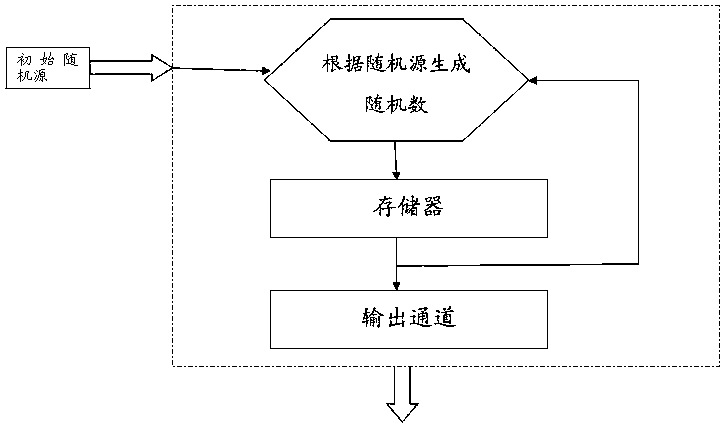
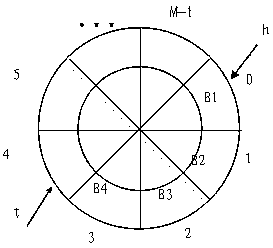
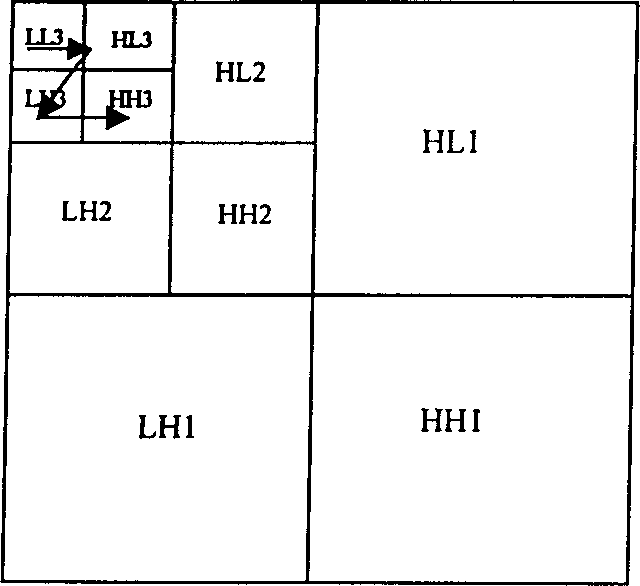
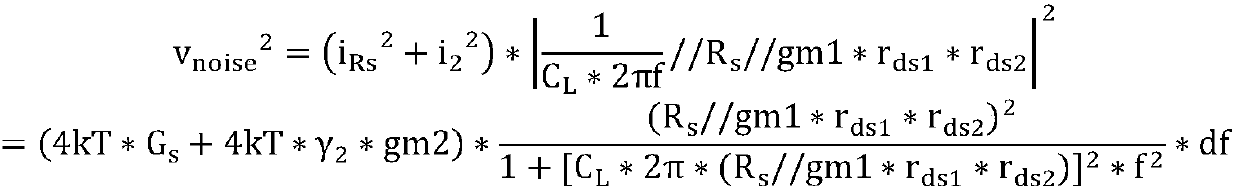Patents
Literature
31 results about "Random series" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
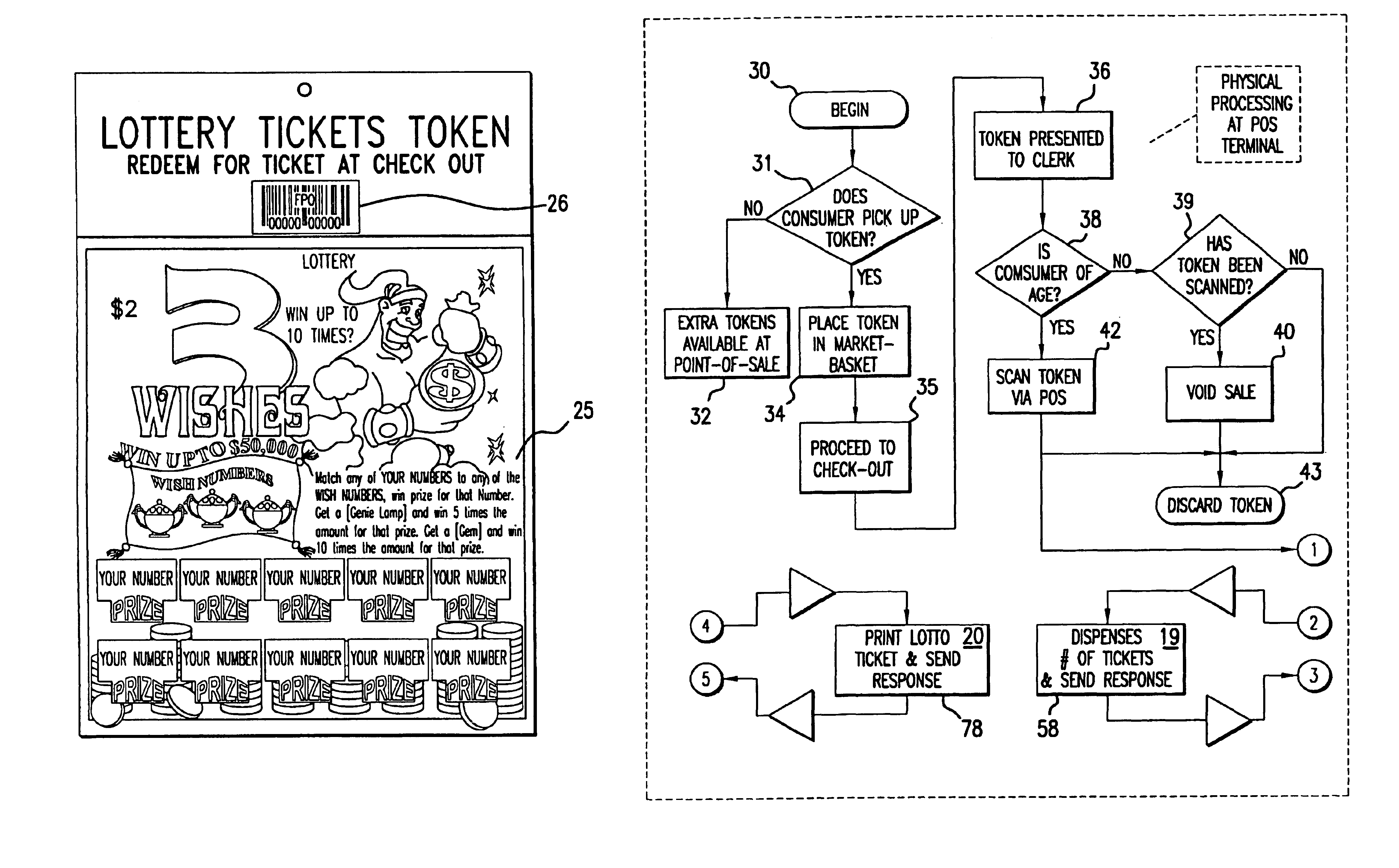
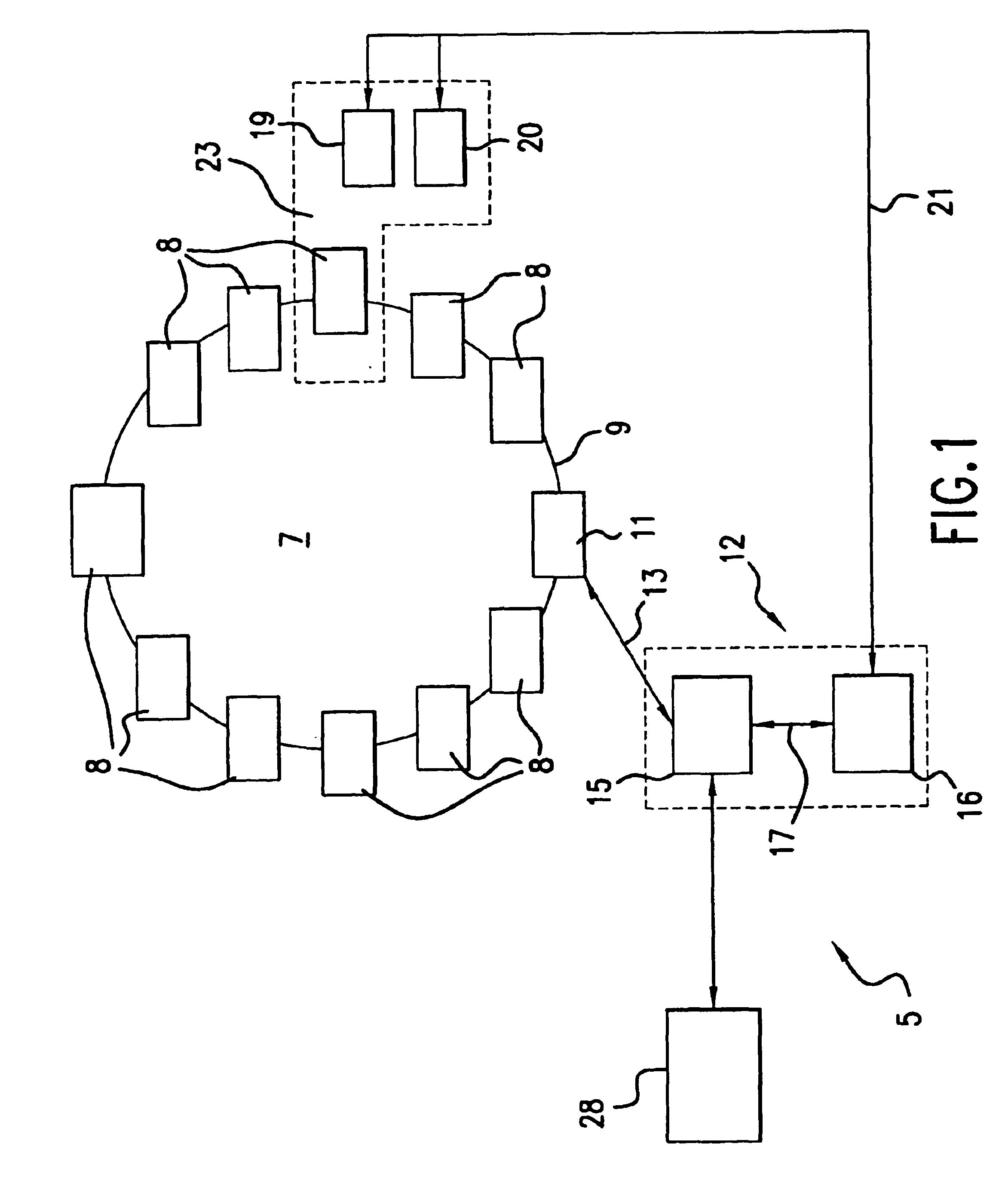
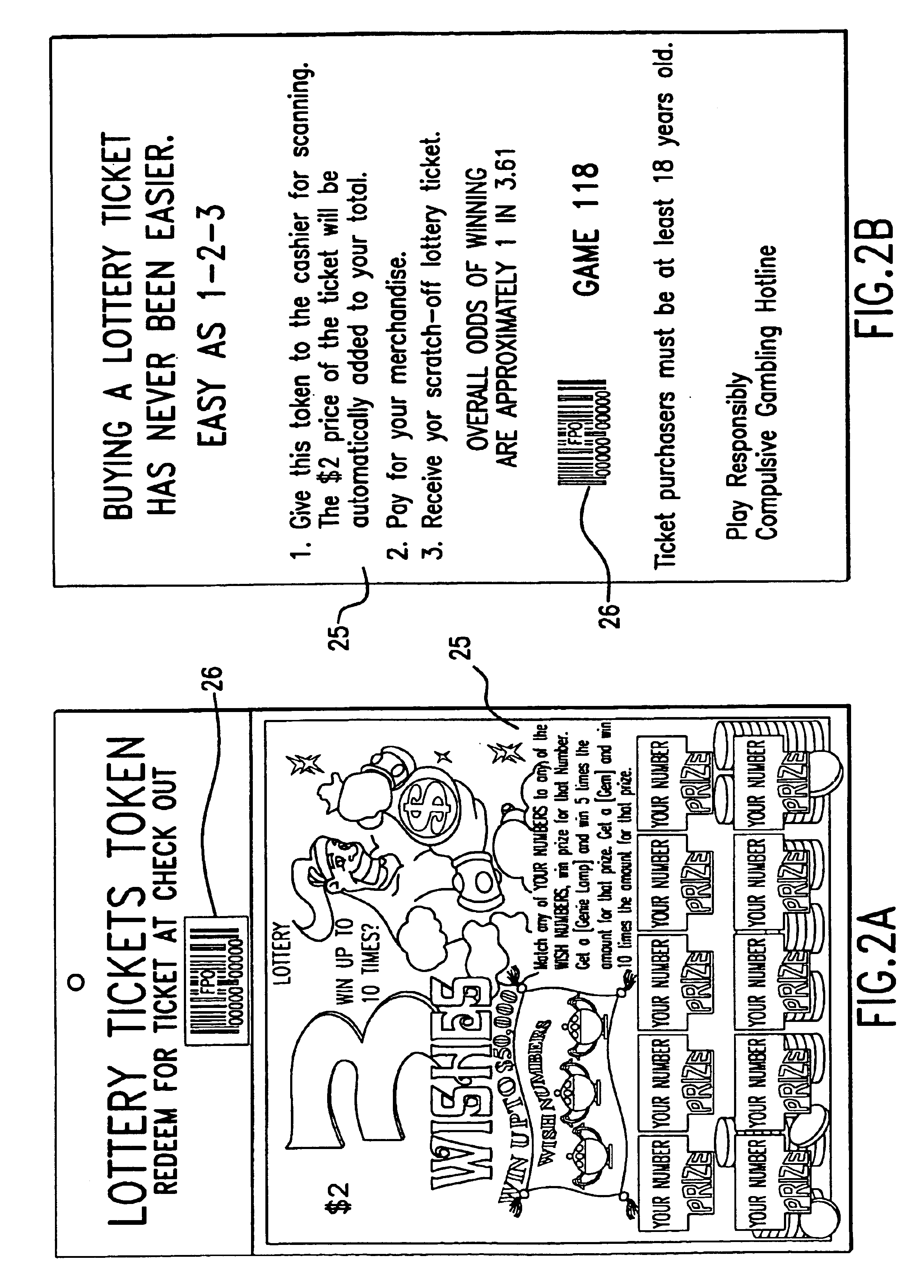
System and method for selling lottery game tickets
InactiveUS6899621B2Simple methodBoard gamesApparatus for meter-controlled dispensingComputer scienceRandom series
A system and method of selling pre-printed lottery game tickets, on-line lottery game tickets, or a combination of pre-printed and on-line lottery game tickets in a retail store is disclosed. At least one lottery game token is provided bearing a game identification code thereon for being scanned at a POS terminal provided as a part of an in-store POS network. The scanned identification code is detected by a POS monitor in communication with the POS terminal, the POS monitor determining from the scanned code the type of lottery game to be played. The POS monitor, or a separate ticket controller in communication with the POS monitor, will then issue a dispense ticket command to a ticket dispenser located at the POS terminal for each pre-printed lottery game to be played. For each on-line lottery game to be played, the detection of the game identification code will result in the generation of a random series of lottery play numbers, whereupon the POS monitor or the ticket controller will instruct a lottery ticket printer located at the POS terminal to print at least one lottery ticket thereat bearing the lottery play numbers thereon.
Owner:SCI GAMES LLC
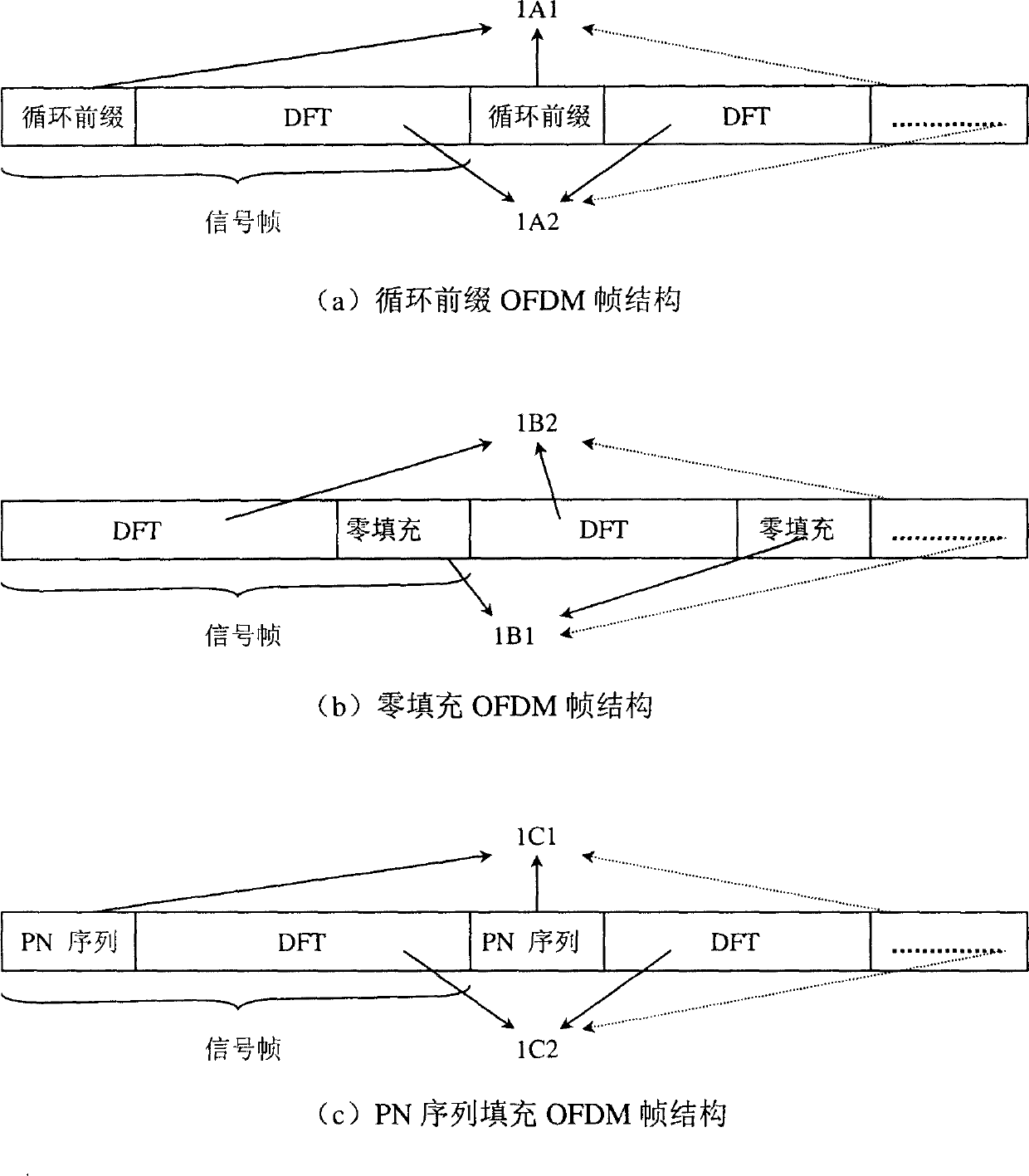
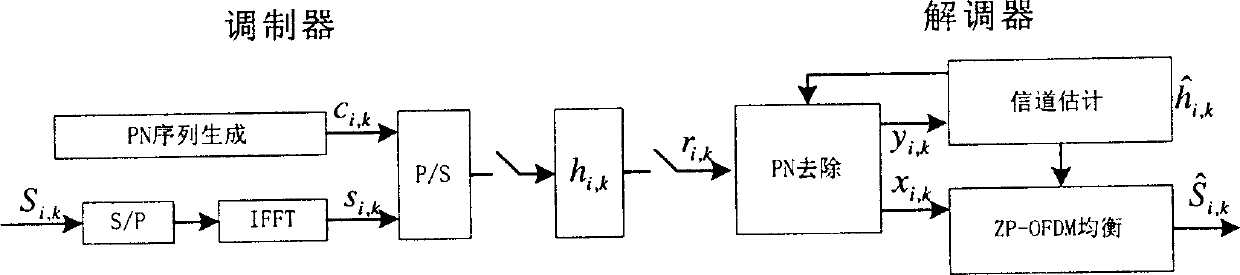
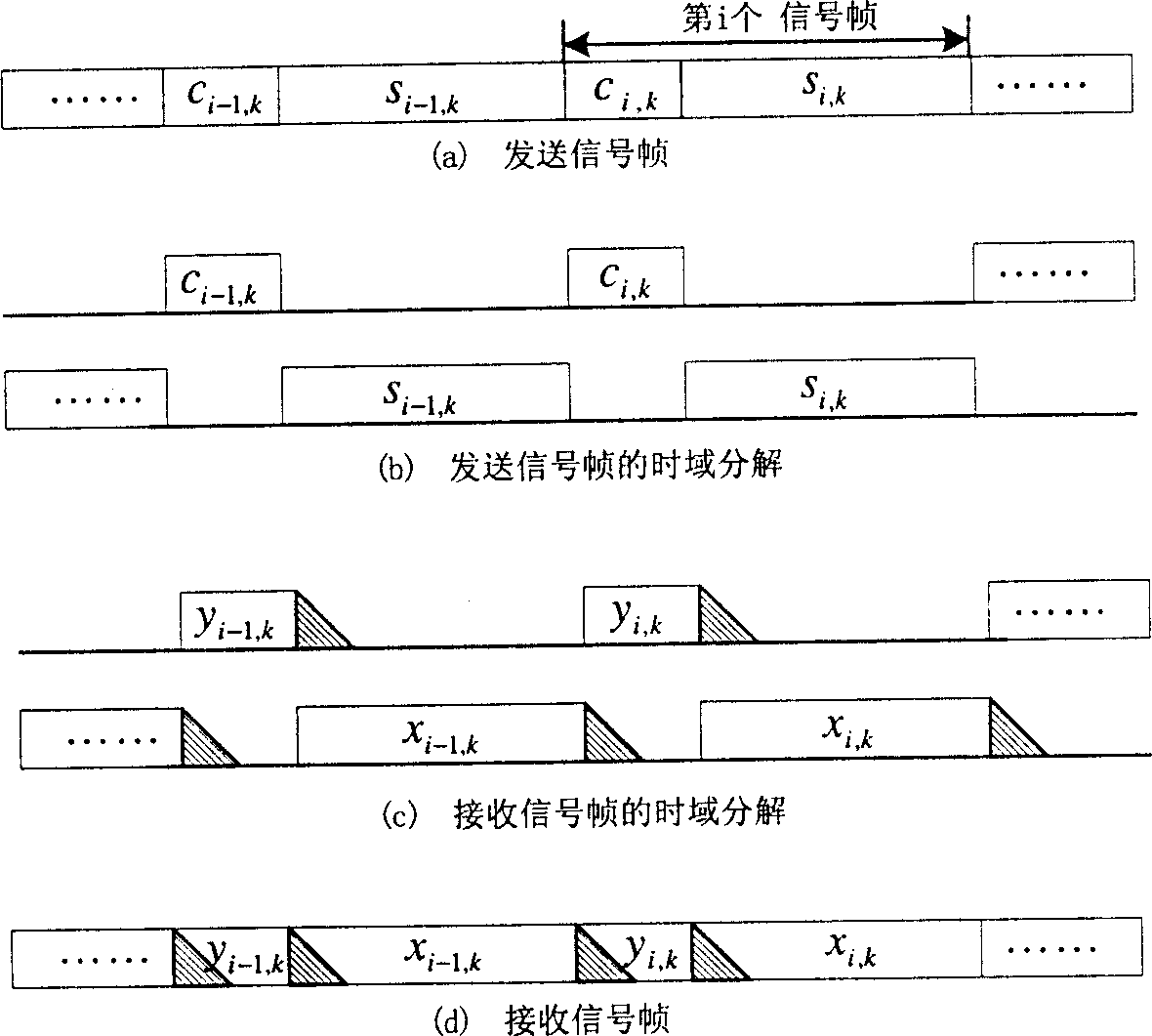
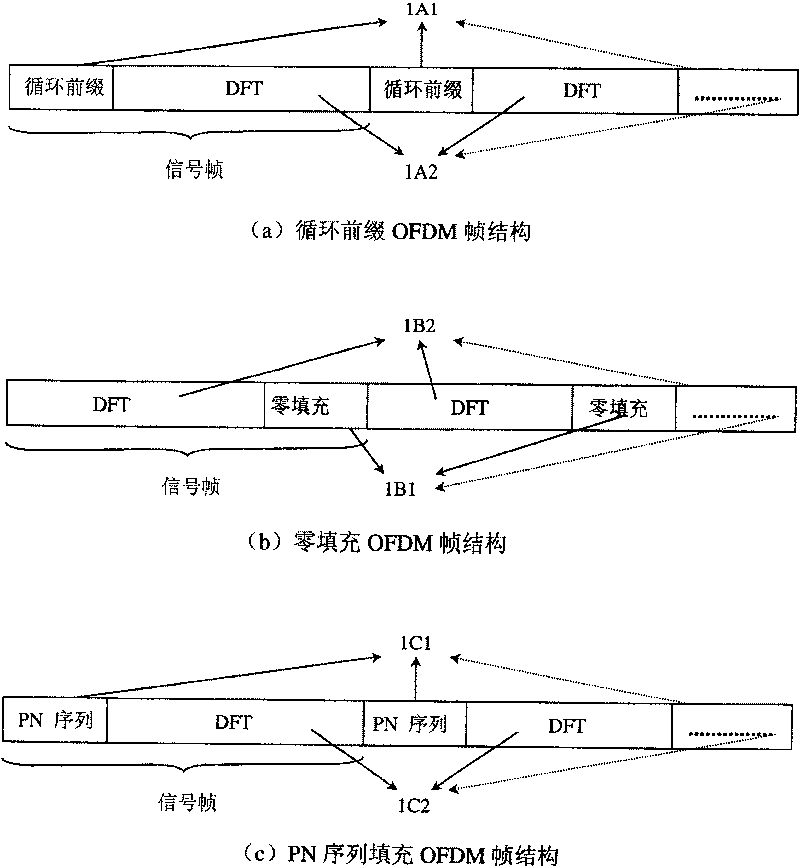
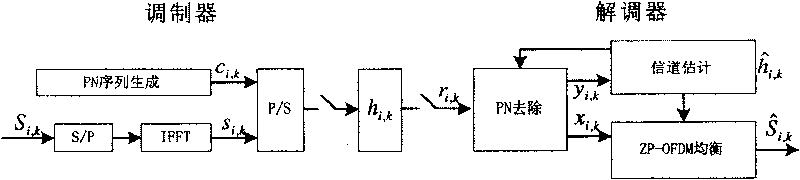
Method for eliminating interaction of pseudo-random series fill in OFDM modulation system
The invention is an iterative echo elimination method. The method includes steps: based on known pulse response of channel (PRCH) at previous two frames, using linear interpolation obtains PRCH at current and next frames; after synchronization of receiver, obtaining pseudo random sequence of current frame and next frame as well as result of convolution between the said pseudo random sequence and corresponding PRCH; removing the said convolution from signal in Ith frame, the receiver obtains convolution between data in Ith frame equivalent to zero filled system and PRCH; using method of time-domain filtering and decision directed feedback removes items of interference and noise between residue codes, and updates estimated value of channel in each frame till presetting iterations. Computer simulation indicates that raising efficiency of spectrum greatly without losing performance of error code. The invention is still valid if single frequency network with large time delay.
