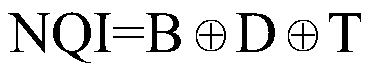Patents
Literature
40 results about "Broadcast authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
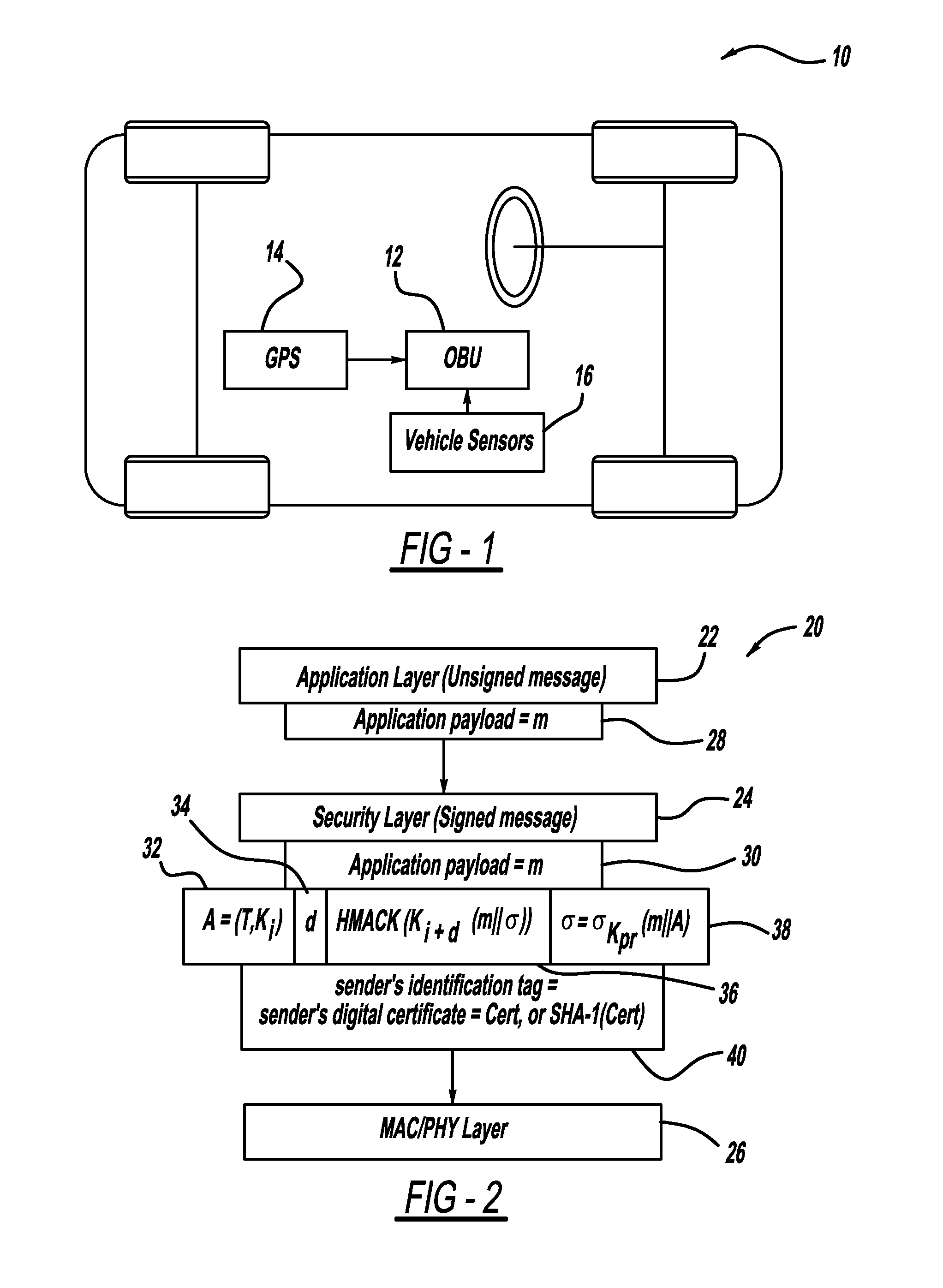
Patent Status
Application Year
Inventor
EFFICIENT TECHNIQUE TO ACHIEVE NON-REPUDIATION AND RESILIENCE TO DoS ATTACKS IN WIRELESS NETWORKS
ActiveUS20110238997A1Multiple keys/algorithms usageRoad vehicles traffic controlDigital signatureNon-repudiation
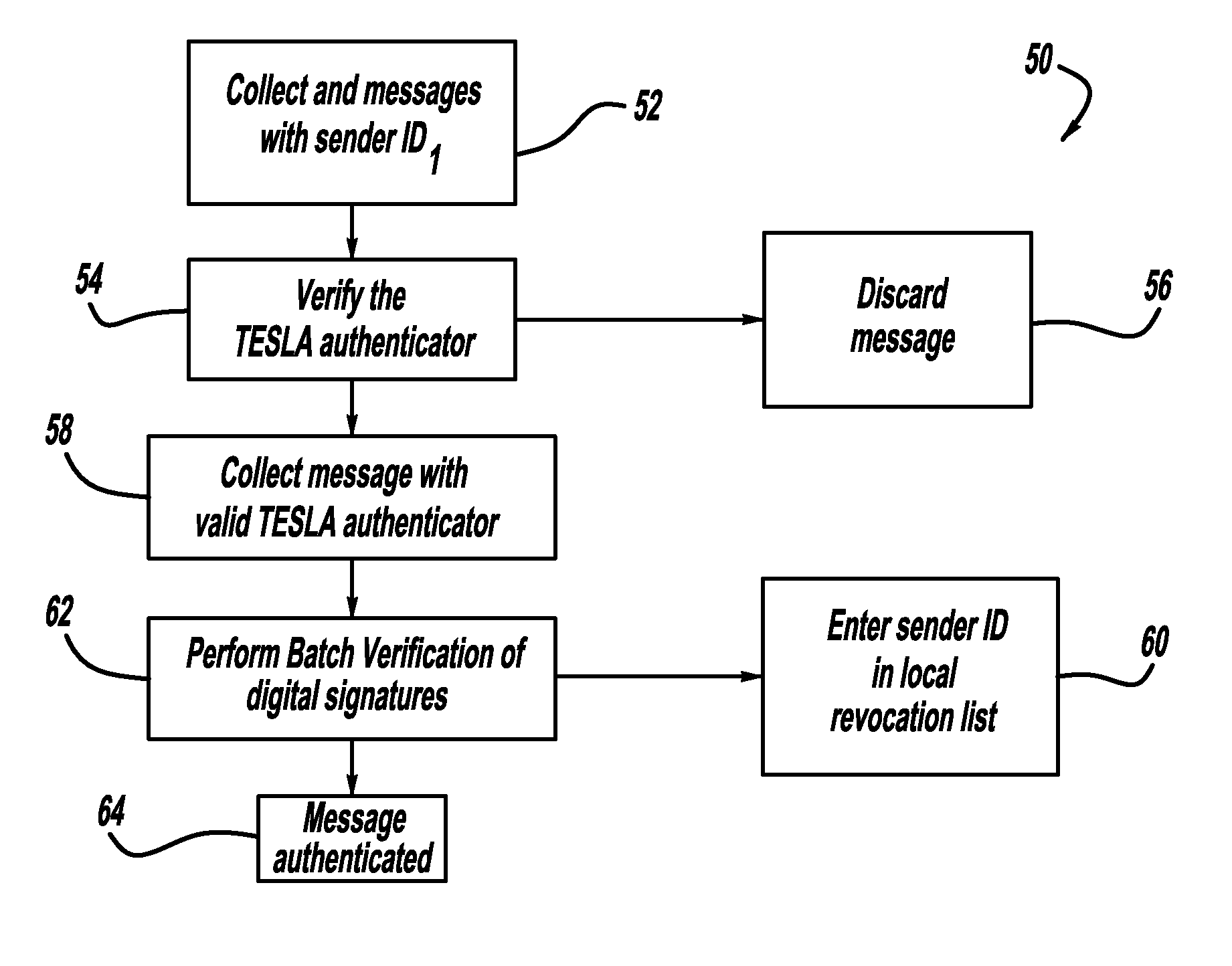
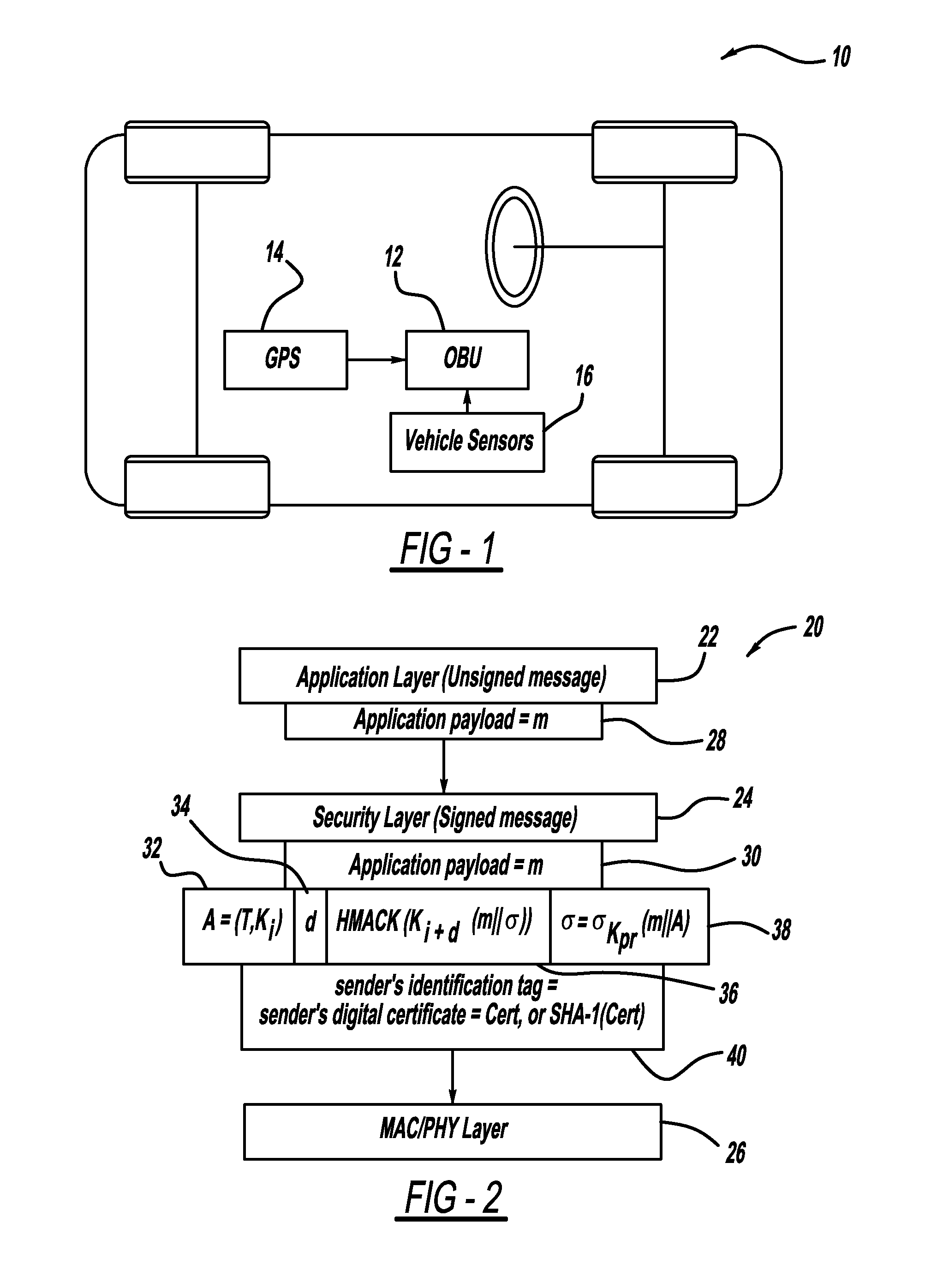
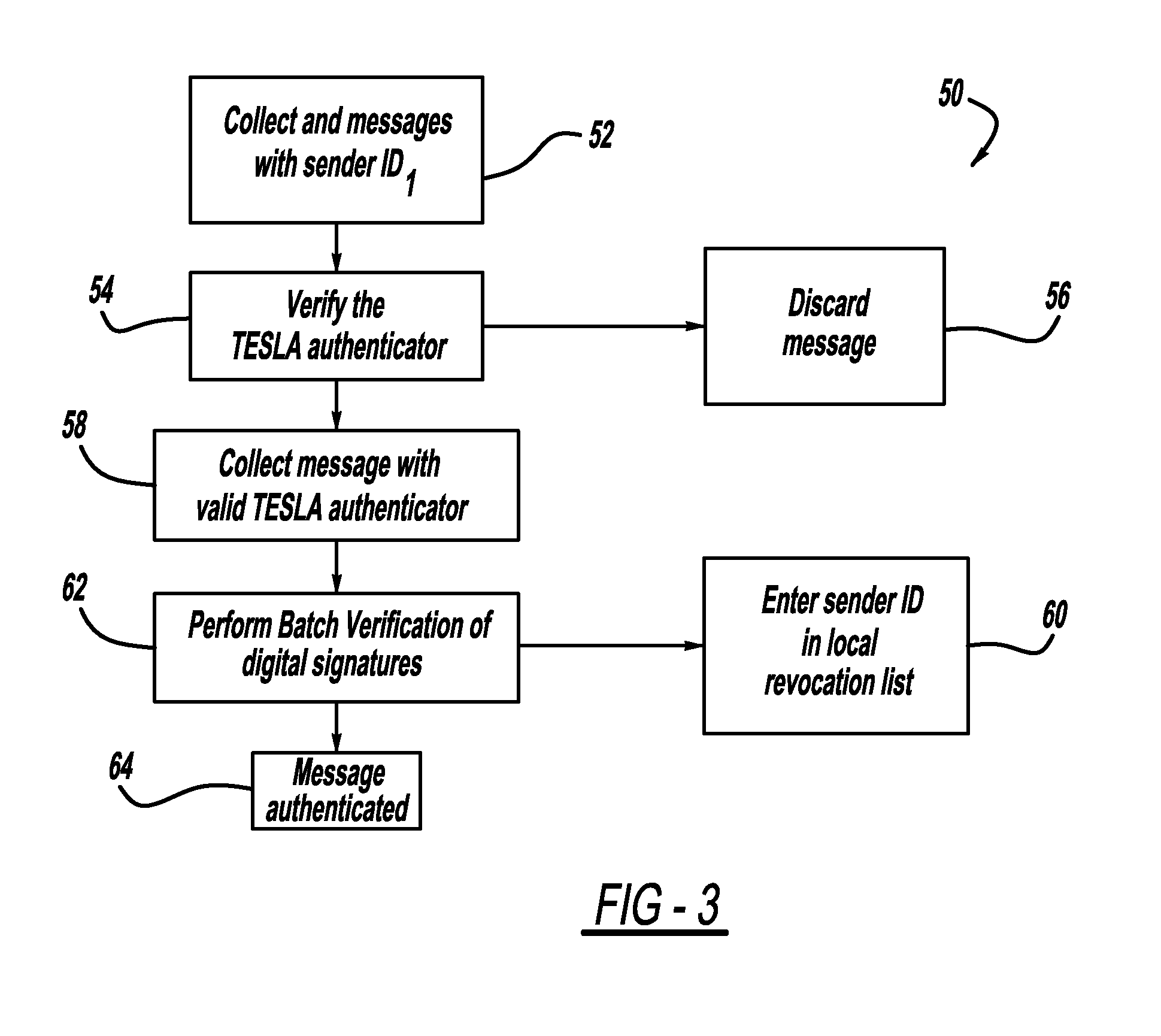
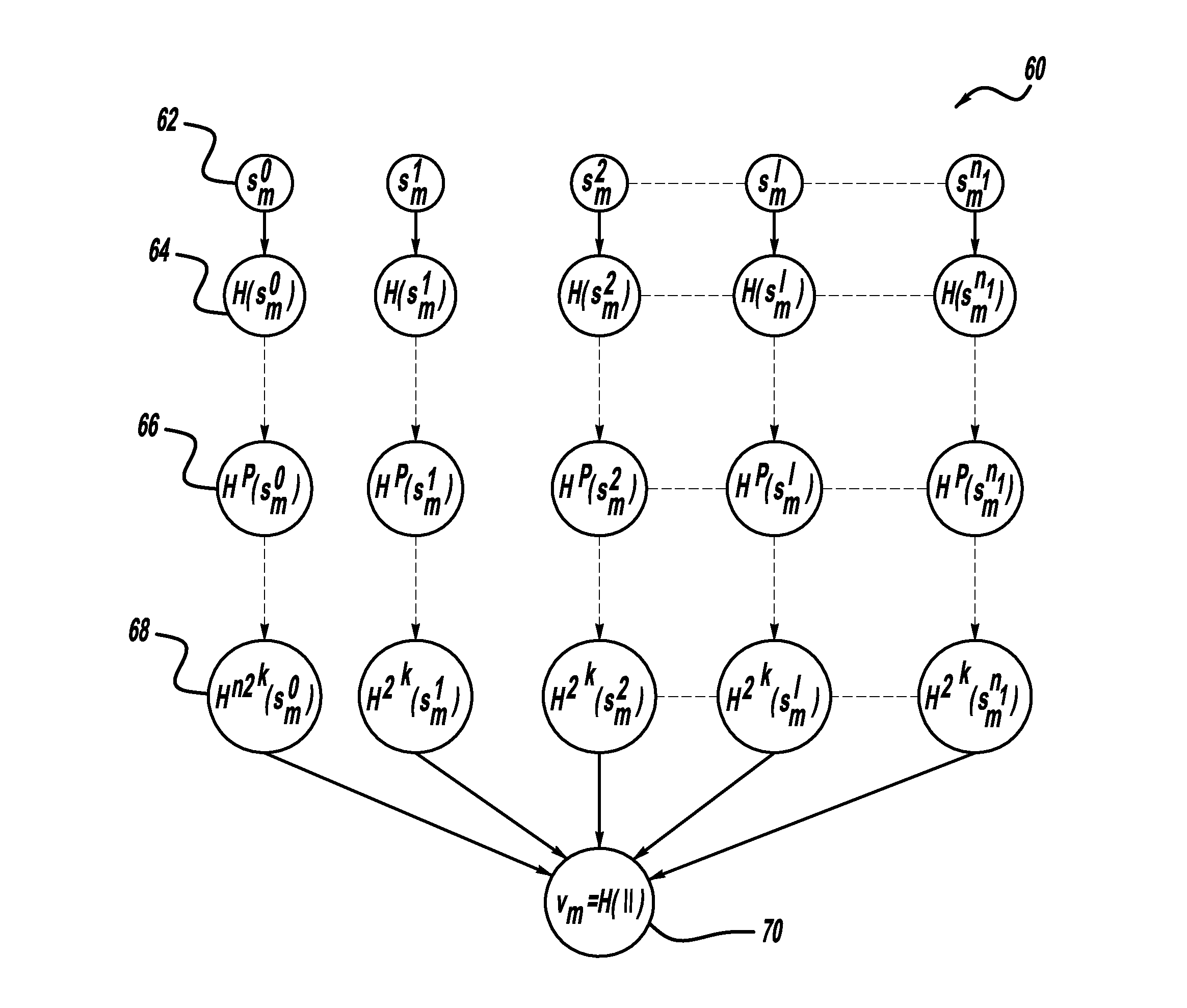
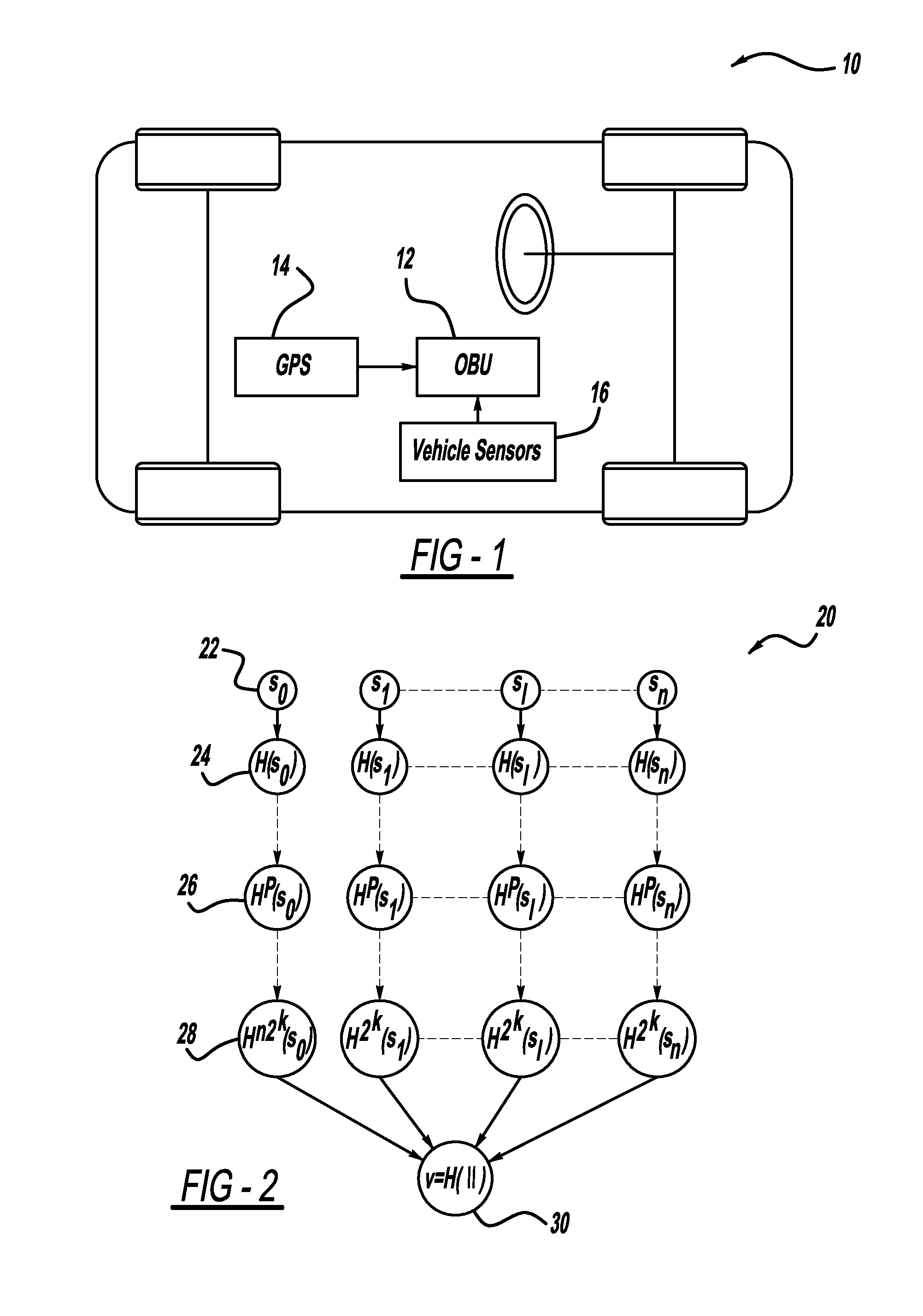
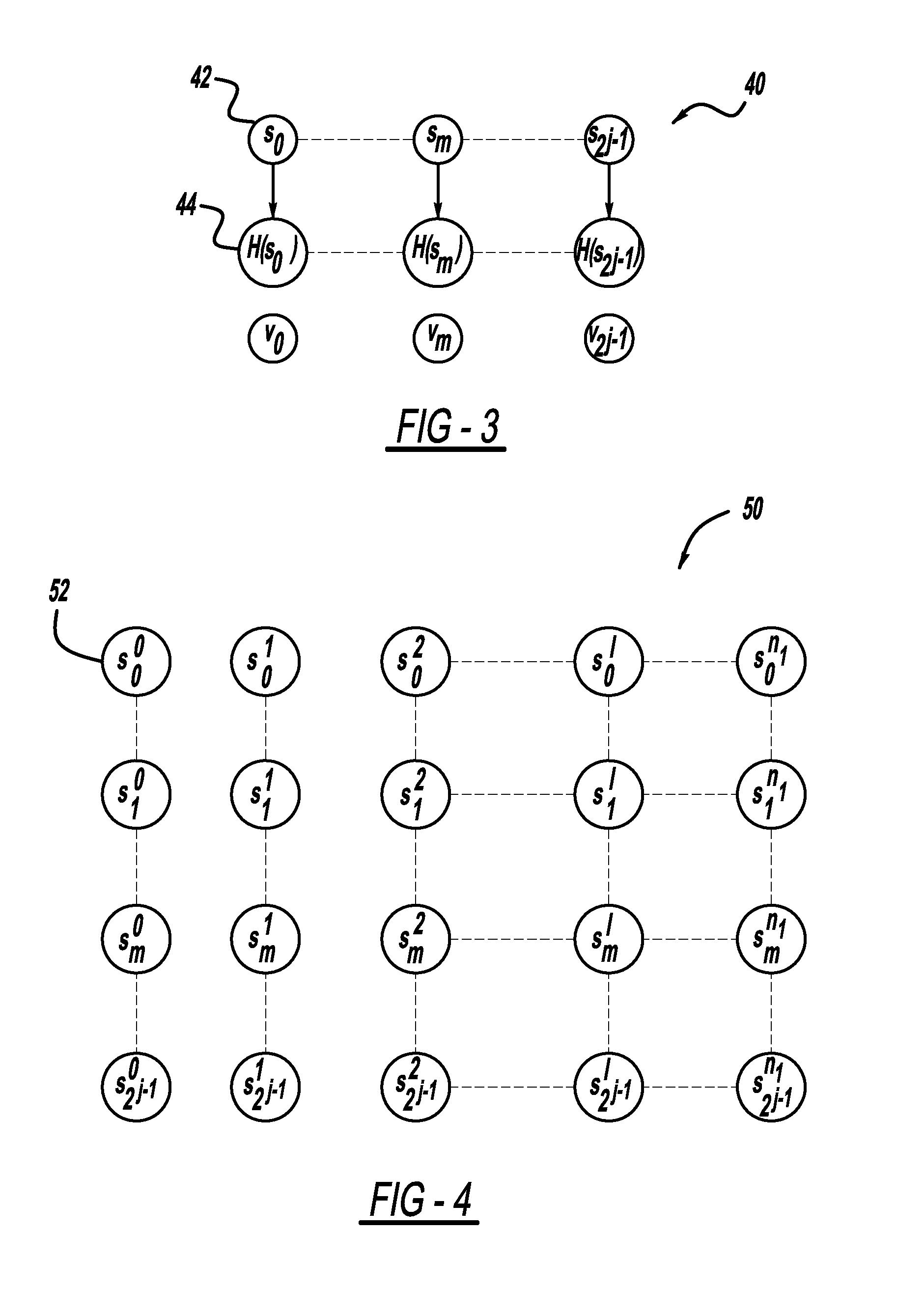
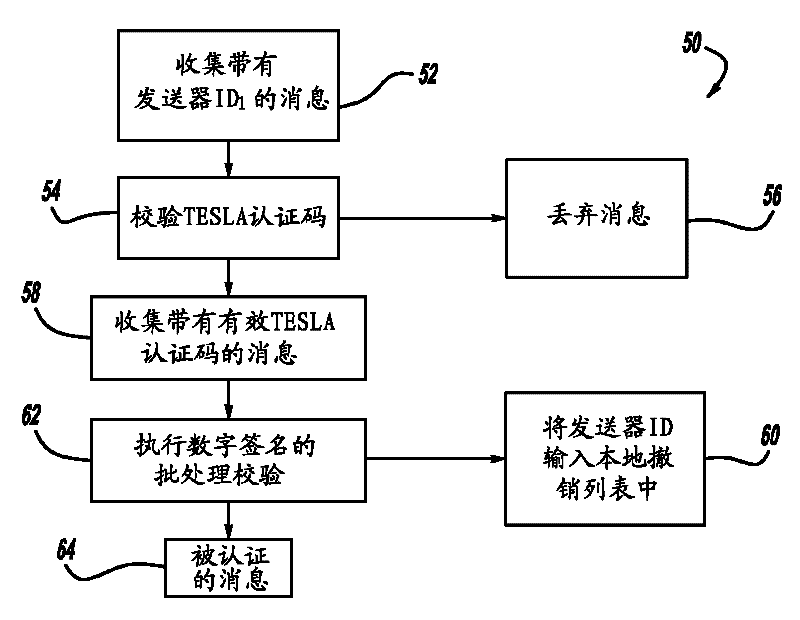
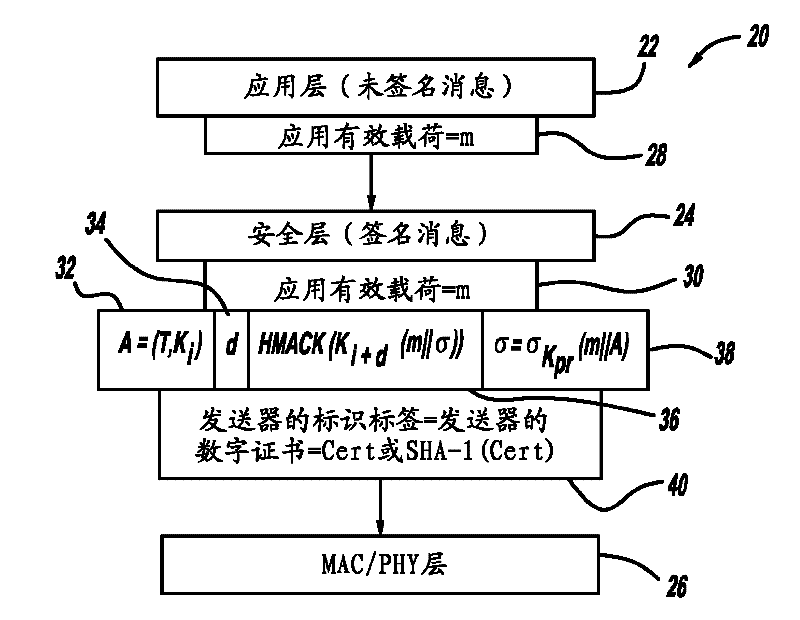
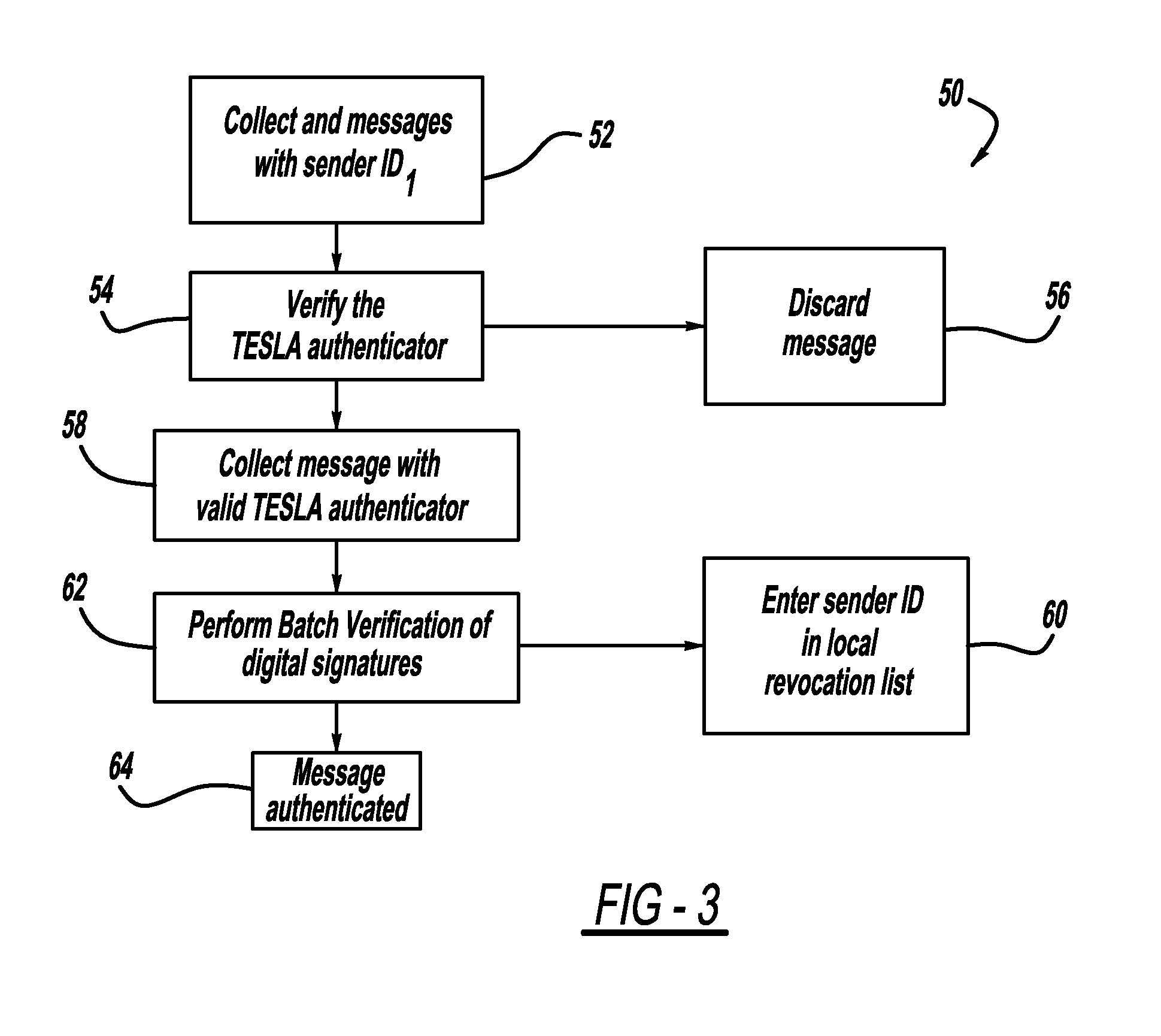
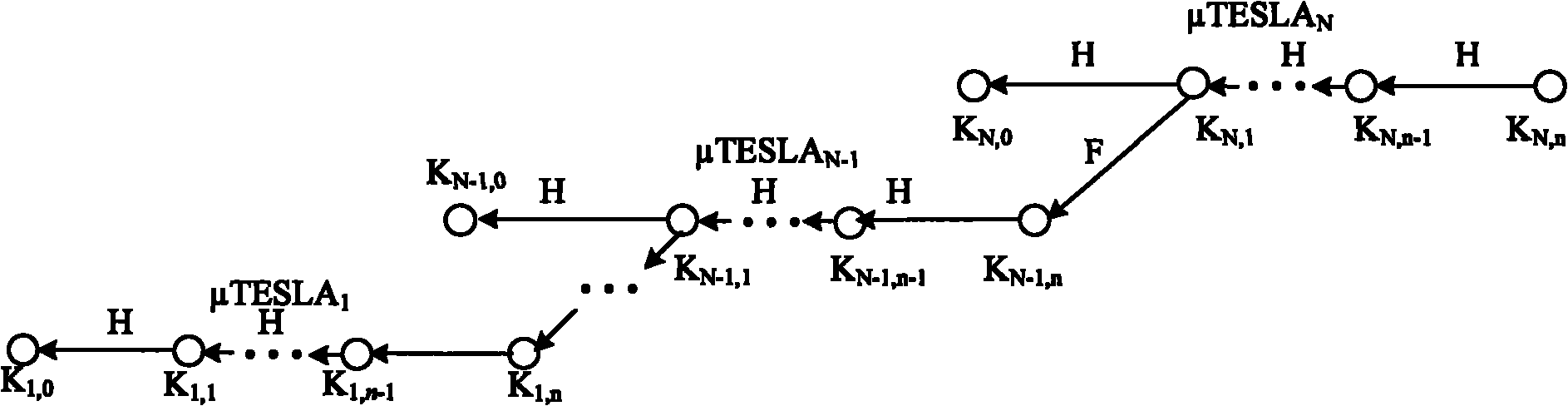
A computationally efficient message verification strategy that achieves non-repudiation and resilience to computational denial of service attacks in conjunction with a broadcast authentication protocol that authenticates messages using a combination of a digital signature and a TESLA MAC. When messages are received at a receiver, the verification strategy separates the messages into messages with the same sender identification. The strategy then determines whether the TESLA MAC authenticator is valid for each message and discards those messages that do not have a valid TESLA MAC. The strategy collects the messages that have a valid TESLA MAC for each sender identification and performs a batch verification process on the group of messages to determine if the messages in the group have a valid digital signature. This strategy verifies each message in the group of messages if the batch verification process shows that the group of messages has a valid digital signature.
Owner:GM GLOBAL TECH OPERATIONS LLC
Classification security-based broadcast authentication design method
InactiveCN101699873ATroubleshoot broadcast authentication issuesReduce overheadNetwork topologiesBroadcast service distributionBroadcast packetMessage type
The invention discloses a classification security-based broadcast authentication design method, which relates to solution for realizing the broadcast authentication of a wireless sensor network, and is mainly used for solving the security authentication problem of a broadcast data packet of the wireless sensor network. A security scheme which can meet the security requirement and has minimum overhead is used for different application and messages so as to reduce the overhead of a protocol to the maximum. For the broadcast data packet in the wireless sensor network, different authentication methods are adopted according to different message types. On the basis of deeply analyzing the shortages of the conventional broadcast authentication technology of the wireless sensor network, the broadcast authentication technology which integrates different security levels is provided aiming at a situation that different application has different requirements on security service intensity; and based on a mixed strategy, the security scheme which can meet the security requirement and has the minimum overhead for different application and the messages is adopted so as to reduce the overhead of the protocol to the maximum.
