Group broadcast authentication method based on block chain and PUFs
An authentication method, blockchain technology, applied in the field of information security, can solve the problems of access, use, disclosure interruption, vulnerability to physical and clone attacks, etc., to ensure tamper-proof and accountability, resist modeling attacks, Avoid the effect of exposure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
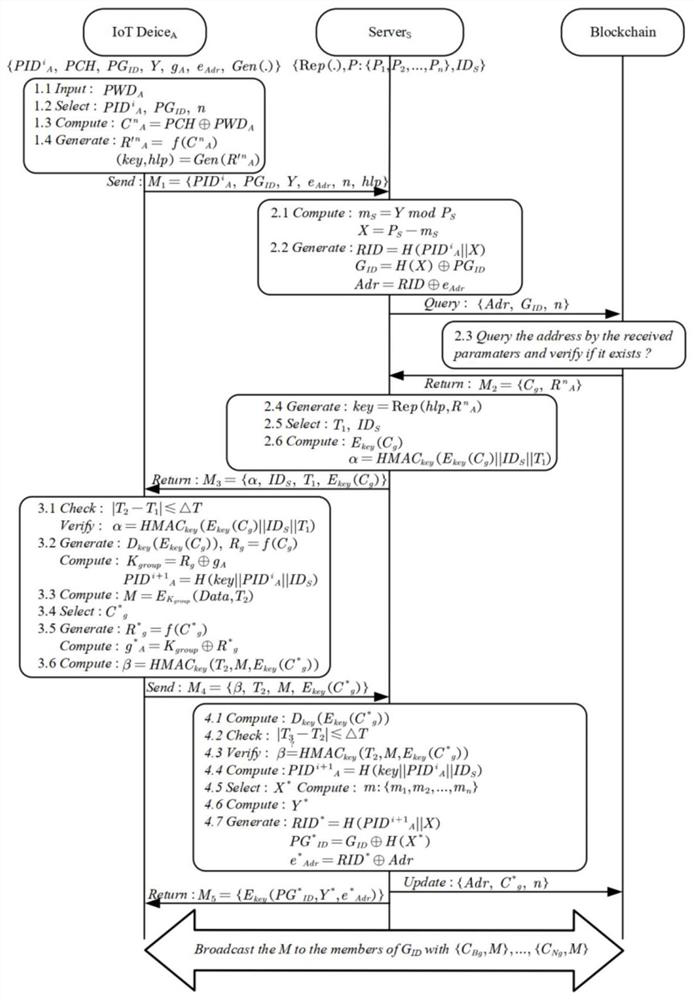
[0027] Such as figure 1 As shown, the specific steps of the authentication phase are as follows:
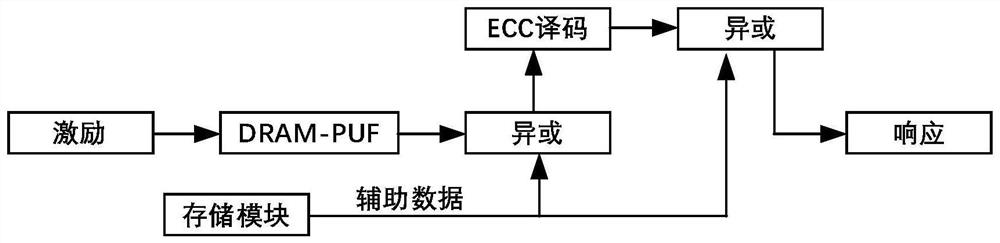
[0028] Step A1: PWD by user password or biometric A Exclusive OR to get the actual stimulus group, randomly select the stimulus C with the sequence number n A , and obtain the corresponding response R through the PUFs module A . Generate the shared secret key and auxiliary data hlp through the Gen function.
[0029] Step A2: Device A constructs M 1 The parameters are sent to the blockchain node Server s , including: device-side pseudo-identity (in this case, PID A ), device group pseudo-identity PG ID , Chinese remainder theorem mapping parameter Y, sequence number n, auxiliary data hlp and blockchain address generator e Adr .
[0030] Step A3: Blockchain Node Server s Based on the Chinese remainder theorem, the parameter m is calculated s, so as to obtain the parameter X, and use it to calculate the actual group identity G ID and device identity intermediate quantity...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com