A block chain ciphertext cloud storage sharing method based on attribute proxy re-encryption
A technology of proxy re-encryption and blockchain, which is applied in the field of information security storage and sharing in cloud systems, and can solve problems such as service interruption, high computing cost, and information loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0100] Example 1. Example process of contract user information interaction in the present invention.
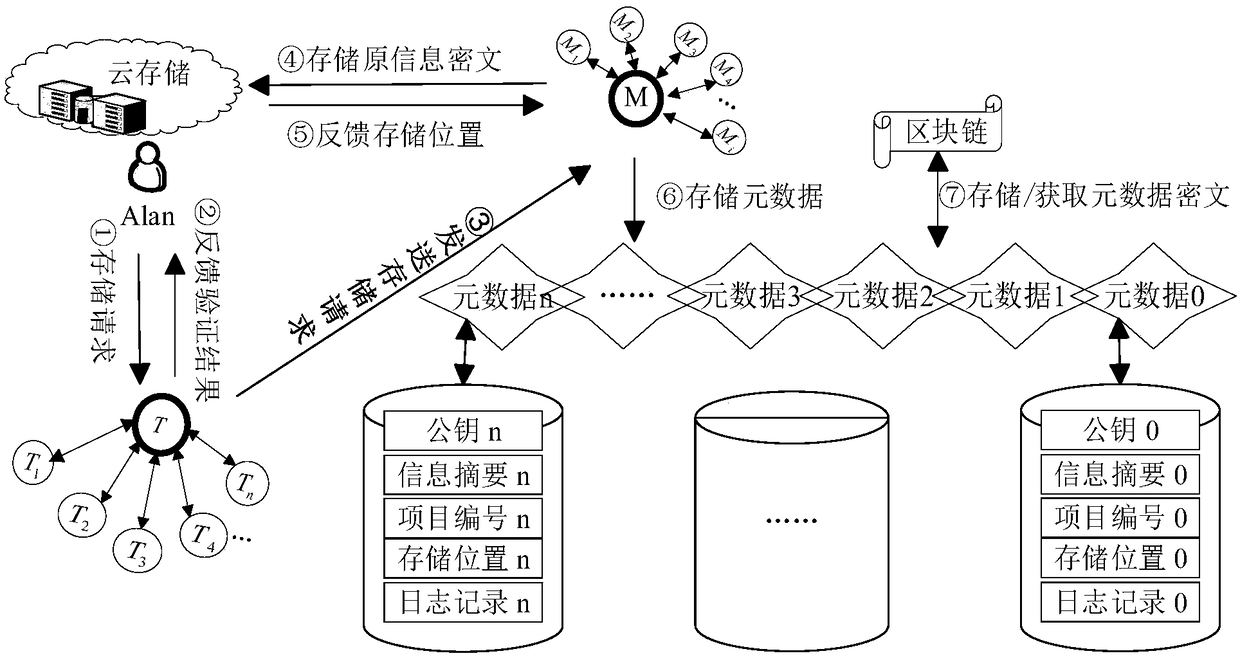
[0101] 1) Alan, the information owner, sends a storage request, and at the same time submits an information quotation and a custom random string so that users can obtain information sharing rewards.
[0102] 2) The transmission leader node T in the cluster to the crowd node T in its own cluster n Broadcast authentication information and validity of user identity. If it is valid, the transmission leader node T will extract the data and temporarily store it in its own log; if it is invalid, it will feedback "illegal user".
[0103] 3) Transfer the leader node T to all the crowd nodes T in the cluster n Copy the information and wait for the response. After confirming that at least half of the nodes in the cluster have received the information, confirm to the information owner Alan that the information has been received. Once the user receives the confirmation information, it ...
Embodiment 2
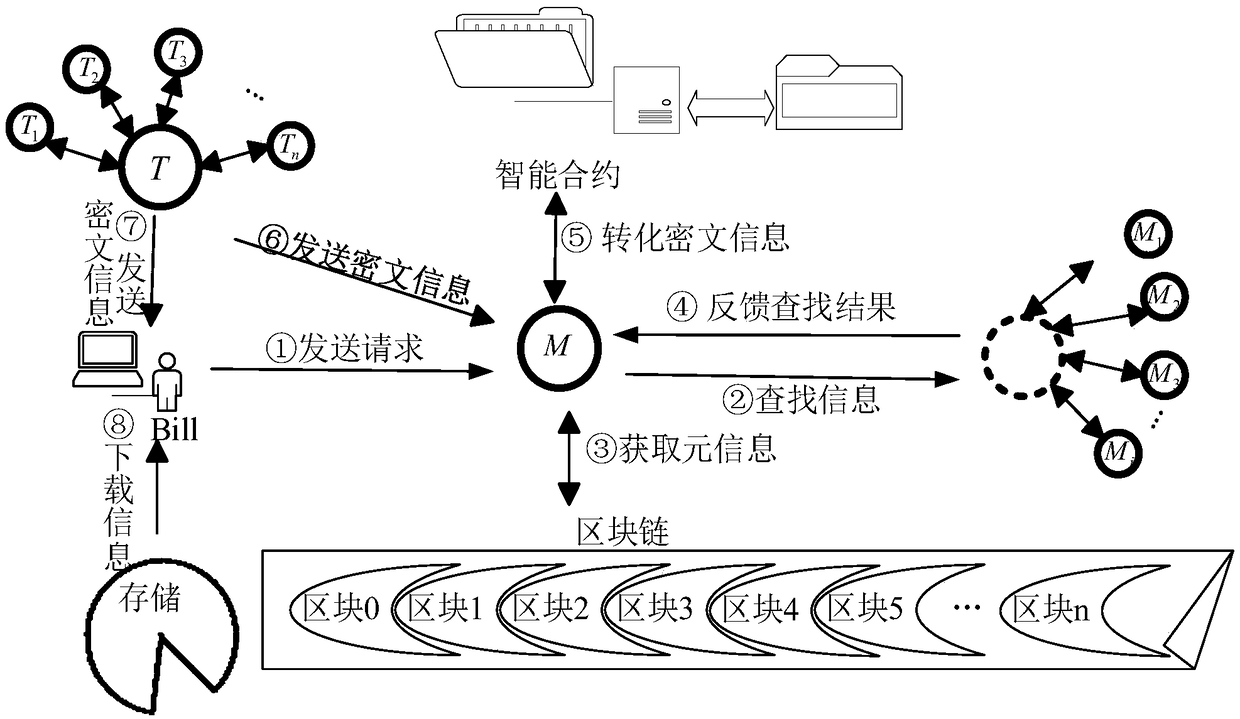
[0110] Example 2. Information interaction smart contract execution process.
