Ciphertext retrieval system and method for supporting proxy re-encryption in combination with identity and attribute
A proxy re-encryption and retrieval system technology, applied in the field of ciphertext retrieval system, can solve the problem of inability to effectively realize the granting of search permissions to multiple users, and achieve the effect of improving system efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] Below in conjunction with accompanying drawing, technical scheme of the present invention is described in further detail:
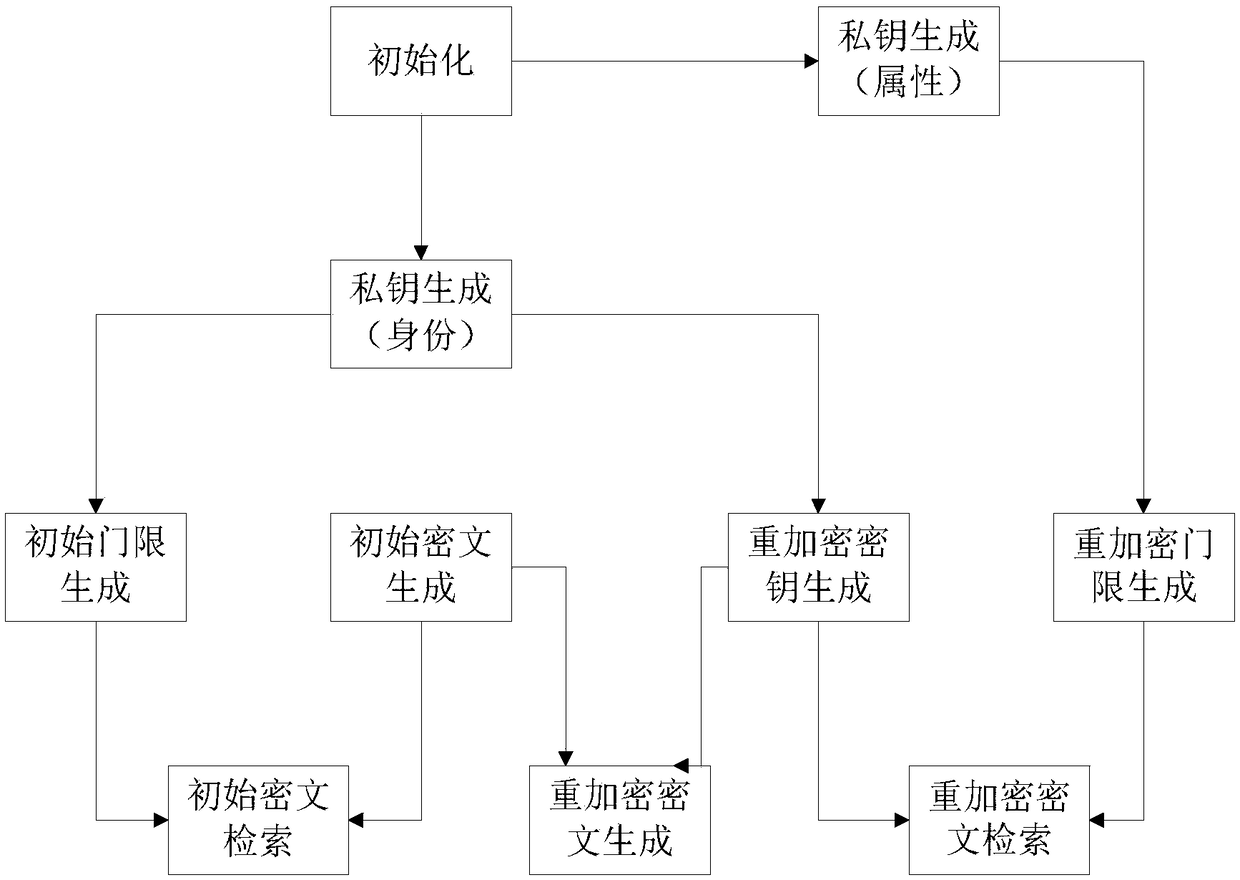
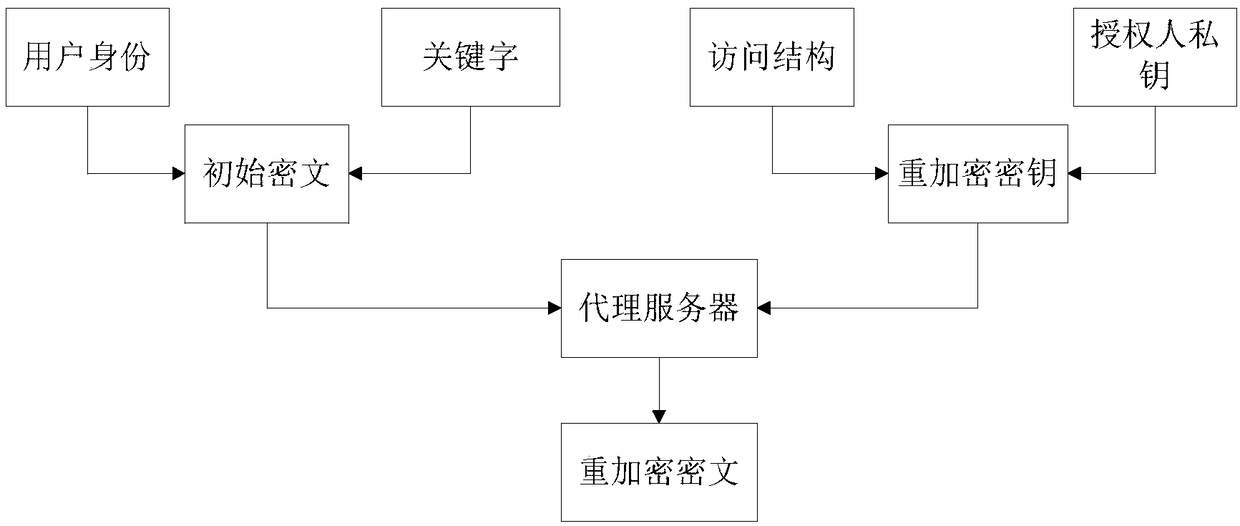
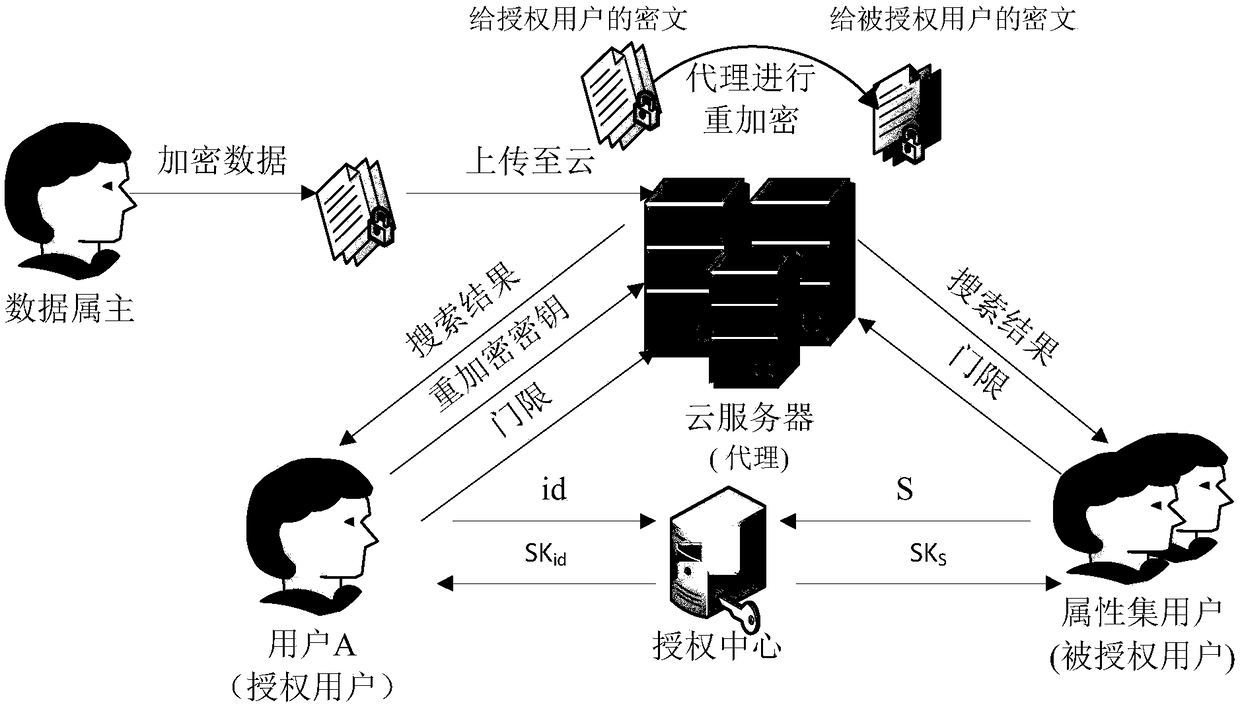
[0060] Aiming at the problem that the existing identity-based searchable encryption method cannot realize the effective sharing of search authority, the invention introduces proxy re-encryption into the identity-based searchable encryption. And considering the fact that the authorizer needs to grant the search authority to multiple users in practical applications, an attribute-based encryption method is used in the re-encryption stage, and a ciphertext retrieval that combines identity and attributes and supports proxy re-encryption is proposed. method. When the authorized user is not online, the search authority can be safely and efficiently shared with other users through the agent, thereby improving the processing efficiency of the system.
[0061] A ciphertext retrieval system that supports proxy re-encryption in cloud computing according to th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com