Identity-based dual-server authorization ciphertext equivalence judgment method
A dual-server, determination method technology, applied in the field of information security cryptography, can solve problems such as difficulty in resisting keyword guessing attacks, and achieve the effect of solving the burden of public key certificate management and resisting keyword guessing attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] Embodiments of the present invention are described in detail below, examples of which are shown in the drawings, wherein the same or similar reference numerals designate the same or similar elements or elements having the same or similar functions throughout. The embodiments described below by referring to the figures are exemplary and are intended to explain the present invention and should not be construed as limiting the present invention.
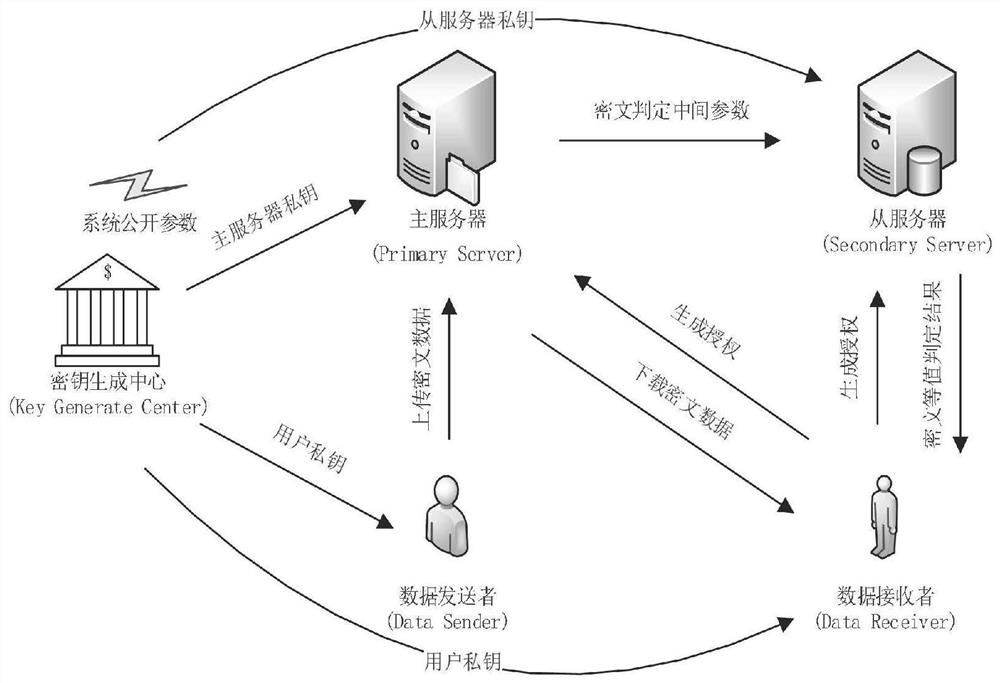
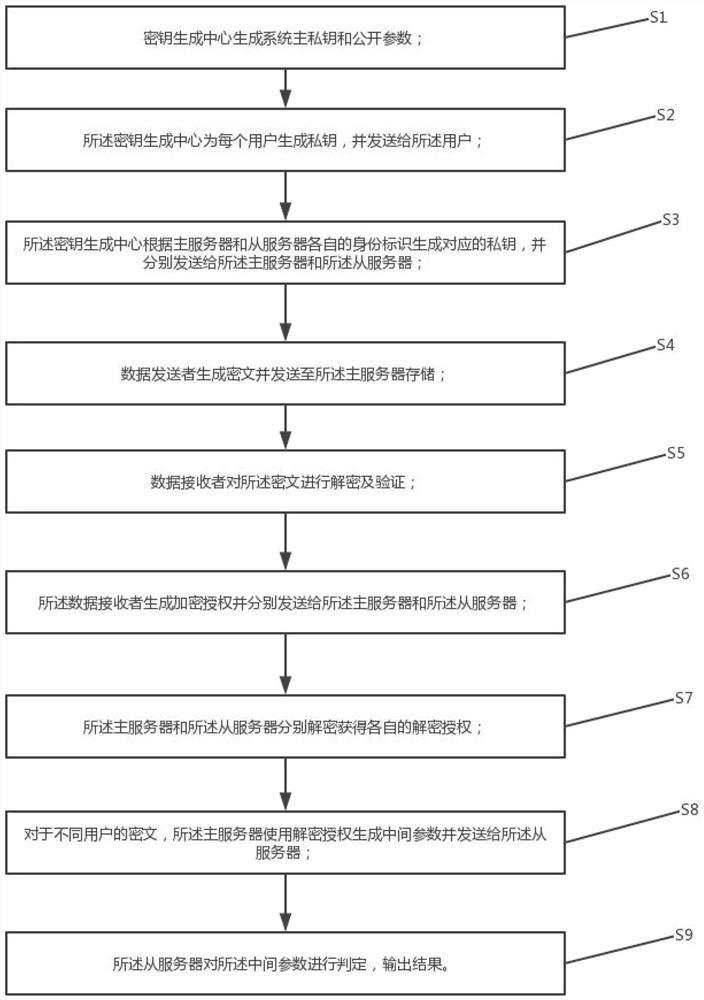
[0030] see figure 1 , the present invention proposes an identity-based dual-server authorization ciphertext equivalence determination method. The system architecture and technical terms are described as follows:
[0031] (1) Key Generate Center (KGC): As a system trusted entity, it is responsible for initializing the system, generating system public parameters, system master private key, user private key, and master and slave server private keys.
[0032] (2) Data Sender: According to the public parameters of the system and the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com