Device area provable security verification method against collusion attack
A security verification and anti-collusion technology, applied in the field of network security, can solve problems such as unsatisfactory security, lack of password verification methods, and failure to consider security issues, etc., to achieve high security effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
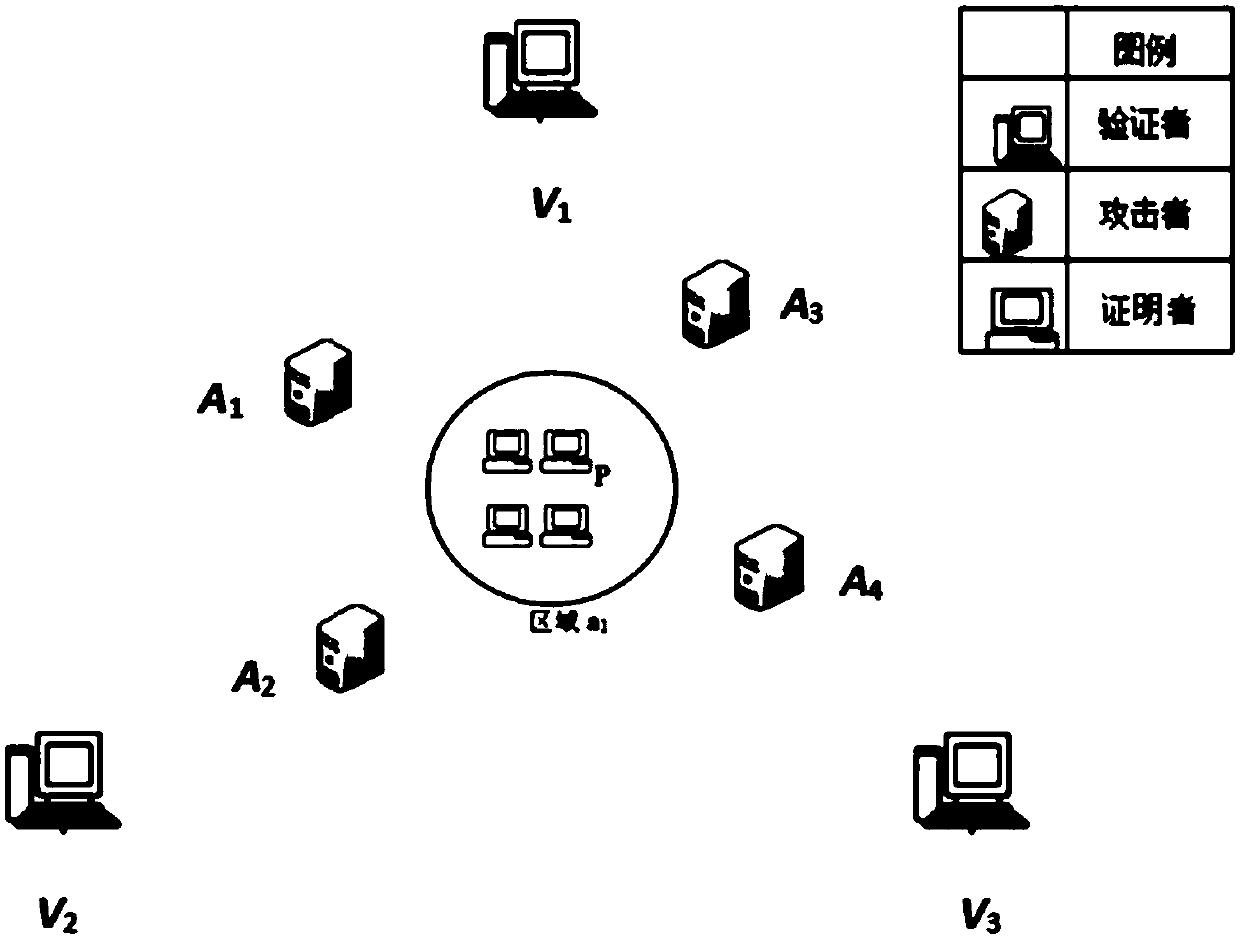
[0047] With the development of the Internet and mobile communication technologies, location information has become increasingly important, and secure location verification is essential. The current existing research technologies mainly include positioning based on network technology, wireless security positioning and location verification, security distance constraint technology and positioning technology based on location cryptography, but the positioning technology based on network technology does not consider the security of positioning in the environment where attacks exist. Problem; the protocol scheme given by wireless security positioning and location verification does not satisfy the provable security under collusion attack, and can only resist the attack of single or non-collusion two attackers; the safety distance constraint can only verify whether the verified person is Within a certain distance, it cannot help to verify the specific location of the prover; location-...
