Double-server multi-user searchable encryption method and device capable of resisting keyword guessing attack
A dual-server, encryption method technology, applied in the field of information security, can solve problems such as low security and inability to resist keyword defects, and achieve the effects of reducing burden, reducing search time complexity, and resisting guessing attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
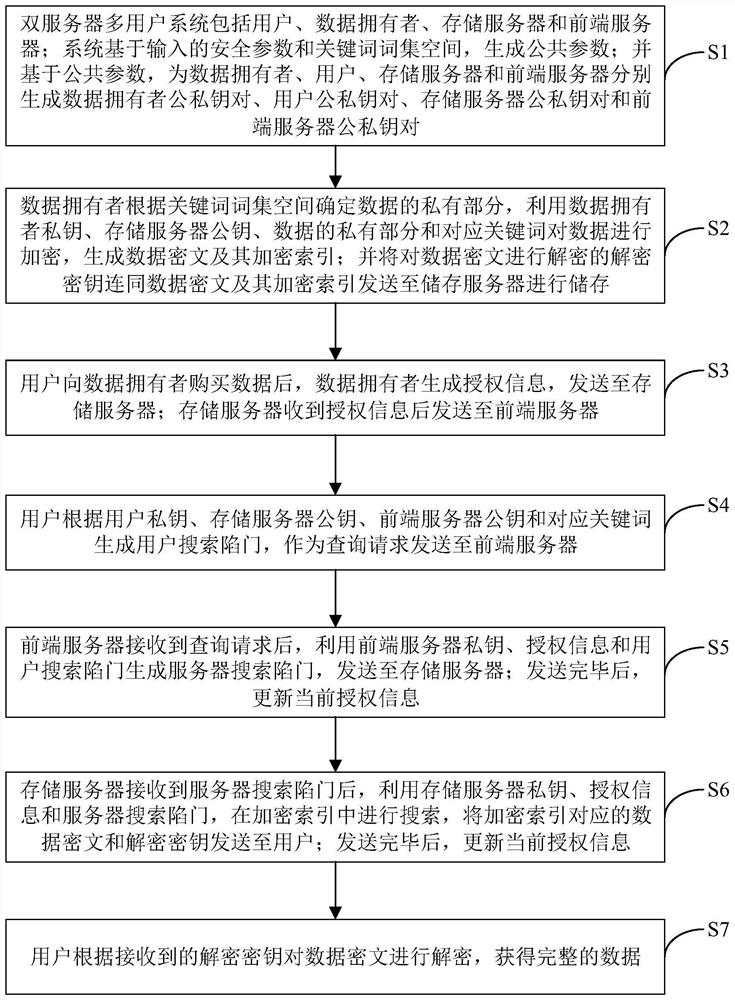
[0064] This embodiment provides a dual-server multi-user searchable encryption method that resists keyword guessing attacks, such as figure 1 shown, including:
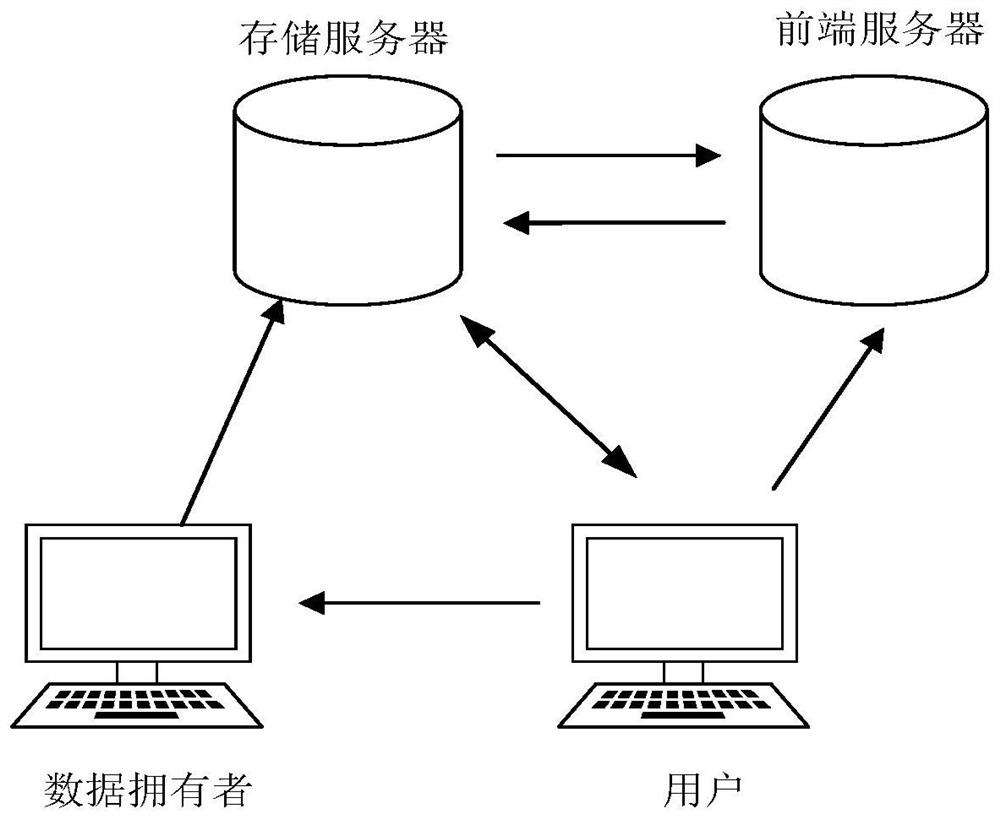
[0065] S1: The dual-server multi-user system includes users, data owners, storage servers and front-end servers; the system generates public parameters based on the input security parameters and keyword word set space; The server and the front-end server respectively generate the data owner public-private key pair, the user public-private key pair, the storage server public-private key pair, and the front-end server public-private key pair;
[0066]S2: The data owner determines the private part of the data according to the keyword word set space, encrypts the data with the private key of the data owner, the public key of the storage server, the private part of the data and the corresponding keywords, and generates the data ciphertext and its encrypted index ; Send the decryption key for decrypting the data ciphertext...
Embodiment 2
[0074] This embodiment provides a dual-server multi-user searchable encryption method that resists keyword guessing attacks, including:
