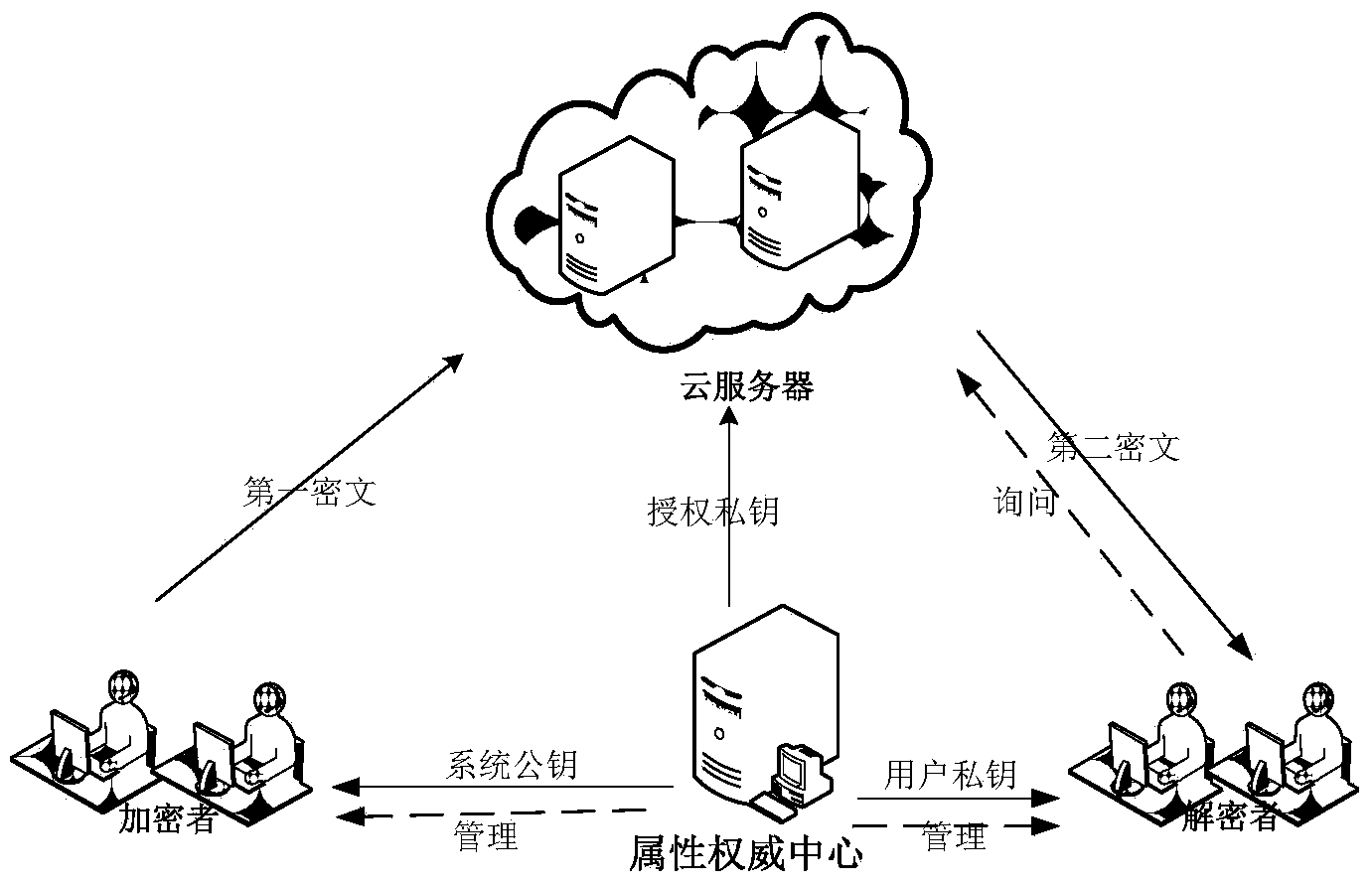
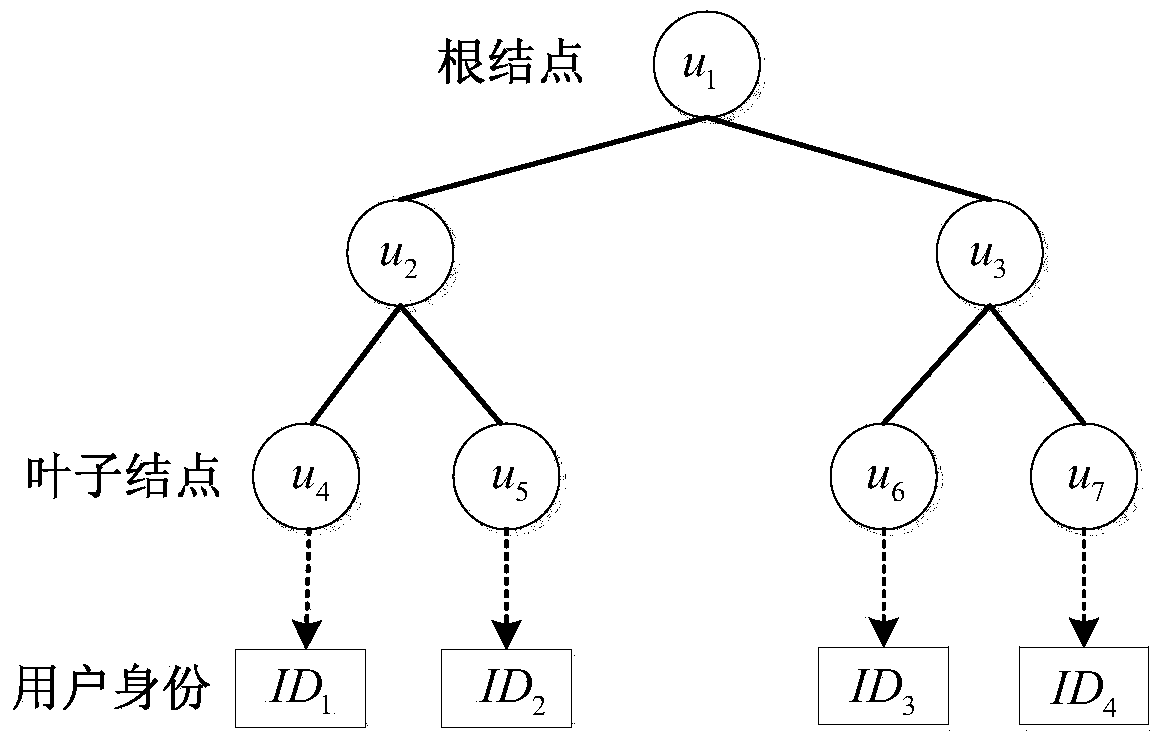
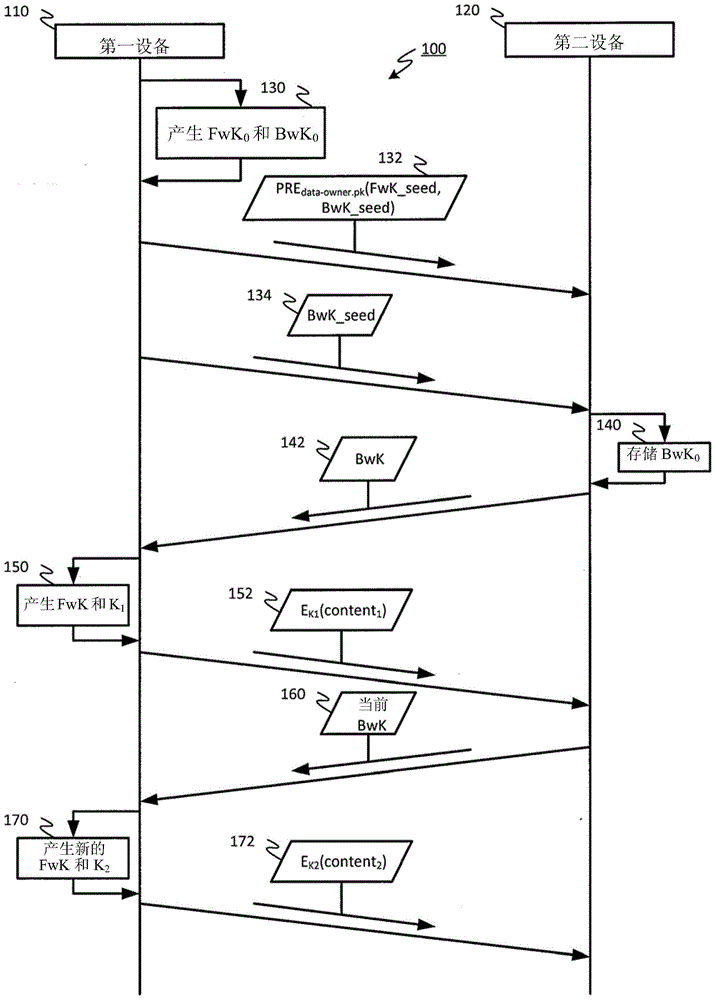
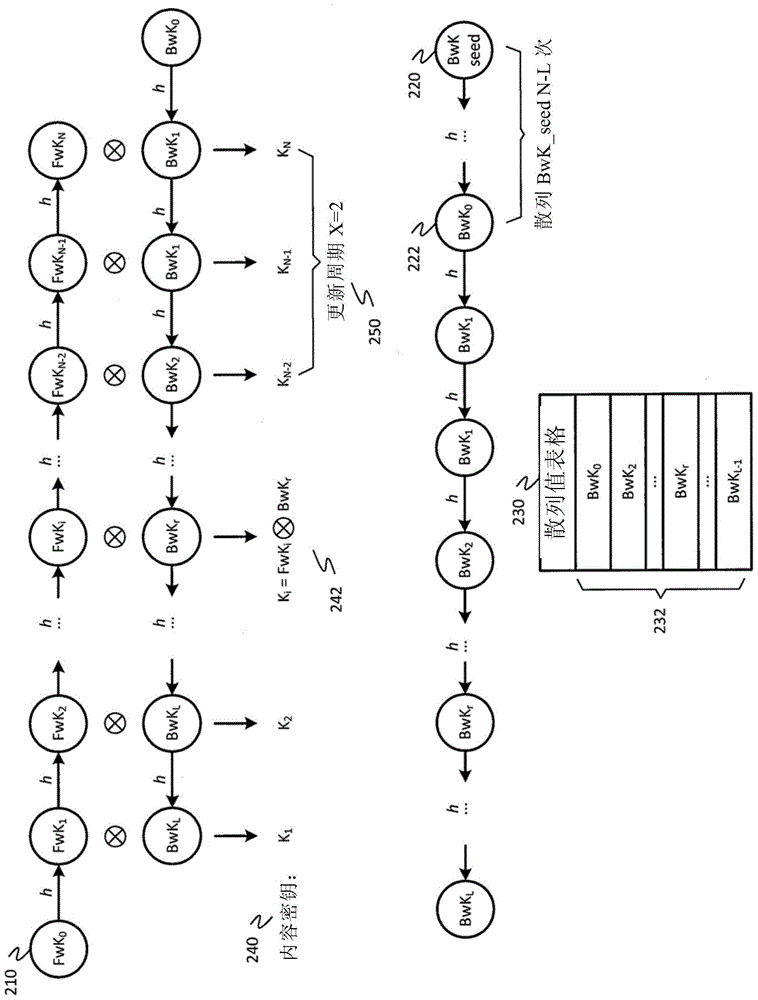
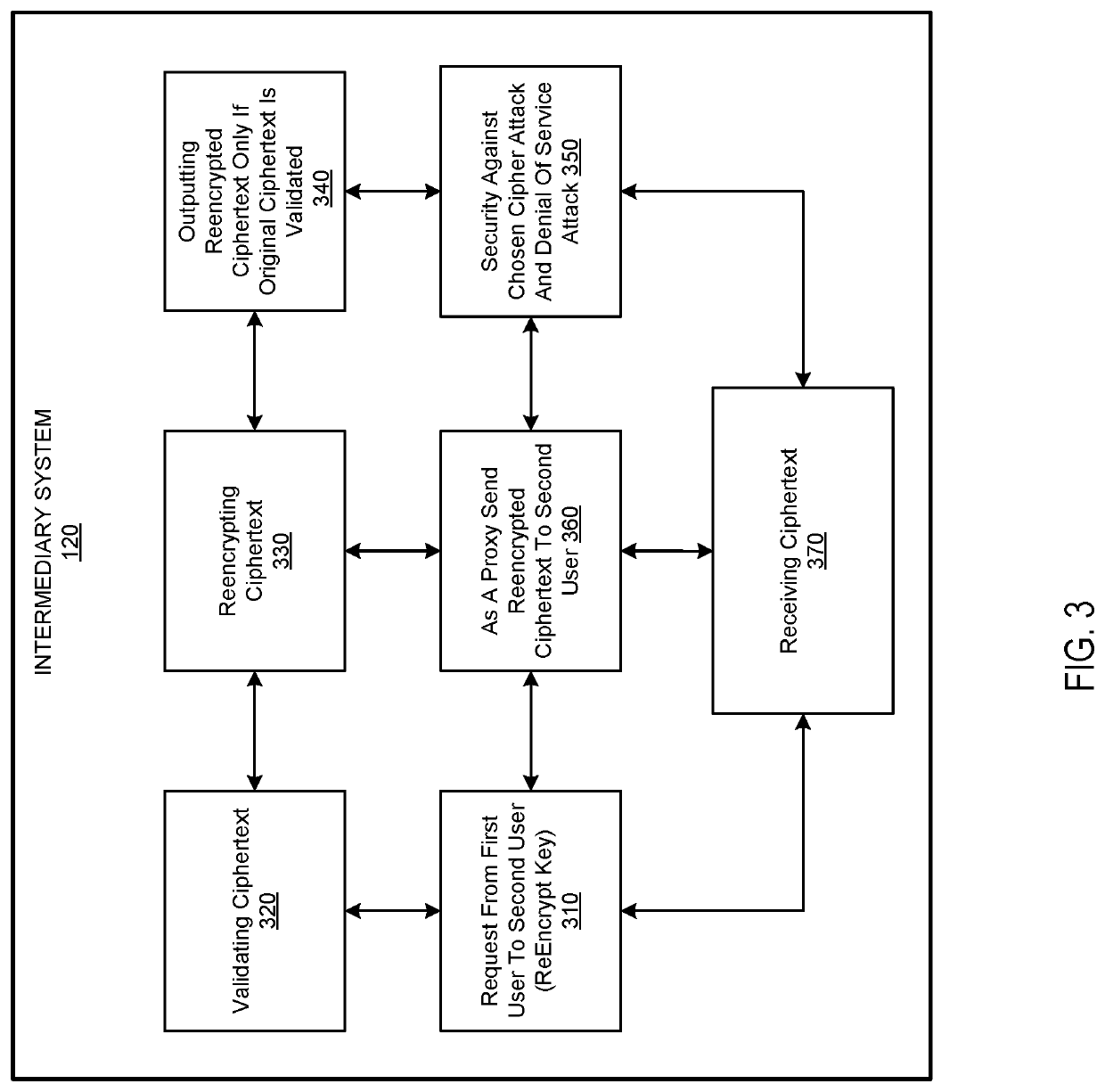
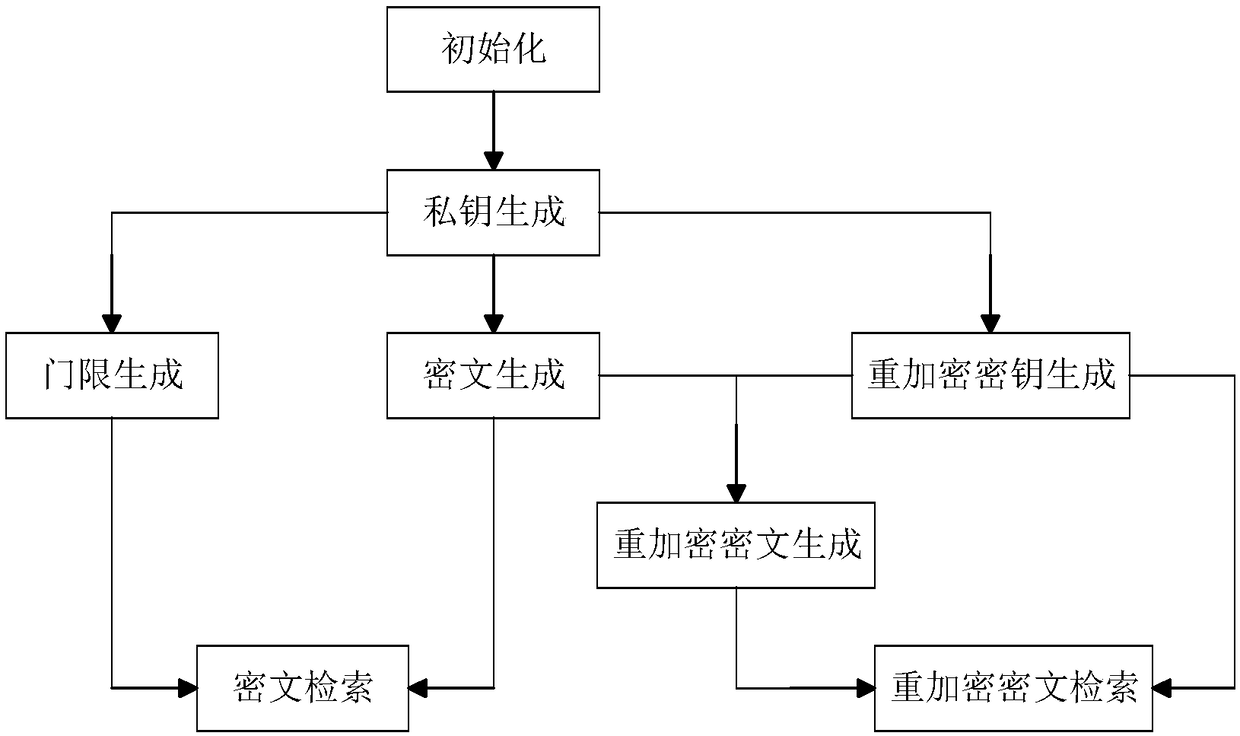
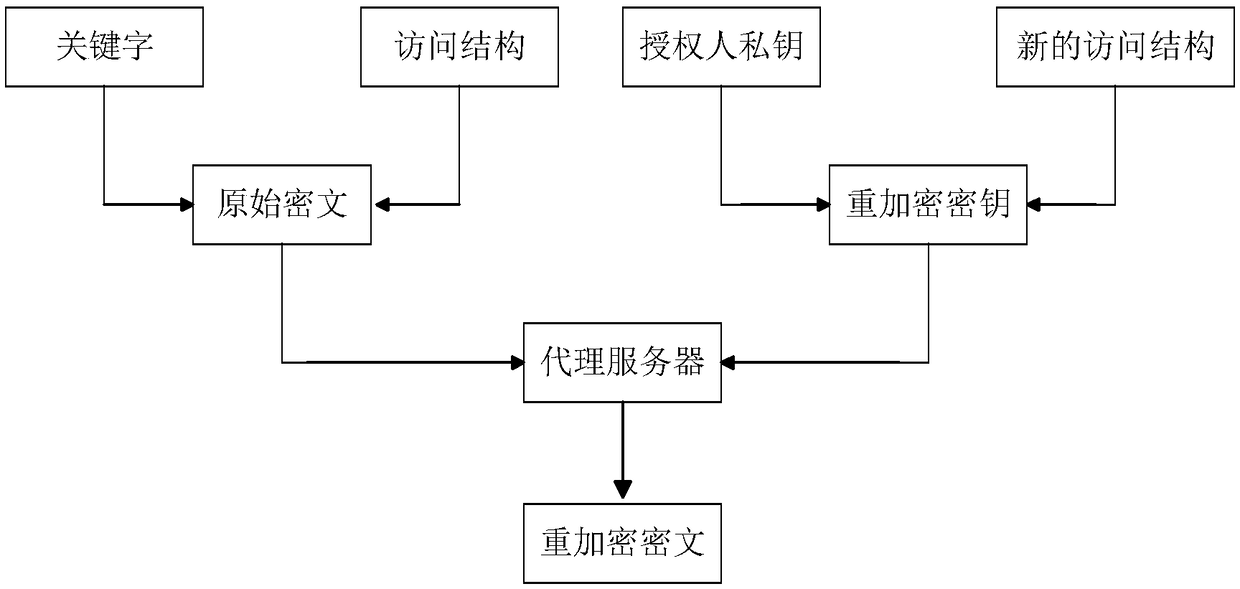
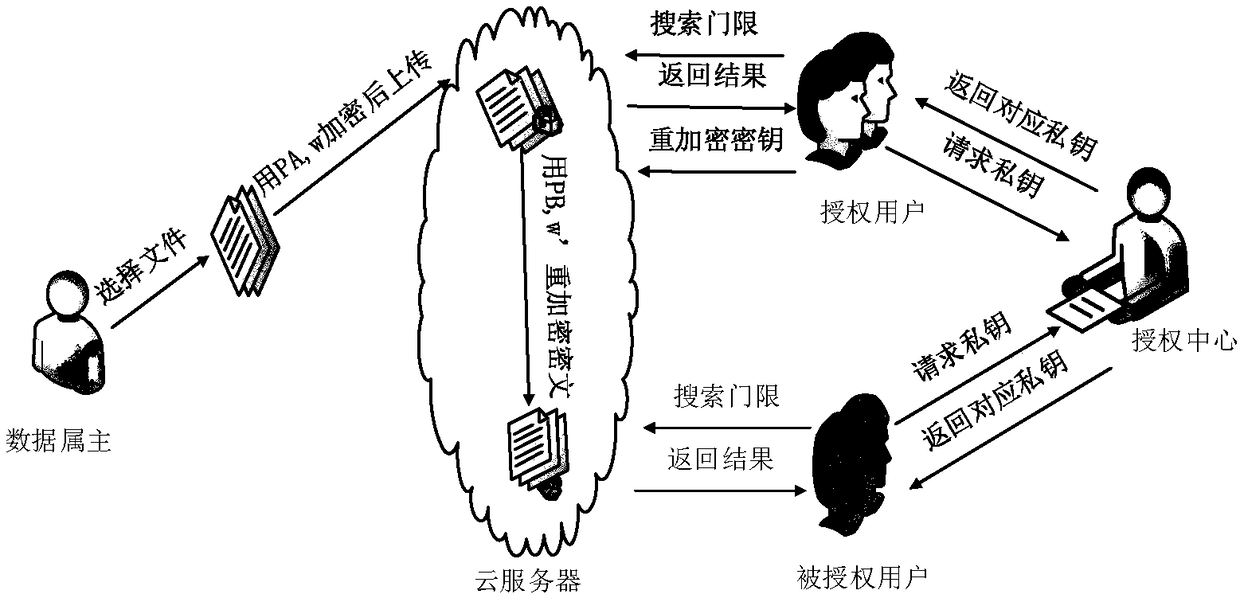
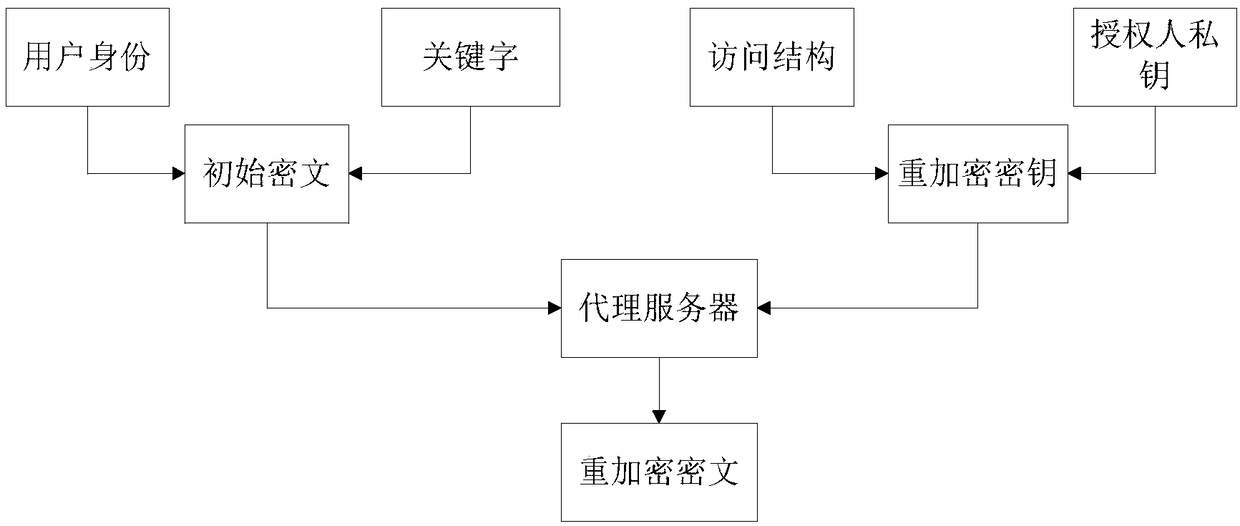
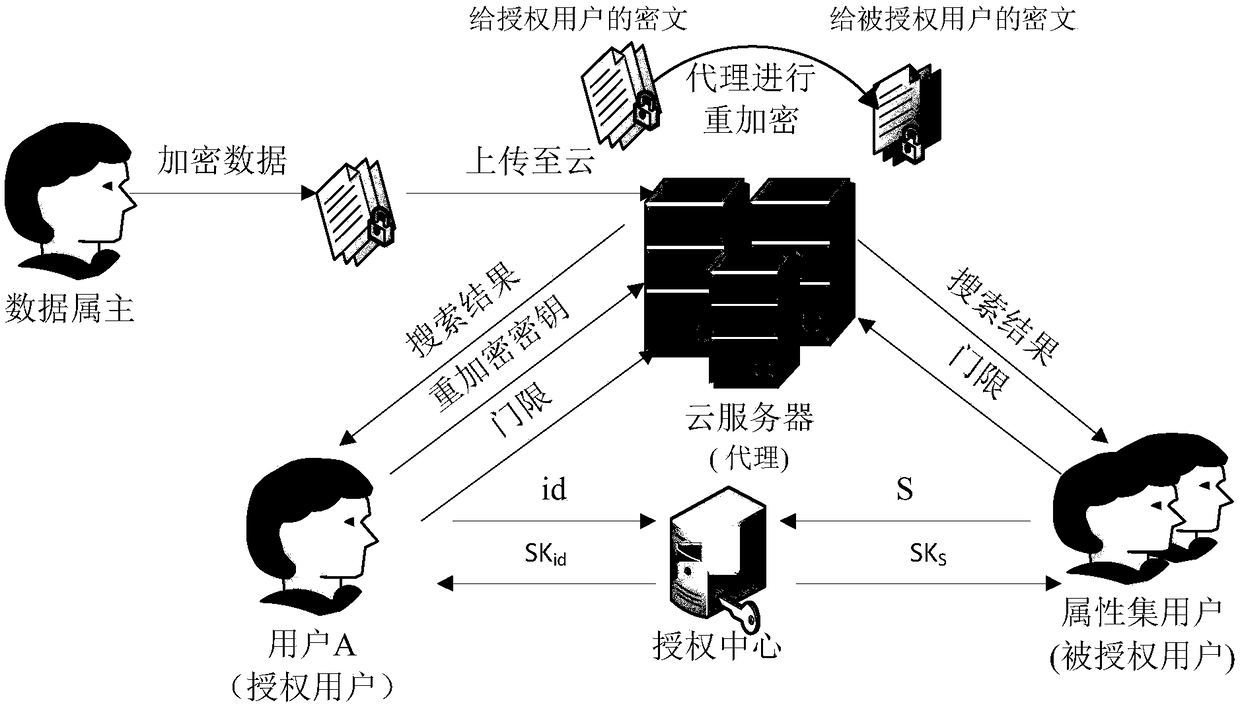
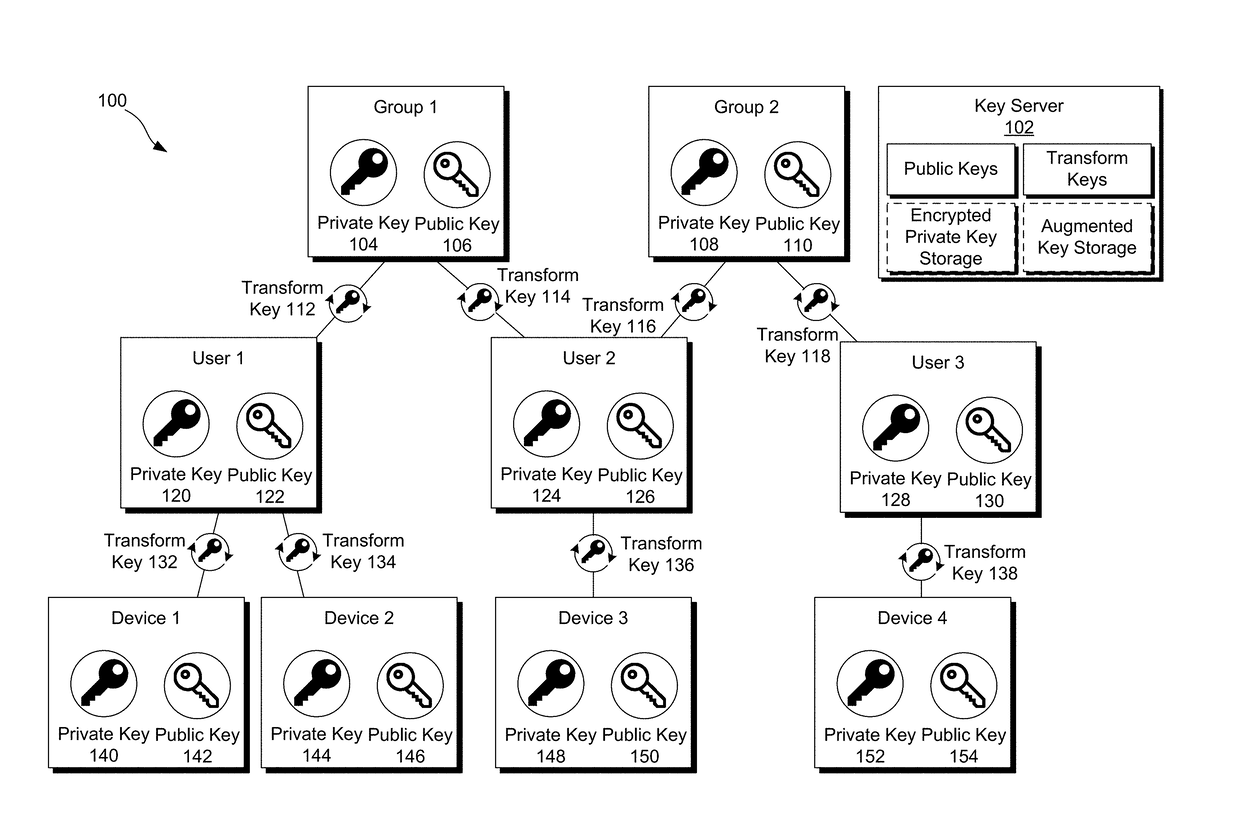
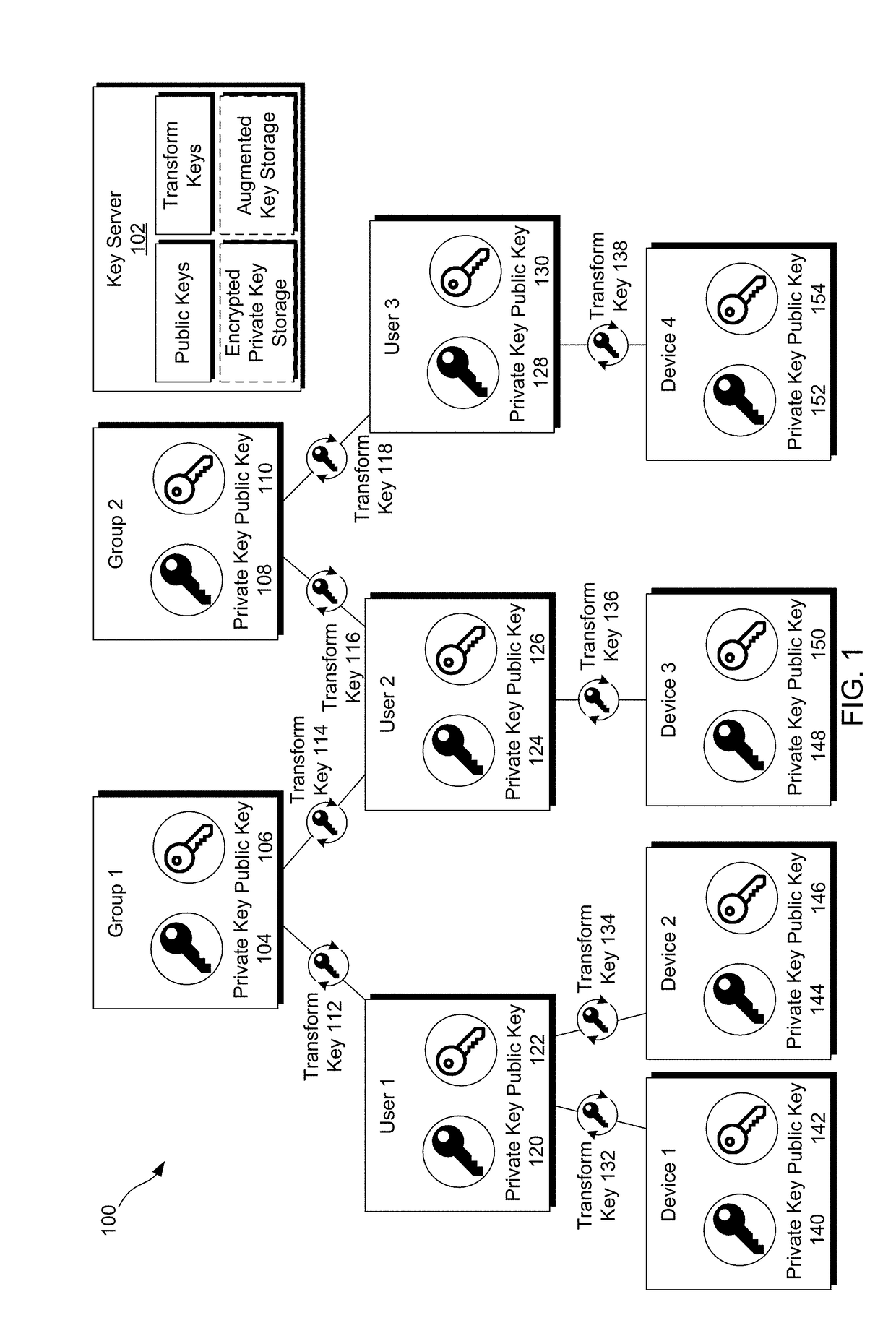
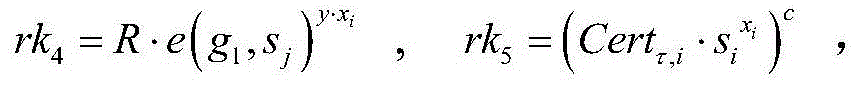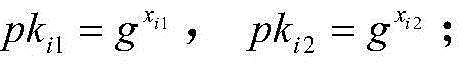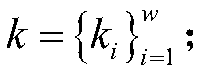Patents
Literature
77 results about "Proxy re-encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
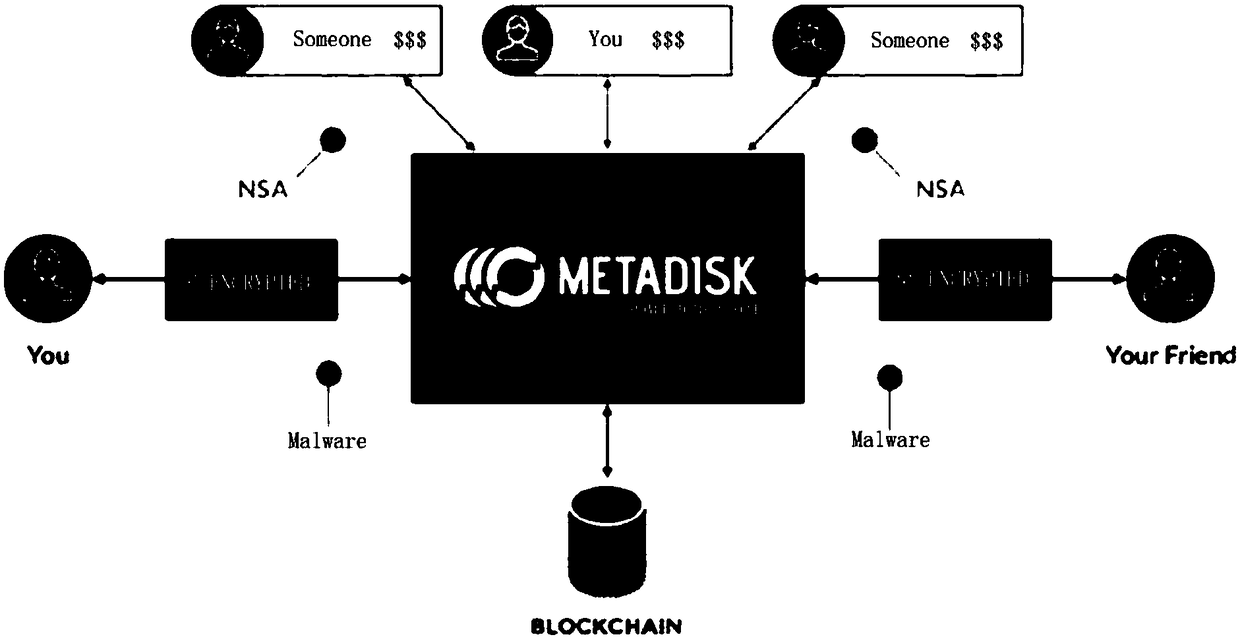
Proxy re-encryption (PRE) schemes are cryptosystems which allow third parties (proxies) to alter a ciphertext which has been encrypted for one party, so that it may be decrypted by another.
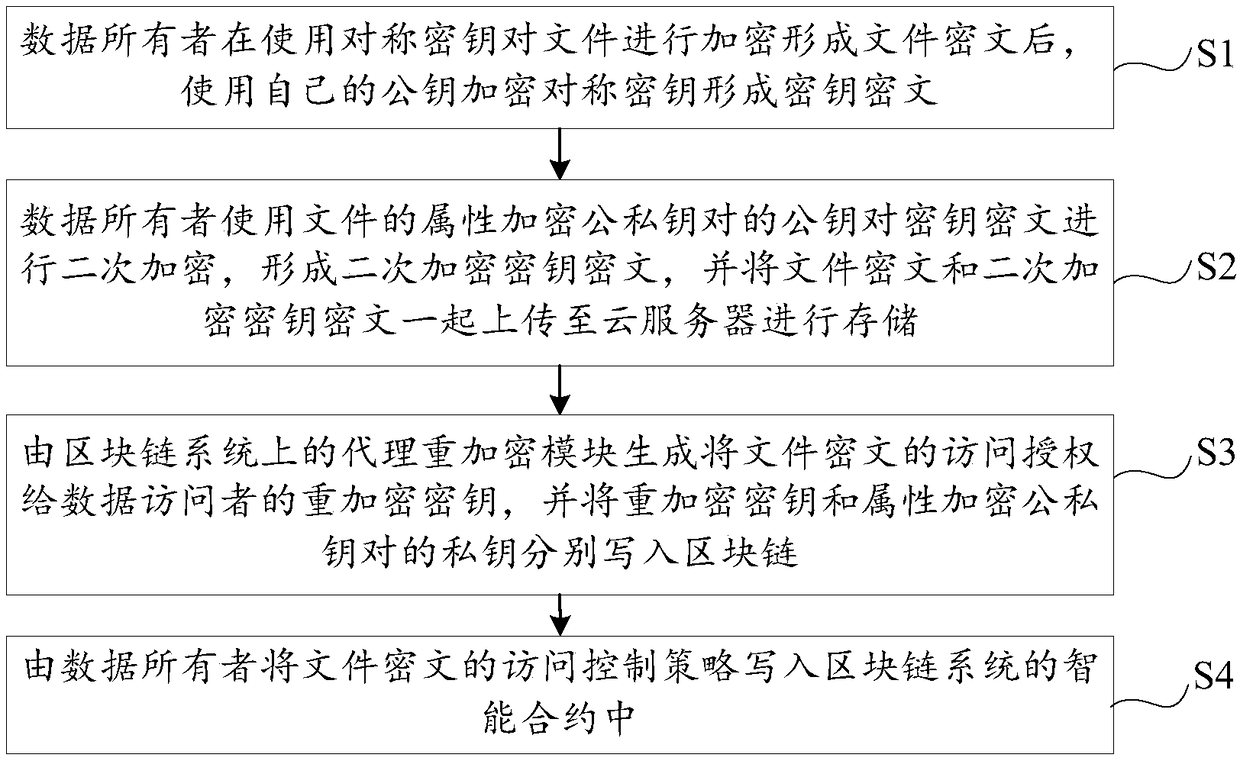
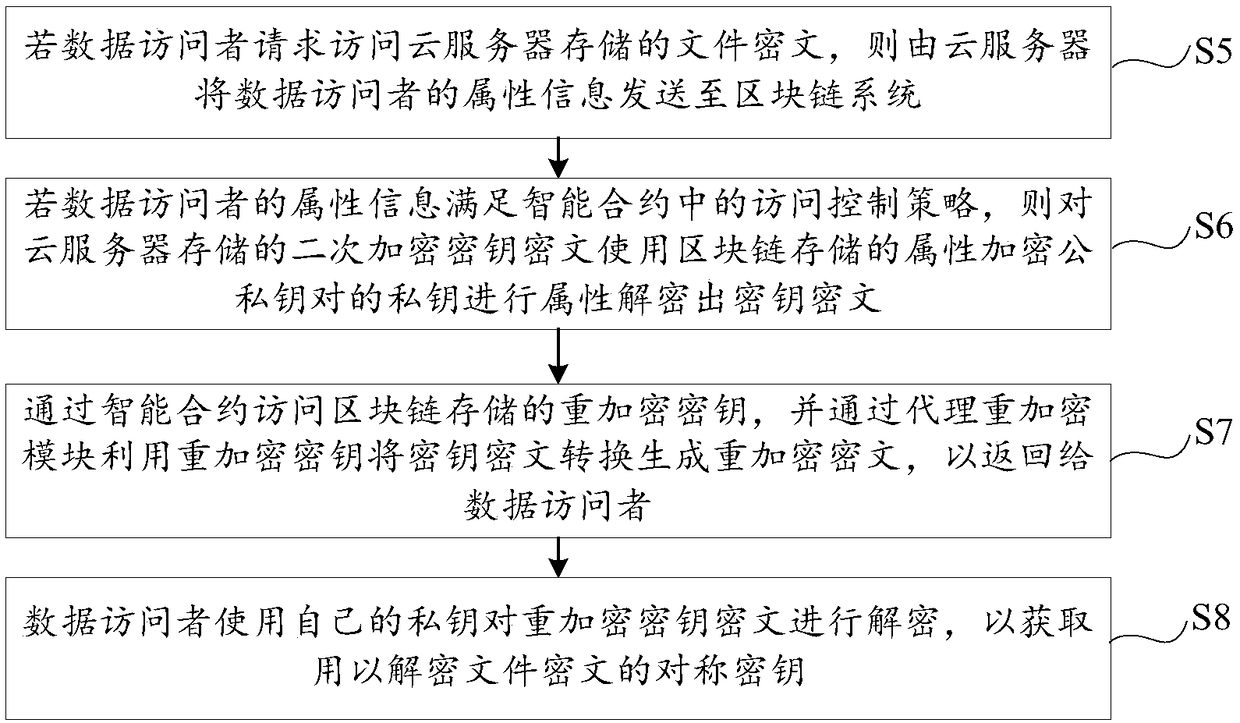
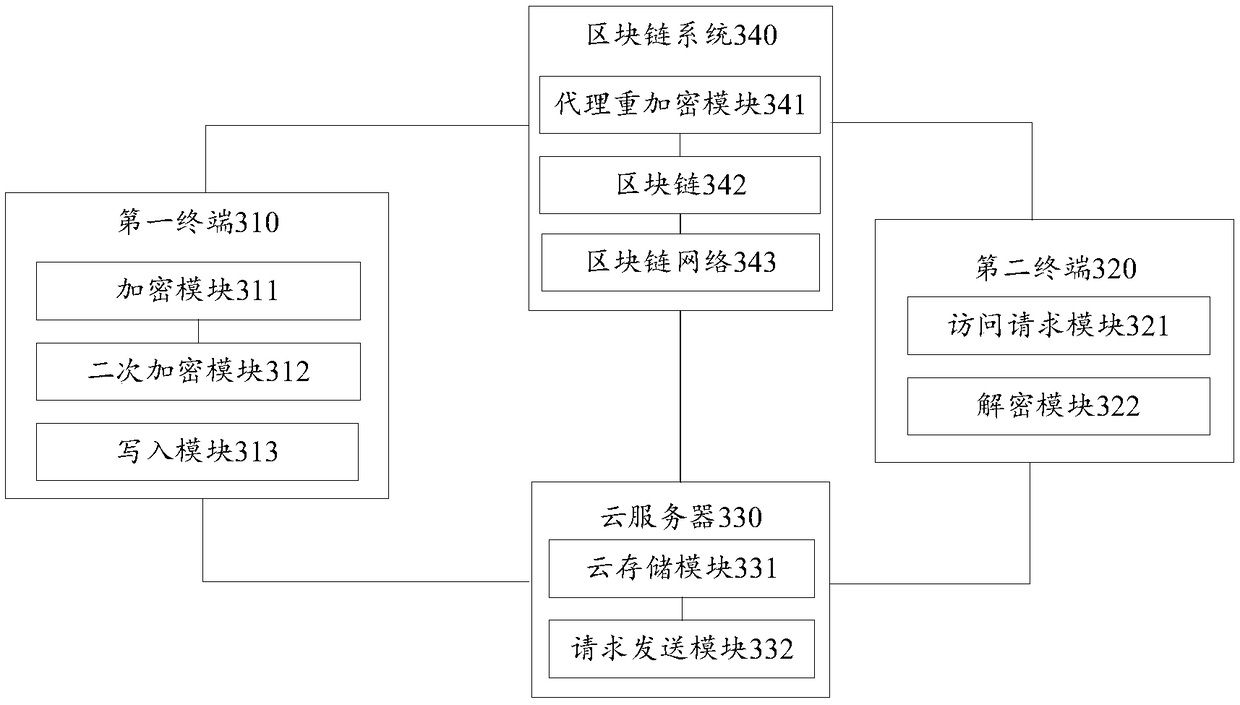
Blockchain-based data cloud storage encryption method and system
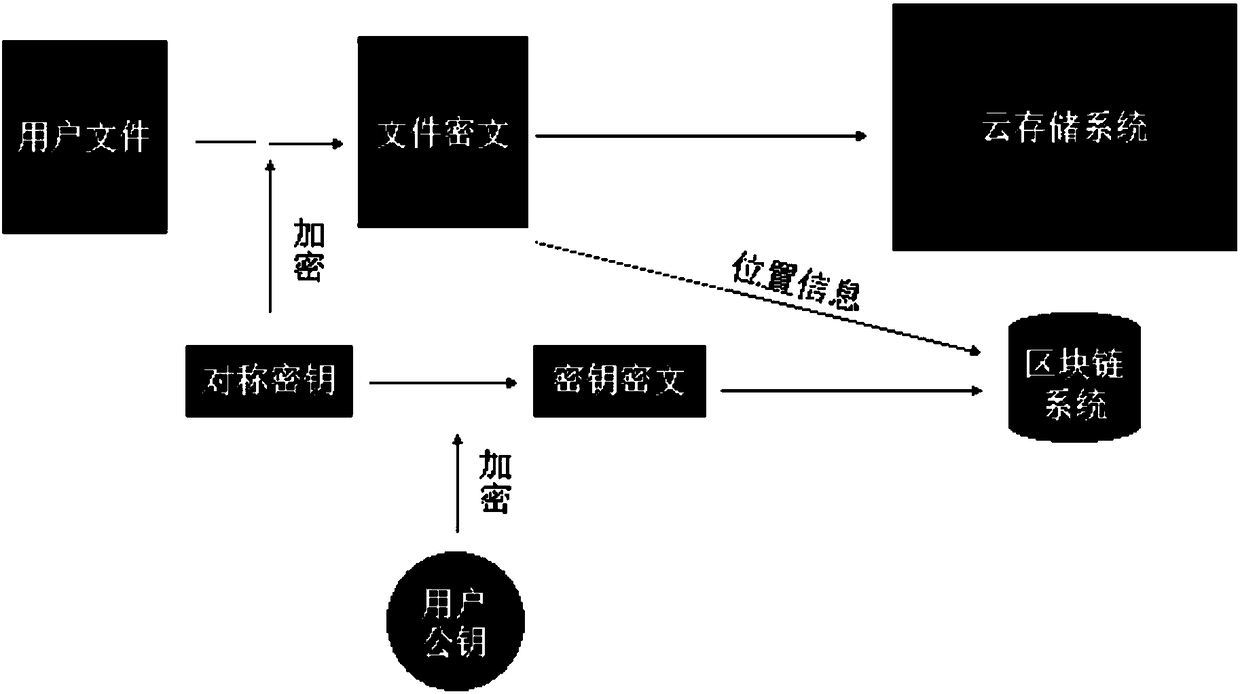
The invention discloses a blockchain-based data cloud storage encryption method and system. The method includes the following steps that: a data owner uses a symmetric key to encrypt a file so as to obtain a file ciphertext, and then, encrypts the symmetric key by using the public key of the data owner so as to obtain a key ciphertext, and the data owner uses the public key of an attribute key pair to perform secondary encryption on the key ciphertext, and stores the file ciphertext and the key ciphertext which has been subjected to secondary encryption to could, wherein the attribute encryption public and private key pair is generated by a proxy re-encryption module; the proxy re-encryption module generates a re-encryption key that authorizes access to the file ciphertext to a data visitor, and writes the re-encryption key and the private key of the attribute encryption public and private key pair into a blockchain; and the data owner writs the access control policy of the file ciphertext into a smart contract. According to the blockchain-based data cloud storage encryption method and system of the embodiments of the invention, the re-encryption technology and the attribute encryption technology are combined, so that the encrypted storage of data files on the cloud can be realized; and the smart contract technology is used to realize the access control of the data on the cloud, and therefore, the privacy and security of the data can be fully guaranteed.
