Keyword searchable delay encryption method and system
An encryption method and keyword technology, applied in digital transmission systems, transmission systems, digital data protection, etc., can solve the problems that it is difficult to guarantee that there will be no collusion, that keyword information cannot be obtained, and that it is difficult to implement, and achieve the effect of increasing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
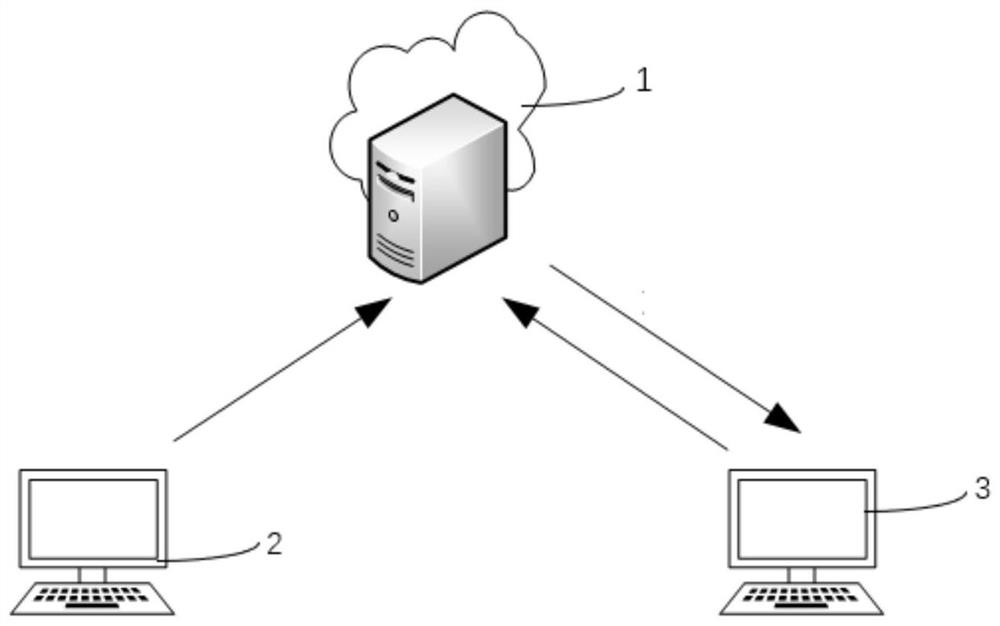
[0056] Such as figure 1 As shown, the keyword searchable delayed encryption system of the present invention at least includes a cloud server 1 , a sending end 2 and a receiving end 3 . The sending end 2 and the receiving end 3 respectively establish a communication connection with the cloud server in a wired or wireless manner.
[0057] Both the sending end 2 and the receiving end 3 can be computers, servers, mobile computers, smart phones, tablet computers, wearable devices and other devices with communication functions and sending information.
[0058] The sending end 2 sends at least one searchable ciphertext and / or file ciphertext A1 to the cloud server 1 .
[0059] The receiving end 3 sends at least one search request A2 containing retrieval trapdoor information to the cloud server 1 .
[0060] The cloud server 1 searches the stored first searchable ciphertext for a qualified second searchable ciphertext based on the retrieval trapdoor information, and feeds back the fi...
Embodiment 2
[0109] This embodiment is a further description of Embodiment 1, and repeated content will not be repeated.
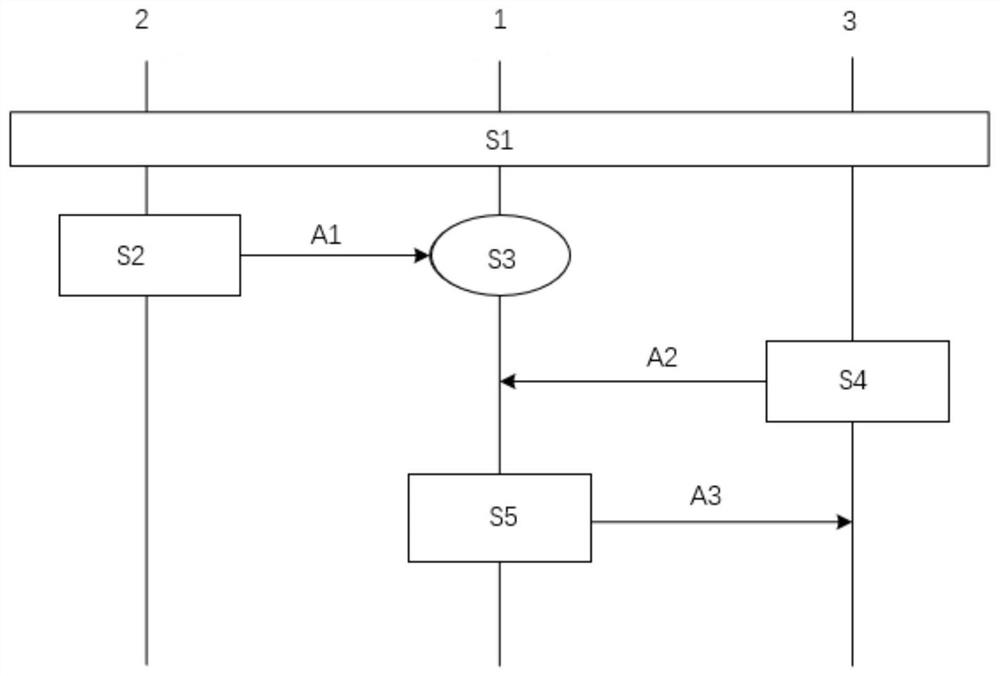
[0110] Such as figure 2 As shown, the steps of the keyword searchable delay encryption method implemented by the keyword searchable delay encryption system of the present invention at least include:
[0111] S1: Construct the corresponding bilinear map and trapdoor delay function according to the preset security parameters and delay time parameters, and calculate the public key PK and private key SK according to the parameters of the bilinear map and trapdoor delay function.
[0112] S2: Generate at least one searchable ciphertext C for at least one keyword W of the file to be uploaded based on the public key PK w . Encrypt the file to be uploaded to generate file ciphertext, and finally upload the generated searchable ciphertext and / or file ciphertext to cloud server 1.
[0113] S3: Cloud server 1 receives and stores searchable ciphertext and file ciphertext.
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com