Owner:NANJING UNIV OF POSTS & TELECOMM
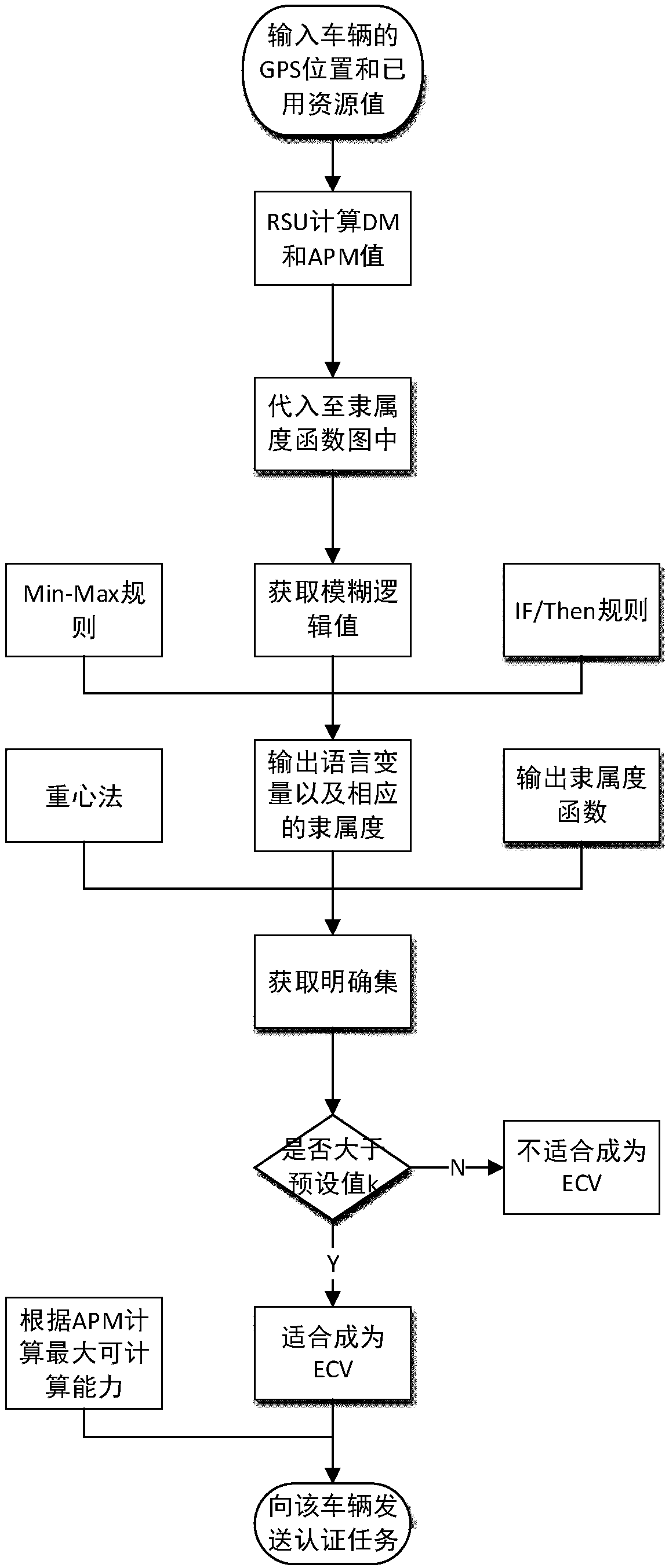
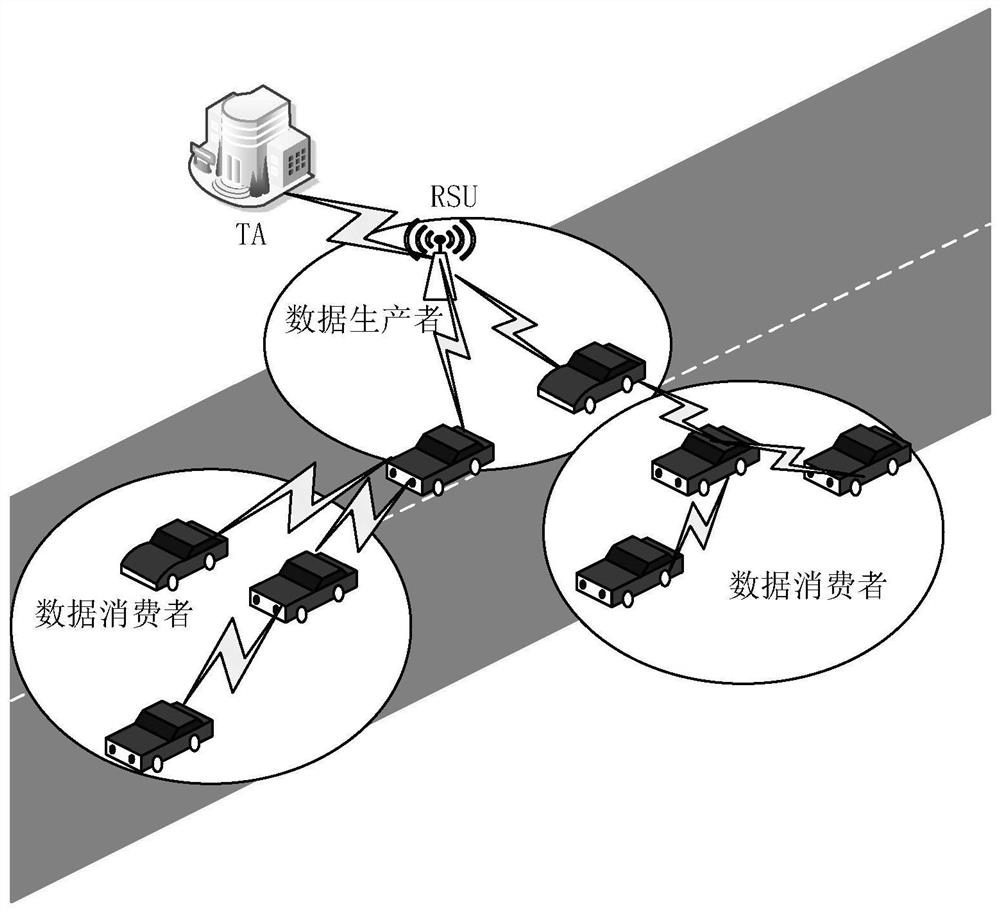
Efficient message authentication method for vehicular ad hoc network based on edge computing
ActiveCN107634837AReduce overheadLow message authentication redundancyKey distribution for secure communicationPublic key for secure communicationLocal optimumEdge computing
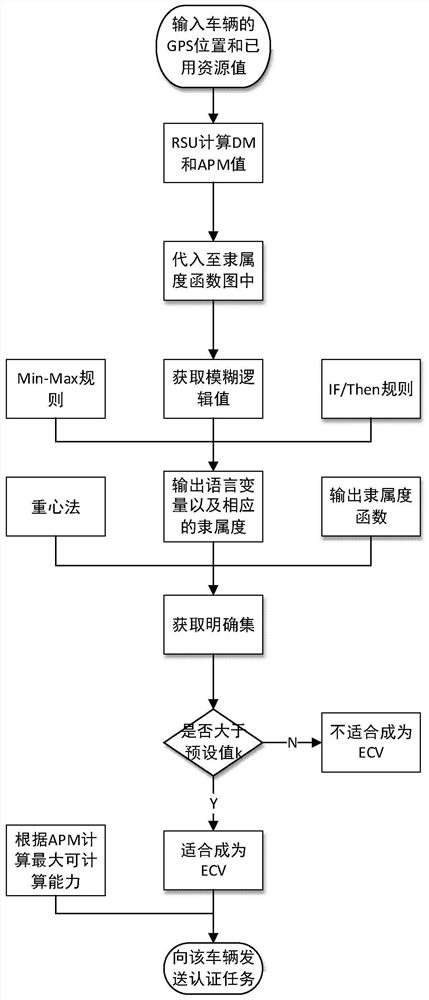
The invention discloses an efficient message authentication method for a vehicular ad hoc network based on edge computing, which comprises the steps of system initialization of participating entitiesof the Internet of vehicles, wherein the step comprises two processes such as parameter generation and vehicle pseudonym and signature generation; and (2) message authentication of an RSU (Roadside Unit) and a vehicle, wherein the step comprises four processes such that the RSU elects an edge computing vehicle (ECV), the ECV executes a task, the RSU checks an authentication result of the ECV and vehicle message authentication is performed. The signing portion of the invention adopts an elliptic curve cryptography based operation, thereby enabling the computation and transmission overhead to below; further the ECV is elected according to a fuzzy logic control theory to achieve local optimal election; the ECV is set to help the RSU to achieve quick and accurate message signature authentication; and the RSU reduces the redundant authentication of the whole system to the maximum extent through broadcasting the authentication result, and the operating efficiency of the whole vehicular ad hoc network is improved.
Owner:ANHUI UNIVERSITY
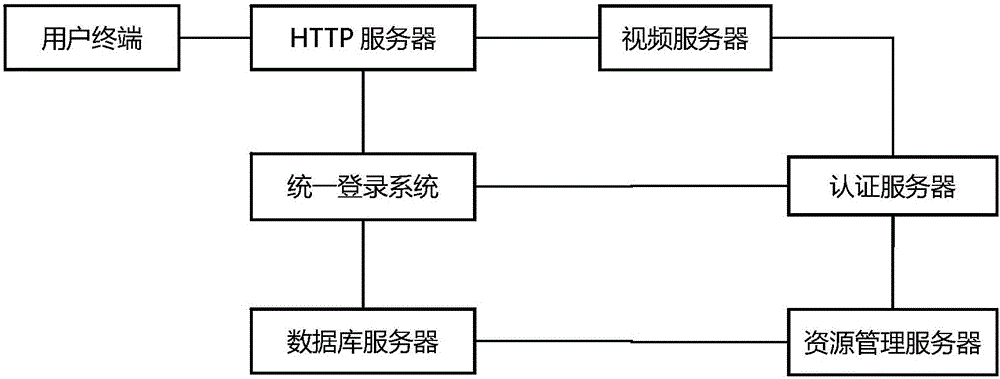
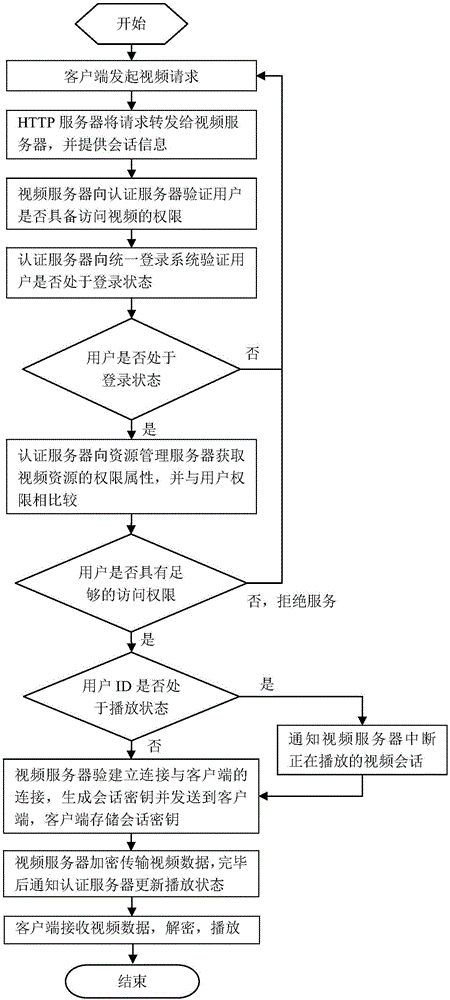
RTMP protocol-based streaming media service user authentication method
The invention discloses an RTMP protocol-based streaming media service user authentication method. Before a video server provides video service, legitimacy of a user identity is verified via an authentication server firstly; the access authority of the user is then verified, the video service is only provided for the user with enough access authority, and an illegal user request or a user request with not enough authority is denied; and finally, encrypted transmission is carried out on the video streaming data, and the user can be prevented from acquiring and spreading the video content in a downloading mode. Through the above means, streaming media resources can be ensured to be used by legal user groups only, an illegal video request is denied, the video resources can be ensured to be reasonably used, and the processing pressure of the video server is reduced at the same time. Reliability and confidentiality of streaming media video on demand and live broadcast authentication can be realized, safety of the network streaming media management can be improved significantly, and an extremely important practical significance is provided for development of the network streaming media safety technology.