Owner:ZHONGAN INFORMATION TECH SERVICES CO LTD
File security sharing method and system based on blockchain cloud storage
ActiveCN108259169AEasy to share remotelyFrequent migrationKey distribution for secure communicationXML EncryptionCloud data
The invention is applicable to the field of data storage technology improvement, and provides a file security sharing method based on blockchain cloud storage. The method includes the steps as follows: S1, performing data encryption on a file by using a symmetric encryption algorithm, and storing a data ciphertext in a cloud disk; S2, enabling a user to generate a key ciphertext by using a symmetric key for decrypting the data ciphertext through encryption, and storing the storage locations of the key ciphertext and the data ciphertext together on a blockchain as a part of metadata; and S3, performing proxy re-encryption on the stored file data by using a new key, and securely sharing the data through the new key and the re-encrypted new ciphertext. Through the implementation of a cloud security storage and sharing mechanism for a private file under a decentralized storage architecture of the blockchain, the data stored in the cloud by the user can only be accessed through a private key, when the own encrypted data needs to be shared to other users, the own original key of an owner cannot be exposed to other people, and the process of downloading all cloud data, re-encrypting the data by using a shared key, and then uploading the data in sequence is not required.
Owner:PEKING UNIV SHENZHEN GRADUATE SCHOOL +1
Method and device with privacy protection function for data sharing and publishing
InactiveCN102176709AProtect data privacyKey distribution for secure communicationSpecial data processing applicationsPrivacy protectionData sharing
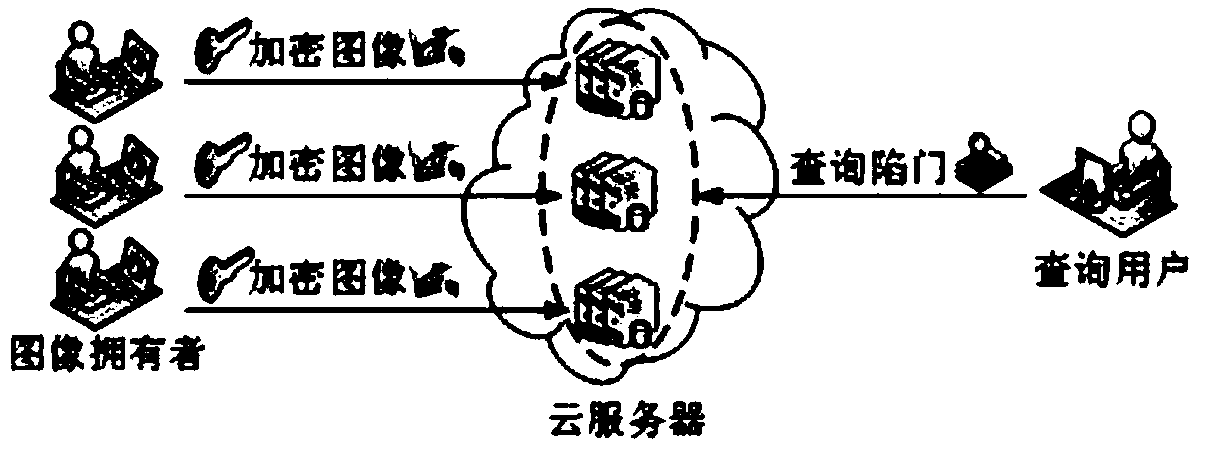
The invention provides a method and device with a privacy protection function for data sharing and publishing. A data owner encrypts own data and data-related keywords according to a preset demand and then stores the data and the data-related keywords at a service provider, a user sends a keyword query request to the service provider, the service provider forwards the received keyword query request to the data owner, the data owner authorizes the service provider by issuing a proxy re-encryption key to the service provider, the service provider, by utilizing the query request of the user, verifies available encrypted files satisfying the query request by comparing the trap door information of a pre-stored encryption query keyword with the trap door information of a hidden query keyword, then the service provider uses the proxy re-encryption key for encrypting the encrypted files satisfying the query request of the user and provides the encrypted files for the user, and the user decrypts the files with own private key, thus data privacy of the data owner is put under protection and the data of the data owner is shared with the authorized legal user.
Owner:BEIJING JIAOTONG UNIV
Method for protecting privacy data of users in cloud environment
InactiveCN102655508AWith transparencyReduce overheadEncryption apparatus with shift registers/memoriesPlaintextInternet privacy
The invention discloses a method for protecting the privacy data of users in a cloud environment. The method comprises the following steps that: a cloud platform receives a user request, and judges whether the user request is a data uploading request or a data reading request; if the user request is a data reading request, the cloud platform searches corresponding data according to an identifier of to-be-read data in the data reading request, and judges whether the data is a ciphertext; if the data is a ciphertext, the cloud platform searches whether the user is authorized in a re-encryption key server; if the user is authorized, the cloud platform re-encrypts the data into a ciphertext (can be decrypted by the user) by using a proxy re-encryption service and a re-encryption key corresponding to the user, and issues the ciphertext to the user; the user decrypts the ciphertext by using a decryption key of the user and a decryption interface of a safety plugin so as to obtain plaintext data; and the user calls a corresponding application program interface to carry out modification on uploaded data by using a client plug-in. According to the invention, the application demands of user data on the cloud platform are not affected while the privacy data of the users is protected,.
Owner:HUAZHONG UNIV OF SCI & TECH
Method for realizing timely user attribute cancel based on ciphertext-policy attribute-based encryption
ActiveCN104113408AReduce workloadTroubleshoot update issuesKey distribution for secure communicationPlaintextBinary tree
Owner:XIDIAN UNIV
Improved encrypted/decrypted content, and method and apparatus for issuing encrypted content
ActiveCN104683099AKey distribution for secure communicationEncryption apparatus with shift registers/memoriesHash chainProxy re-encryption
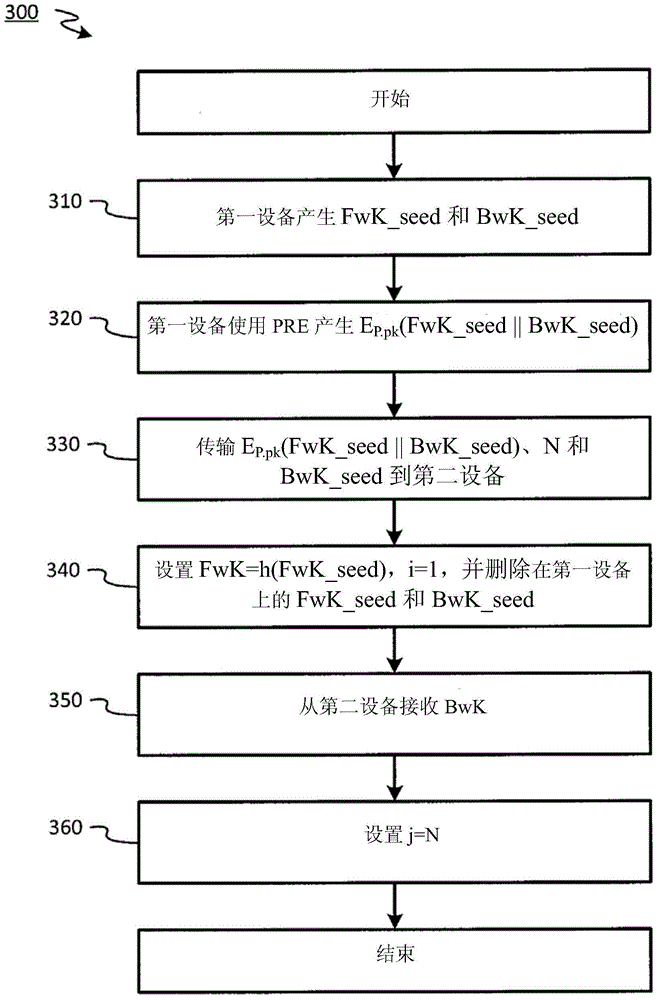
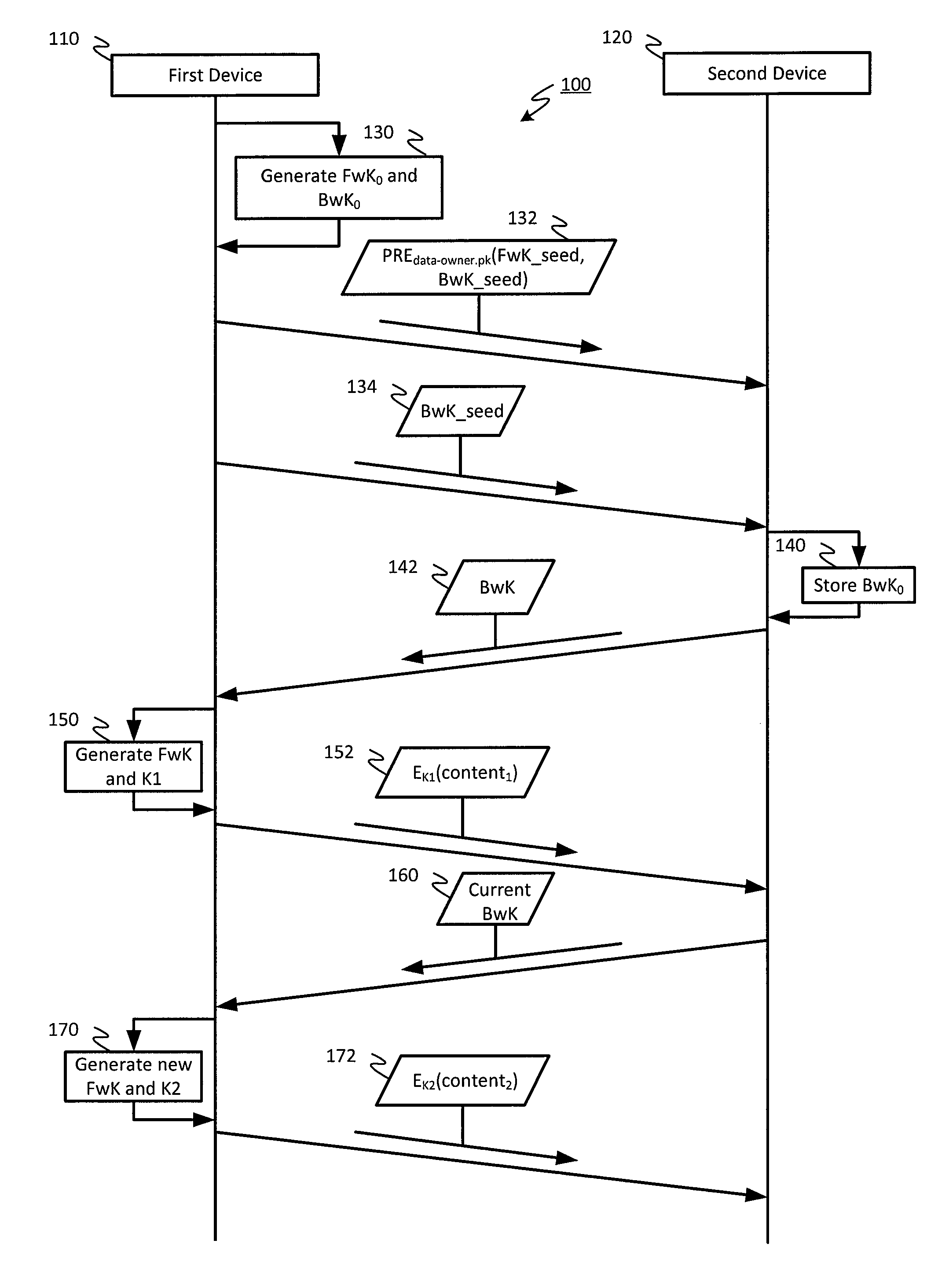
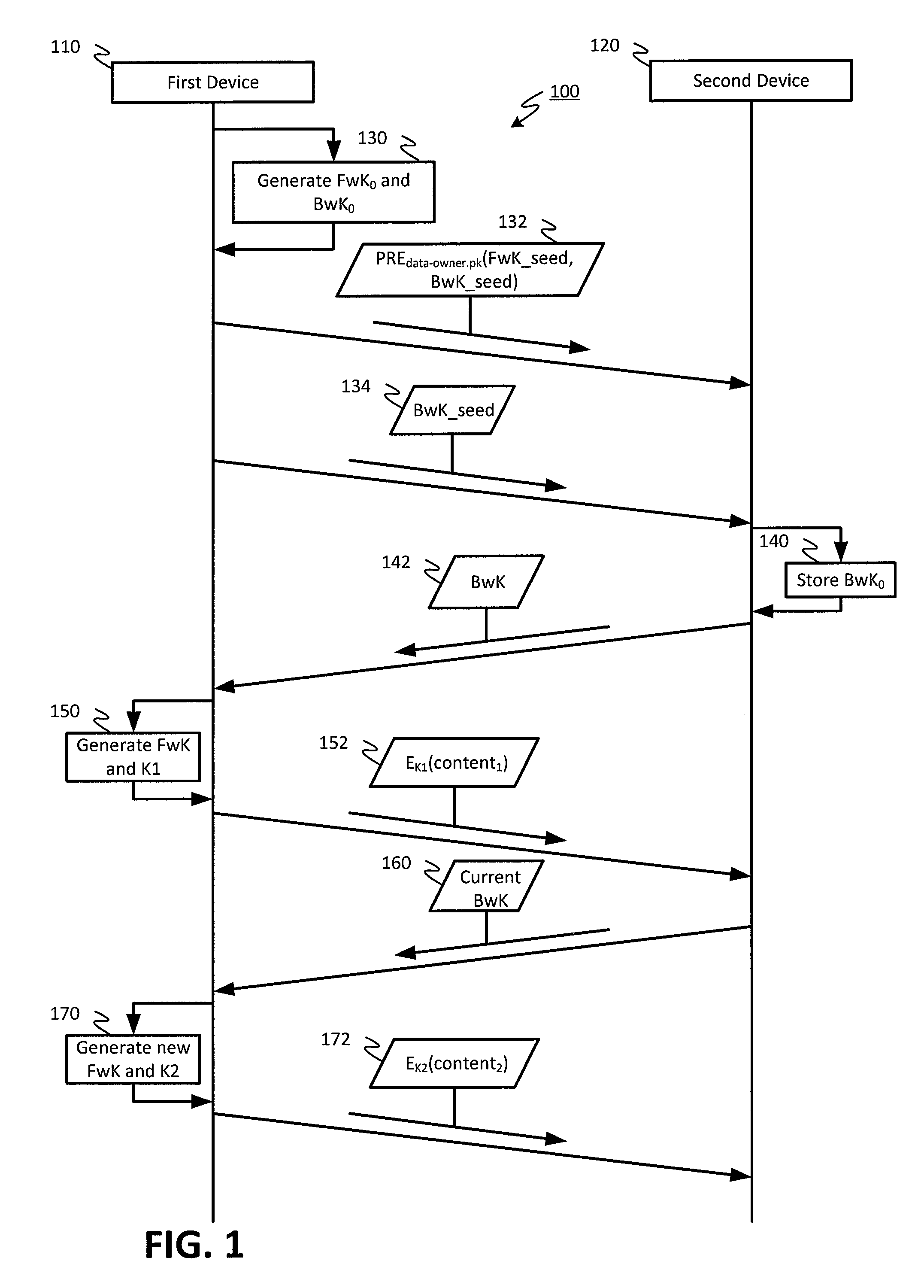
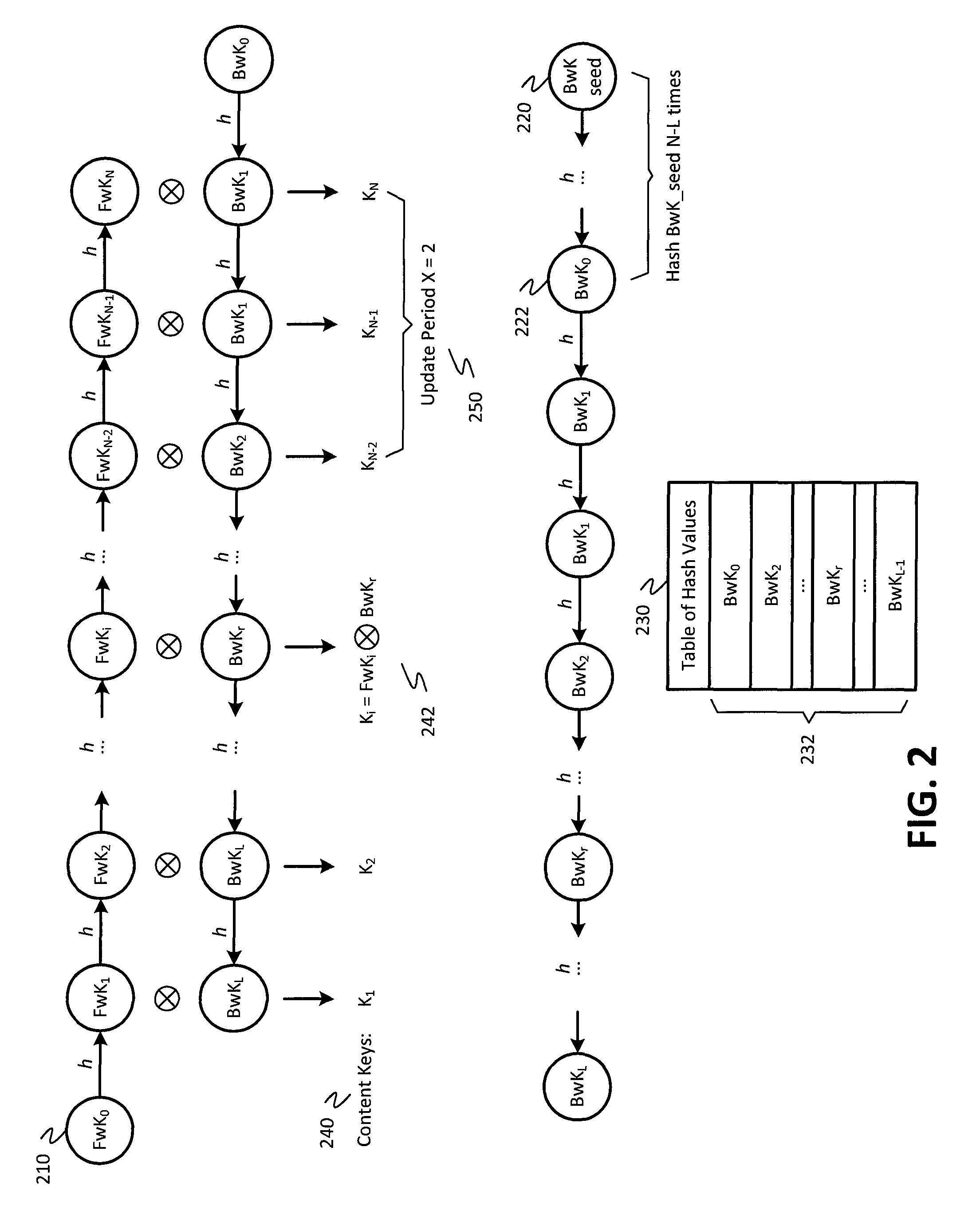
The invention discloses improved encrypted / decrypted contents, and a method and apparatus for issuing encrypted contents. In one embodiment, a first device encrypts contents by using a dual hash chain technology. The first device maintains forward hash chains. A second device maintains reverse hash chains. A content key for encrypting contents is guided out through forward and reverse hash chain values. The second device dose not know seeds used for generating forward hash chains and thus a content key cannot be produced, therefore, encrypted contents are less liable to leak. Moreover, the invention provides a technology for re-encrypting contents through a proxy re-encryption (PRE) technology. In this way, encrypted contents can be provided to a request device for decryption with need of forward and reverse hash chains. Furthermore, the invention provides a technology, having a fine-grained access control function, for issuing encrypted contents to the request device.
