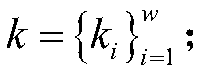An encrypted image retrieval method supporting multiple keys
An encrypted image, multi-key technology, applied in still image data retrieval, metadata still image retrieval, key distribution, and can solve problems such as increased computing overhead on the user side
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The present invention will be further described below in conjunction with the accompanying drawings.
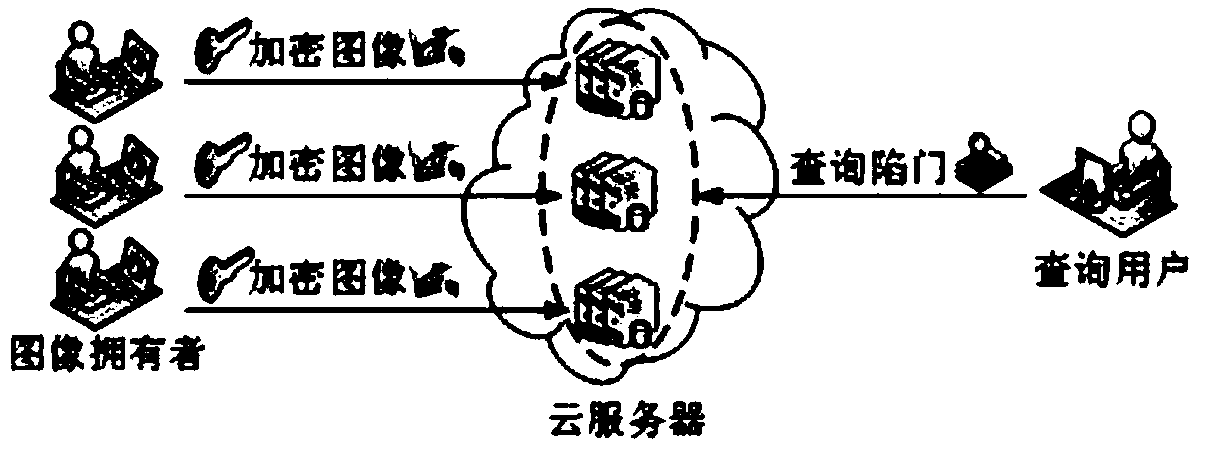
[0048] see figure 1 , in the present invention, the user only needs to generate a trapdoor to query the image sets encrypted by different keys, which solves the problem that the query user needs to generate a trapdoor corresponding to each encryption key in the traditional method.
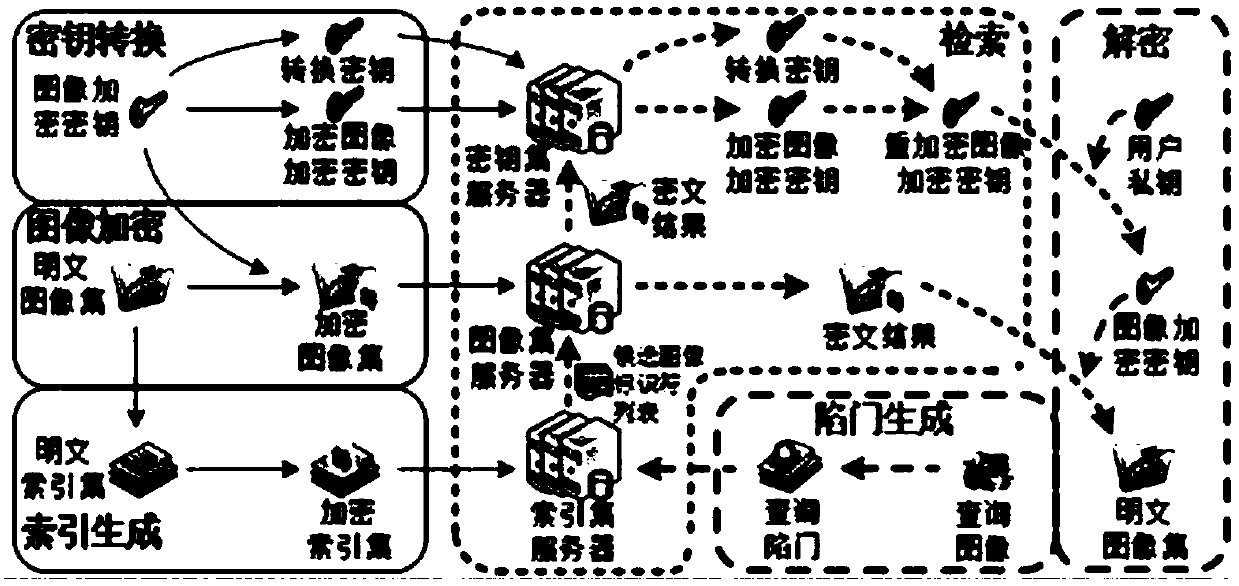
[0049] see figure 2 , the present invention includes 4 entities, namely key generation center, image owner, image query user and cloud server. The fully trusted key generation center is responsible for system initialization and key distribution; the image owner is responsible for index establishment; the query user is responsible for trapdoor generation; the honest and curious cloud server is responsible for retrieving the encrypted image set and re-encrypting the key ciphertext. In order to realize the encrypted image retrieval method supporting multiple keys, the specific implementatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com