Embodiment 2
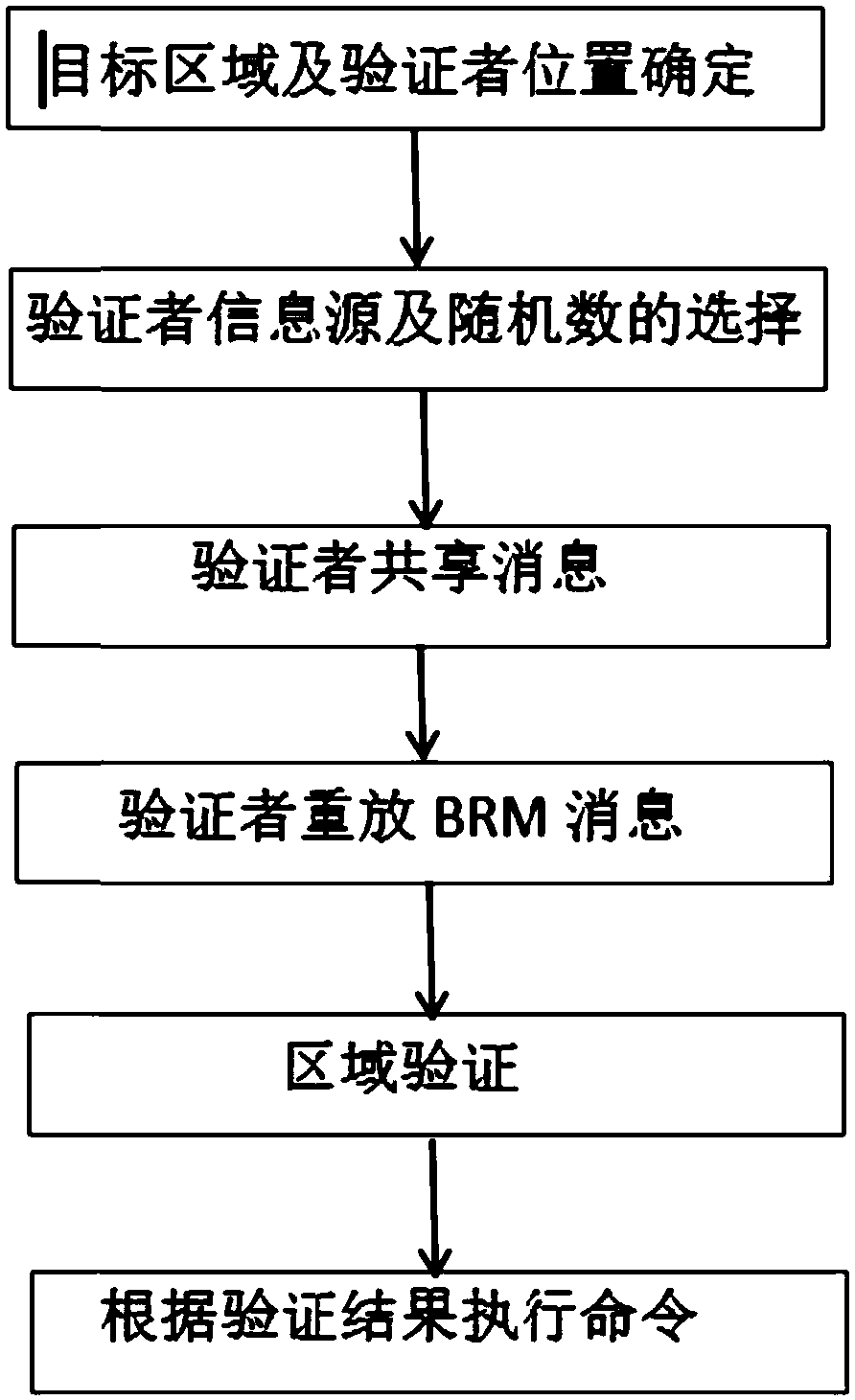
[0066] The device area verifiable security verification method against collusion attack is the same as that of Embodiment 1, wherein the verifier message sending process in step (4), the specific steps are as follows:
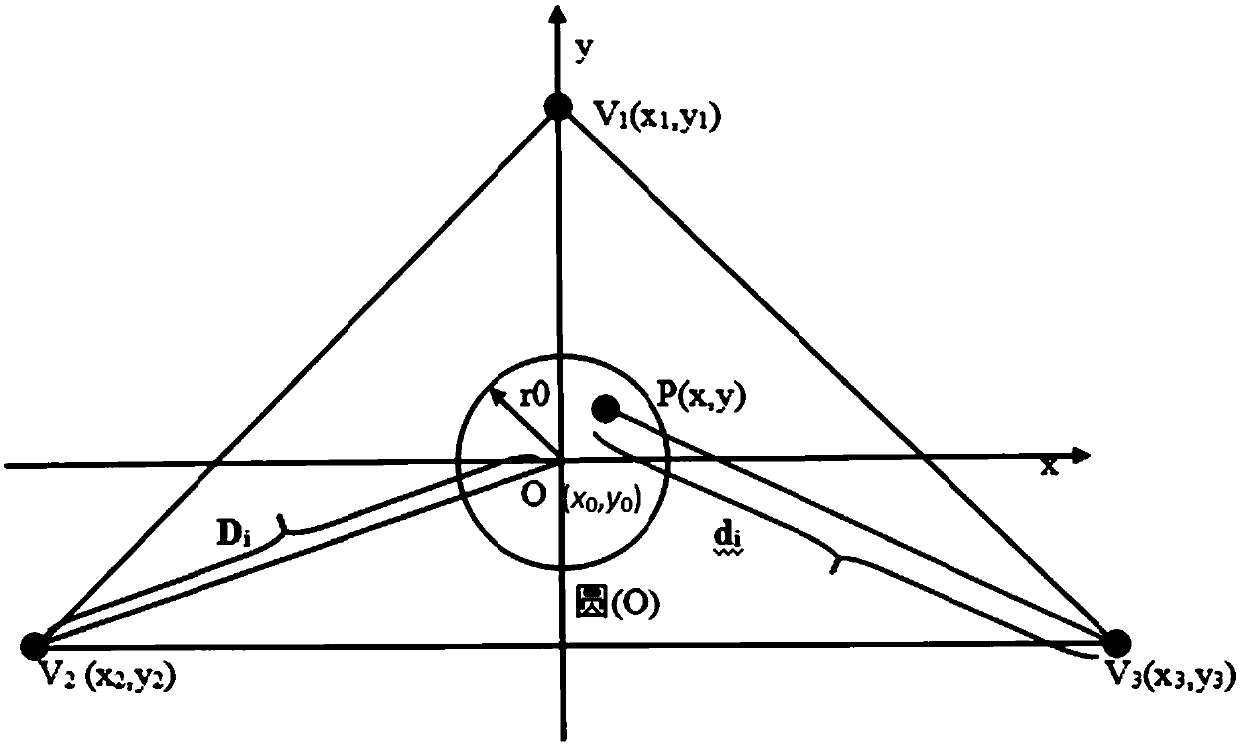
[0067] (4a) Let the verifier V 1 , V 2 , V 3 The first message sent arrives at the center of the circle O at time T at the same time, O(x 0 ,y 0 ) represents the coordinates of the center of the circle, and the second message arrives at O simultaneously at time T', where T'=T+Δt, Δt=2r 0 / v,r 0 represents the radius of the circle of the target area, v represents the verifier sending the message at the speed of radio waves;
[0068] (4b) The distance between the verifier and the center of the circle O is different, and the message needs to reach the center of the circle at the same time, so the verifier V i The moment of sending the message is different, let V 1 , V 2 , V 3 The time to send the first message is T respectively 1 , T 2 , T 3 Indicate...
Embodiment 3
[0077] The device area verifiable security verification method against collusion attack is the same as that of Embodiment 1, wherein in step (5), the prover P receives all the verifiers V i The first message M sent i time t i , and the prover P receives all the validators V i The second message M sent i ' time t i ' is calculated as follows:
[0078] t 1 =T 1 +d 1 / v,t 1 '=t 1 +Δt;
[0079] t 2 =T 2 +d 2 / v,t 2 '=t 2 +Δt;
[0080] t 3 =T 3 +d 3 / v,t 3 '=t 3 +Δt;
[0081] d 1 , d 2 , d 3 represents the validator V 1 (x 1 ,y 1 ), V 2 (x 2 ,y 2 ), V 3 (x 3 ,y 3 ) is the distance from the prover P(x,y).
[0082] The first message and the second message sent by the verifier are sent in the form of broadcast. Because the prover is in the circular area, the prover can receive all the messages sent by each verifier. The time when the prover in the area receives each message is equal to the time when the verifier sends the message plus the time it take...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com