NOT operational character supported characteristic-based CP-ABE method having CCA security
A CP-ABE, operator technology, applied in safety communication devices, digital transmission systems, electrical components, etc., can solve problems such as increased system overhead, poor flexibility, and inability to support NOT operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] Embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
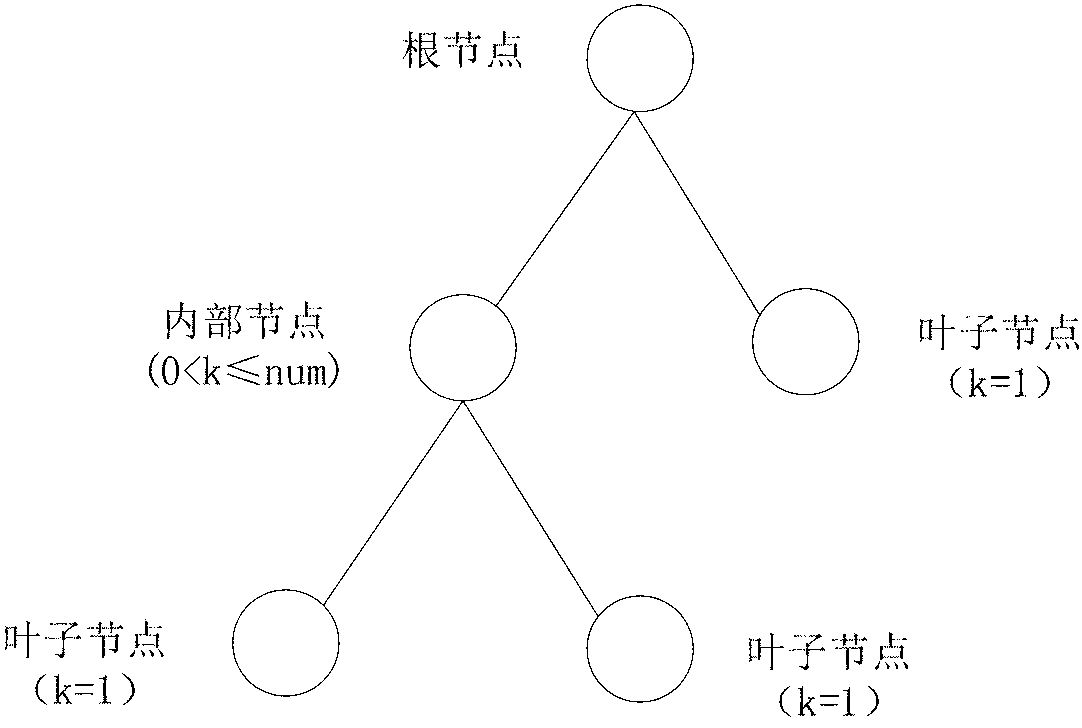
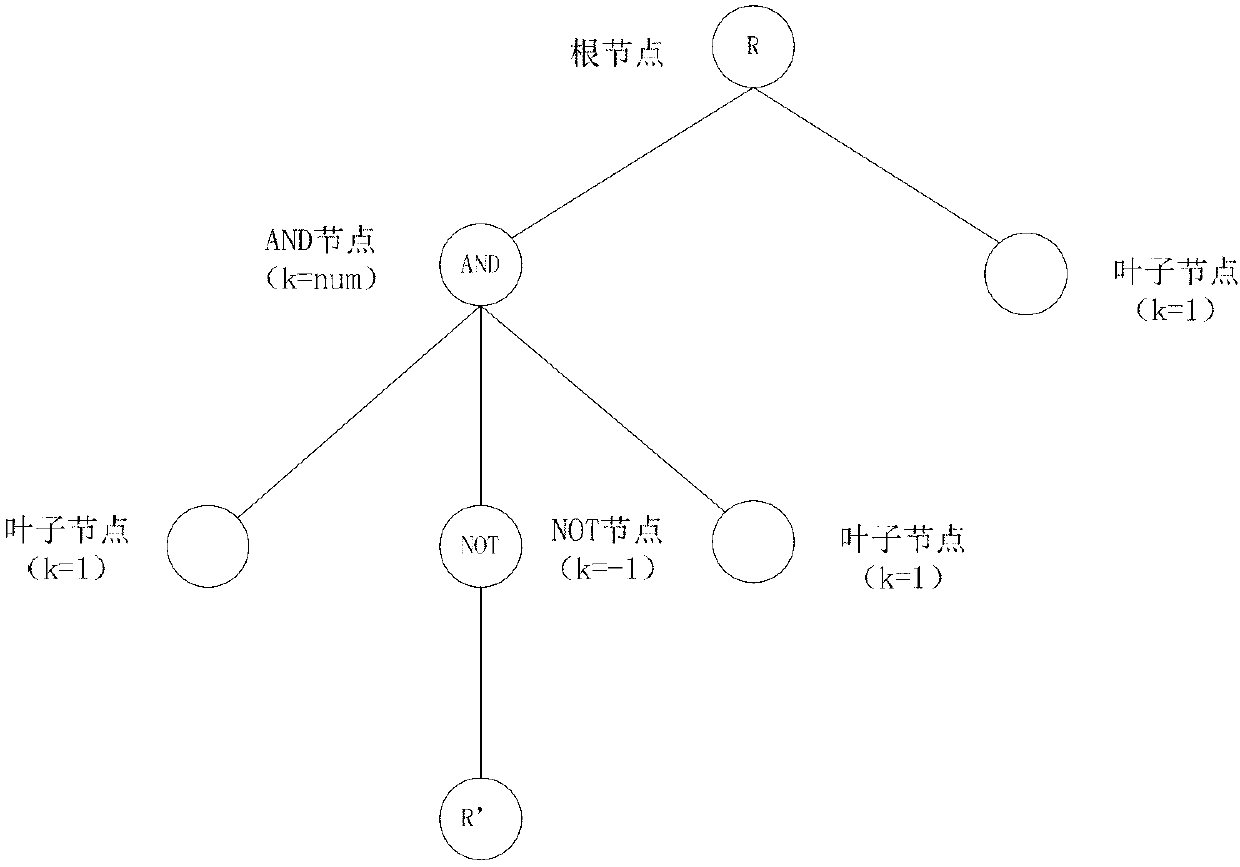
[0015] The core idea mainly included in the present invention: destroy the Shamir secret sharing mechanism, and destroy the interpolation points related to the NOT attribute when performing Lagrangian interpolation backtracking calculation, so that when the calculation goes back to the root node of the strategy tree, q can be obtained R (0)≠s. Then from the user's perspective, the decryption algorithm has been executed, but the final M obtained is not the correct M, thus achieving the purpose of the NOT operation.
[0016] Before describing the method, define the following parameters and methods:
[0017] 1. G 0 and G 1 It is a multiplicative cyclic group with two orders of large prime number p, and g is the group G 0 The generator of e:G 0 ×G 0 →G 1 is an efficiently computable bilinear map. Z p is a set obtained modulo p, including all positi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com