Authentication key exchange method based on message recovery signature
A technology for authenticating keys and messages, applied in the field of cryptography, can solve the problems of large communication volume, inability to achieve perfect forward security, weak forward security, etc., achieve high security, save communication overhead, and reduce communication traffic Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
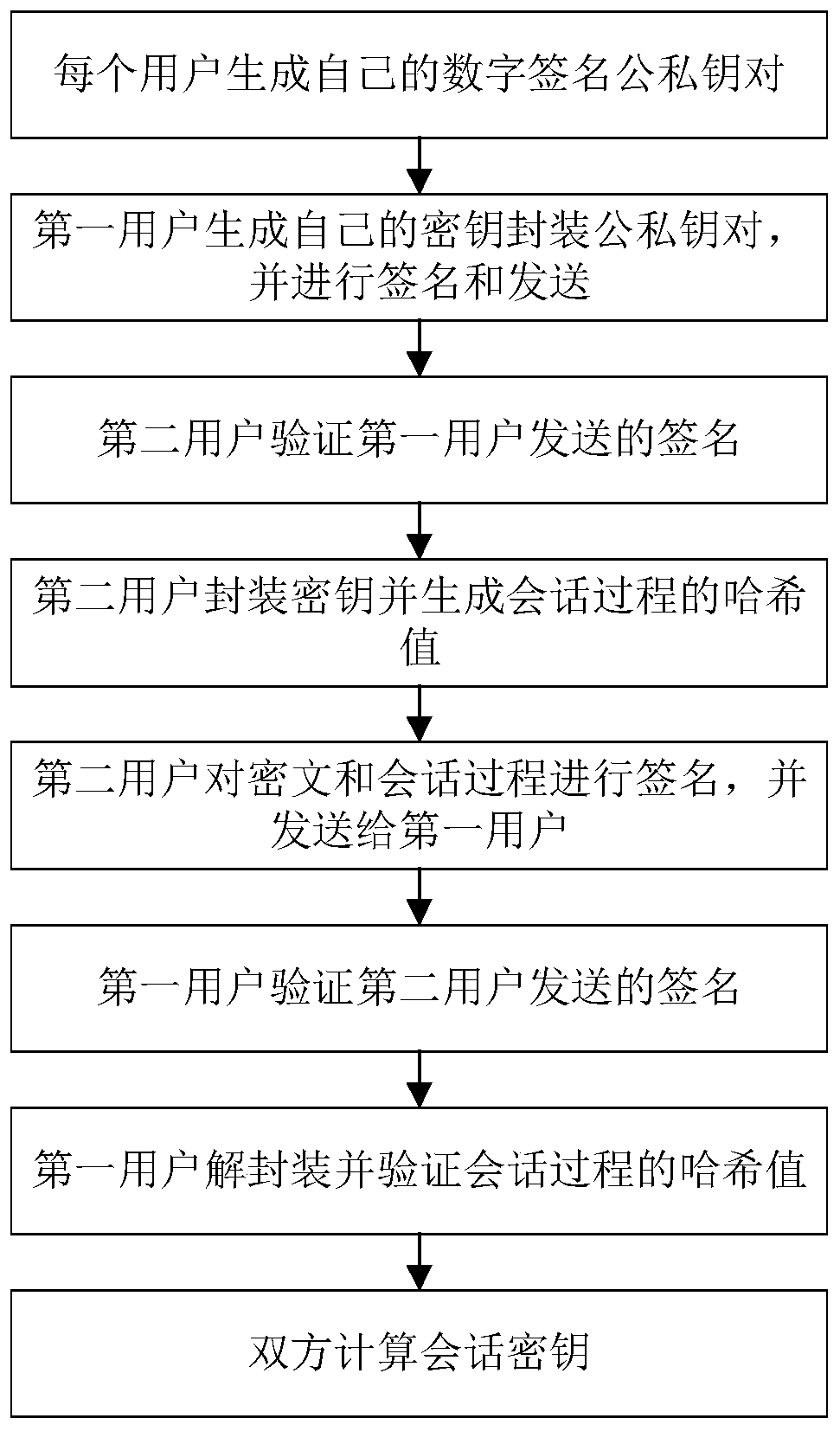
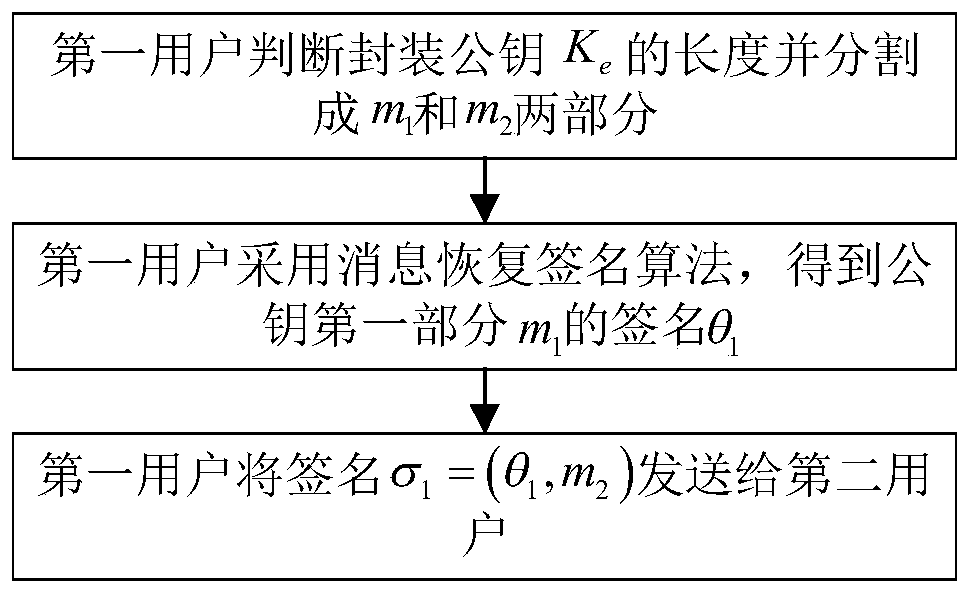
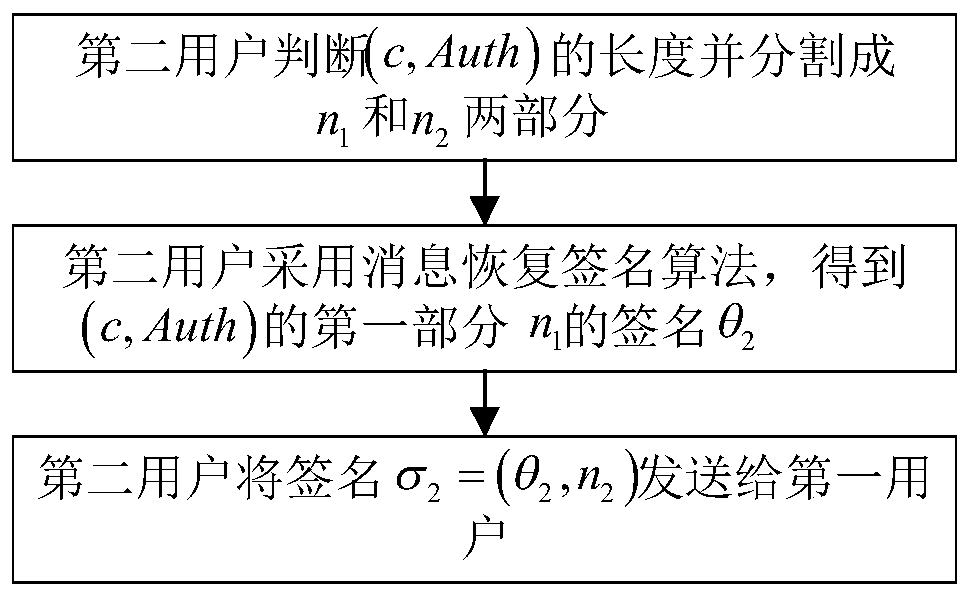
[0035] refer to figure 1 , the implementation steps of the present invention include as follows:
[0036] Step 1. Each user generates their own digital signature public-private key pair.
[0037] 1.1) The first user generates his own signature public-private key pair
[0038] (1.1a) The first user uses a signature key generation algorithm to generate a digital signature public-private key pair. The parameters of the signature key generation algorithm are: (N, Q), where N is a power of 2, Q is a prime number and Q≡1mod2N , take N=512, Q=12289 here;
[0039] (1.1b) Calculate the standard deviation
[0040] (1.1c) according to the discrete Gaussian distribution Sample a 2N-dimensional vector, where each component has a mean of 0 and a standard deviation of σ f The one-dimensional discrete Gaussian distribution of , then the 2N...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com