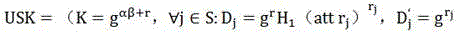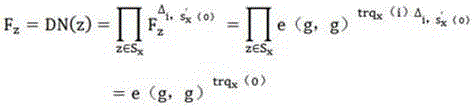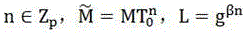Keyword search algorithm based on attribute encryption in cloud computing
A technology of keyword search and attribute encryption, which is applied in the field of cloud storage, can solve the problems of keyword guessing attacks and insufficient consideration of channel security, etc., and achieve good anti-collusion, flexible multi-user access control, and guarantee channel security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0008] 1. The principle of this algorithm
[0009] The basic theory that the present invention adopts is the principle of bilinear mapping and represents the access structure with its access tree, so first introduce bilinear mapping and access structure control:
[0010] 1. Bilinear mapping:
[0011] Let G and G T is a group of order p (p is a prime number), g is the generator of G, and there is an effectively computable bilinear map e between them: G×G→G T , with the following properties in the map:
[0012] (1) Bilinear, a, b∈Z p and g, h∈G, satisfying e(g a , h b ) = e(g, h) ab
[0013] (2) Non-degenerate, e(g, h)≠1
[0014] (3) Computability, g, h∈G, e(g, h) are all efficiently computable
[0015] (4) DBDH problem, g is the generator z∈Z of G p , g a , g b , g s , e(g,g) cannot be distinguished in polynomial time abs with e(g,g) z
[0016] (5) CDH problem, g is the generator of G, random a, b∈Z p , g a , g b cannot compute g in polynomial time ab .
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com