Owner:HANGZHOU SHISHUO EDUCATION TECH CO LTD
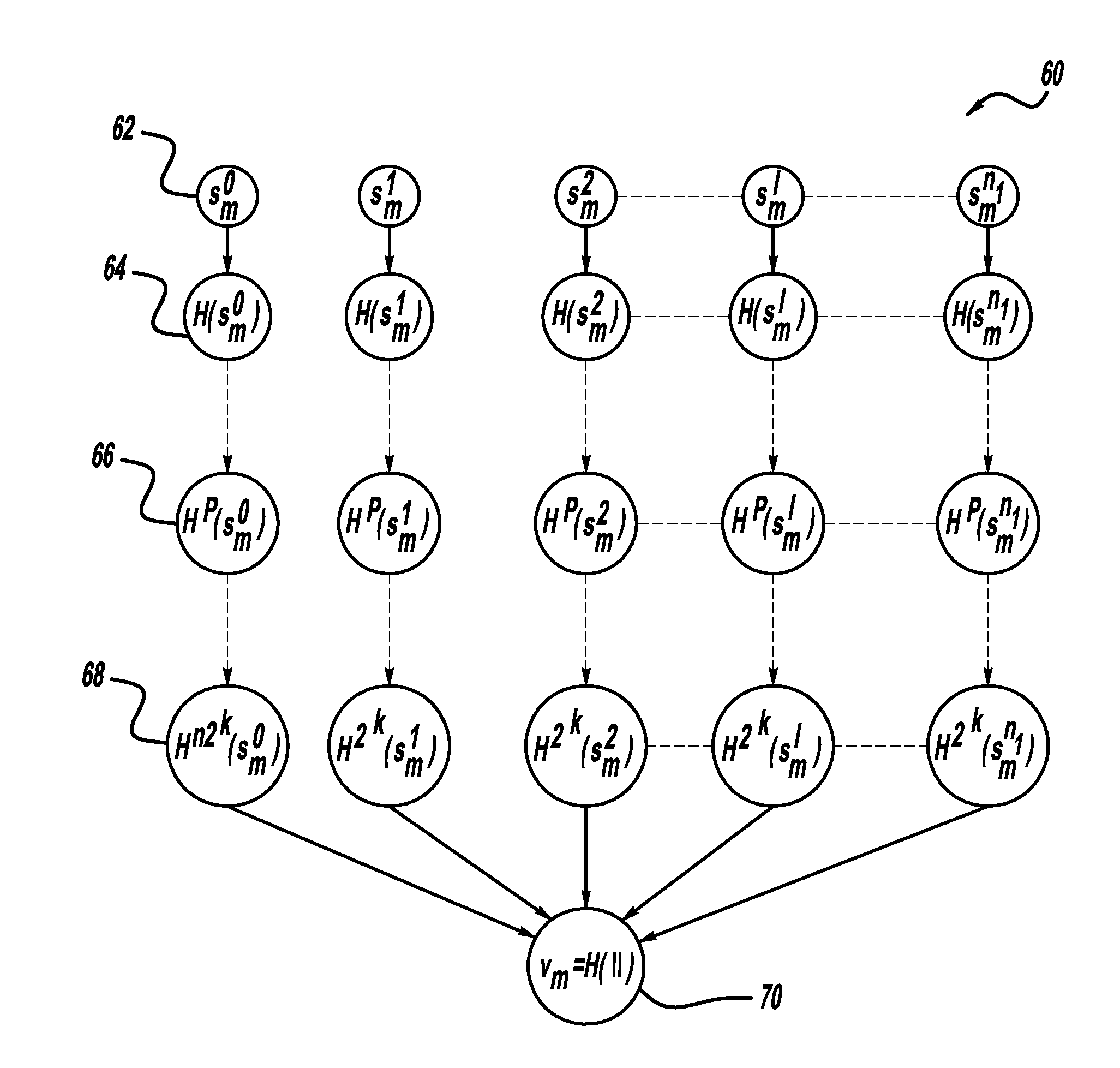
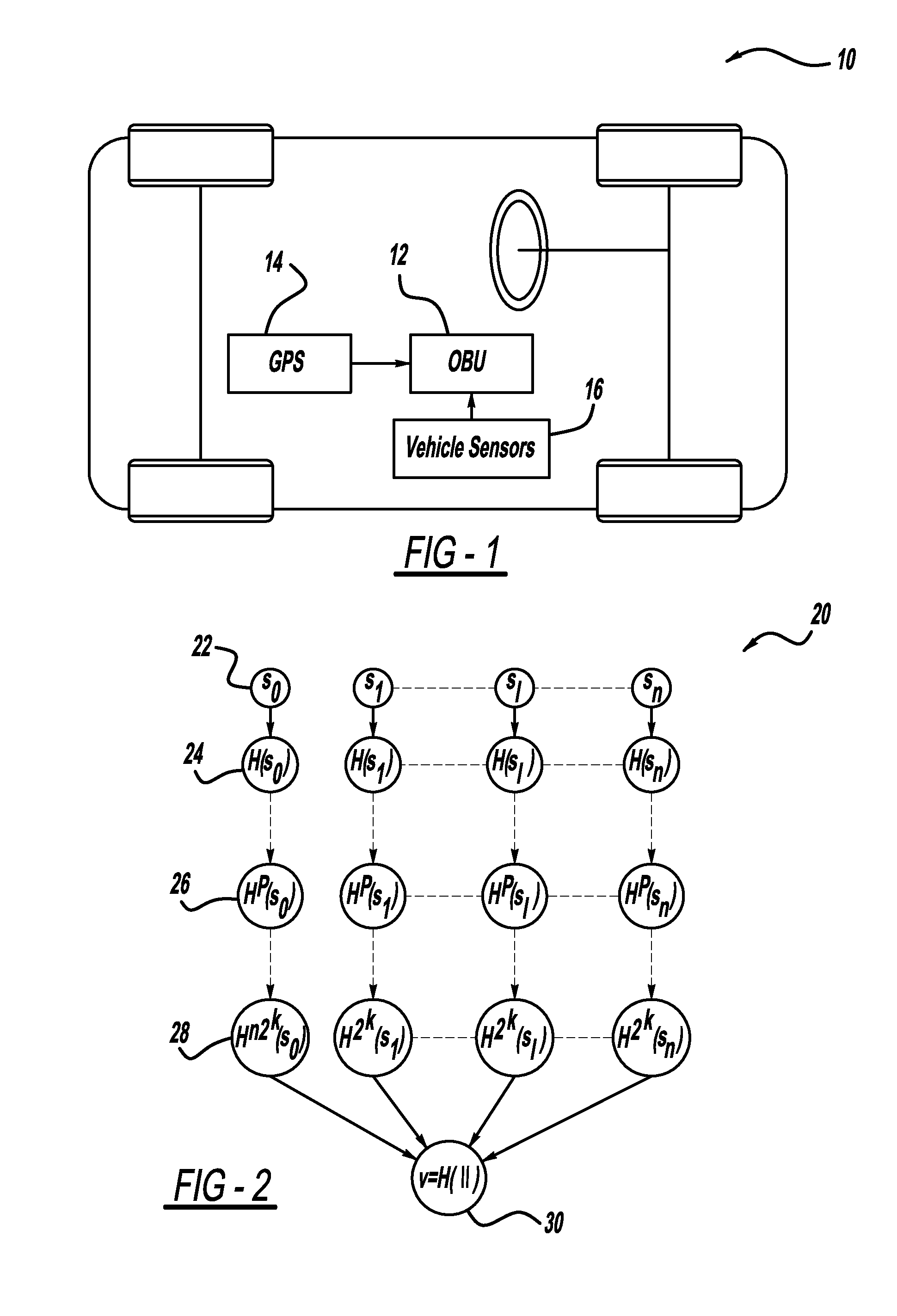
Flexible broadcast authentication in resource-constrained systems: providing a tradeoff between communication and computational overheads
ActiveUS20110066859A1Multiple keys/algorithms usageUser identity/authority verificationGeneration processHash function
A method for authenticating a message that is transmitted wirelessly. The method includes providing a set of private key values that define a private key and performing a key pair generation process that provides a key pair including the private key and a public key, where performing the key pair generation process includes applying one or more hash functions to the private key values, where a succeeding hash function provides a hash of a previous hash function. The scheme uses a signature generation process that generates a message digest by applying a hash function on the message to be signed and then separates the message digest into two parts including signing bits and selection bits and using the private key to sign the message. A receiver verifies the authenticity of the received message using the public key and a signature verification algorithm.
Owner:GM GLOBAL TECH OPERATIONS LLC
Efficient technique to achieve non-repudiation and resilience to DoS attacks in wireless networks
ActiveCN102202303AMultiple keys/algorithms usageRoad vehicles traffic controlWireless mesh networkDigital signature
A computationally efficient message verification strategy that achieves non-repudiation and resilience to computational denial of service attacks in conjunction with a broadcast authentication protocol that authenticates messages using a combination of a digital signature and a TESLA MAC. When messages are received at a receiver, the verification strategy separates the messages into messages with the same sender identification. The strategy then determines whether the TESLA MAC authenticator is valid for each message and discards those messages that do not have a valid TESLA MAC. The strategy collects the messages that have a valid TESLA MAC for each sender identification and performs a batch verification process on the group of messages to determine if the messages in the group have a valid digital signature. This strategy verifies each message in the group of messages if the batch verification process shows that the group of messages has a valid digital signature.
Owner:GM GLOBAL TECH OPERATIONS LLC
Method for broadcast authentication of wireless sensor network based on automaton and game of life
ActiveCN102164369AOvercome structural flawsExpand communication rangeNetwork traffic/resource managementNetwork topologiesMobile wireless sensor networkCluster algorithm
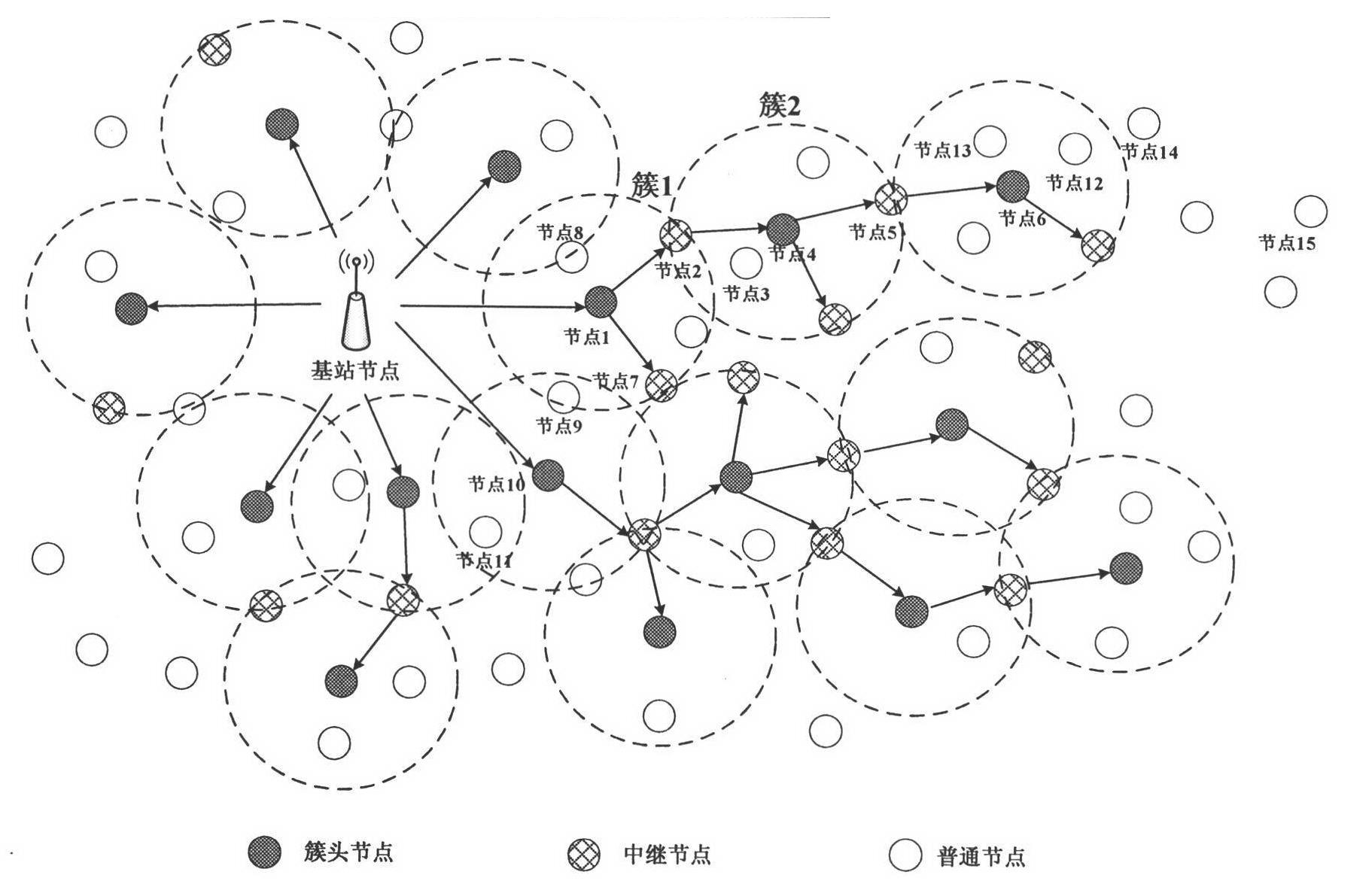
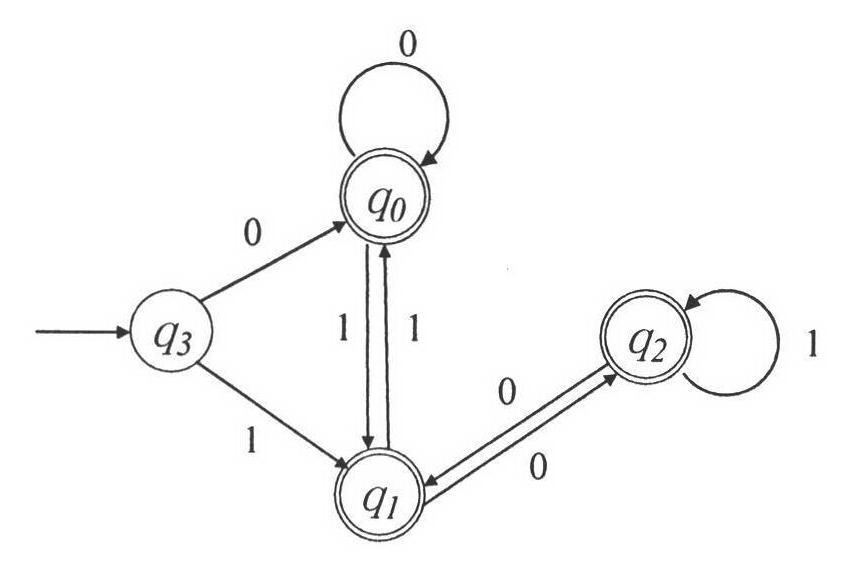
The invention discloses a method for the broadcast authentication of a wireless sensor network based on an automaton and a game of life, which aims at the problems of limitations to coverage and special network traffic distribution of a base station in the authentication of the wireless sensor network which has relatively more hidden dangers due to own characteristics. By the method, the coverageof the base station can be expanded to realize the broadcast of nodes of the whole network, and the distributional pattern of the network traffic of the wireless sensor network (WSN) is simulated. The broadcast authentication of the wireless sensor network is realized mainly by combining a plurality of ways such as an improved deterministic finite automaton, a clustering algorithm, a game of lifealgorithm and the like. A specific technical scheme and specific steps and flows are designed. The method is remarkably distinguished from the conventional broadcast authentication method used for the WSN, and is advanced in the aspects of communication ranges of nodes of the base station, the rational allocation of node energy in the network, the simulation of a network traffic pattern, and the like.
Owner:NANJING UNIV OF POSTS & TELECOMM
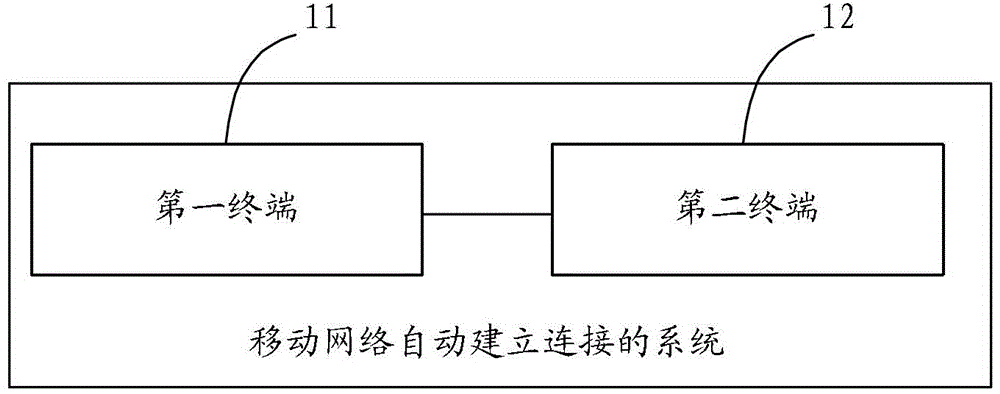
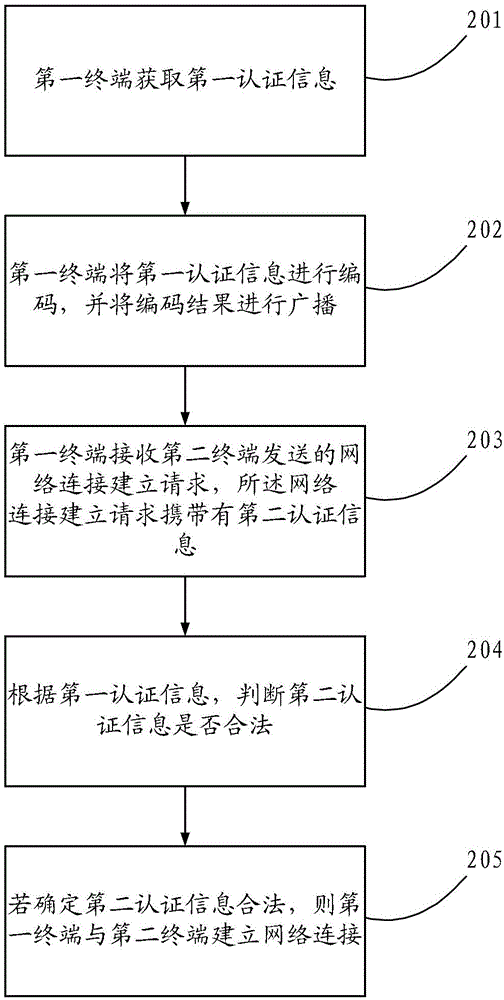
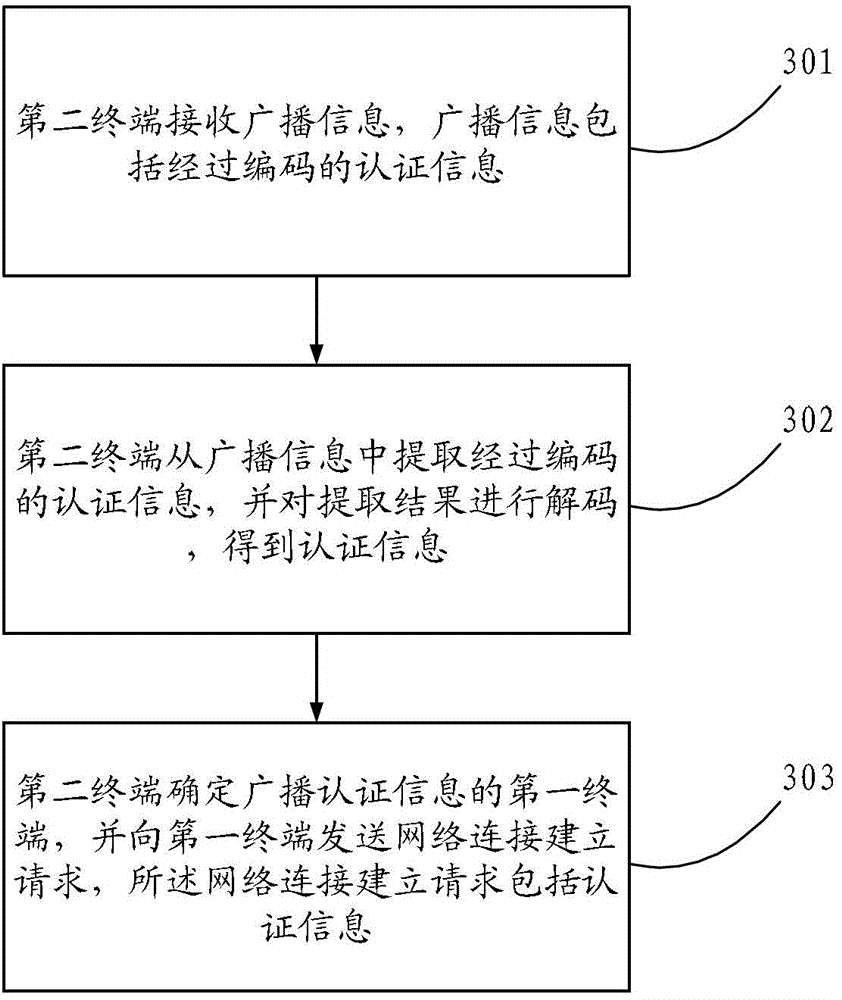
Method for automatically establishing connection of mobile network and terminal
InactiveCN104427471AImprove connection establishment speedImprove experienceAssess restrictionConnection managementNetwork connectionTerminal equipment
Disclosed are a method for a mobile network to automatically establish a connection, and a terminal, which can solve the problems of a complex operation and a low efficiency due to the fact that, in the process of network connection between an access point terminal and other terminals, a user is required to manually set a lot of information and operations to complete this network connection process. In the technical solution of the present invention, an access point terminal can broadcast authentication information which is needed for accessing other terminals to the network connection. After receiving the broadcast, other terminals can acquire the authentication information from the broadcasted information and then establish a network connection with the terminal which sends the broadcast, according to the acquired authentication information. The present invention is mainly applied to the process of establishing a network connection between terminal devices.
Owner:HUAWEI TECH CO LTD
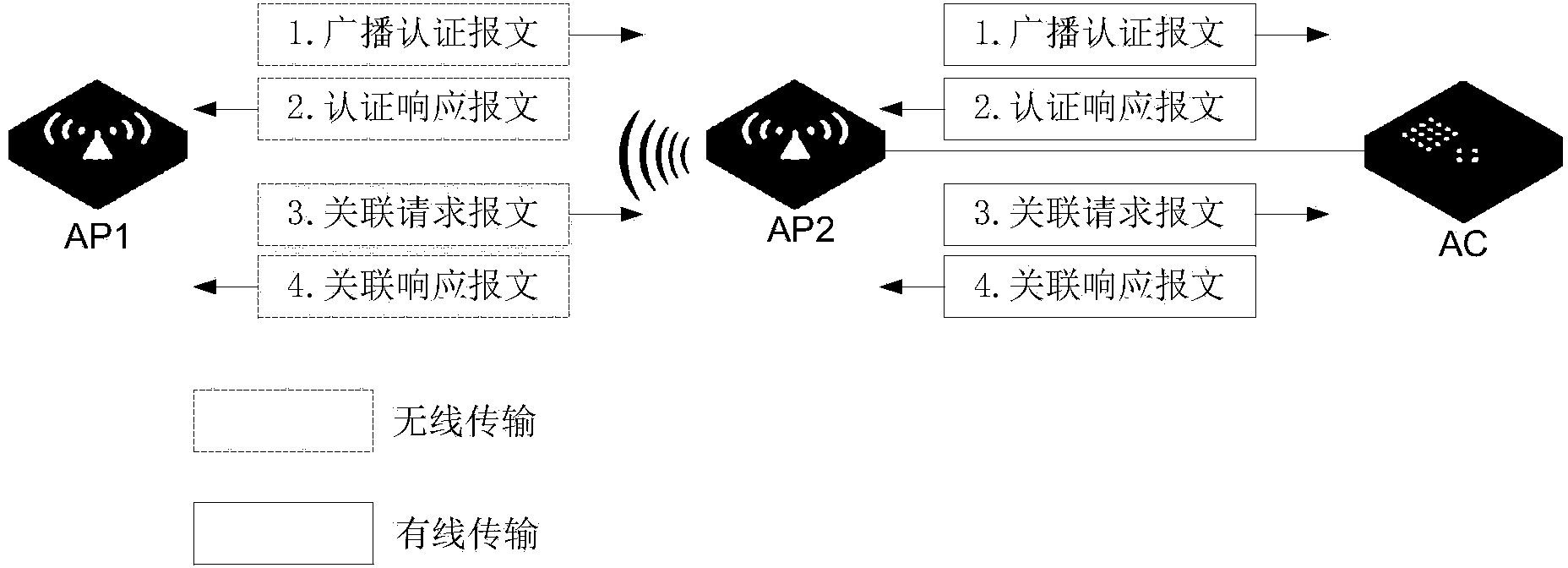
AP failure processing method, AP device and AC device
The invention provides an AP failure processing method, an AP device and an AC device. The method includes the first step of sending a wireless radio authentication message in case of failure of obtaining an IP address, the second step of sending an association request message to an AC through an neighboring AP when an authentication response message sent by the AC and transferred by the neighboring AP through the wireless network is received, wherein the authentication response message is sent aiming at a broadcasting authentication message, the third step of receiving an association response message sent by the AC and transferred by the neighboring AP through the wireless network, wherein the association response message contains an IP address distributed by the AC, and the fourth step of using the IP address to send a fault information message to the AC through the neighboring AP. According to the technical scheme, a fault AP can be quickly found and located.
