Authenticated lattice-based key agreement or key encapsulation
A technology of lattice and key, applied in key distribution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0070] While the presently disclosed subject matter is capable of embodiments in many different forms, one or more specific embodiments are shown in the drawings and will be described in detail herein, it being understood that this disclosure is to be considered as a principle of the disclosed subject matter and are not intended to be limited to the specific embodiments shown and described.
[0071] Hereinafter, elements of the embodiments are described in operation for the sake of understanding. However, it is apparent that the various elements are arranged to perform the functions described as being performed by them.
[0072] Furthermore, the presently disclosed subject matter is not limited to the embodiments, since features described herein or recited in mutually different dependent claims may be combined.
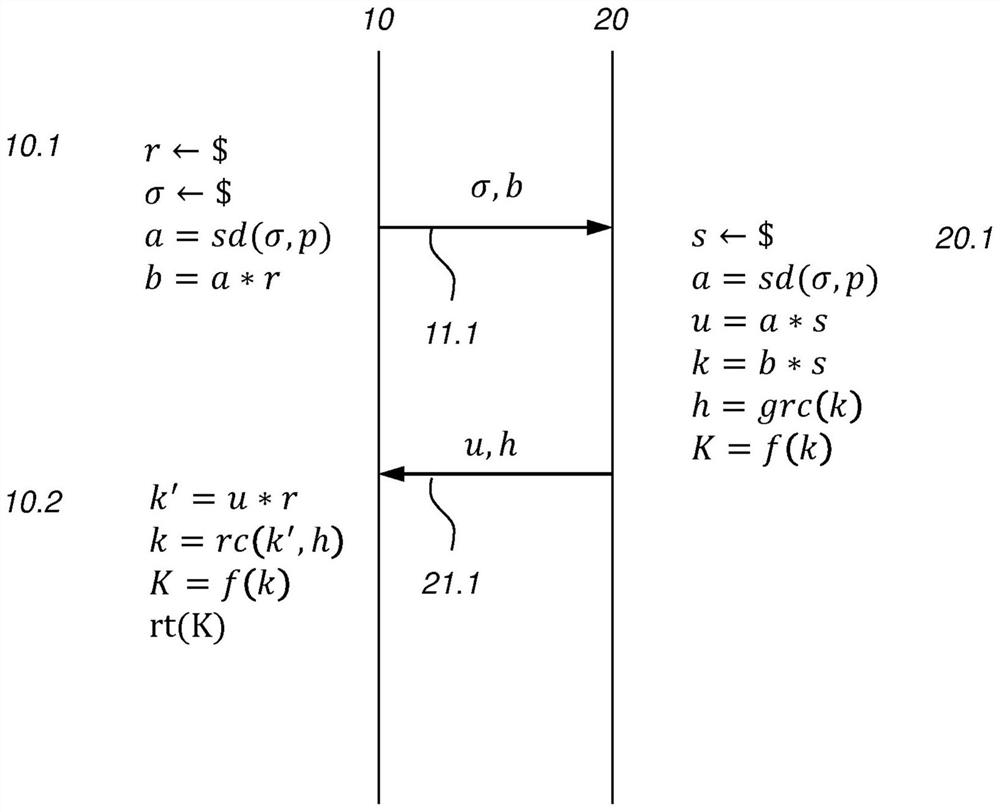
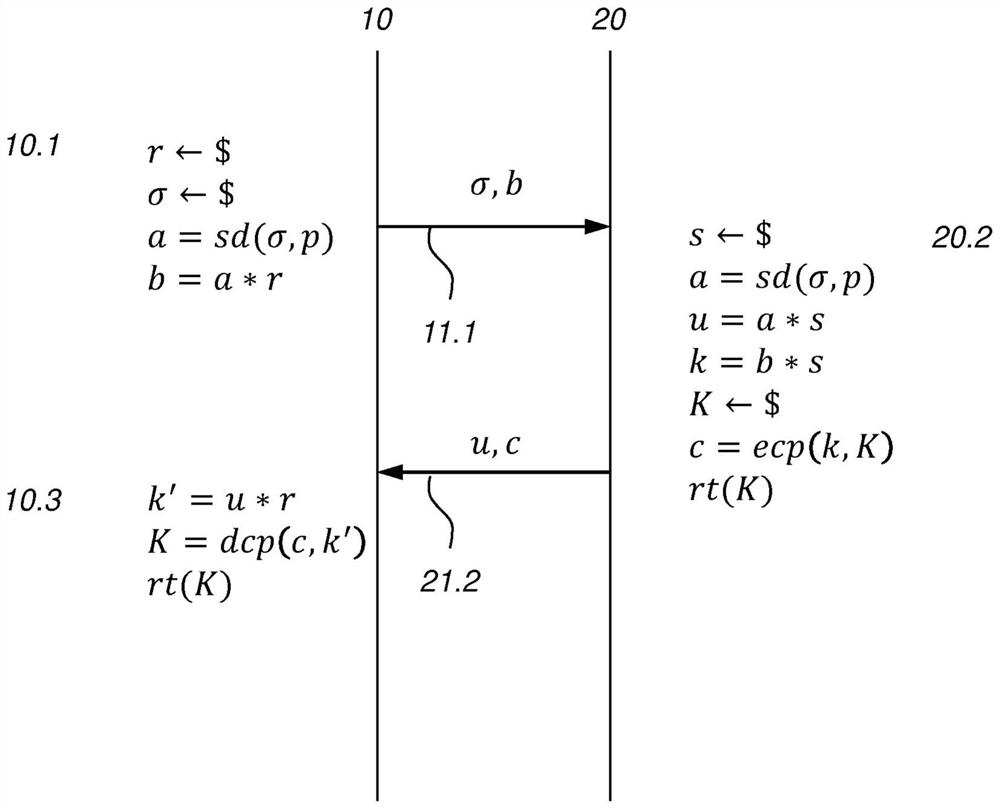
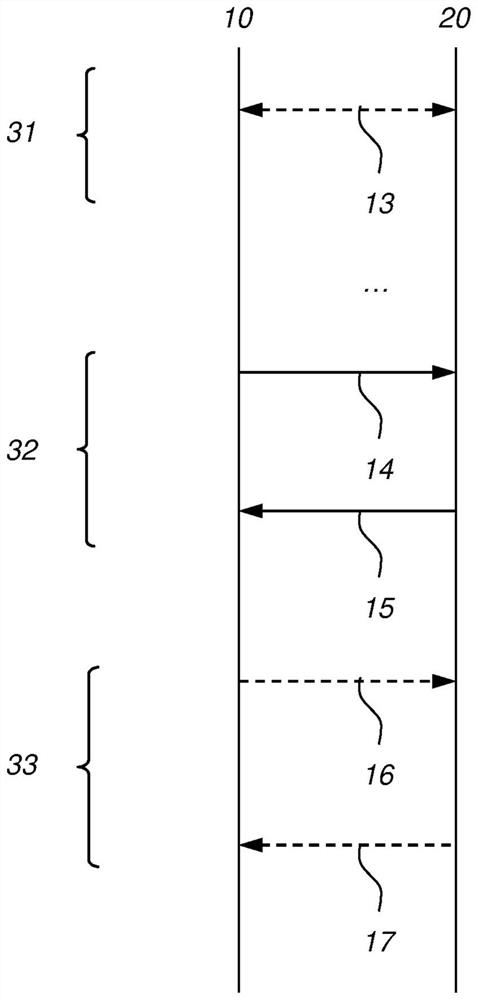
[0073] Various embodiments are disclosed below. exist Figure 1-3 In, various protocols for which the first cryptographic device 10 and the second cryptographic de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com