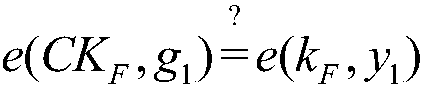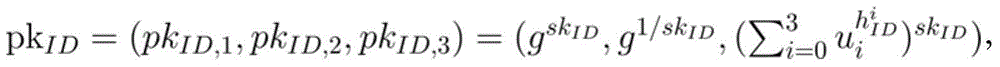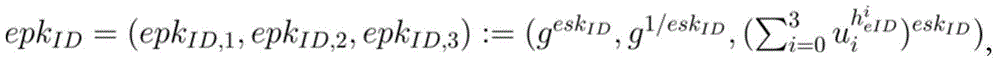Patents
Literature
58 results about "Key encapsulation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Key encapsulation mechanisms (KEMs) are a class of encryption techniques designed to secure symmetric cryptographic key material for transmission using asymmetric (public-key) algorithms. In practice, public key systems are clumsy to use in transmitting long messages. Instead they are often used to exchange symmetric keys, which are relatively short. The symmetric key is then used to encrypt the longer message.
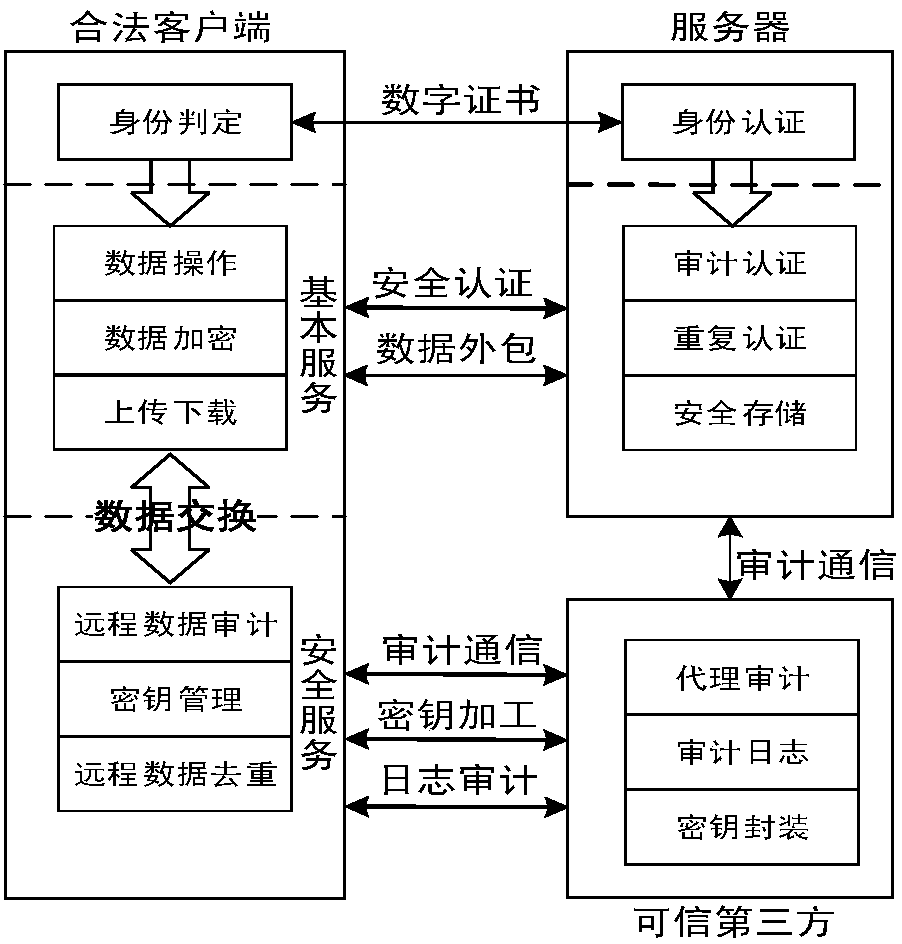
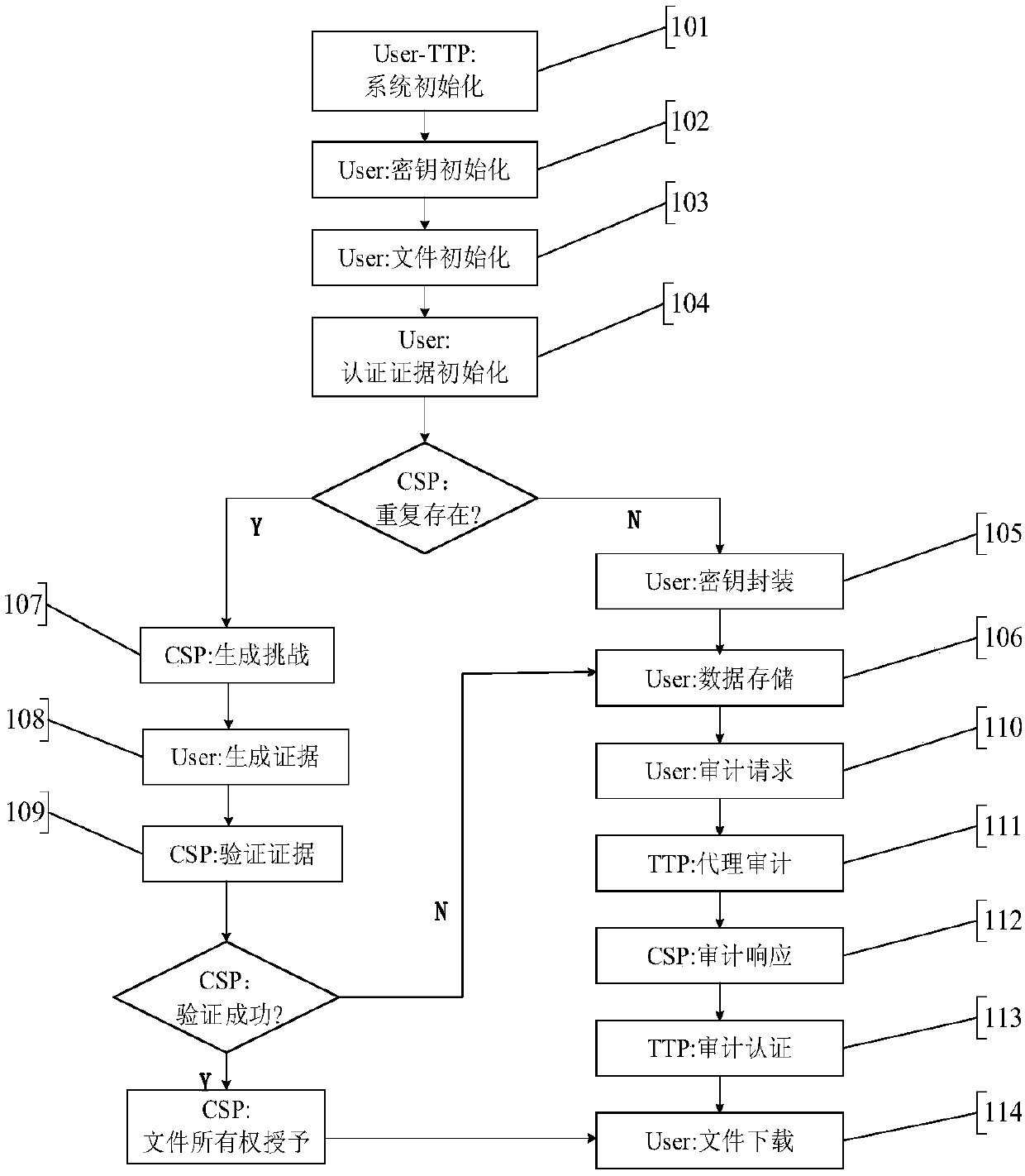
Cloud data duplication elimination and integrity auditing method based on convergence encryption
ActiveCN107800688ASafe and efficient managementTo achieve deduplicationKey distribution for secure communicationUser identity/authority verificationCloud dataTrusted third party
The invention discloses a cloud data duplication elimination and integrity auditing method based on convergence encryption. According to the method, through adoption of a convergence key encapsulation / de-encapsulation algorithm based on blind signatures, convergence keys can be securely stored and moreover convergence key duplication elimination can be realized; and through utilization of a BLS signature algorithm based on the convergence keys, auditing public keys are stored by a trusted third party TTP, the TTP carries out proxy auditing, and duplication elimination of auditing signatures and the auditing public keys is realized. The method comprises the specific steps of carrying out system initialization; carrying out key initialization; carrying out file initialization; carrying out authentication evidence initialization; carrying out key encapsulation; carrying out data storage; carrying out duplication challenge; carrying out duplication response; carrying out duplication authentication; carrying out request auditing; carrying out proxy auditing; carrying out auditing response; carrying out auditing authentication; and carrying out file downloading. According to the method,a utilization rate of a cloud storage space is improved, the duplication elimination of auditing signatures and the auditing public keys is realized, and the storage and computing cost of a client arereduced.
Owner:NANJING UNIV OF SCI & TECH
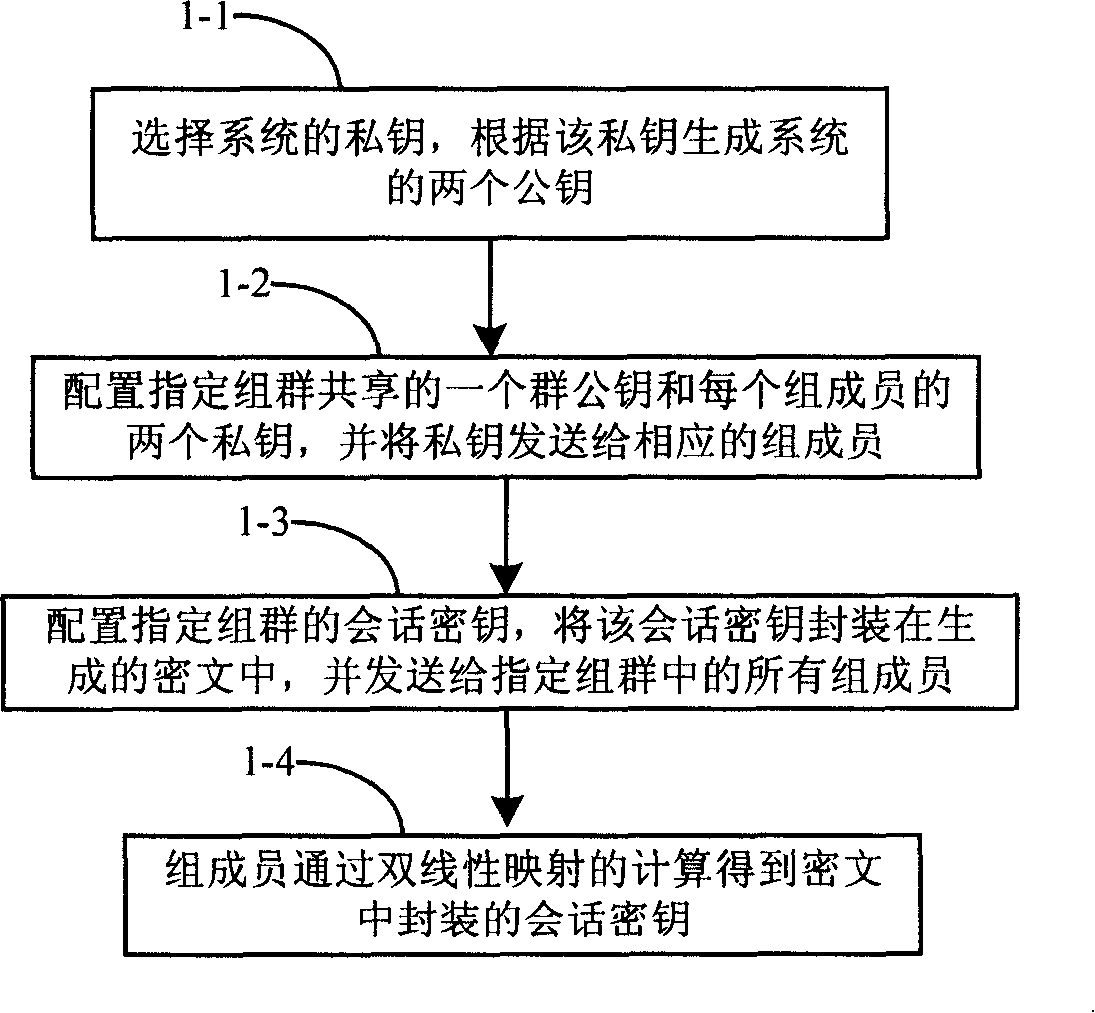
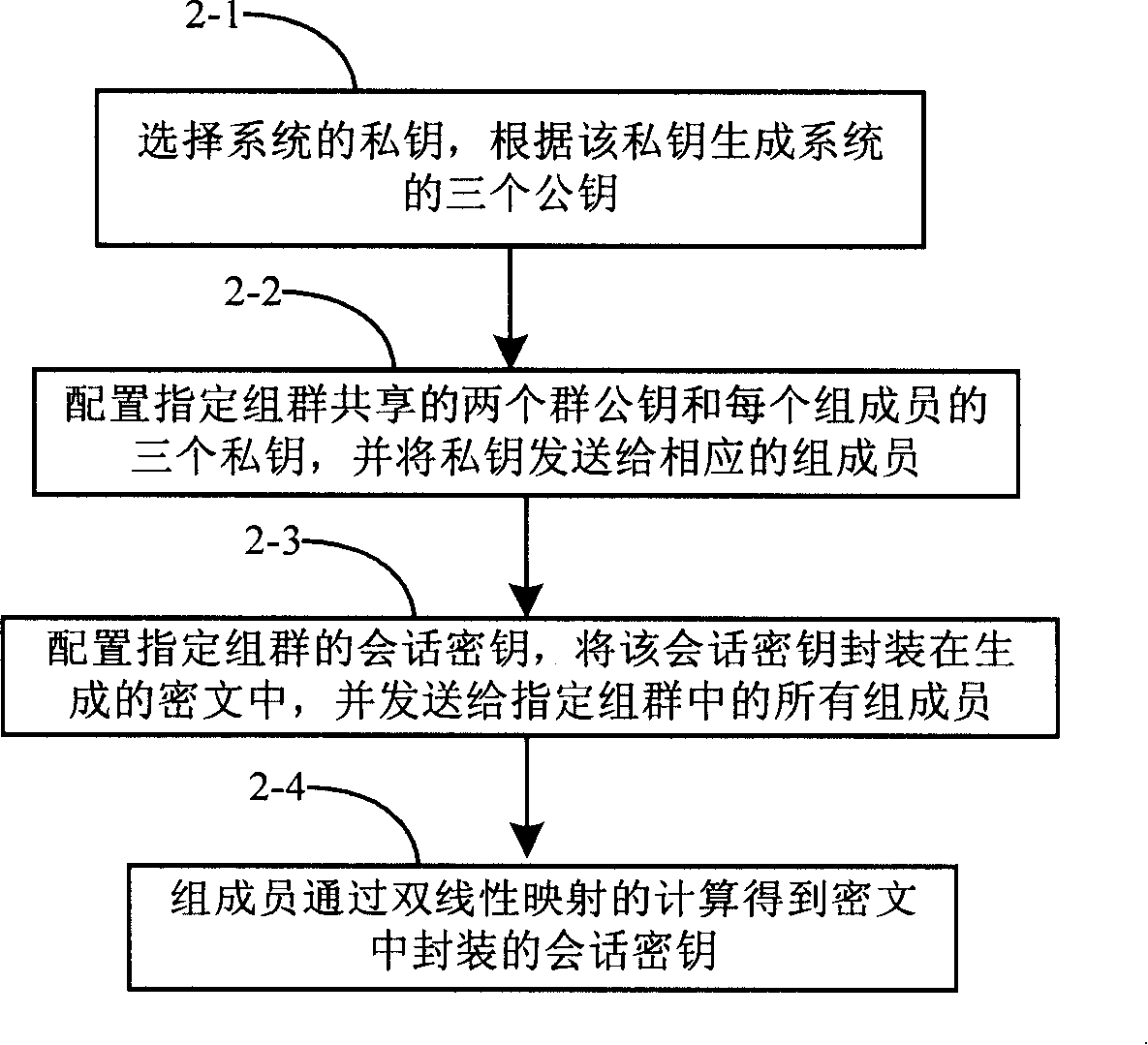
Method for secret key configuration based on specified group
InactiveCN101170404ASimplify the packaging processReduce computational workloadKey distribution for secure communicationRadio/inductive link selection arrangementsWorkloadKey encapsulation
The invention provides a key configuration method to a designated group. The method mainly comprises that the designated group is configured with a shared public key to obtain the private key of each member in the designated group, and sends the private keys to the corresponding group member. The adoption of the method of the invention is able to efficiently decrease the workload of both a sender and a receiver, and also carry out the key packages to all the group members.
Owner:HUAWEI TECH CO LTD +1
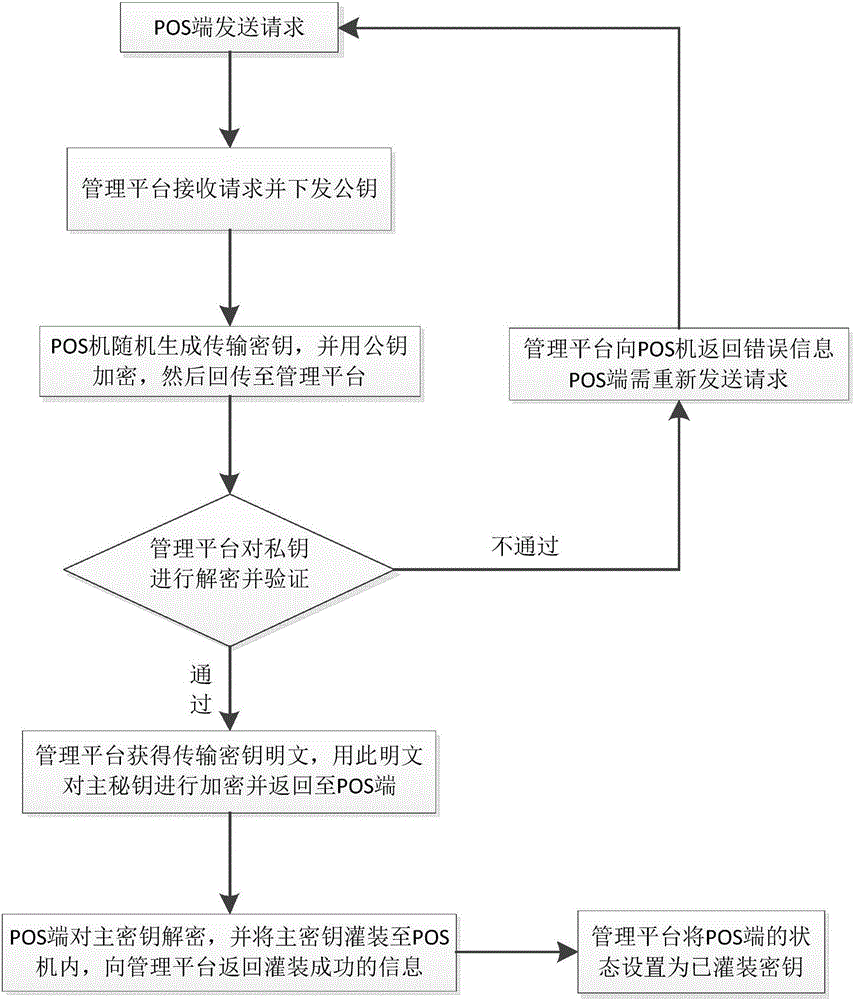
Method for remotely issuing POS key
InactiveCN106027247ASave time and costShorten the timeKey distribution for secure communicationPoint-of-sale network systemsComputer securityKey encapsulation
The present invention discloses a method for remotely issuing a POS key, comprising the following steps in sequence: S1. a POS terminal uploads a request to acquire a public key to a management platform, and the management platform issues the public key to a POS machine; S2. the POS machine generates a transmission key at random, encrypts same using the public key, and uploads same to the management platform, and the management platform decrypts and verifies same using a private key; S3. after the transmission key passes validation, the management platform decrypts same to obtain transmission key plaintext, encrypts a master key using the transmission key plaintext, and returns same to the POS terminal; and S4. after decrypting same, the POS terminal encapsulates the master key in the machine, and notifies the platform of key encapsulation success. By means of the method for remotely issuing a POS key disclosed by the present invention, key encapsulation can be performed on each POS machine through a mechanism requested by a customer without performing key encapsulation on each POS machine by the manufacturer before it leaves the factory or by the merchant before delivery, thereby greatly saving time costs of key encapsulation.