Owner:TSINGHUA UNIV
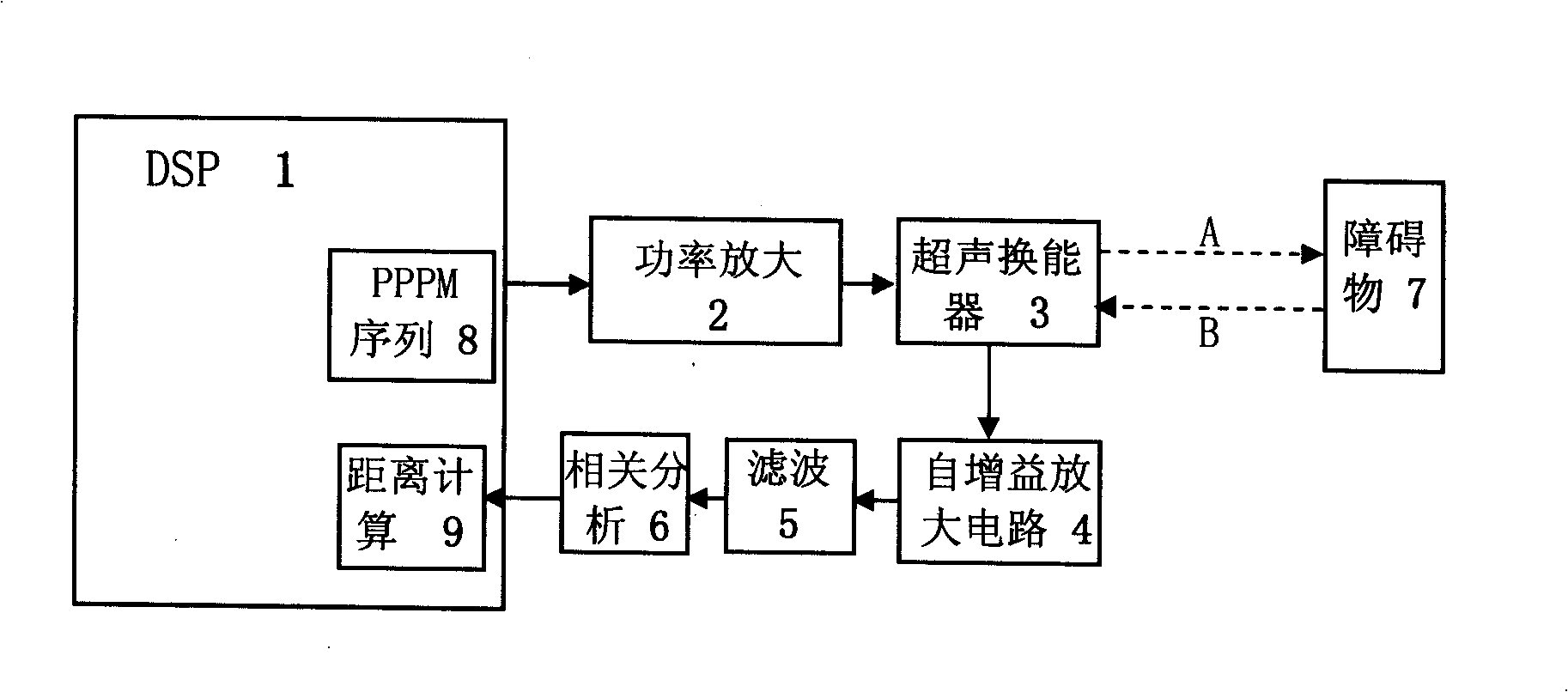
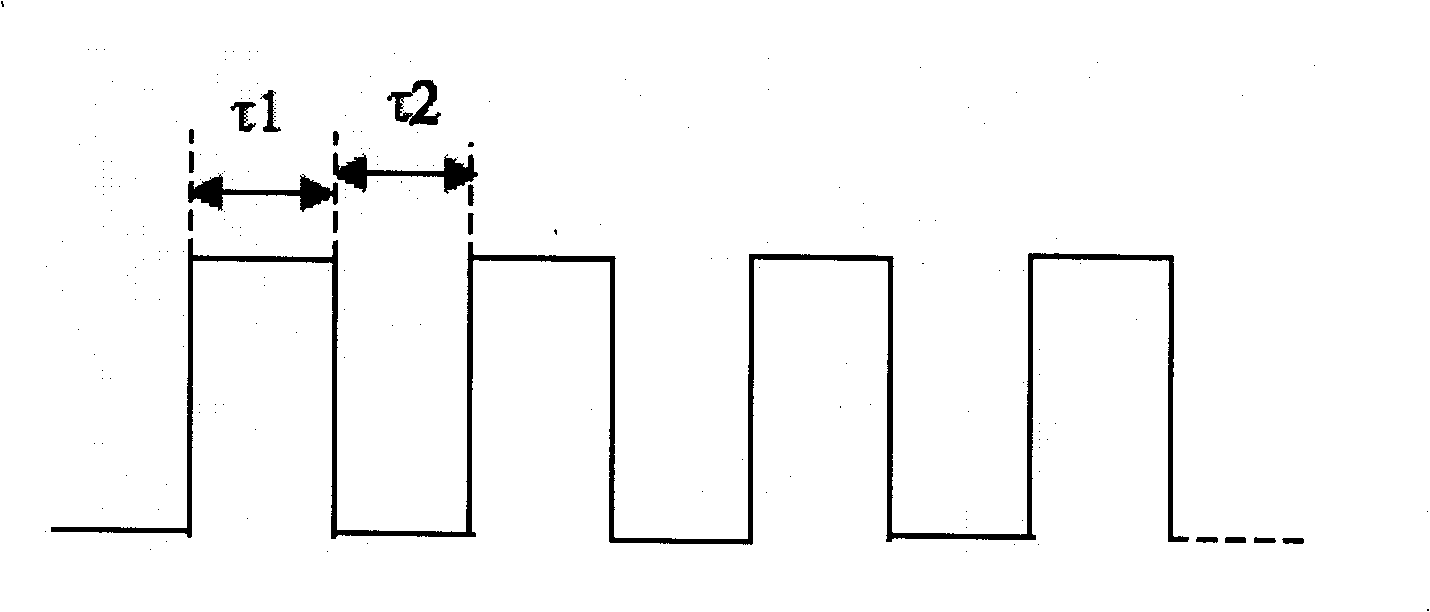
Ultrasound excitation method for eliminating robot ultrasound ranging system interference
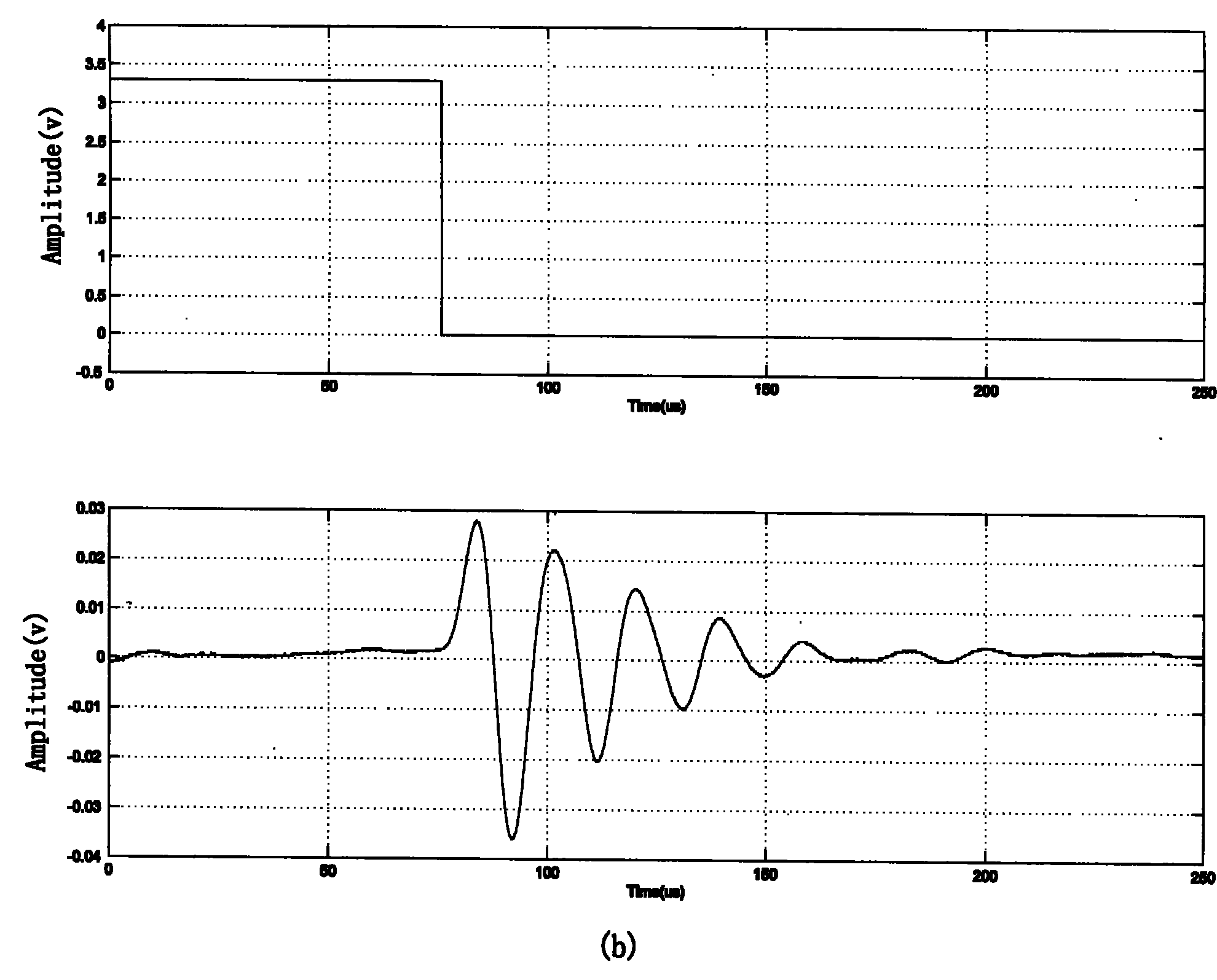
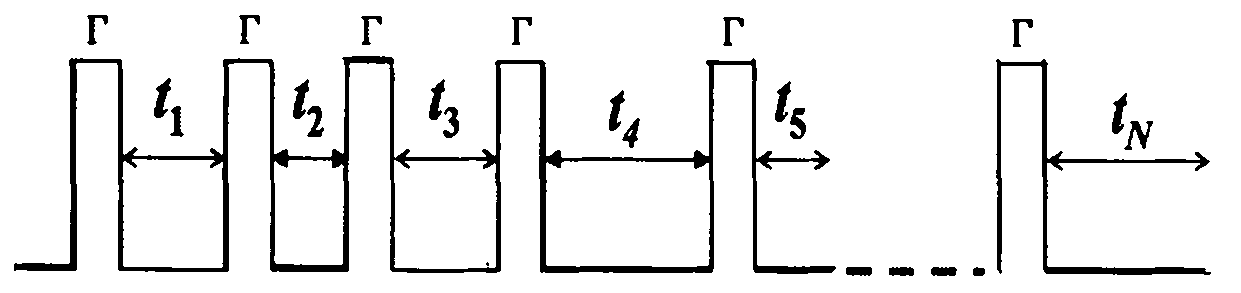
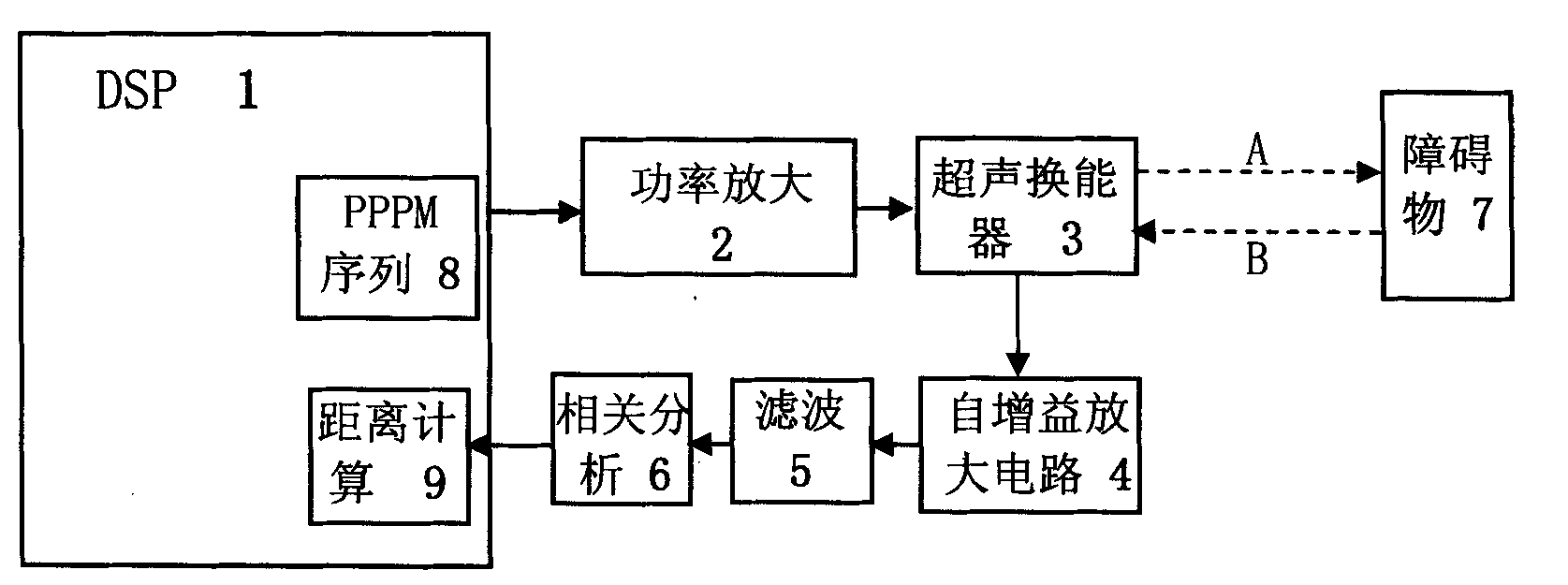
InactiveCN101271154AAvoid crosstalkShort durationGenetic modelsAcoustic wave reradiationSonificationObstacle avoidance
An ultrasonic excitation method for eliminating the crosstalk of a robot ultrasonic ranging system adopts the pseudo-random pulse position modulation mode for constructing a sole transmitting sequence for each ultrasonic transducer and uses the genetic optimization algorithm for optimizing the time interval between the adjacent pulses in the pseudo-random pulse position modulation sequence, thus allowing the duration of the transmitting sequence of each ultrasonic transducer to be 1.5 to 2ms. The ultrasonic excitation method comprises the following steps: 1. a string of pulse signals X are generated; 2. K groups of different pseudo-random series Psi are generated; 3. the pulse positions in the pulse signals X are respectively modulated by using the K groups of pseudo-random series, thus obtaining K groups of pseudo-random pulse position modulation sequences; 4. the best pseudo-random pulse position modulation sequence of the K groups is obtained; 5. K groups of ultrasonic transducers are respectively excited. The ultrasonic excitation method can lead each ultrasonic transducer to have the sole transmitting sequence, thus fundamentally avoiding the occurrence of the crosstalk; the real-time requirement of the robot navigation can be ensured; the working efficiency of a robot ultrasonic obstacle avoidance system can be effectively improved; and the reliability of the robot ultrasonic obstacle avoidance system can be greatly improved.
Owner:TIANJIN UNIV
Wireless encryption smart home remote monitoring method and system
ActiveCN106453329AImprove securityAdjust permissions reasonablyKey distribution for secure communicationHome controlComputer science
The invention provides a wireless encryption smart home remote monitoring method, and the method comprises the steps: S0, storing an alarm drive instruction at a smart home control center in advance, and carrying out the statistics of the type and time of a control instruction sent by a mobile terminal; S1, prestoring the same random number list, wherein the random number list comprises a plurality of random numbers and the reading sequence of the random numbers; S2, transmitting a calculation result to the intelligent smart home control center through a self-defining communication protocol; S3, enabling the smart home control center to read the random numbers in the random number list stored at the smart home control center according to the reading sequence of the other random numbers sent by the mobile terminal, employing an asymmetric algorithm for calculation, and enabling the smart home control center to transmit the calculation result to the mobile terminal through the self-defining communication protocol; S4, enabling the mobile terminal to read the random numbers in the random number list stored in the mobile terminal according to the reading sequence of the other random numbers, and employing the asymmetric algorithm for calculation.
Owner:浙江凡双科技有限公司
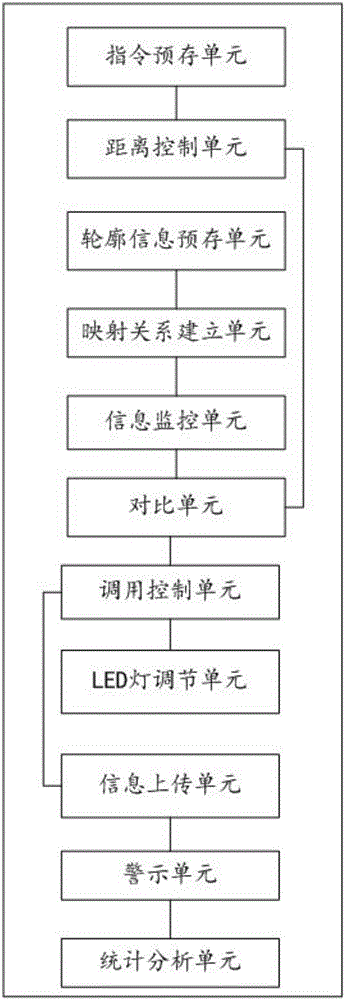
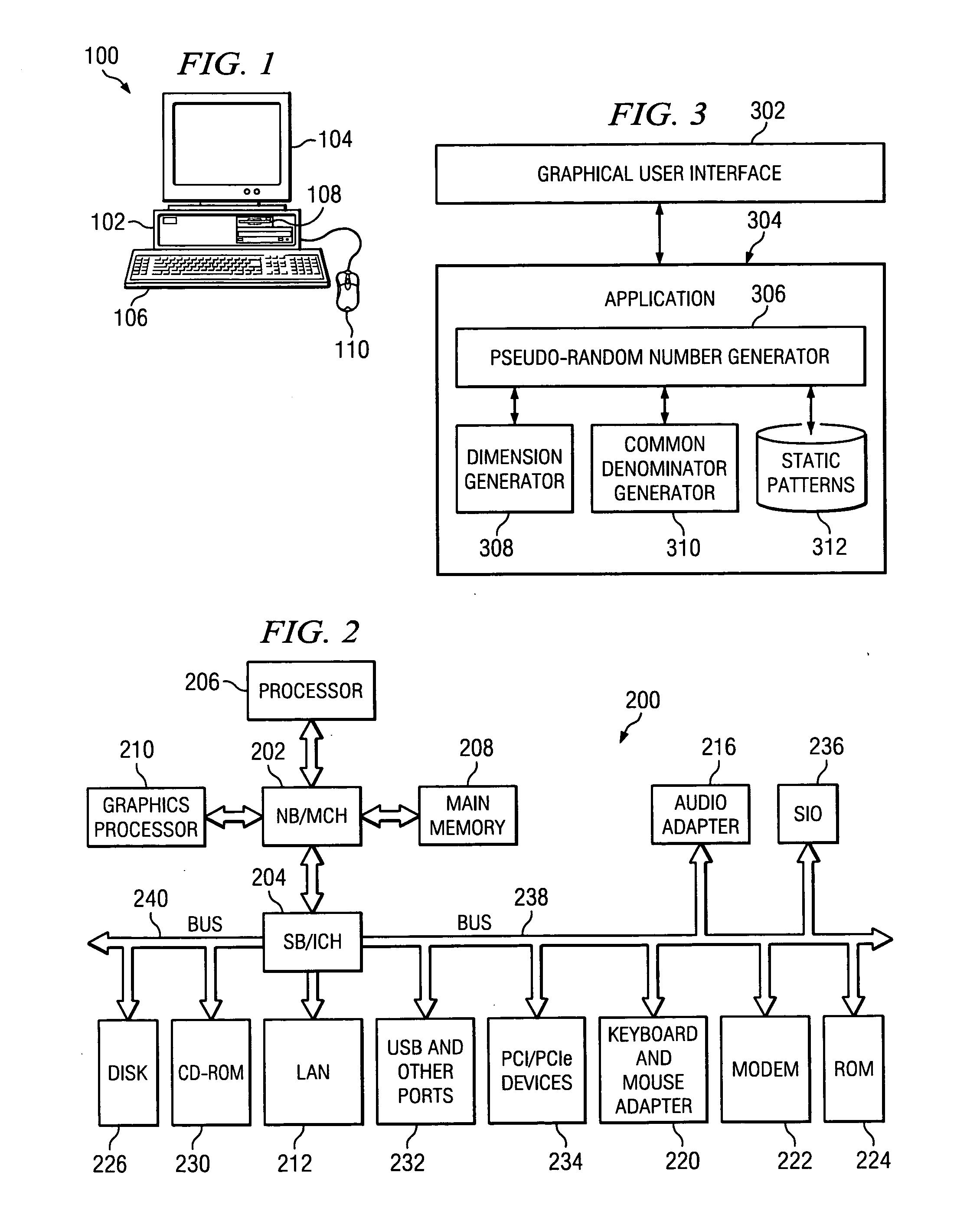
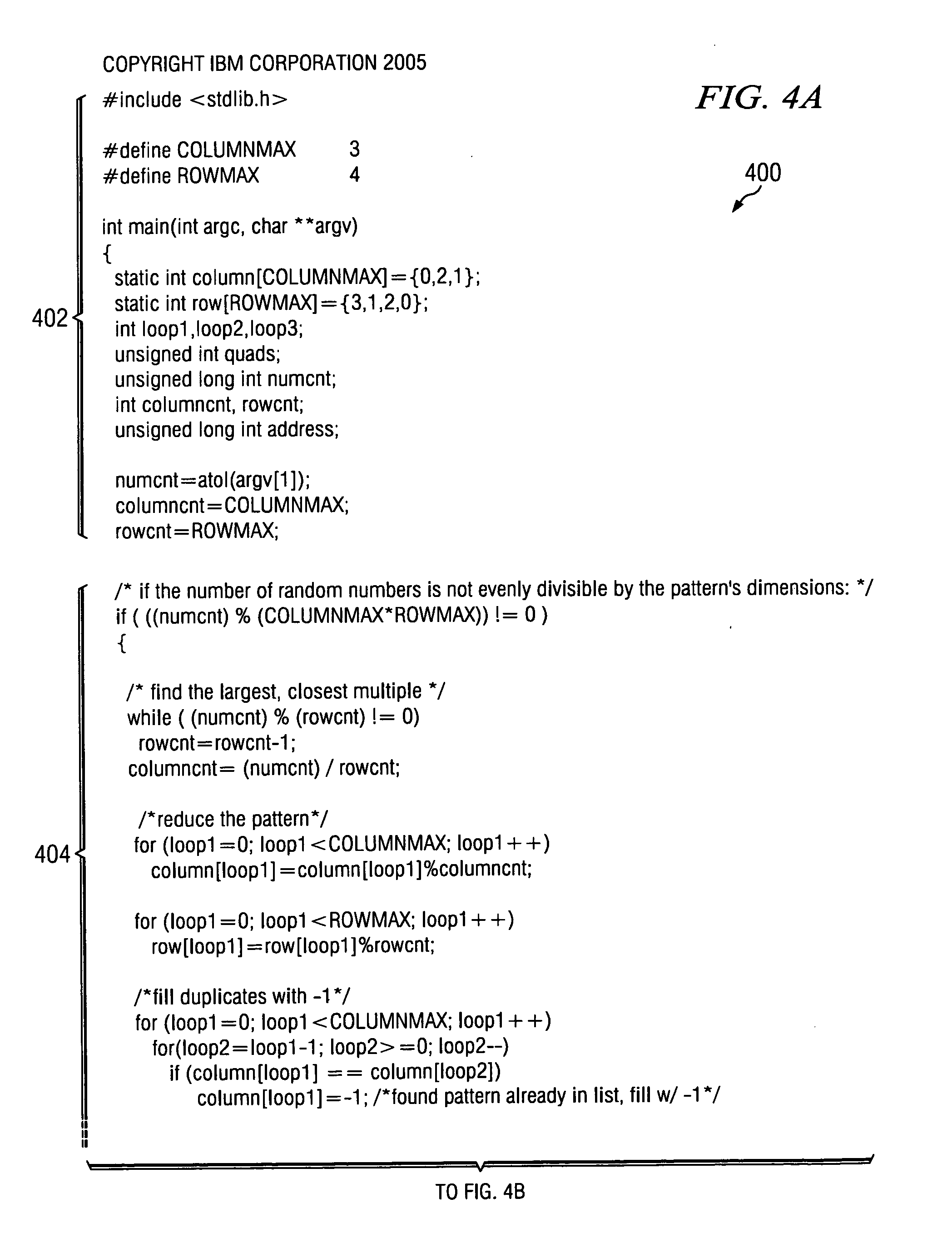
Lightweight pseudo-random number generator
InactiveUS20070165848A1Digital data processing detailsSecuring communicationData processing systemStatic mode
A computer implemented method, data processing system, and computer usable code are provided for generating random numbers. The aspects of the present invention receive a request for a number of random numbers and determine common denominators for the number of random numbers. Grid dimensions are determined using the common denominators and a static pattern is retrieved using the grid dimensions. A list of random numbers is then generated using the static pattern and the grid dimensions and the list of random numbers is returned to a requestor.