[0111] A large number of users and information are designed in the present invention. In order to facilitate transaction processing, it is divided into the following stages in chronological order: contract release, transaction release, authority review, security check, and transaction settlement. combine Figure 4 The specific expression is as follows:
[0112] 1) Formulate the contract: The contract creator uses a high-level language to convert the contract with the user attribute collection feature into a binary contract code, records it in the local network, and calls all local users to sign the contract. After the node confirms the signature, it passes the ether The Fang virtual machine is deployed in the Ethereum blockchain, and feeds back the contract address and calling instructions to the user.
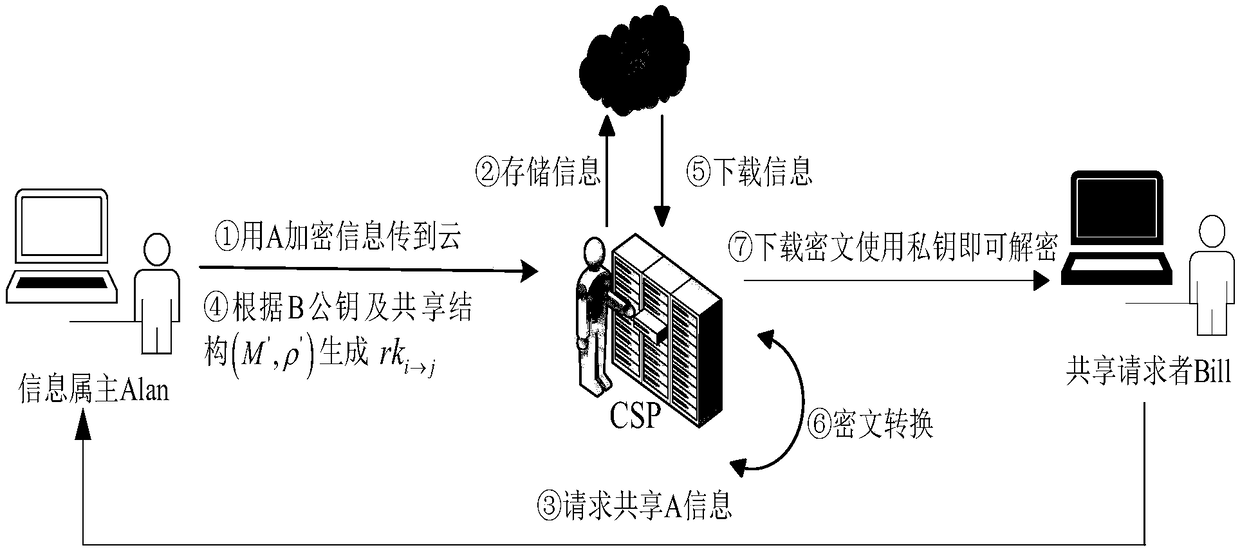
[0113] 2) Release transaction: Alan, the information owner, stores metadata Data→{LC,w,IN} acc...
Embodiment 3
[0117] Example 3. Safety analysis of the present invention.
[0118] a) Security proof of information exchange:
[0119] The present invention is based on the q-parallel BDHE difficulty problem for security proof, and judges the bilinear difficulty problem. If the assumption is true, the adversary under the random oracle model The advantages Neglecting it means that the invention chooses plaintext security (CPA, Chosen Plaintext Attack).
[0120] Theorem 1 If the advantage of the present invention in solving the q-parallel BDHE problem is negligible, then it is said that the q-parallel BDHE hypothesis is in (G, G T ) is established, the invention is CPA safe under the random oracle model.
[0121] Prove the assumption that there exists an attacker In the CPA game, its advantages It cannot be ignored that the adversary wins the security game. then construct a game challenger If there is an attacker To break the CPA under the security model with an advantage of ξ,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com