Owner:宁夏丝路通网络支付有限公司北京分公司
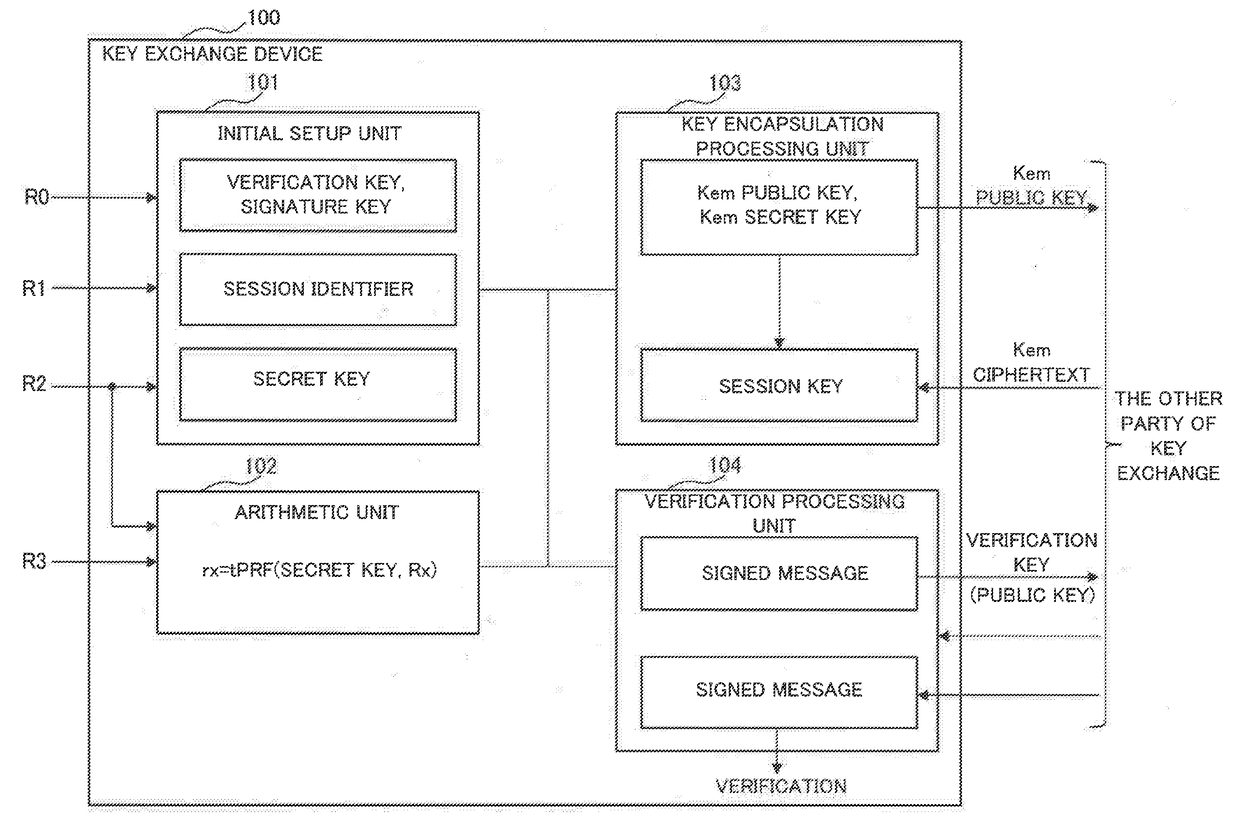
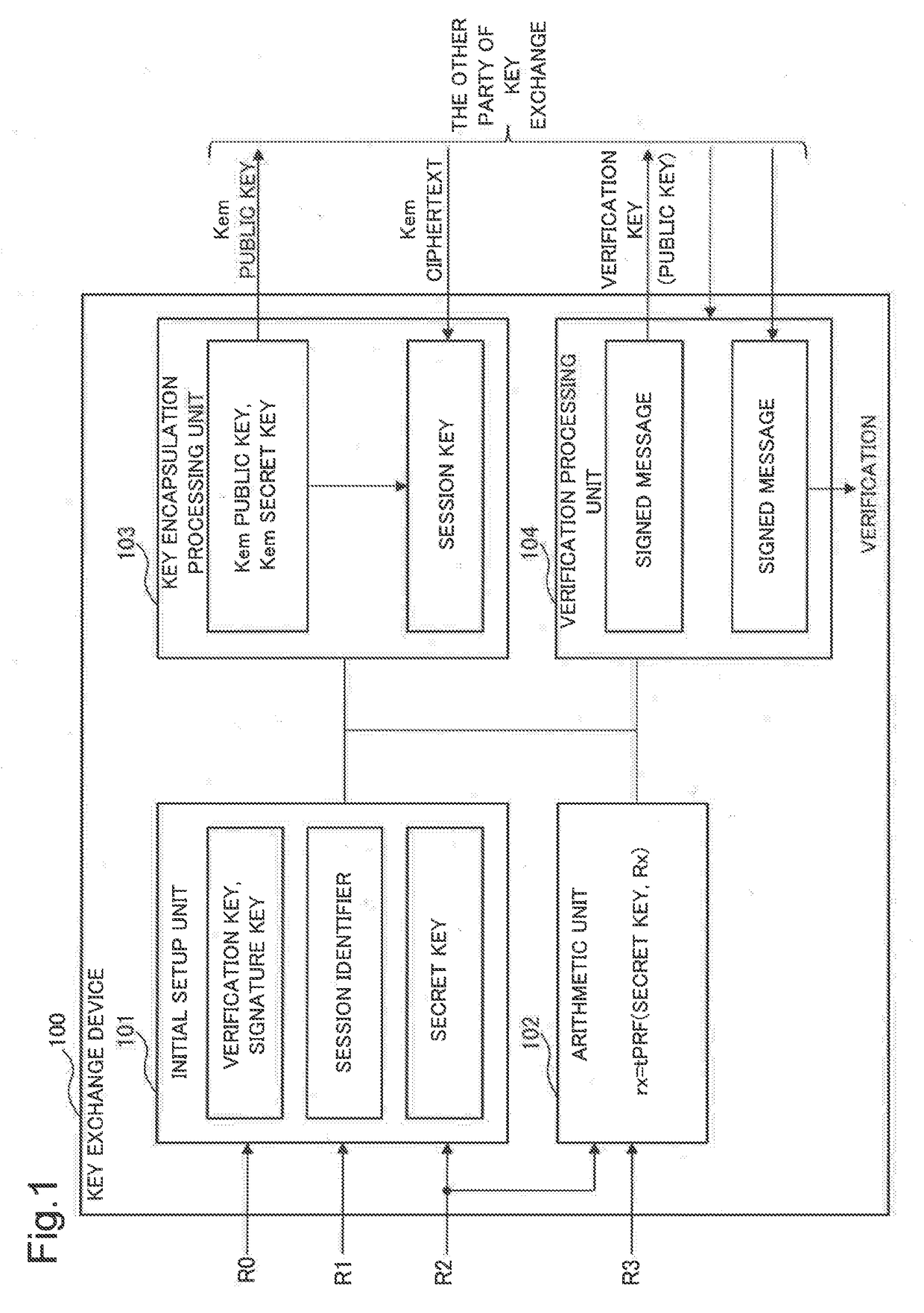
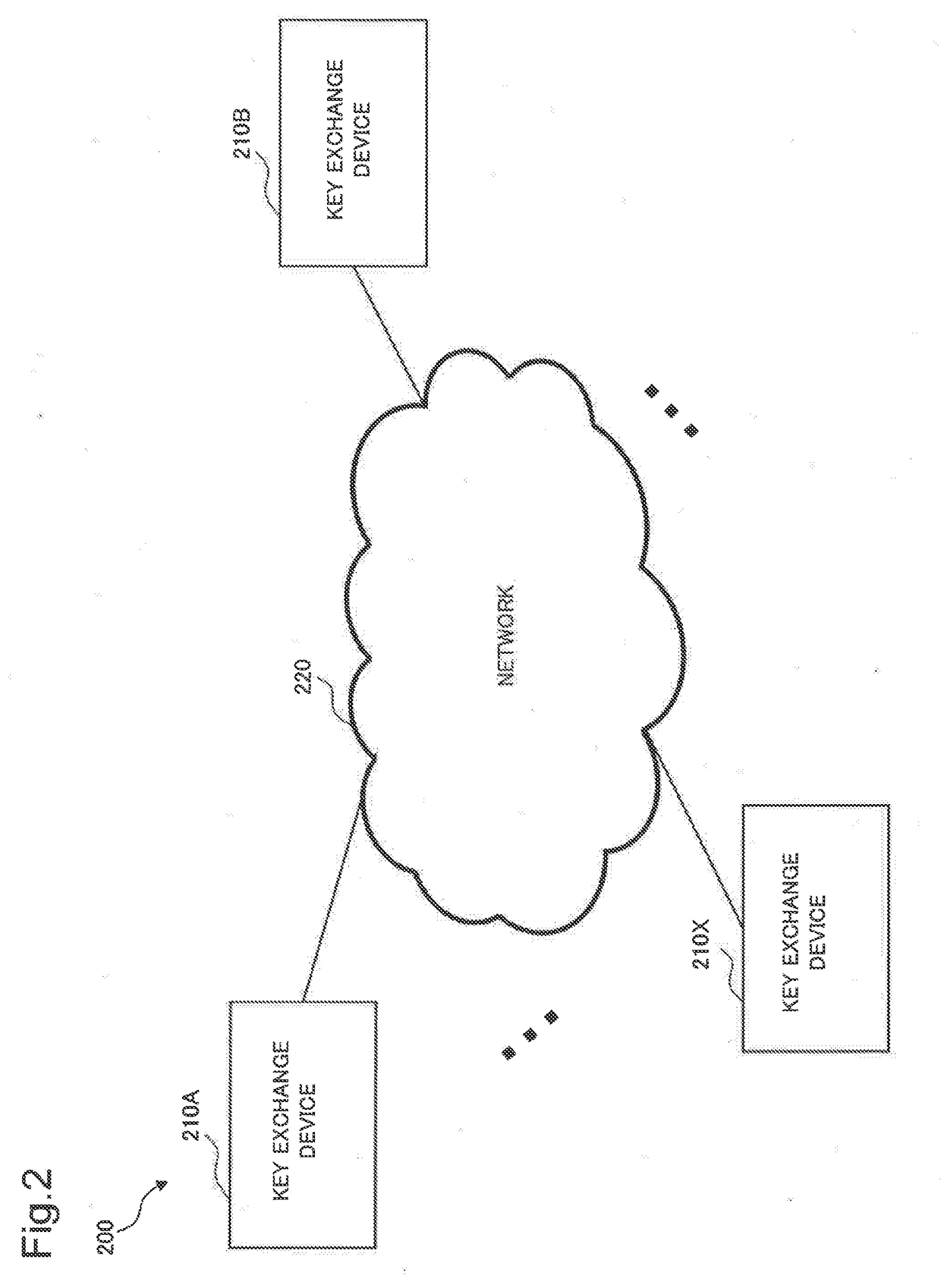
Key exchange system, key exchange method, key exchange device, control method thereof, and recording medium for storing control program
ActiveUS20170187524A1Key distribution for secure communicationMultiple keys/algorithms usageCiphertextMagnetic tape
A key exchange device includes an initial setup unit that generates a verification key that serves as a public key and a signature key based on a discretionary random tape, a session identifier based on a first random tape, and a secret key based on a second random tape; an arithmetic unit that generates an encrypted second random tape by an arithmetic operation of a pseudo-random function having the second random tape and the secret key as variables and an encrypted third random tape by an arithmetic operation of the pseudo-random function having a third random tape and the secret key as variables; a key encapsulation processing unit that generates a key-encapsulated public key and a key-encapsulated secret key based on the encrypted second random tape to transmit the key-encapsulated public key to an other party of key exchange and decrypts a session key using the key-encapsulated public key and a key-encapsulated ciphertext received from the other party of key exchange; and a verification processing unit that generates a signature based on the signature key, a transmission message and the encrypted third random tape, transmits the signature to the other party of key exchange and verifies a signature received from the other party of key exchange based on a verification key that is a public key of the other party of key exchange, a received message and the signature received.
Owner:NEC CORP
ABOOE method capable of being proved to be safe
ActiveCN103973449AKey distribution for secure communicationUser identity/authority verificationPlaintextCiphertext
The invention discloses an ABOOE method. The ABOOE method has the plaintext safety selection function and the ciphertext safety selection function. The encryption process based on ABE is decomposed into the offline stage and the online stage. At the offline stage, on the premise that plaintexts and needed attribute sets are unknown, complex calculation need by encryption is preprocessed; at the online stage, after messages and the attribute sets are known, ciphertexts can be generated only with a small amount of simple calculation. A construction method and corresponding schemes of an ABOOKEM are provided, and the safe and universal ABOOE method for converting the one-way ABOOKEM into CCA is constructed. According to the method, safety of the ABOOE method is effectively improved on the premise that the calculated amount is not increased. According to the ABOOE method, encryption efficiency of ABE is improved, and the ABOOE method is suitable for terminal equipment of which the calculated amount is highly limited.