Owner:MACHINES CORP INT BUSINESS
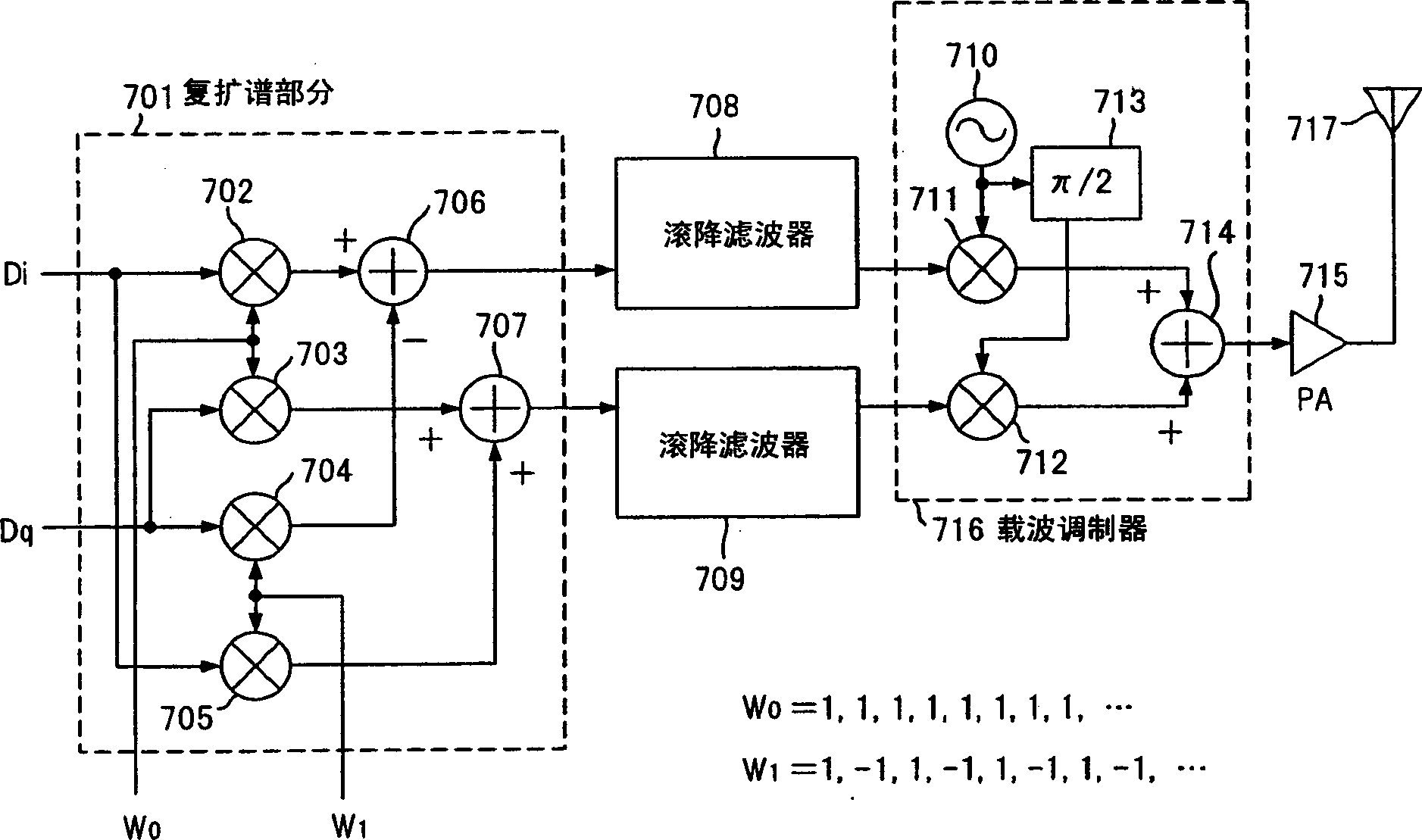
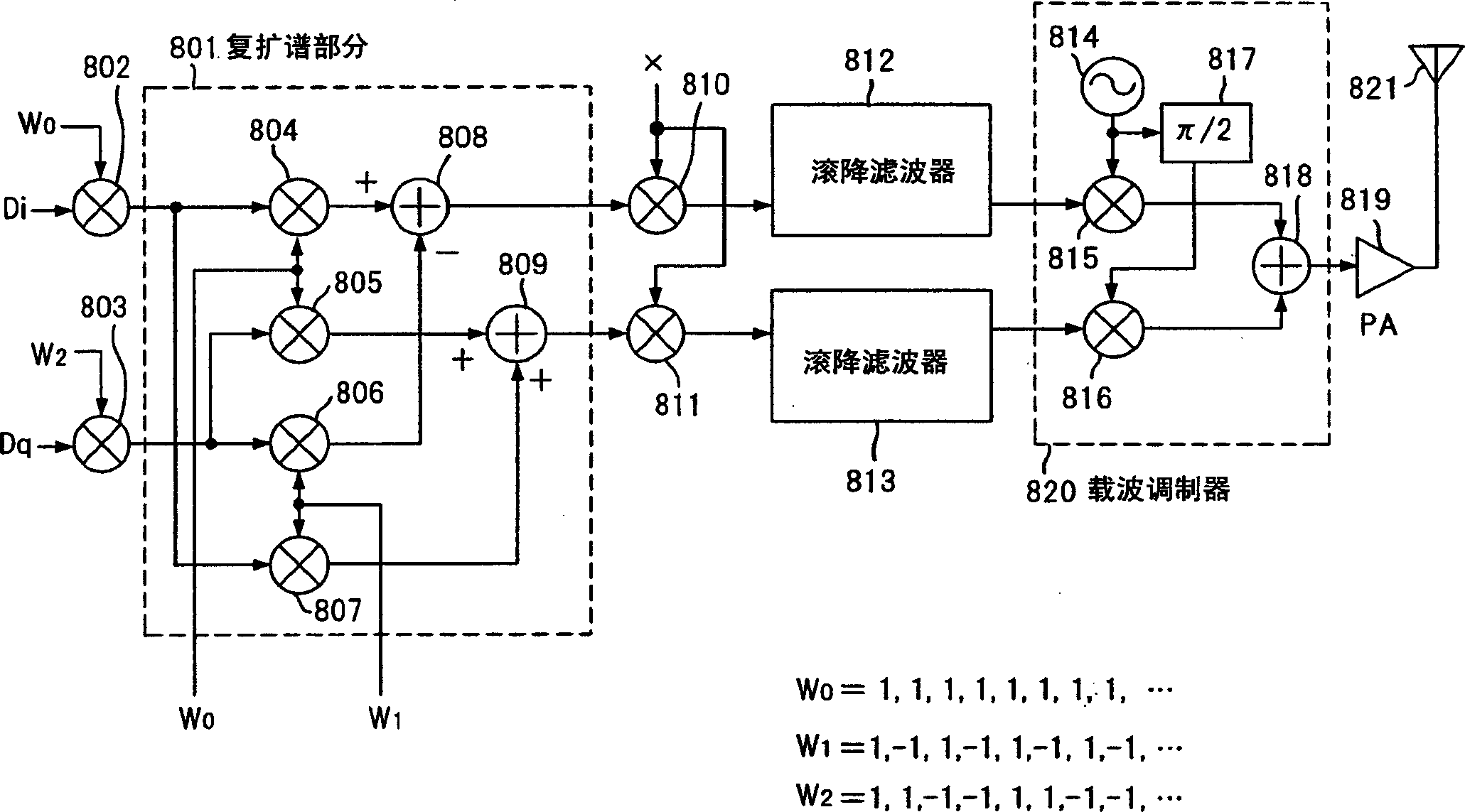
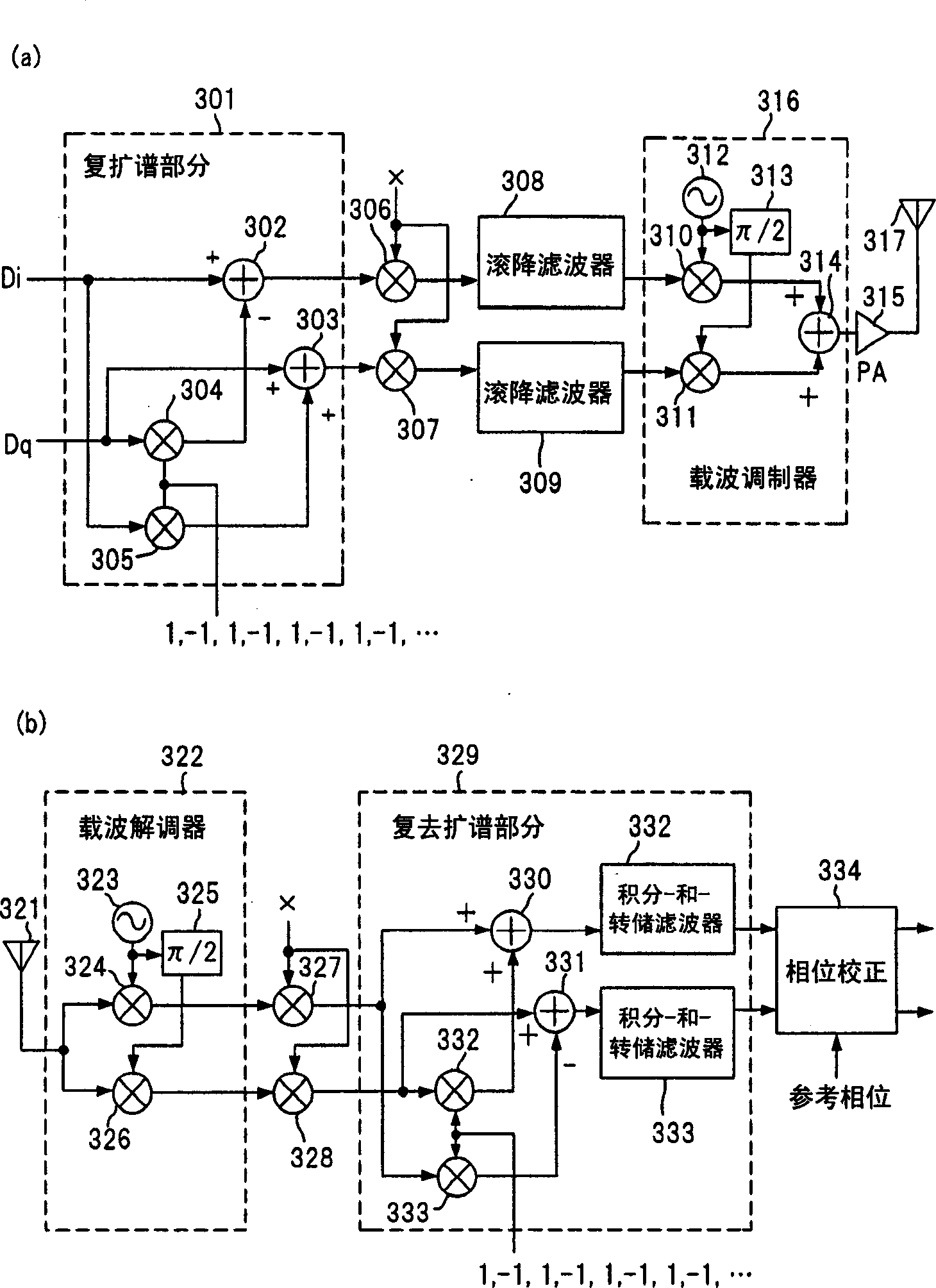
Spread-spectrum communication device
InactiveCN1342346AIncrease symbol ratePower managementConnection managementAudio power amplifierControl signal
A spread-spectrum communication device which has a reduced size, consumes less power and is produced at low cost by suppressing variation of the amplitude of a signal and relaxing the linearity required by an amplifier. A transmission signal is divided into an I-phase component and a Q-phase component. A complex spectrum-spreading unit (301) spreads the spectrum by means of multipliers (304, 305) and adders (302, 303) by using a series pattern in which 1 and -1 alternately appear. The output of the complex spectrum-spreading unit (301) is modulated by multipliers (306, 307) by using a pseudo-random series PN<(k)> (x) assigned to each user. A baseband signal shaped in waveform by roll-off filters (308, 309) is modulated by a carrier modulation unit (316), sent to and amplified by a power amplifier (315), and transmitted from an antenna (317).
Owner:SHARP KK
True random number generator based on liquid molecule Brownian movement
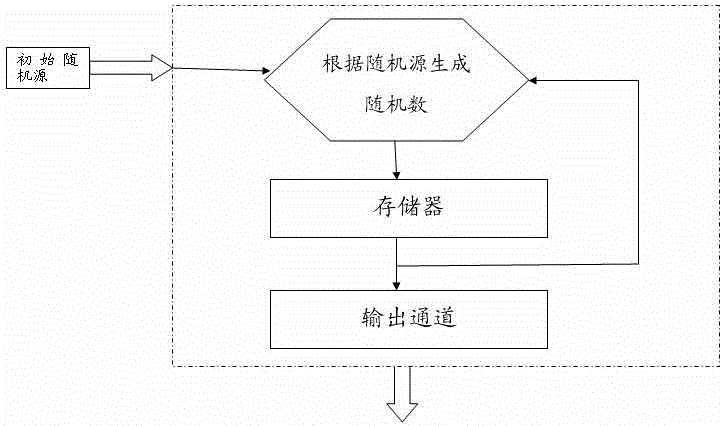
The invention discloses a true random number generator which comprises a random number acquiring unit and a random number generating unit. The random number acquiring unit comprises a high-pressure-resistant closed transparent liquid pool containing the mixture formed by particles performing Brownian movement, a high-speed microimaging device periodically shooting the internal cross section of the mixture so as to obtain multiple frames of pictures. The random number generating unit comprises a digitization processor for processing the multiple frames of pictures so as to obtain a preliminary random number string A0 and a postprocessor for processing A0 so as to obtain a random number sequence.
