs a message or file in electronic form, and the signed message or file can be transmitted in the computer network, and indicates that the signer is responsible for the content of the message or file; the encryption is the use of technical means Encode important data for transmission.
[0038] The method is implemented in the following steps
[0039] Step 1. System establishment
[0040] 1) Given a security factor κ, the key generation center (PKG) arbitrarily selects a cyclic group G of prime number p order 1 , G 2 , g is G 1 The generator of bilinear map e: G 1 *G 1 →G 2, all attribute s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com