Owner:北京未来云服科技有限公司
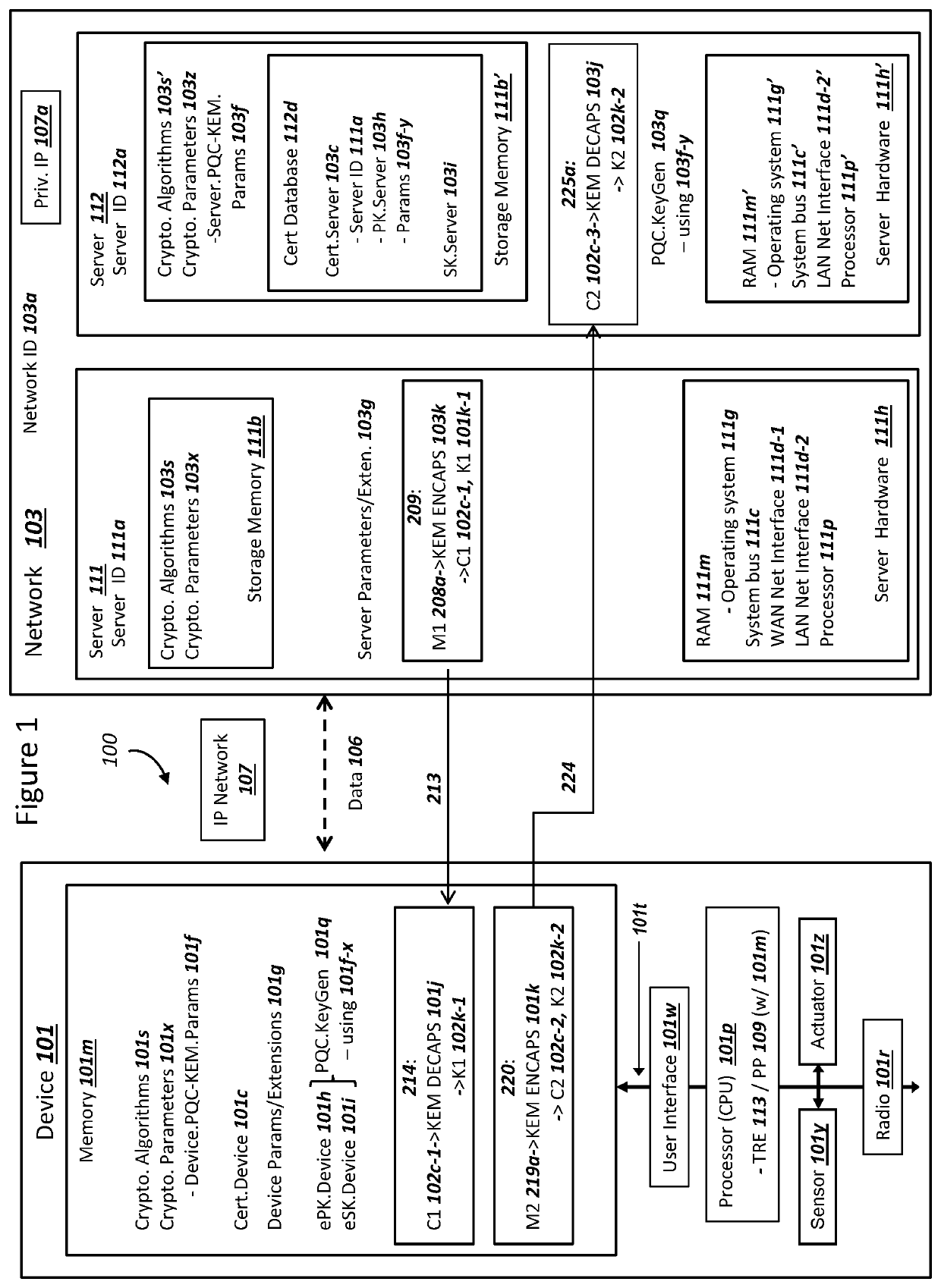
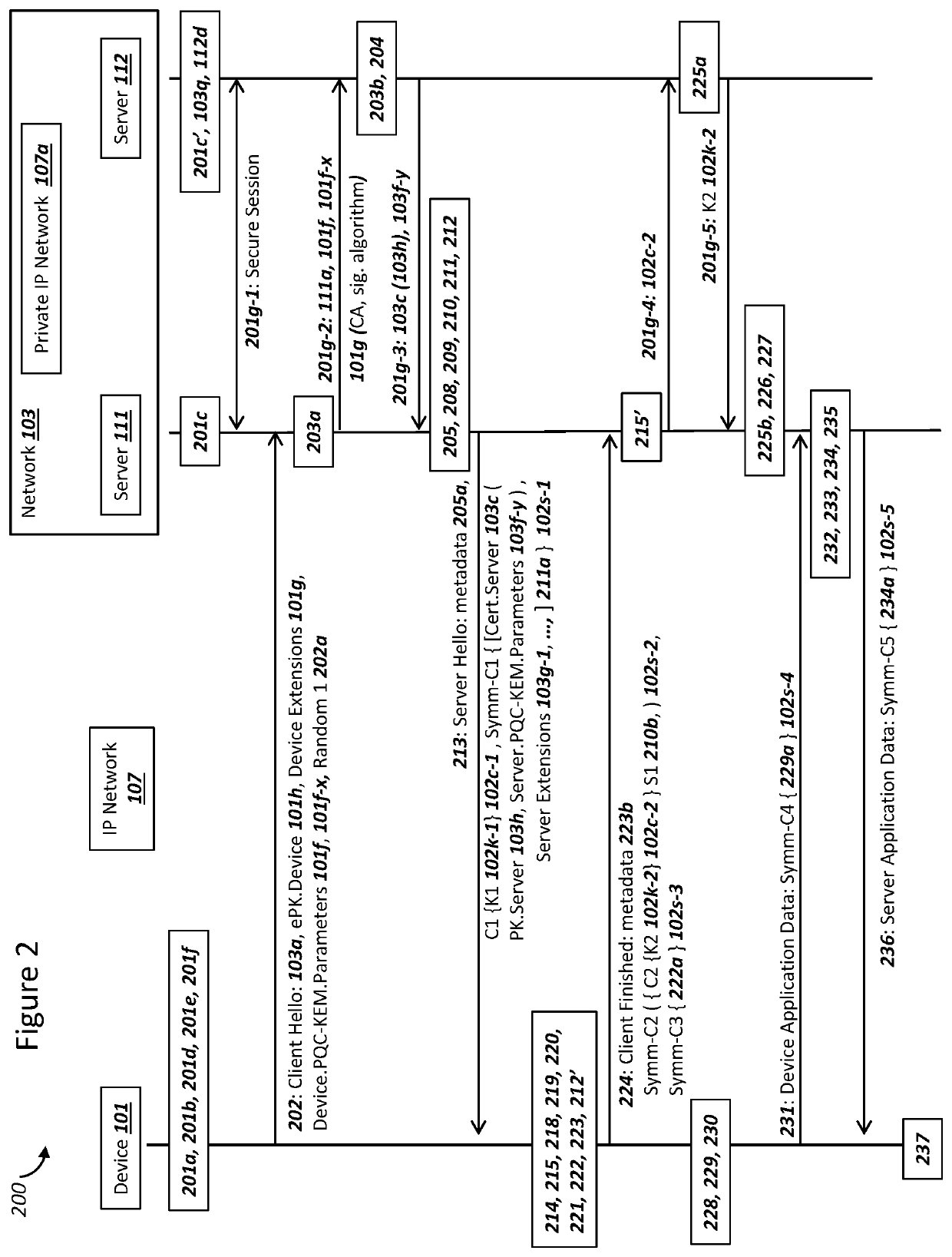
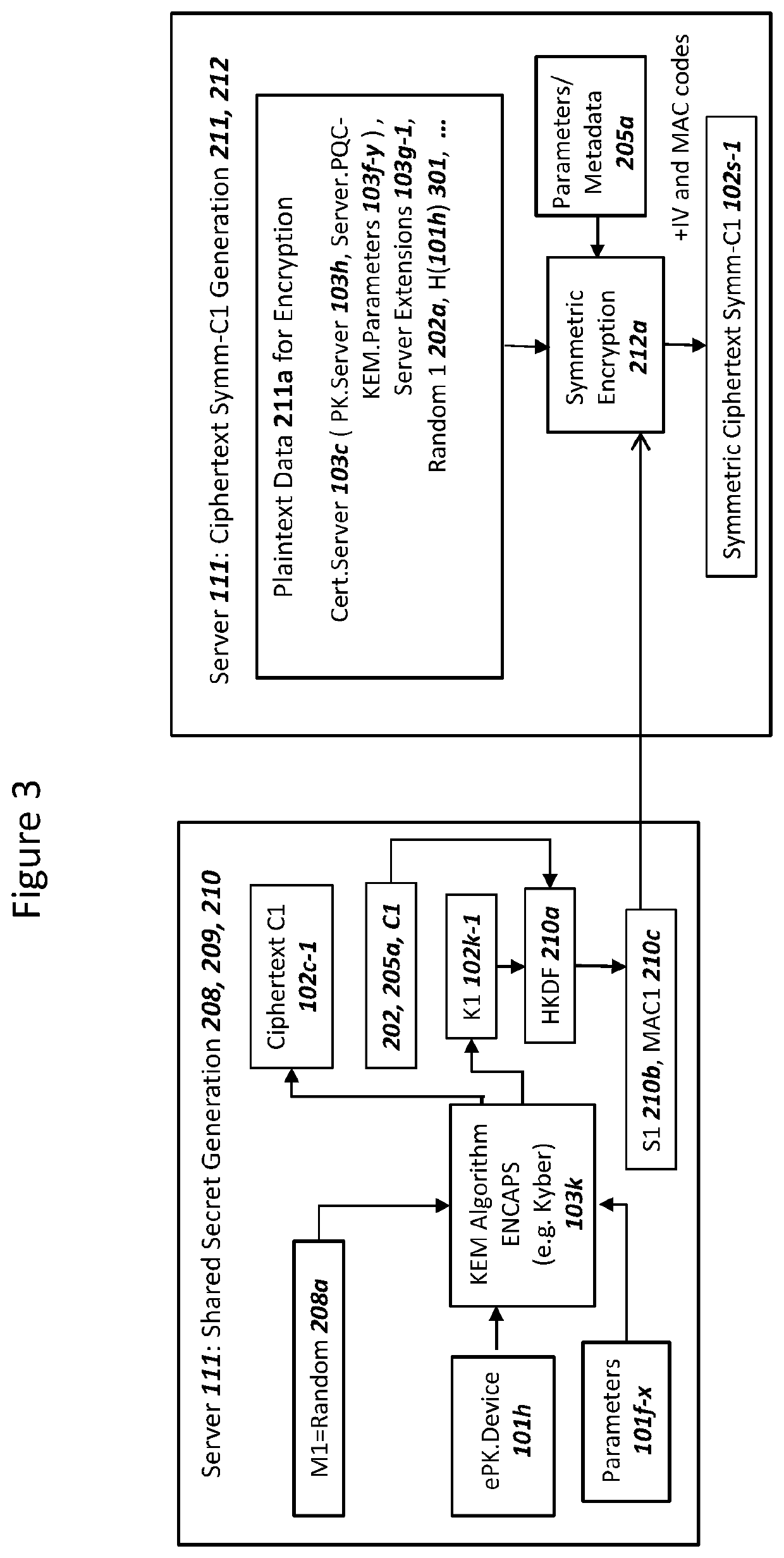
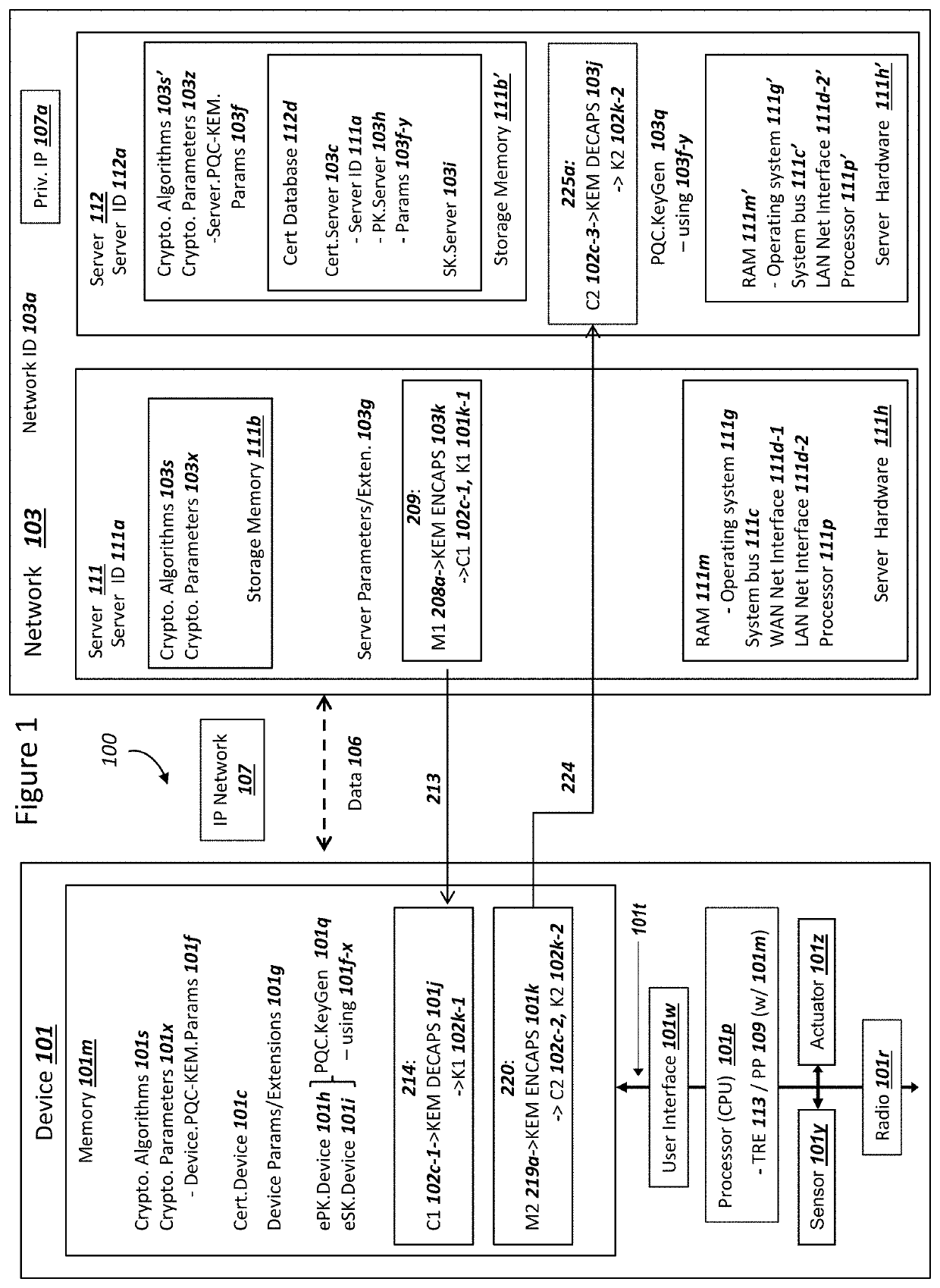
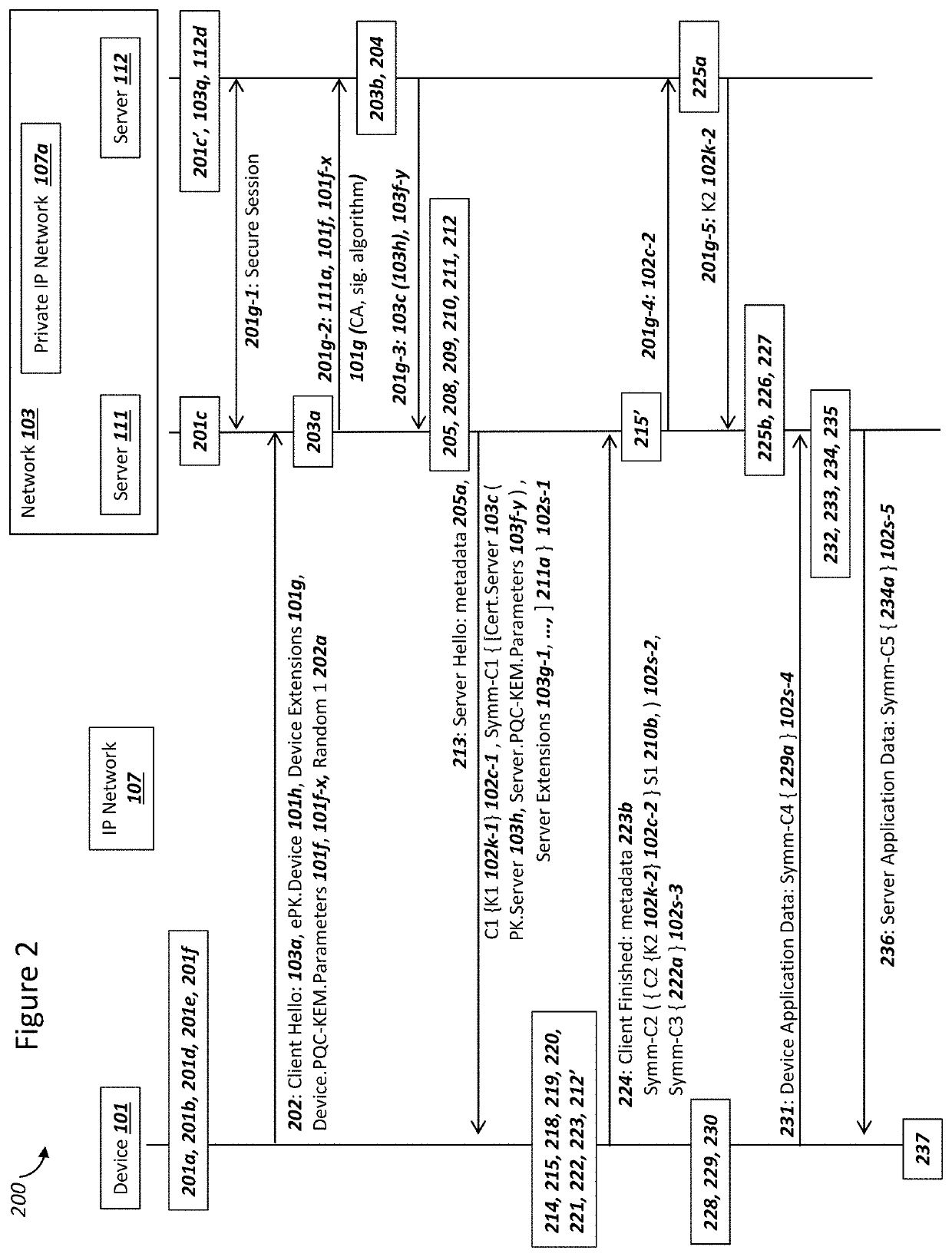
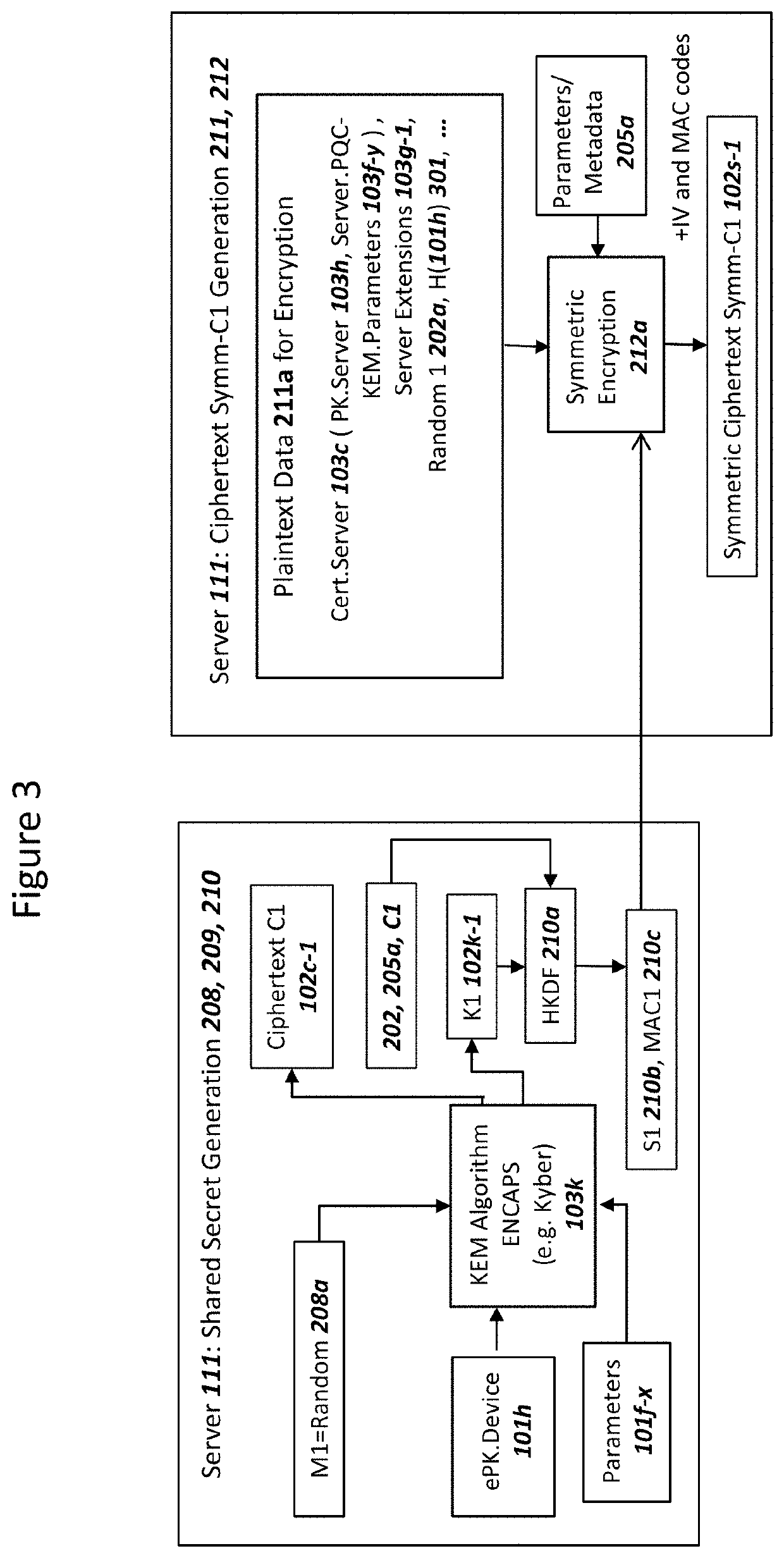
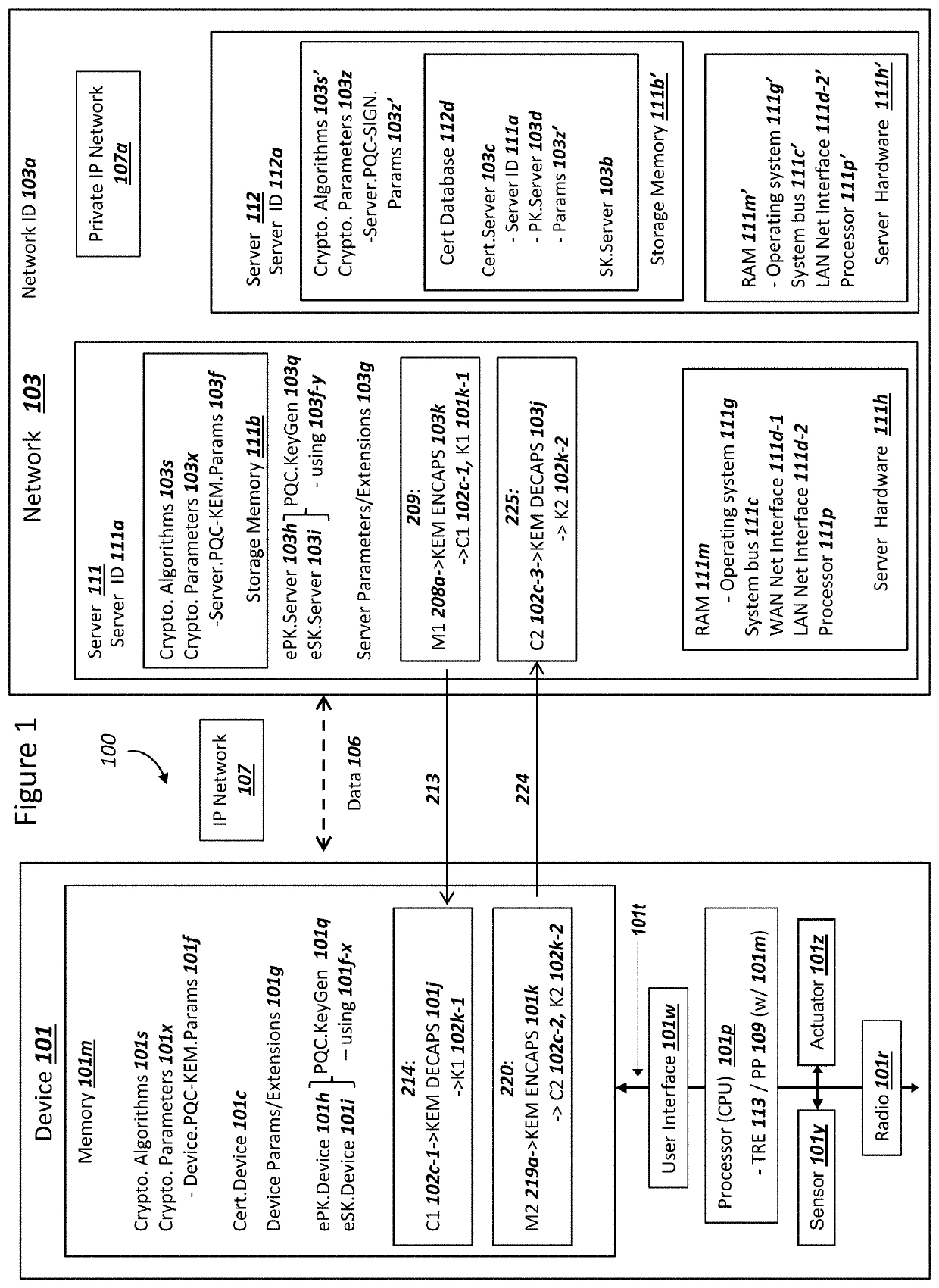
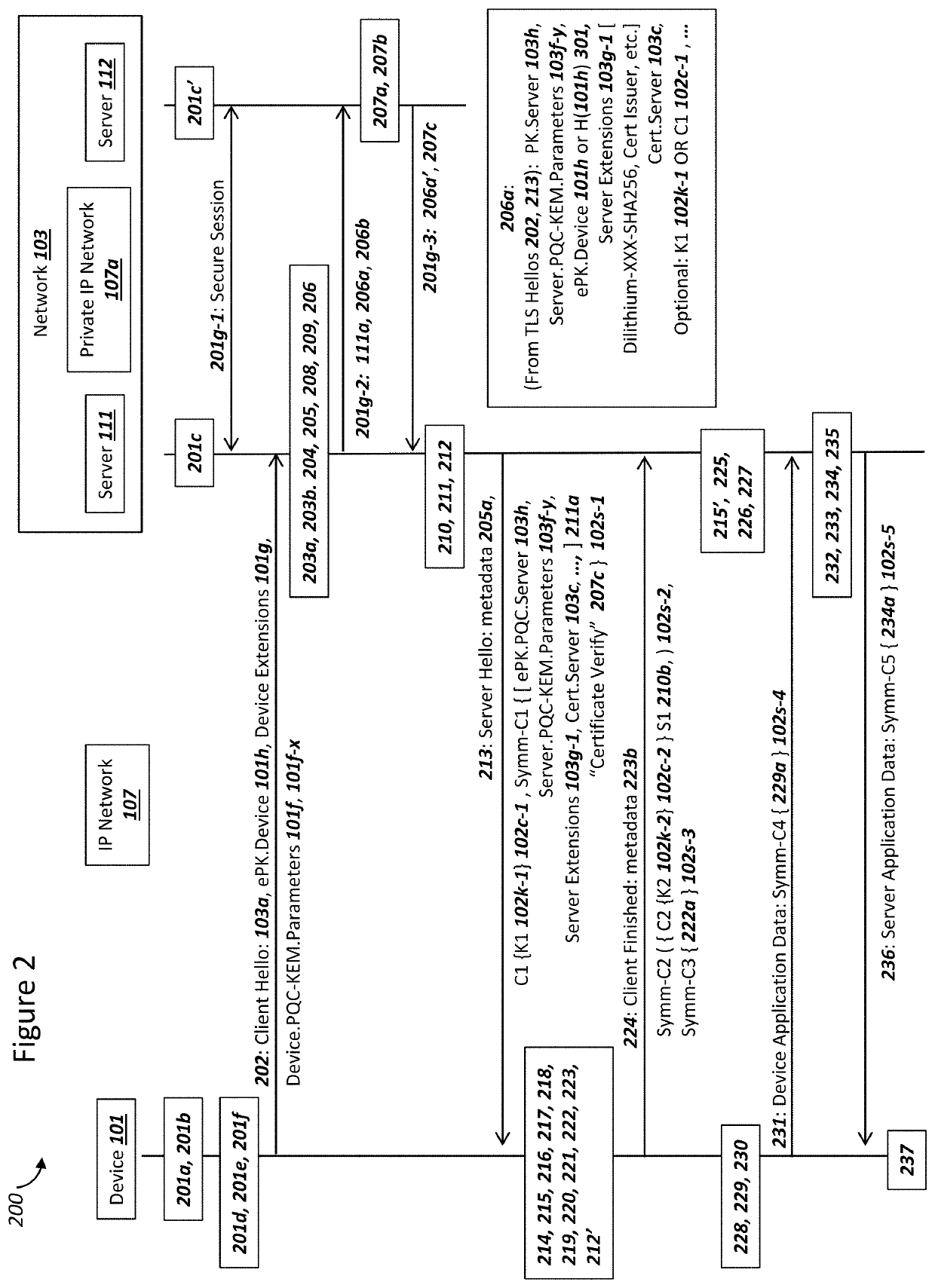
Network securing device data using two post-quantum cryptography key encapsulation mechanisms
ActiveUS11153080B1Less-long-term and detailed studyGuaranteed long-term securityKey distribution for secure communicationPublic key for secure communicationKey (cryptography)Ciphertext
A network and a device can support secure sessions with both (i) a post-quantum cryptography (PQC) key encapsulation mechanism (KEM) and (ii) forward secrecy. The device can generate (i) an ephemeral public key (ePK.device) and private key (eSK.device) and (ii) send ePK.device with first KEM parameters to the network. The network can (i) conduct a first KEM with ePK.device to derive a first asymmetric ciphertext and first shared secret, and (ii) generate a first symmetric ciphertext for PK.server and second KEM parameters using the first shared secret. The network can send the first asymmetric ciphertext and the first symmetric ciphertext to the device. The network can receive (i) a second symmetric ciphertext comprising “double encrypted” second asymmetric ciphertext for a second KEM with SK.server, and (ii) a third symmetric ciphertext. The network can decrypt the third symmetric ciphertext using the second asymmetric ciphertext.
Owner:NIX JOHN A
Key distribution and reconstruction method and device based on mobile internet
InactiveCN104754570AIncreased risk of deviating from agreementIncrease the number of expected execution roundsSecurity arrangementProvable securityReconstruction method
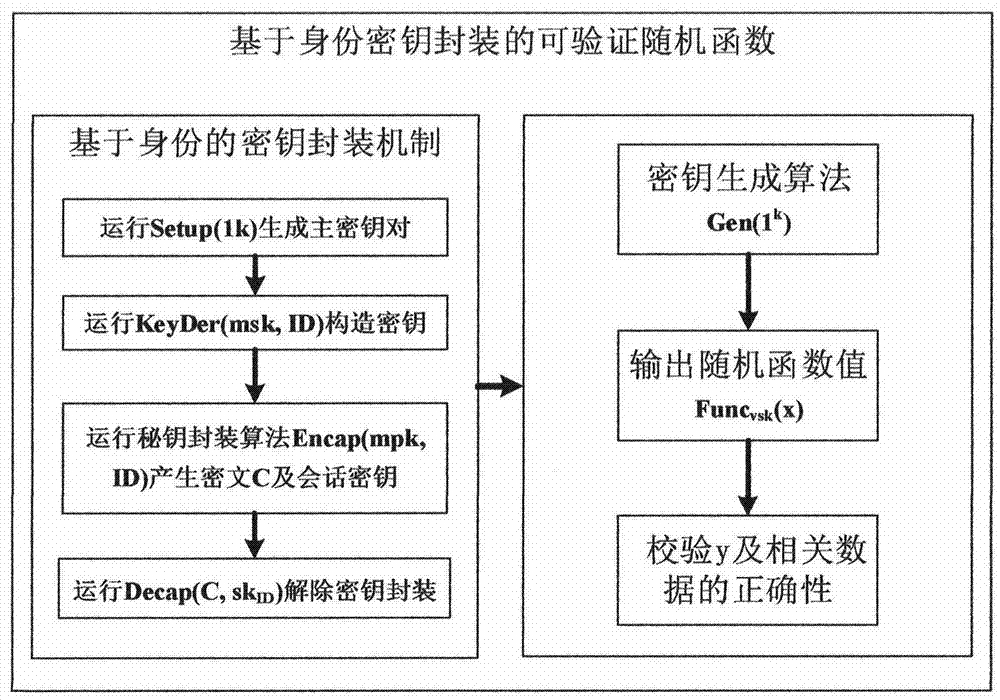
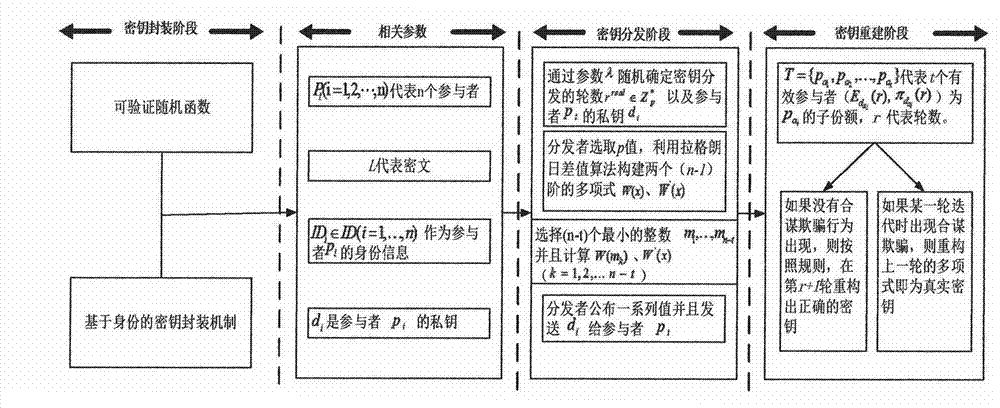
The invention provides a key distribution and reconstruction method based on the mobile internet. The method includes the steps of S1, constructing an identity-based key packaging model and a verifiable random function; S2, distributing keys; S3, reconstructing the keys. A calculable collusion-proof equilibrium method is designed, a protocol collusion-proof game-with-entropy model is constructed, and thus collusive attack of participants is prevented; a cryptographic protocol communication game model is constructed, and the defect that password protocols constructed in the broadcast communication network are unable to be implemented in the mobile internet is overcome; the key packaging mechanism applicable to the verifiable random function is studied, the rational key sharing protocol requiring no pubic key infrastructure is designed, and calculation fairness and delivery in the mobile internet is guaranteed; finally, the protocol is subjected to security analysis and proving through the theory of provable security.