Owner:HONG KONG APPLIED SCI & TECH RES INST
A block chain ciphertext cloud storage sharing method based on attribute proxy re-encryption
ActiveCN109189727AImprove securityImprove sharing efficiencyDigital data protectionFile access structuresAttribute-based encryptionCloud storage
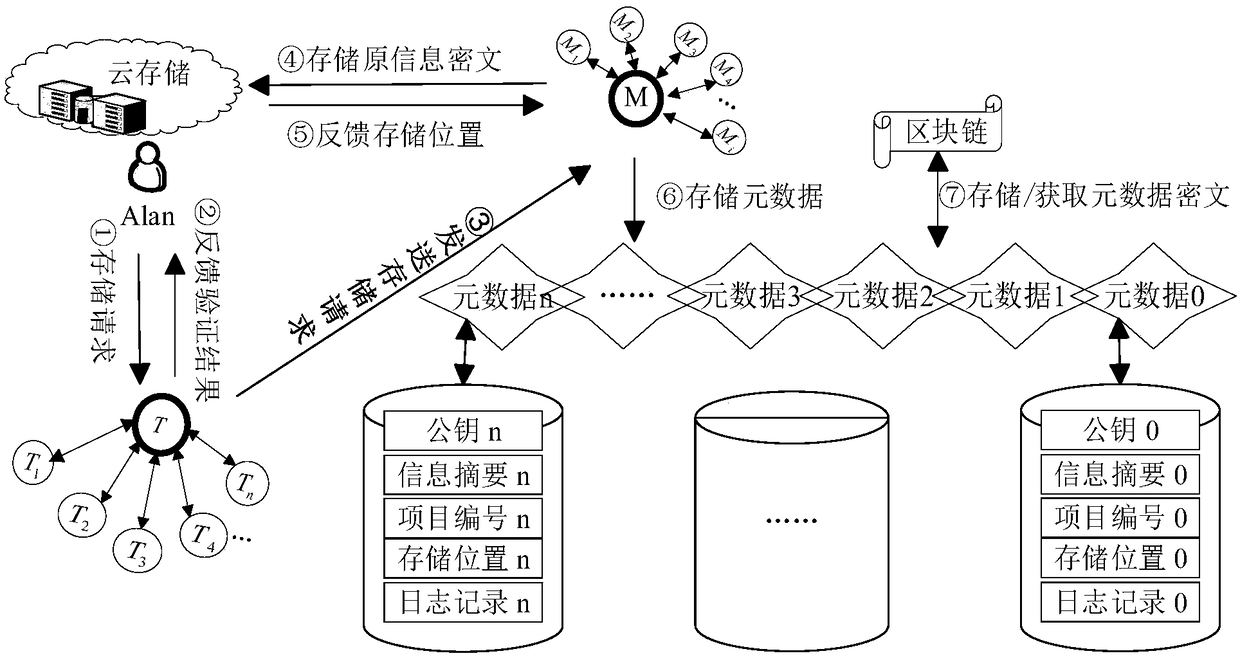
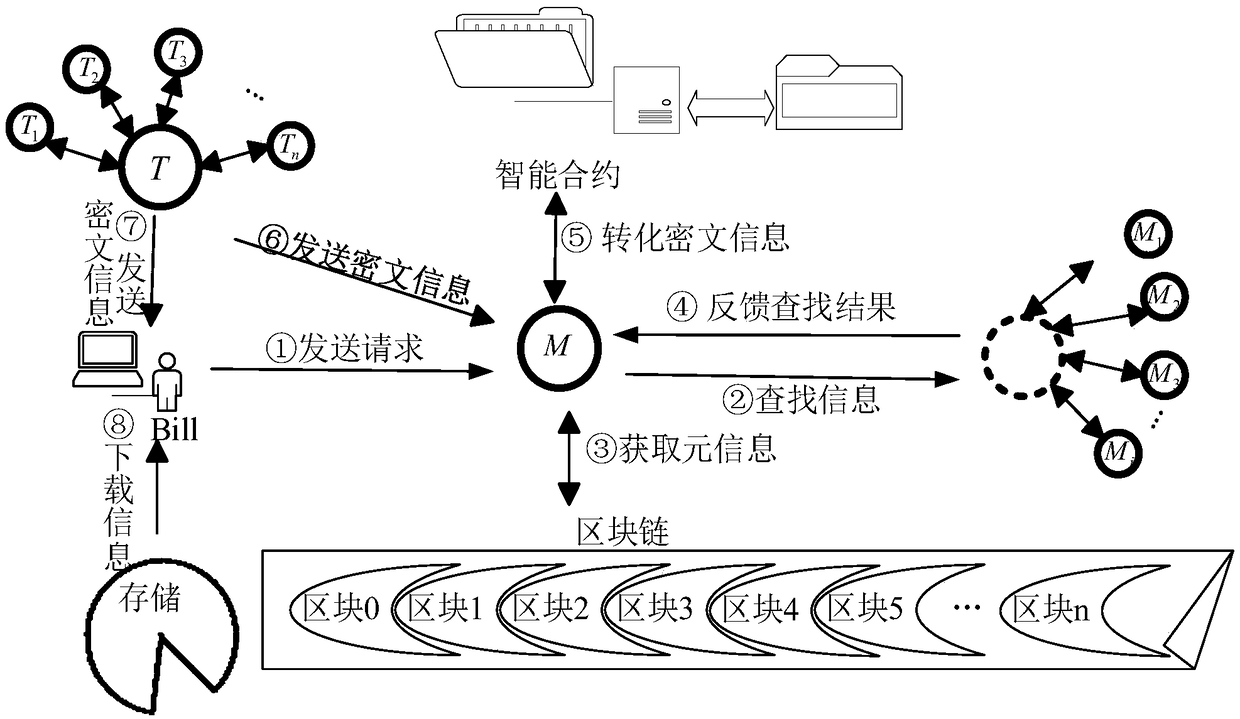
A block chain ciphertext cloud storage sharing method based on attribute proxy re-encryption is provided. On the basis of proxy re-encryption and attribute-based encryption technology, the invention proposes a block chain ciphertext storage sharing idea based on attribute proxy re-encryption for keyword retrieval. The metadata ciphertext is stored separately from the original information ciphertext by the attribute proxy re-encryption algorithm, the pool verification pool mechanism of block chain technology is used to determine the bookkeeping weight of the node, the information interaction contract is introduced to audit the identity of the user, and the transaction cost is automatically cleared. The security and the experimental analysis show that the invention shortens the encryption and decryption time, and reduces the high-frequency access pressure of the cloud memory. When the number of attributes is 100, the time consuming of re-encryption and decryption is 1.69 s, and the efficiency of the system is improved by 19.04%-49.68%. The method has stronger anti-collusion aggression, and has good application prospect in the field of internet of things.
Owner:南方电网互联网服务有限公司
System and method for key recovery
ActiveUS7831833B2Key distribution for secure communicationDigital data processing detailsApplication softwareComputer science
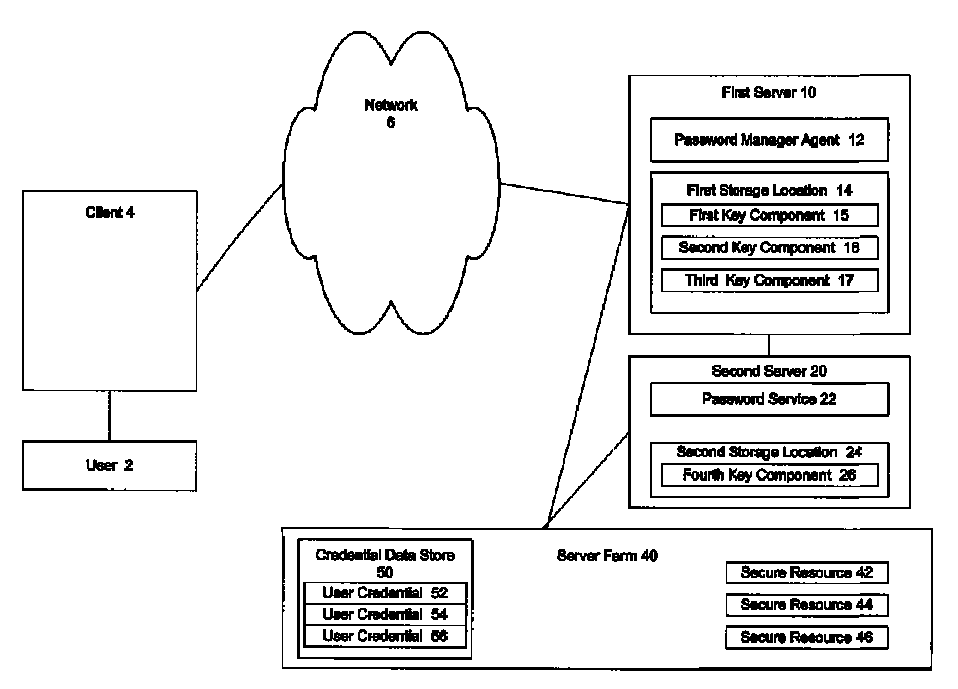
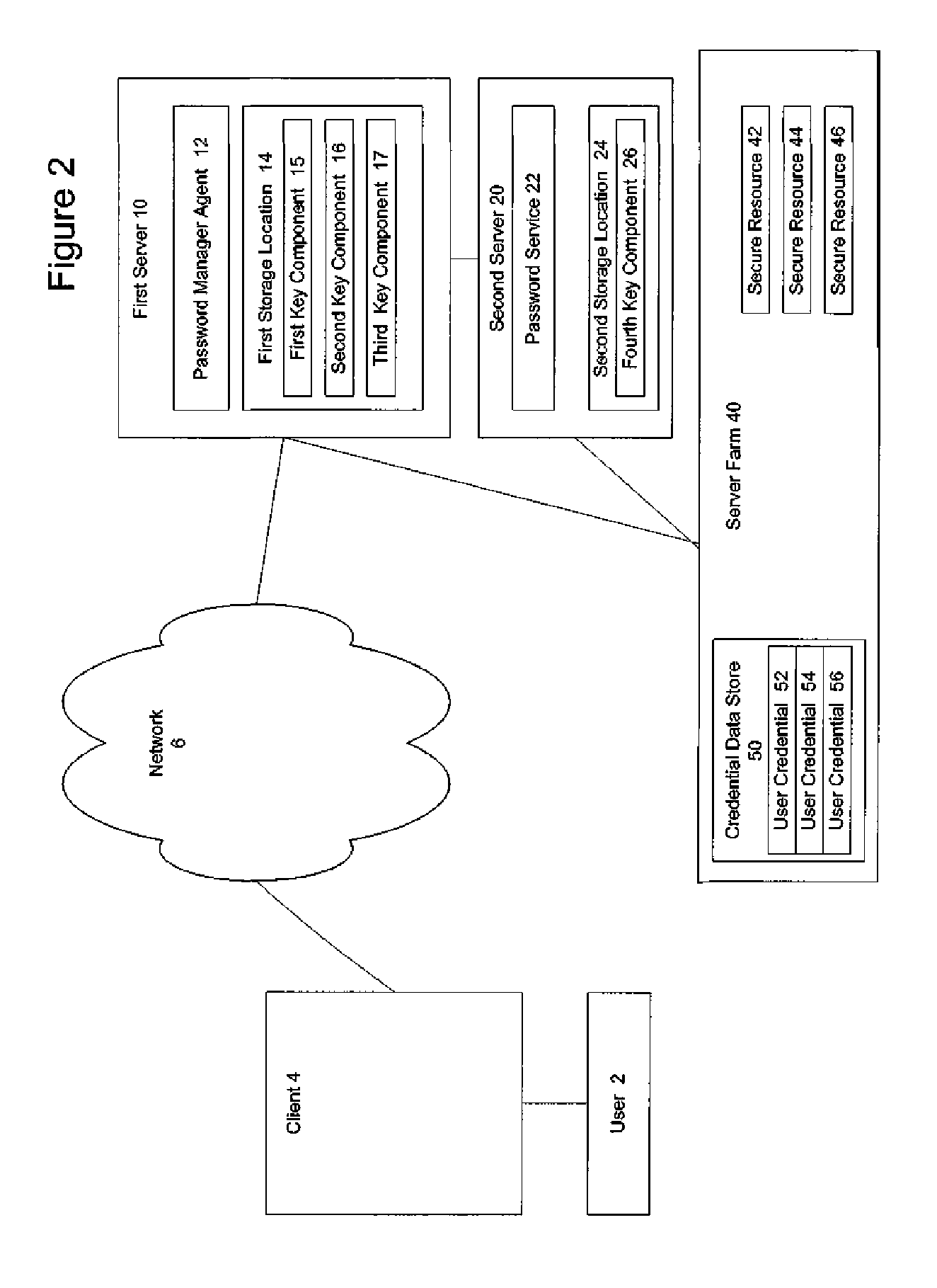
A secure mechanism for transparent key recovery for a user who has changed authentication information is disclosed. A password manager agent intercepts requests by a user to access secure resources that require user credentials. Upon detecting changed authentication information for the user, the password manager agent automatically regenerates the components of a cryptographic key associated with the user that was previously used to encrypt user credentials for the user and then destroyed. After regeneration of the original cryptographic key, the password manager agent uses the key to decrypt the user credentials necessary for the requested application. The regenerated key is then destroyed and the user credentials are re-encrypted by the password manager agent using a new cryptographic key associated with the user made up of multiple components. Following the re-encryption of the user credentials, the components used to assemble the new key are securely stored in multiple locations and the new key is destroyed.
Owner:CITRIX SYST INC
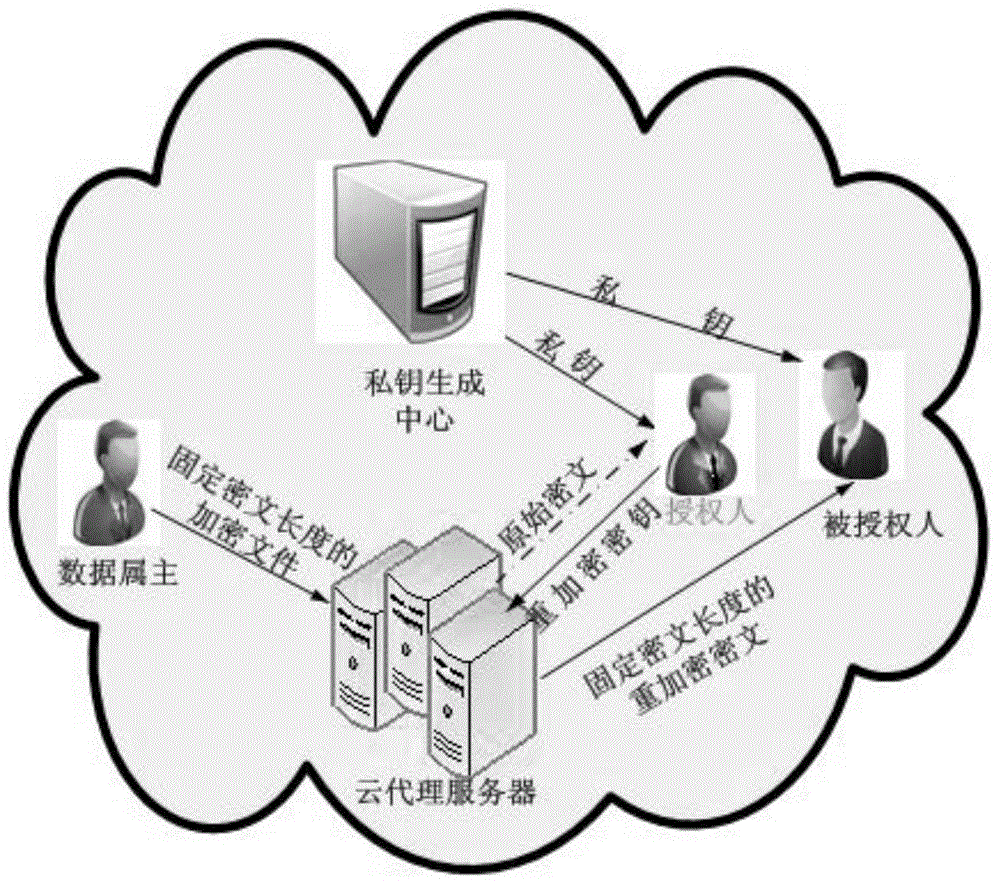
CP-ABE-based fixed ciphertext length proxy re-encryption system and method in cloud computing
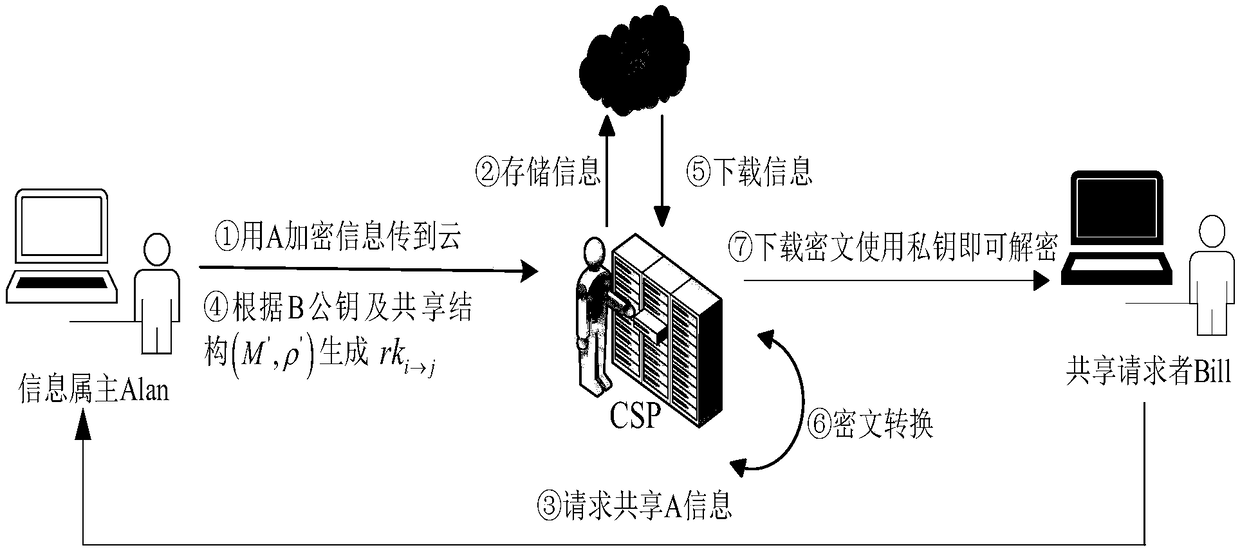
The invention discloses a CP-ABE-based fixed ciphertext length proxy re-encryption system and method in cloud computing. By the adoption of the method, efficient safe access and sharing of a data file in the cloud computing environment are achieved. According to the method, on one hand, the proxy re-encryption technology is adopted for ciphertext conversion so that a ciphertext which can be decrypted by an authorizer can be converted into a ciphertext which can be decrypted by an authorized person, to be specific, after a file of a data owner is encrypted and uploaded to a cloud proxy server, under the condition that the authorizer is not available, the cloud proxy server re-encrypts the encrypted file, and the authorized person can acquire a plaintext through decryption with a private key of the authorized person after acquiring the re-encrypted file from the cloud proxy server, so that safe access and sharing of data are guaranteed; on the other hand, during ciphertext encryption, the CP-ABE-based fixed ciphertext length algorithm is adopted for ciphertext computing, so that the length of the ciphertext is fixed and does not increase along with the increase of the number of attributes, and then computing expenses are effectively reduced.