[0075] S1: The dual-server multi-user system includes users, data owners, storage servers, and front-end servers; the system generates public parameters based on the input security parameters and keyword word set space; The server and the front-end server respectively generate the data owner's public-private key pair, the user's public-private key pair, the storage server's public-private key pair, and the front-end server's public-private key pair; the details are:
[0076] System input-based safety parameters1 λ and keyword vocabulary space Generate public parameters, denoted as in, respectively represent the first, second and third multiplicative cyclic groups, all of which are of order q; g 1 ,g 2 Represent the first and second method cyclic group generators respectively; e represents the bilinear mapping: H 1 ,H 2 ,H 3 repr...
Embodiment 3
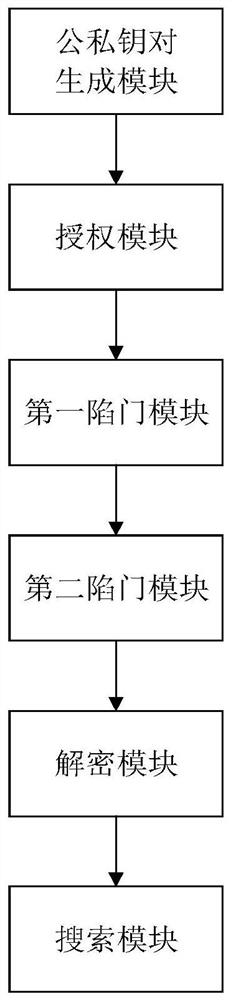
[0110] This embodiment provides a dual-server multi-user searchable encryption device that resists keyword guessing attacks, based on the searchable encryption method described in Embodiment 1 or 2, such as image 3 shown, including:
[0111] The public-private key pair generation module, the dual-server multi-user system includes users, data owners, storage servers and front-end servers; the system generates public parameters based on the input security parameters and keyword word set space; and based on the public parameters, it is the data owner. , the user, the storage server and the front-end server respectively generate the data owner's public-private key pair, the user's public-private key pair, the storage server's public-private key pair and the front-end server's public-private key pair;
[0112] Encryption module, the data owner determines the private part of the data according to the keyword word set space, and encrypts the data by using the private key of the data...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com