Owner:HENAN NORMAL UNIV
Unicast secret communication method and multicast secret communication method based on identity
InactiveCN103297225AGuaranteed privacyEnsure safetyKey distribution for secure communicationMultiple keys/algorithms usageSecure communicationIdentification key
The invention relates to a unicast secret communication method and a multicast secret communication method based on identity, and belongs to the field of communication and information security technologies. Security communication channels are established based on identity cryptography, and privacy and security of legal user operation are guaranteed. Key management is easy, a system key management center only needs to be responsible for creating distributing a private key to each user and manages a master key of the security center and a set of common parameter files, identity is taken as an identification key to be packaged, and secret communication based on the cryptology can be realized as long as identity labels of the others are acquired.
Owner:顾纯祥
Distributed data security sharing method and system based on block chain, and computer readable medium
ActiveCN113595971AImprove production efficiencyGuaranteed safe transmissionKey distribution for secure communicationUser identity/authority verificationPlaintextCiphertext
The invention discloses a distributed data security sharing method and system based on a block chain, and a computer readable medium. The method comprises the following steps: outputting a system master key pair and a user key pair; performing encryption; packaging and then uploading the system master key to the block chain; generating a conversion key by the master key agency storage node; converting the key calculation node to generate a new capsule; obtaining the master key ciphertext from the block chain by the data user and obtaining the system master key; obtaining an attribute private key; and obtaining the shared data ciphertext by the data user, inputting the attribute private key, and obtaining the plaintext through a decryption algorithm. According to the distributed data security sharing method and system based on the block chain, and the computer readable medium, key encapsulation of the master key is realized by using a distributed proxy key encapsulation mechanism, the problem of secure distribution and management of the master key in a block chain network is solved, the generation efficiency of the private key is improved, and the problems of safe distribution and management of the master key in the block chain network and the like in the prior art are solved.
Owner:YUNNAN UNIVERSITY OF FINANCE AND ECONOMICS +1
Public key encryption method based on cells
ActiveCN110138752AResist attackShorten the lengthKey distribution for secure communicationPlaintextCiphertext
The invention discloses a public key encryption method based on cells. The invention firstly proposes a class of asymmetric modular band error learning (AMLWE) mathematics difficulty problems, and also provides variations and generalized definitions of the class of mathematics difficulty problems. Based on the AMLWE mathematical difficulty problem, the invention provides a public key encryption method for selecting plaintext security on a grid. Based on the encryption method, the invention also provides a key encapsulation mechanism for selecting ciphertext security and a public key encryptionmethod for selecting ciphertext security. The public key encryption method and the key packaging mechanism designed by the invention have the characteristics and advantages of proving security, resisting quantum computer attacks, being short in public key and ciphertext length, high in calculation efficiency, flexible in parameter selection and the like. By utilizing a universal conversion method, the invention also provides (authenticated) a key exchange protocol.
Owner:北京信息科学技术研究院
Data decryption method based on quantum shared key
InactiveCN107809314AImprove encryption efficiencySimple processKey distribution for secure communicationCiphertextData content
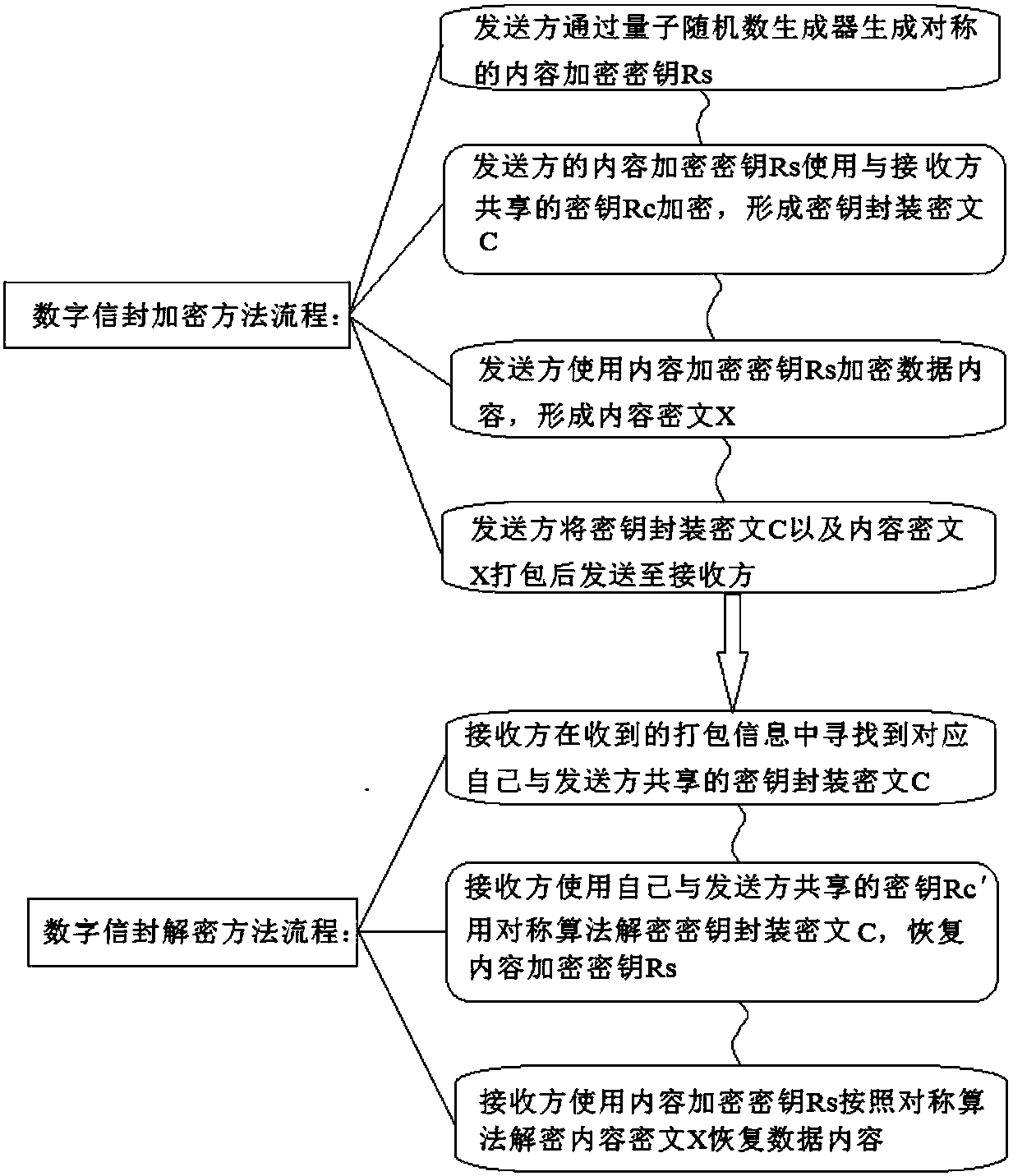
A data encryption method based on a quantum shared key. The data sender generates a symmetric content encryption key Rs through a quantum random number generator; the content encryption key Rs of the sender is encrypted with the key Rc shared with the receiver to form an The key-encapsulated ciphertext C; the sender uses the content encryption key Rs to encrypt the data content to form the content ciphertext X; the sender packs the key-encapsulated ciphertext C and the content ciphertext X and sends it to the receiver, and the receiver uses the key The Rc decryption key encapsulates the ciphertext C to obtain the content encryption key Rs, and then uses Rs to decrypt the content ciphertext X to restore the data content. Compared with the prior art, the sending end of the present invention encrypts data content with a local content encryption key, encrypts the content encryption key with a key shared with the receiving end, and encrypts data with a content encryption key. Compared with using a shared key The method for directly encrypting the data content and then transmitting it does not need to encrypt the data content multiple times for the point-to-point communication, thereby improving the encryption efficiency.
Owner:ZHEJIANG QUANTUM TECH CO LTD
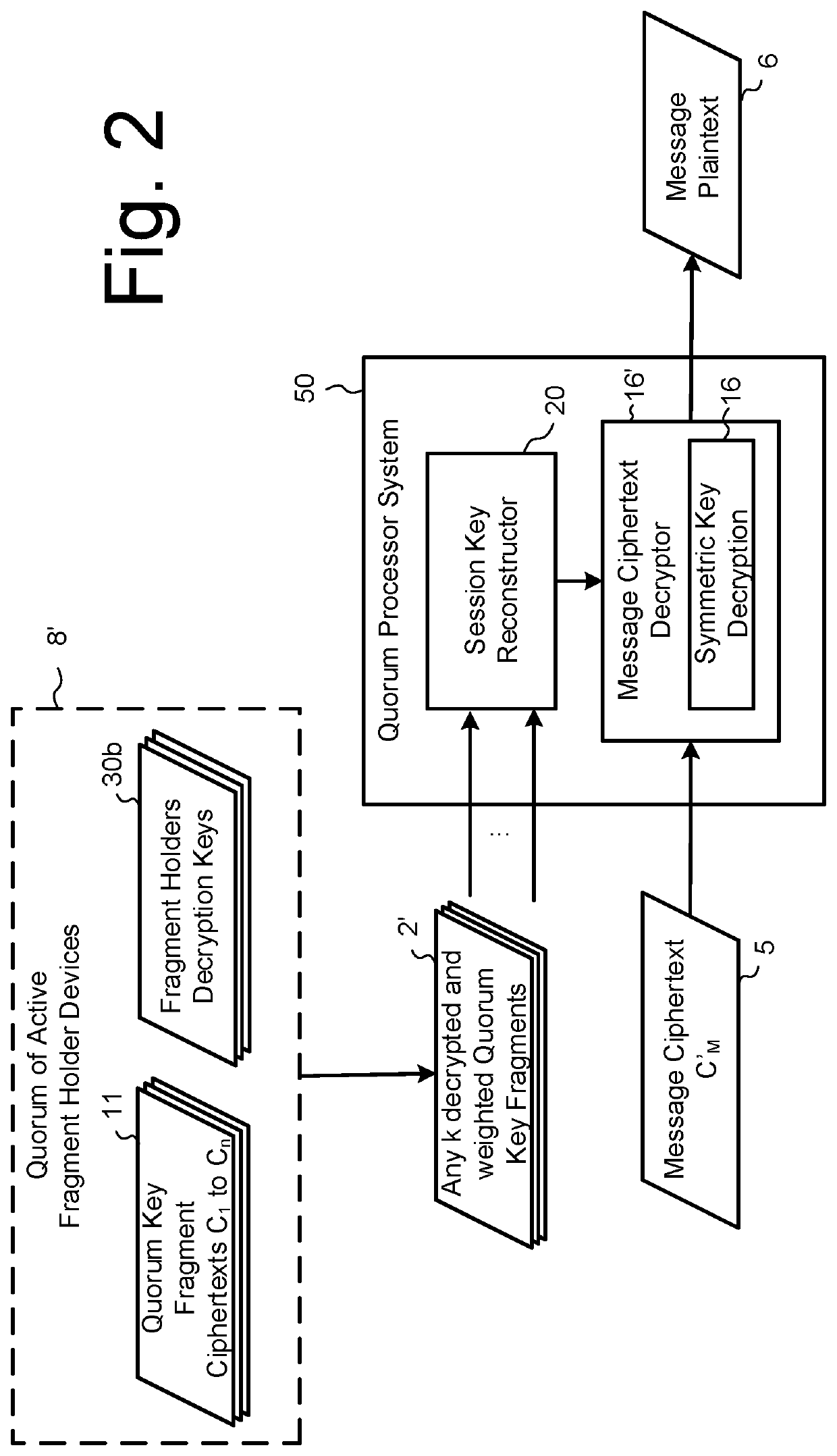
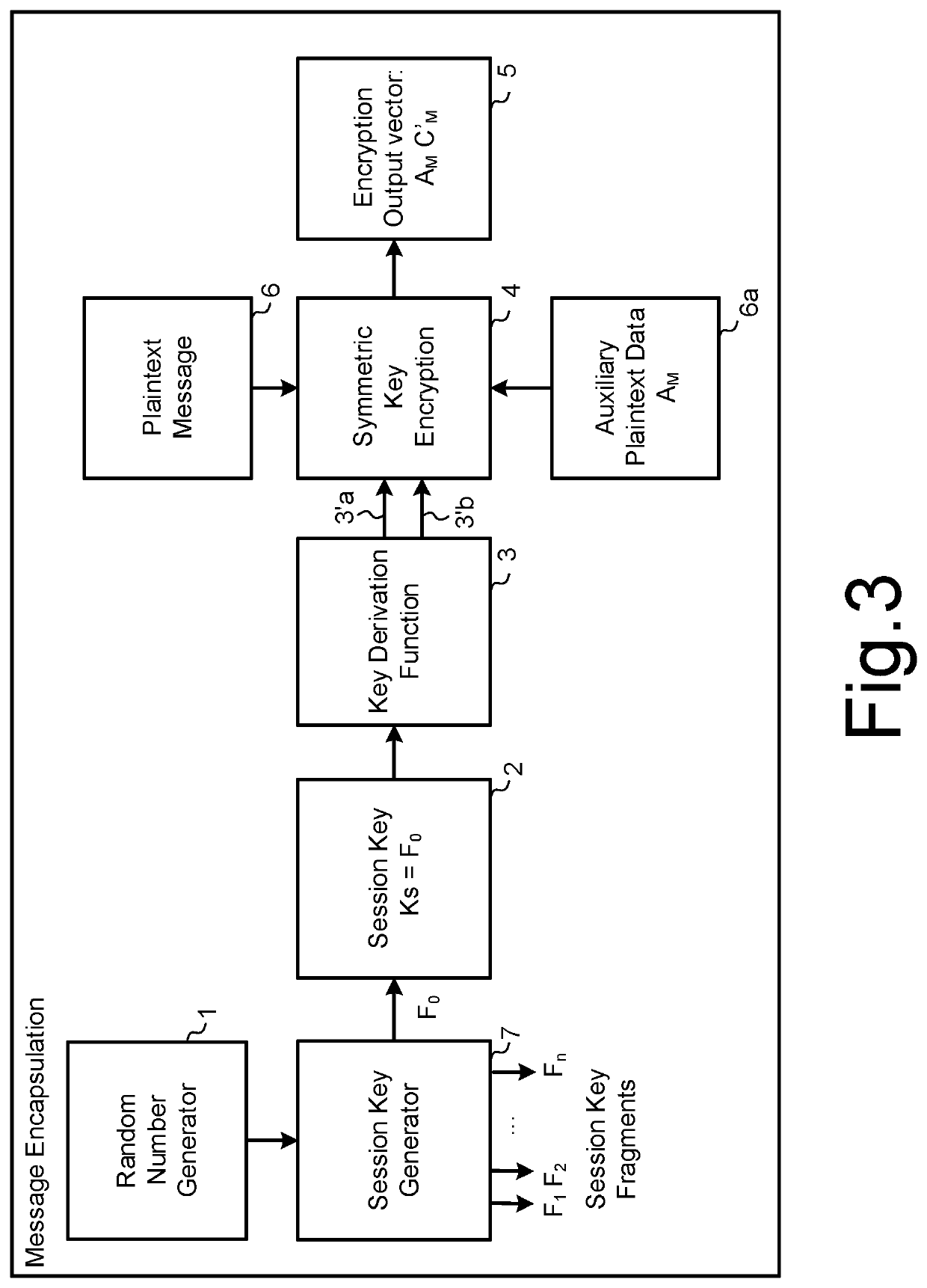
Ciphertext based quorum cryptosystem
ActiveUS20210099290A1Low costImprove efficiencyKey distribution for secure communicationMultiple keys/algorithms usageInternet privacyCiphertext
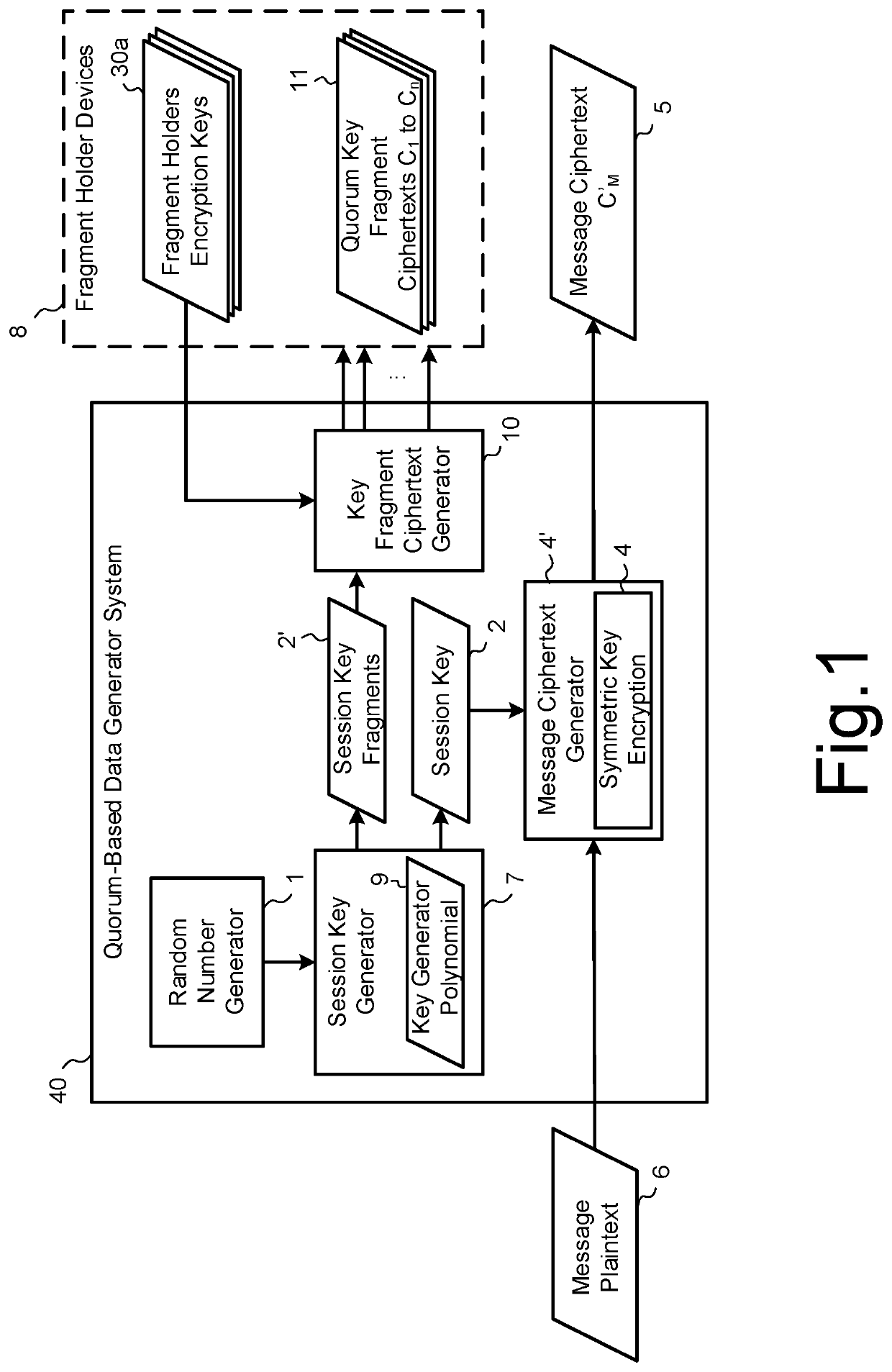
Methods are described for constructing a secret key by multiple participants from multiple ciphertexts such that any quorum combination of participants can decrypt their respective ciphertexts and so generate a fixed number of key fragments that can be combined by a recipient to generate the secret key. Worked examples are described showing how the encryption keys for the ciphertexts may be key wrapped using a key encapsulation mechanism for which ciphers that are resistant to attack by a quantum computer may be used. In these cases, a post-quantum quorum system is realised. Methods are described by which the quorum key fragment ciphertexts may be updated so that the original key fragments become invalid without necessitating any change to the secret key.