Owner:NEW H3C TECH CO LTD
Flexible broadcast authentication in resource-constrained systems: providing a tradeoff between communication and computational overheads
ActiveUS8452969B2Multiple keys/algorithms usageUser identity/authority verificationGeneration processHash function
A method for authenticating a message that is transmitted wirelessly. The method includes providing a set of private key values that define a private key and performing a key pair generation process that provides a key pair including the private key and a public key, where performing the key pair generation process includes applying one or more hash functions to the private key values, where a succeeding hash function provides a hash of a previous hash function. The scheme uses a signature generation process that generates a message digest by applying a hash function on the message to be signed and then separates the message digest into two parts including signing bits and selection bits and using the private key to sign the message. A receiver verifies the authenticity of the received message using the public key and a signature verification algorithm.
Owner:GM GLOBAL TECH OPERATIONS LLC
Authentication Method Employing Elliptic Curve Cryptography
ActiveUS20090180612A1Digital data processing detailsUser identity/authority verificationComputer hardwareEnd system
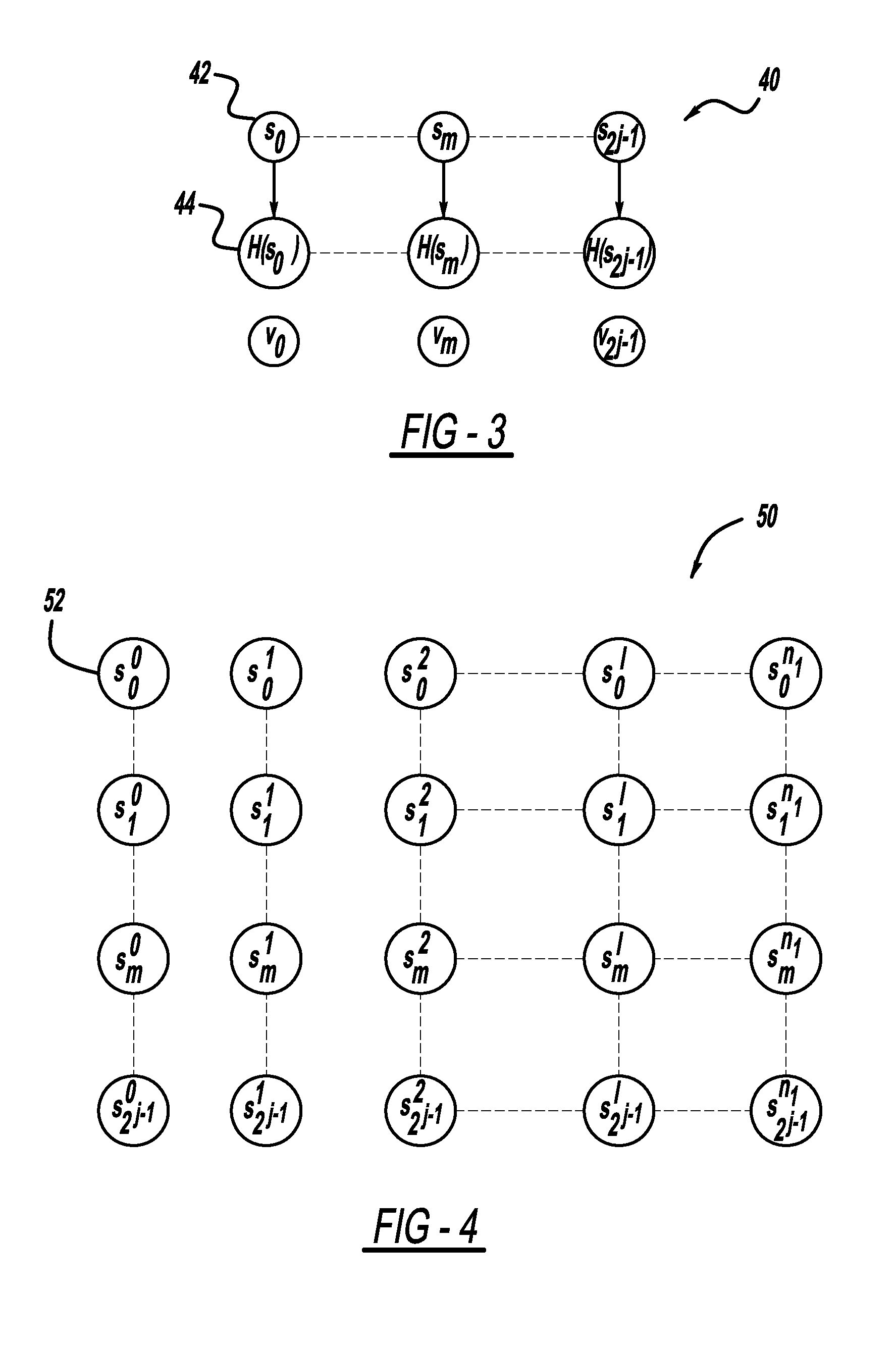
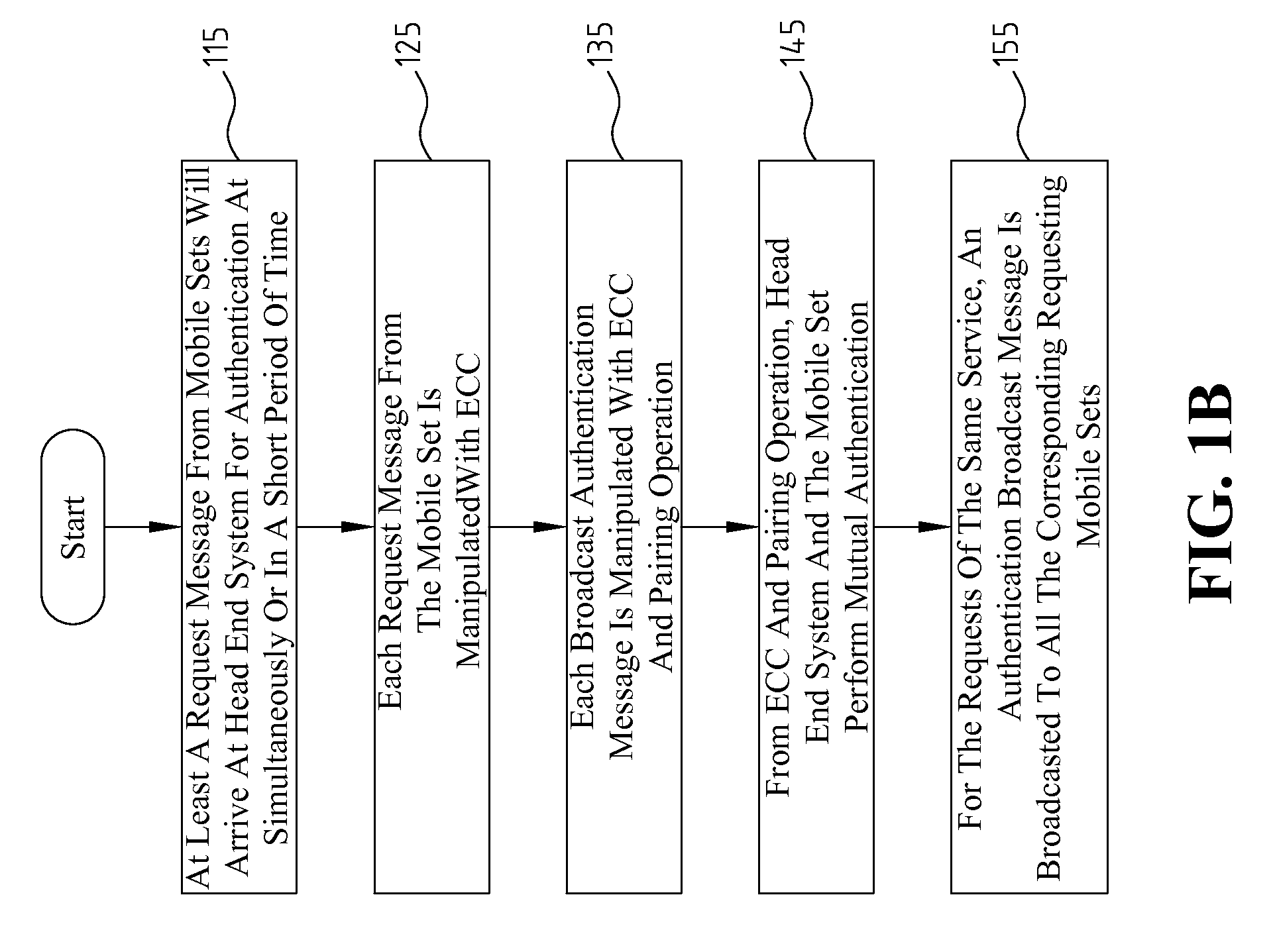
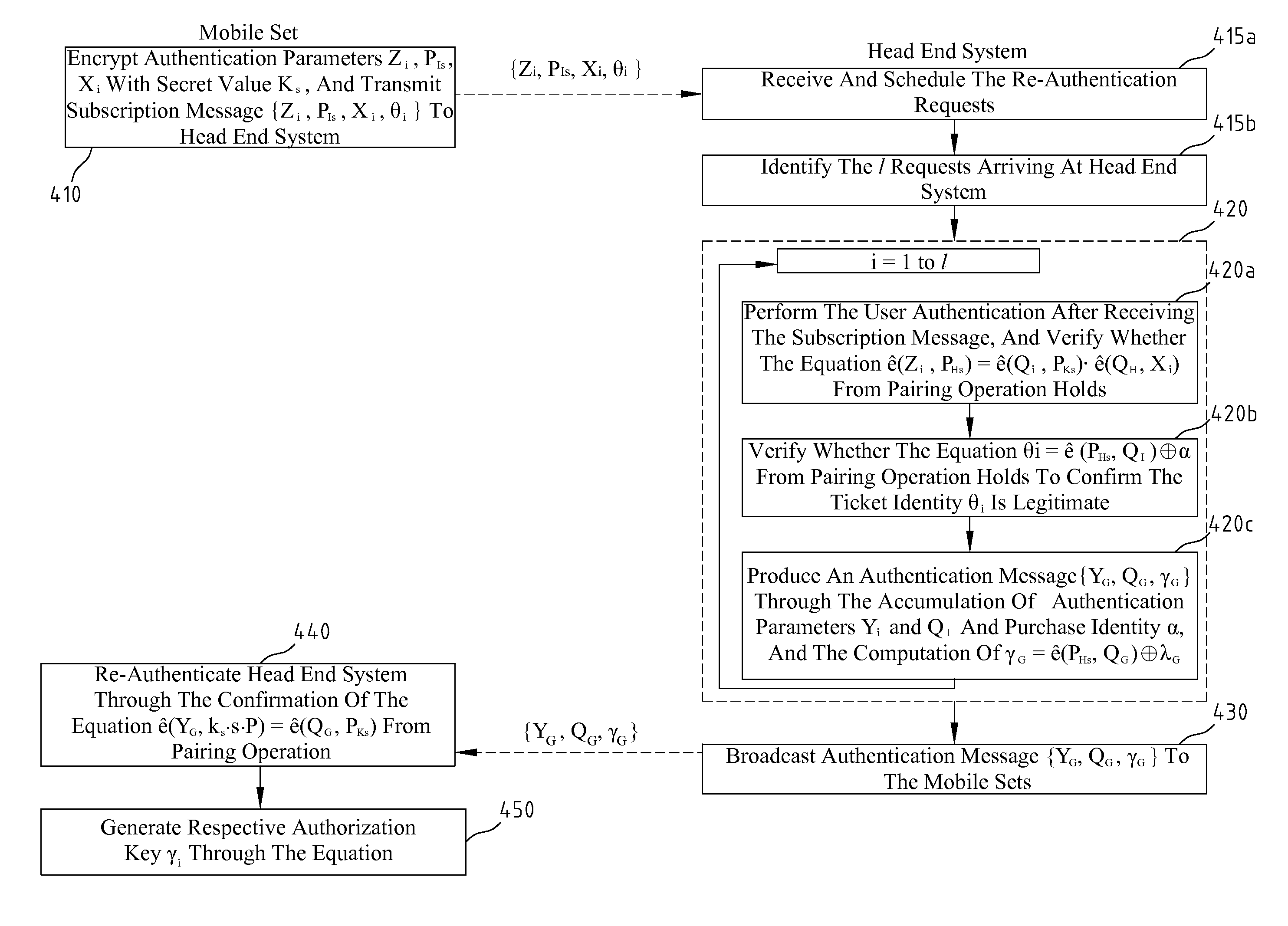
Disclosed is an authentication method employing elliptic curve cryptography (ECC), applicable to a mobile broadcast TV system having one or more head end systems, at least a transmitter, and at least a mobile set. The authentication method comprises at least one request message from mobile sets simultaneously or in a short period of time arriving at a head end system for authentication; manipulating each broadcast authentication message by ECC; manipulating each service request message by ECC and pairing operation; performing a mutual authentication between the head end system and mobile sets by ECC and pairing operation; and broadcasting one group of authentication messages to all the mobile sets of many requests arrived at the head end system simultaneously or in a short period of time for the same service.
Owner:IND TECH RES INST
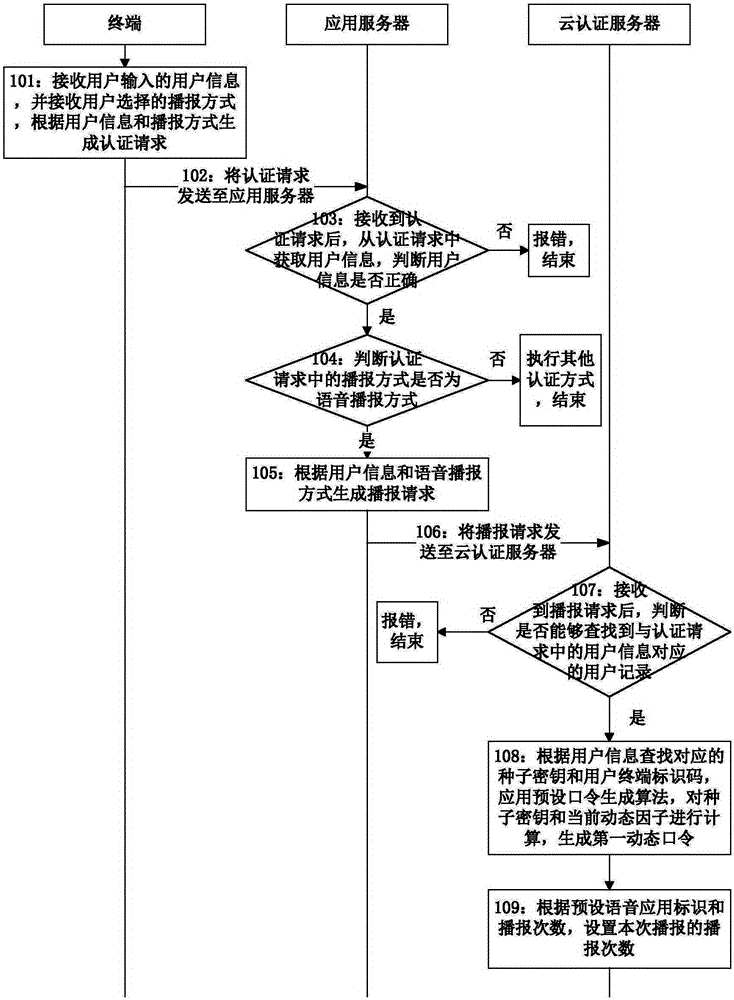
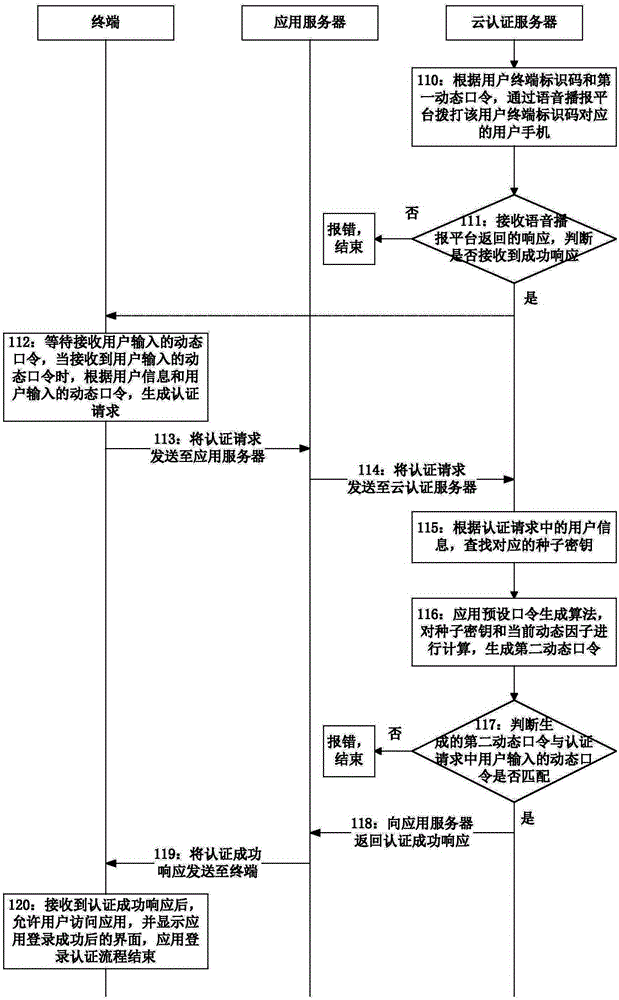
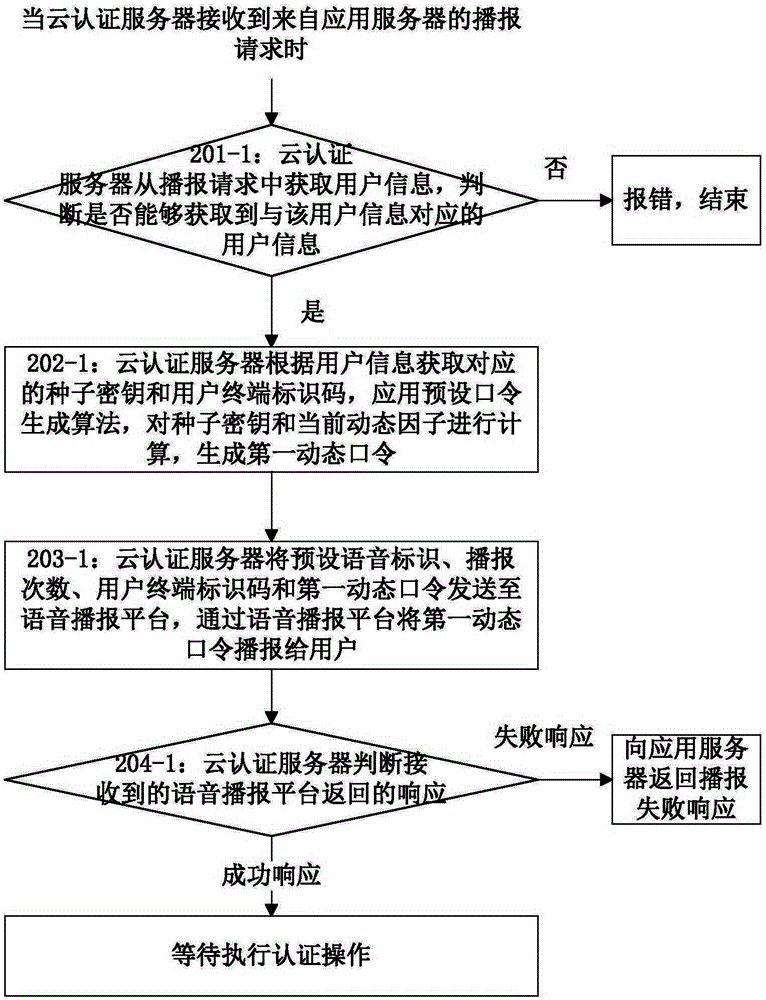
Method for realizing voice broadcast authentication and cloud authentication server
InactiveCN105323251APrevent snooping and stealingEnsure safetyUser identity/authority verificationUser inputPassword
The invention discloses a method for realizing voice broadcast authentication and a cloud authentication server thereof, and belongs to the field of information security. The method comprises the following steps: when receiving a broadcast request, the cloud authentication server obtains a corresponding seed key and a user terminal identification code according to user information in the broadcast request, calculates the seed key to generate a first dynamic password and sends the first dynamic password to a voice broadcast platform according to the user terminal identification code to be broadcasted; and when receiving an authentication request, the cloud authentication server obtains a corresponding seed key according to user information in the authentication request, and calculates the seed key to generate a second dynamic password, and when the first dynamic password input by a user is matched with the second dynamic password in the authentication request, the authentication is successful. By adopting the method in the technical scheme of the invention, the generated dynamic password can be broadcasted to the user by the voice broadcast platform, and the dynamic password is prevented from being spied and stolen after being generated, so that the authentication security is guaranteed.
Owner:FEITIAN TECHNOLOGIES
Efficient technique to achieve non-repudiation and resilience to DoS attacks in wireless networks
ActiveUS8904183B2Multiple keys/algorithms usageParticular environment based servicesWireless mesh networkDigital signature
A computationally efficient message verification strategy that achieves non-repudiation and resilience to computational denial of service attacks in conjunction with a broadcast authentication protocol that authenticates messages using a combination of a digital signature and a TESLA MAC. When messages are received at a receiver, the verification strategy separates the messages into messages with the same sender identification. The strategy then determines whether the TESLA MAC authenticator is valid for each message and discards those messages that do not have a valid TESLA MAC. The strategy collects the messages that have a valid TESLA MAC for each sender identification and performs a batch verification process on the group of messages to determine if the messages in the group have a valid digital signature. This strategy verifies each message in the group of messages if the batch verification process shows that the group of messages has a valid digital signature.