Owner:李昀芊
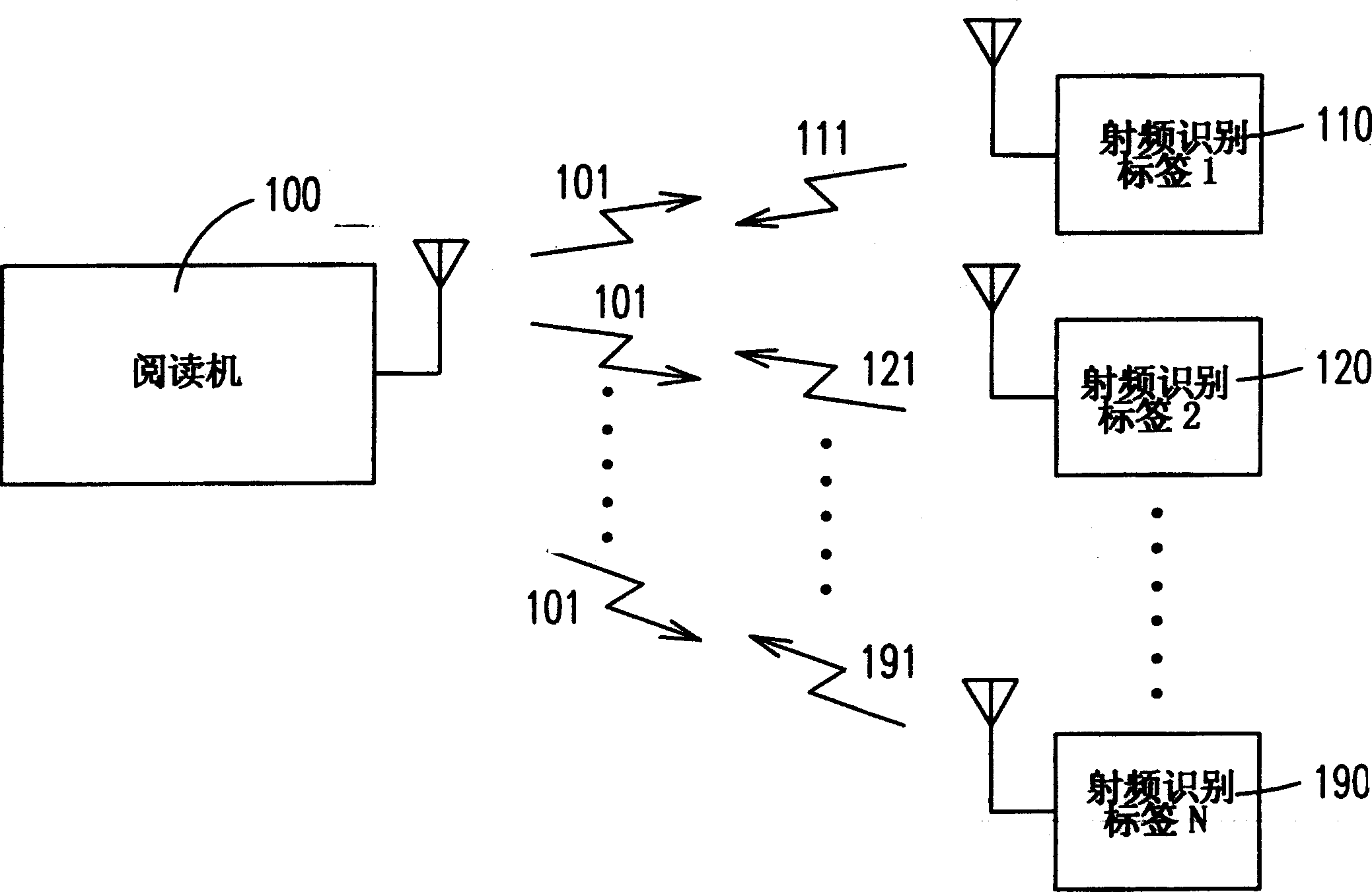
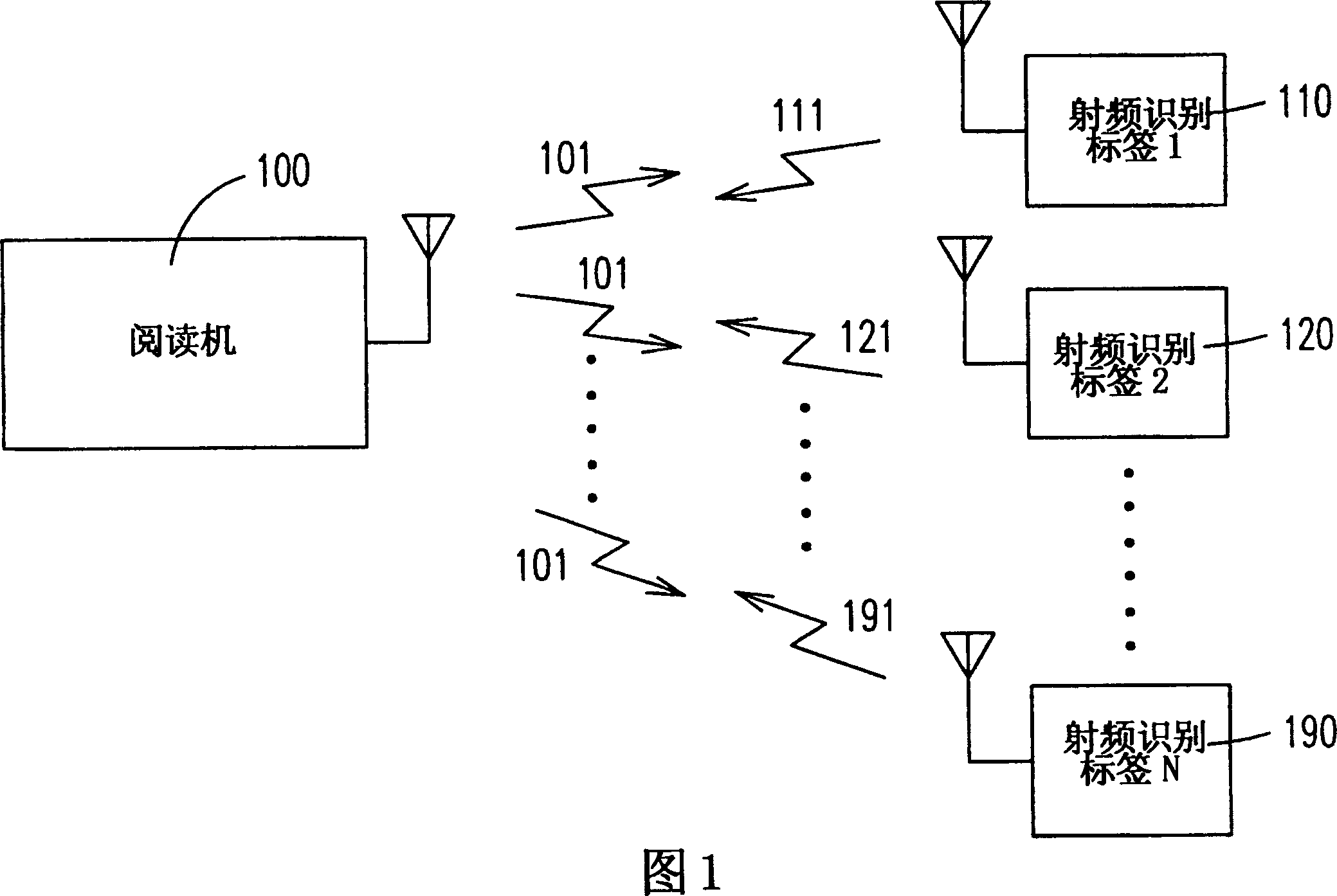
Recognition code transmission method and circuit arrangement
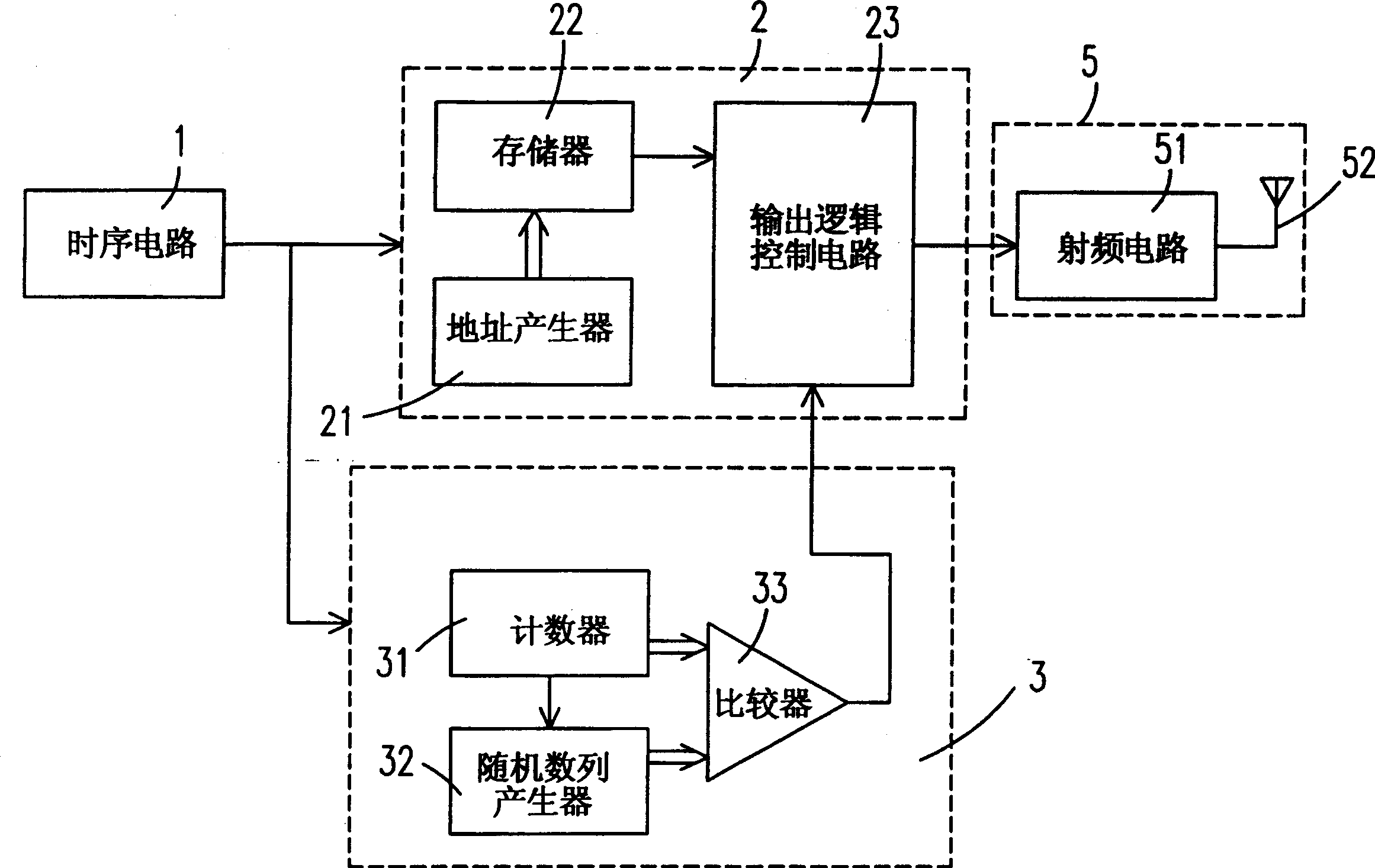
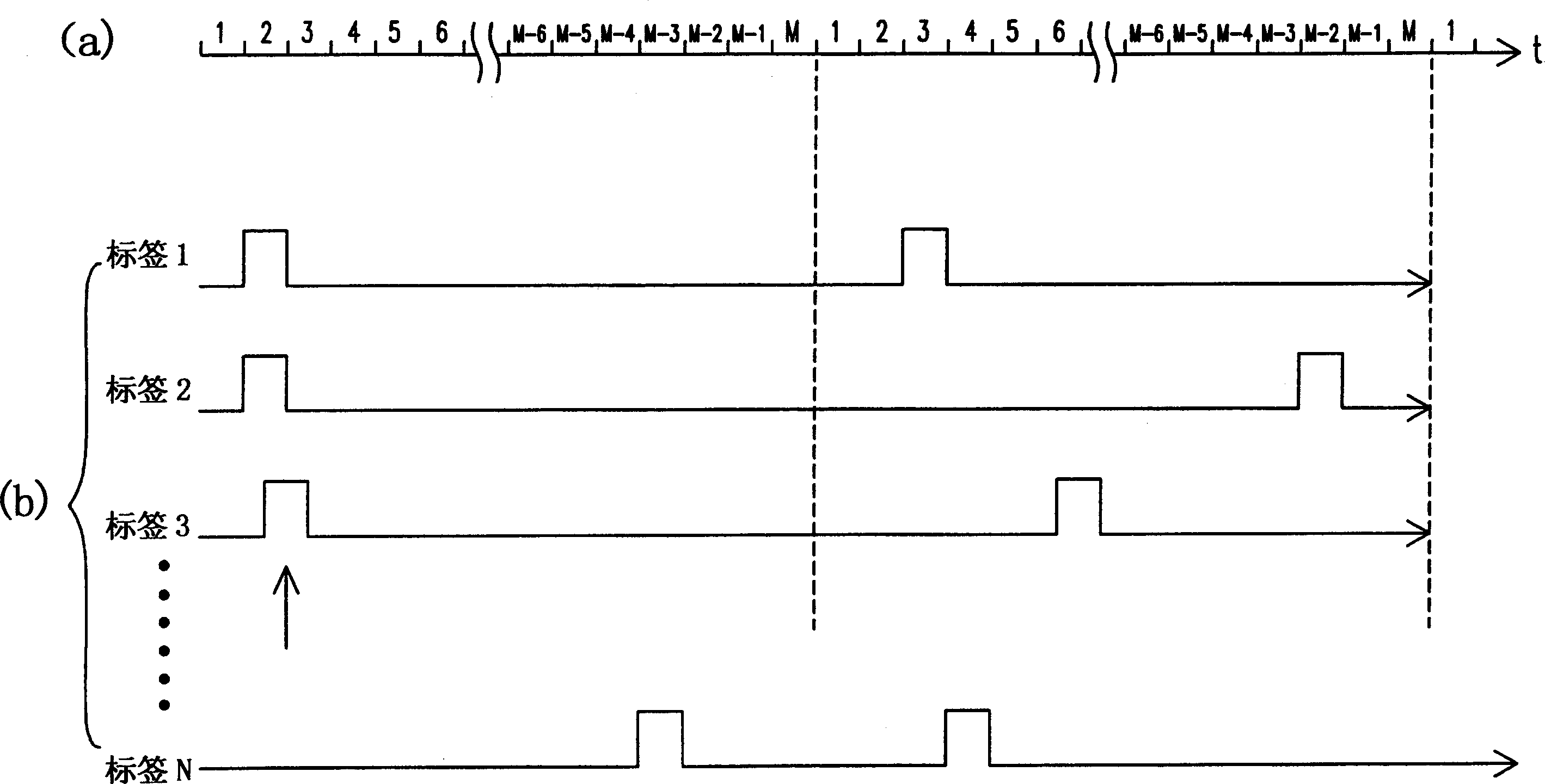
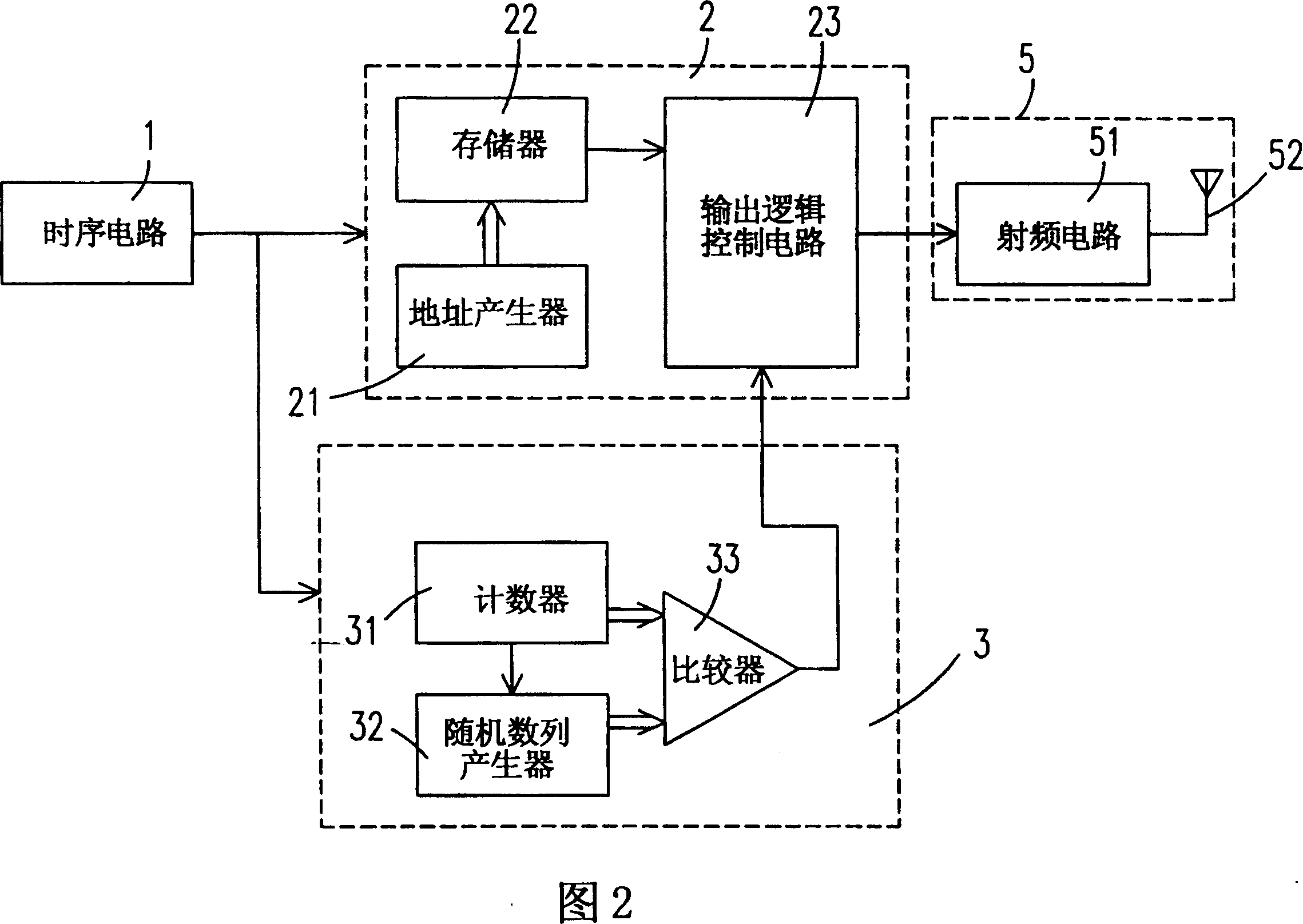
A device for controlling the transmission of ID code on RF recognition label is composed of a timing circuit, a working region selector consisting of a counter, a random numeral generator and a comparator for comparing the counter's value with the output of random numeral generator to povide an enable signal if they are matched, and a memory for storing the ID code and outputting it when said enable signal is received. It can prevent the collision between labels.
Owner:HOLTEK SEMICON
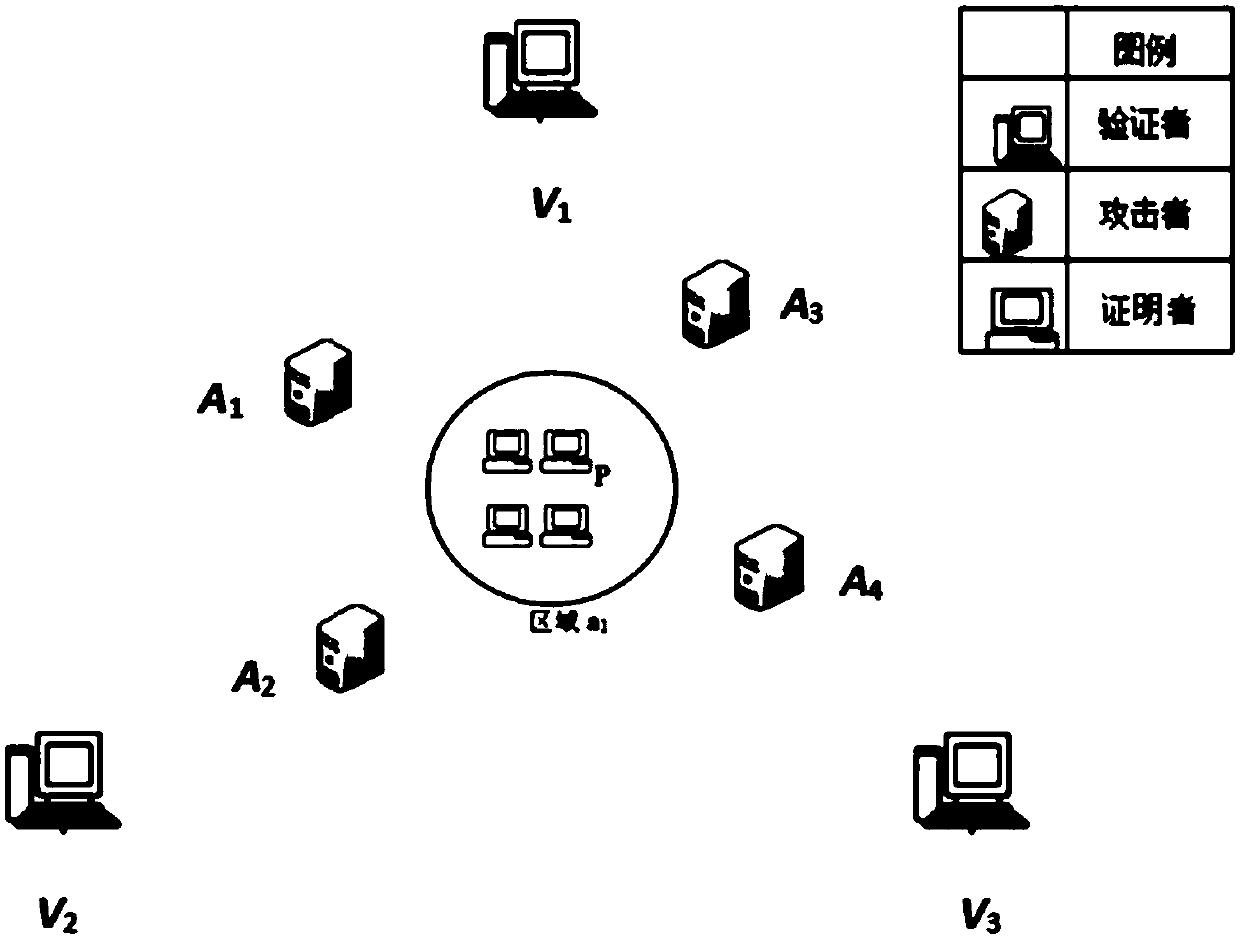
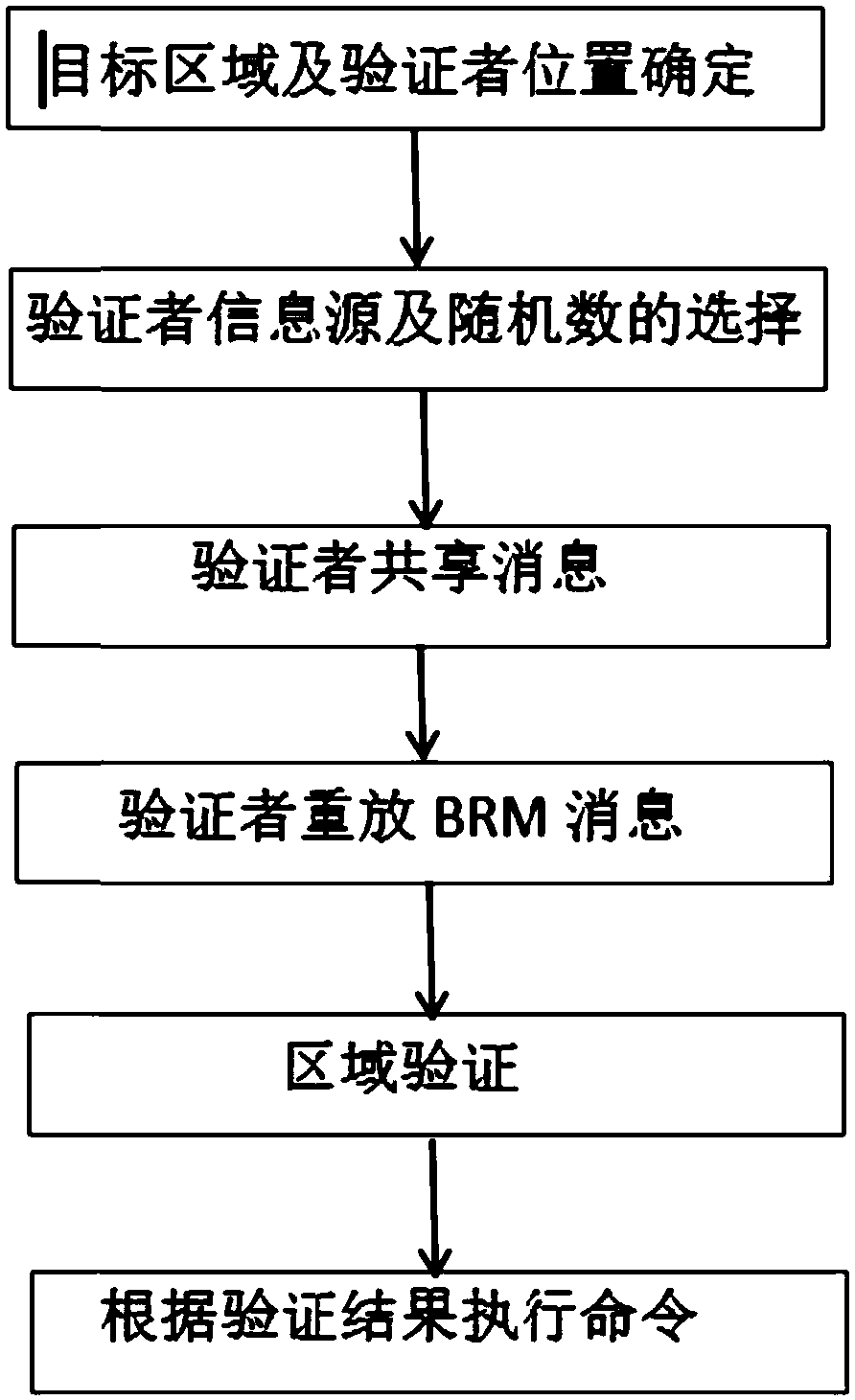
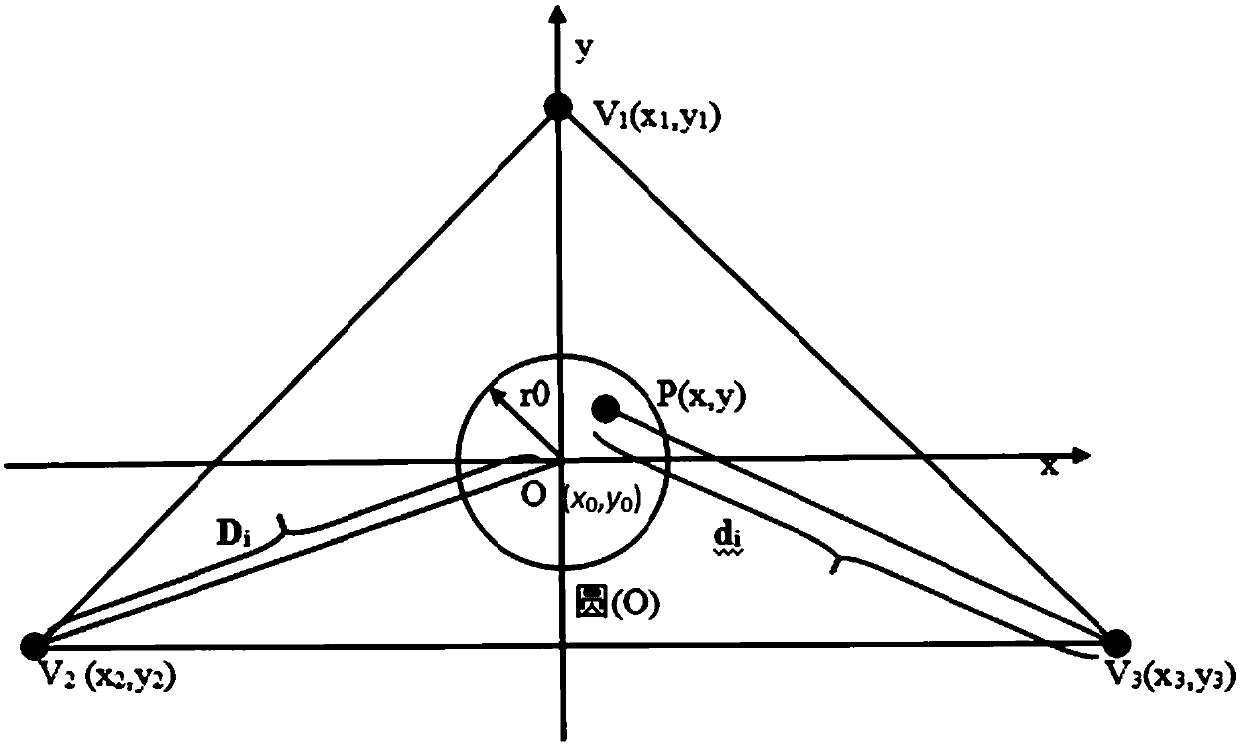
Equipment area provable security verification method with resistance to collusion attack
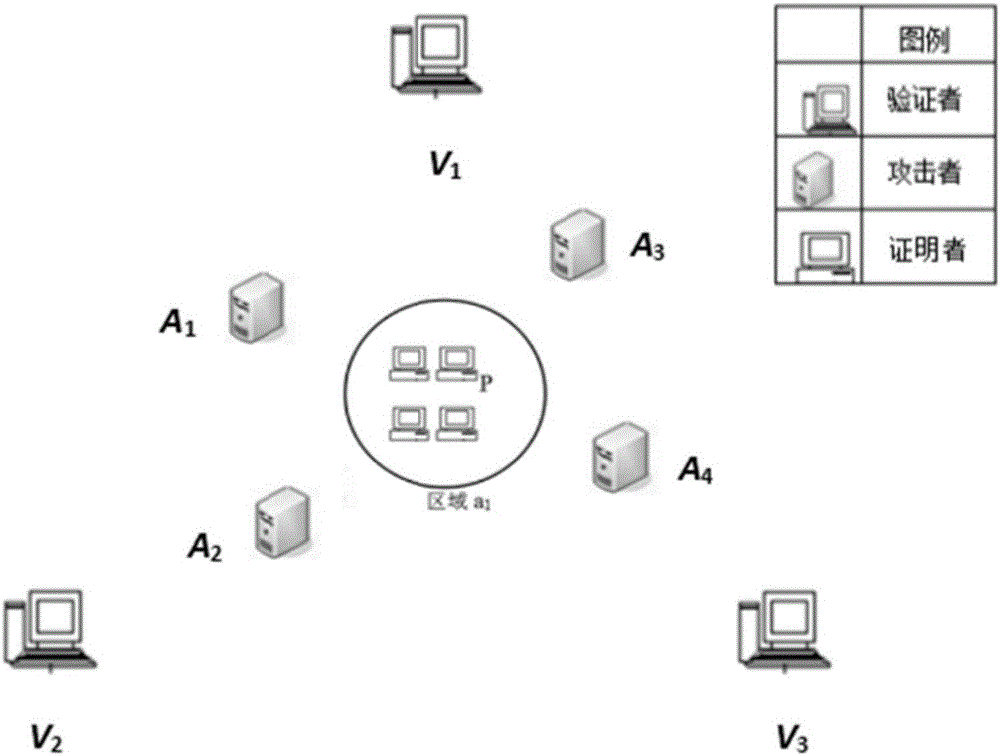
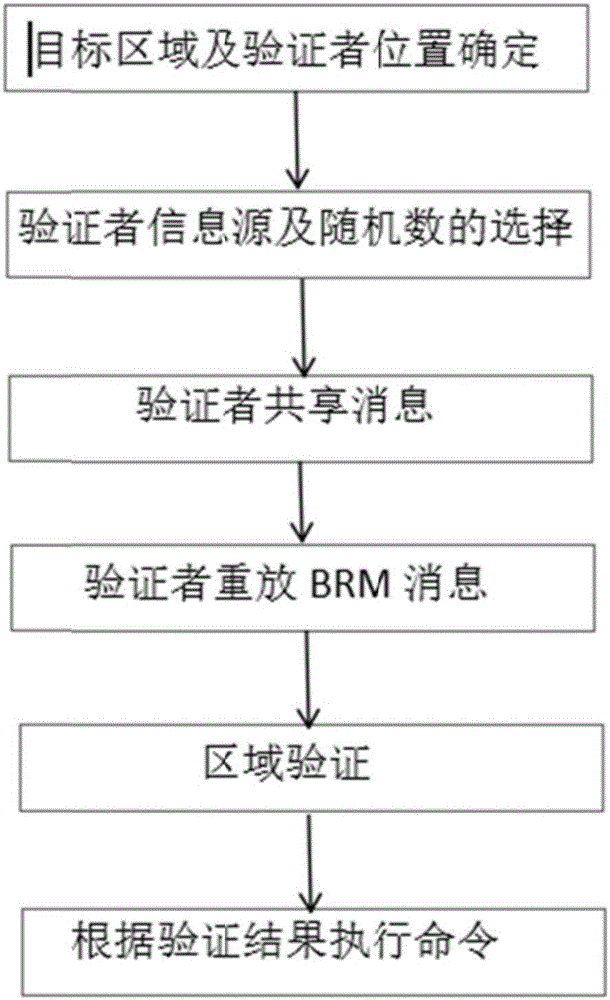
The invention discloses an equipment area provable security verification method with resistance to collusion attack and mainly solves the problem of absence of a security verification method with areas as credential information in existing position-based cryptography technologies. The implementation scheme of the method comprises steps as follows: a provable security verification model is built, and a prover is located in a target area; verifiers select information sources and random series and share information with one another, and the verifiers replay information in a broadcasting manner; a metric value is generated by the prover, and a verification value is calculated, and position information of the prover is broadcasted; the verifiers verify correctness of the verification value, whether the position information of the prover is accepted is judged, if the verification value passes the verification, the position information of the prover is broadcasted, otherwise, the verification value does not pass the verification, that is, the position claimed by the prover is not in the area, and the verification is finished. According to the method, any prover in the target area can effectively resist the collusion attack of multiple opponents after verification, and the security verification of the position of the prover is realized. The method can be used for verifying whether the equipment, namely, the prover, is located in the target area.