Owner:PQ SOLUTIONS LTD
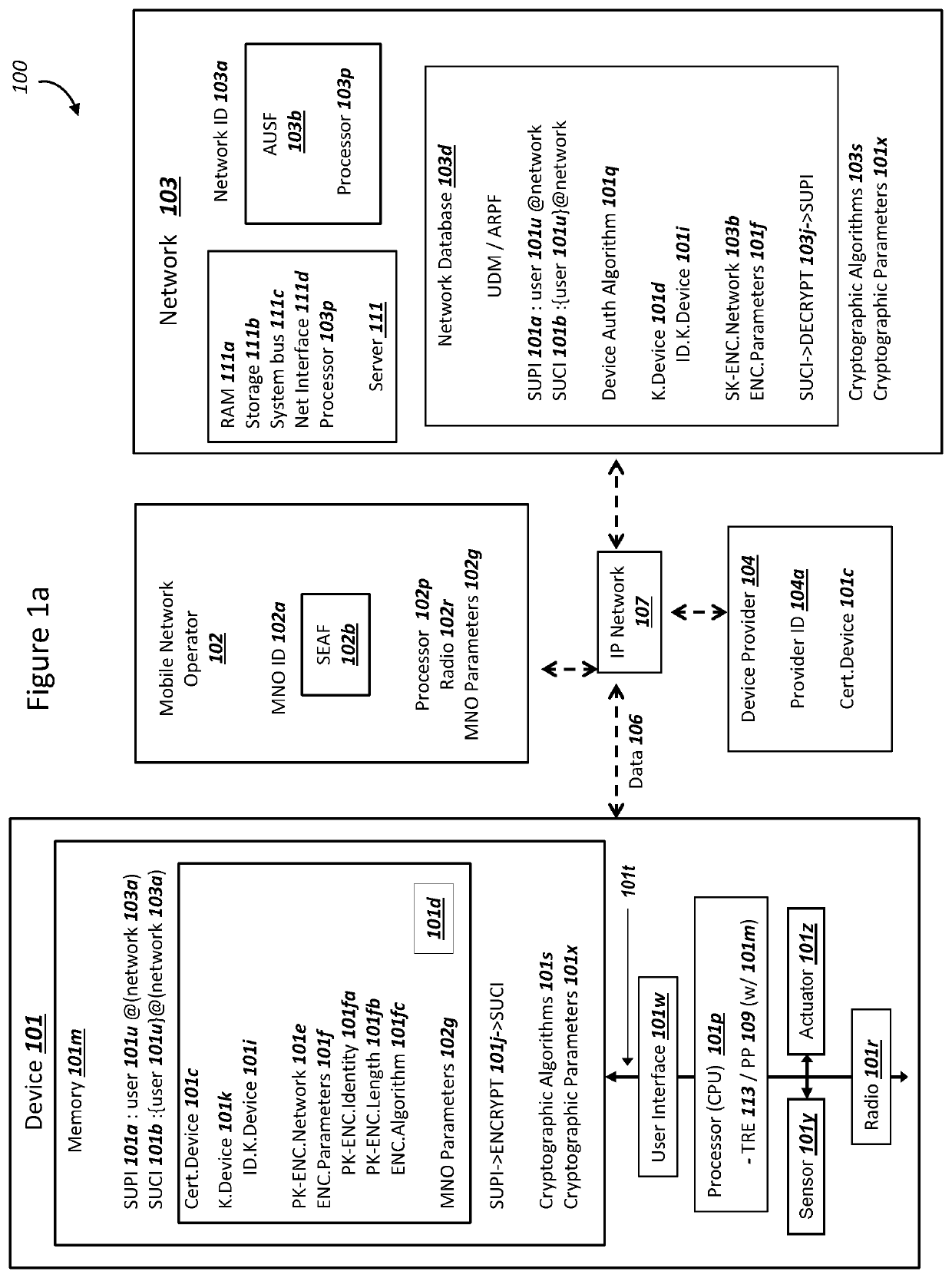
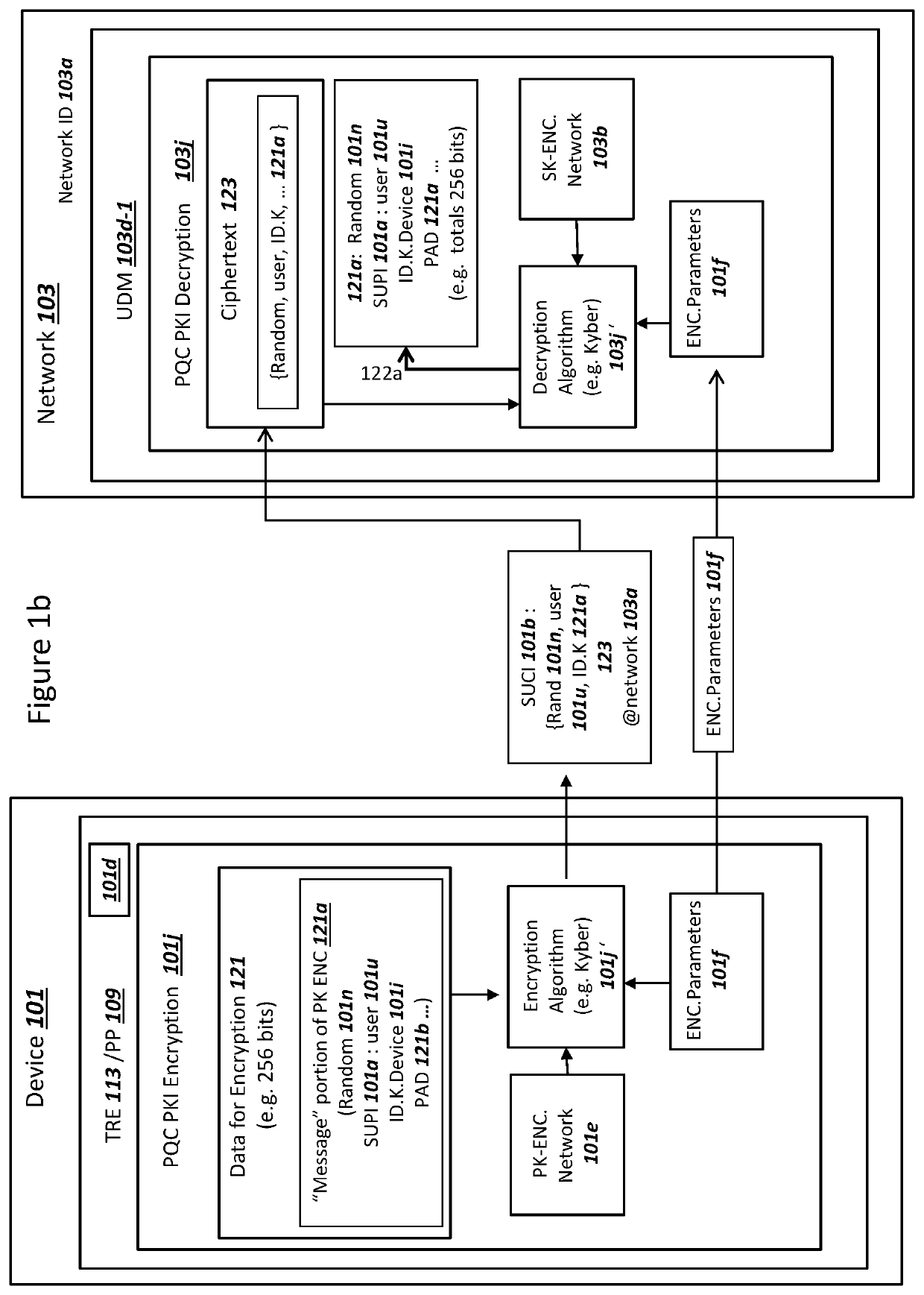
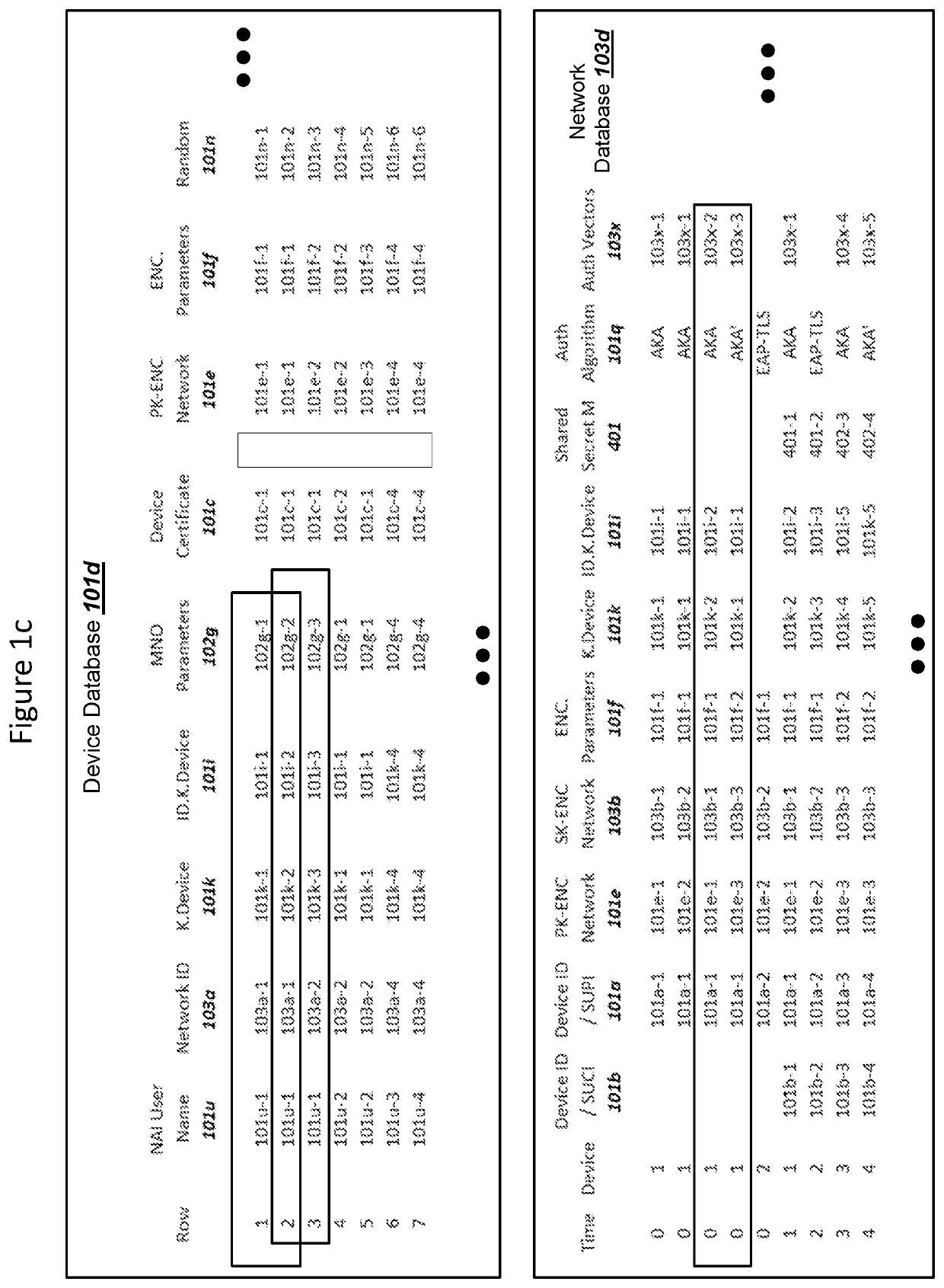
Subscription Concealed Identifier (SUCI) Supporting Post-Quantum Cryptography
PendingUS20210409214A1Key distribution for secure communicationPublic key for secure communicationKey (cryptography)Ciphertext
A device and a network can authenticate using a subscription concealed identifier (SUCI). The device can store (i) a plaintext subscription permanent identifier (SUPI) for the device, (ii) a network static public key, and (iii) a key encapsulation mechanism (KEM) for encryption using the network static public key. The network can store (i) a device database with the SUPI, (ii) a network static private key, and (iii) the KEM for decryption using the network static private key. The device can (i) combine a random number with the SUPI as input into the KEM to generate a ciphertext as the SUCI, and (ii) transmit the ciphertext / SUCI to the network. The network can (i) decrypt the ciphertext using the KEM to read the SUPI, (iii) select a key K from the device database using the SUPI, and (iv) conduct an Authentication and Key Agreement (AKA) with the selected key K.
Owner:NIX JOHN A
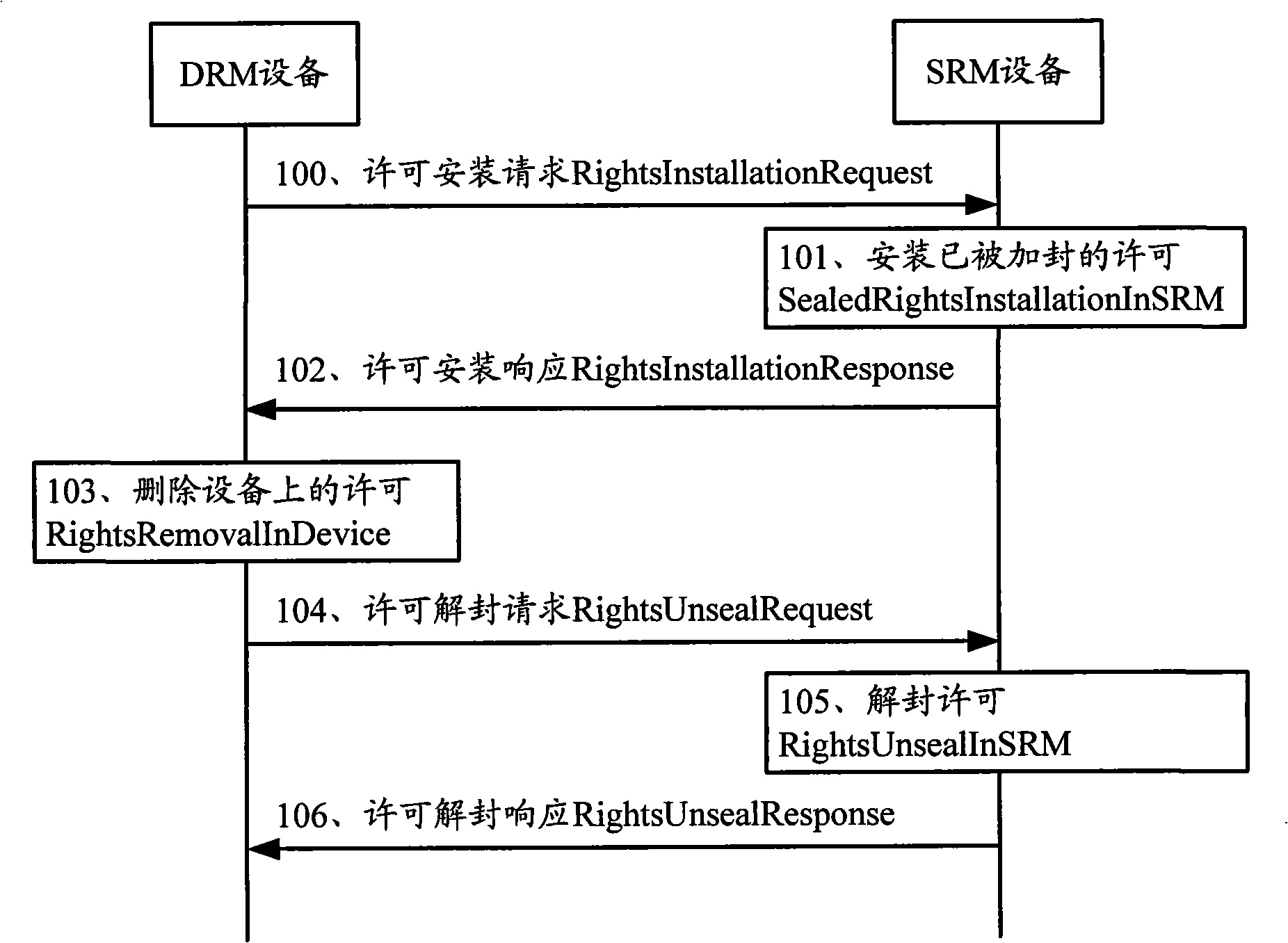
Method and apparatus for encapsulating field permission cryptographic key
ActiveCN101325486AAchieve transferGuaranteed security protectionError preventionUser identity/authority verificationCiphertextKey encapsulation
The invention discloses an encapsulation method of domain license cipher key, include: encrypting the content encryption key and message verification cipher key by using the domain cipher key, for acquiring a first cipher text; encapsulating the first cipher text into the domain license. The invention simultaneously discloses a communication apparatus. Adoption of the invention can realize domain licensed cipher key encapsulation process, ensures the security protection of cipher key information in the transference process, and has simple realization and strong practicability.
Owner:HUAWEI TECH CO LTD
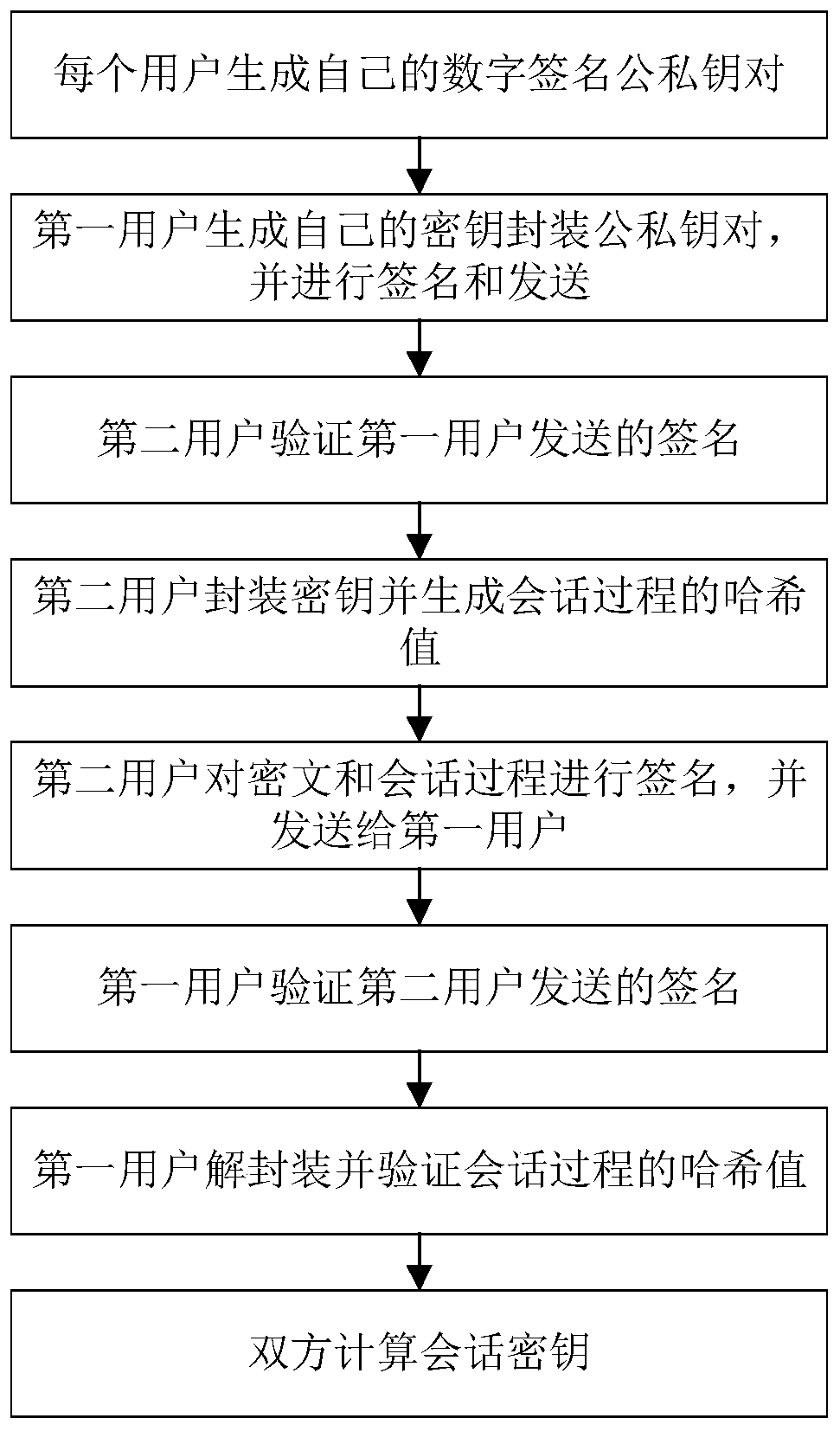
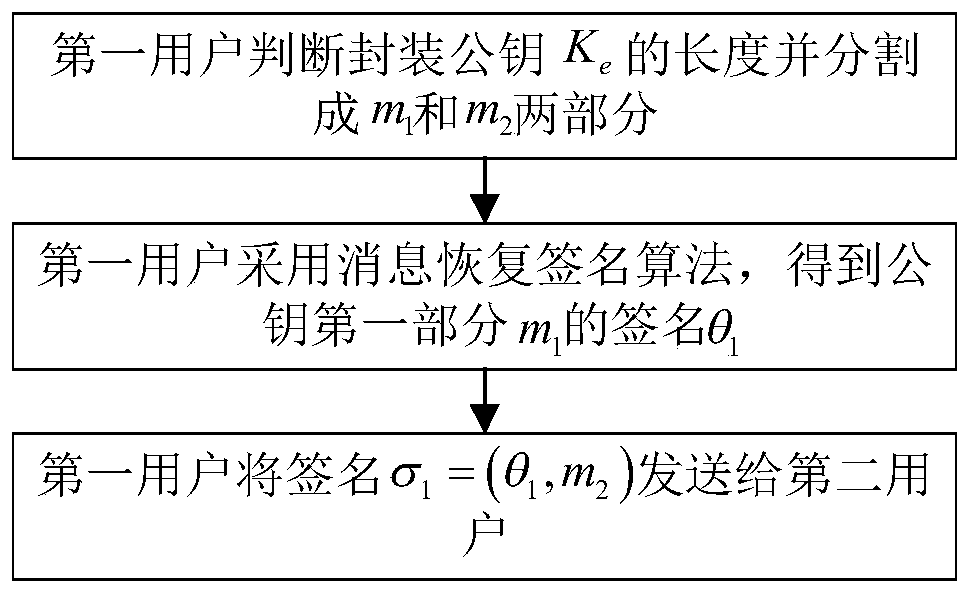
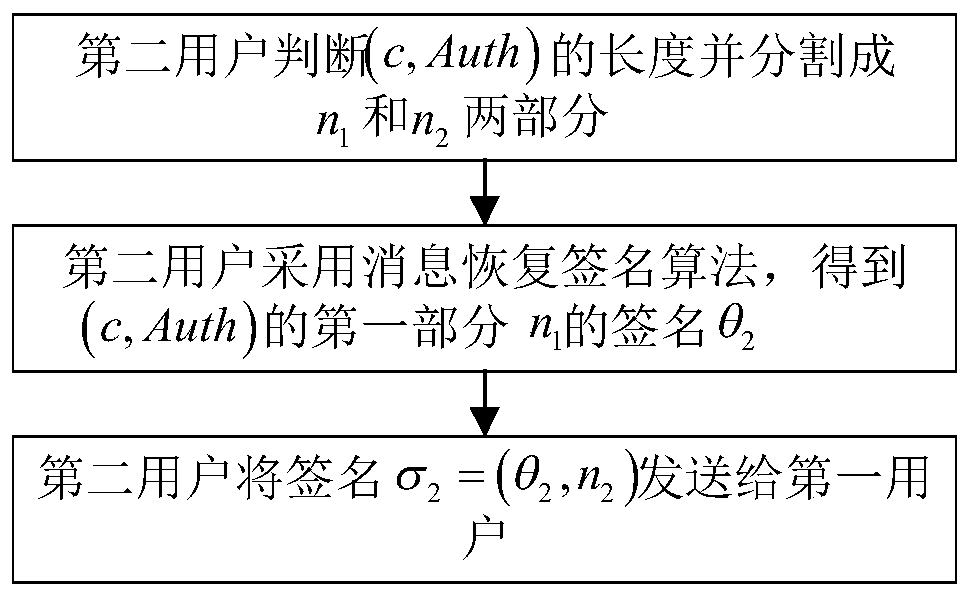
Authentication key exchange method based on message recovery signature
ActiveCN109995509AReduce trafficReduce overheadKey distribution for secure communicationEncryption apparatus with shift registers/memoriesUser verificationDigital signature
Owner:XIDIAN UNIV
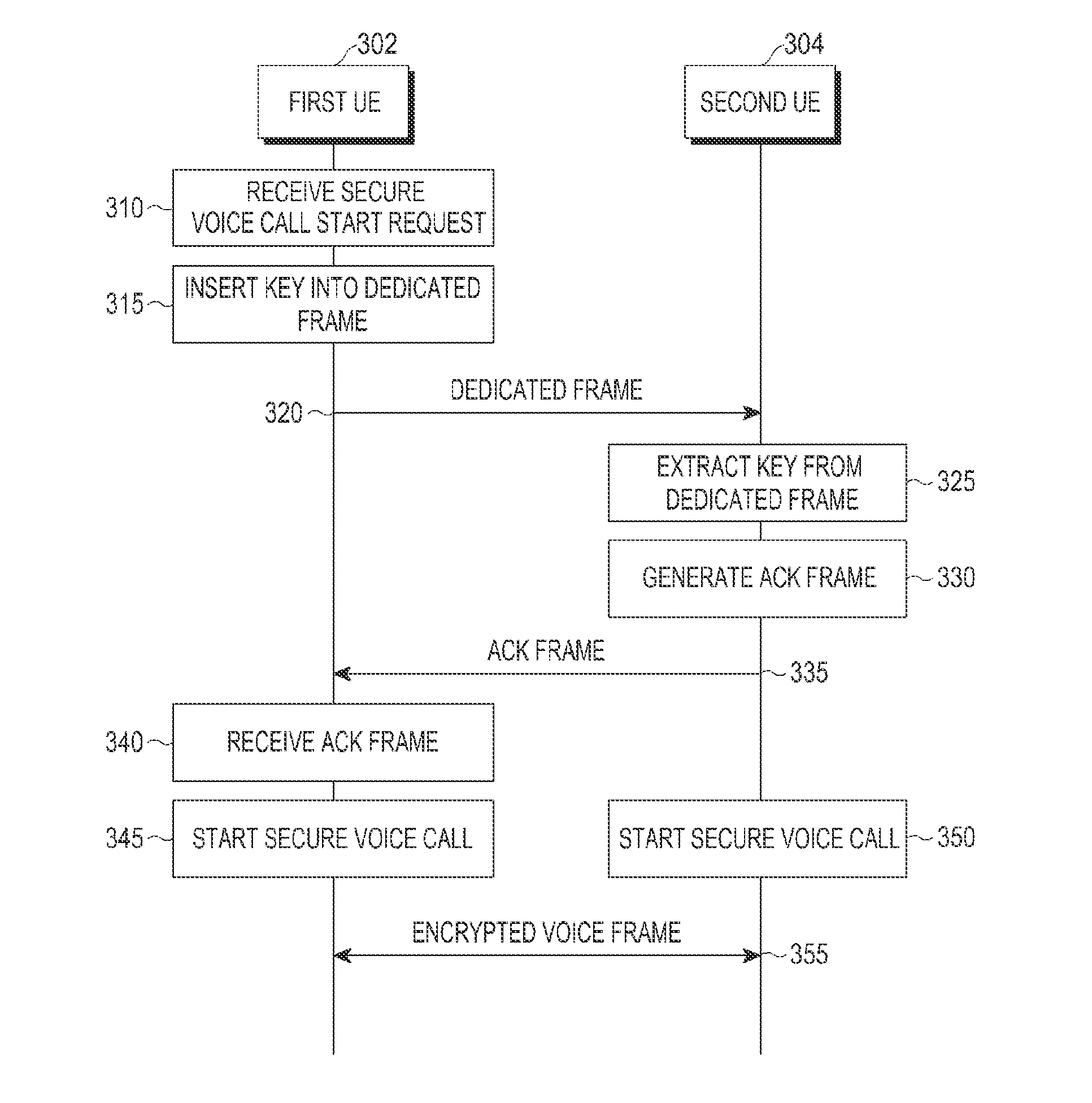
Method and apparatus for performing secure voice call
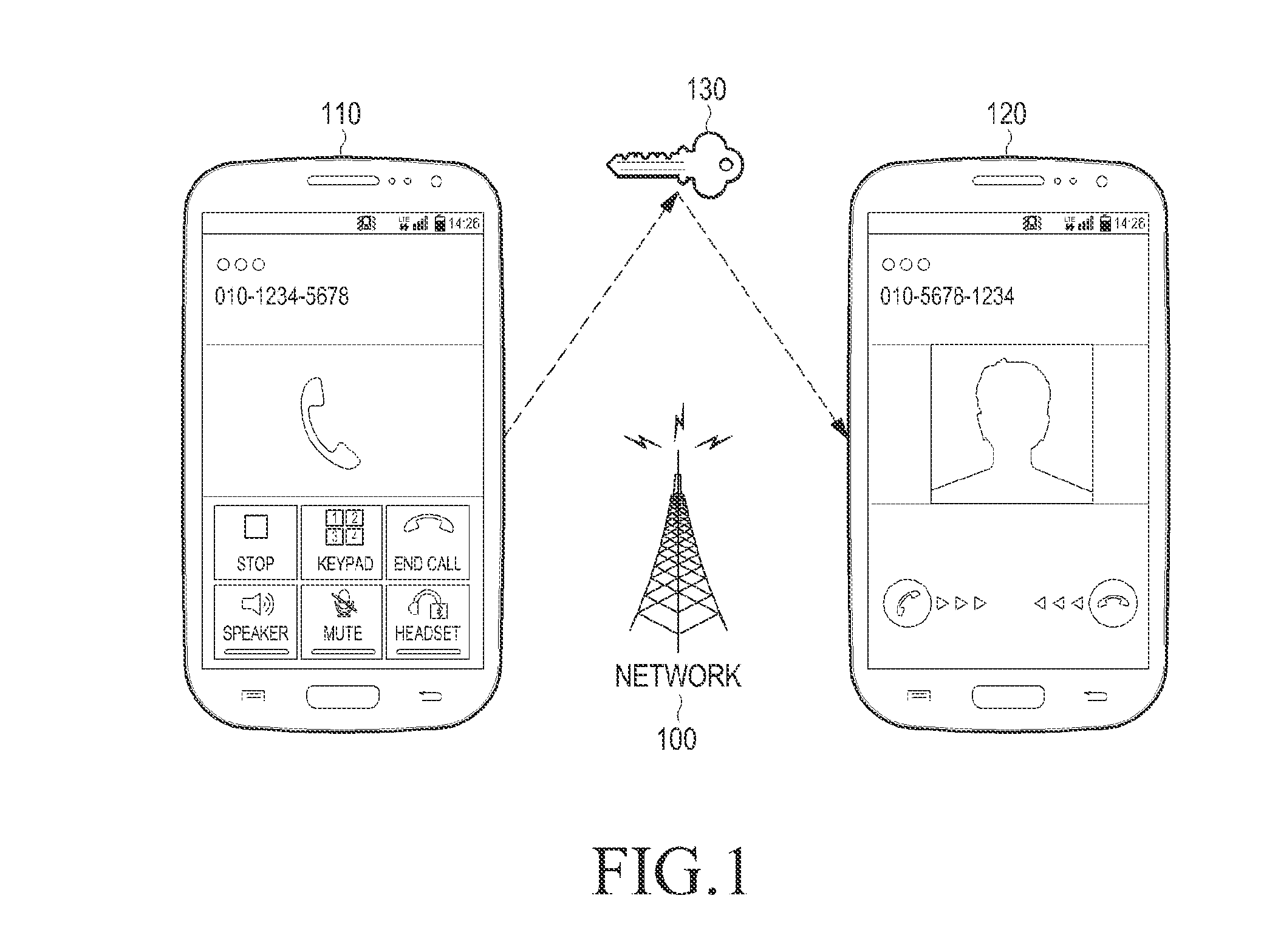
InactiveUS20150180663A1Multiple keys/algorithms usageSecret communicationComputer hardwareSecure voice
A method and apparatus for performing a secure voice call is provided. The method includes generating an encryption key to be used in the secure voice call, encapsulating the encryption key using a pre-agreed upon master key, generating at least one dedicated frame including the encapsulated encryption key, transmitting the at least one dedicated frame in place of at least one voice frame generated by a vocoder to a counterpart User Equipment (UE), receiving an Acknowledgement (ACK) frame indicating successful reception of the encryption key from the counterpart UE, encrypting the at least one voice frame generated by the vocoder using the encryption key and transmitting the encrypted at least one voice frame to the counterpart UE, after receiving the ACK frame, and decrypting the at least one voice frame received from the counterpart UE using the encryption key, after receiving the ACK frame.
Owner:SAMSUNG ELECTRONICS CO LTD
Device Securing Communications Using Two Post-Quantum Cryptography Key Encapsulation Mechanisms
ActiveUS20220038269A1Improve securityImprove security levelKey distribution for secure communicationPublic key for secure communicationKey (cryptography)Ciphertext