Owner:GM GLOBAL TECH OPERATIONS LLC
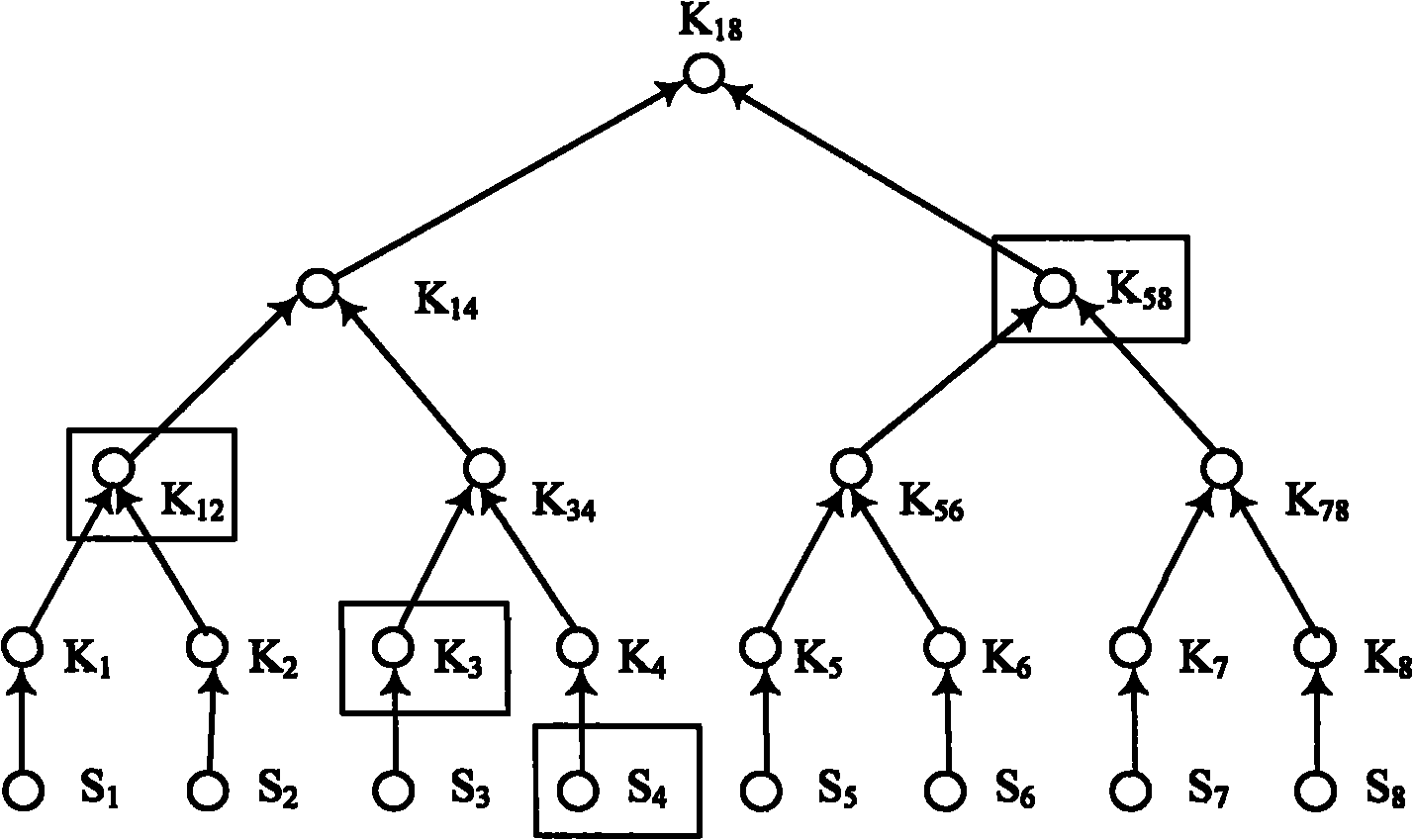
Broadcast authentication method for wireless network with limited node resource
ActiveCN101877690AReduce broadcast authentication overheadImprove undo efficiencySpecial service provision for substationUser identity/authority verificationParameter distributionBroadcasting
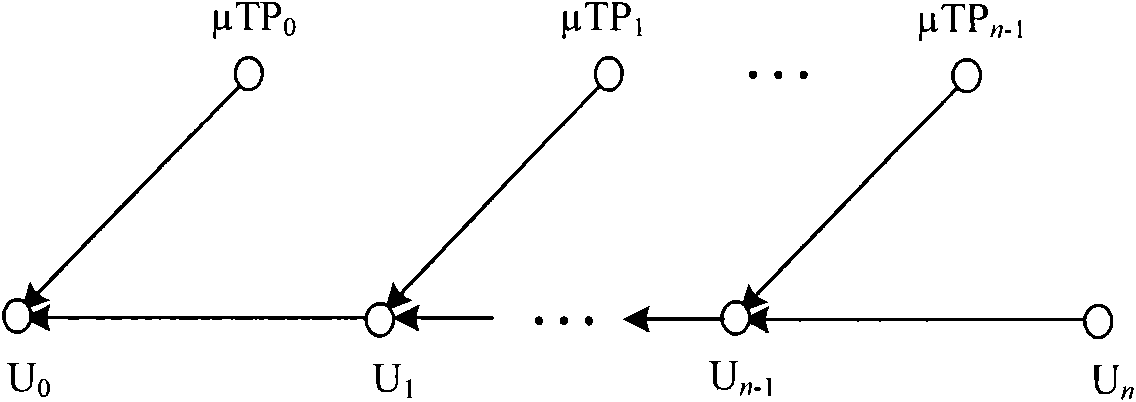
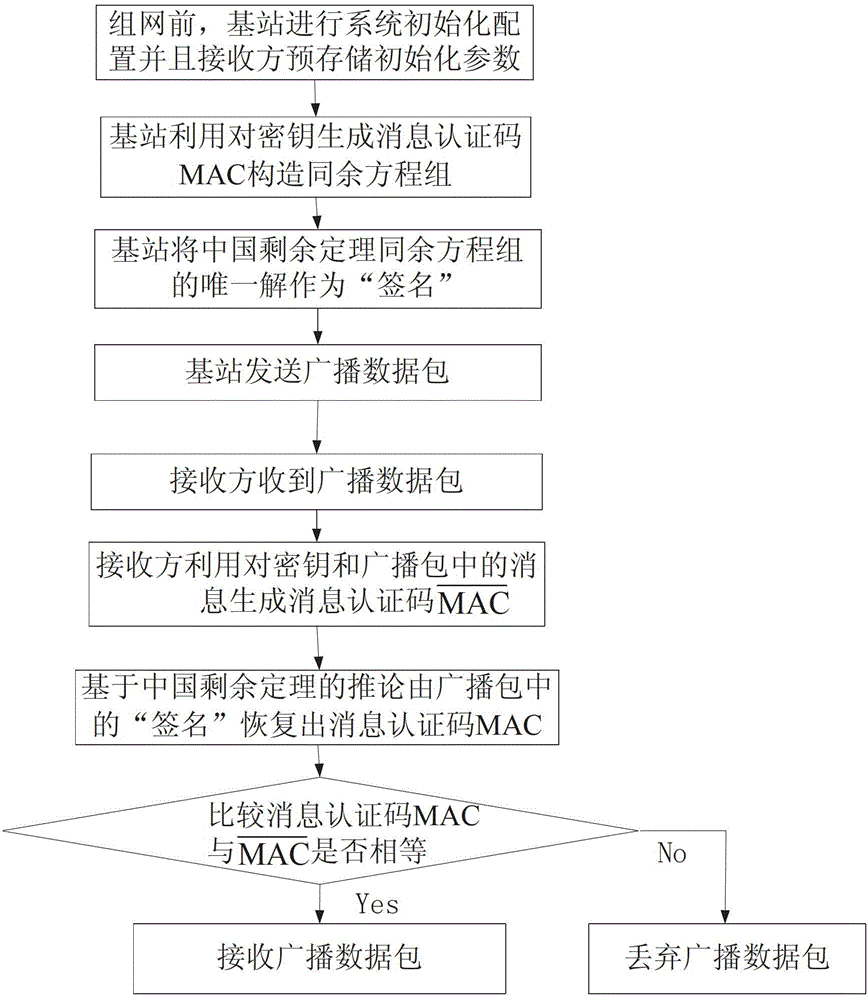
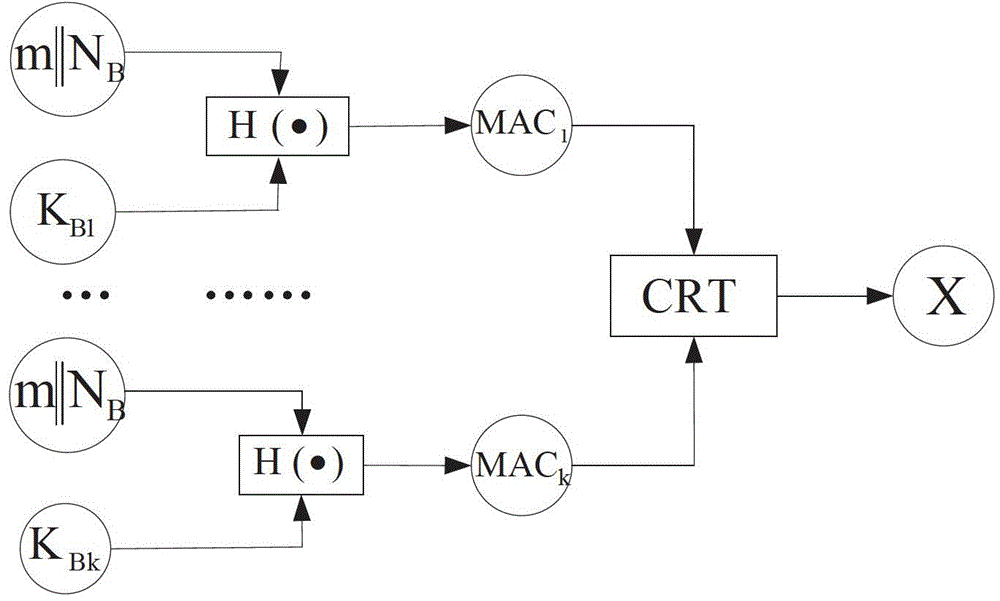
The invention provides a broadcast authentication method for a wireless network with a limited node resource. The method comprises the following steps that: 1), a protocol is initialized; 2), a broadcast node (BNode) requests a mu TESLA parameter chain to a back server (BServer); 3), a receiving node (RNode) authenticates the broadcast node (BNode); 4), the broadcast node (BNode) distributes mu TESLA parameters; and 5), the receiving node (RNode) authenticates the broadcast information of the broadcast node (BNode). On the basis of a one-way chain and a Merkle tree mechanism, and by constructing the mu TESLA parameter chain mu TPC and mu TPC tree mu TPCT, the broadcast authentication method realizes safe and highly efficient mu TESLA parameter distribution, improves the tree-based mu TESLA method, is more suitable for the broadcast authentication for the wireless network of which the node resource is limited, can resist DoS attacks in the mu TESLA parameter distribution process, has low calculation, communication and storage costs, can immediately eliminate authentication capacity of a captured node, and is applied to the large-scale wireless network with a plurality of broadcast nodes.
Owner:CHINA IWNCOMM
Lightweight authentication protocol based on one-way function
ActiveCN107395627AAvoid Flood DoS AttacksKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCryptosystemOne-way function
The invention discloses a lightweight authentication protocol based on a one-way function, characterized by comprising the following steps: 1) key generation: selecting required parameters based on an RSA cryptosystem, and generating a key pair for each member; 2) user registration: submitting registration information via a secure channel by a user; 3) authentication and broadcast: acknowledging user's identity in the authentication process, encrypting information and sending the encrypted information in a broadcast manner; and 4) password change: changing a password in a convenient and efficient manner. The lightweight authentication protocol has the advantages: Flood type DoS attack caused by high-complexity operation of a server due to playback success is avoided while playback attack is defended. Moreover, in consideration with the packet loss rate of the channel, the counter values of double communication parties can be allowed to have a difference within a certain range, and once the values exceed the range, the channel is regarded to have too high error rate or to be attacked.
Owner:HOHAI UNIV
IPTV program generating method and system based on next generation network
InactiveCN101360222ARich program contentEasy to implementSpecial service provision for substationAnalogue secracy/subscription systemsUser equipmentComputer science
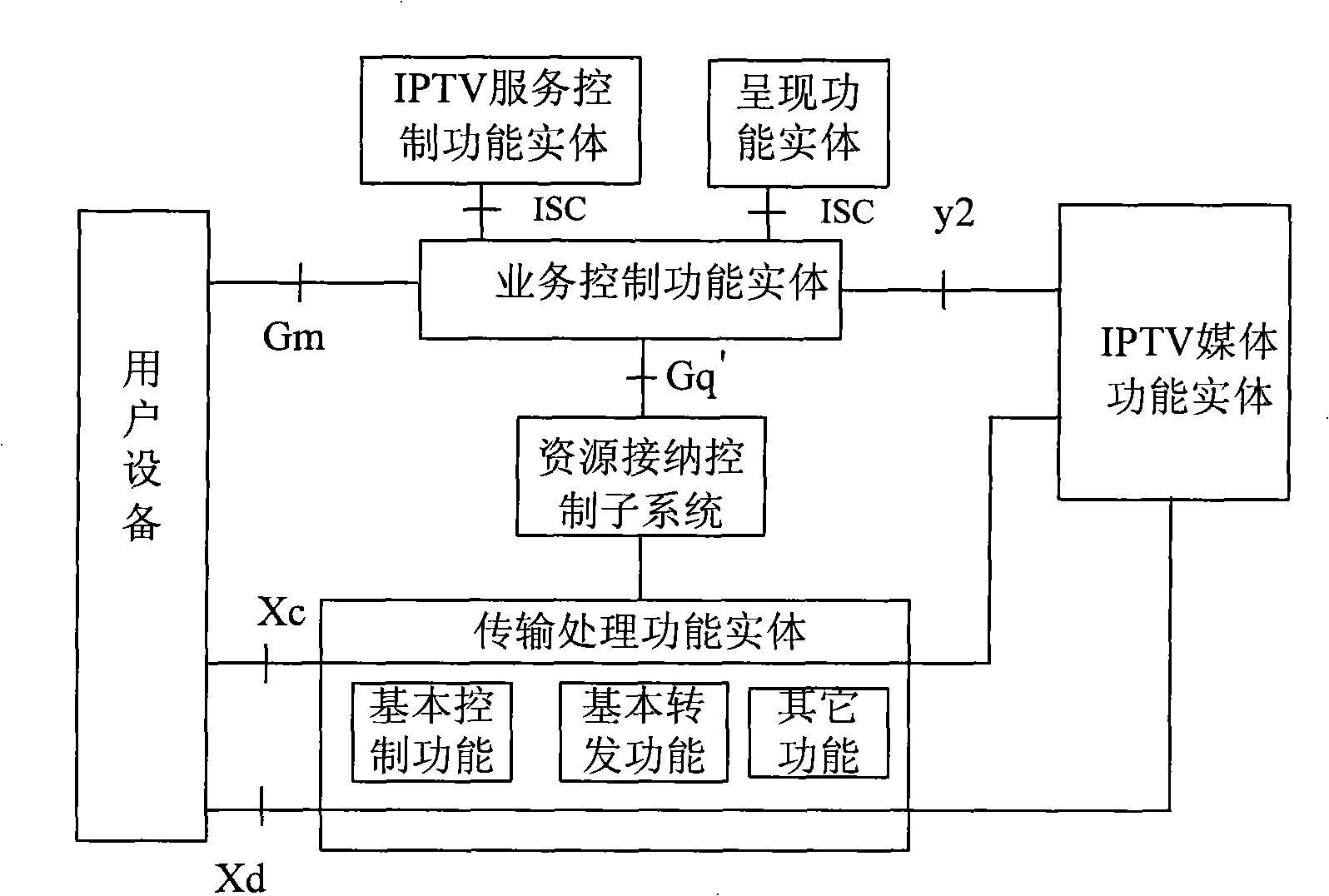
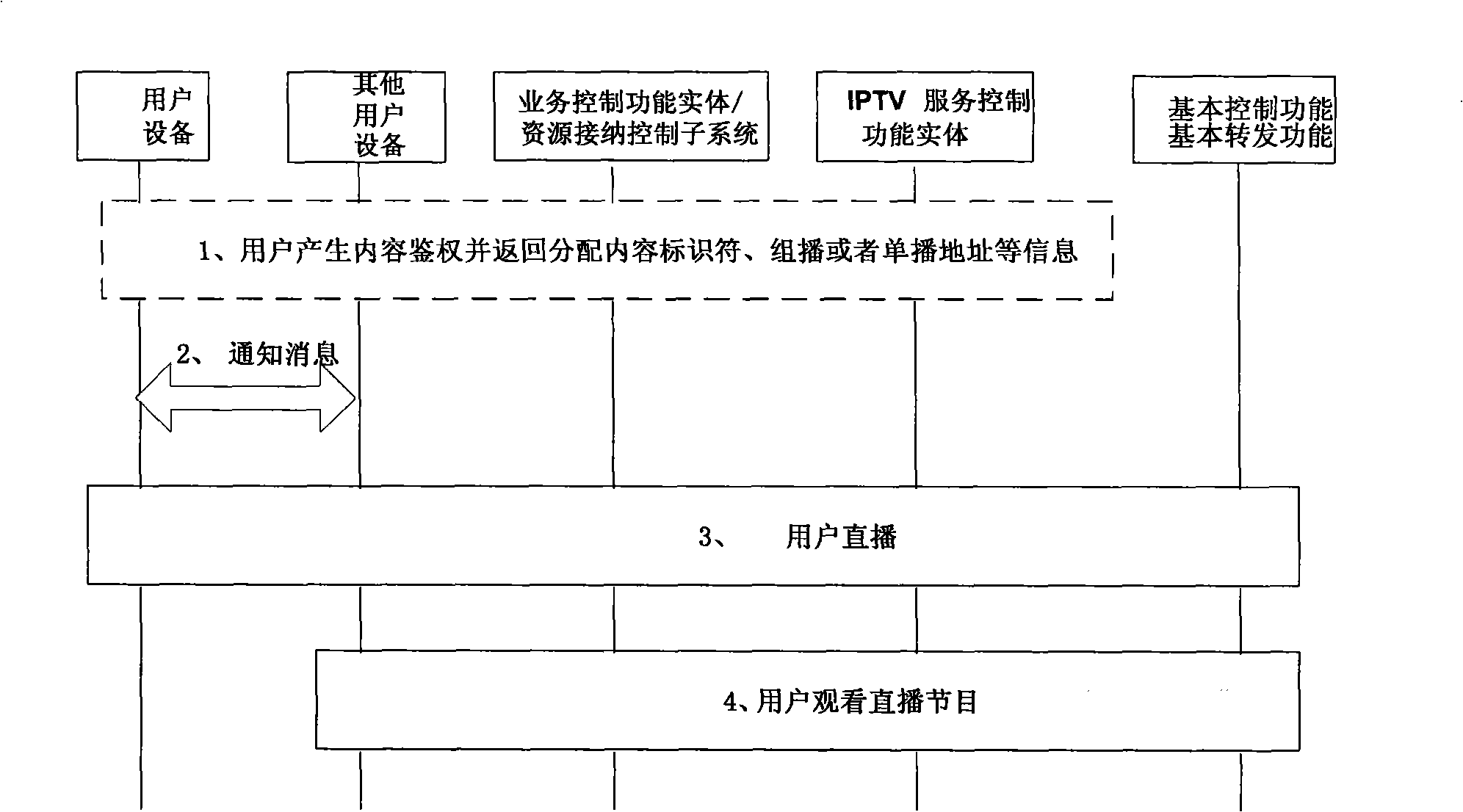
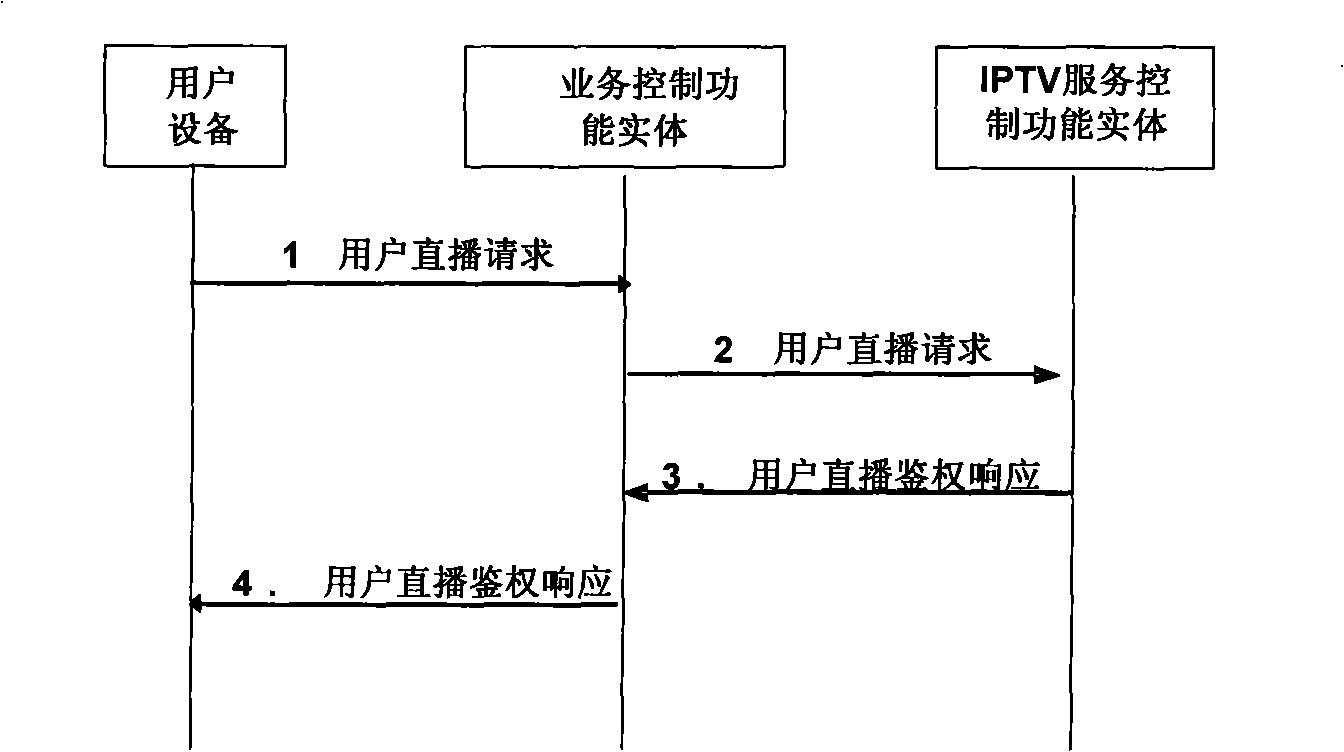
The invention discloses a generating method and a system for IPTV programs based on the next-generation network, making live broadcast to other user equipment to enrich content of IPTV service by an IPTV user equipment, and the method and the system mainly adopt the technical proposal that: step A. the IPTV user equipment initiates a program live broadcast authentication request; step B. the authentication request in the step A is examined to decide whether to permit the IPTV user equipment to make program live broadcast to other IPTV user equipment; step C. the IPTV user equipment sends live broadcast notification messages to the other user equipment if the authentication request is approved; and step D. the IPTV user equipment generates live streams from content of the programs by way of unicast or multicast so that other user equipment can join in the live streams; and a live source thereof can be a transmission processing functional entity of an IPTV system, and also can be an IPTV media functional entity.