Owner:NANJING UNIV OF POSTS & TELECOMM
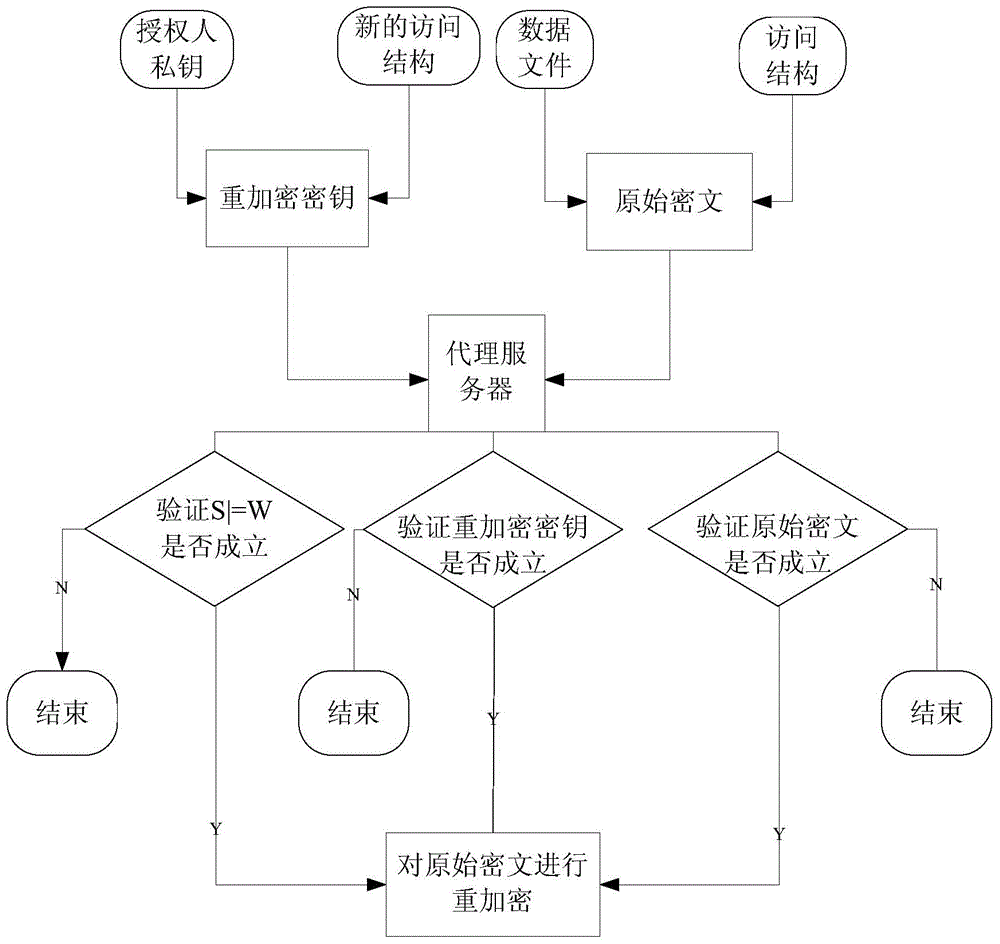
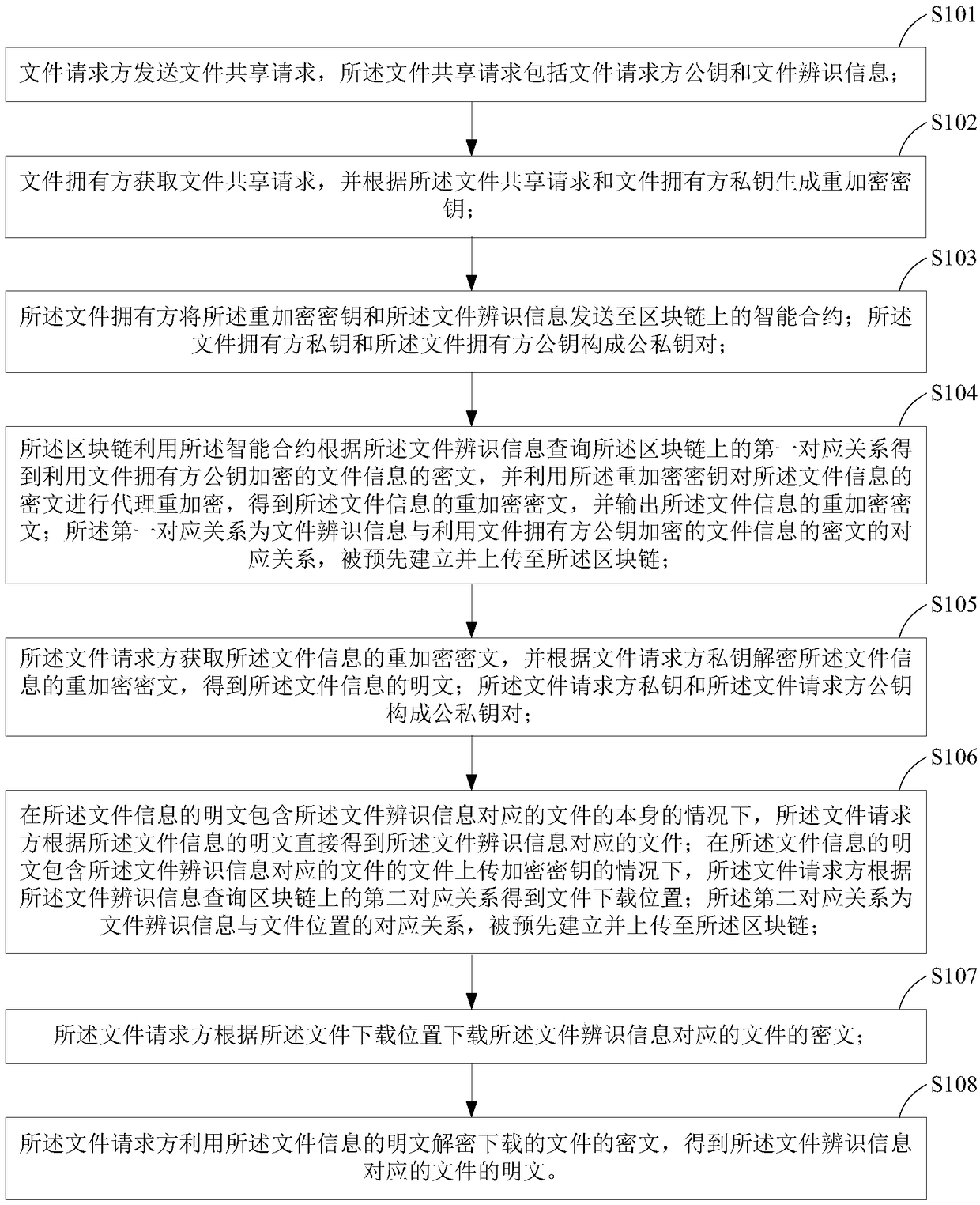
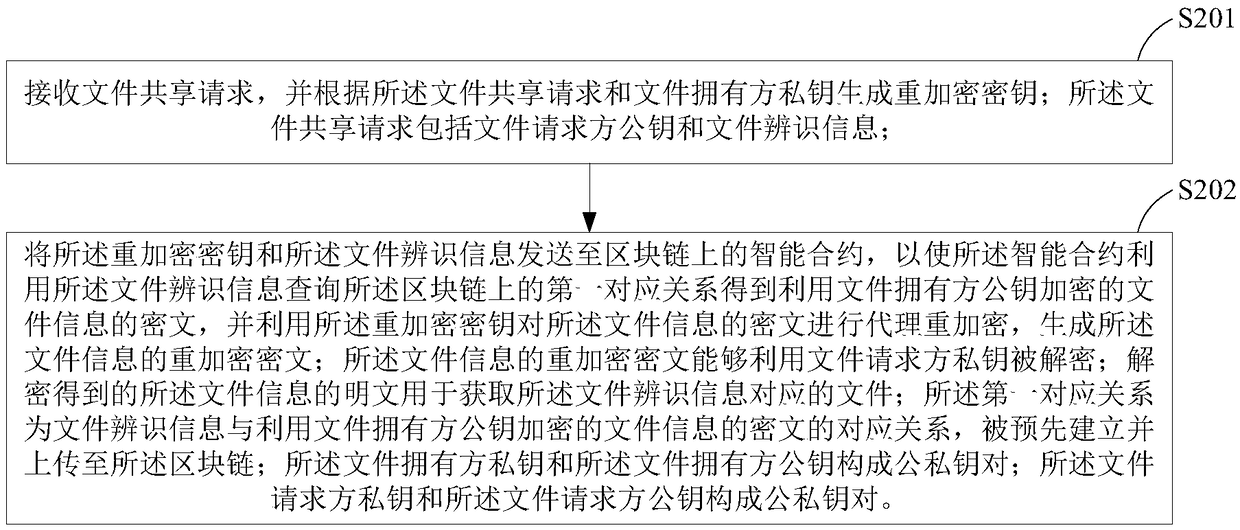
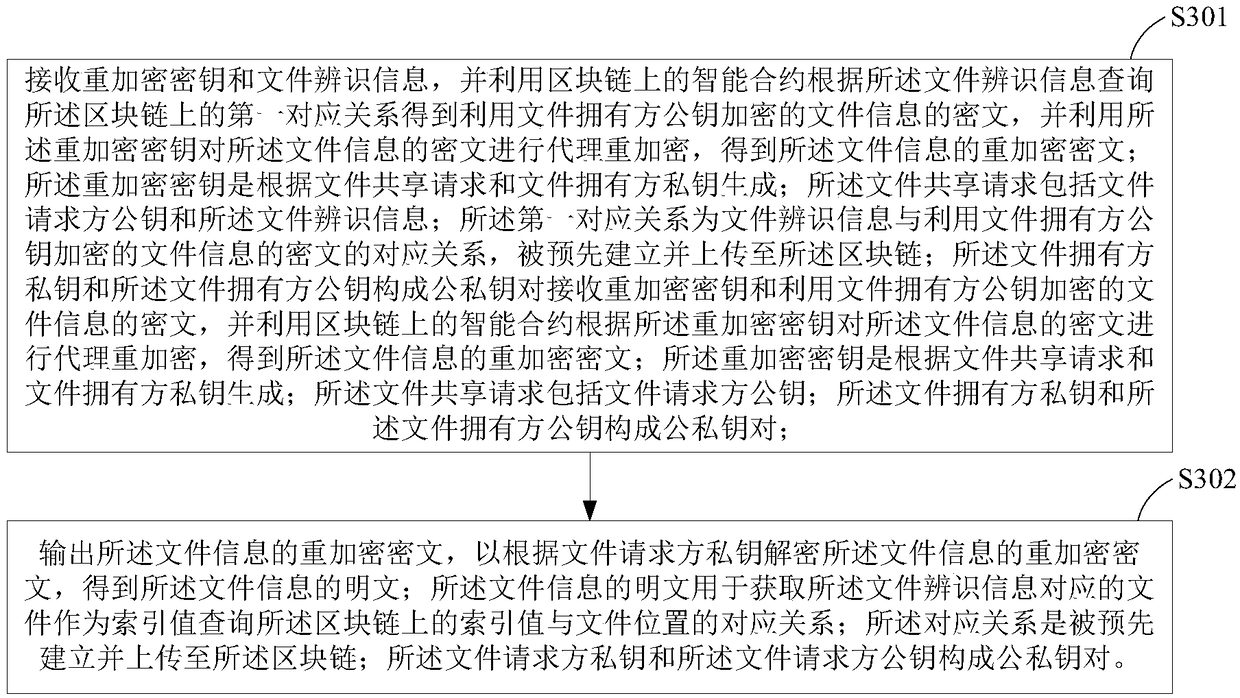
Authorized file share method and device
ActiveCN109144961AAchieve sharingTake advantage ofKey distribution for secure communicationDigital data information retrievalPlaintextSmart contract
The invention provides an authorized file sharing method and a device. The method comprises the following steps: generating a re-encryption key according to the file sharing request and the private key of the file owner, wherein the file sharing request includes a file requester public key and file identification information; sending the re-encryption key and the file identification information tothe smart contract on the block chain, so that the intelligent contract uses the file identification information to query the correspondence between the pre-established file identification information and the cipher text of the file information encrypted by the file owner's public key, obtaining the ciphertext of the file information encrypted by the public key of the file owner, and performing proxy re-encryption on the ciphertext of the file information by using the re-encryption key; the re-encrypted ciphertext being decrypted using the private key of the file requester. The plaintext of the decrypted file information is used for obtaining the file corresponding to the file identification information. The invention can protect data security and ensure data ownership by using block chain and proxy re-encryption.
Owner:JUZIX TECH SHENZHEN CO LTD
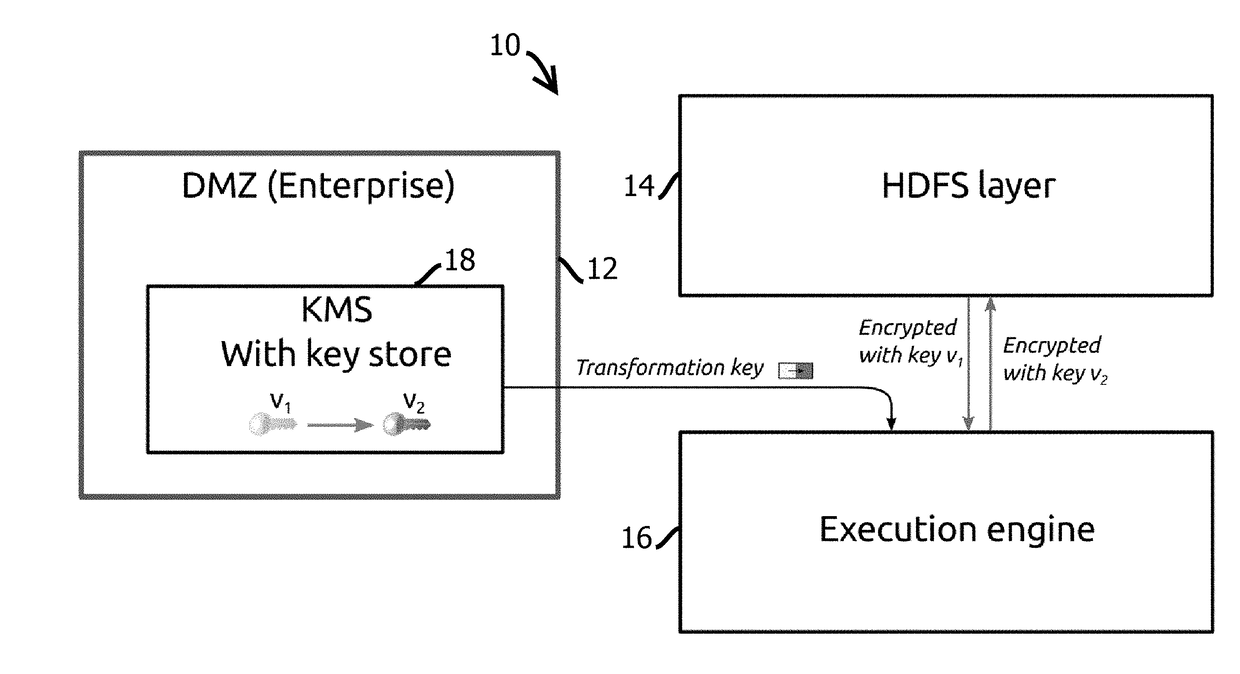
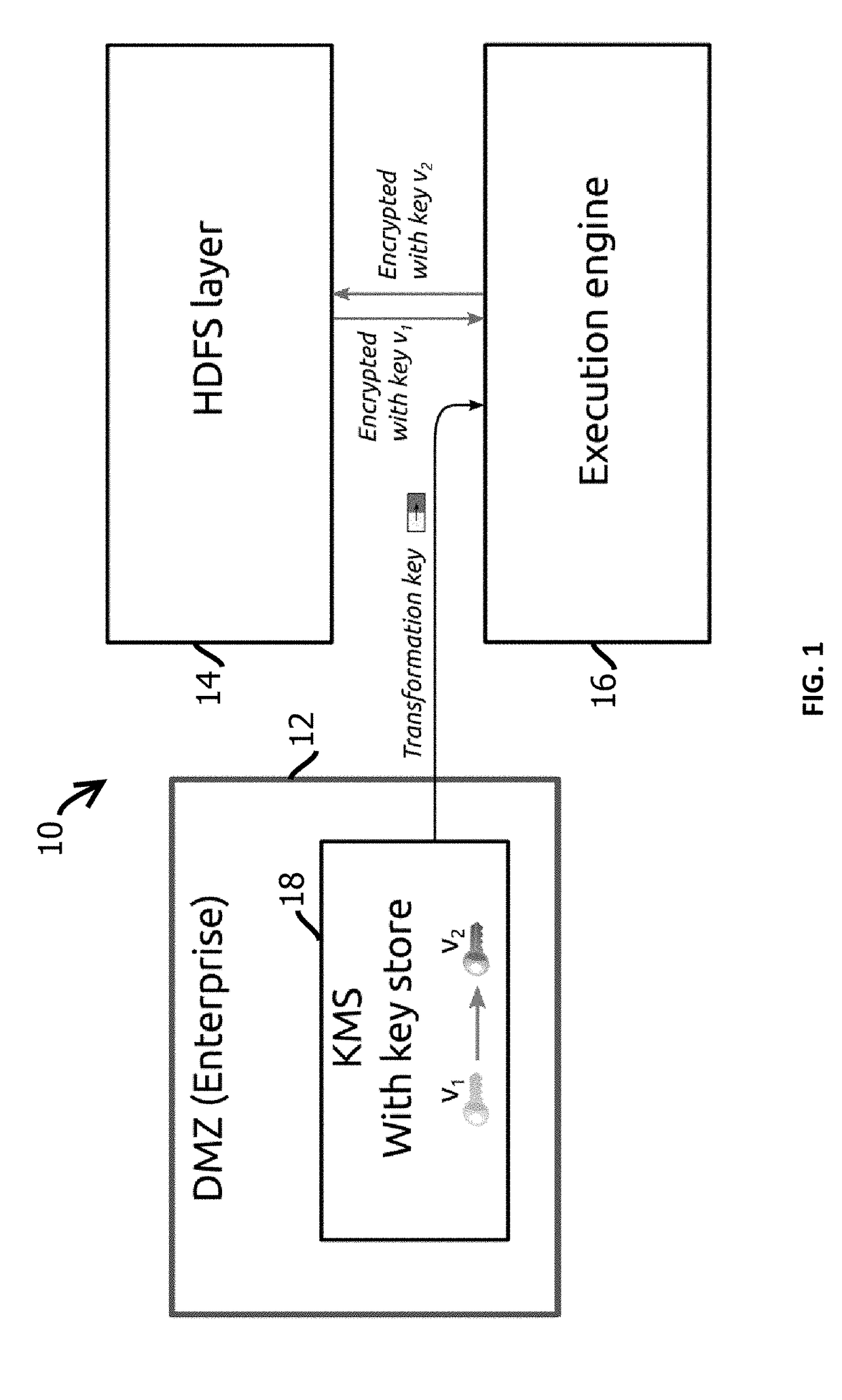
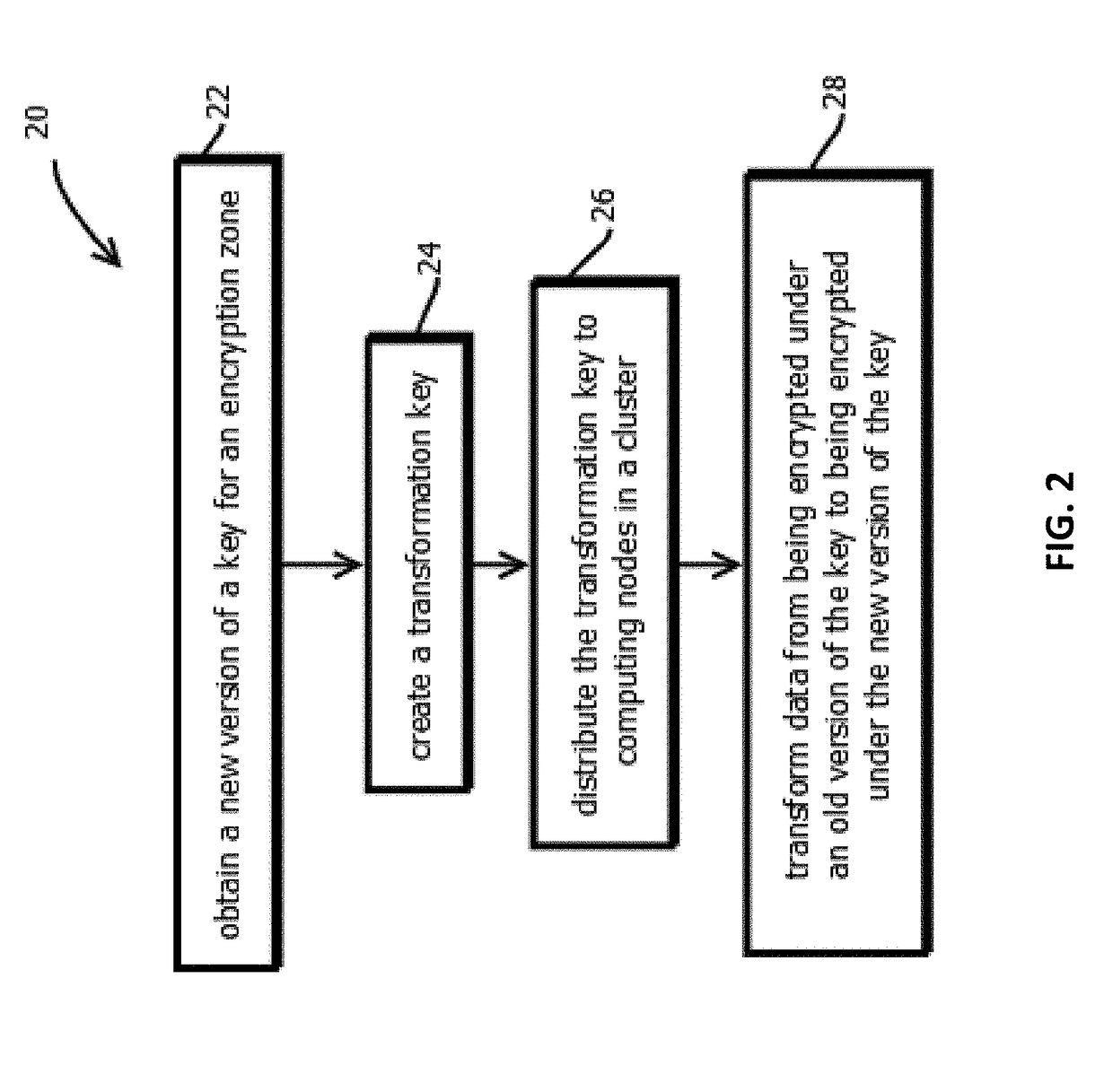
Method and system for secure delegated access to encrypted data in big data computing clusters
ActiveUS20180254901A1Key distribution for secure communicationMultiple keys/algorithms usageKey generationProxy re-encryption
Provided is a process including: encrypting each of a plurality of data encryption keys with a first public cryptographic key to form encrypted data encryption keys; obtaining a second public cryptographic key; generating a transformation key based on the first public-private cryptographic key pair and the second public cryptographic key; and transforming the encrypted data encryption keys with proxy re-encryption based on the transformation key; and obtaining the second private cryptographic key and the transformed encrypted data encryption keys.
Owner:ZERODB INC
Preservation of User Data Privacy in a Network
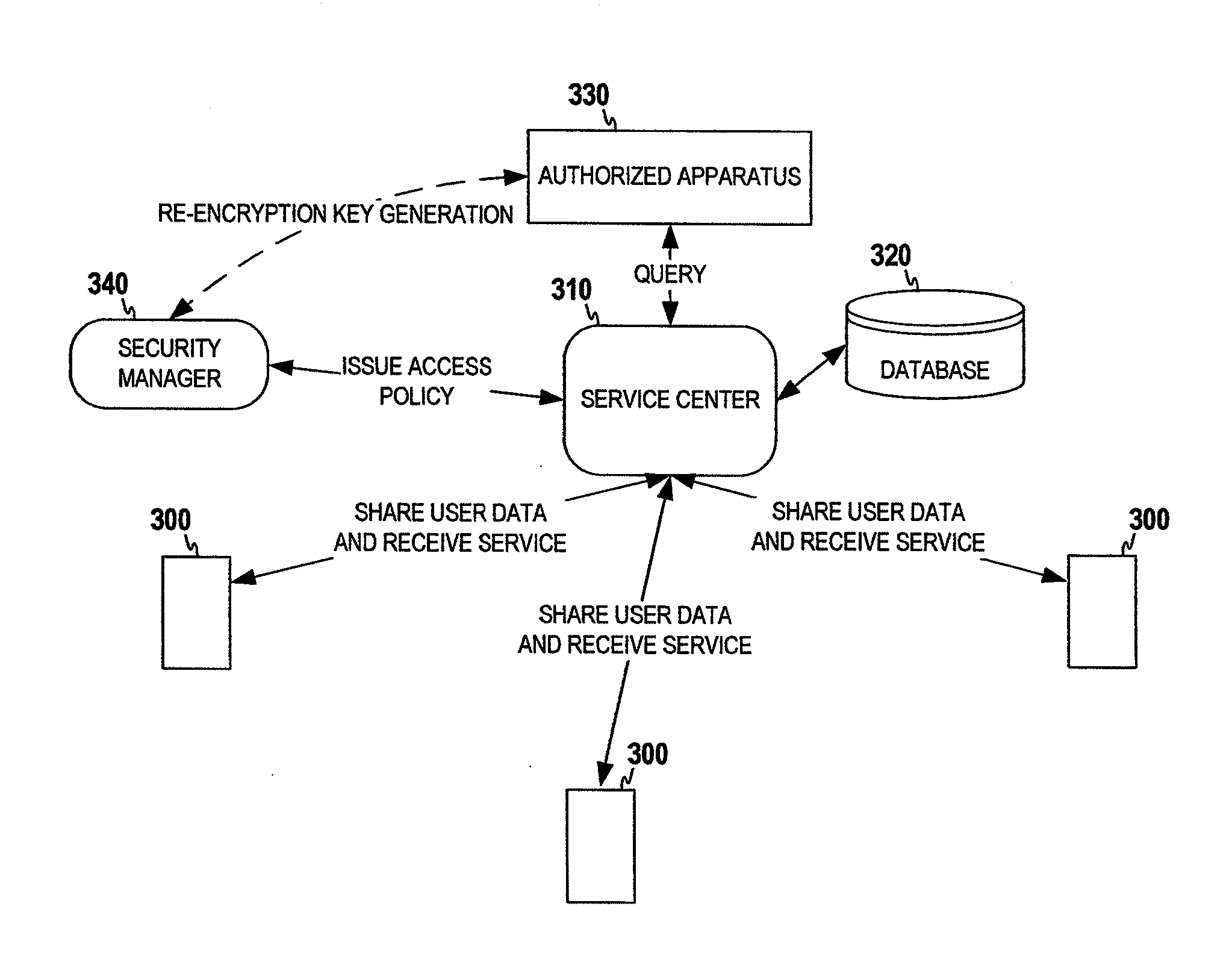
ActiveUS20120239942A1Privacy protectionLow costUnauthorized memory use protectionHardware monitoringProxy re-encryptionEncryption
An example apparatus is provided that receives a pseudonym and encrypted identifier, where the pseudonym is of a user's personal data. The pseudonym has been generated using a first secret key, and the encrypted identifier has been generated by encrypting the identifier using a second secret key. The first and second secret keys are known to other user(s) authorized to access the data, and are unknown to the apparatus. The operations also include storing the personal data in a database under the pseudonym, and indexed by the encrypted identifier. The keys used for encryption and pseudorandom generation can be provided by a second apparatus (e.g. an offline security manager), which may employ a proxy re-encryption scheme to provide proper keys to the apparatus based on access policies. Only the authorized users can decrypt the keys with their private keys, thus can query the user records stored in the apparatus.
Owner:NOKIA TECHNOLOGLES OY
Encryption techniques for improved sharing and distribution of encrypted content
In an embodiment, content may be encrypted by a first device using a dual hash chain technique, where the first device maintains a forward hash chain and a second device maintains a backward hash chain, and content keys for encrypting content are derived using values of the forward and backward hash chains. The second device may not have knowledge of a seed used to generate the forward hash chain, and therefore may be unable to generate the content keys, reducing a likelihood that the encrypted content becomes compromised. Additionally, embodiments provide for techniques for using proxy re-encryption (PRE) to re-encrypt content, such that the encrypted content may be provided to and decrypted by a requesting device without knowledge of the forward and backward hash chains. Additionally, embodiments provide techniques for distributing encrypted content to a requesting device with fine-grained access control.
Owner:HONG KONG APPLIED SCI & TECH RES INST
Systems and methods of blockchain platform for intermediaries and passwordless login
InactiveUS20200313856A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesInternet privacyEngineering
The systems and methods on a blockchain platform for one or more intermediaries for services including proxy re-encryption, independent audit, multiple-signatures based smart wallet associated with a smart contract and split-key authentication to achieve secure passwordless login. Proxy re-encryption by receiving a ciphertext from a first user with condition parameters that has been encrypted with a dynamically selected encryption algorithm. Audit service receiving an encrypted file from a user for storage on the blockchain platform; enforcing the security policy parameters for all access requests to the file on the blockchain platform; and optionally providing audit report of the encrypted file storage and access. A smart wallet with a group key using multiple signatures based on receipt of a threshold number of signatures. Split-key authentication by splitting the private key into two or more parts; and assigning the split private key part to two or more client devices.