A network and a device can support secure sessions with both (i) a post-quantum cryptography (PQC) key encapsulation mechanism (KEM) and (ii) forward secrecy. The device can generate (i) an ephemeral public key (ePK.device) and private key (eSK.device) and (ii) send ePK.device with first KEM parameters to the network. The network can (i) conduct a first KEM with ePK.device to derive a first asymmetric ciphertext and first shared secret, and (ii) generate a first symmetric ciphertext for PK.server and second KEM parameters using the first shared secret. The network can send the first asymmetric ciphertext and the first symmetric ciphertext to the device. The network can receive (i) a second symmetric ciphertext comprising “double encrypted” second asymmetric ciphertext for a second KEM with SK.server, and (ii) a third symmetric ciphertext. The network can decrypt the third symmetric ciphertext using the second asymmetric ciphertext.
Owner:NIX JOHN A
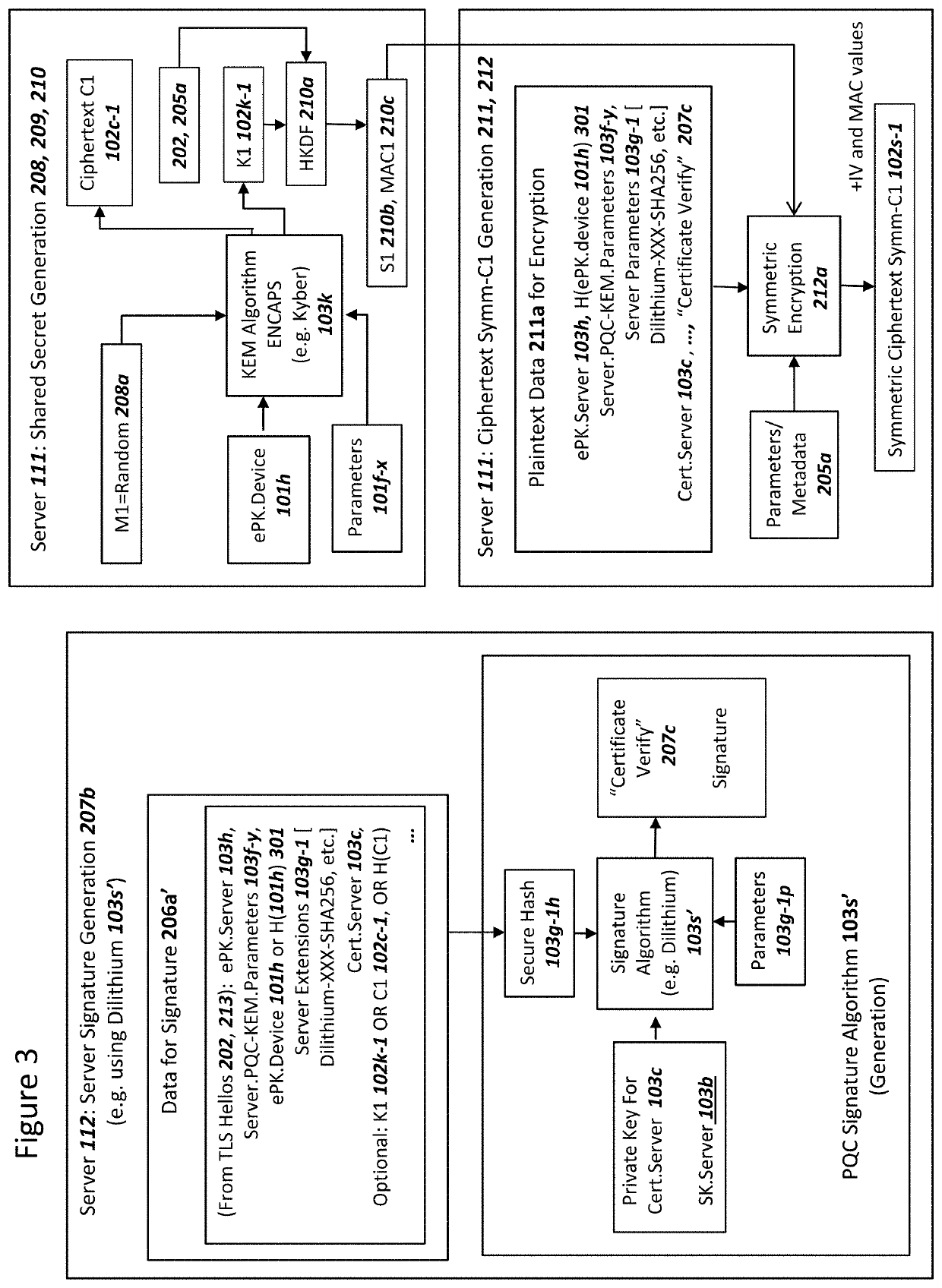
Secure Server Digital Signature Generation For Post-Quantum Cryptography Key Encapsulations
PendingUS20220209944A1Improve securityImprove security levelKey distribution for secure communicationPublic key for secure communicationKey (cryptography)Ciphertext
A network and a device can support a secure session with both (i) multiple post-quantum cryptography (PQC) key encapsulation mechanisms (KEM) and (ii) forward secrecy. The network can operate (i) a first server for conducting KEM with the device and (ii) a second server for generating a digital signature which can be verified by the device with a server certificate. The first server can receive a device ephemeral public key (ePK.device) and generate (i) a server ephemeral public key (ePK.server) and private key. The first server can send, to the second server, data comprising ciphertext for the ePK.device, ePK.server and the server certificate. The second server can (i) generate the digital signature over the data, and (ii) send the digital signature to the first server. The first server can conduct a KEM with ePK.device and the ciphertext in order to encrypt at least ePK.server and the digital signature.
Owner:NIX JOHN A
Safe and efficient one-round tripartite key exchange method under standard model
InactiveCN105119885AImprove efficiencyEnsure safetyKey distribution for secure communicationCommunications securitySecurity parameter
The present invention discloses a safe and efficient one-round tripartite key exchange method under a standard model. The method comprises a step 1 of setting a safety parameter of the multi-receiver secret key packaging input, generating a bilinear group, selecting an element from the bilinear group to generate a system parameter; a step 2 of selecting a private key of each receiver from a positive integer multiplication group according to the generated system parameter, and calculating a public key according to the selected private keys; a step 3 of each user generating a temporary public key pair and a private key pair according to the generated system parameter, and sending the temporary public key pair to other two users; a step 4 of each receiver using the own long-term and temporary private keys, and calculating a final session key according to the received temporary public key. A secret key generation algorithm of the present invention has the highest efficiency, for users, the communication security of a specific group can be guaranteed in a specific group environment, the external attack and the break of the communication activity of the specific group are prevented.
Owner:CHONGQING UNIV OF TECH
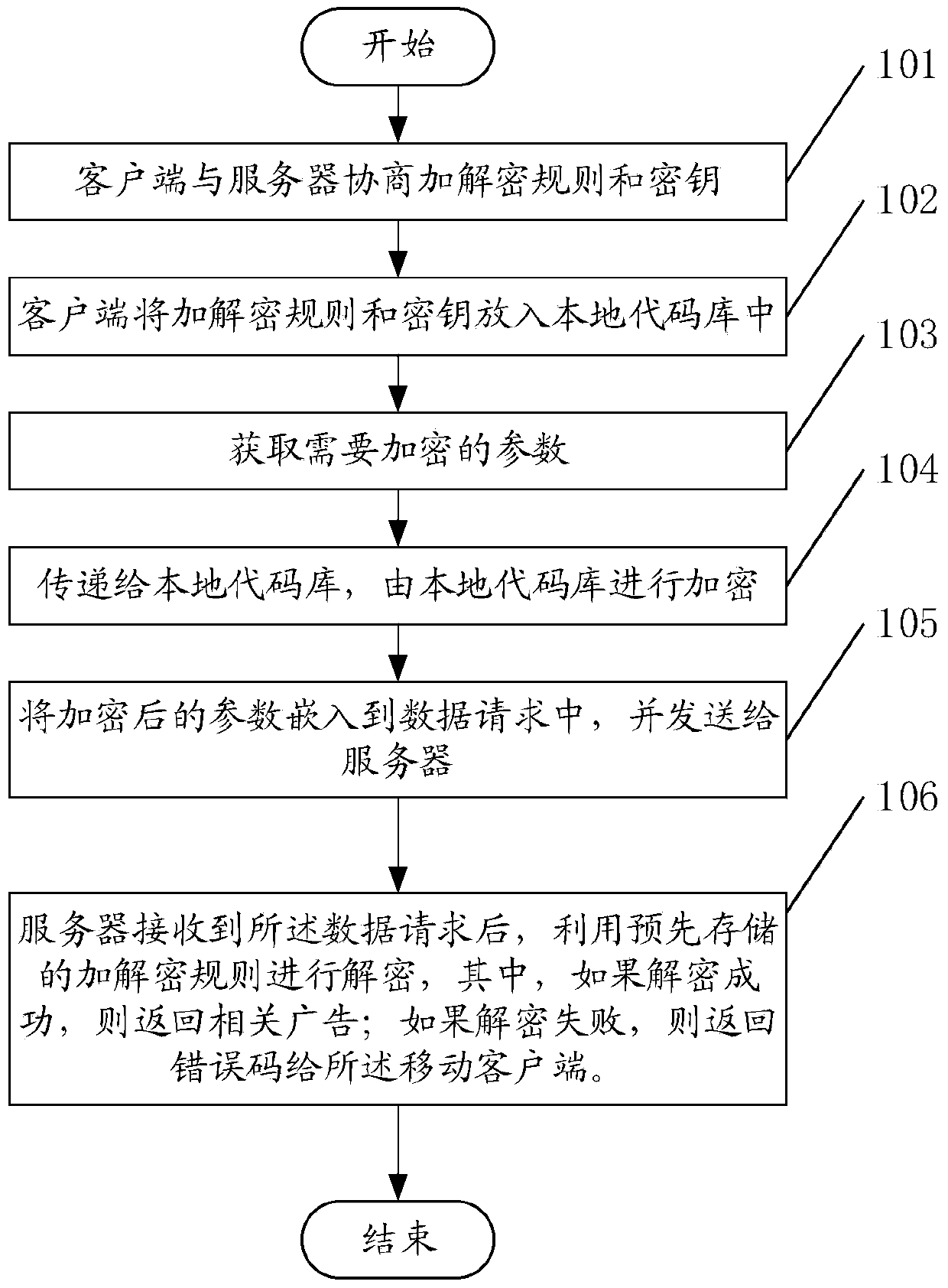
Mobile client advertisement invoking method and system
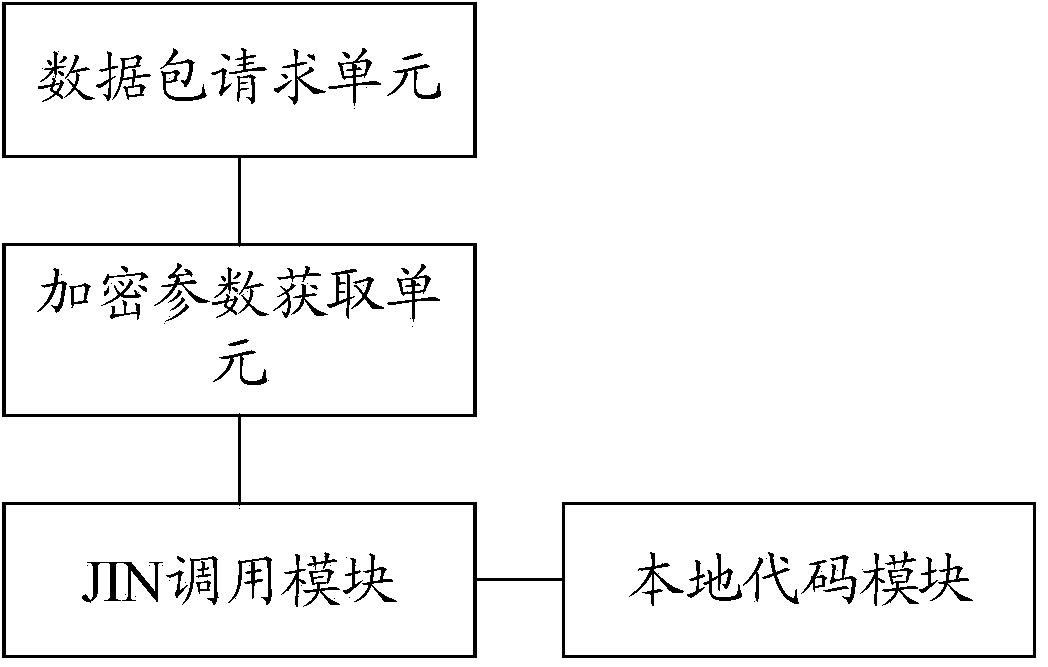
InactiveCN103746967AAvoid crackingImprove securityTransmissionSpecific program execution arrangementsComputer hardwareClient-side
The invention discloses a mobile client advertisement invoking method and system. The method comprises the following steps that: a mobile client issues a data request carrying an encryption parameter to a server terminal, wherein the encryption parameter is generated based on an encryption and decryption rule and a secret key that are packaged at a local code base by the mobile client and is a verification parameter for an advertisement request; and after the receiver receives the data request, the encryption and decryption rule that is stored in advance is used to carry out decryption; if the decryption is done successfully, a related advertisement is returned; and if the decryption fails, an error code is returned to the mobile client. Because the encryption and decryption rule and the secret key are packaged in the local data base that is difficult to be cracked, the security is improved; and the good technical effect is realized.