Owner:ZTE CORP
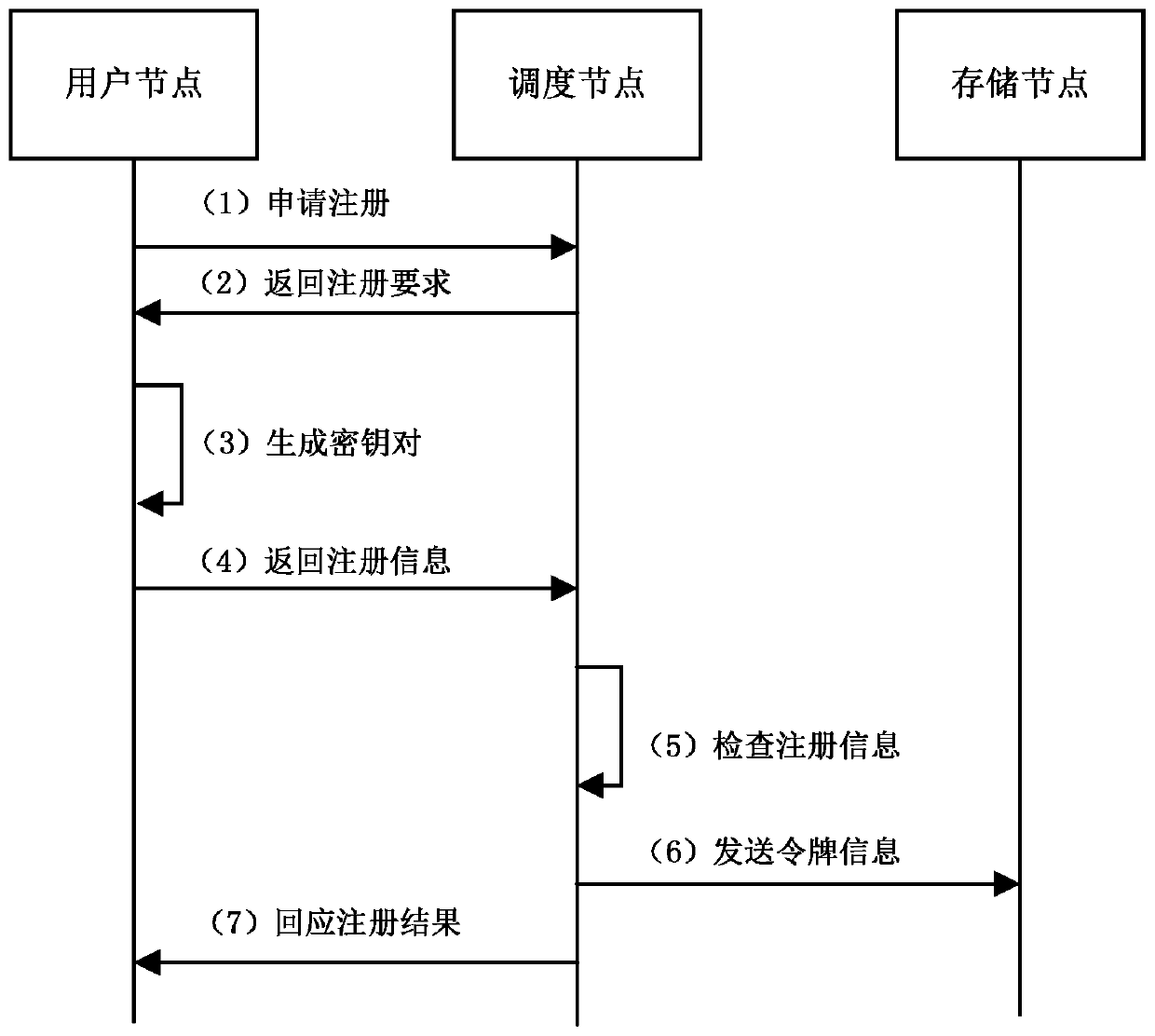
Distributed identity authentication method
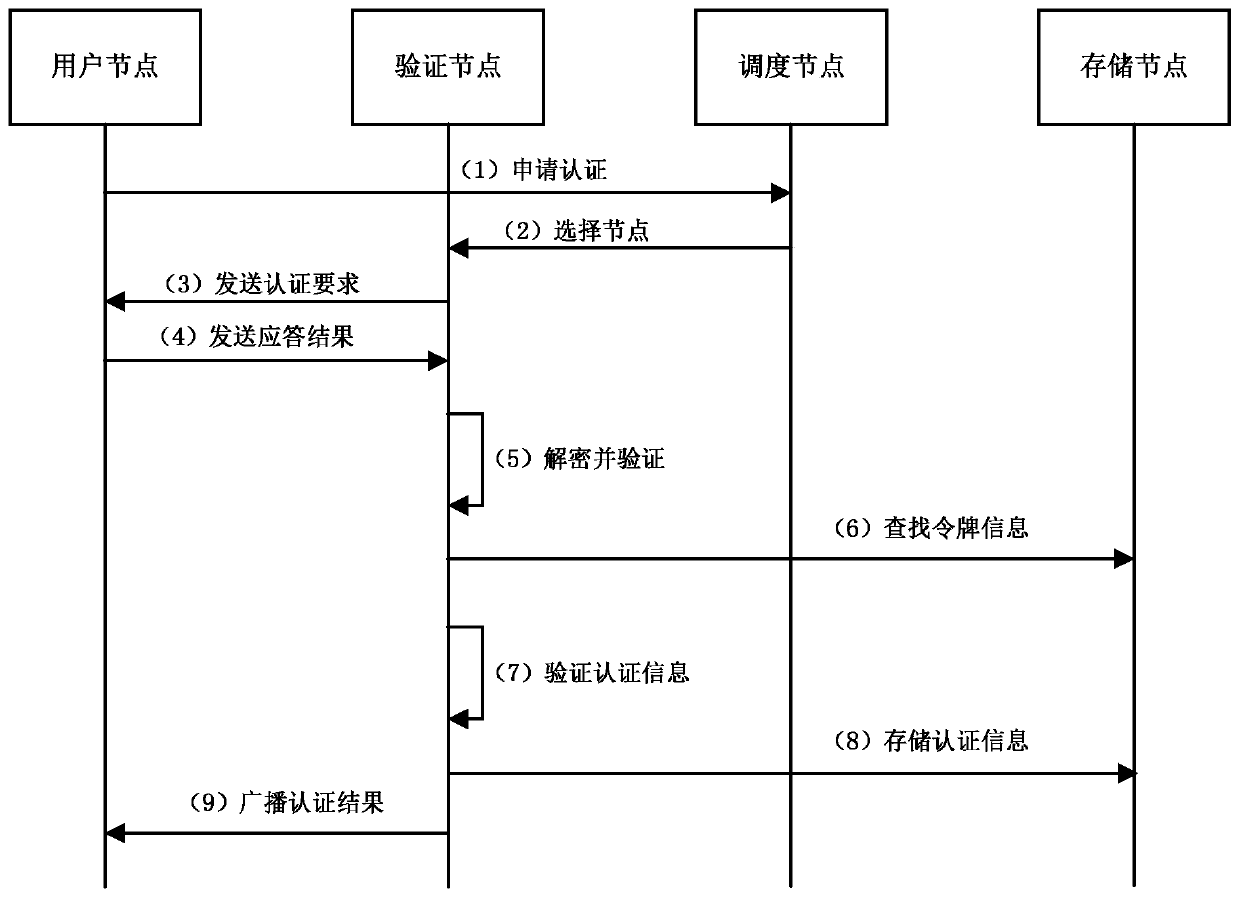
PendingCN110912687AImprove authentication efficiencyDoes not occupy local resourcesKey distribution for secure communicationPublic key for secure communicationDistributed computingBroadcast authentication
The invention discloses a distributed identity verification method, which comprises the following steps: a user node sending an authentication request to a scheduling node, and selecting a verification node; the verification node sending an authentication request to the user node, and the user node sending a response result to the verification node; the verification node verifying the response result to determine whether the authentication is successful or not; the verification node searching token information from the storage node according to the public key of the user node; matching the token information with the authentication information provided by the user node, judging and verifying whether the authentication information is valid or not, if yes, generating new authentication information according to the user data and storing the information in the storage node, and further broadcasting authentication success information to the user node. According to the invention, identity authentication can be reliably realized, the authentication efficiency is high, the authentication is reliable, and local resources are not occupied.
Owner:上海海加网络科技有限公司
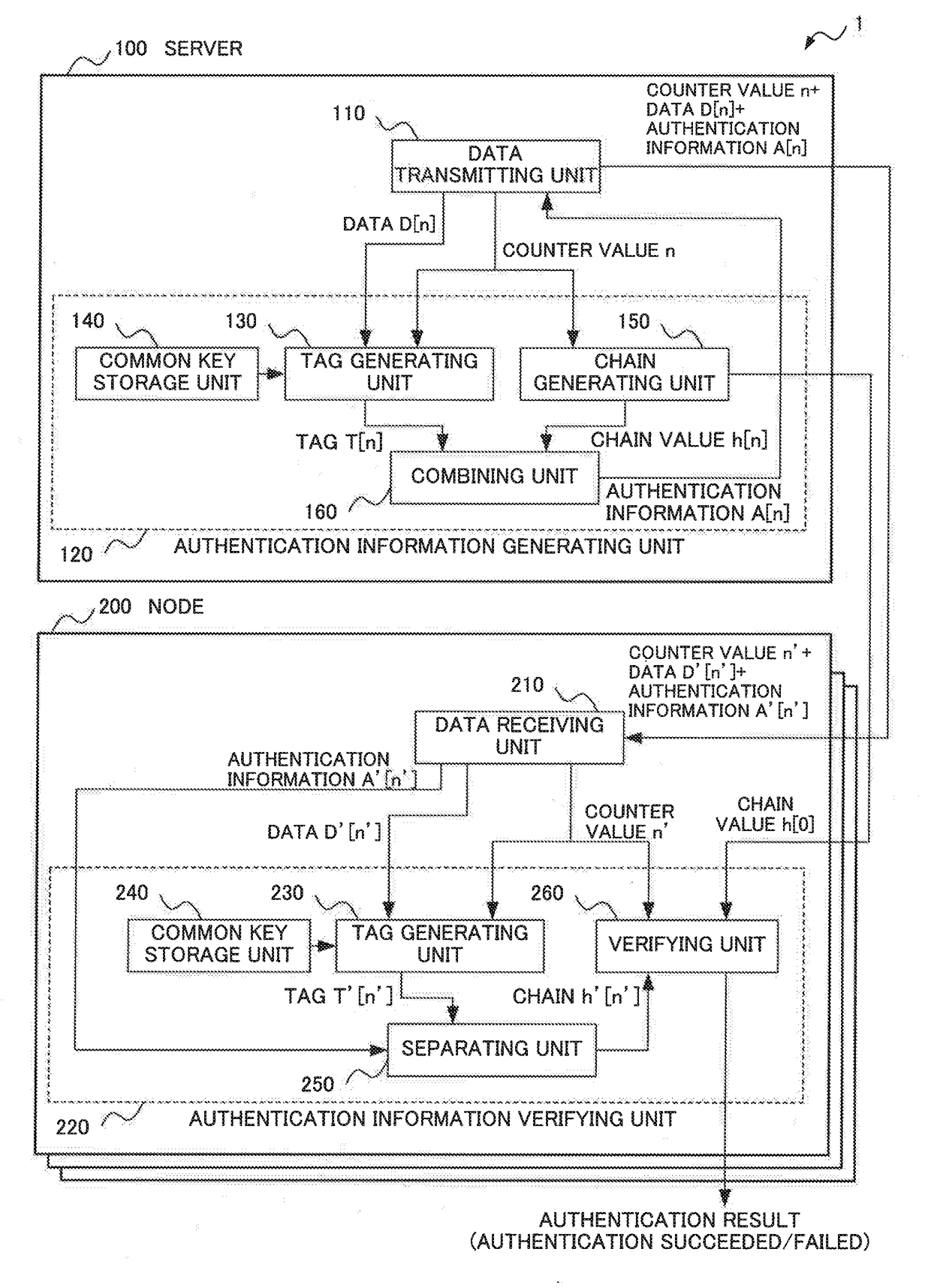
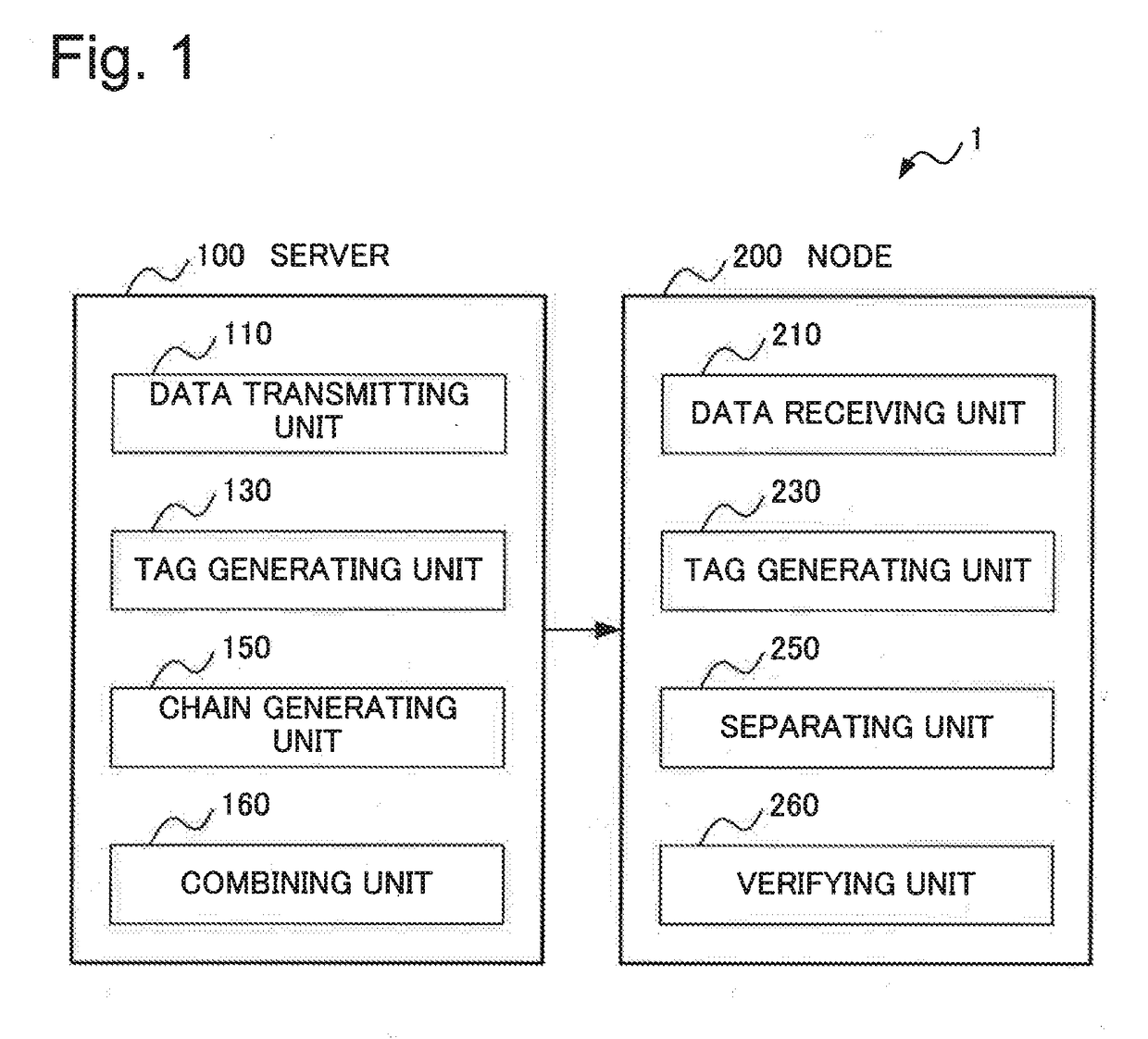
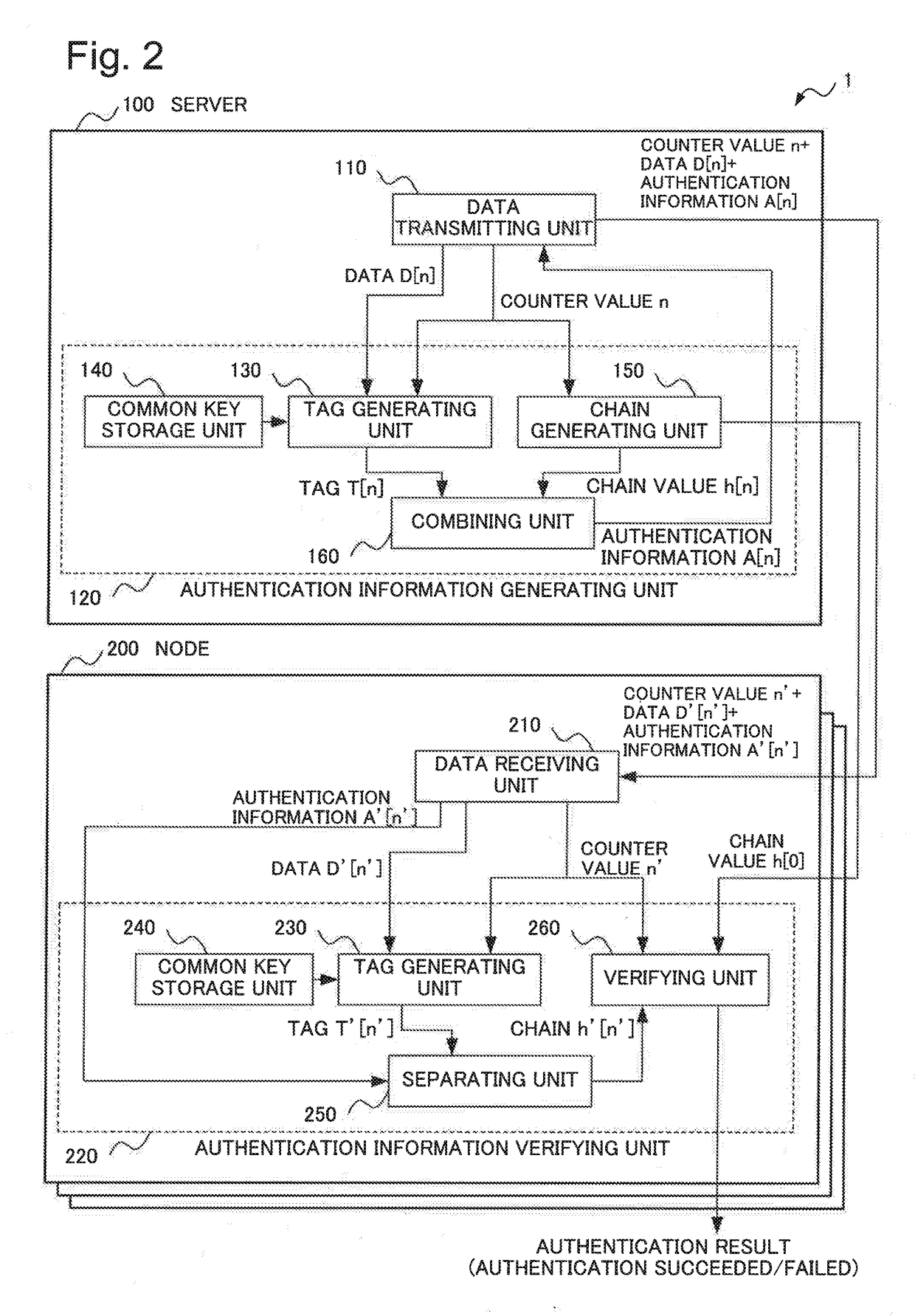
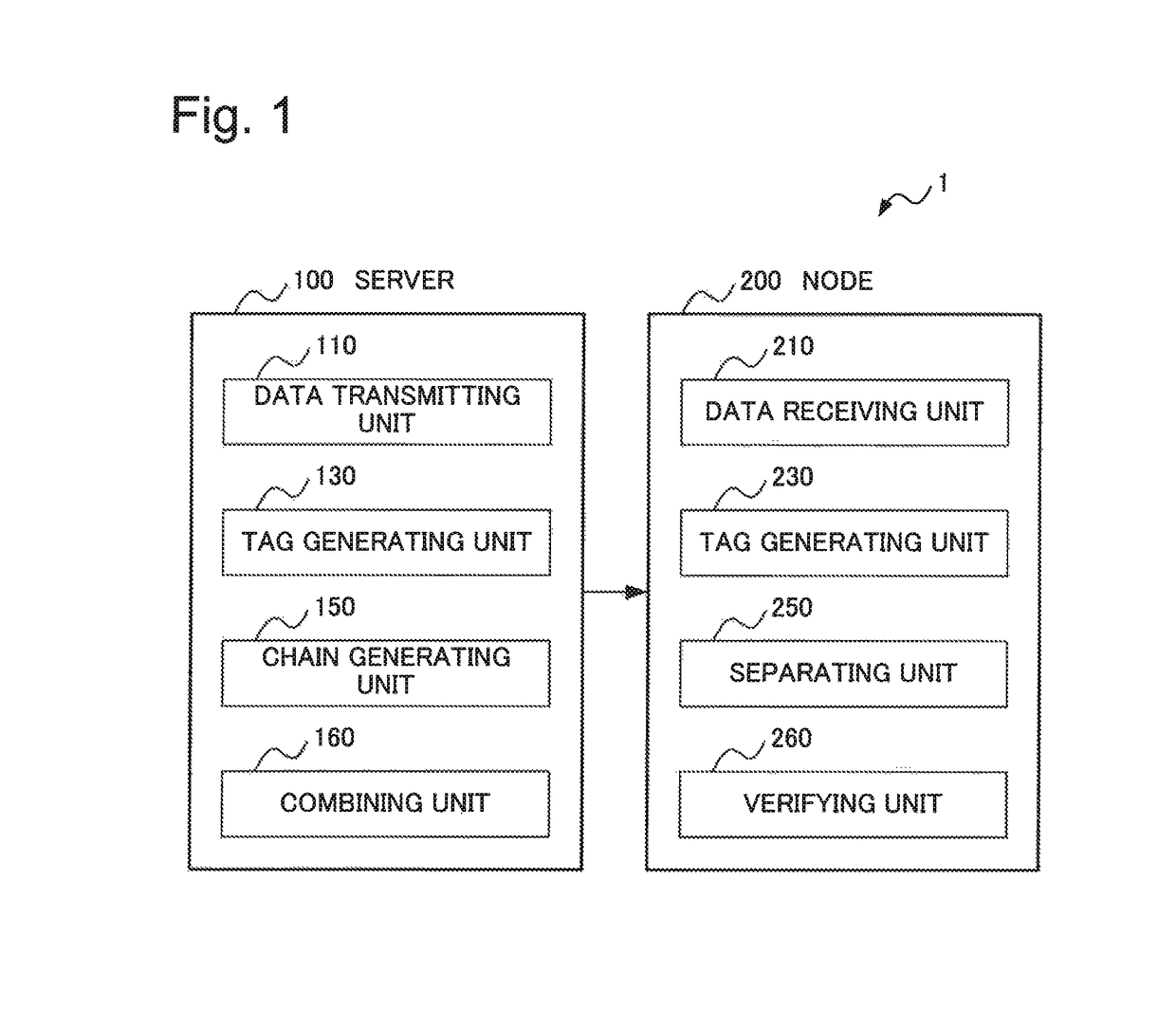
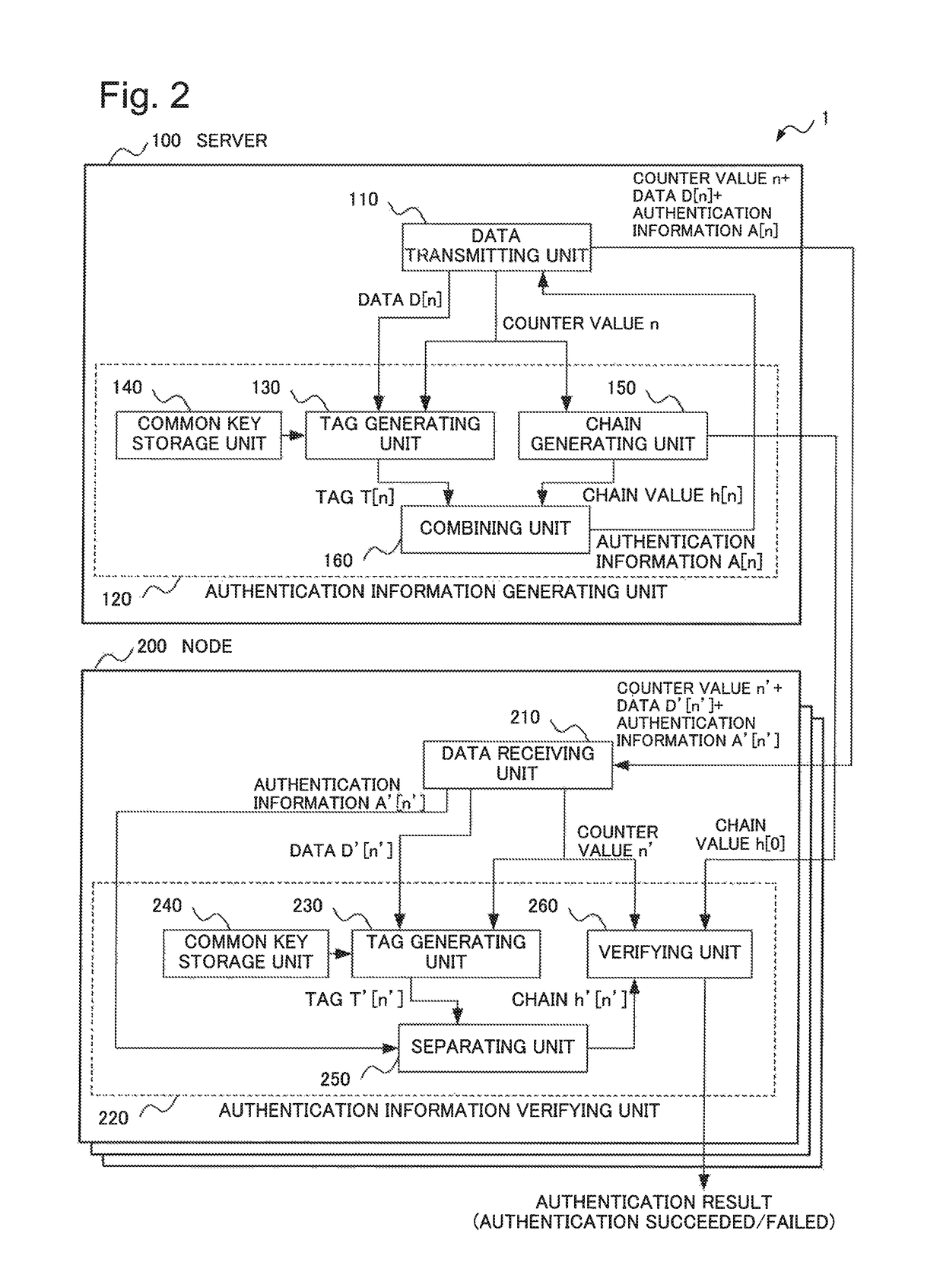
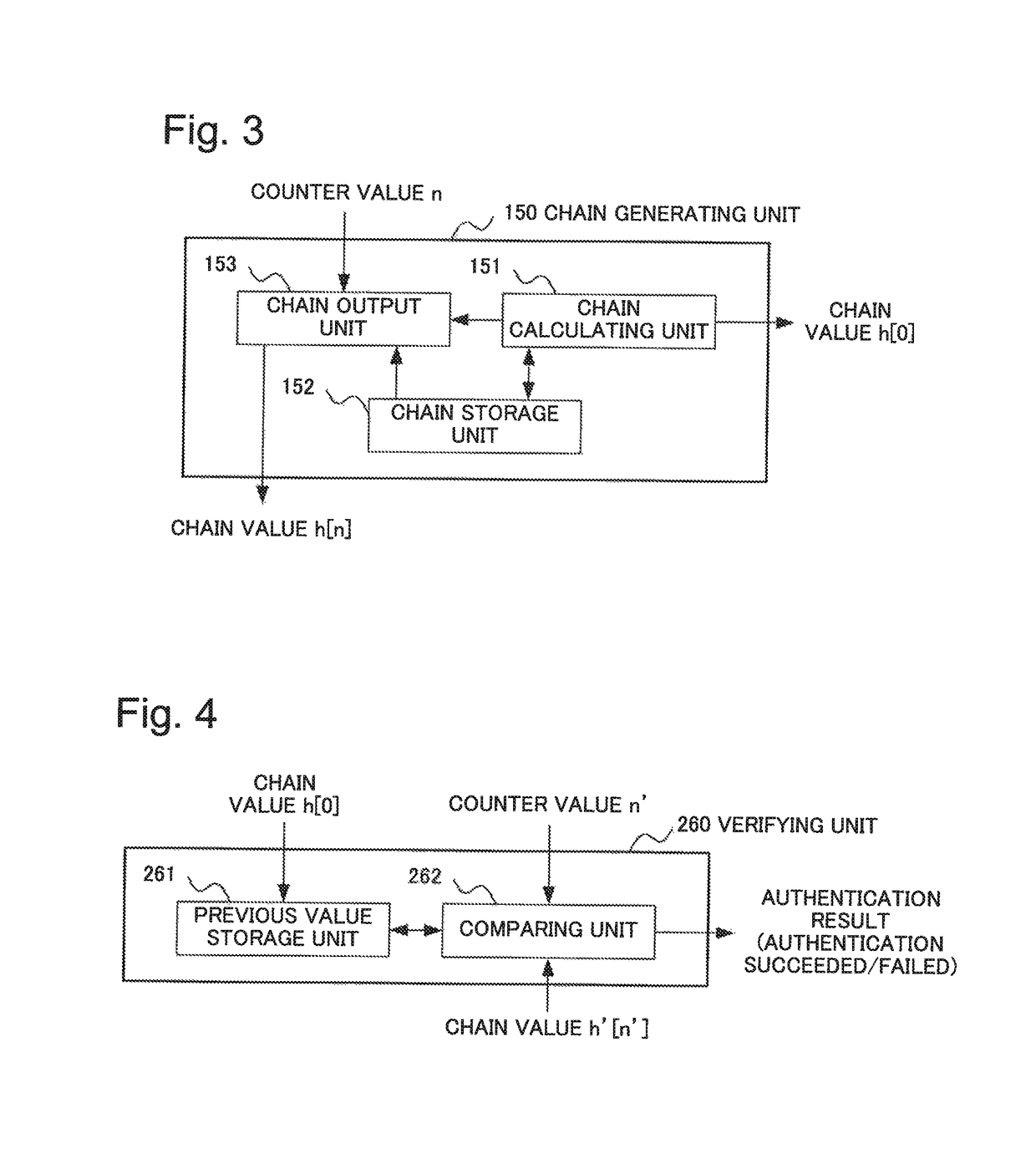
Information processing system, information processing apparatus, information processing method, and recording medium
ActiveUS20170318002A1Highly secure broadcast authenticationReduce delaysUser identity/authority verificationInformation processingOne-way function
An information processing system performing highly secure broadcast authentication while reducing a delay until authentication, a communication amount, and a computation amount is provided. A server (100) generates authentication information for transmission data by combining a tag relating to the transmission data and a chain value associated in a chain with transmission order of the transmission data. The tag relating to the transmission data is generated by using a common key. The chain is generated by using a one-way function. A node (200) verifies whether a chain value associated with transmission order of data received in the past is generated or not by applying the one-way function to a chain value extracted by using a tag relating to the received data and authentication information for the received data. The tag relating to the received data is generated by using the common key.