Owner:XIDIAN UNIV
Cross flow fan and air conditioner with the fan
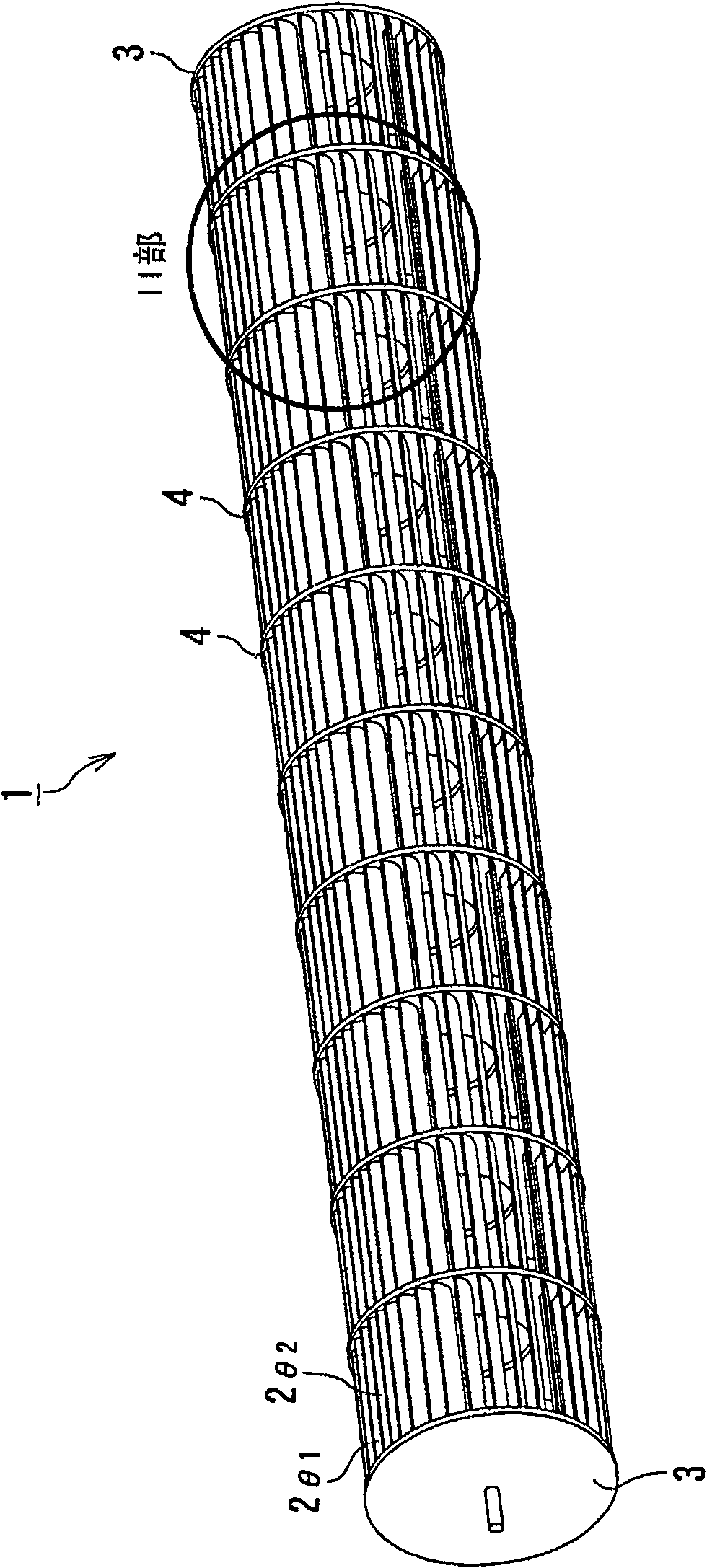
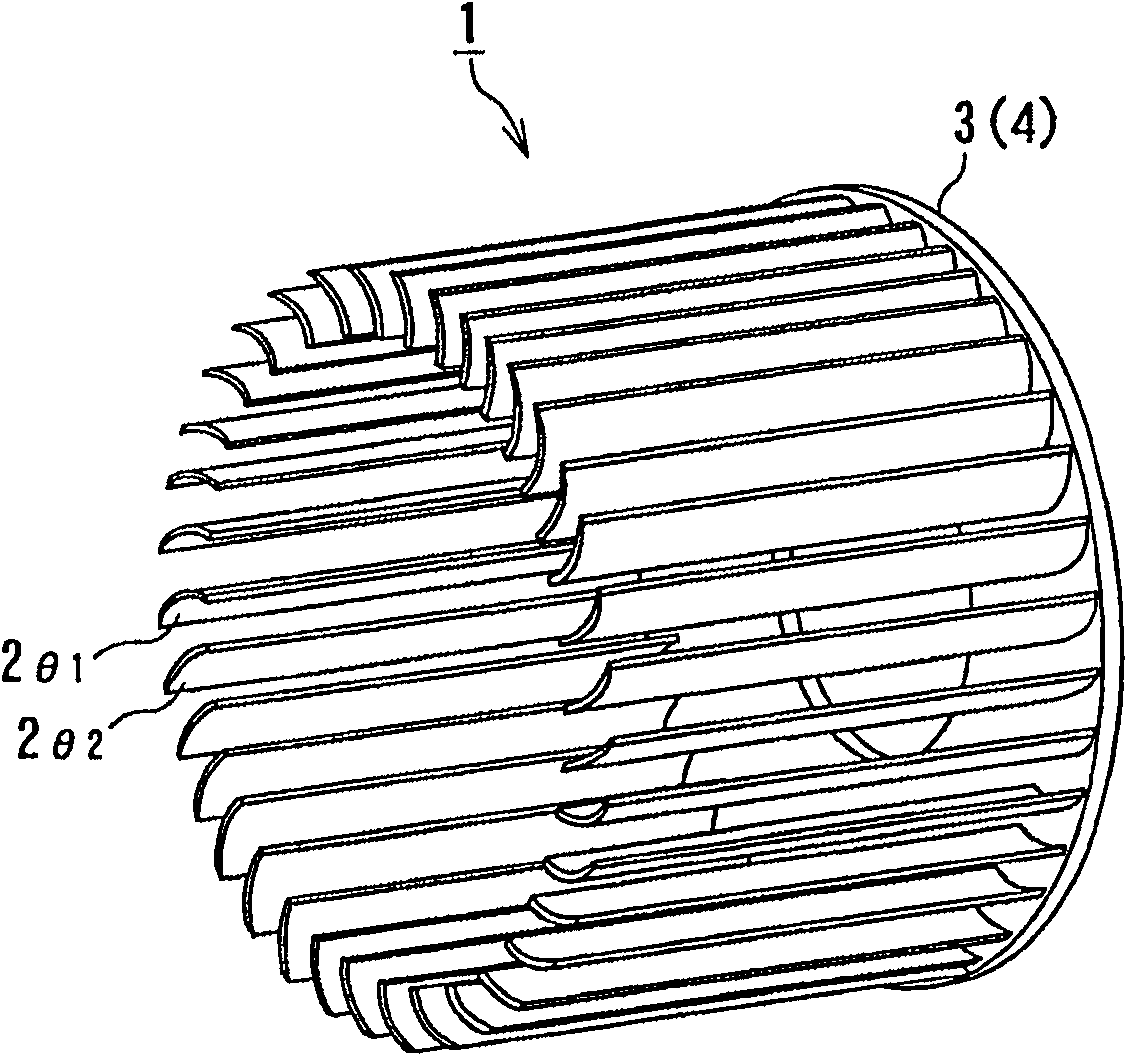
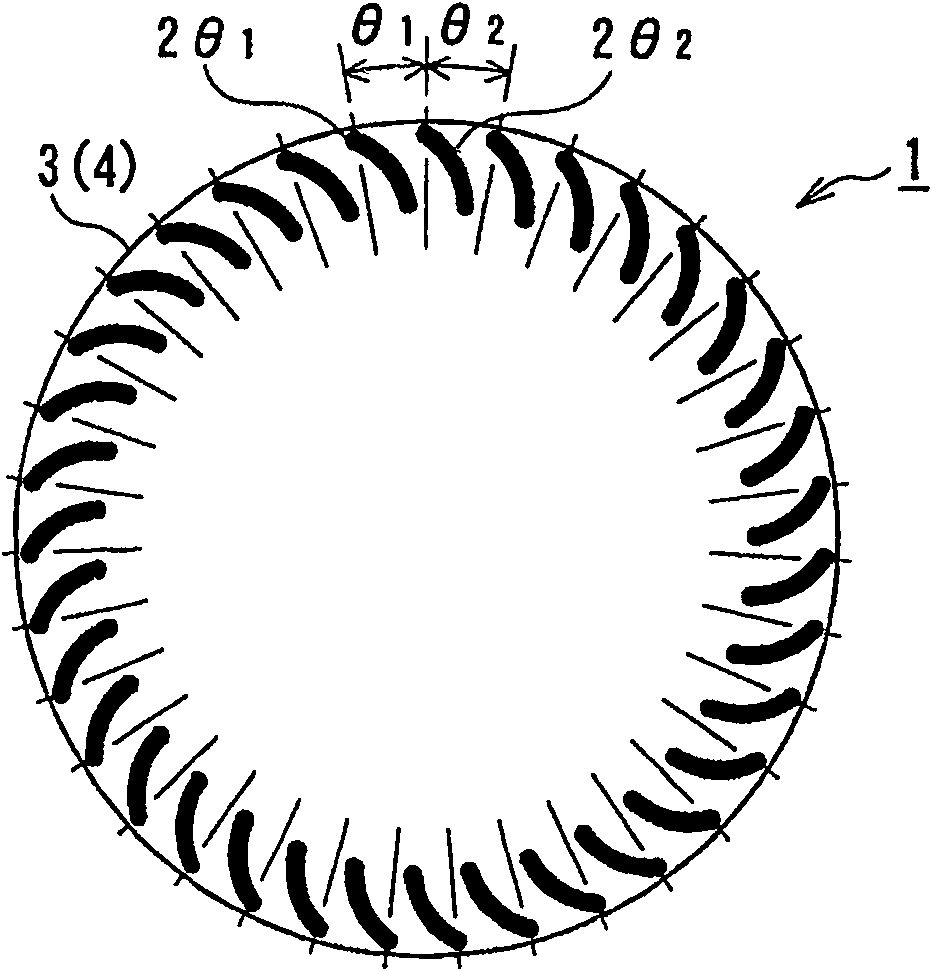
ActiveCN100552230CIncrease air volumeReduce air supply noisePump componentsLighting and heating apparatusEngineeringRandom series
A cross flow fan (1) for an air conditioner capable of reducing a load on a motor while reducing the noise of a blower, comprising a plurality of blades (2theta1, 2theta2) and support plates (3, 4) pivotally supporting the plurality of blades (2theta1, 2theta2) at both ends thereof, characterized in that the plurality of blades (2theta1, 2theta2) are disposed annularly on the support plates so as to form a cyclic pseudo-random series while maintaining a periodicity at two different pitch angles (theta1, theta2) so that, when a displacement Delta as the ratio of a difference (theta1 - theta2) between the two pitch angles to a pitch angle (theta) when all blades are disposed at equal intervals is Delta = (theta1 - theta2) / theta, the displacement Delta is 0.09 <= Delta <= 0.26.
Owner:TOSHIBA CARRIER CORP
Outer loop transmission power control method and radio communication device
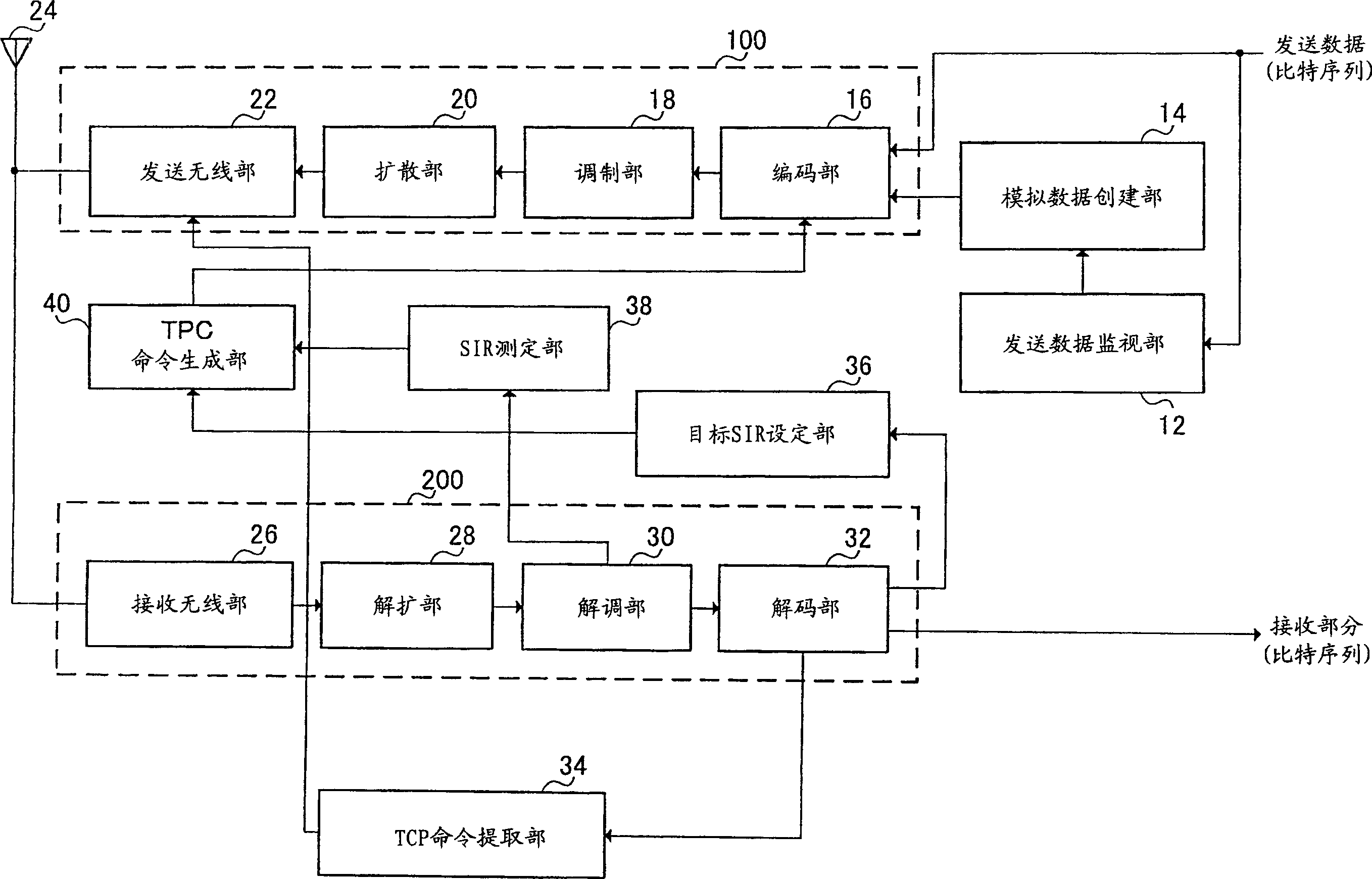
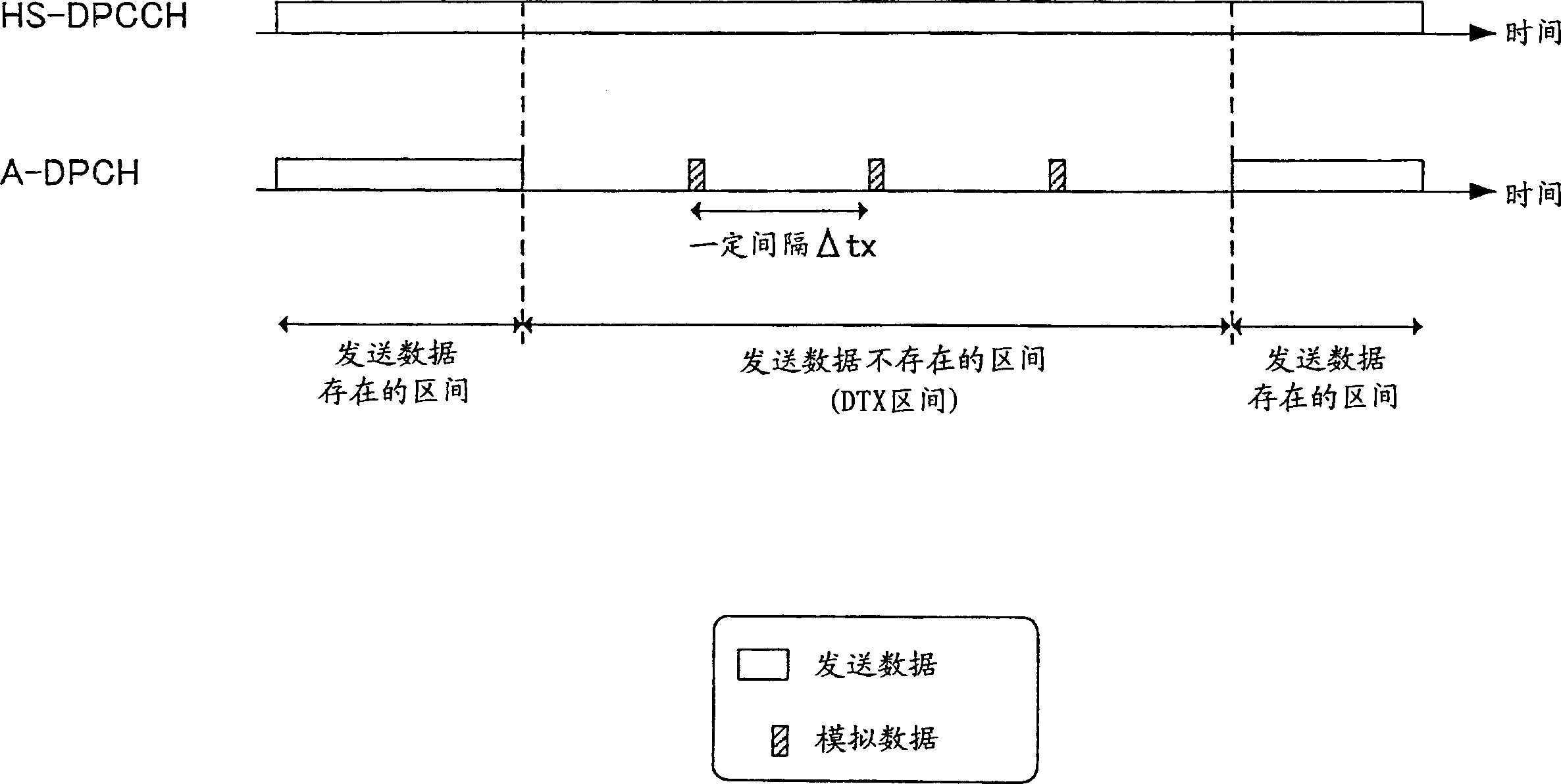
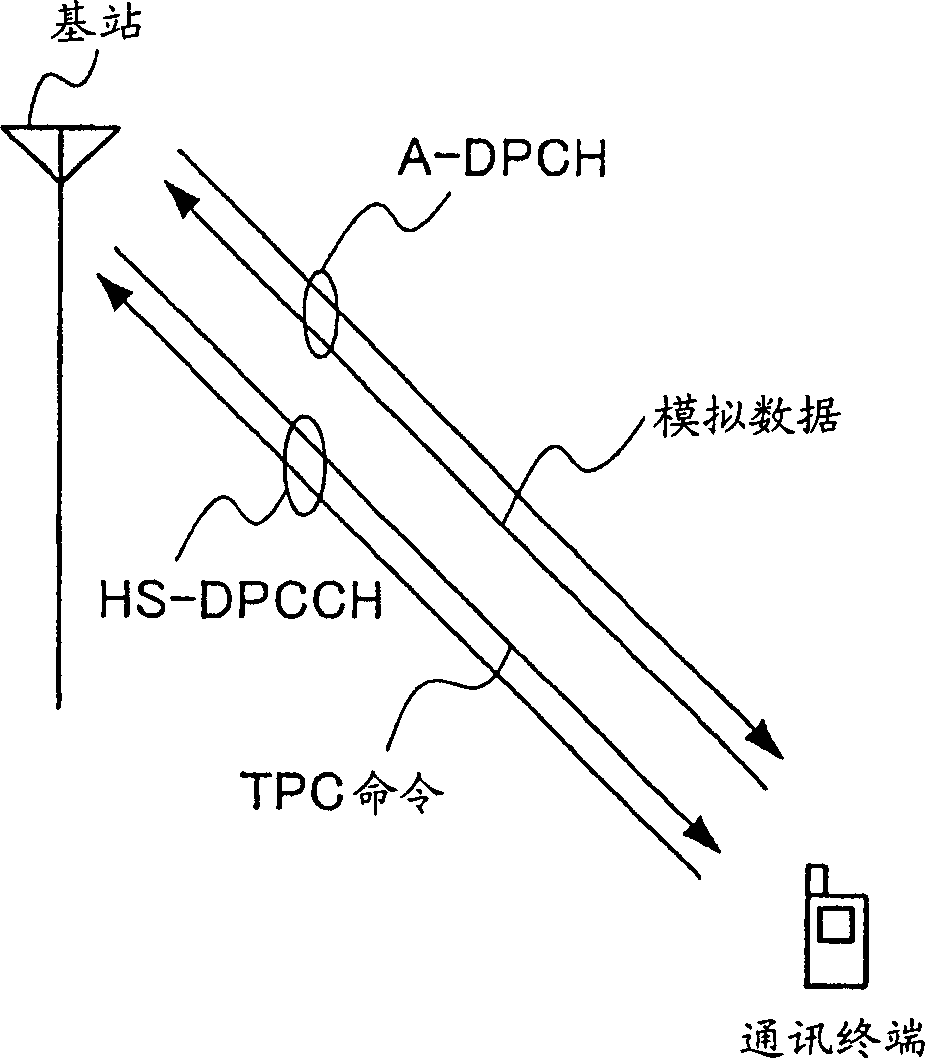
In a wireless communication system where A-DPCH (Associated-Dedicated Physical Channel, with dedicated physical channel) and HS-DPCCH (High Speed-Dedicated Physical Control Channel, high-speed dedicated physical control channel) coexist, in order to (Discontinuous Transmission, discontinuous transmission) also can carry out appropriate outer loop transmit power control to HS-DPCCH during, transmit data monitoring section (12) monitor whether the bit sequence that transmits by A-DPCH exists, analog data creation section (14 ) generates a random sequence for the outer loop transmission power control of the HS-DPCCH in the DTX interval where the bit sequence does not exist, the encoding part (16) performs CRC encoding on the generated random sequence, and then the transmitting radio part (22) passes A- DPCH sends the random series after CRC encoding.