Owner:BEIJING ZHANGKUO TECH
Processor for realizing post quantum cryptography Saber algorithm
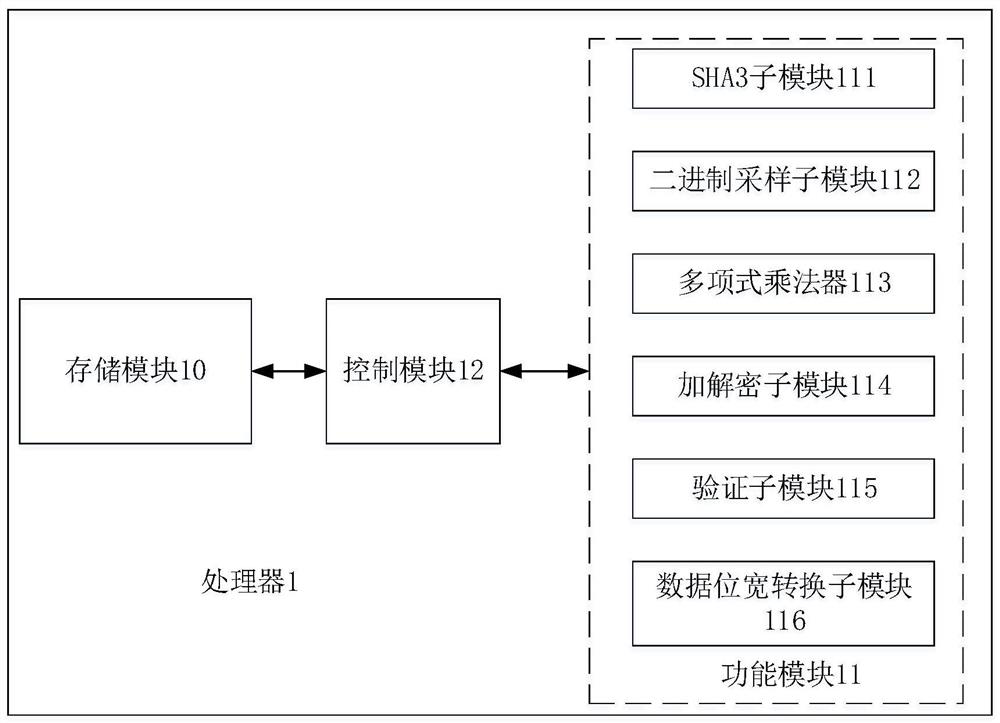
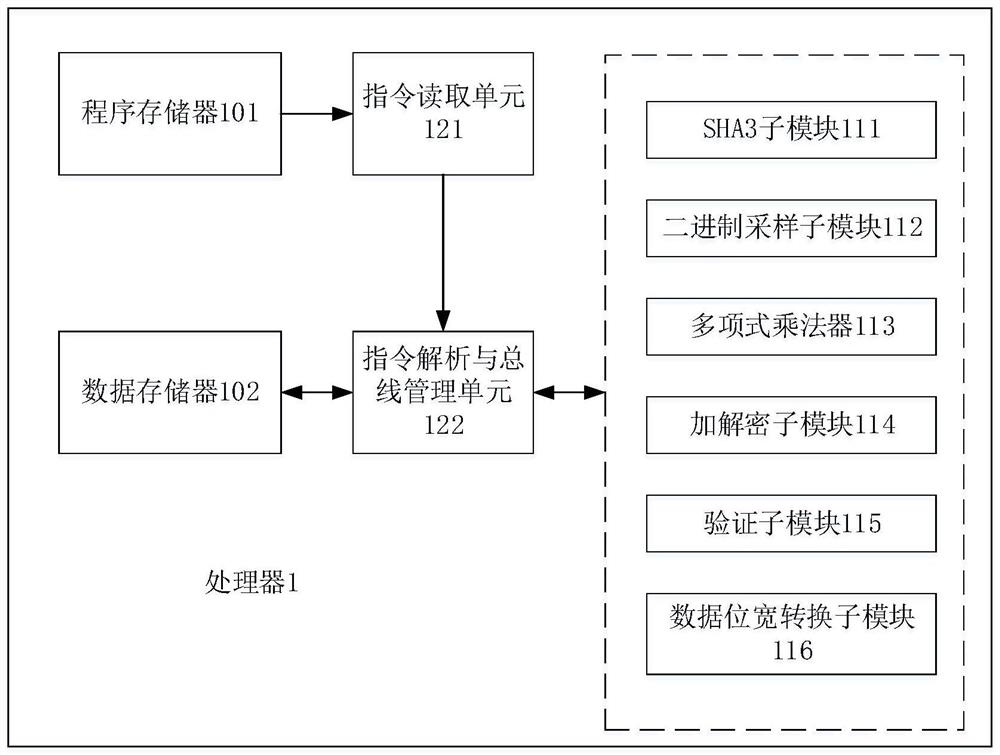
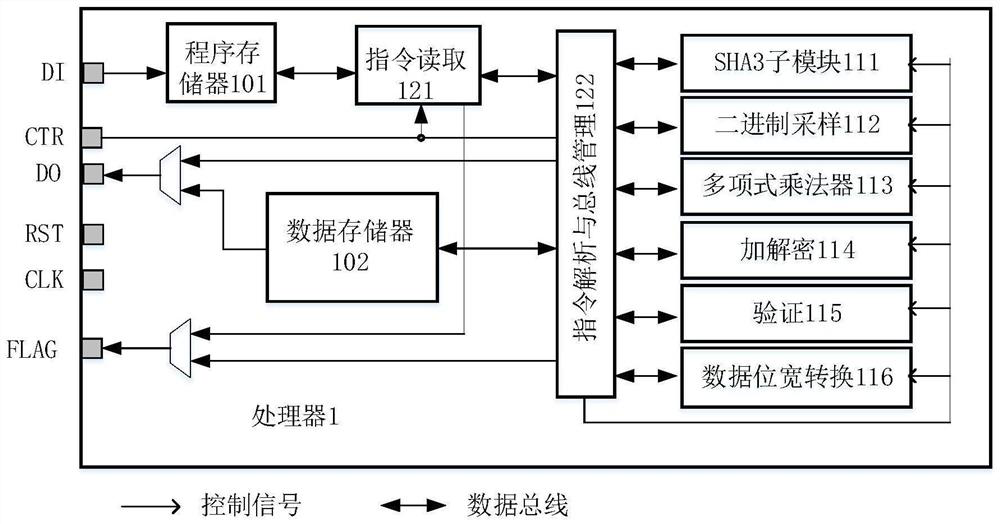
PendingCN114154640AReduce consumptionA large amountQuantum computersMachine execution arrangementsKey (cryptography)Algorithm
The embodiment of the invention relates to the technical field of information security, and discloses a processor for implementing a post quantum cryptography Saber algorithm, the processor is implemented by hardware and comprises a storage module for storing data and instructions, the processor uses a customized reduced instruction set, and the instructions stored in the storage module are instructions in an instruction set; the function module is used for executing operations related to the post quantum cryptography Saber algorithm, and the function module comprises the following sub-modules: a third generation secure hash algorithm SHA3 sub-module, a binary sampling sub-module, a polynomial multiplier, an encryption and decryption sub-module, a verification sub-module and a data bit width conversion sub-module; and the control module is used for controlling each sub-module in the functional module to execute corresponding operation according to the instruction stored in the storage module so as to realize at least one of key generation, key encapsulation and key de-encapsulation in the post quantum cryptography Saber algorithm. According to the embodiment of the invention, the resource overhead can be saved while high efficiency is realized.
Owner:HUAZHONG UNIV OF SCI & TECH
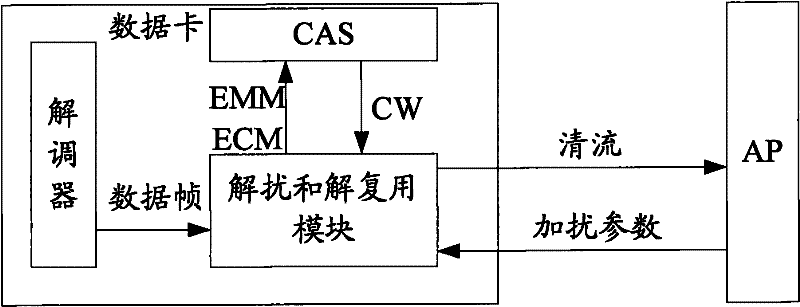
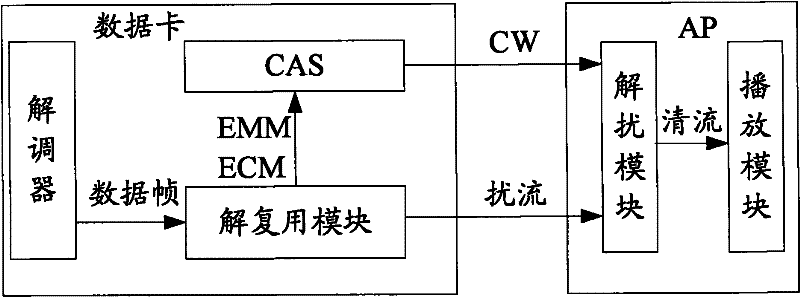
Data card, terminal device, information transmission method and system
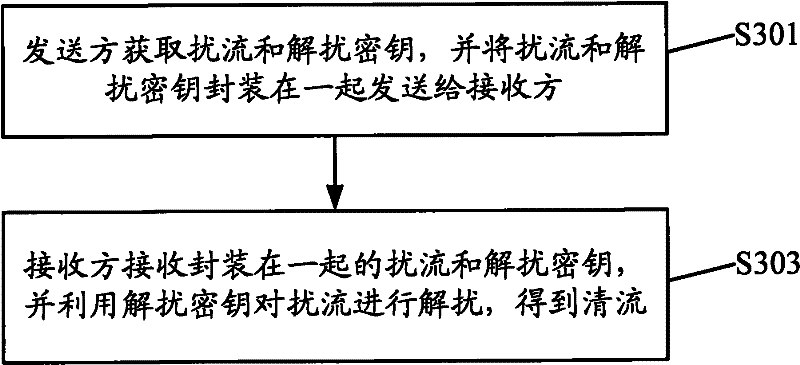
ActiveCN102281463AAvoid performance bottlenecksRealize synchronous transmissionSelective content distributionInformation transmissionEncapsulated data
The invention discloses a data card, a terminal device, and an information transmission method and system, wherein the method includes: a sender acquires a scrambling and descrambling key, and packages the scrambling and descrambling keys together and sends them to a receiver; The receiver receives the encapsulated scrambler and descrambling key, and uses the descrambling key to descramble the scrambled stream to obtain a clear stream. The present invention performs descrambling on the AP side, and at the same time calculates the descrambling key on the data card side, further repackages the scrambled flow and the corresponding descrambling key into a new data frame, and then sends it to the AP for The AP processes and plays, and can realize the synchronous transmission of the key and the code stream, thereby effectively solving the problem of partial descrambling failure in related technologies, and avoiding excessive occupation of processing resources of the data card, and solving the performance bottleneck of the data card.
Owner:ZTE CORP
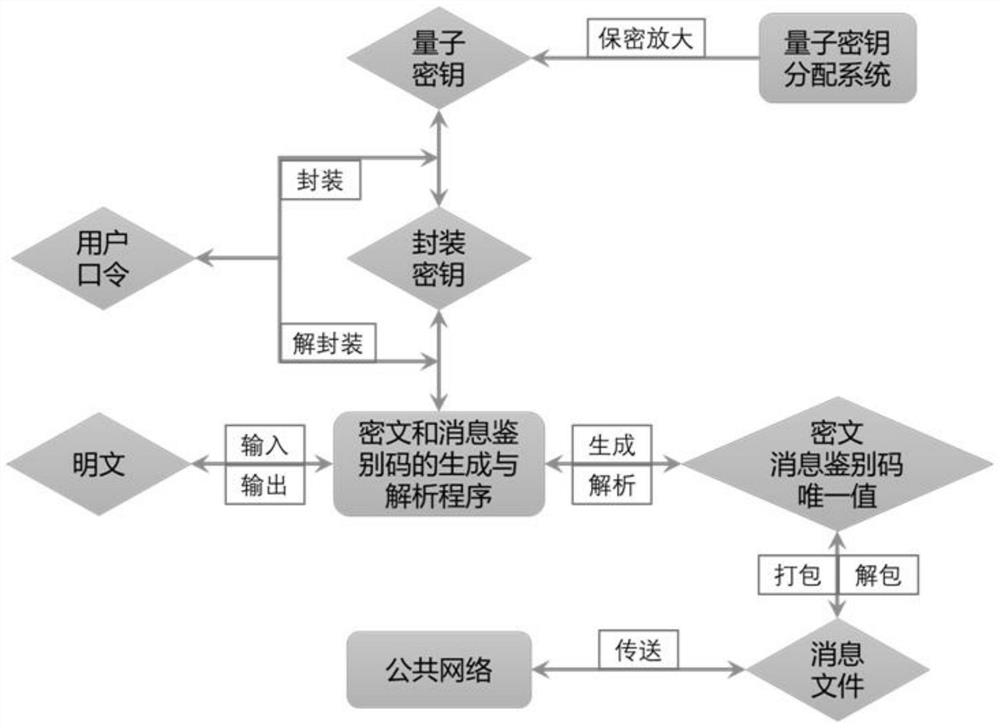
Strong authentication method and system based on quantum symmetric key
ActiveCN112311554AReduce the size of the operationImprove computing speedKey distribution for secure communicationUser identity/authority verificationPlaintextCiphertext
The invention belongs to the technical field of quantum key distribution, and particularly relates to a strong authentication method and system based on a quantum symmetric key, and the method comprises the steps: obtaining a quantum key file, and carrying out the secret amplification of the quantum key file according to a poly1305 algorithm; packaging the obtained quantum key by using a key packaging algorithm and a user password; the sender performing decapsulation to obtain a quantum key and a plaintext, obtaining a message authentication code, a ciphertext and a unique value through a poly1305 algorithm, and transmitting the message authentication code, the ciphertext and the unique value to the receiver through a public network after packaging; and the receiver receiving the packagedmessage, unpacking the packaged message to obtain a ciphertext, a unique value and a received message identification code, calling a quantum key and a poly1305 algorithm to calculate to obtain a plaintext and a calculated message identification code, and comparing whether the calculated message identification code is the same as the received message identification code to identify the integrity ofthe message. Message integrity of users of two communication parties can be powerfully guaranteed, leakage of sensitive information is effectively prevented, decoding of a quantum computer is resisted, and information safety is ensured.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
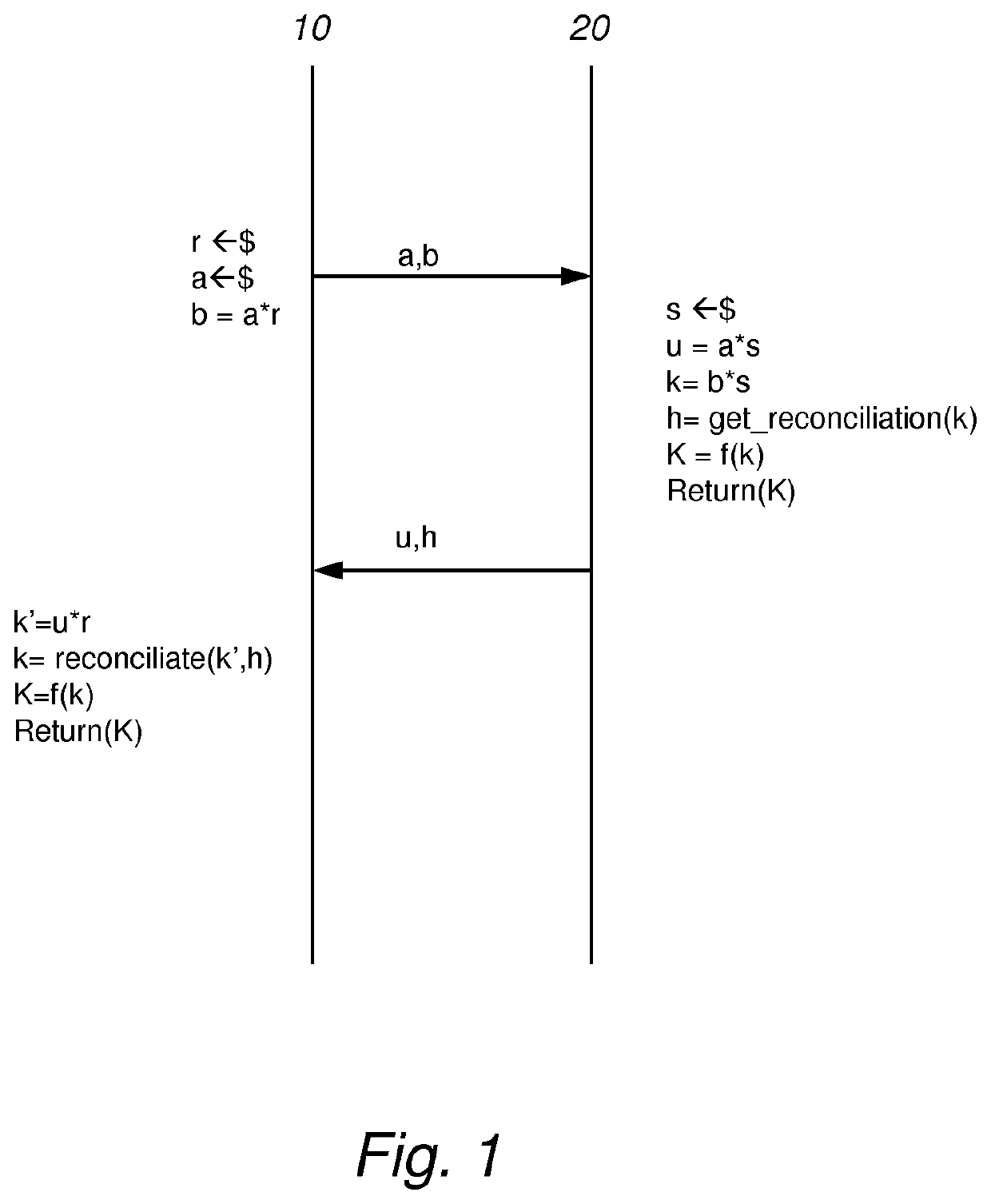
Authenticated lattice-based key agreement or key encapsulation
PendingCN114008967AAvoid attackIntensity is not affectedKey distribution for secure communicationComputational scienceEngineering
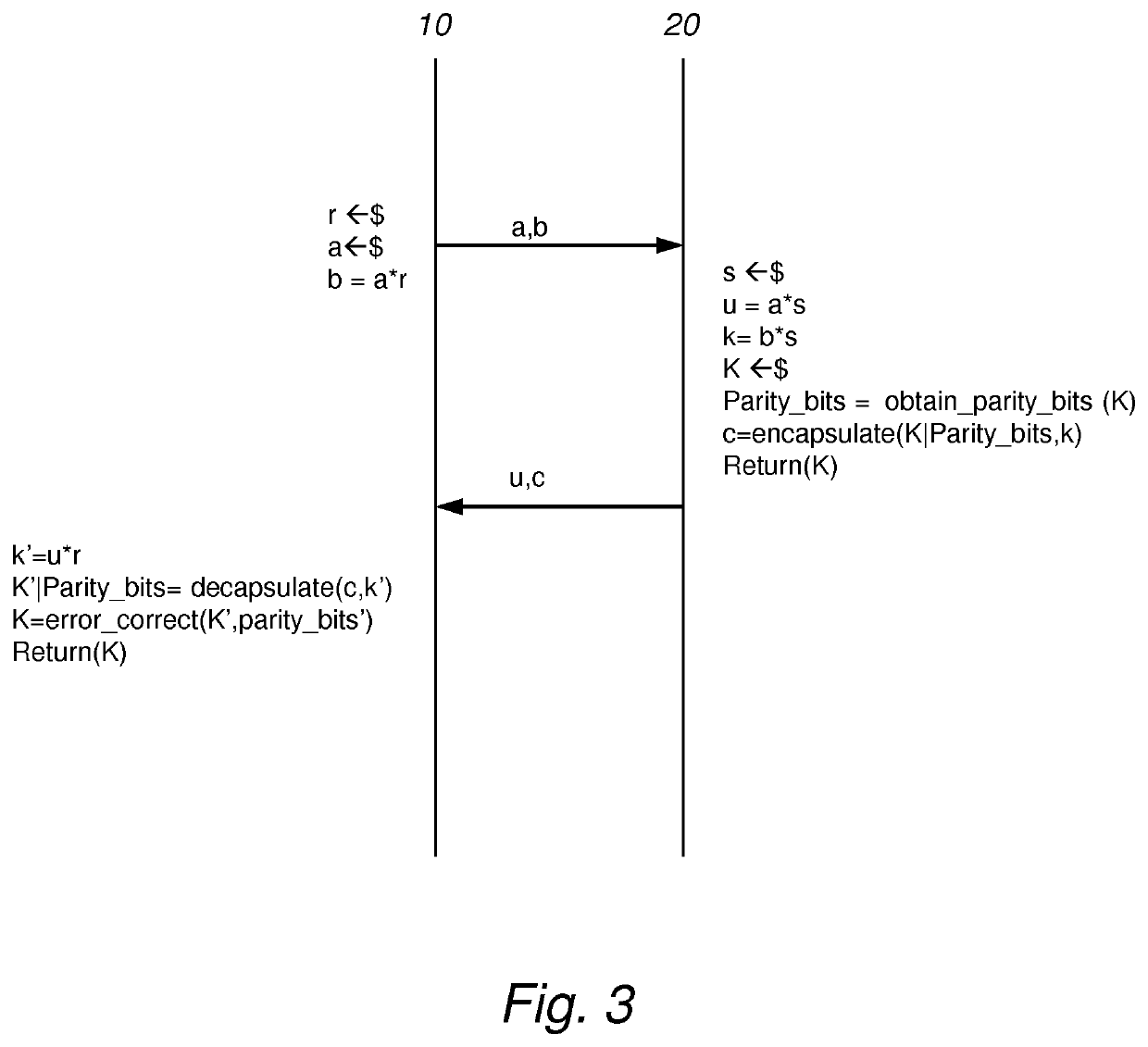
Some embodiments are directed to a system with a first cryptographic device (10) and second cryptographic device (20). The devices may compute a final seed from a preshared secret known to the devices, and on a pre-seed that exchanged between them. The final seed may be used to derive a common object (a).