Owner:NEC CORP
Information processing system, information processing apparatus, information processing method, and recording medium
ActiveUS10200356B2Highly secure broadcast authenticationDelay amountUser identity/authority verificationInformation processingOne-way function
An information processing system performing highly secure broadcast authentication while reducing a delay until authentication, a communication amount, and a computation amount is provided. A server (100) generates authentication information for transmission data by combining a tag relating to the transmission data and a chain value associated in a chain with transmission order of the transmission data. The tag relating to the transmission data is generated by using a common key. The chain is generated by using a one-way function. A node (200) verifies whether a chain value associated with transmission order of data received in the past is generated or not by applying the one-way function to a chain value extracted by using a tag relating to the received data and authentication information for the received data. The tag relating to the received data is generated by using the common key.
Owner:NEC CORP
Authentication method employing elliptic curve cryptography
ActiveUS8117447B2Digital data processing detailsUser identity/authority verificationEnd systemBroadcast authentication
Disclosed is an authentication method employing elliptic curve cryptography (ECC), applicable to a mobile broadcast TV system having one or more head end systems, at least a transmitter, and at least a mobile set. The authentication method comprises at least one request message from mobile sets simultaneously or in a short period of time arriving at a head end system for authentication; manipulating each broadcast authentication message by ECC; manipulating each service request message by ECC and pairing operation; performing a mutual authentication between the head end system and mobile sets by ECC and pairing operation; and broadcasting one group of authentication messages to all the mobile sets of many requests arrived at the head end system simultaneously or in a short period of time for the same service.
Owner:IND TECH RES INST
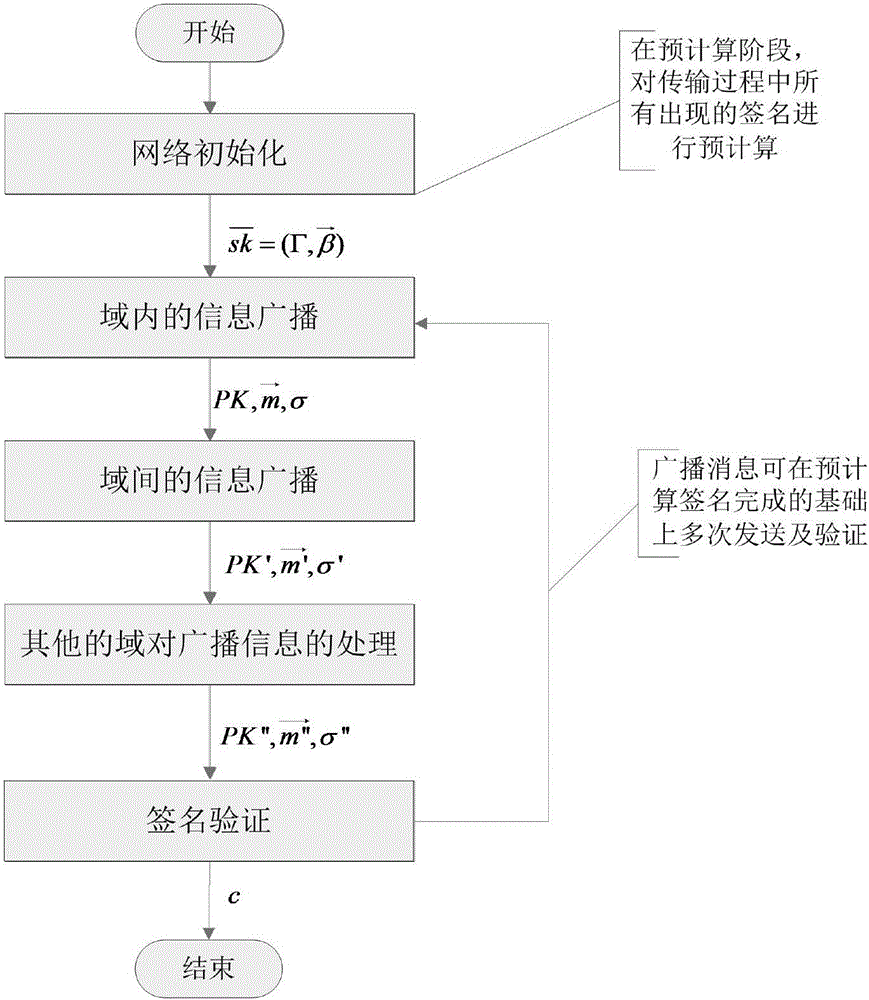
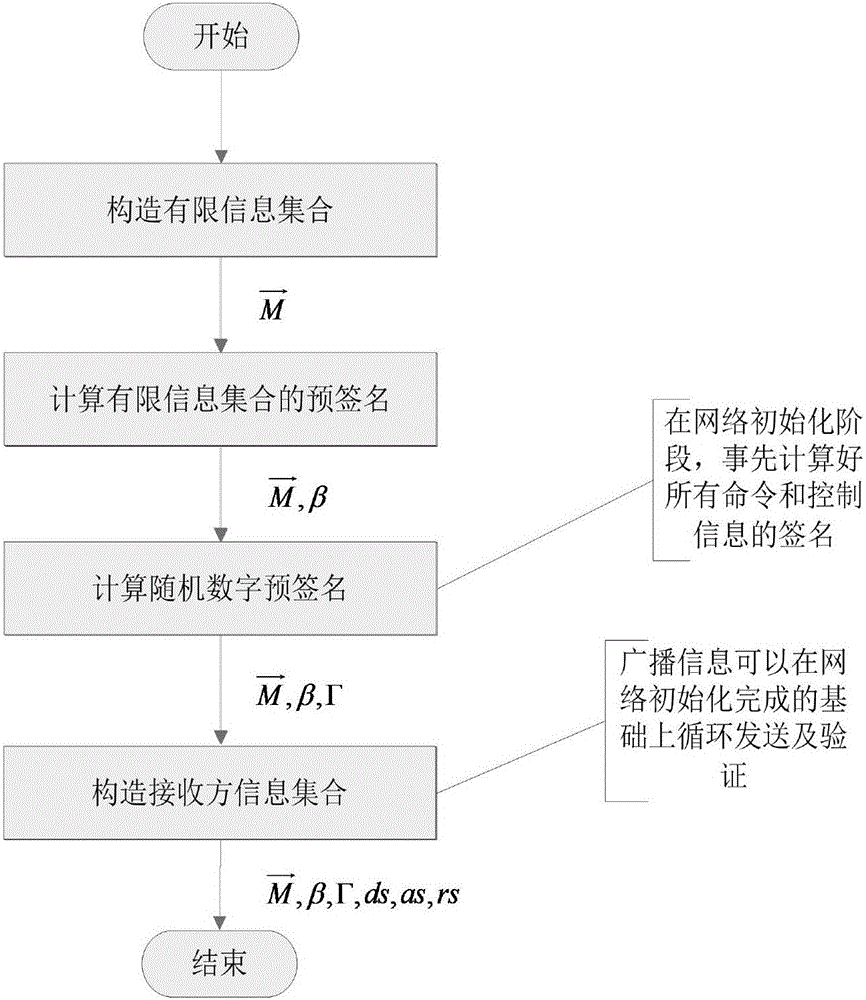
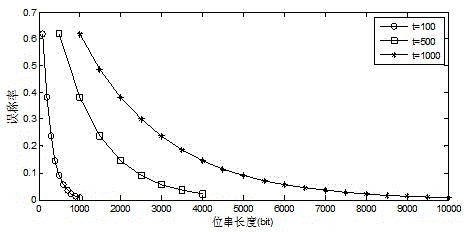
Cross-domain broadcast authentication method in space information network
ActiveCN105743647AImprove efficiencyImprove communication efficiencyPublic key for secure communicationUser identity/authority verificationExtensibilityInformation transmission
The invention discloses a cross-domain broadcast authentication method in a space information network. The method mainly solves the problems in the prior art that the authentication efficiency is low, the extensibility is low and the concurrence of multiple security domains in the space information network is not taken consideration when cross-domain broadcast authentication is carried out. The realization scheme of the method comprises that in a system deployment stage, the terminal and agent of each security domain finish calculating signing work with relatively high costs; in a broadcast information transmission stage, corresponding signatures only need to be taken out from a pre-calculated signature set; moreover, cross-domain transmission of the broadcast information is finished through the agent of each security domain, wherein re-signing needs to be carried out each time when one stage of agent is passed; and finally, a broadcast receiver finishes information authentication through the previous signatures. According to the method, through adoption of a pre-calculation mode, the efficiencies of signing and authenticating the broadcast authentication are greatly improved; moreover, through arrangement of the security domain agents, under a condition of not relating to the security systems of different security domains, the security transmission and cross-domain authentication of the broadcast information are ensured.
Owner:XIDIAN UNIV
A broadcast authentication method for wireless sensor networks based on ecdsa algorithm
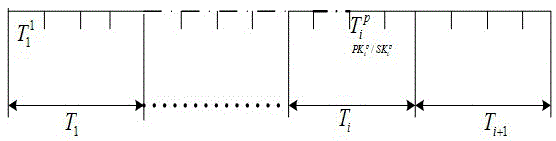
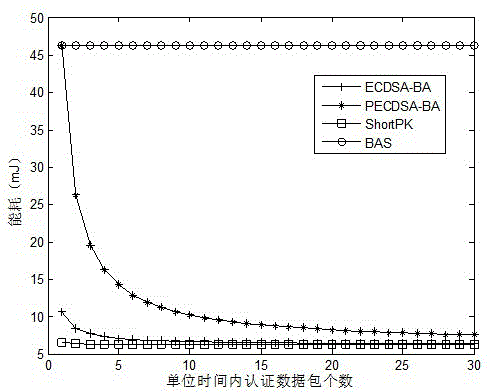
InactiveCN102684874BTolerance lossReduce computational costUser identity/authority verificationNetwork topologiesData packPublic key authentication
The invention relates to a wireless sensor network broadcast authentication method based on an ECDSA algorithm, belonging to the fields of communication technology and information security. The present invention utilizes ECDSA algorithm and Bloom? filter, by dividing the survival time of the wireless sensor network into several small time periods, a key pair is generated for each time period according to the ECDSA signature algorithm, and the public key set is mapped to a bit string by hash operation, and the bit string The string is loaded into the network node, and then public key authentication, message signature and message authentication are performed. This method has good real-time performance, low calculation cost, and can tolerate data packet loss. Compared with the ShortPK algorithm, it occupies less memory. Lifetime PECDSA-BA, this method has the advantages of real-time performance, computing performance, security performance, tolerance to data packet loss and so on.
Owner:HENAN UNIV OF SCI & TECH
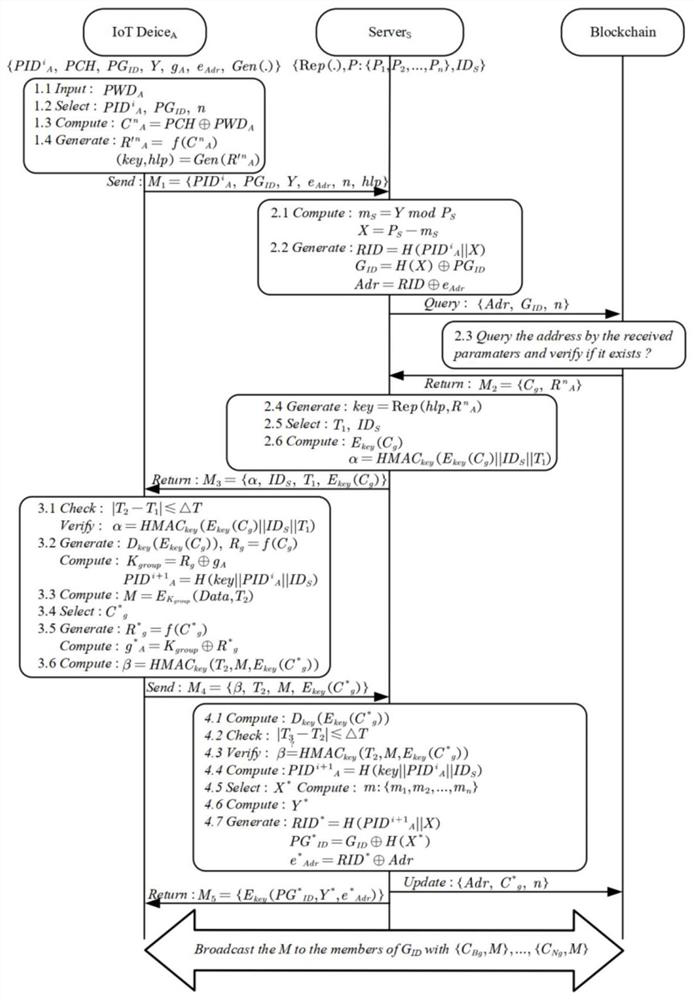
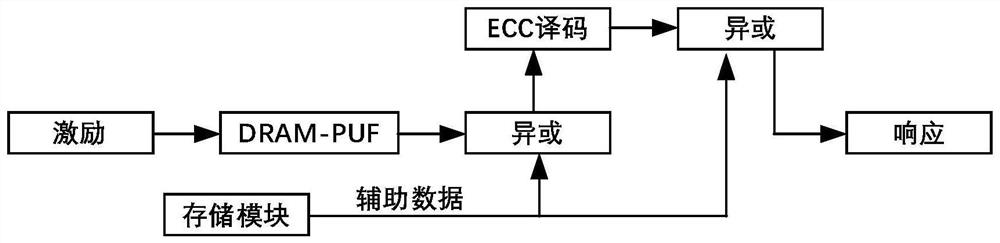
Group broadcast authentication method based on block chain and PUFs
PendingCN114124380AAvoid exposureEnsure safetyKey distribution for secure communicationUser identity/authority verificationEngineeringBroadcast authentication
The invention discloses a group broadcast authentication method based on a block chain and PUFs (Physical Unclonable Frameworks). The method comprises a registration stage, an authentication stage and an updating stage, the registration stage comprises registration of a block chain node, registration of a device end and registration of a group; in the authentication stage, key negotiation and bidirectional authentication between a device end and a block chain node are completed; the authentication of the block chain node to the equipment end comprises two steps of authentication including initial authentication and secondary authentication, and the authentication of the equipment end to the block chain node is one-time authentication; in the updating stage, updating of authentication parameters of the equipment end and updating of registration parameters of the equipment end on the block chain are completed by the block chain node; according to the method, the PUFs and the block chain technology are combined, the single-point failure problem existing in the PUFs and the traceability of broadcast messages are solved, meanwhile, the physical aggression resistance of the equipment end is guaranteed, anonymity is achieved through the anonymous ID, and expansibility management and lightweight authentication of group members are achieved.
Owner:东南大学深圳研究院
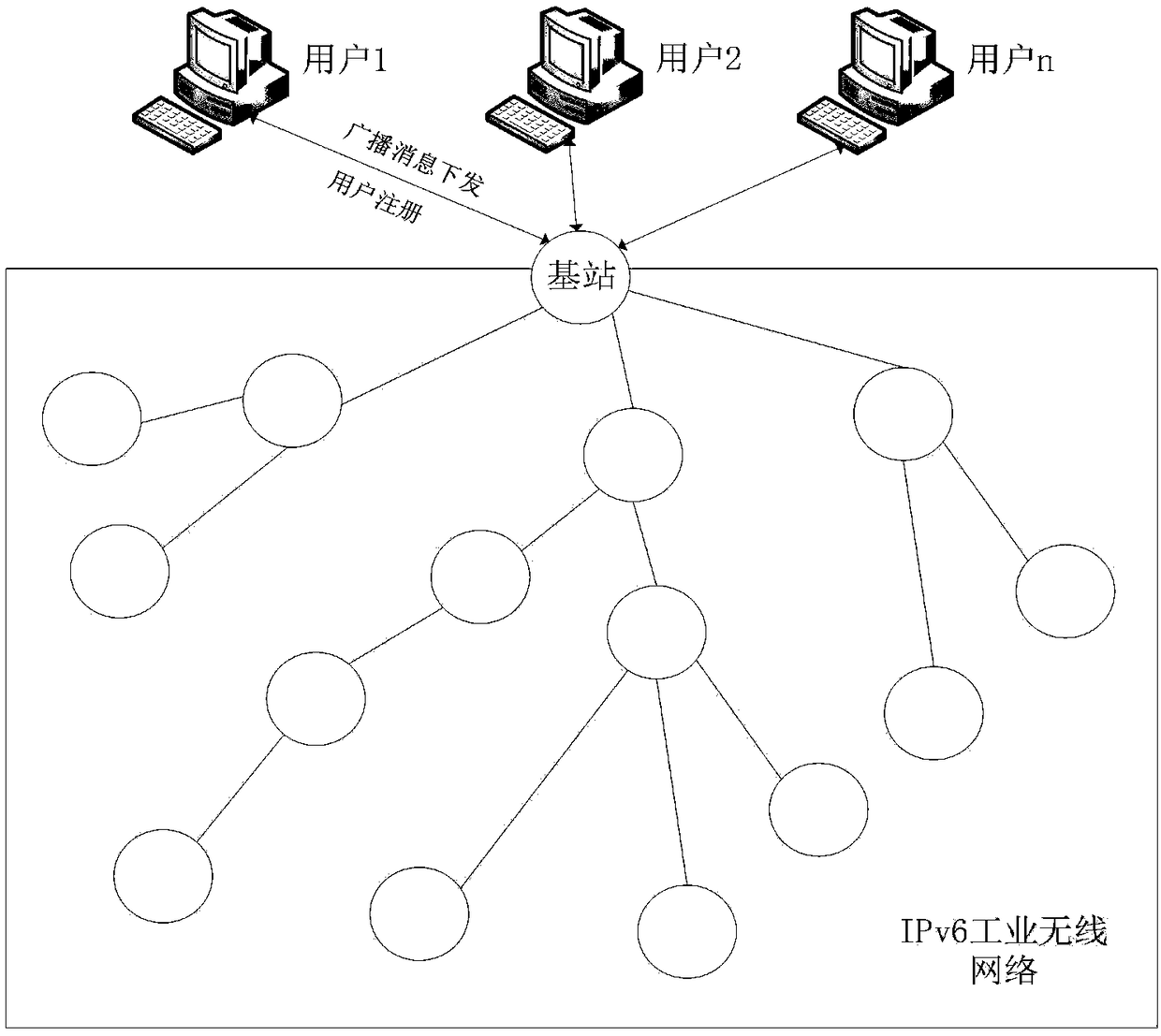
IPv6 industrial wireless network data security transmission method based on broadcast signcryption
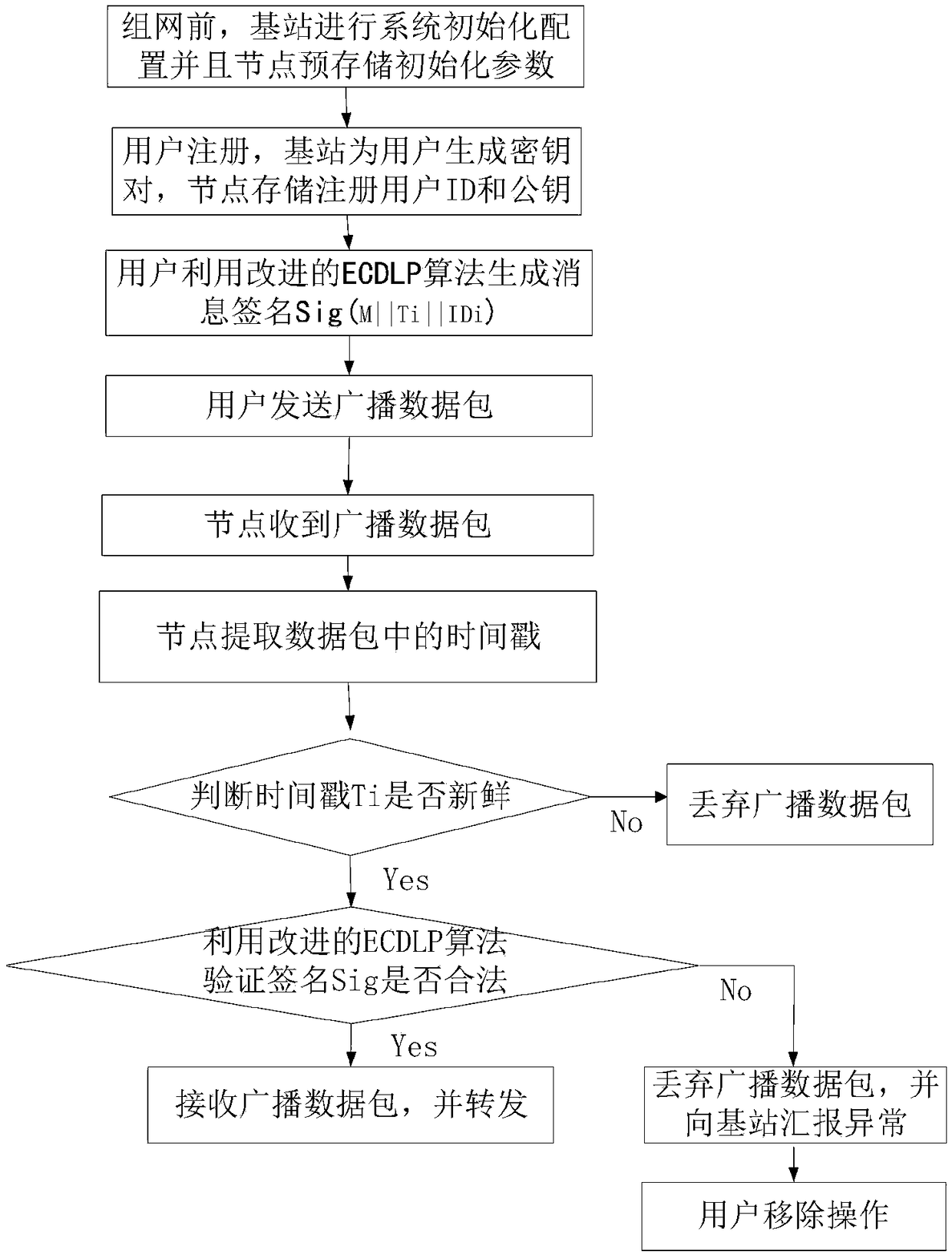
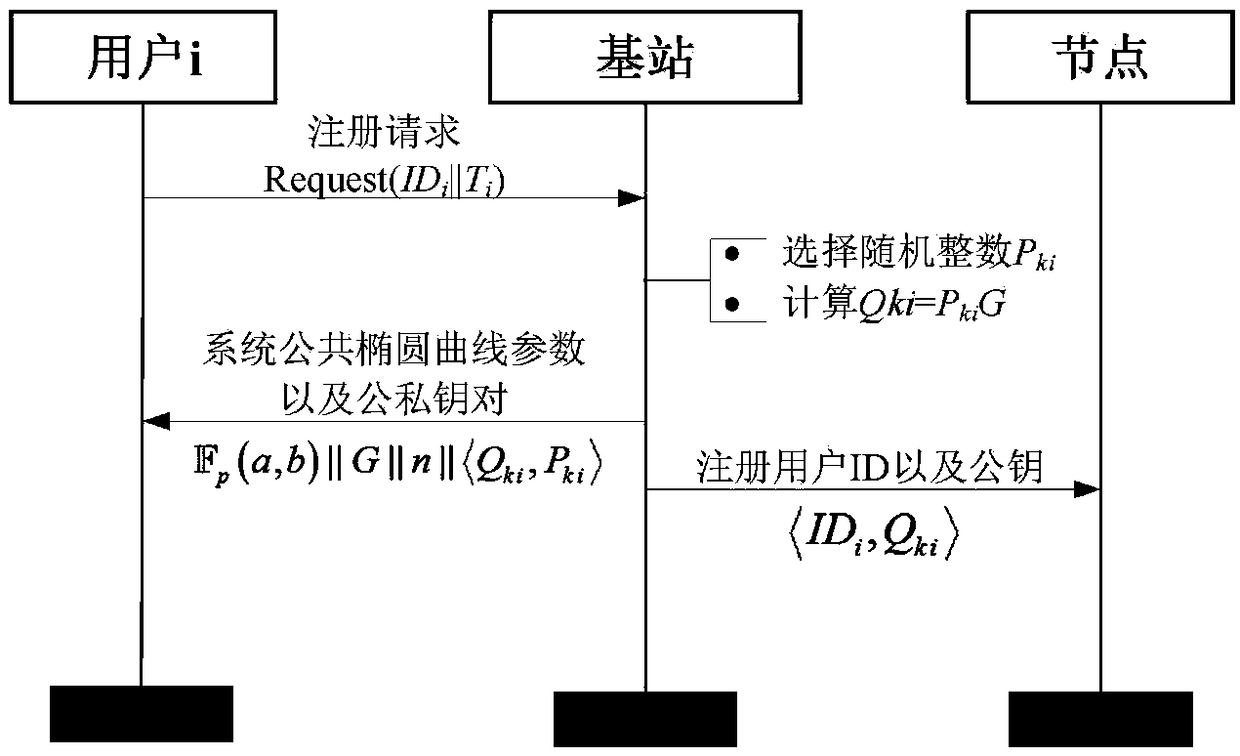
ActiveCN109451501ATroubleshoot broadcast authentication issuesAchieve immediate authenticationUser identity/authority verificationSecurity arrangementBroadcast packetConfidentiality
The invention relates to an IPv6 industrial wireless network data security transmission method based on broadcast signcryption, and belongs to the field of communication. According to the method, based on a user broadcast communication mode of an IPv6 industrial wireless network, a data security transmission method based on ECC signcryption is provided, and comprises an improved ECDLP digital signature scheme and an IPv6 industrial wireless network broadcast authentication scheme; and therefore, the end-to-end data transmission security is guaranteed. The method has the advantages that the IPv6 industrial wireless network broadcast authentication scheme is provided, so that high security and efficiency are achieved; dynamic addition and removal of a user can be supported, so that the robustness and flexibility of the network can be ensured; user anonymity can be realized, so that user privacy is protected; the improved ECDLP digital signature scheme is adopted for solving the problemsof source authentication and message integrity authentication of a user broadcast data packet in the IPv6 industrial wireless network, so that the confidentiality and authentication of data are guaranteed.
