Efficient technique to achieve non-repudiation and resilience to DoS attacks in wireless networks
A wireless network and authentication code technology, applied in the field of authenticating messages transmitted in wireless networks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0074] The following discussion of authentication protocols for wireless communication systems employing digital signatures and TESLA authentication is merely exemplary in nature and is in no way intended to limit the scope of the invention, its application or uses.
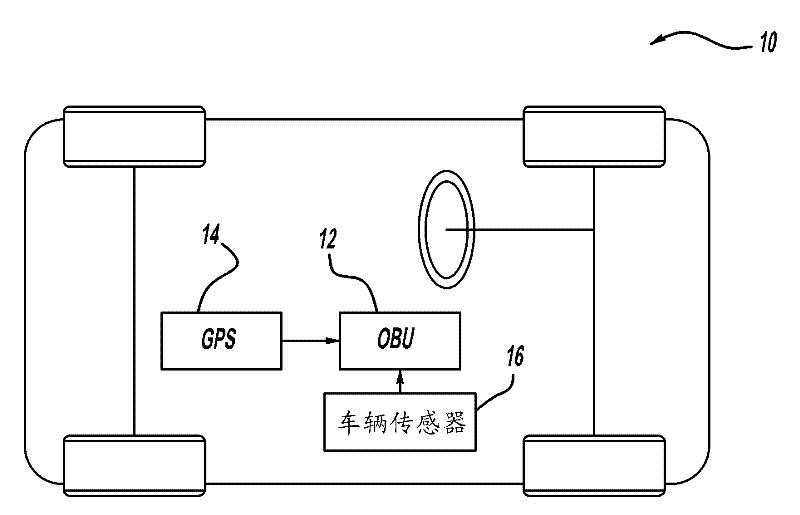
[0075] figure 1 A plan view of a vehicle 10 including an on-board unit (OBU) 12 for a V2X wireless communication system is shown. OBU 12 receives location information from GPS receiver 14 and is able to communicate with other OBUs on other vehicles within a limited range. The vehicle 10 also includes various types of vehicle sensors 16 such as cameras, accelerometers, temperature sensors, etc. that provide information to the OBU 12 . Vehicle sensor information can be used by the OBU 12 to notify other vehicles of various road and other conditions, such as ice, fuel spills, and the like.
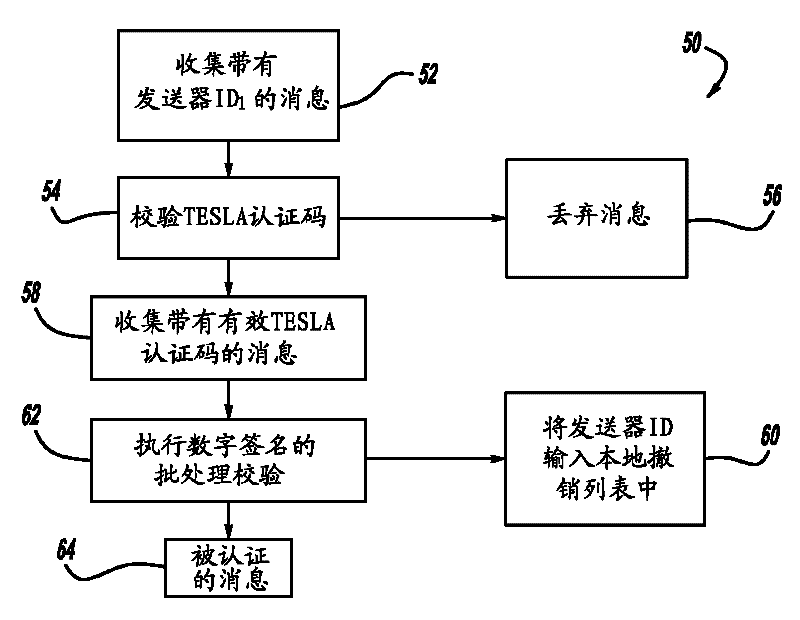
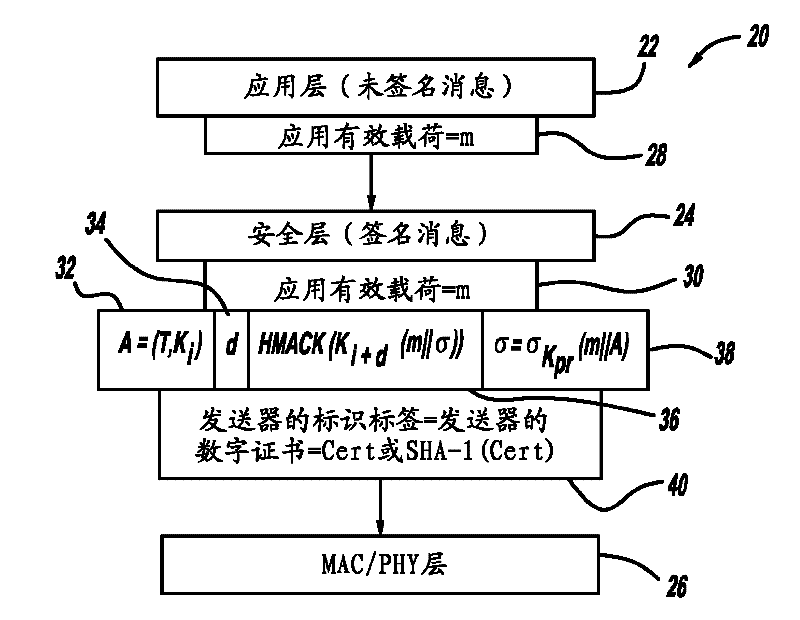
[0076] A computationally efficient message verification strategy for verifying messages for wireless networks is described b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com