Owner:KONINKLJIJKE PHILIPS NV
Universal blockchain key packaging technology
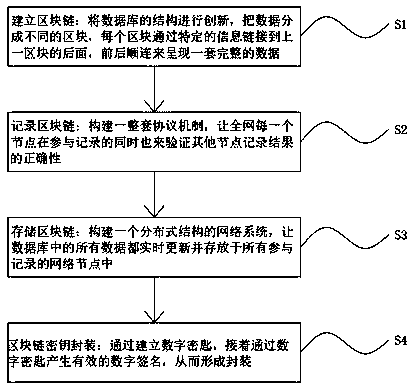
PendingCN111368333ABuild normalNormal storageDatabase distribution/replicationDigital data protectionDistributed structureNetworked system
The invention discloses a universal blockchain key packaging technology. The technology comprises the following steps: S1, establishing a blockchain; s2, recording a block chain; s3, storing the blockchain; s4, packaging a block chain key; block chain establishment, the establishment of a normal block chain is ensured; then, the data is recorded; each node in the whole network participates in recording and verifies the correctness of recording results of other nodes at the same time; constructing a network system with a distributed structure through a storage block chain; according to the method, all data in a database is updated in real time and stored in all network nodes participating in recording, and finally key encapsulation is performed on the data, so that encryption is performedthrough a key, encryption of a normal block chain and later information storage are ensured, and information tampering is prevented.
Owner:国金公用通链(海南)信息科技有限公司
H5 resource packet uploading method, H5 resource packet downloading method and related equipment
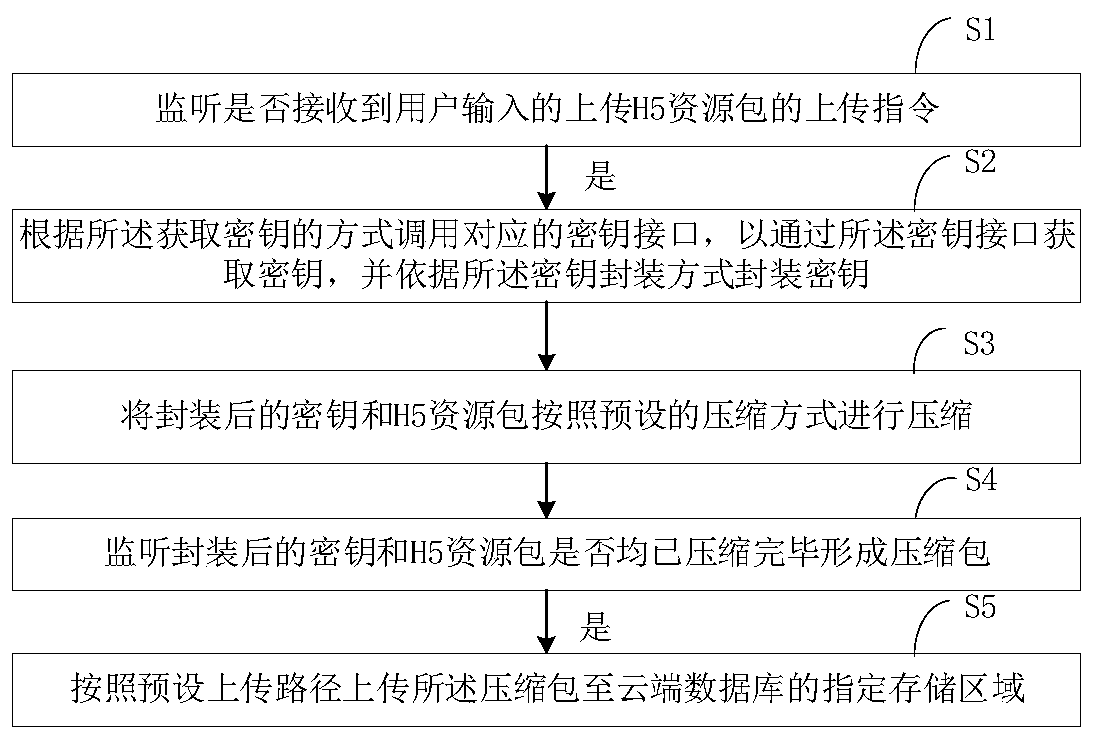
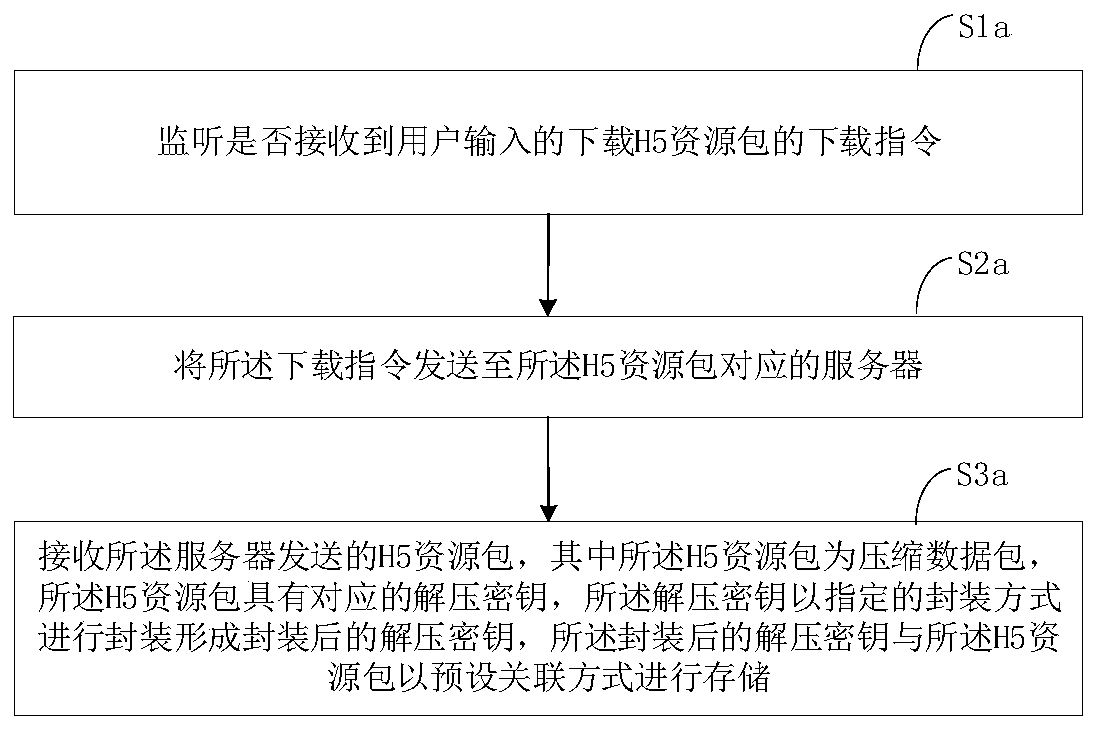
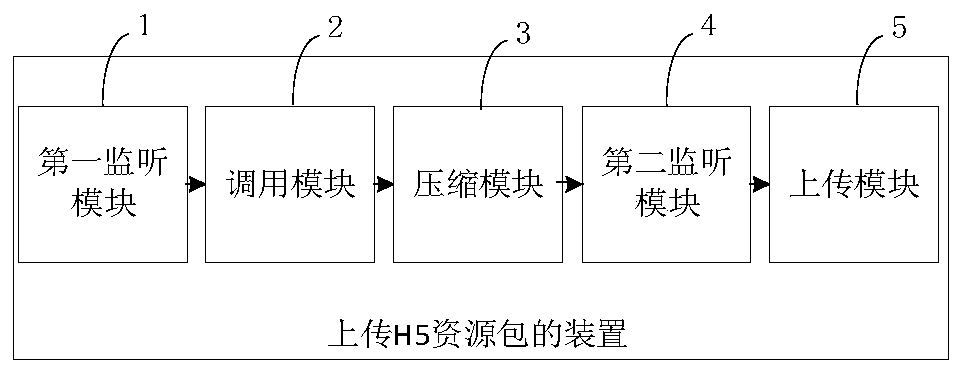
PendingCN110069904AImprove securityReduce the Risk of MisappropriationDigital data protectionProgram/content distribution protectionPathPingEngineering
The invention discloses an H5 resource packet uploading method, an H5 resource packet downloading method and related equipment. The H5 resource packet uploading method comprises the following steps: monitoring whether an uploading instruction for uploading an H5 resource packet input by a user is received or not; if yes, calling a corresponding secret key interface according to the secret key obtaining mode to obtain a secret key through the secret key interface, and packaging the secret key according to the secret key packaging mode; compressing the packaged secret key and the H5 resource package according to a preset compression mode to form a compressed package; and uploading the compressed packet to an appointed storage area of a cloud database according to a preset uploading path. Theserver encrypts the uploaded H5 resource packet and encapsulates the secret key, so that the security of the secret key is enhanced, and the risk that the H5 resource packet is stolen is reduced.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
Privacy-protected mobile communication authentication method
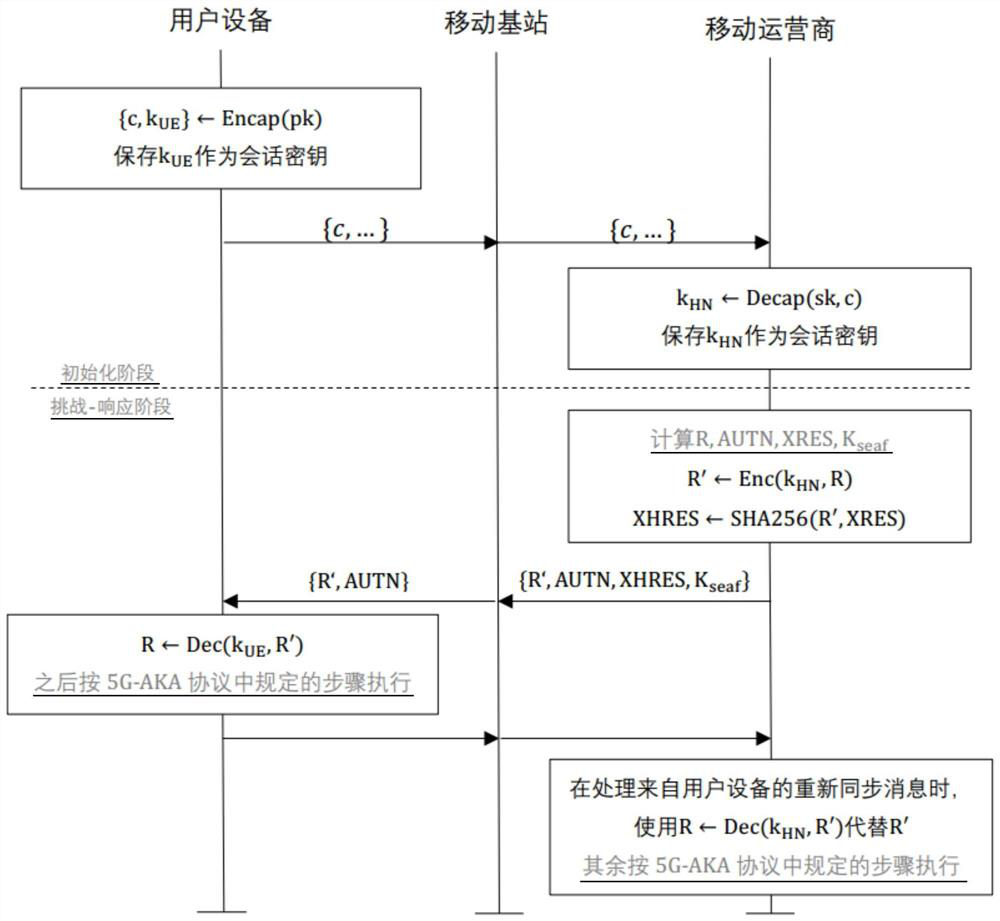
ActiveCN111669748APrivacy protectionLong-term privacy protectionSecurity arrangementPrivacy protectionEngineering
The invention provides a privacy-protected mobile communication authentication method, belongs to the field of communication technologies and information security technologies, and aims to enhance privacy protection in mobile communication authentication. In an initialization stage of a 5G-AKA protocol, user equipment and a mobile operator negotiate to generate a session key through a key encapsulation mechanism and store the session key; in a challenge-response stage of the 5G-AKA protocol, the mobile operator randomly selects a challenge value R, encrypts the challenge value R by adopting the session key, and generates an authentication vector according to the encrypted challenge value R'; after receiving the authentication vector, the user equipment decrypts the R' by adopting the session key to obtain a decrypted challenge value, and generates information corresponding to the execution state of an SIM card according to the decrypted challenge value; and the mobile operator selectsa corresponding processing mode according to the type of the information.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
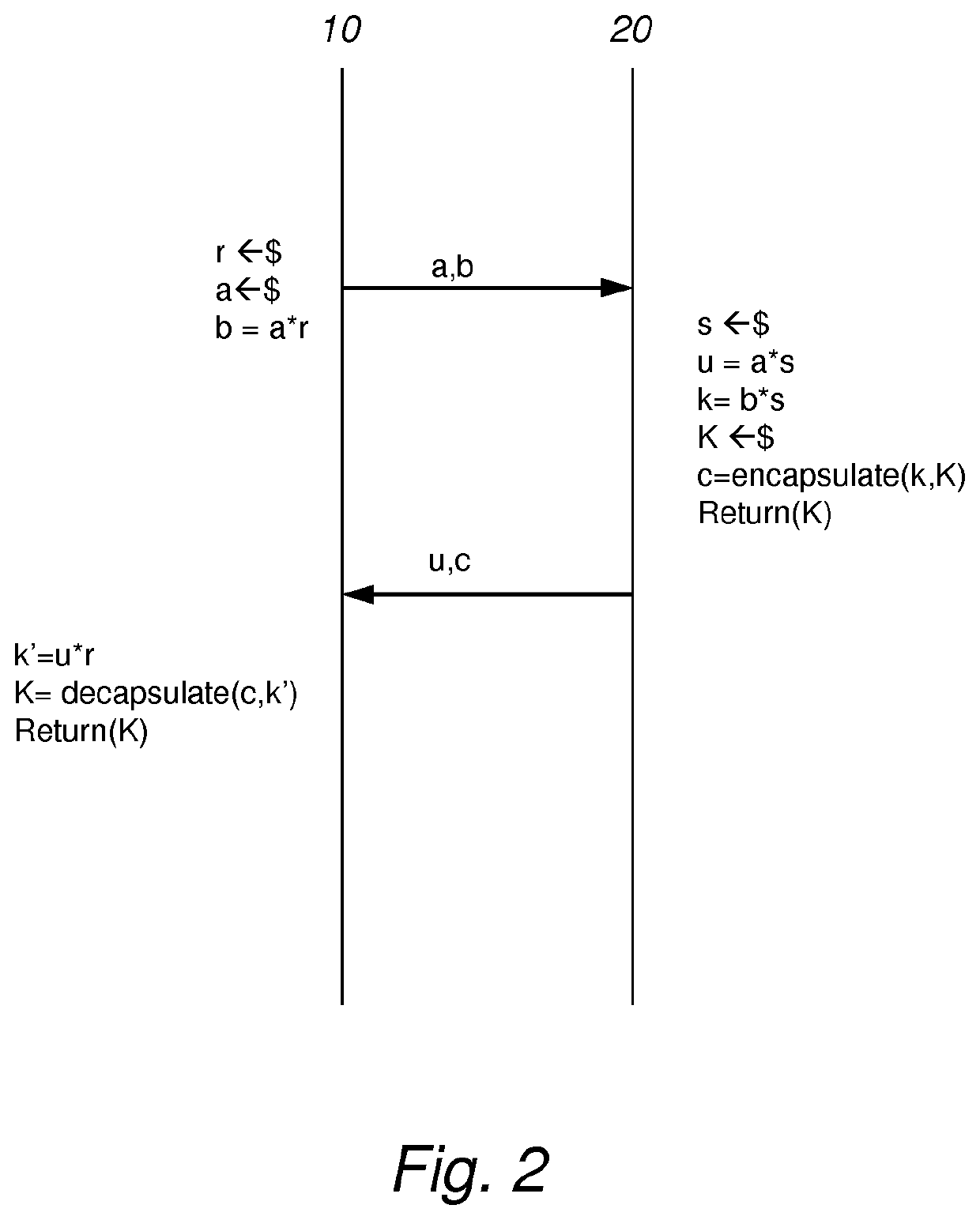
Key encapsulation protocols
ActiveUS20210266164A1Reduce failure rateReduce the possibilityKey distribution for secure communicationPublic key for secure communicationComputer hardwareComputer architecture
Some embodiments are directed to a cryptographic device (20). A reliable bit function may be applied to a raw shared key (k*) to obtain reliable indices, indicating coefficients of a raw shared key, and reliable bits derived from the indicated coefficients. Reconciliation data (h) may be generated for the indicated coefficients of the raw shared key. A code word may be encapsulated using the reliable bits by applying an encapsulation function, obtaining encapsulated data (c) which may be transferred.
Owner:KONINKLJIJKE PHILIPS NV
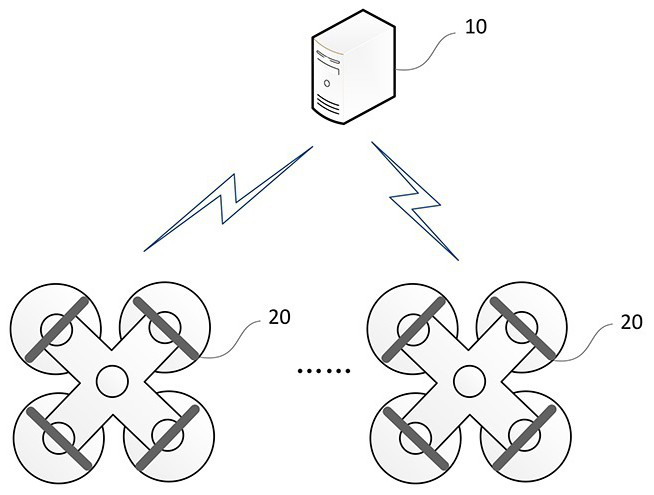
Data security transmission method and system for embedded AI chip on edge side of unmanned aerial vehicle
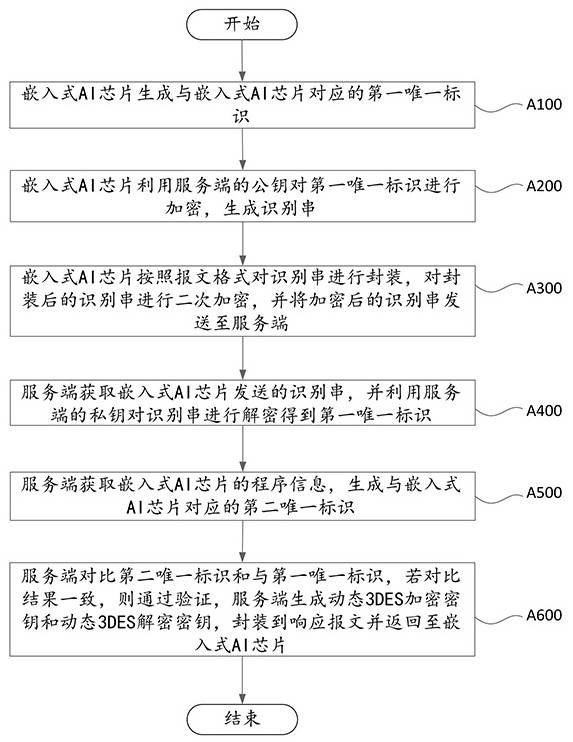
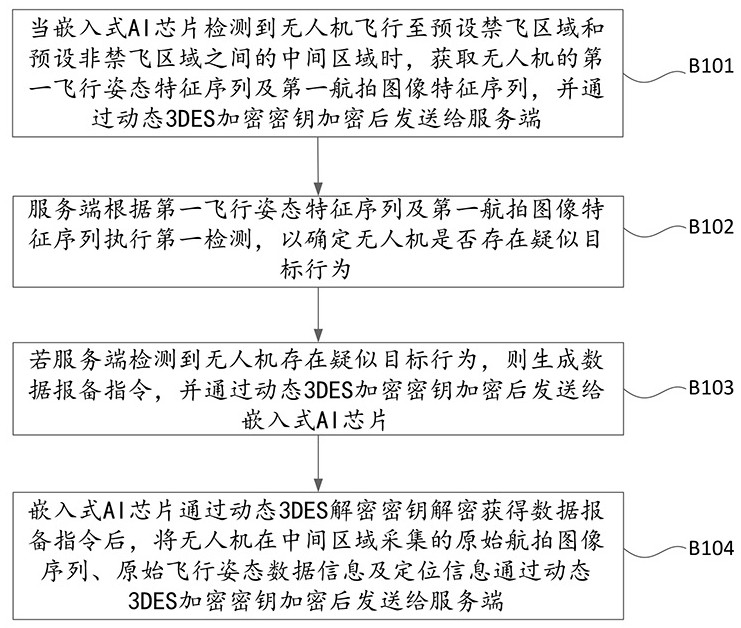
ActiveCN113469139AImprove data exchange securityEnsure safetyCharacter and pattern recognitionDigital data protectionUncrewed vehicleUnique identifier
The invention provides a data security transmission method and system for the embedded AI chip on the edge side of the unmanned aerial vehicle. The first unique identifier corresponding to the embedded AI chip is generated through the embedded AI chip, the first unique identifier is encrypted to generate the identification string, and the encrypted identification string is sent to the server. And the server side obtains the program information of the embedded AI chip, generates a second unique identifier corresponding to the embedded AI chip, and compares the second unique identifier with the first unique identifier, if the comparison result is consistent, verification is passed, and the server side generates a dynamic 3DES encryption key and a dynamic 3DES decryption key, packages the dynamic 3DES encryption key and the dynamic 3DES decryption key into a response message and returns the response message to the embedded AI chip. Therefore, the embedded AI chip can subsequently encrypt or decrypt the data interacted with the server side by using the dynamic 3DES encryption key and the dynamic 3DES decryption key, so that the data interaction security between the unmanned aerial vehicle and the server side is improved.
Owner:广州中科智云科技有限公司
Block chain authorization calculation control method
The invention provides a block chain authorization calculation control method. According to the block chain authorization calculation control method, on an original energy chain open permission chain node, an encrypted byte stream packaged by using a key expanded by an instruction set is obtained; the surrounded container sends the encrypted byte stream packaged by using the key expanded by the instruction set to an untrusted environment, and writes encrypted data into a disk; the key is packaged in a way that a specific central processing unit (CPU) comprises a root key and a root SealKey which are stored in a storage circuit, a remote authentication process is supported to be started, and the root key is only supported by a platform.
Owner:上海零数众合信息科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com