Owner:0CHAIN LLC
Attribute-based ciphertext searching system and method in support of proxy re-encryption
ActiveCN108418681AImplement fine-grained descriptionPrivacy protectionKey distribution for secure communicationAccess structureConfidentiality
The invention discloses an attribute-based ciphertext searching system and method in support of proxy re-encryption. According to the method, two functions that a user securely carries out searching and effectively shares searching authority in a cloud environment are realized at the same time. According to the method, through adoption of an LSSS linear secret sharing scheme, an attribute of an access user can be described in fine granularity, and the relatively high computing efficiency is achieved. In a threshold generation phase, a blind technology is carried out on a user key through utilization of a random value, and then the user key is submitted to a cloud server, so the confidentiality and security of the user key are ensured. A searching authority entrusting problem when an authorization user is offline in practical application is taken into consideration. A proxy re-encryption technology is imported, and the cloud server converts a ciphertext, so the encryption / decryption pressure of a data owner is migrated, and the system efficiency is greatly improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
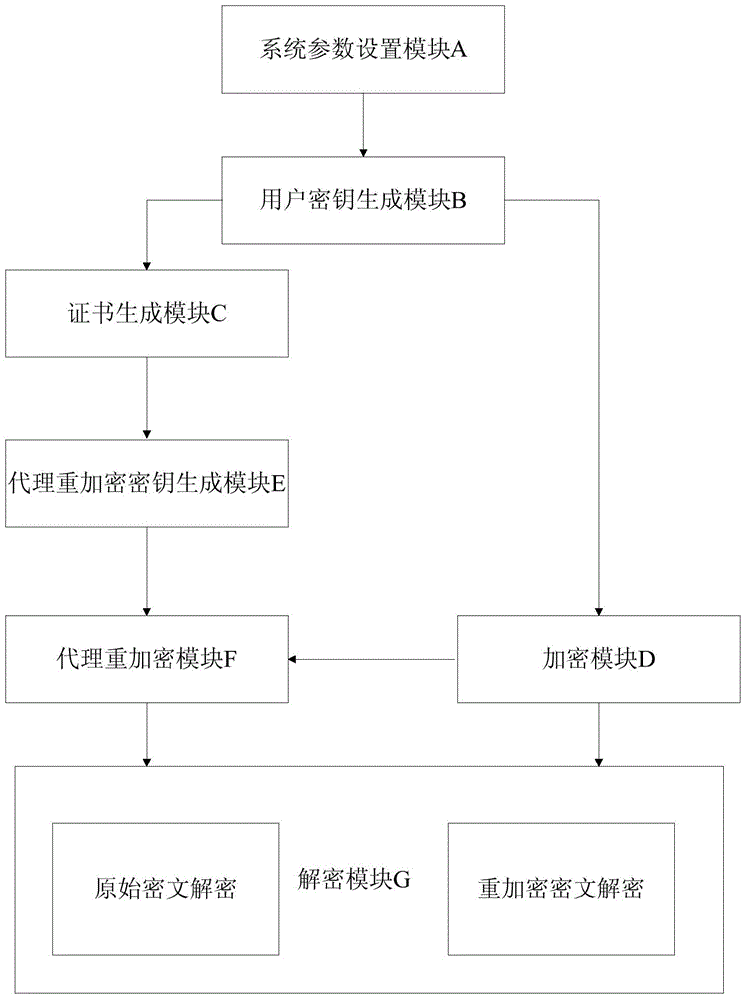
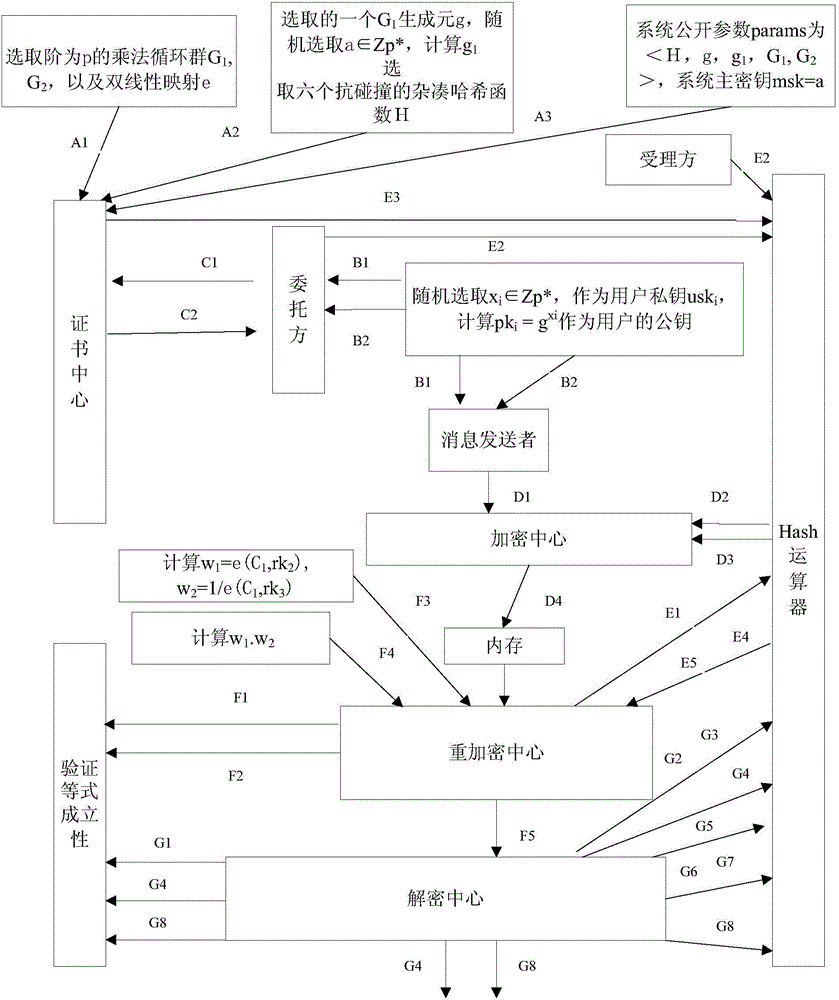
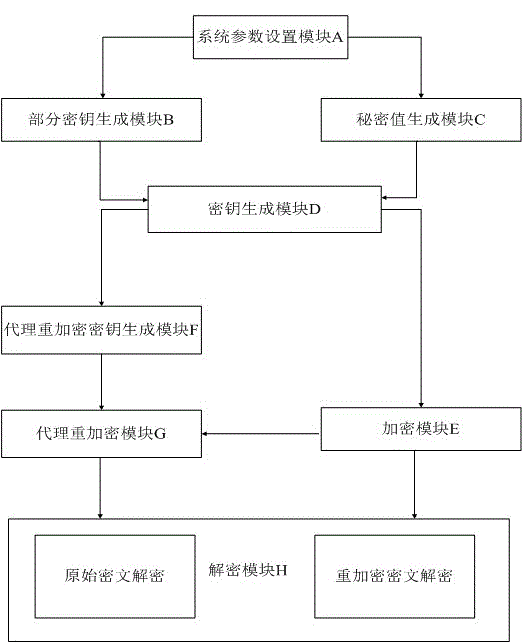
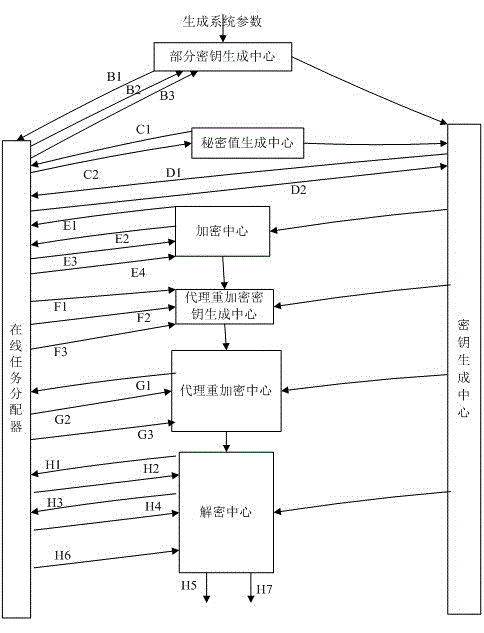
Proxy re-encryption method and system on basis of certificate conditions
InactiveCN104363218ASimplify the management processControl re-encryption capabilitiesTransmissionPlaintextCryptographic key generation
The invention discloses a proxy re-encryption system on the basis of certificate conditions. The proxy re-encryption system comprises a system parameter setting module, a user key generation module, a certificate generation module, an encryption module, a proxy re-encryption key generation module, a proxy re-encryption module and a decryption module, wherein the system parameter setting module generates a system master key and system public parameters; the user key generation module generates public keys and private key pairs of various users; the certificate generation module endorses the identity of the users and the public keys and generates certificates of the users; the encryption module is used for encrypting messages and transmitting the messages to the decryption module and the proxy re-encryption key generation module; the proxy re-encryption key generation module generates proxy re-encryption keys and transmits the same to the proxy re-encryption module; the proxy re-encryption module re-encrypts original cryptographs to generate re-encryption cryptographs to be transmitted to the decryption module; the decryption module restores corresponding plaintexts. The invention further discloses a proxy re-encryption method on the basis of certificate conditions. On the premise of guaranteeing safety of the system, the original cryptographs can be flexibly subjected to proxy re-encryption, and rights of proxies are strictly controlled.
Owner:HOHAI UNIV
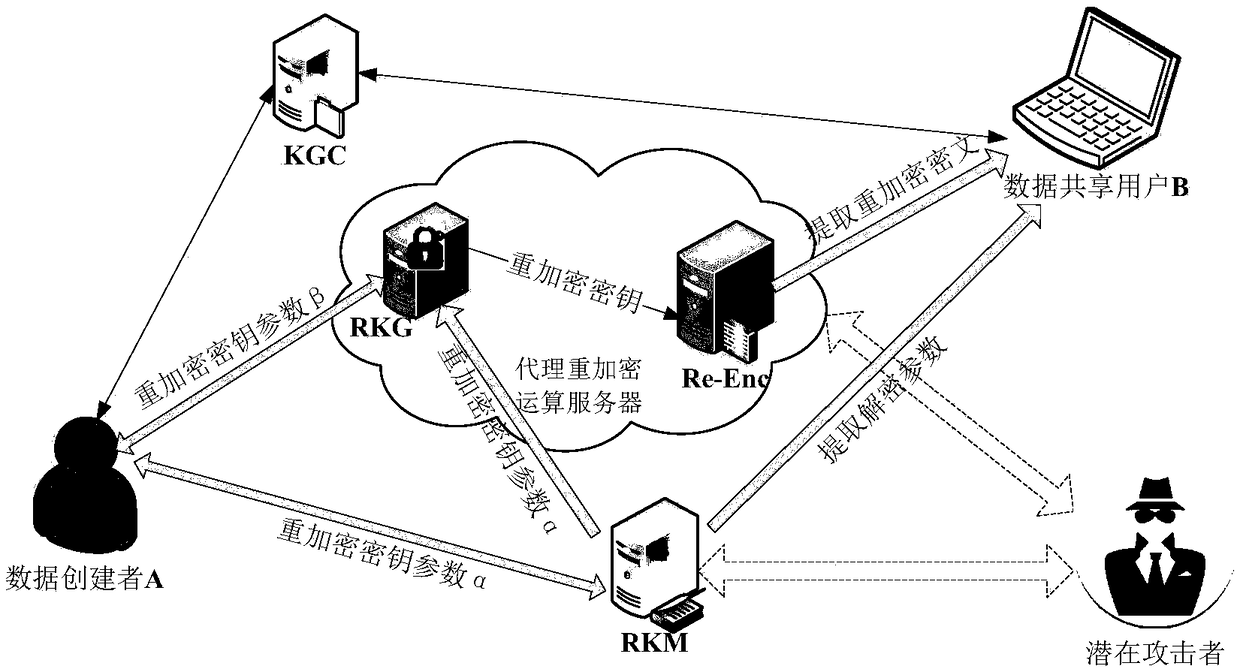
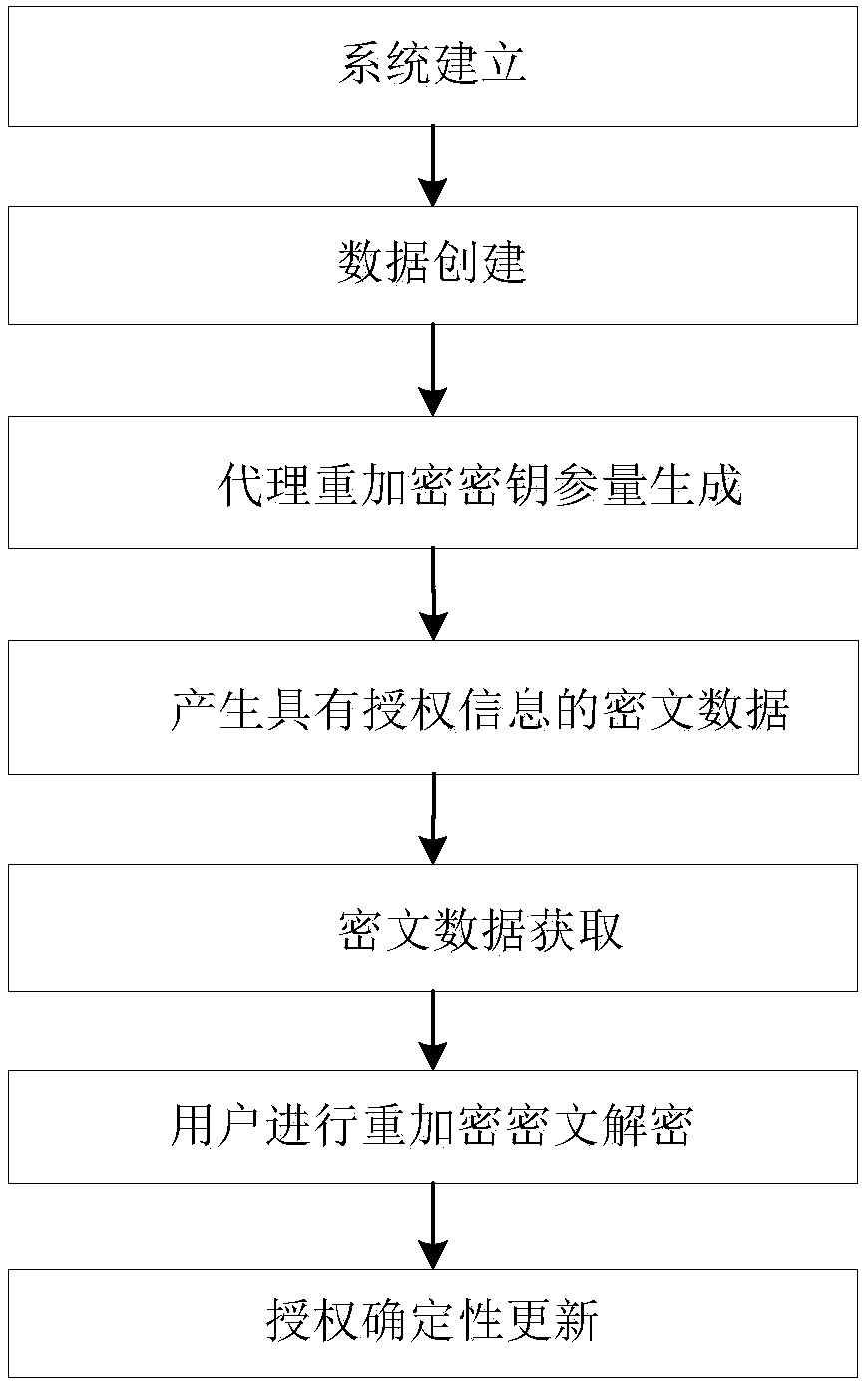
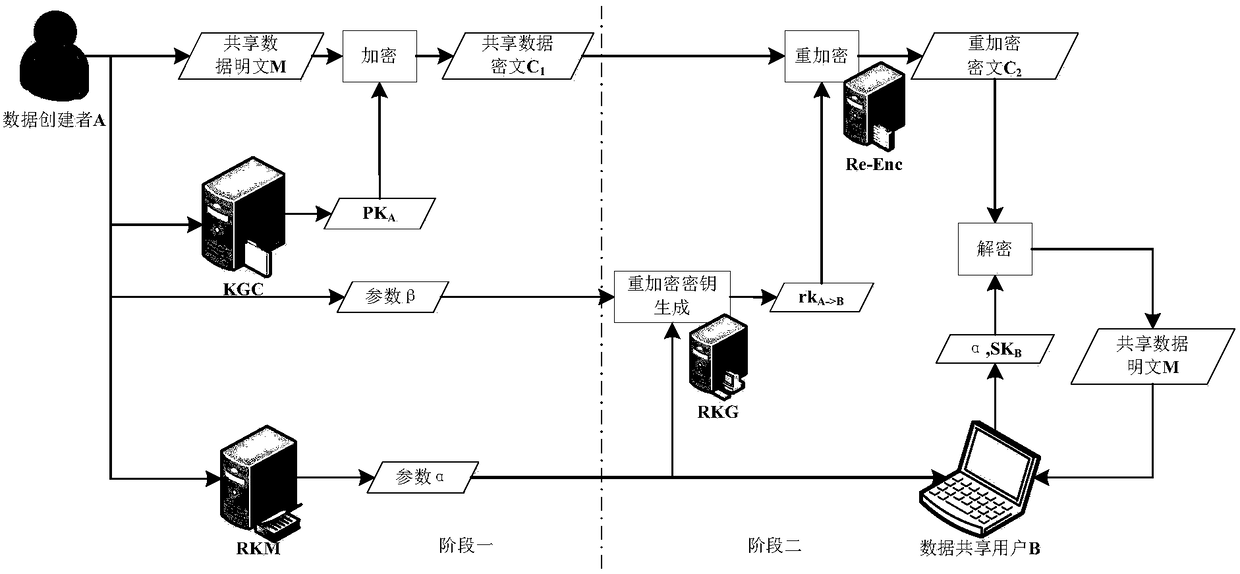
Data authorization deterministic update method based on proxy re-encryption for cloud
ActiveCN108600217ALighten the burden on the cloudKey distribution for secure communicationCloud dataData sharing
The invention relates to a data authorization deterministic update method based on proxy re-encryption for a cloud. The method is realized based on a system model, and the system model comprises a KGCserver, an RKM server, an RKG server and an RE-Enc server; the method comprises the following steps of establishing a system; creating data; generating proxy re-encryption key parameters; generatingciphertext data with authorization information; obtaining the ciphertext data; carrying out re-encryption ciphertext decryption by a user; and updating authorization deterministic. According to the method, the proxy re-encryption is introduced into the cloud data sharing and authorization update, and authorization management of the data is carried out by managing a re-encryption key; and the key management difficulty and the calculation amount of the user during data sharing and authorization management are reduced, and meanwhile, the re-encryption key is segmented and managed, and the deterministic update of the key is realized when the authorization is changed.
Owner:NANJING UNIV OF SCI & TECH
Certificateless condition based proxy re-encryption system and method
The invention discloses a certificateless-condition-based proxy re-encryption system and method. A certificateless public key system and a proxy re-encryption system are combined together, so that certificate management is avoided and problems in secrete key distribution and escrow are eliminated. In a condition of ensuring encryption safety, online re-encryption is performed flexibly and the re-encryption capability of a proxy center is controlled, so that only ciphertext meeting specific conditions can be re-encrypted effectively. At the same time, since the certificateless public key system is used, the system and method provided by the invention have advantages of traditional public key encryption and identify-based encryption and are good in performance and convenient in application in an open network environment. The novel system and method provided by the invention are safe and efficient.