Owner:PANASONIC CORP
Lithium ion battery protector
InactiveCN104104068AFix security issuesRealize arbitrary series and parallel useEmergency protective circuit arrangementsSecondary cells servicing/maintenanceMOSFETAluminium-ion battery
The invention discloses a lithium ion battery protector which comprises a circuit break protection switch made of shape memory alloy. The circuit break protection switch comprises two contacts at the two sides. At a normal temperature, the contacts at the two sides are contacted; and when at a memory temperature, the contacts at the two sides are separated. The lithium ion battery protector utilizes the memory performance of the shape memory alloy, so that the anti-interference and anti-high-voltage capability and passive over-current capability are improved, and a complex protection system for the lithium ion battery is simplified; and the battery is modularized, so that the defects, such as short service life, poor stability, weak anti-interference capability, weak anti-high-voltage capability and weak anti-over-current capability and the like at present, of an electronic semiconductor (such as MOSFET) are overcome, and the problem of the safety of the lithium ion battery is effectively solved. The physical characteristics of the material of the switch are utilized, so that when temperature signals are utilized to trigger the switch, the cell balancing and over charge inhibition function are taken into consideration, the battery module can be guaranteed to realize predictable random series / parallel connection usage, and the usage threshold of the power lithium battery is reduced.
Owner:SINONEWENERGY SUZHOU TECH
Pseudo-random series producing method for use in Markov paging test
InactiveCN1406012AResolve synchronizationSynchronization is simpleCode division multiplexRadio/inductive link selection arrangementsExclusive orElectronic serial number
The base station stores the electric serial number sent by the mobile station. The base station takes the current GPS time every 20 ms. The 'exclusive or' logic operation is carried out between the absolute time obtained and the 32 digits set up at the mobile station. Whether the low 9 digits of the value of result with logic operation being executed is identical to the low 9 digits of the serialnumber or not is determined. If yes, the low 31 digits of the said value of result are assigned as the status value of the pseudo random sequence storage. Then, from the preset formula, the current status value of the pseudo random sequence storage is calculated and the Markov data frame utilized for link test is generated. The invented method solves the synchronization issue of generating pseudorandom sequence and makes the statistics of the error frame rate of the force inverted link as well as monitors its quality.
Owner:ZTE CORP
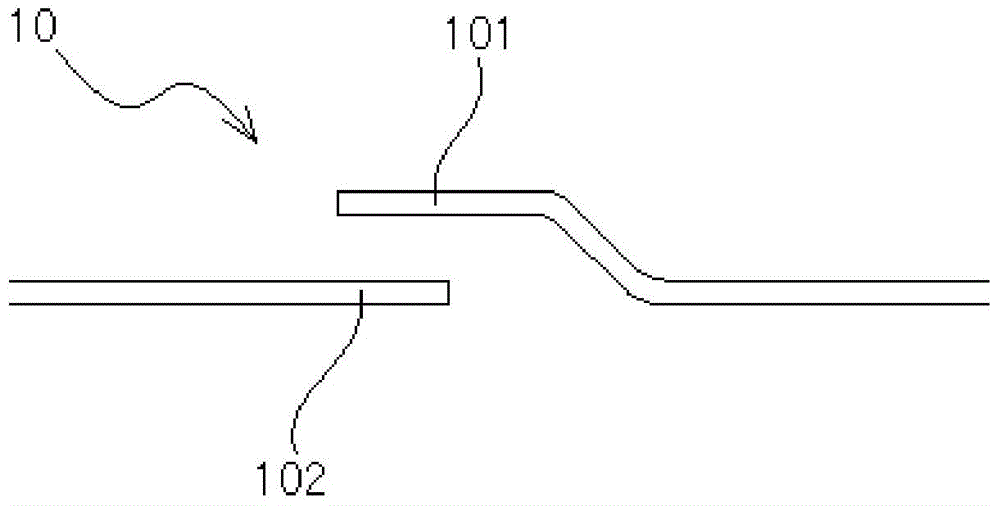
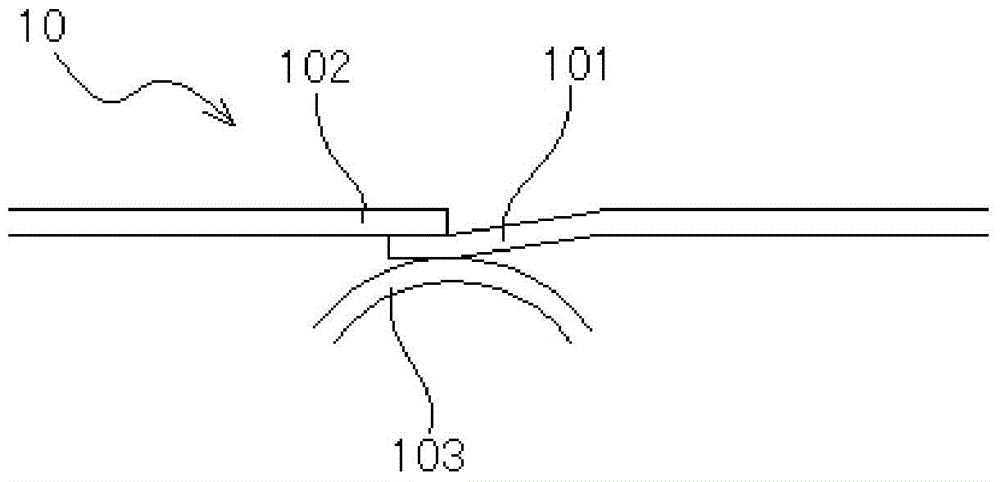
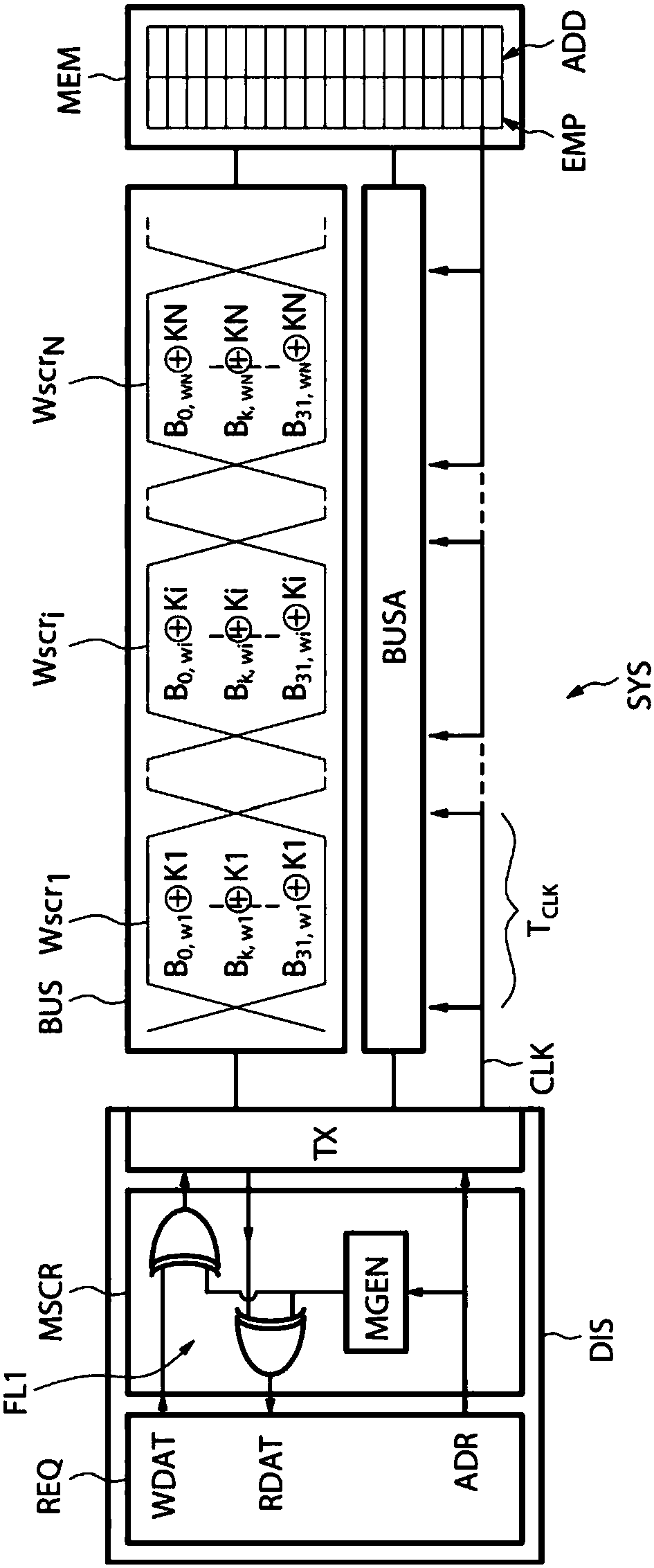
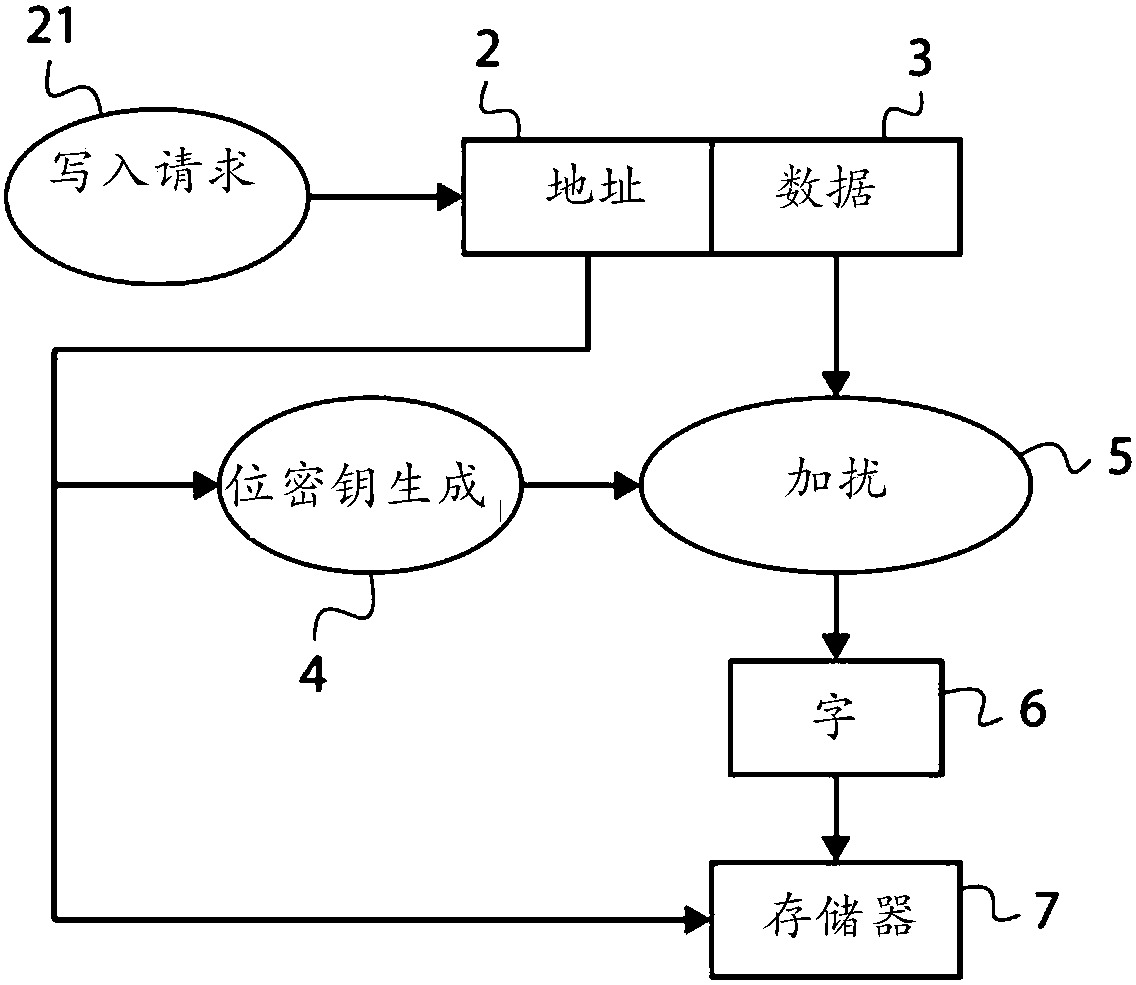
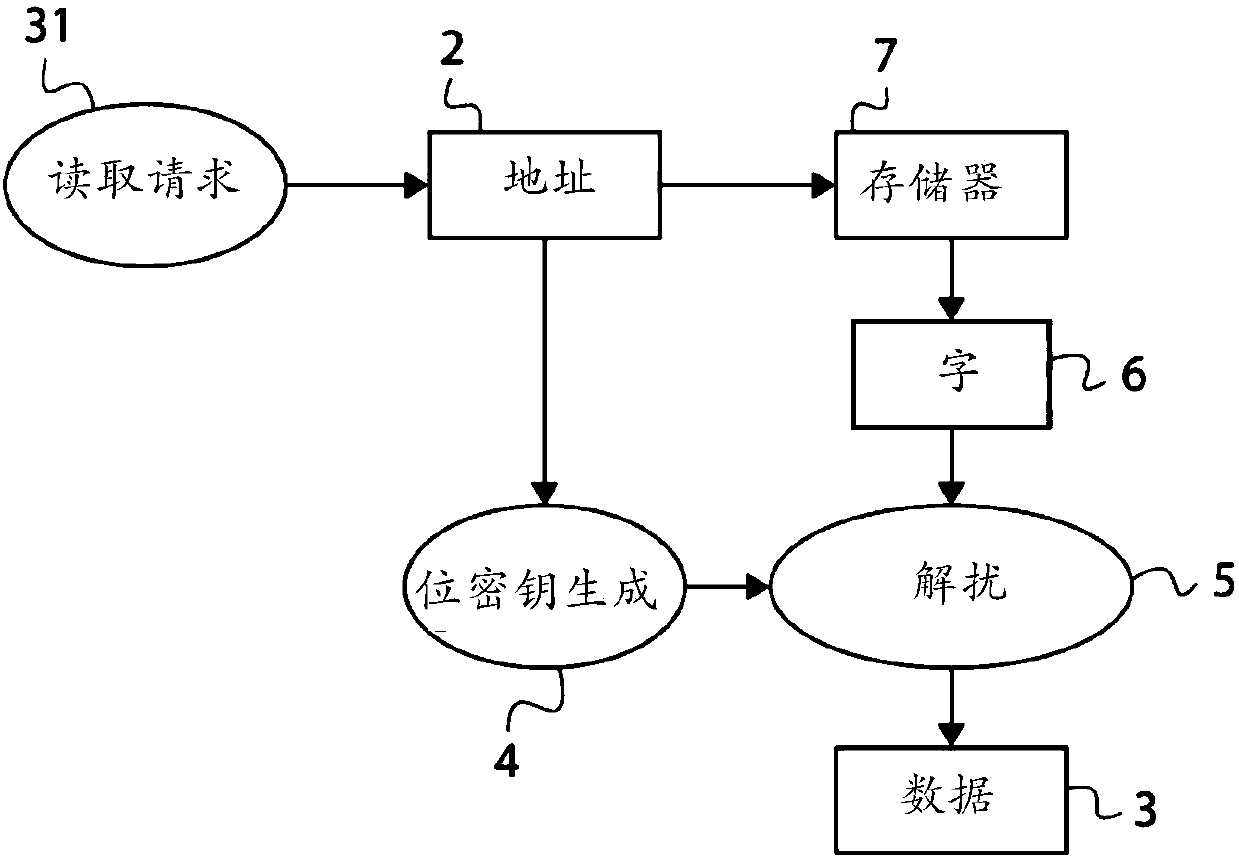
Method and device for transfer of data to or from a memory
ActiveCN107799140ASynchronising transmission/receiving encryption devicesDigital data protectionRandom seriesLogical Function
A method for reading or writing data at an address of a memory is disclosed. The data includes a number of consecutive words that each has a plurality of bits. The words are transferred to or from thememory in synchronization with a clock signal so that each word is transferred in one cycle of the clock signal. The bits are scrambled or unscrambled by applying a logic function to the bits of eachword. The logic function is identical for the scrambling and the unscrambling and makes use of a bit-key that is dedicated to the word and is identical for the scrambling and the unscrambling. Each bit-key comes from a pseudo-random series generated based on the address.
Owner:STMICROELECTRONICS (GRENOBLE 2) SAS +1
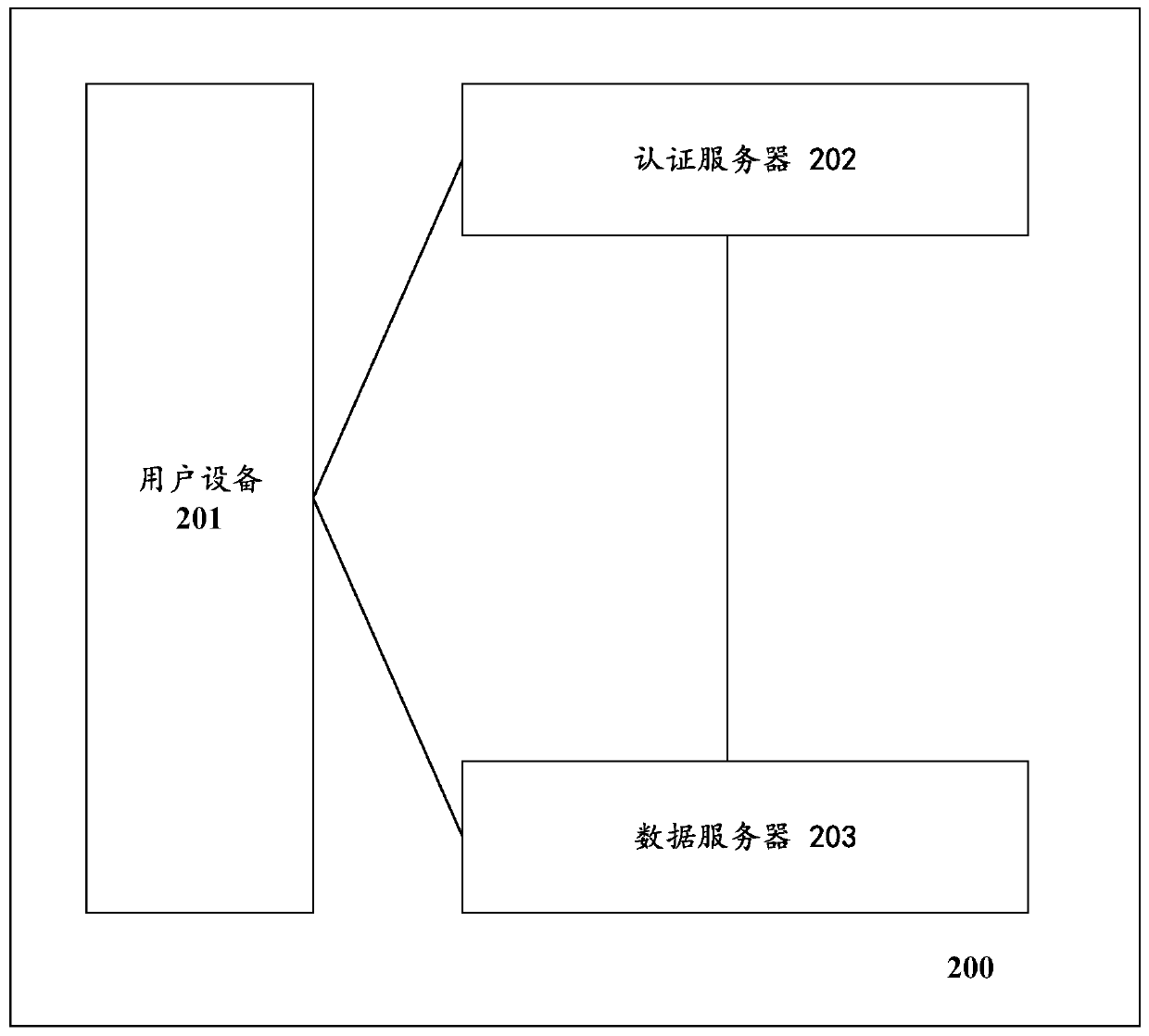
A method and a system for carrying out collaborative authentication on identification information in the Internet
The invention discloses a method and a system for collaborative authentication of identification information in the Internet. The method comprises the following steps: user equipment sends an identityauthentication request to an authentication server in the Internet; When it is determined that the verification result of the initial verification of the user equipment is passed, the authenticationserver sends the basic text file and the random sequence generator to the user equipment; The user equipment generates a first random sequence by using the random sequence generator and sends the first random sequence to the authentication server, and forms a first character sequence; authentication data comprising a plurality of pieces of identification information is generated according to the first character sequence and the authentication data is sent to the authentication server, and encrypted mixed information is decrypted to obtain a plurality of decrypted characters and fingerprint information, and a virtual private network connection between the user equipment and a data server is established when the decrypted characters are the same as the plurality of characters sent by the user equipment and the fingerprint information passes the verification.
