Efficient message authentication method for vehicular ad hoc network based on edge computing
A message authentication and edge computing technology, which is applied to public keys for secure communication, user identity/authority verification, and key distribution, can solve problems such as insufficient computing efficiency, redundant authentication, and failure to meet performance requirements, and achieve computing and Low communication overhead, low message authentication redundancy, and high operating efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0056] The edge computing-based efficient message authentication method for Internet of Vehicles in this embodiment includes the following steps:
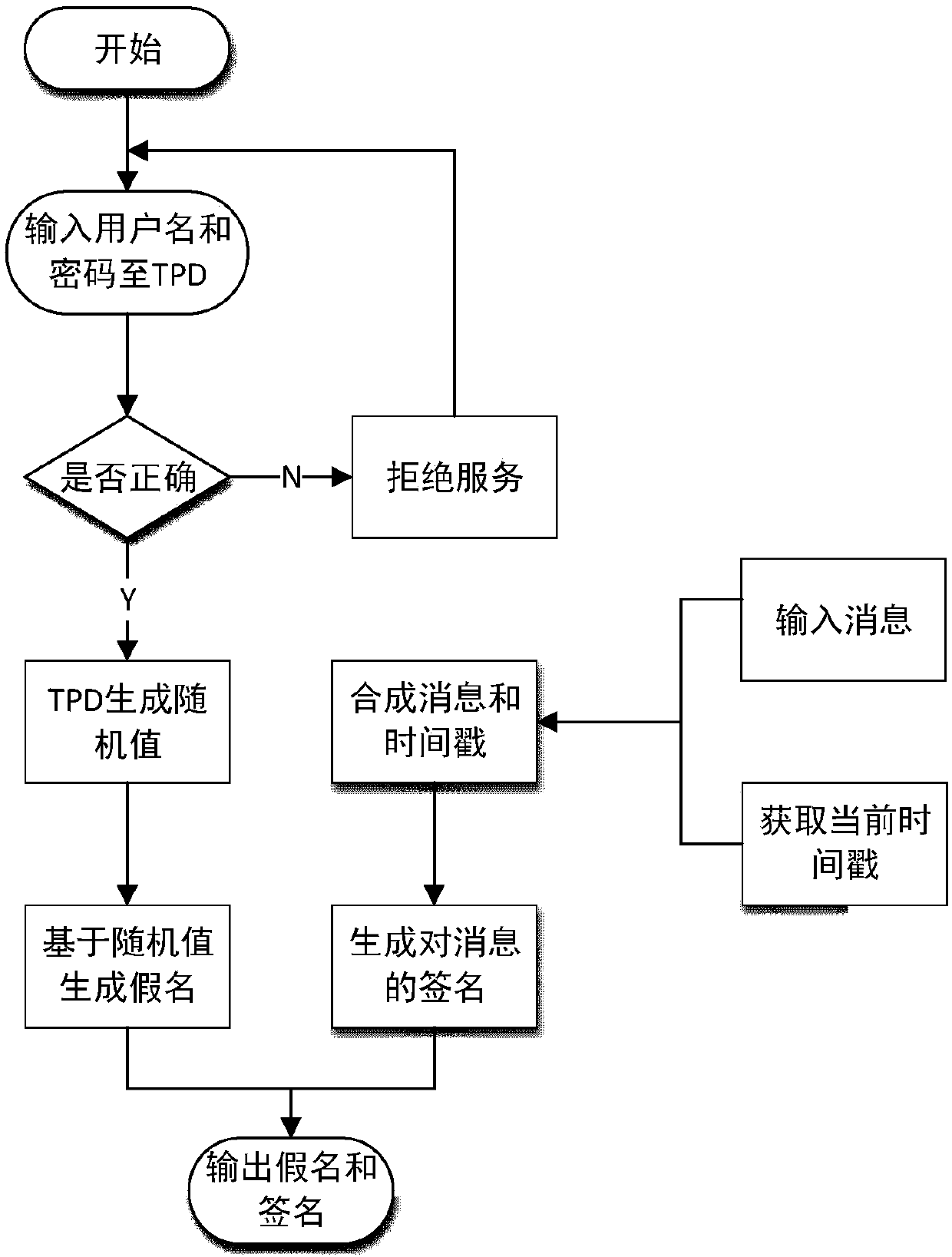
[0057] (1) System initialization of participating entities in the Internet of Vehicles: parameter generation, and vehicle generation of pseudonyms and signatures;
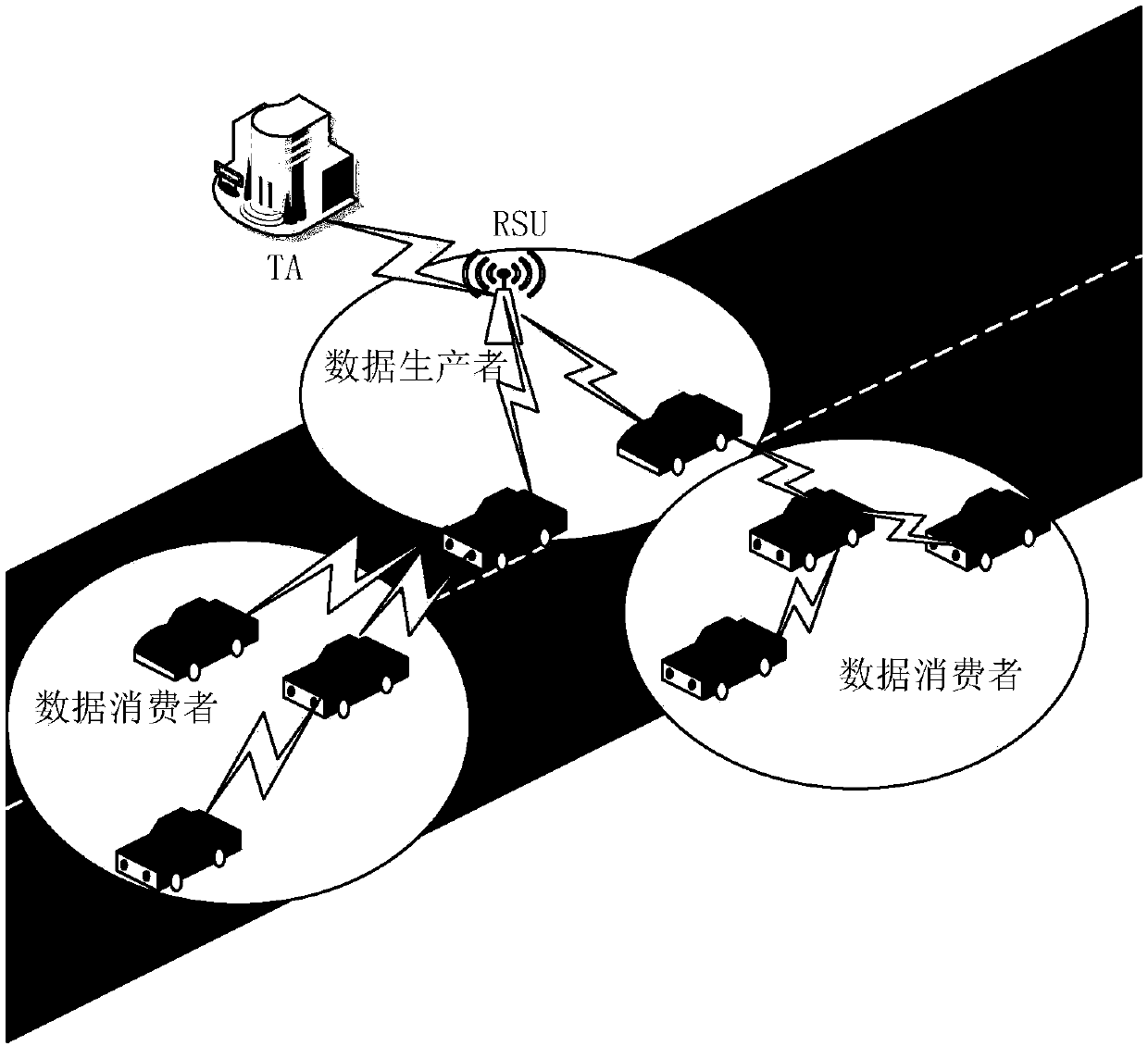
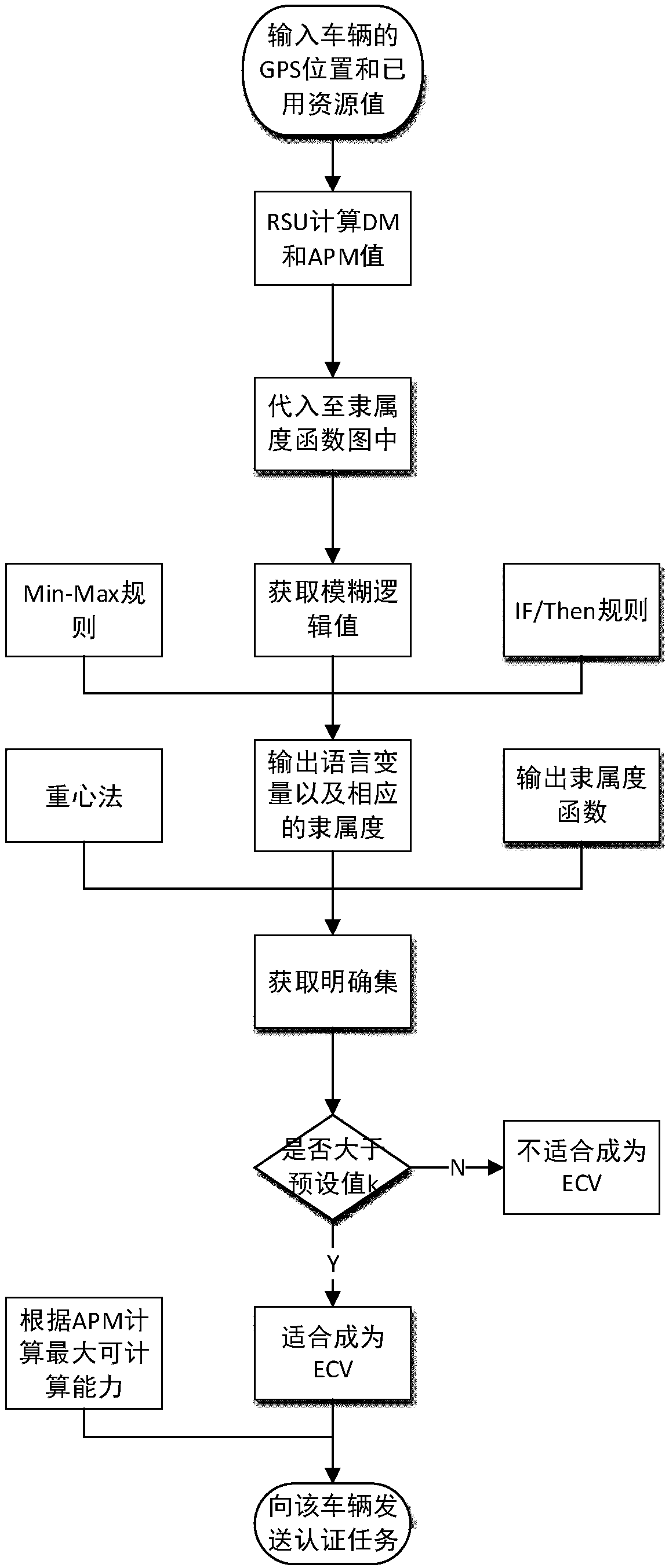
[0058] (2) Message authentication of RSU and vehicle: RSU elects an edge computing vehicle (ECV), ECV performs tasks, and RSU checks the authentication result of ECV and vehicle message authentication.
[0059] In the parameter generation phase of step (1), TA generates the necessary system parameters, and then TA preloads these system parameters into the vehicle's TPD (tamper-proof device, anti-tampering device) and all RSUs through a secure communication channel. Specific steps are as follows:
[0060] 1) TA randomly selects two large prime numbers p, q, and one defined as y 2 =x 3 The nonsingular elliptic curve E of +ax+b mod q (where a,b∈F p ), and in group G q...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com