Convertible proxy signcryption method with provable security
A proxy signcryption and proxy signature technology, applied in the field of convertible proxy signcryption, can solve the trust crisis, hinder the mainstream cloud computing service platform and other problems, and achieve the effect of ensuring confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
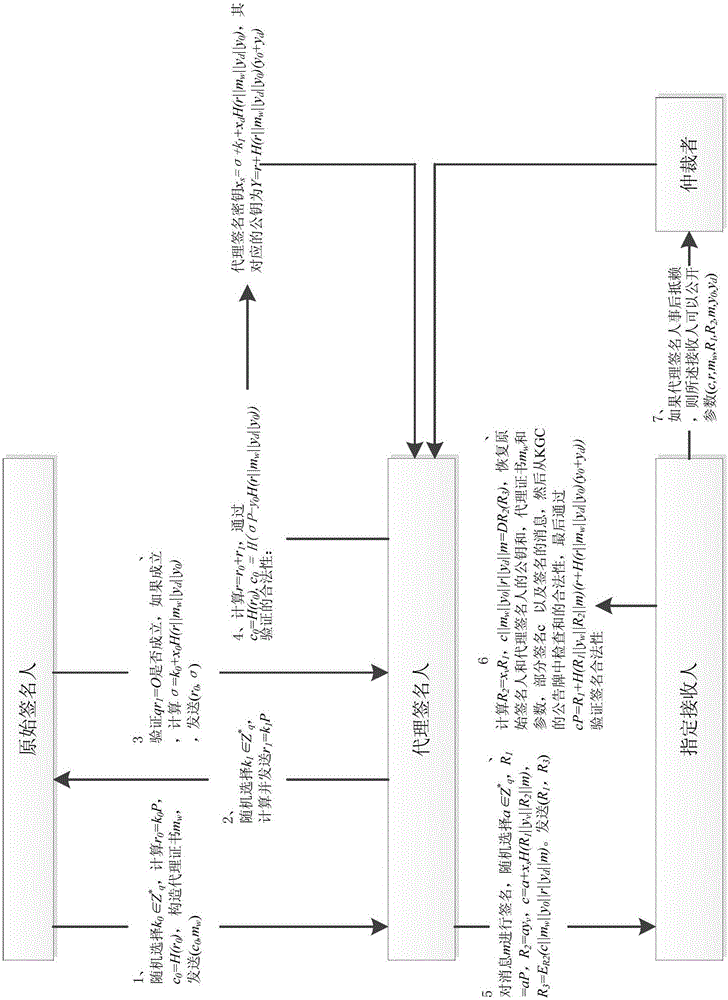
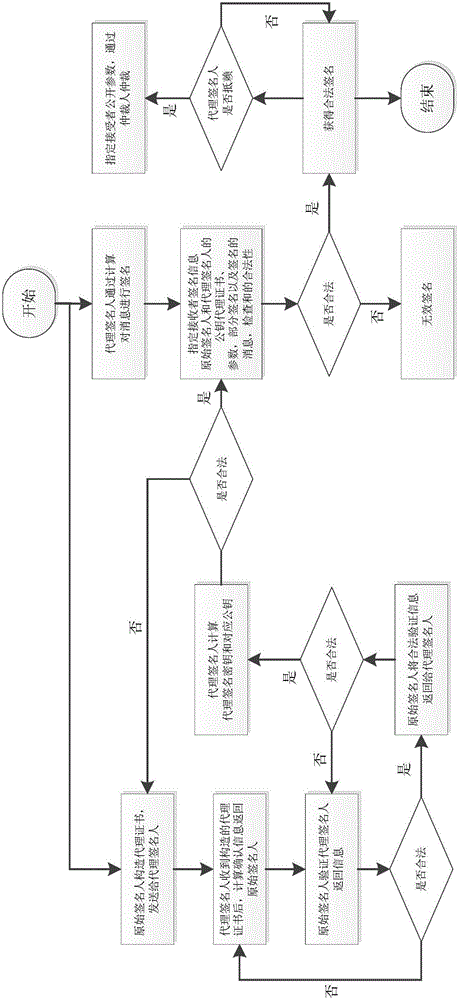
[0025] combined with figure 1 , 2 , the present invention is further illustrated by specific examples.
[0026] 1. A provably safe transferable proxy signcryption method comprising the following steps:
[0027] Step 1. Proxy signature key generation;
[0028] 1.1 The original signer randomly selects k 0 ∈ Z * q , where q is a set of large prime numbers selected from the key generation center KGC, which generates public-private key pairs (x 0 belongs to Z * q ,y 0 =x 0 P), (x d belongs to Z * q ,y d =x d P) and (x v belongs to Z * q ,y v =x v P), Z * q For the set of positive integers in the set of large prime numbers, calculate r 0 =k 0 P, P is E(GF q ) generator, E(GF q ) is an elliptic curve defined on the finite field GF(q), c 0 =H(r 0 ), H():{0,1} * →{0,1} 256 is a secure Hash function, constructing proxy certificate m w , and then put (c 0 ,m w ) to the proxy signer;
[0029] 1.2 The proxy signer receives (c 0 ,m w ), randomly select k ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com