Owner:北京天易数聚科技有限公司
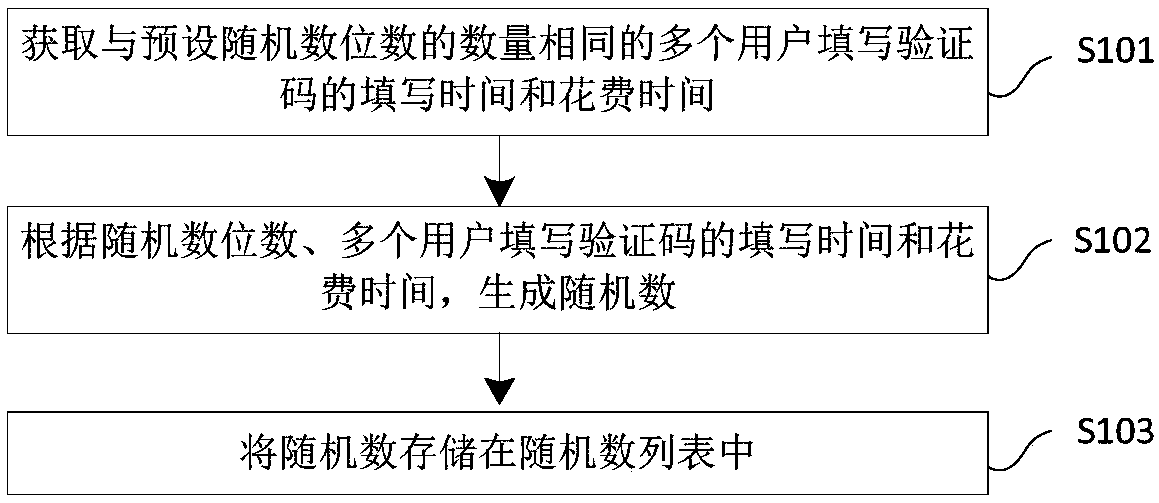
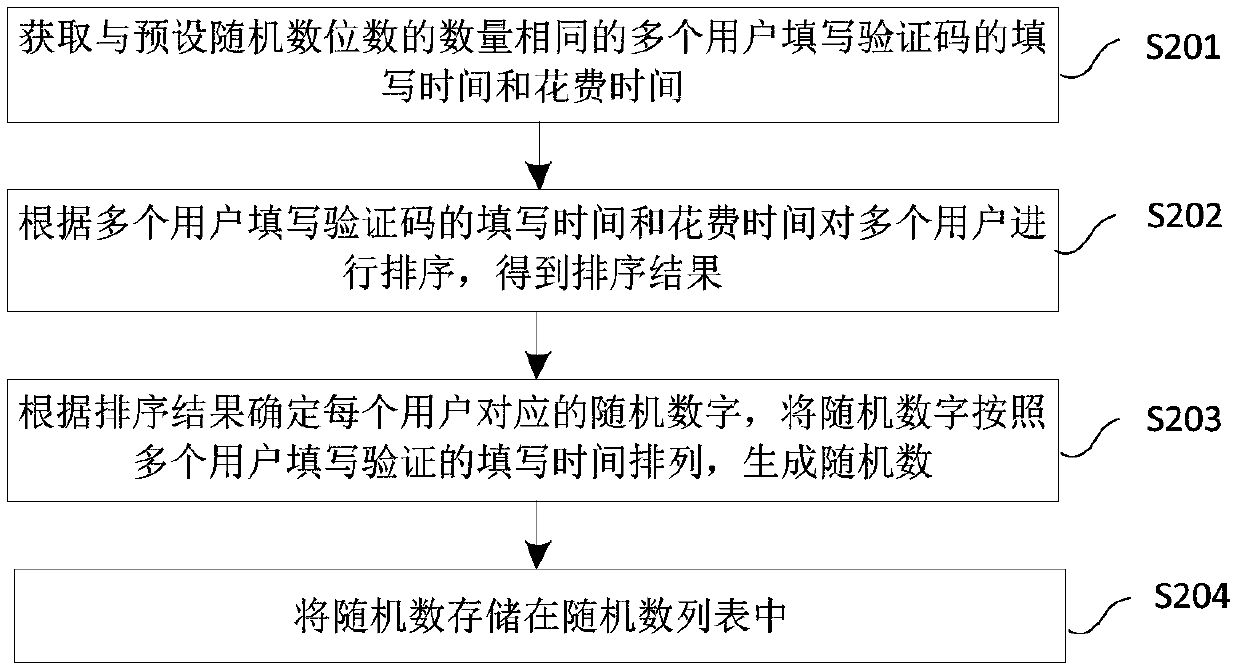
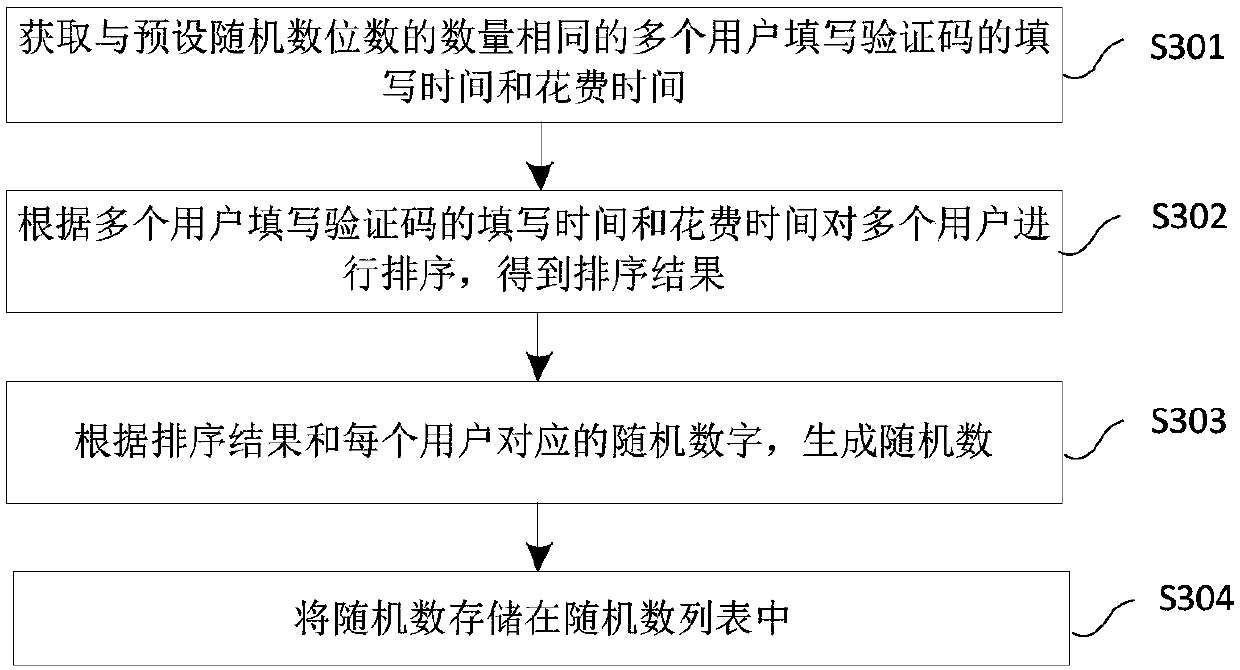
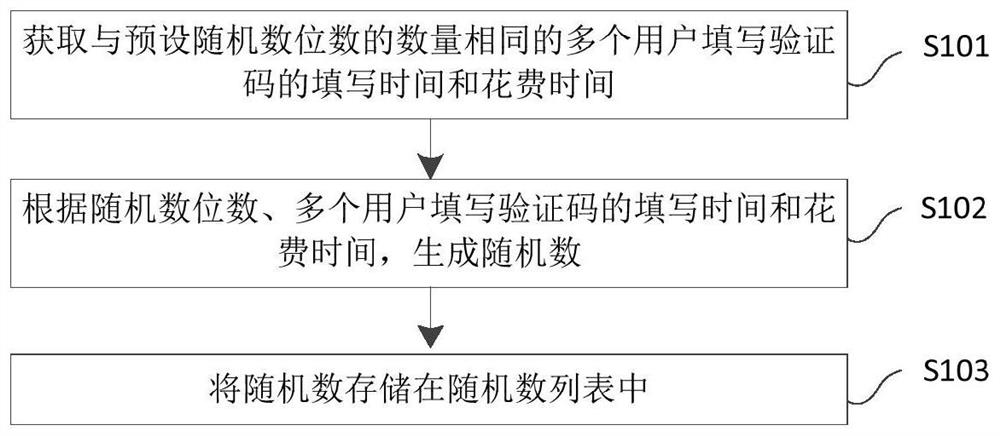
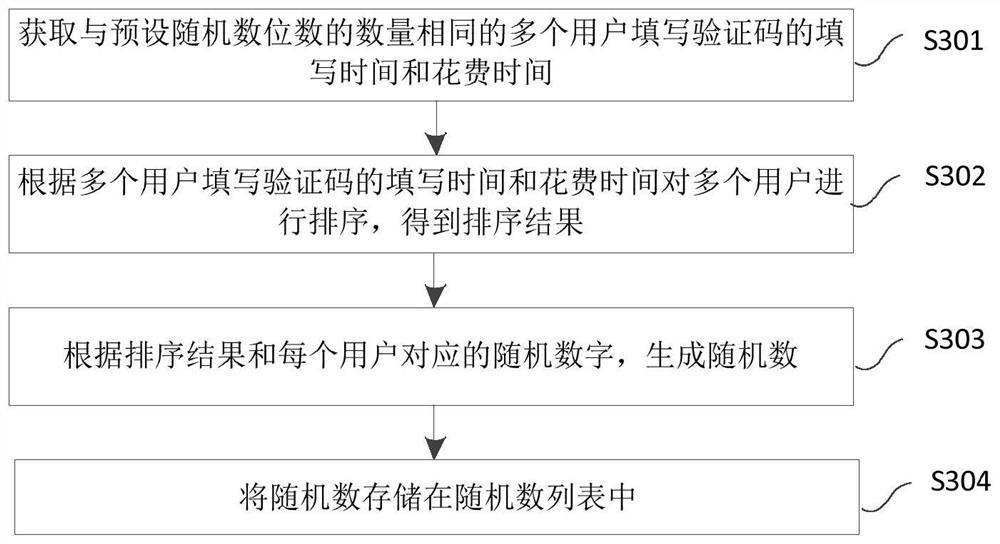
Random number generation method and device, and storage medium
The invention provides a random number generation method and device, and a storage medium. the method comprises the steps: obtaining the filling time and cost time of a plurality of users with the same number of preset random number digits for filling verification codes, and generating a random number according to the random number digits and the filling time and cost time of the plurality of users for filling the verification codes; And storing the random numbers in a random number list. The random number generated through the method is a true random number, has high random characteristics, and is suitable for an information security system with high requirements on the random number.
Owner:TAIKANG LIFE INSURANCE CO LTD
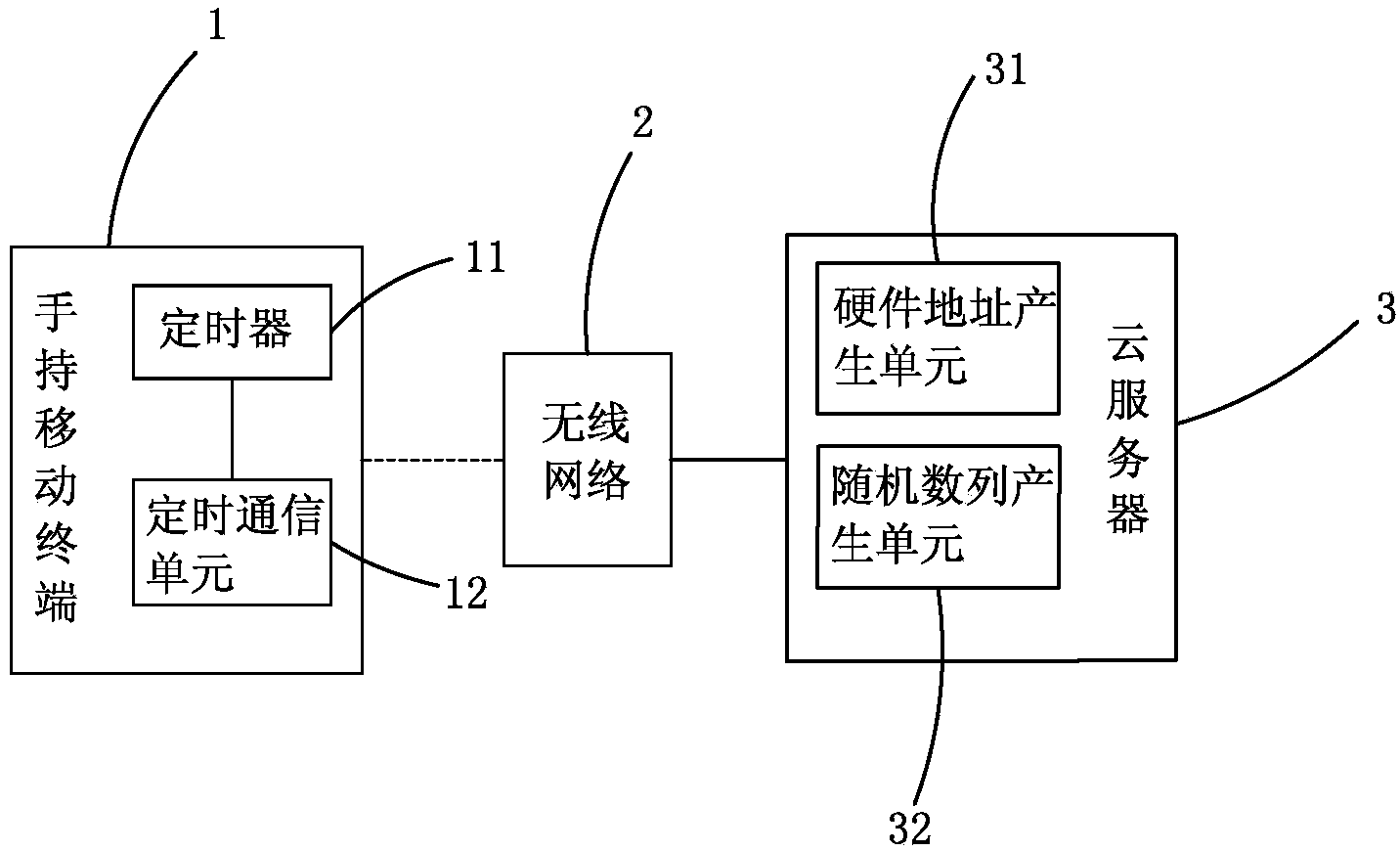
Data backup recovery and sharing system based on cloud server
InactiveCN103873589AEasy backup and restoreImprove visibilityTransmissionRedundant operation error correctionCommunication unitTerminal equipment
The invention provides a data backup recovery and sharing system based on a cloud server. The data backup recovery and sharing system is characterized in that a handheld mobile terminal device, a network and the cloud server are included, a handheld mobile terminal comprises a timer and a timing communication unit, the handheld mobile terminal device sends backup data to the cloud server through the wireless network regularly, and the cloud server is provided with a hardware address recognition unit and random series generating unit. According to the data backup recovery and sharing system based on the cloud server, the timer is arranged, the backup data can be automatically sent to the cloud server when the handheld mobile terminal is in idle, the backup data have a unique mark corresponding to the handheld mobile terminal, and the unique mark can be used as a code of recovery data. Meanwhile, the backup data of another handheld mobile terminal can be shared on the handheld mobile terminal. The backup recovery of the data is convenient, and the identification degree is high.
Owner:林鲁冰
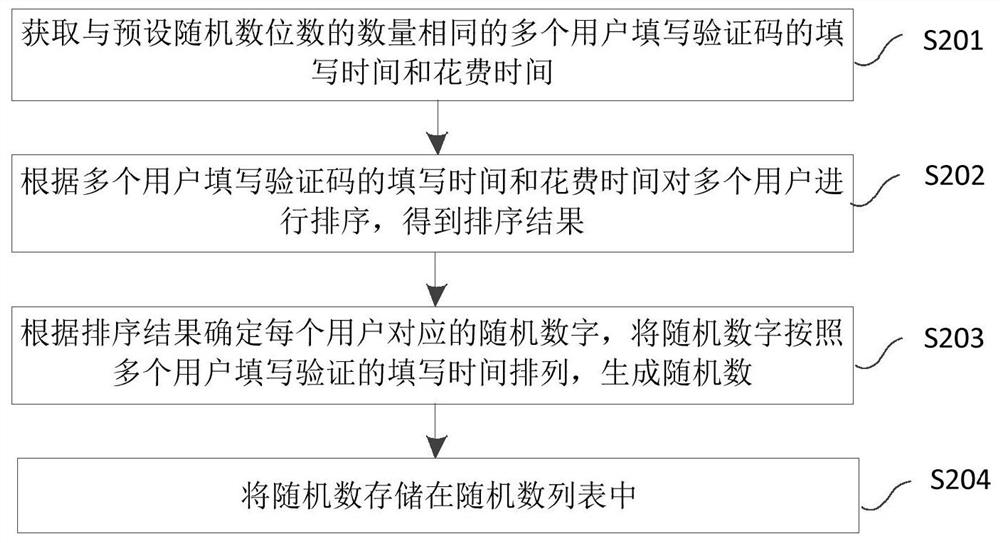
Random sequence generating method and device
The embodiment of the invention discloses a random sequence generating method and device. The random sequence generating method comprises the following steps: according to preset fitting precision, determining a definitional domain interval and definitional domain subintervals of a step function; in a mapping interval range, generating uniformly distributed random sequences; according to a preset mapping relation and the function values of the definitional domain subintervals of the step function, acquiring mapping subintervals corresponding to the definitional domain subintervals of the step function in the mapping interval range of the uniformly distributed random sequences; in the definitional domain subintervals of the step function, uniformly generating the random sequences according to the number of random numbers in the corresponding mapping subintervals. By the random sequence generating method, through fitting of probability density functions of random number sequences to be generated and through division from the existing random number sequences according to a preset mapping rule, the obtained random sequences not only conform to actually required distribution, but also can meet requirements of a large number theorem and a central limit theorem in a statistical sense.
Owner:CHINA MOBILEHANGZHOUINFORMATION TECH CO LTD +1
Method and apparatus for generating password of target event
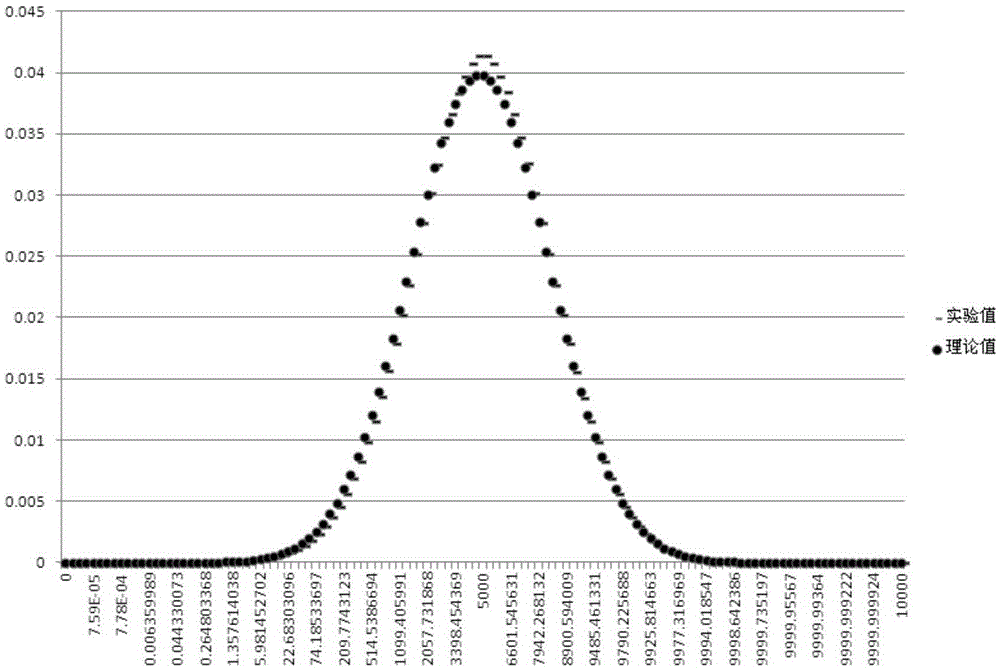
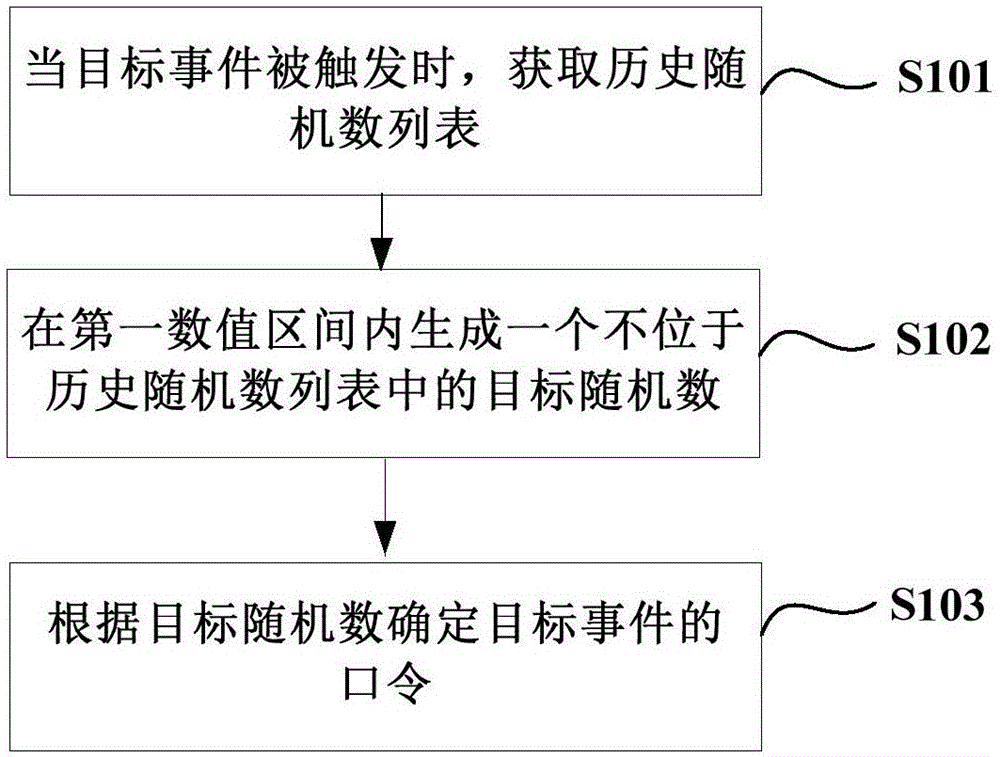
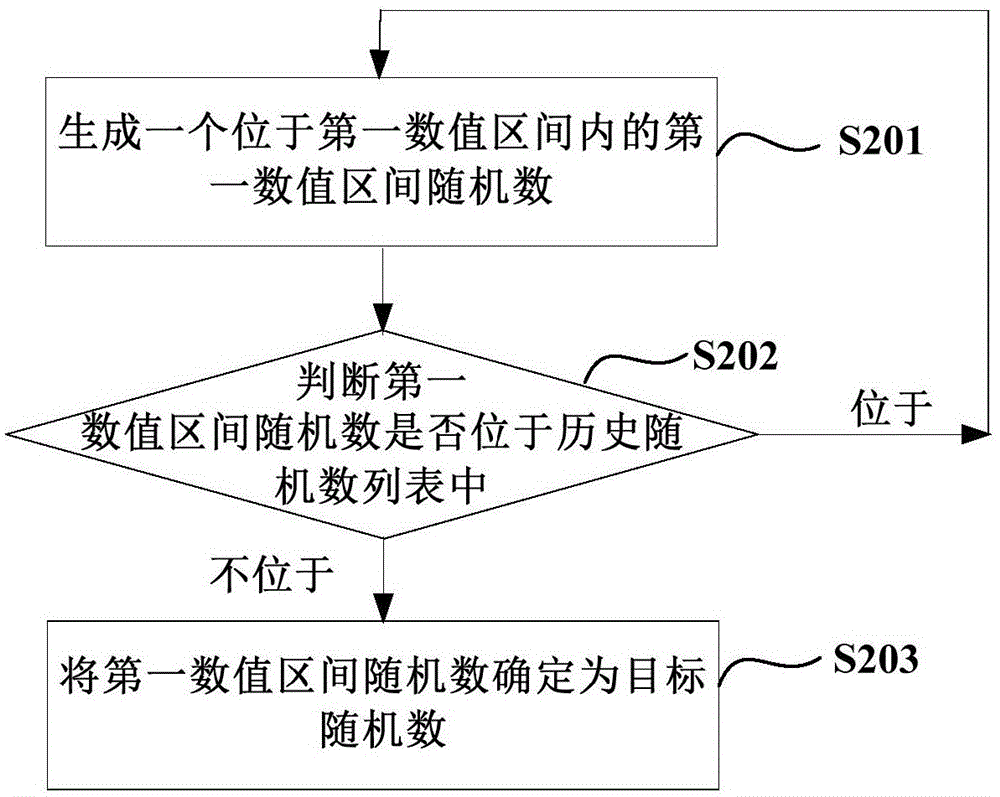
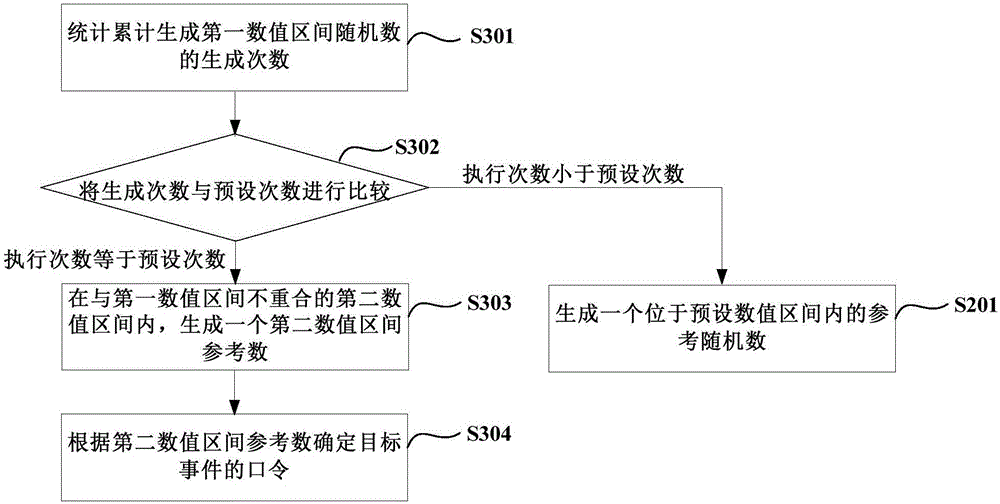
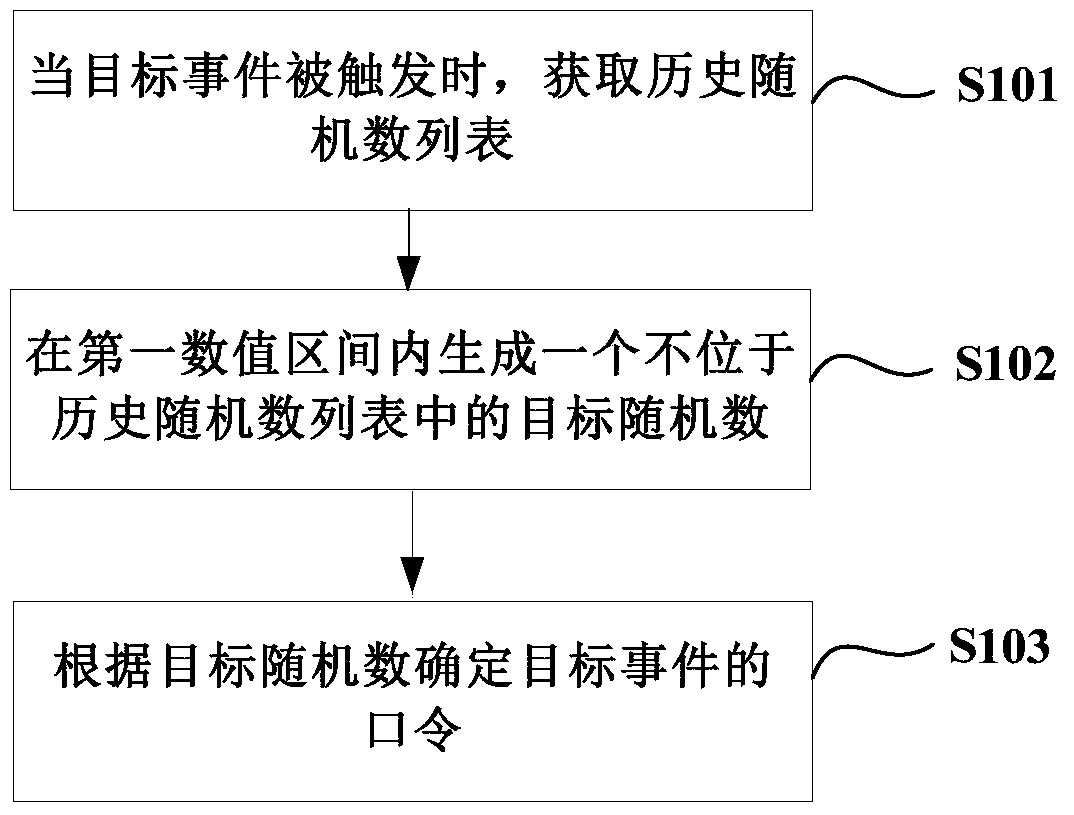
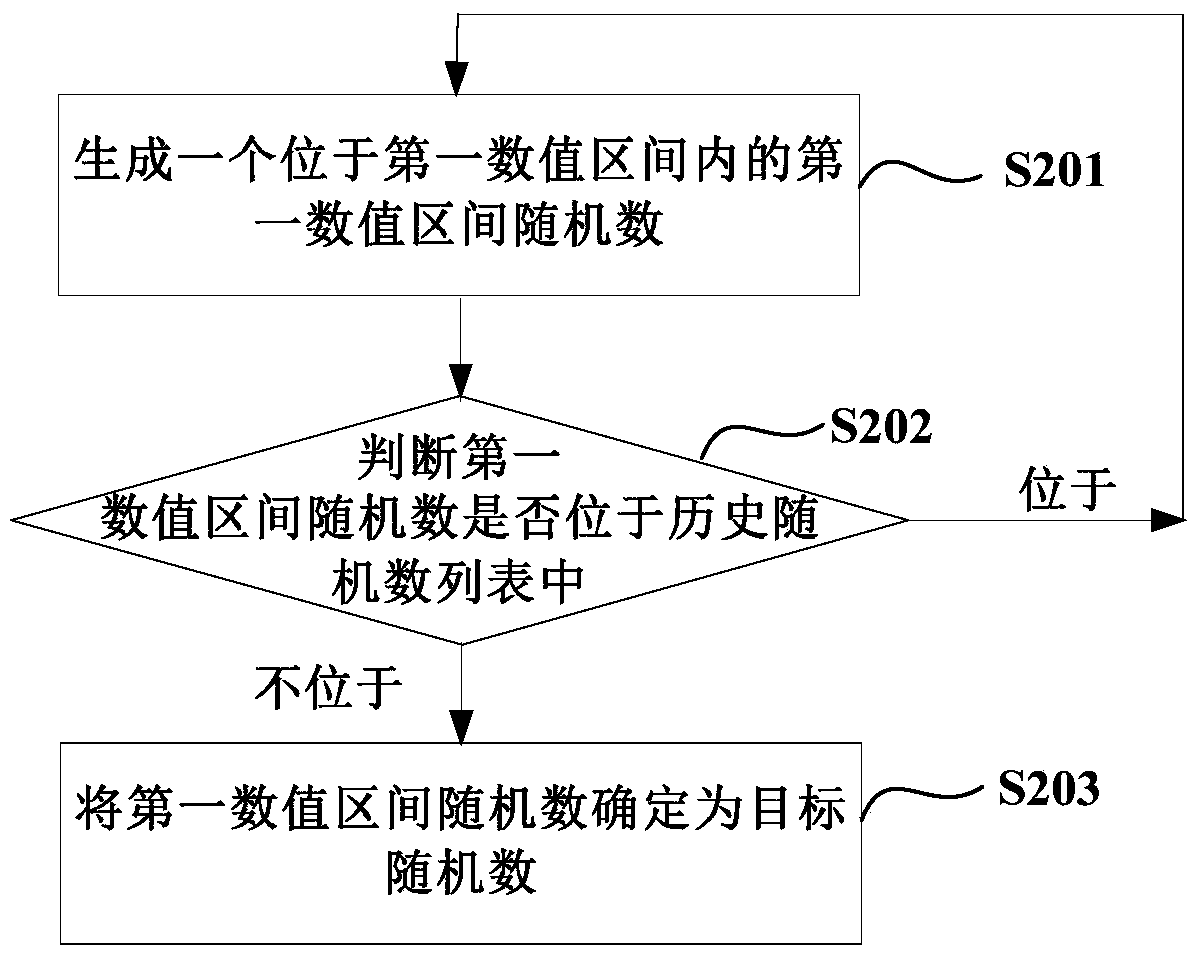
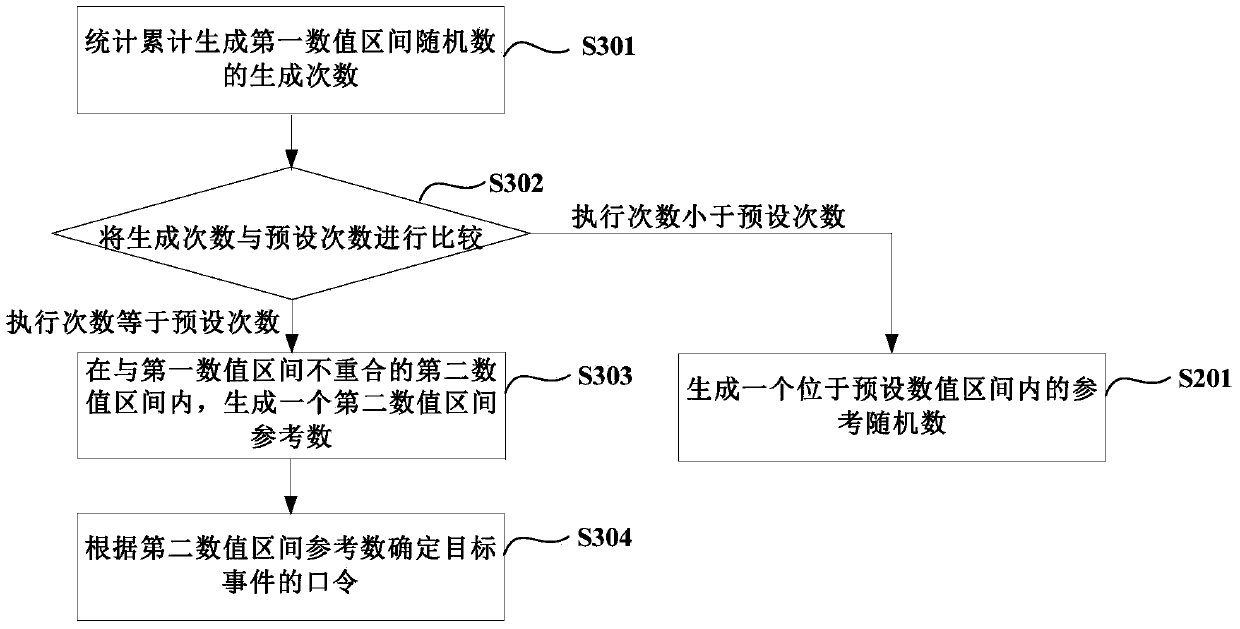
ActiveCN106470108AMultiple storage spacesUser identity/authority verificationPasswordComputer science
The invention relates to a method and apparatus for generating a password of a target event. The method includes: obtaining a historical random series list when the target event is triggered, wherein the historical random number list comprises random numbers corresponding to generated passwords; generating a target random number which is not located in the historical random number list in a first value interval; and determining the password of the target event according to the target random number. According to the method and apparatus, the generation of a lot of different random numerical values in advance is not needed so that the occupation of a lot of time due to the generation of a lot of different random numerical values in advance is prevented; and the generated random numerical values in advance does not need to be stored in a local manner so that the occupation of much local storage space is avoided.
Owner:ADVANCED NEW TECH CO LTD
Ultrasound excitation method for eliminating robot ultrasound ranging system interference
InactiveCN101271154BAvoid crosstalkShort durationGenetic modelsAcoustic wave reradiationSonificationObstacle avoidance
An ultrasonic excitation method for eliminating the crosstalk of a robot ultrasonic ranging system adopts the pseudo-random pulse position modulation mode for constructing a sole transmitting sequence for each ultrasonic transducer and uses the genetic optimization algorithm for optimizing the time interval between the adjacent pulses in the pseudo-random pulse position modulation sequence, thus allowing the duration of the transmitting sequence of each ultrasonic transducer to be 1.5 to 2ms. The ultrasonic excitation method comprises the following steps: 1. a string of pulse signals X are generated; 2. K groups of different pseudo-random series Psij are generated; 3. the pulse positions in the pulse signals X are respectively modulated by using the K groups of pseudo-random series, thus obtaining K groups of pseudo-random pulse position modulation sequences; 4. the best pseudo-random pulse position modulation sequence of the K groups is obtained; 5. K groups of ultrasonic transducers are respectively excited. The ultrasonic excitation method can lead each ultrasonic transducer to have the sole transmitting sequence, thus fundamentally avoiding the occurrence of the crosstalk; the real-time requirement of the robot navigation can be ensured; the working efficiency of a robot ultrasonic obstacle avoidance system can be effectively improved; and the reliability of the robot ultrasonic obstacle avoidance system can be greatly improved.
Owner:TIANJIN UNIV
reversible random number generator
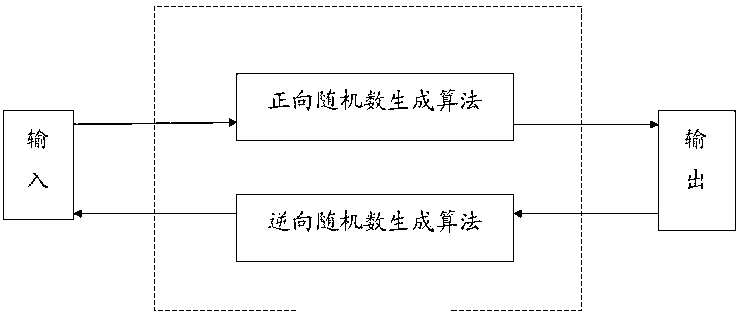
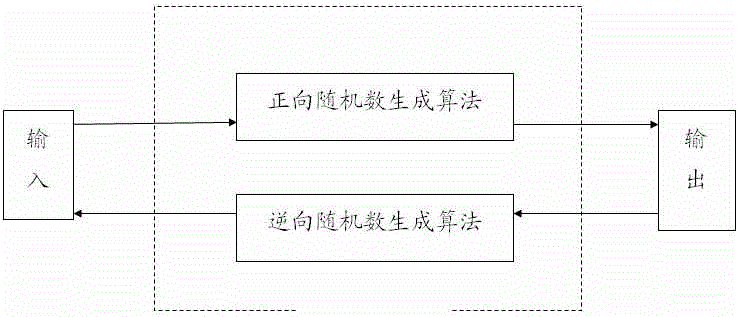
The invention discloses a reversible random number generator, being one of a reversible generator based on a memory, a uniformly distributed reversible generator and reversible generators in other distribution manners. The reversible random number generator has the advantages that a random number sequence can be generated by virtue of a forward random number generation algorithm, the random number sequence can be pushed back by virtue of a reverse random number generation algorithm according to the currently output random number, performance is excellent, and working effect is good.
Owner:NANTONG INST OF TECH
Method for eliminating interaction of pseudo-random series fill in OFDM modulation system
The invention is an iterative echo elimination method. The method includes steps: based on known pulse response of channel (PRCH) at previous two frames, using linear interpolation obtains PRCH at current and next frames; after synchronization of receiver, obtaining pseudo random sequence of current frame and next frame as well as result of convolution between the said pseudo random sequence and corresponding PRCH; removing the said convolution from signal in Ith frame, the receiver obtains convolution between data in Ith frame equivalent to zero filled system and PRCH; using method of time-domain filtering and decision directed feedback removes items of interference and noise between residue codes, and updates estimated value of channel in each frame till presetting iterations. Computer simulation indicates that raising efficiency of spectrum greatly without losing performance of error code. The invention is still valid if single frequency network with large time delay.