Owner:HOHAI UNIV
Proxy-based encryption method, proxy-based decryption method, network equipment, network device and system
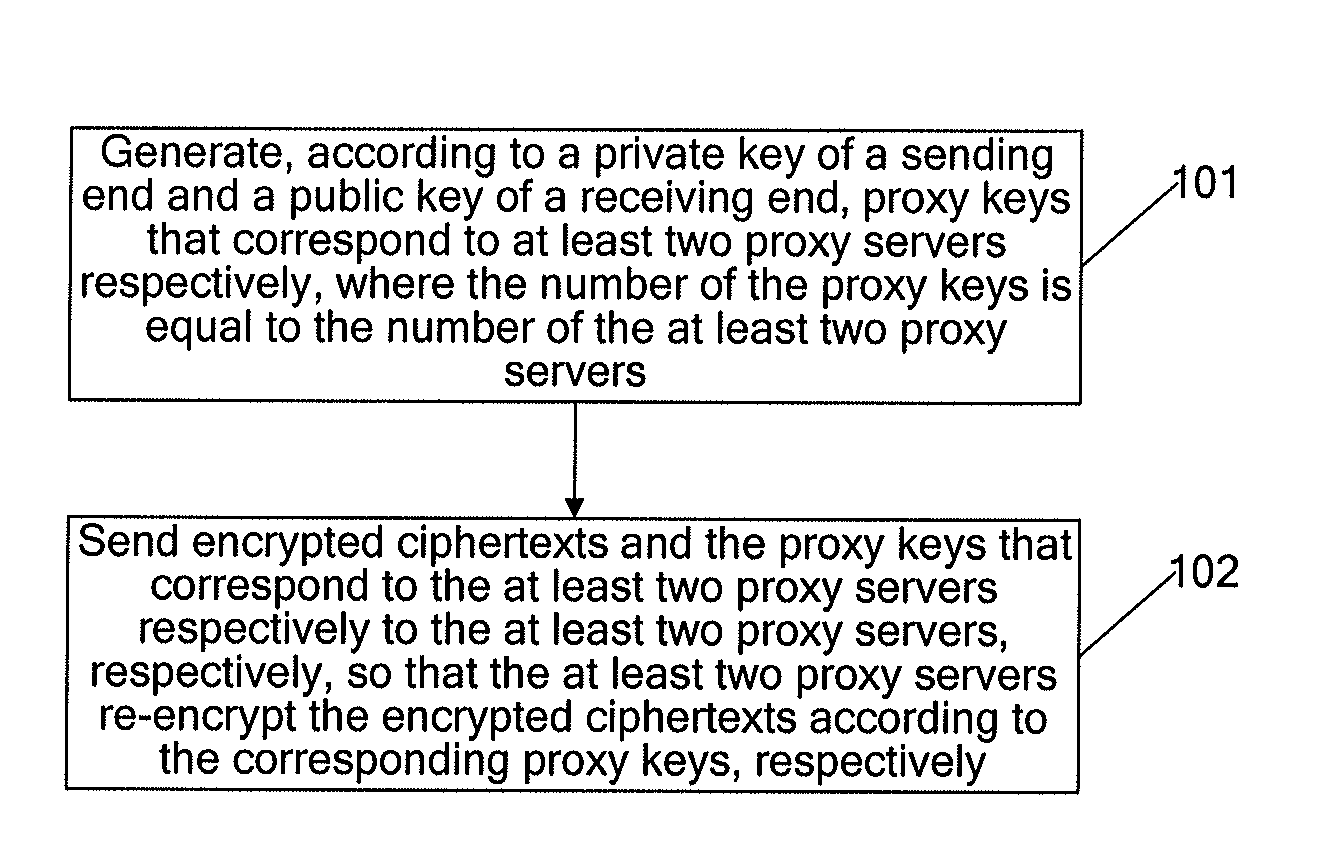
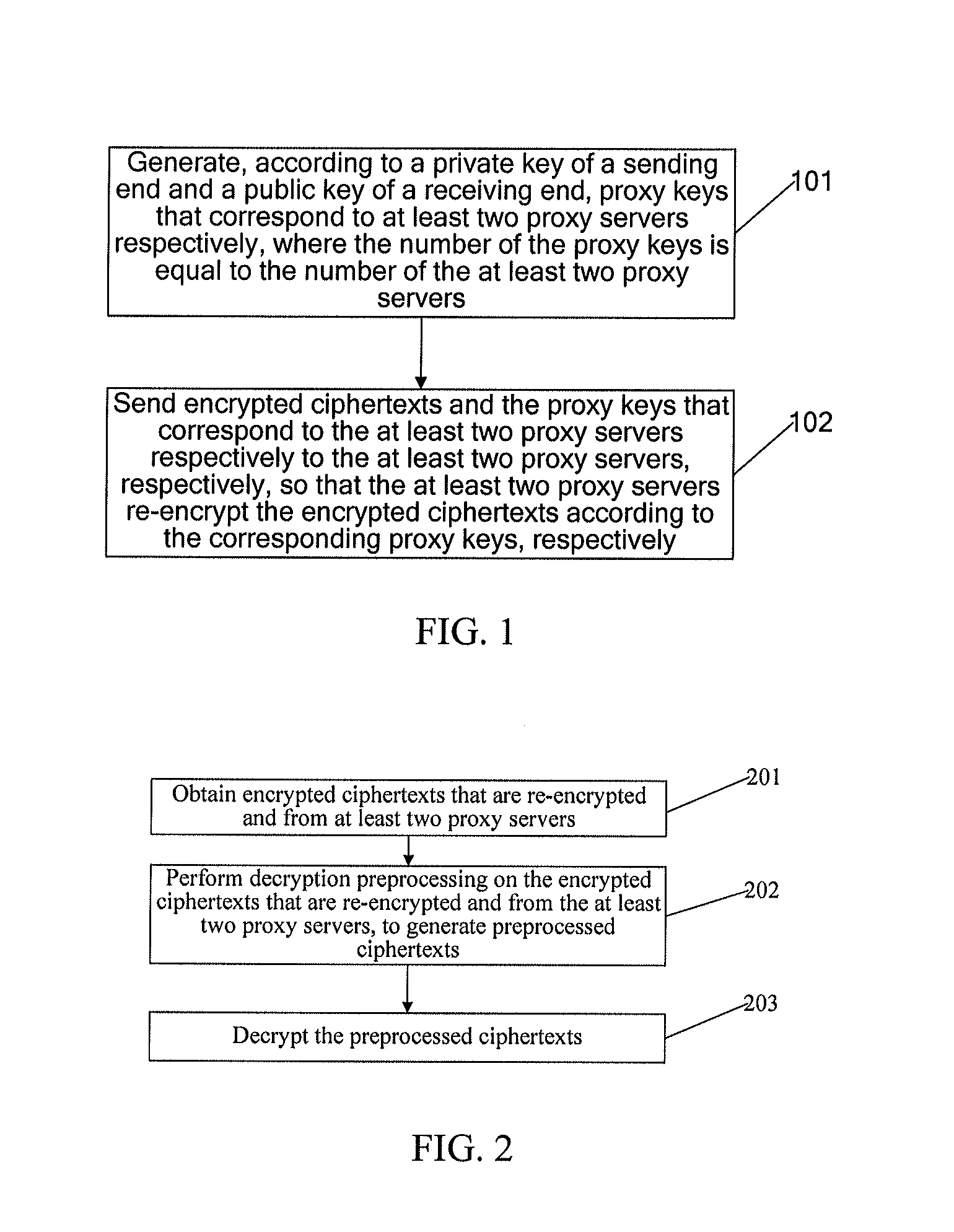
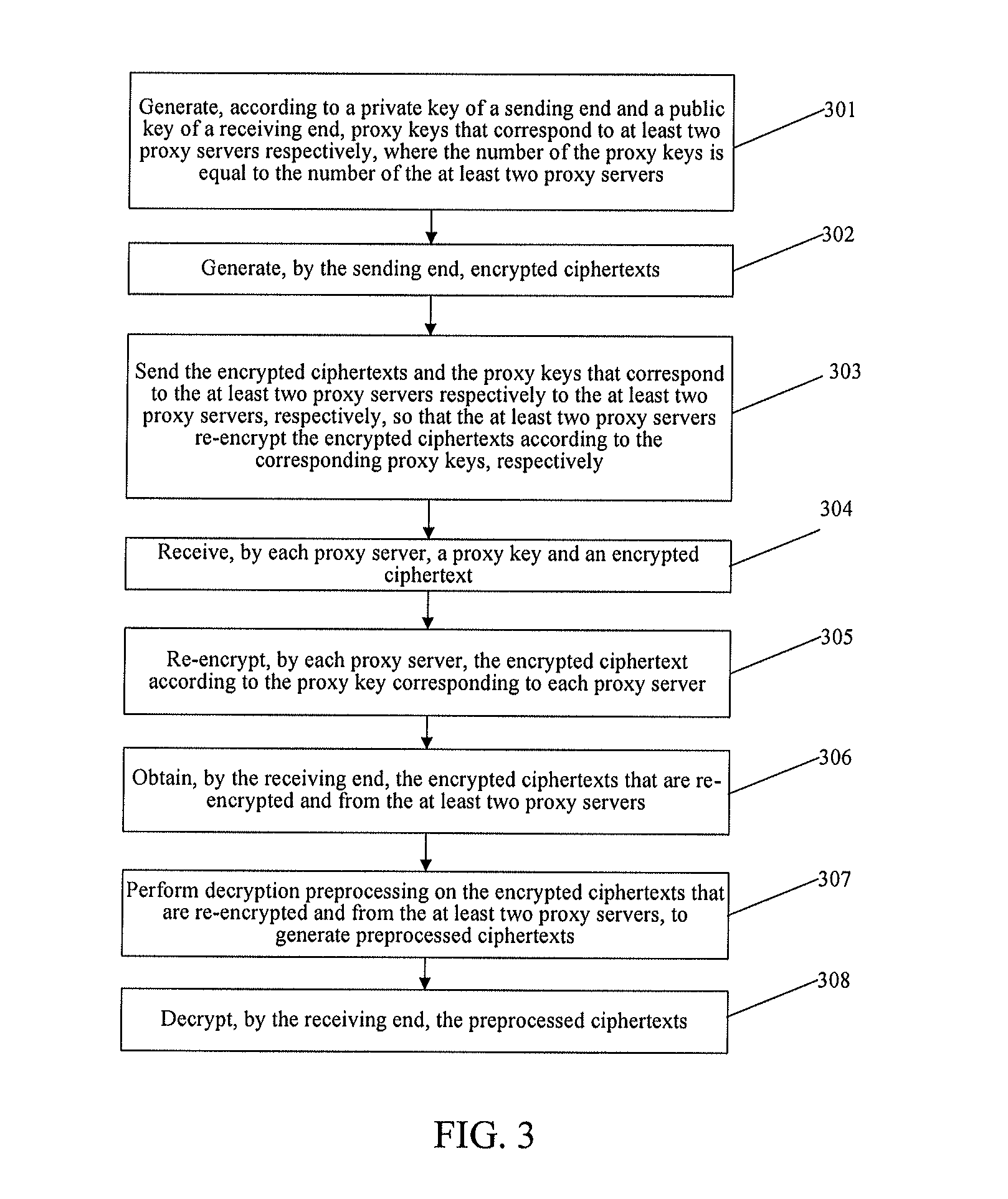
InactiveUS20130156188A1Improve reliabilityImprove securityKey distribution for secure communicationSecret communicationProxy serverProxy re-encryption
A proxy-based encryption method includes generating, according to a private key of a sending end and a public key of a receiving end, proxy keys that correspond to at least two proxy servers, respectively. The number of the proxy keys is equal to the number of the proxy servers. The method further includes sending encrypted ciphertexts and the proxy keys that correspond to the at least two proxy servers respectively to the at least two proxy servers, respectively, so that the at least two proxy servers re-encrypt the encrypted ciphertexts according to the corresponding proxy keys.
Owner:HUAWEI TECH CO LTD
An encrypted image retrieval method supporting multiple keys
ActiveCN109543061AProtect privacy and securityImprove retrieval speedKey distribution for secure communicationMetadata still image retrievalFeature vectorPlaintext
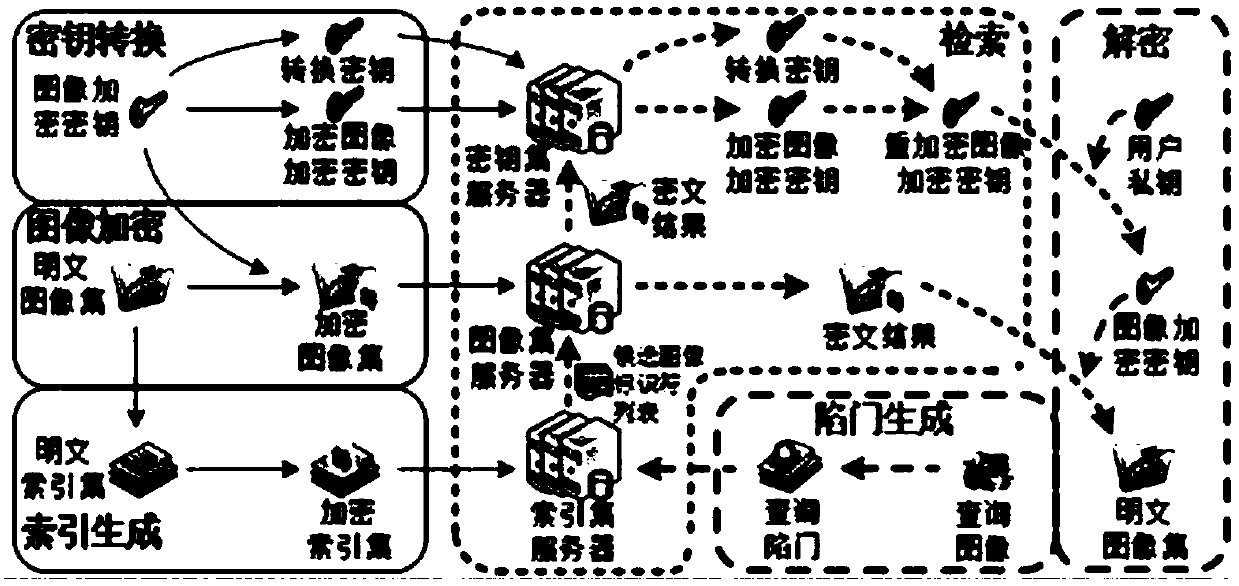
The invention discloses an encrypted image retrieval method supporting multiple keys. The invention utilizes proxy re-encryption technology to convert different image encryption keys into the form that the inquiry user can decrypt with his private key, applies local sensitive hash algorithm to pre-classify the image set, improves the retrieval speed, and then encrypts the image feature vector withthe safe nearest neighbor algorithm to improve the retrieval precision. The invention supports a query user to query image sets from different encryption keys by using a query trap under a multi-keyscenario, and the user can only decrypt the query result by using a legal private key. The invention can protect data privacy and safety, and the cloud server cannot obtain any plaintext information from the ciphertext set, the index set and the ciphertext key set, nor can it obtain any plaintext information from the query trap. The invention is efficient and feasible in practical application.
Owner:XIDIAN UNIV
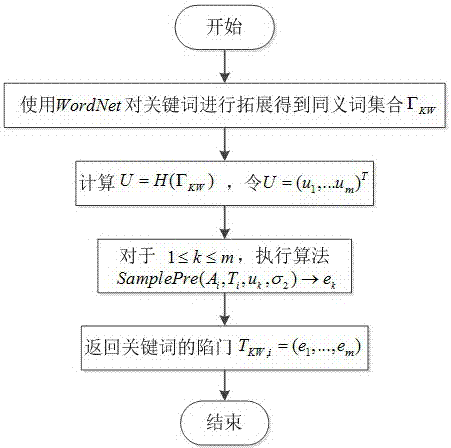
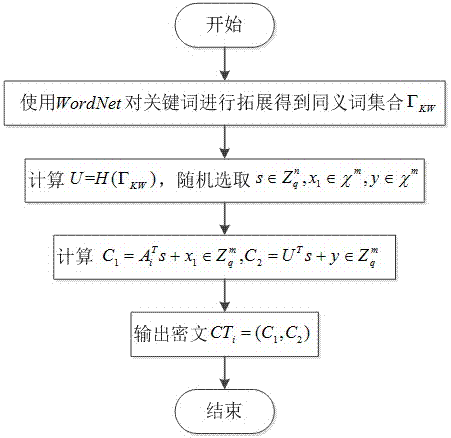
Semantic searchable encryption method for proxy re-encryption resistant to post quantum attack
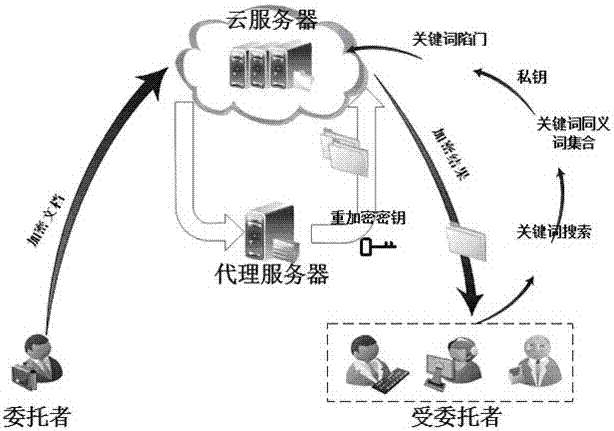
ActiveCN106921674AIncrease flexibilityCan't searchDigital data protectionCryptographic attack countermeasuresUser inputPassword
The invention relates to a semantic searchable encryption method for proxy re-encryption resistant to a post quantum attack. According to the method, synonym extension is performed on a search keyword input by a user, so that relative keywords semantically similar to the original input keyword can be found, extension query is beneficial to matching more relative documents, and flexibility of search can be effectively enhanced; search permission proxy can be supported via a proxy re-encryption mechanism; a data owner utilizes unidirectional proxy re-encryption to consign own search permission to the other user, the consignee can search encrypted data of the consignor, and the consignor cannot search the data of the consignee; the function of resisting the post quantum attack is achieved by a lattice-based password technology, and security of cloud storage is improved. According to the scheme of the method provided by the invention, the problems that existing searchable schemes are low in query efficiency, limited in search permission and unable to resist quantum attack are effectively solved.
Owner:FUZHOU UNIV
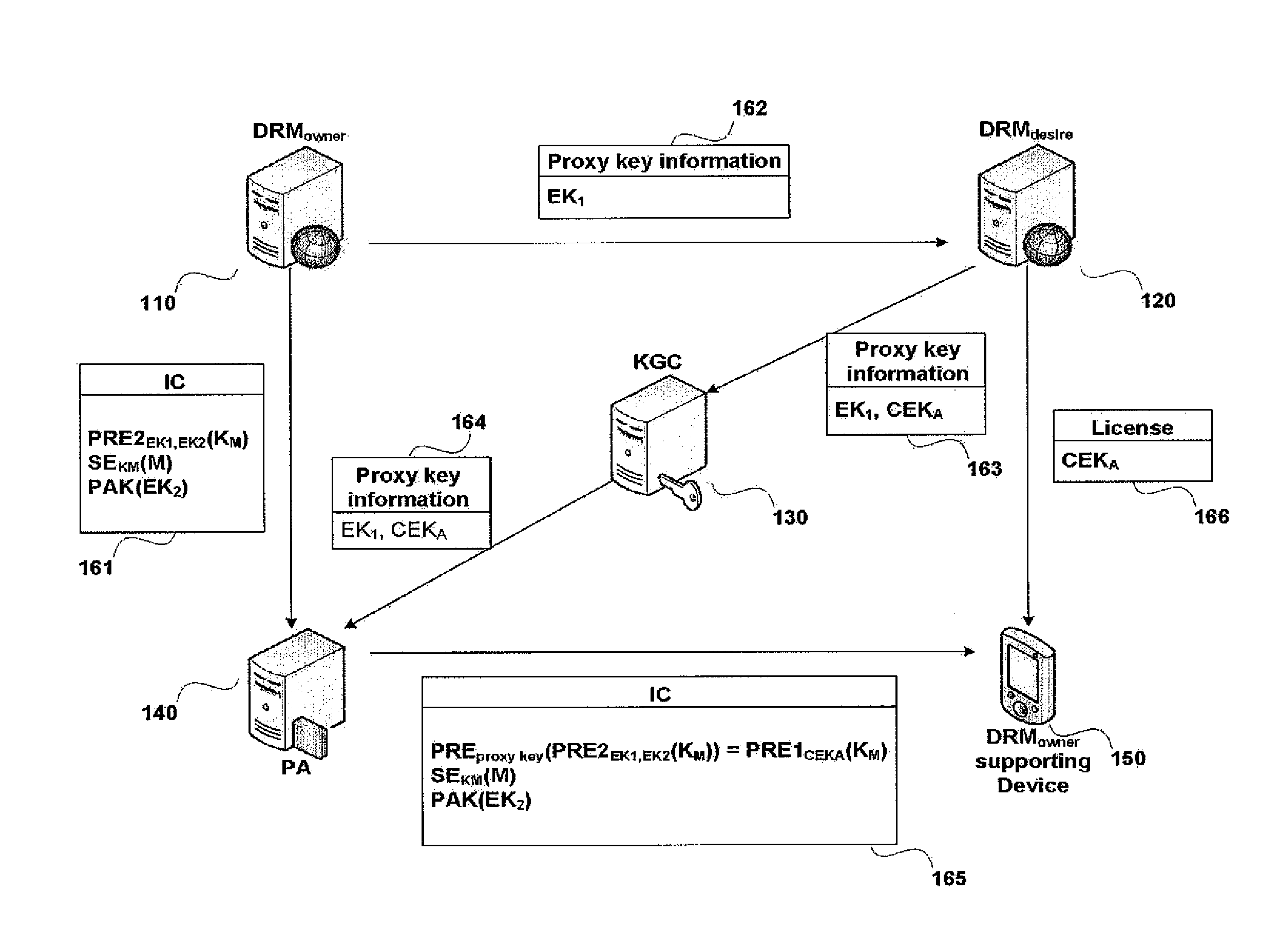
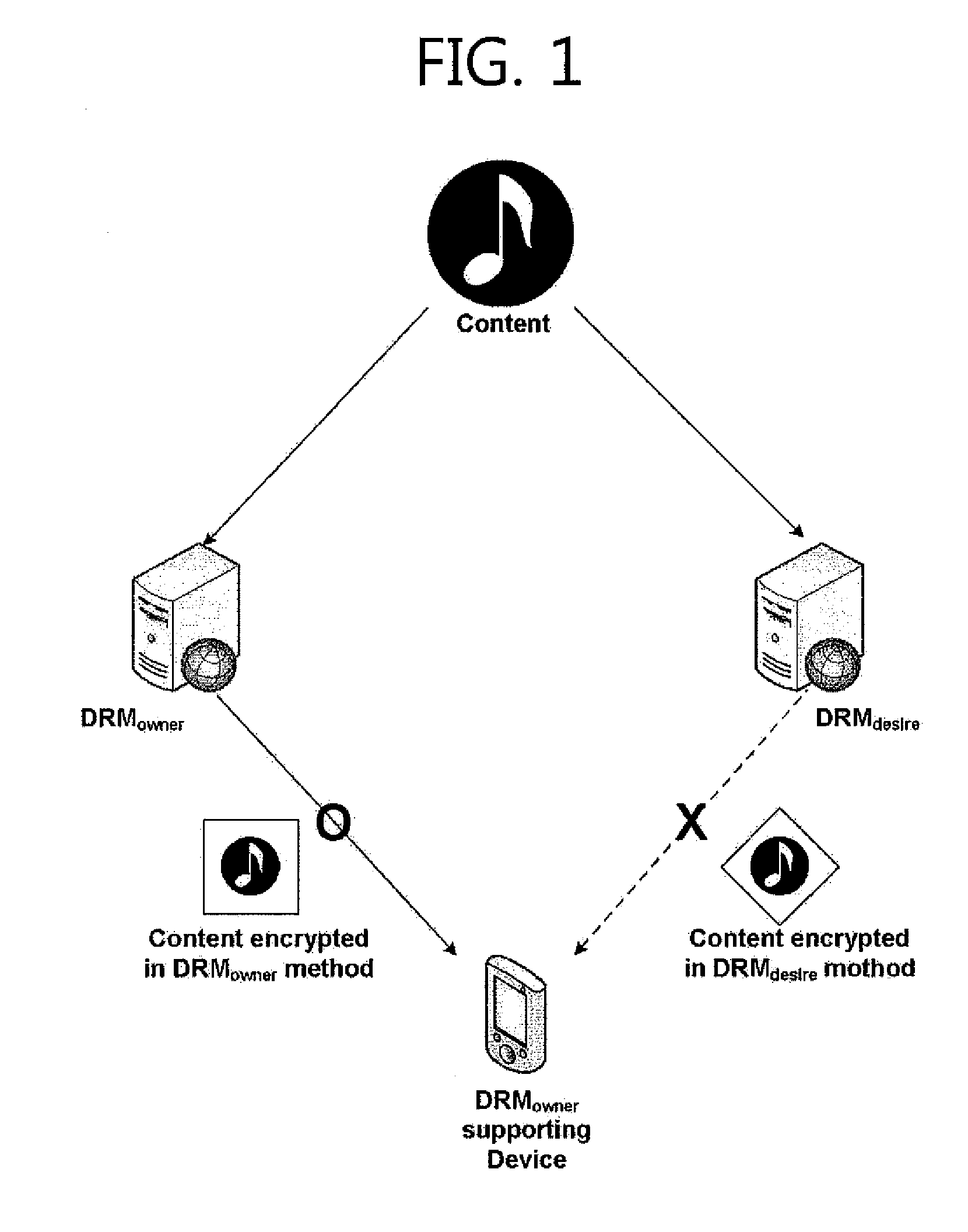
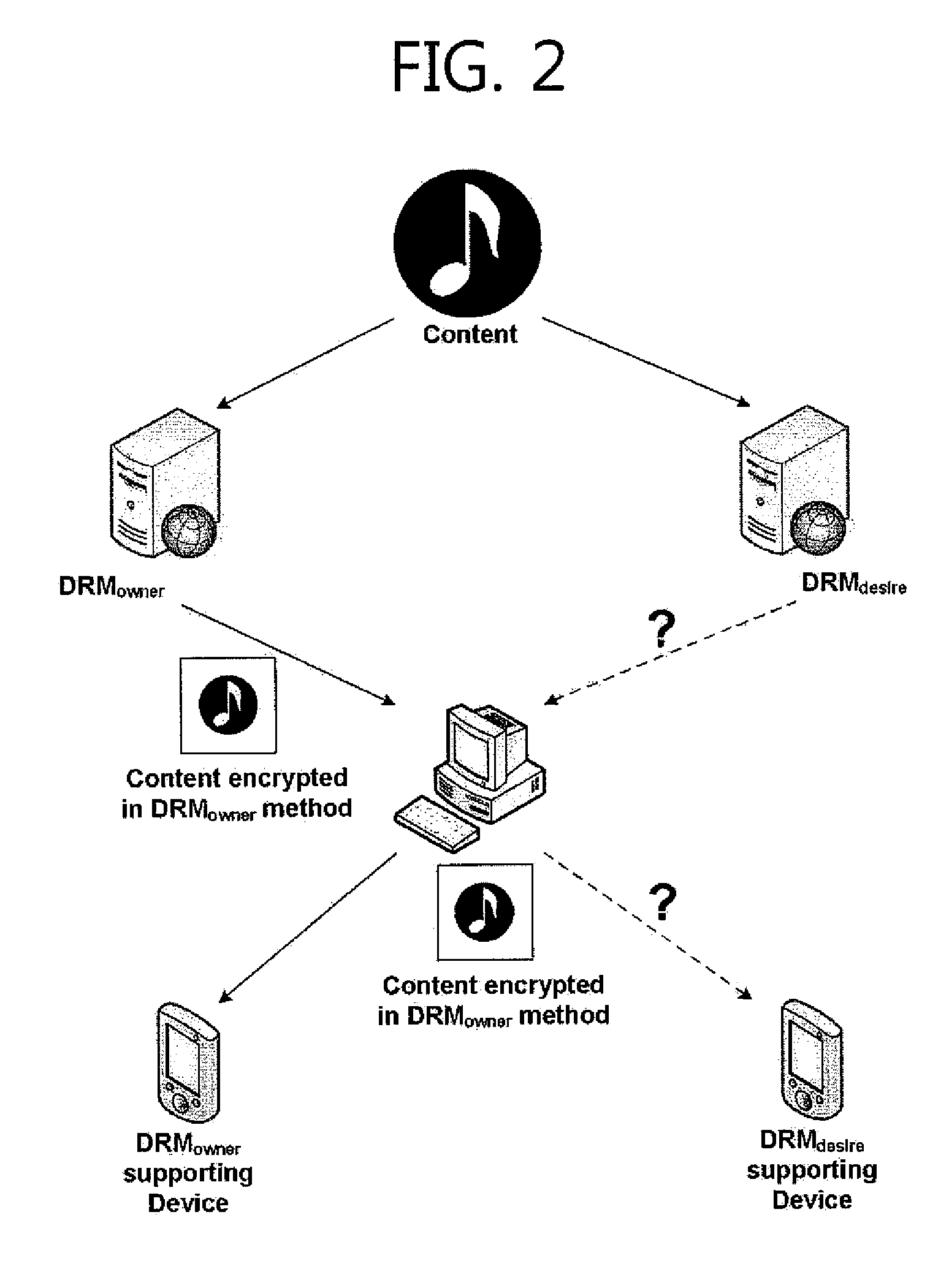
Methods and apparatuses for providing DRM interoperability
InactiveUS8386799B2Unauthorized memory use protectionHardware monitoringComputer networkService provision
Methods and apparatuses for providing DRM interoperability are provided. Proxy re-encryption technique using bilinear map is used, and the same content can be used in different devices. According to the method of providing DRM interoperability includes in proxy agent with respect to digital rights management (DRM) service providers and device which supports predetermined DRM, first DRM service provider, second DRM service provider, the proxy agent, and the device identify each other, and proxy re-encrypt an interoperable content (IC) and provide the IC to the device. The IC is second-level encrypted by using a key of the first DRM service provider, and the proxy re-encryption is performed by using a proxy key generated from proxy key information provided from the first DRM service provider and the second DRM service provider. Therefore, a problem in which interoperability cannot be guaranteed since a DRM technique depends on a service provider is resolved.