Owner:KYLAND TECH CO LTD
An authentication method and authentication system
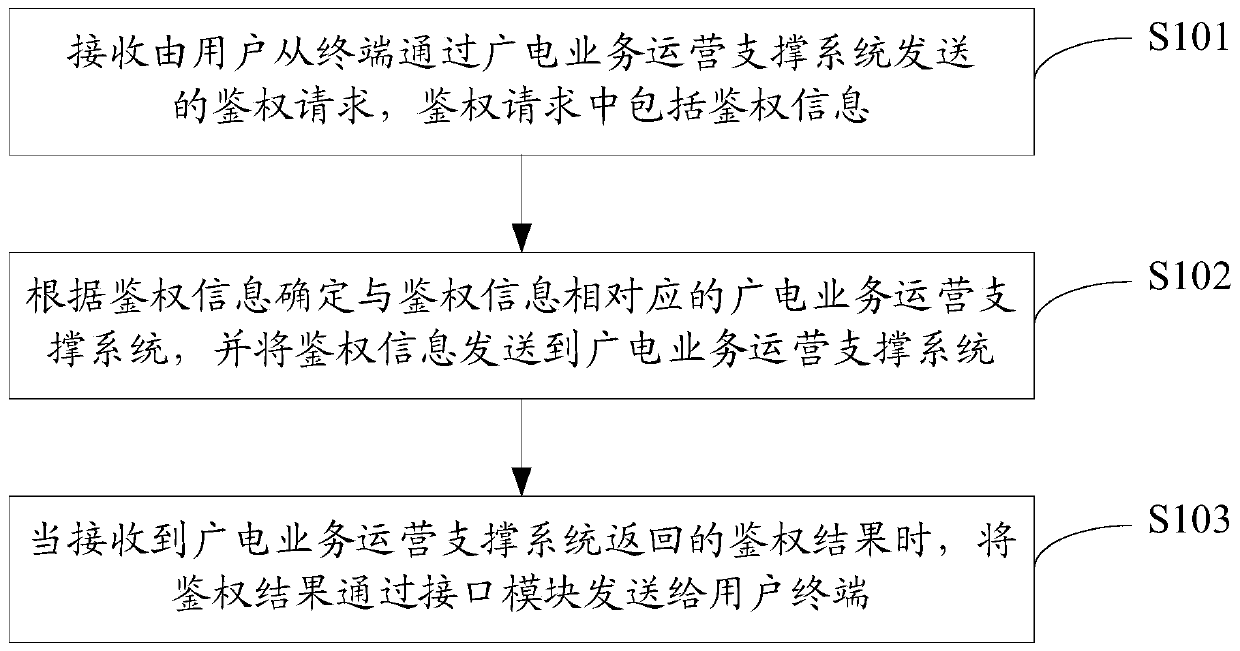
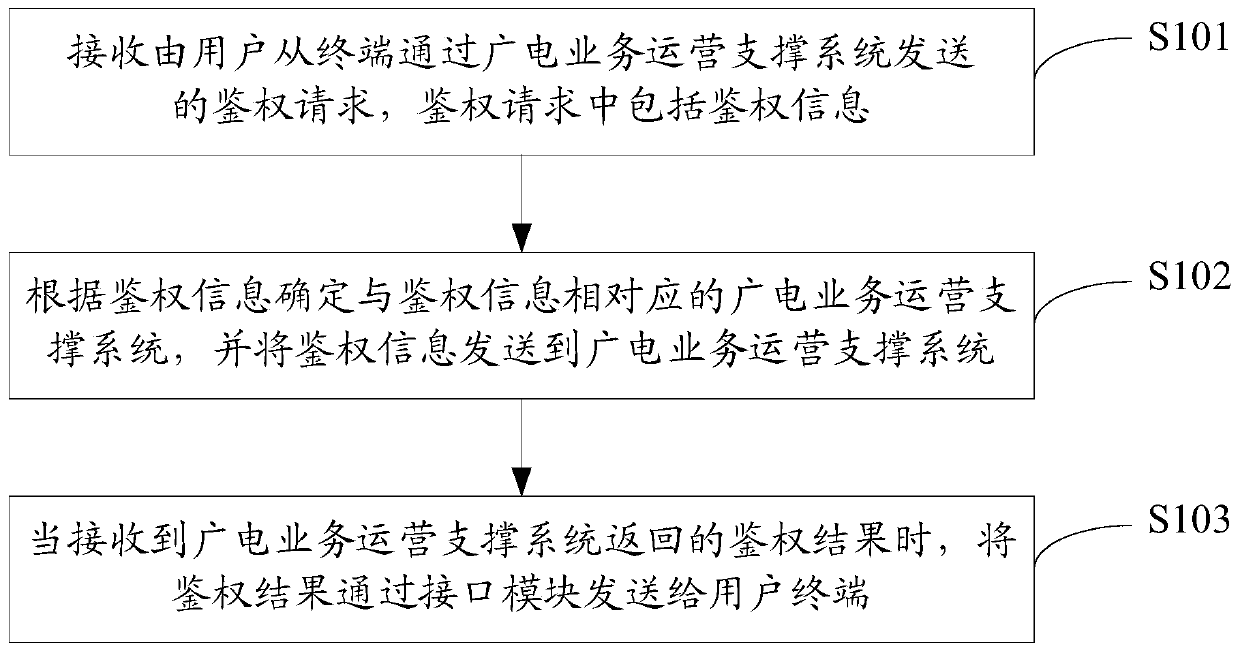
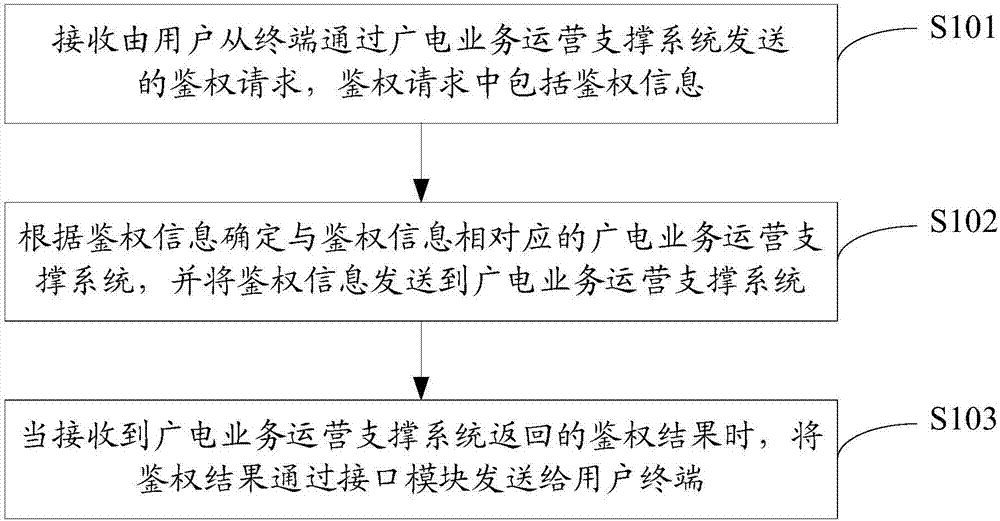
ActiveCN107172494BRealize unified managementSelective content distributionInterface layerUser authentication
The invention discloses an authentication method and an authentication system. The method is applied to an interface layer of an authentication platform. The authentication platform includes an independent interface layer, a radio and television business operation support system and an on-demand push system. The method includes: receiving The authentication request sent by the user from the terminal through the radio and television service operation support system, the authentication request includes the authentication information; the radio and television service operation support system corresponding to the authentication information is determined according to the authentication information, and the authentication information is sent to The radio and television business operation support system; when receiving the authentication result returned by the radio and television business operation support system, the authentication result is sent to the terminal through the interface layer. The invention connects different radio and television business operation support systems by establishing a unified interface layer, and realizes unified management of user authentication and playback authentication.
Owner:SHENZHEN IPANEL TECH LTD
A Security Method for Coap Protocol in Multicast
ActiveCN108040042BImprove securityKey distribution for secure communicationSafety propertyEngineering
The invention relates to a safety method for a CoAP protocol under a multicast situation, and belongs to the technical field of the network. On the basis of the CoAP protocol designed by orienting a resource-limited an IP network, the invention proposes a safety method for a CoAP protocol multicast mechanism. The safety method comprises a multicast authenticiaton encryption algorithm and a Booleanarray detection mechanism to guarantee the end-to-end security, and the safety method is suitable for the own agent mechanism of the CoAP protocol. The safety method has the advantages as follows: finishing the secrecy transmission to a server node in a multicast group from the information while the broadcast authentication is realized, thereby enabling the server to extract the encryption information from an authenticated agent server, wherein other servers cannot receive the encryption information. By adopting the GDOI algorithm and a symmetric key mechanism in a sensor network, the Booleanarray mechanism is added in the agent server, and the security of the data communication is improved under the situation of guaranteeing the information transmission.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
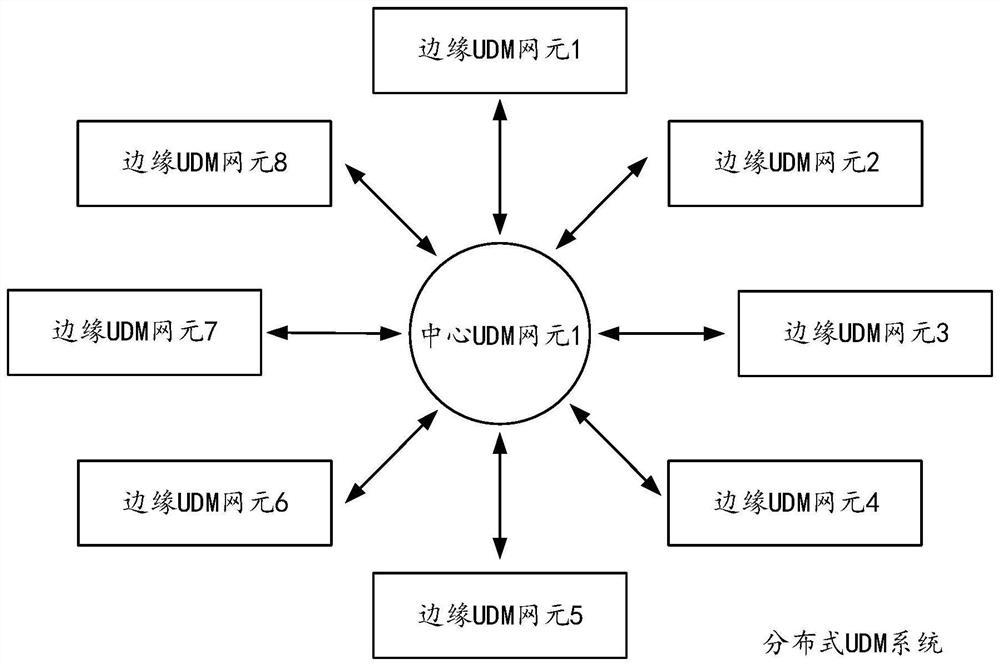
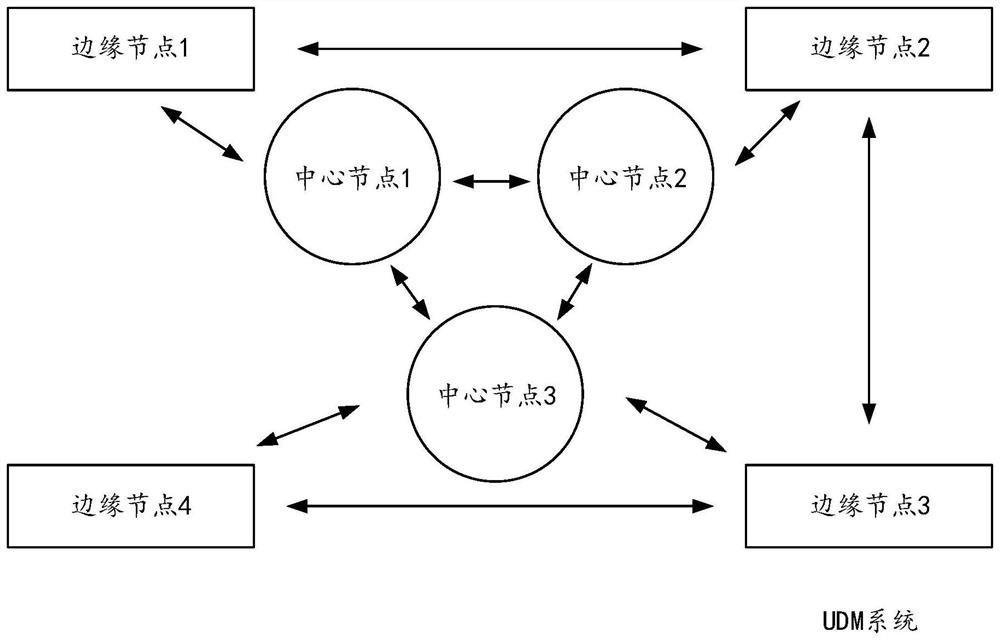
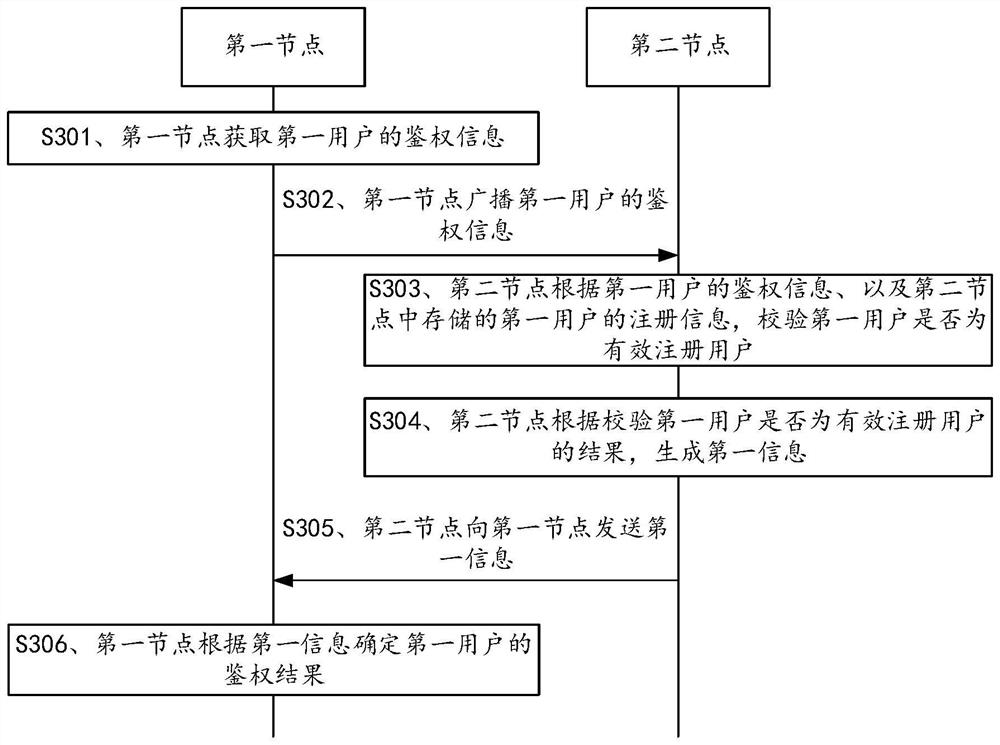
Data management method, device and system, equipment and storage medium
The invention provides a data management method, device and system, equipment and a storage medium, and relates to the field of communication. The method is applied to a first node in a UDM system, and comprises the following steps: acquiring authentication information of a first user; broadcasting authentication information of the first user; receiving first information sent by at least one second node; the second node is a node except the first node in the plurality of edge nodes or a central node; the first information is generated after the second node verifies whether the first user is an effective registered user according to the authentication information of the first user and the registration information of the first user stored in the second node; the first information is used for indicating whether the authentication information of the first user passes the verification of the second node; and determining an authentication result of the first user according to the proportion of the first information indicating to pass the verification of the second node in all the first information and a preset first proportion. The method is suitable for the authentication process and is used for improving the security of the UDM system.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Message Authentication Method for Internet of Vehicles Based on Edge Computing
ActiveCN107634837BReduce overheadLow message authentication redundancyKey distribution for secure communicationPublic key for secure communicationLocal optimumEdge computing
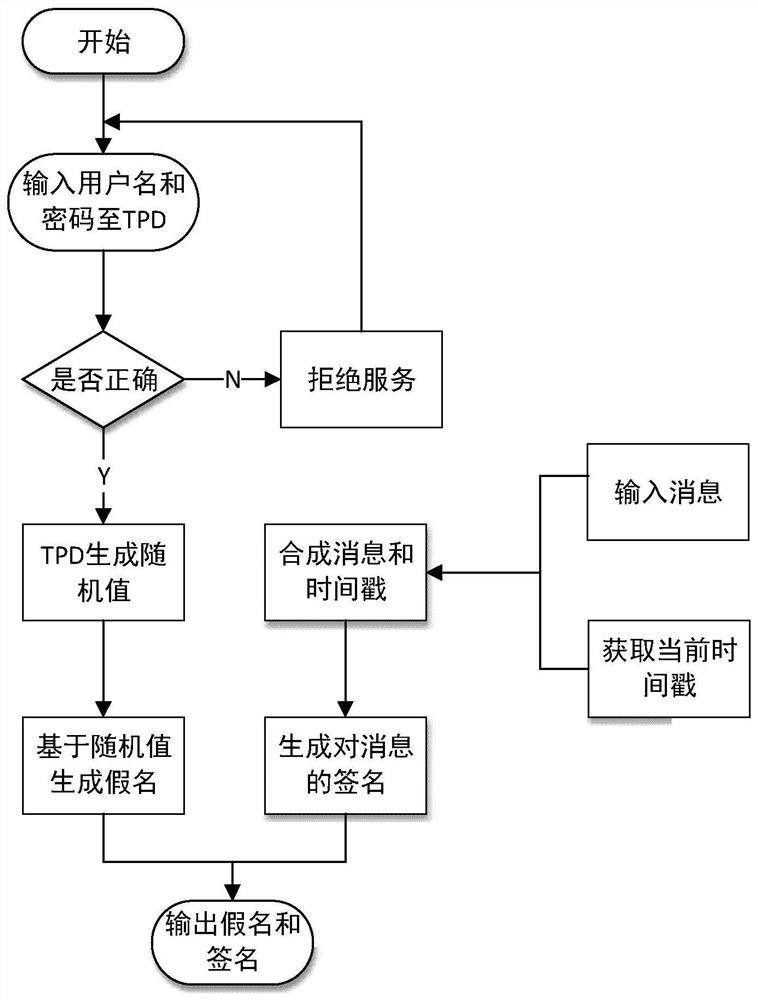
The invention discloses an efficient message authentication method for a vehicular ad hoc network based on edge computing, which comprises the steps of system initialization of participating entitiesof the Internet of vehicles, wherein the step comprises two processes such as parameter generation and vehicle pseudonym and signature generation; and (2) message authentication of an RSU (Roadside Unit) and a vehicle, wherein the step comprises four processes such that the RSU elects an edge computing vehicle (ECV), the ECV executes a task, the RSU checks an authentication result of the ECV and vehicle message authentication is performed. The signing portion of the invention adopts an elliptic curve cryptography based operation, thereby enabling the computation and transmission overhead to below; further the ECV is elected according to a fuzzy logic control theory to achieve local optimal election; the ECV is set to help the RSU to achieve quick and accurate message signature authentication; and the RSU reduces the redundant authentication of the whole system to the maximum extent through broadcasting the authentication result, and the operating efficiency of the whole vehicular ad hoc network is improved.
Owner:ANHUI UNIVERSITY
Method suitable for broadcast authentication of wireless sensor network
ActiveCN102917313BTroubleshoot broadcast authentication issuesAchieve immediate authenticationSpecial service provision for substationUser identity/authority verificationBroadcast packetHash-based message authentication code
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Authentication method and authentication system
ActiveCN107172494ARealize unified managementSelective content distributionInterface layerUser authentication
The invention discloses an authentication method and an authentication system. The method is applied to an interface layer of an authentication platform. The authentication platform comprises the interface layer, broadcasting business operation support systems and a video-on-demand push system which are independent of one another. The method comprises the following steps: receiving an authentication request sent by a user from a terminal through one broadcasting business operation support system, wherein the authentication request includes authentication information; determining the broadcasting business operation support system corresponding to the authentication information according to the authentication information, and sending the authentication information to the broadcasting business operation support system; and when receiving an authentication result returned by the broadcasting business operation support system, sending the authentication result to the terminal through the interface layer. A unified interface layer is built to connect different broadcasting business operation support systems, and therefore, unified management of user authentication and broadcast authentication is realized.
Owner:SHENZHEN IPANEL TECH LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com