Owner:TSINGHUA UNIV
A method and device for generating a password for a target event
The invention relates to a method and apparatus for generating a password of a target event. The method includes: obtaining a historical random series list when the target event is triggered, wherein the historical random number list comprises random numbers corresponding to generated passwords; generating a target random number which is not located in the historical random number list in a first value interval; and determining the password of the target event according to the target random number. According to the method and apparatus, the generation of a lot of different random numerical values in advance is not needed so that the occupation of a lot of time due to the generation of a lot of different random numerical values in advance is prevented; and the generated random numerical values in advance does not need to be stored in a local manner so that the occupation of much local storage space is avoided.
Owner:ADVANCED NEW TECH CO LTD
Device area provable security verification method against collusion attack
The invention discloses an equipment area provable security verification method with resistance to collusion attack and mainly solves the problem of absence of a security verification method with areas as credential information in existing position-based cryptography technologies. The implementation scheme of the method comprises steps as follows: a provable security verification model is built, and a prover is located in a target area; verifiers select information sources and random series and share information with one another, and the verifiers replay information in a broadcasting manner; a metric value is generated by the prover, and a verification value is calculated, and position information of the prover is broadcasted; the verifiers verify correctness of the verification value, whether the position information of the prover is accepted is judged, if the verification value passes the verification, the position information of the prover is broadcasted, otherwise, the verification value does not pass the verification, that is, the position claimed by the prover is not in the area, and the verification is finished. According to the method, any prover in the target area can effectively resist the collusion attack of multiple opponents after verification, and the security verification of the position of the prover is realized. The method can be used for verifying whether the equipment, namely, the prover, is located in the target area.
Owner:XIDIAN UNIV
Recognition code transmission method and circuit arrangement
A device for controlling the transmission of ID code on RF recognition label is composed of a timing circuit, a working region selector consisting of a counter, a random numeral generator and a comparator for comparing the counter's value with the output of random numeral generator to povide an enable signal if they are matched, and a memory for storing the ID code and outputting it when said enable signal is received. It can prevent the collision between labels.
Owner:HOLTEK SEMICON
Reversible random number generator
InactiveCN106201434AImprove performanceImprove work performanceRandom number generatorsNumber generatorPseudorandom number generator
The invention discloses a reversible random number generator, being one of a reversible generator based on a memory, a uniformly distributed reversible generator and reversible generators in other distribution manners. The reversible random number generator has the advantages that a random number sequence can be generated by virtue of a forward random number generation algorithm, the random number sequence can be pushed back by virtue of a reverse random number generation algorithm according to the currently output random number, performance is excellent, and working effect is good.
Owner:NANTONG INST OF TECH
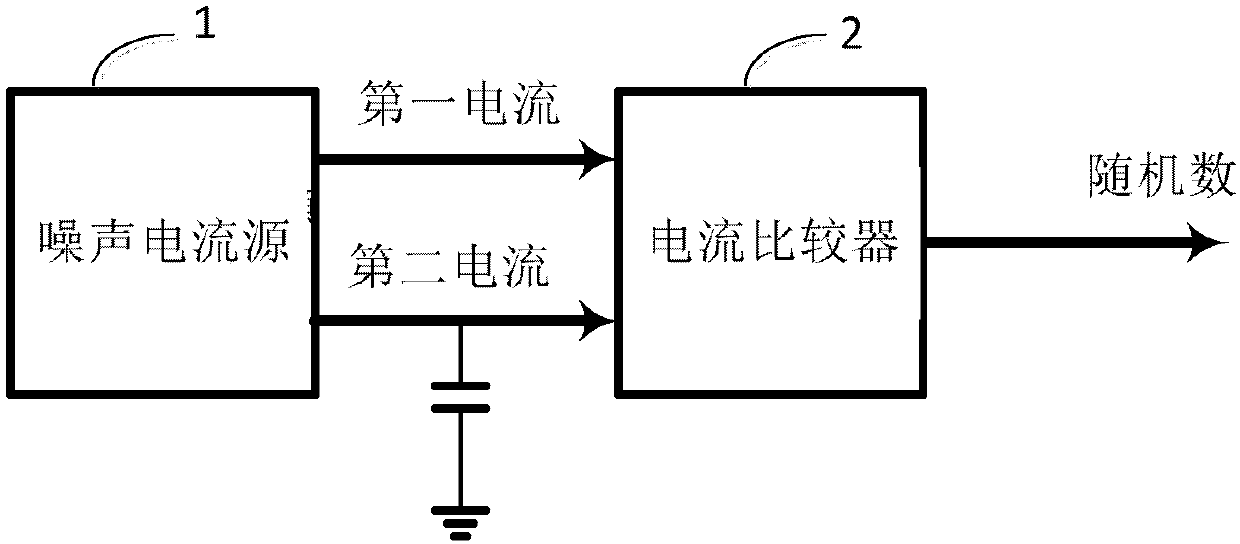
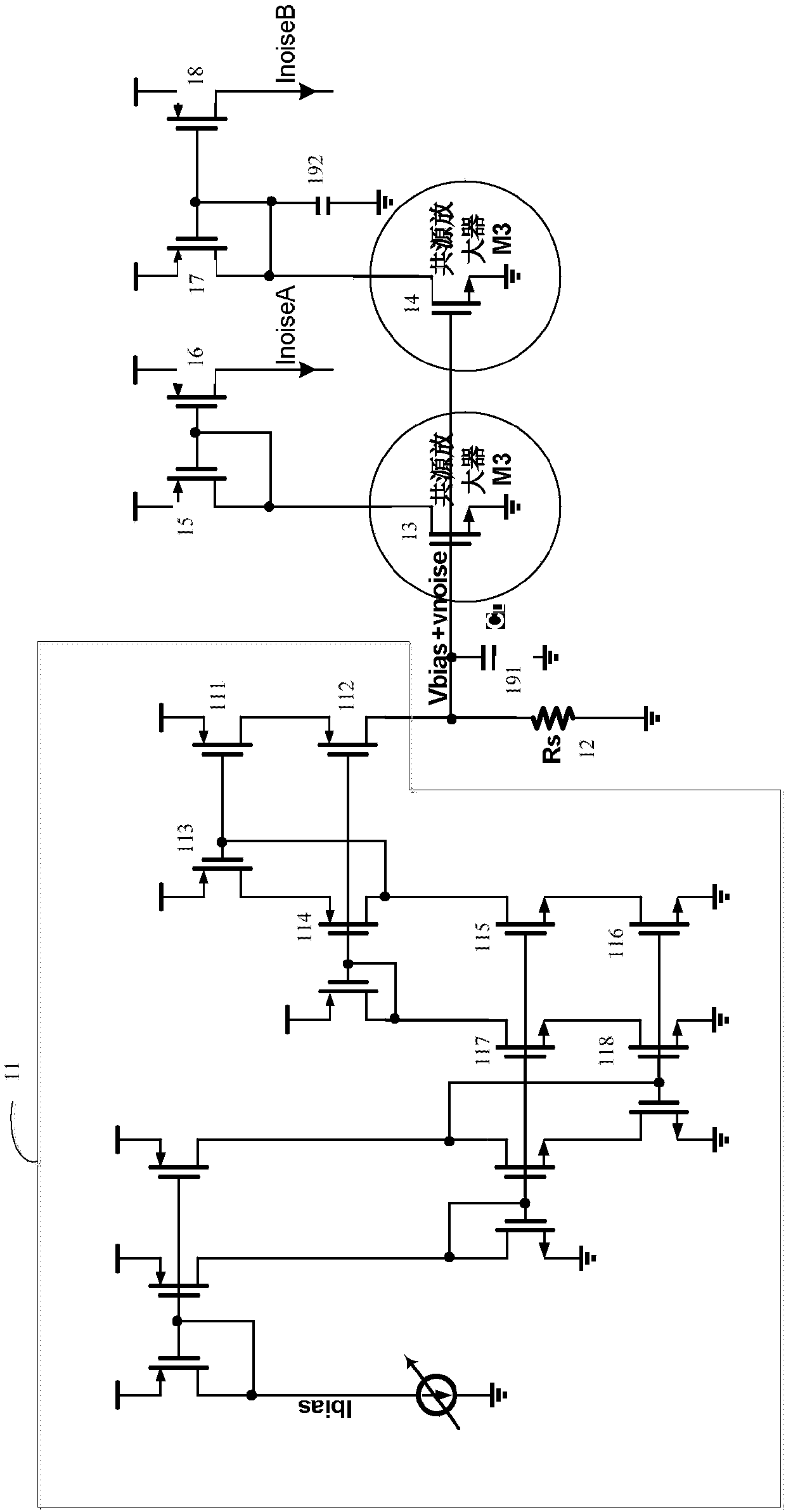
Noise type random number generator
The present invention provides a noise type random number generating device, the noise current source includes: a cascode current source, a resistor, a first common source amplifier, a first mirror, a first CMOS transistor, a second CMOS transistor, a first Three CMOS tubes, a fourth CMOS tube, a first capacitor and a second capacitor; the grid of the first CMOS tube is connected to the grid of the second CMOS tube, so that the drain of the second CMOS tube outputs the first current; the third The gate of the CMOS transistor is connected to the gate of the fourth CMOS transistor, so that the drain of the fourth CMOS transistor outputs the second current. The drain of the second CMOS transistor and the drain of the fourth CMOS transistor are respectively connected to the current comparator, so that the first current and the second current respectively flow into the current comparator to obtain a random number sequence. This increases the rate at which random numbers are generated.
Owner:DATANG MICROELECTRONICS TECH CO LTD
Method for embedding digital watermark
InactiveCN1148961CImprove robustnessTelevision system detailsColor television detailsMultimedia signal processingDocumentation
The digital wat remark technique based on a wavelet transform is a method for protecting multi media video data, belonging to the multi media signal processing area. First, number of stages of analyzed wavelet is selected, and the multi media data are analyzed by use of the wavelet transform. Then, some of the wavelet coefficients are selected. The watermark is embedded in the domain of the wavelet transform. Finally, the video data with the watermark embedded are obtained through the inverse wavelet transform. Naked eyes can not distinguish between the original video data and the video data with the watermark embedded. The digital watermark provides a means for distinguishing the said problem. The watermark can be any meaningful digital file or meaningless random series. The invention protects video data or files transferred on networks.
Owner:SUN YAT SEN UNIV
Random number generation method, device and storage medium
The invention provides a random number generation method and device, and a storage medium. the method comprises the steps: obtaining the filling time and cost time of a plurality of users with the same number of preset random number digits for filling verification codes, and generating a random number according to the random number digits and the filling time and cost time of the plurality of users for filling the verification codes; And storing the random numbers in a random number list. The random number generated through the method is a true random number, has high random characteristics, and is suitable for an information security system with high requirements on the random number.
Owner:TAIKANG LIFE INSURANCE CO LTD
Pseudo-random series producing method for use in Markov paging test
InactiveCN1252952CResolve synchronizationSynchronization is simpleCode division multiplexRadio/inductive link selection arrangementsLogical operationsExclusive or
The base station stores the electric serial number sent by the mobile station. The base station takes the current GPS time every 20 ms. The 'exclusive or' logic operation is carried out between the absolute time obtained and the 32 digits set up at the mobile station. Whether the low 9 digits of the value of result with logic operation being executed is identical to the low 9 digits of the serial number or not is determined. If yes, the low 31 digits of the said value of result are assigned as the status value of the pseudo random sequence storage. Then, from the preset formula, the current status value of the pseudo random sequence storage is calculated and the Markov data frame utilized for link test is generated. The invented method solves the synchronization issue of generating pseudo random sequence and makes the statistics of the error frame rate of the force inverted link as well as monitors its quality.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com