Owner:POSTECH ACAD IND FOUND
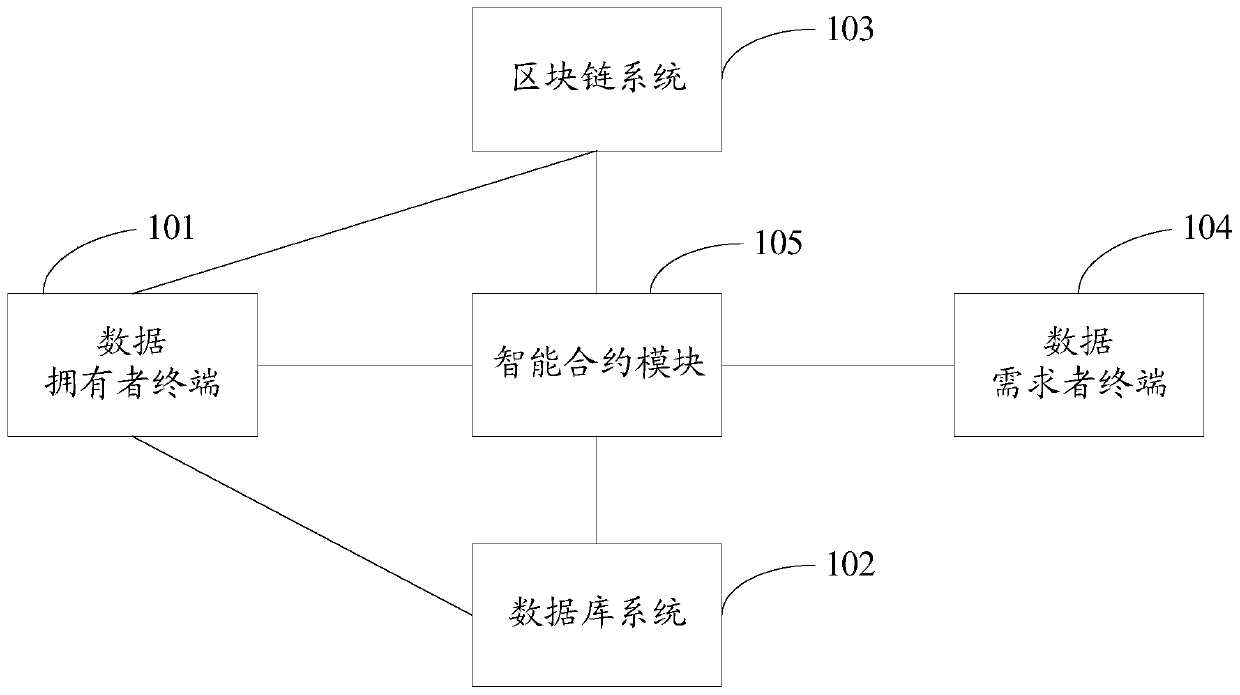
Blockchain data transaction system and method based on proxy re-encryption and smart contract
ActiveCN110430186AGuaranteed privacy and securityRealize economic valueKey distribution for secure communicationFinanceTransaction dataData needs
The invention discloses a blockchain data transaction system and a blockchain data transaction method based on proxy re-encryption and an intelligent contract. The system comprises a data owner terminal, a database system, a blockchain system, a data demander terminal and an intelligent contract module. According to the method, the security privacy of the transaction data can be ensured by using the proxy re-encryption technology, and the efficient and automatic execution of the data transaction can be realized by using the smart contract, so that the security privacy and efficiency problems of the blockchain data transaction are solved. The economic value of the data is realized, and the application value of the data is brought into full play.
Owner:STATE GRID E COMMERCE CO LTD +2
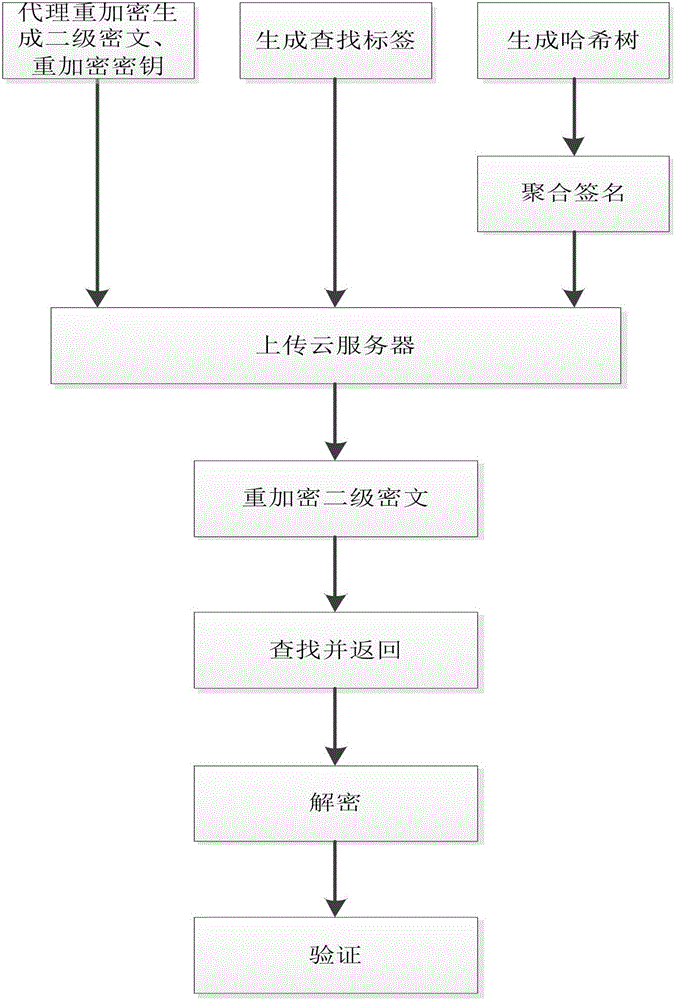
Multiple users-based outsourcing database audit method
InactiveCN106452748AImprove privacy protectionReduce the burden onKey distribution for secure communicationUser identity/authority verificationPlaintextData privacy protection
The present invention discloses a multiple users-based outsourcing database audit method, aiming to solve problems of low signature verification efficiency and complex decryption in the prior art. The method comprises a first step that a data owner encrypts data by using a proxy re-encryption method so as to form a second-level ciphertext, generates a re-encryption secret key by inquiring a public key of a user, generates a searching label by using an Evdokimov encryption manner, and generates hash tree root signature by using aggregate signature; and the signature, second-level ciphertext, re-encryption secret key and the searching label are transmitted to a cloud server; a second step that the cloud server encrypts the second-level ciphertext so as to generate a first-level ciphertext; a third step that a user sends a search request to the cloud server, and the cloud server searches and returns a corresponding first-level ciphertext; and a fourth step that the user decrypts the first-level ciphertext so as to form a plaintext, and performs aggregate verification on the plaintext. Through adoption of the method, the burden on the data owner is greatly reduced, interaction is reduced for one time, data privacy protection is improved, and the method can be applied to safe data outsourcing in a cloud calculation environment.
Owner:XIDIAN UNIV
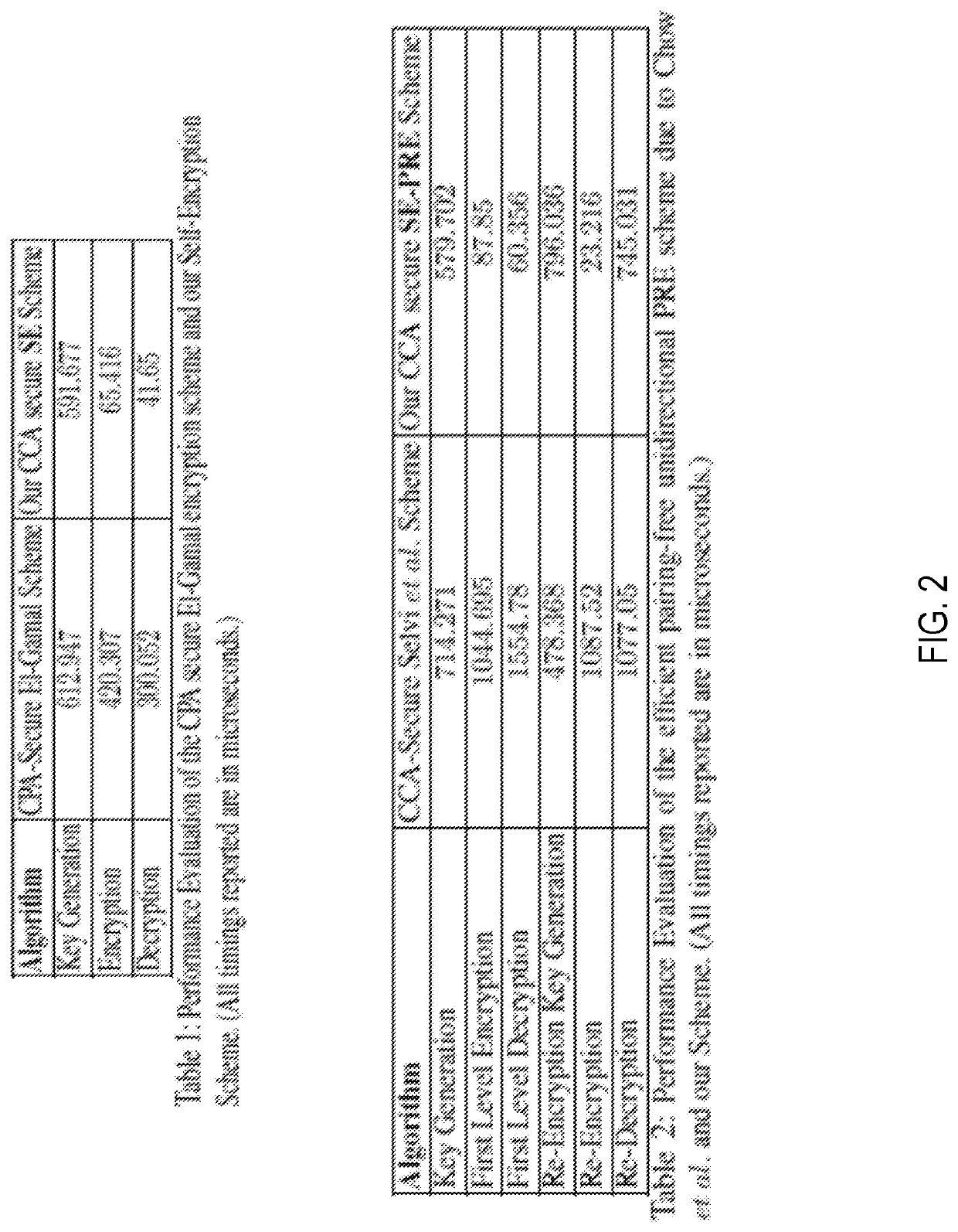
CCA secure proxy re-encryption method with delegable verifiability
ActiveCN107086911AGuaranteed validityAvoid the danger of damage to rights and interestsKey distribution for secure communicationUser identity/authority verificationPlaintextComputer science
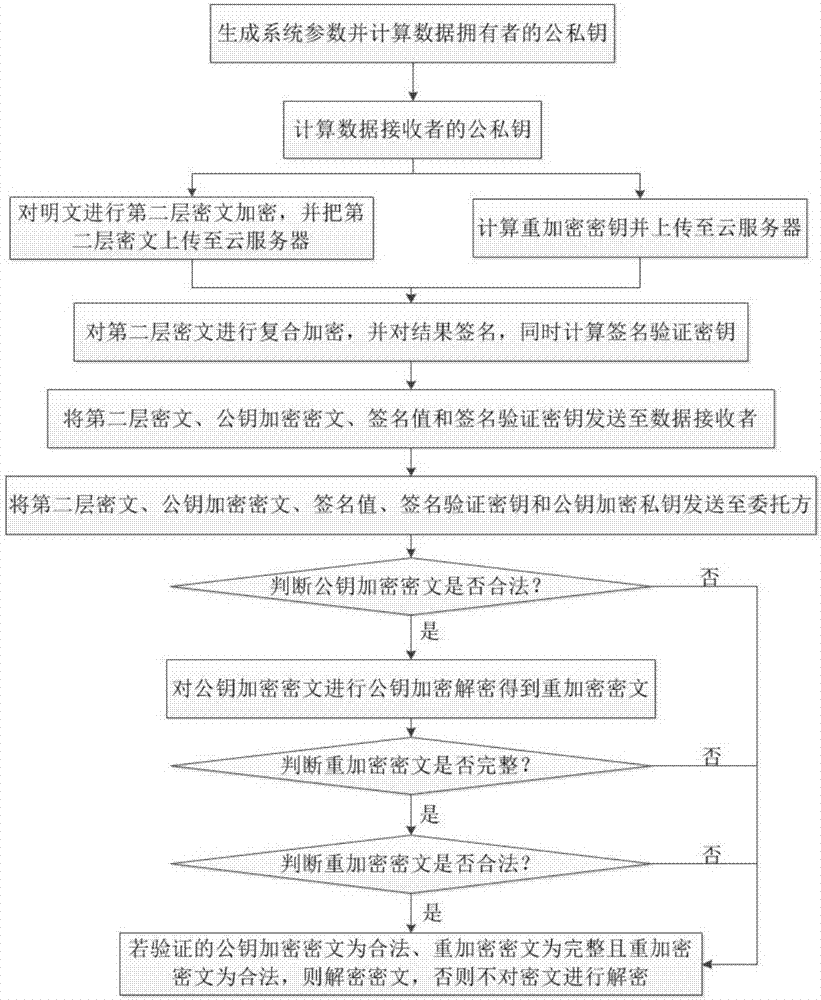
The invention provides a CCA secure proxy re-encryption method with delegable verifiability and is used for solving the problem that in the prior art, an encryption method is insufficient in security. The method comprises the realization steps that a data owner generates a system parameter and calculates own public key and private key; a data receiver calculates own public key and private key; the data owner carries out second-layer ciphertext encryption on a plaintext, uploads a result to a cloud server, moreover calculates a re-encryption key and sends the re-encryption key to the cloud server; the cloud server carries out composite encryption on a second-layer ciphertext, signs the result, moreover, calculates a signature verification key and sends the second-layer ciphertext, a public key encrypted ciphertext, a signature value and the signature verification key to the data receiver; the data receiver sends the received data and the public key encrypted private key to a client; the client carries out legality verification on the public key encrypted ciphertext; the client carries out integrity and legality verification on a re-encrypted ciphertext; and the data receiver decides whether to decrypt the ciphertext or not according to verification results.
Owner:XIDIAN UNIV
Data broadcasting distribution protection method based on proxy re-encryption and security chips
InactiveCN103095462AReduce the burden onSmall burdenSpecial service provision for substationUser identity/authority verificationComputerized systemGeneral purpose computer
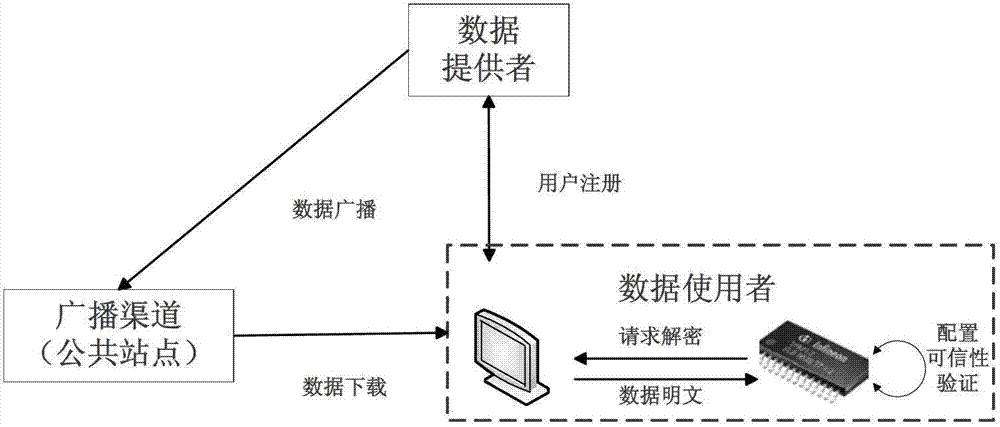
The invention discloses a data broadcasting distribution protection method based on proxy re-encryption and security chips. The method includes that a data user adopts a general-purpose computer system provided with the security chips as computing equipment, before data is distributed, a data owner and the data user agree upon public security parameters and cryptology algorithms of both sides and the security chips acquire encryption keys, the data owner generates a data encryption packet, binds configuration requirements for hardware to the data encryption packet and then broadcasts the data encryption packet to a public channel, and the data user acquires the data encryption packet from the public channel, the security chips checks the configuration of the computer system, if the configuration requirements are met, the data encryption packet is re-encrypted and then the data user decrypts the re-encrypted data, and if the configuration requirements are not met, the decryption is rejected. The data broadcasting distribution protection method based on the proxy re-encryption and the security chips can ensure that a computing platform of the data user can obtain and use the distributed data only when specific configuration is met, the protection strength is strong, and the implementation cost is low.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
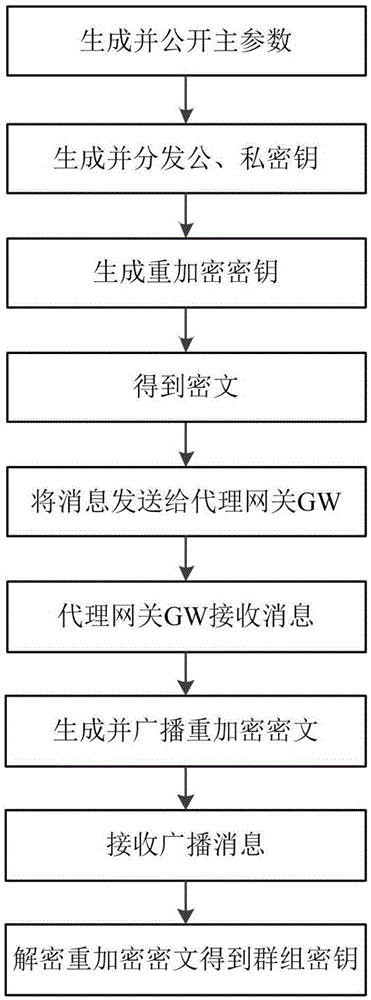
Group key distribution method for machine-type communication based on proxy re-encryption
ActiveCN105262587AReduce loadImprove service qualityKey distribution for secure communicationWireless commuication servicesDistribution methodBroadcasting
The invention discloses a group key distribution method for machine-type communication based on proxy re-encryption. The problem of network signaling jam and server overload in the prior art is mainly solved. The distribution method is realized through the following steps: 1, generating a system parameter; 2, generating and distributing public and secret keys; 3, generating a re-encryption key; 4, obtaining a ciphertext; 5, sending a message to a proxy gateway; 6, receiving the message by the proxy gateway; 7, generating and broadcasting a re-encrypted ciphertext; 8, receiving a broadcast message; and 9, decoding the re-encrypted ciphertext to obtain a group key. According to the invention, through proxy re-encryption, the re-encrypted ciphertext is generated and broadcasted by utilization of the proxy gateway, and the problem, of network signaling jam and server overload, generated during key distribution of a machine-type communication server and a machine-type communication equipment group is relieved. The method is applicable to a machine-type communication network.
Owner:XIDIAN UNIV
Ciphertext retrieval system and method for supporting proxy re-encryption in combination with identity and attribute
ActiveCN108400871AImprove efficiencySimple key generationPublic key for secure communicationDigital data protectionAccess structureSecret share
The invention discloses a ciphertext retrieval system and method for supporting proxy re-encryption in combination with identity and attribute. The method realizes sharing of a secure and efficient one-to-many user search authority in a cloud environment. The previous identity-based searchable encryption and proxy scheme combines identity-based proxy re-encryption with a searchable encryption scheme to implement agency for a one-to-one search authority. The scheme uses an identity-based encryption method in the initial ciphertext encryption, and adopts an LSSS linear secret shared matrix access structure in the re-encryption phase, which can authorize the ciphertext retrieval authority to other users who conform to the access structure. Therefore, the scheme supports the sharing of a moregranular user search authority and has higher computational efficiency. In the re-encryption threshold generation phase, the user key is blinded by the random value and submitted to a cloud server, ensuring the confidentiality and security of the user key.
Owner:NANJING UNIV OF POSTS & TELECOMM
Orthogonal access control for groups via multi-hop transform encryption
ActiveUS20180316495A1Lower latencyIncrease the number ofKey distribution for secure communicationMultiple keys/algorithms usageControl systemProxy re-encryption
Disclosed is an orthogonal access control system based on cryptographic operations provided by multi-hop proxy re-encryption (PRE) that strictly enforces only authorized access to data by groups of users, scalable to large numbers of users. Scalable delegation of decryption authority can be shared with a plurality of members of a group whether those members be users or devices, and members of a group can further create sub groups and delegate decryption authority to those members, whether users or devices. Members are granted access via generation of transform keys, and membership or access can be revoked merely be deleting the transform key—no elimination of the encrypted data, regardless of its storage location, is needed.
Owner:IRONCORE LABS INC
Multi-user file sharing control method in cloud environment
ActiveCN106850656ASmall amount of calculationReduce trafficKey distribution for secure communicationQuantum computerFile sharing
The invention discloses a multi-user file sharing control method in a cloud environment. The method utilizes an NTRU algorithm and a proxy re-encryption technology, proposes an efficient and safe multi-user shared file control scheme, and implements more fine-grained delegate control of a file owner on a shared file. The method mainly comprises parts of key generation, encryption, proxy re-encryption and decryption. When a ciphertext storage space is reduced, the method only needs to carry out addition, subtraction, multiplication and modular operations, calculated quantities of file encryption and decryption are only in linear increasing relationship with a multiplication operation of a number of file blocks, and after the file owner authorizes, file sharing users can access respective different file block contents. The multi-user file sharing control method disclosed by the invention has the advantages of resistance to a quantum calculation attack, low calculation cost and low communication traffic, and is more suitable for an environment in which client calculation resources and communication resources are limited.
Owner:深圳市嘉鸿网络科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com