Identity verification method for resisting password-guessing replay attack
A technology of replay attack and authentication information, applied in the field of authentication against password guessing replay attacks, it can solve the problems of password leakage, forgetting password, improving and so on.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
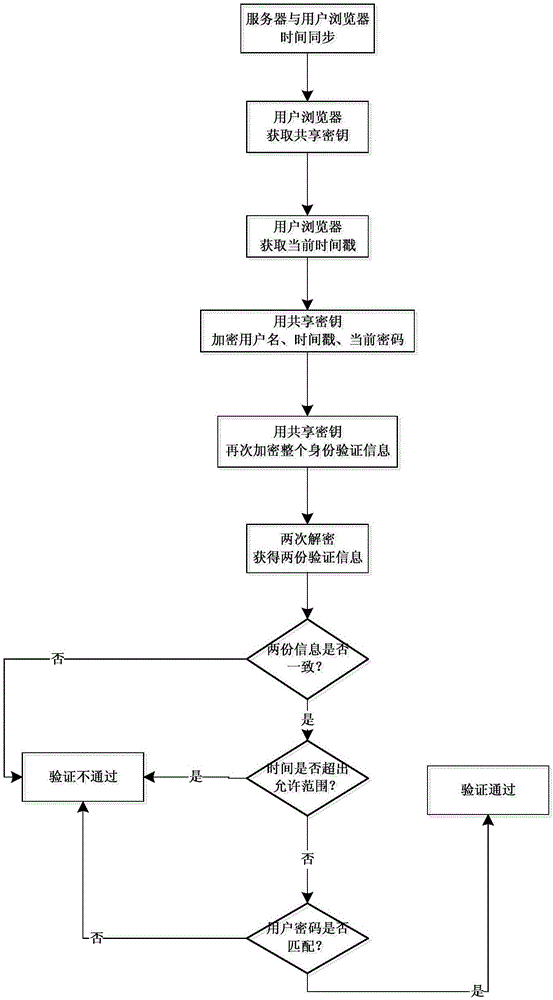
[0034] Such as figure 1 , 2 Shown; the following to use the inherent server control Login provided by ASP.net to create a user login page Login.aspx detailed description.
[0035] The page code of Login.aspx is as follows:
[0036]
[0037]
[0038]
[0039]
[0040] Login
[0041]
[0042]
[0043]
[0044]
[0045]
[0046]
[0047]
[0048]
[0049]
[0050]
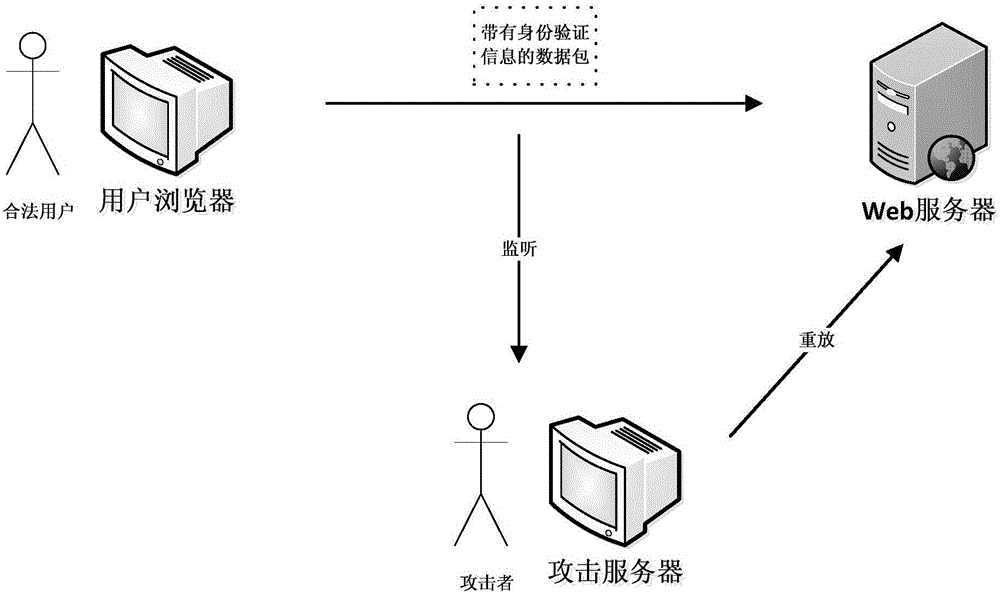
[0051] Such as figure 2 As shown, the attack process is as follows: the legitimate user sends a normal access request to the web server, but the attacker monitors the communication process. Afterwards, the attacker constructs a request based on the monitored identity information, impersonating a legitimate user to access the web server. For the above ASP.net website, the principle implementation plan of replay attack is as follows:
[0052] 1) The user enters the URL of the web server, and the server responds to the login page Login.aspx;
[0053] 2) The user enters the user name and pas...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com