Connection keyword authentication searchable encryption method based on national cryptographic algorithm
A national secret algorithm and encryption method technology, which is applied in the field of domestic password keyword encryption, can solve the problems of system security impact and search efficiency reduction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
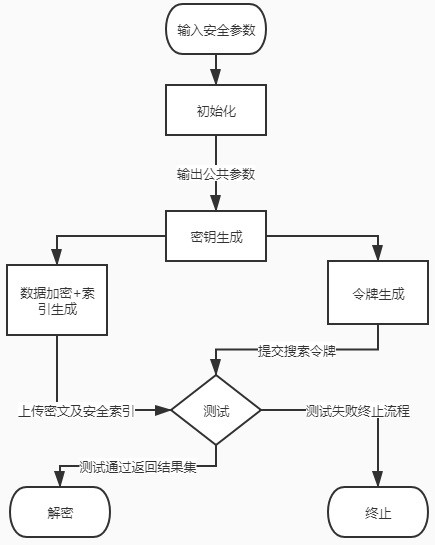
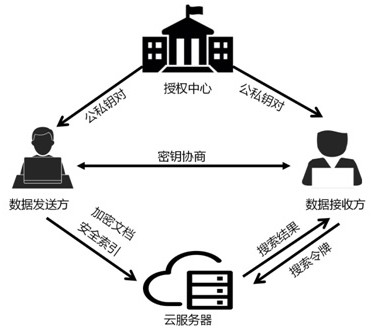
[0040] The present invention is described in further detail now in conjunction with accompanying drawing.
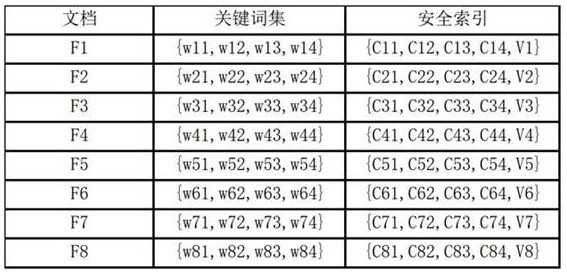
[0041] In order to succinctly express the relationship between the document-keyword set-security index in the present invention, the relationship among the three is listed in Table 1 below.
[0042] Table 1
[0043]
[0044] Concrete steps of the present invention are:
[0045] Step 1: Initialization algorithm: the authorization center inputs security parameters, runs the initialization algorithm, and generates two prime numbers q order cyclic group , and the bilinear map , where e needs to satisfy the following three properties:
[0046] (1) Bilinear: for any element , any element ,Have , in is the group of integers modulo q;
[0047] (2) Non-degenerate: if ,in , then there is ,Right now ;
[0048] (3) Computability: There is an effective algorithm for any element , can be calculated ;
[0049] Step 1.2: Authorization center selects group...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com