A Security Method for Coap Protocol in Multicast
A protocol and security technology, applied in the network field, can solve the problem of confidential transmission of difficult information to the multicast group server, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The preferred embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
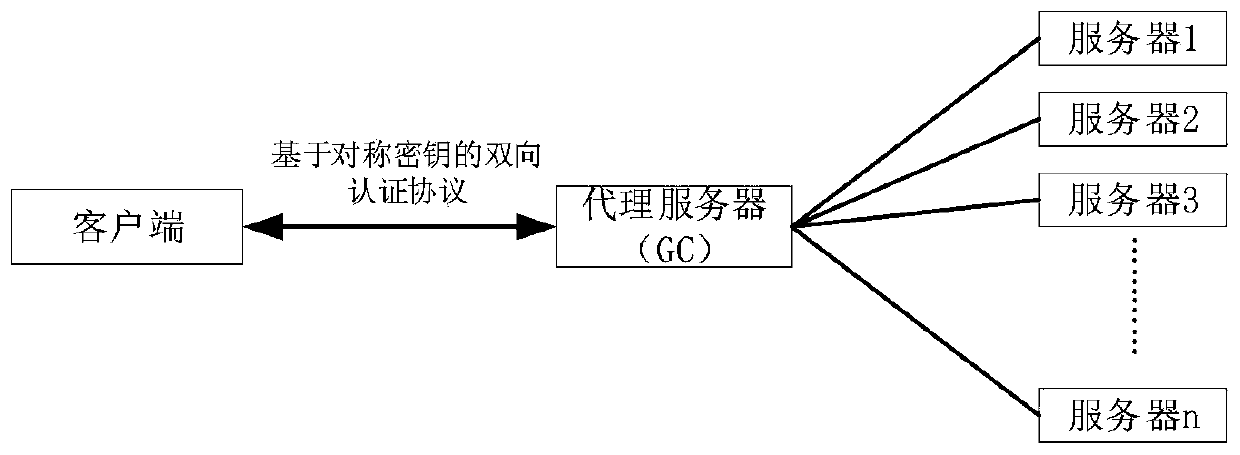
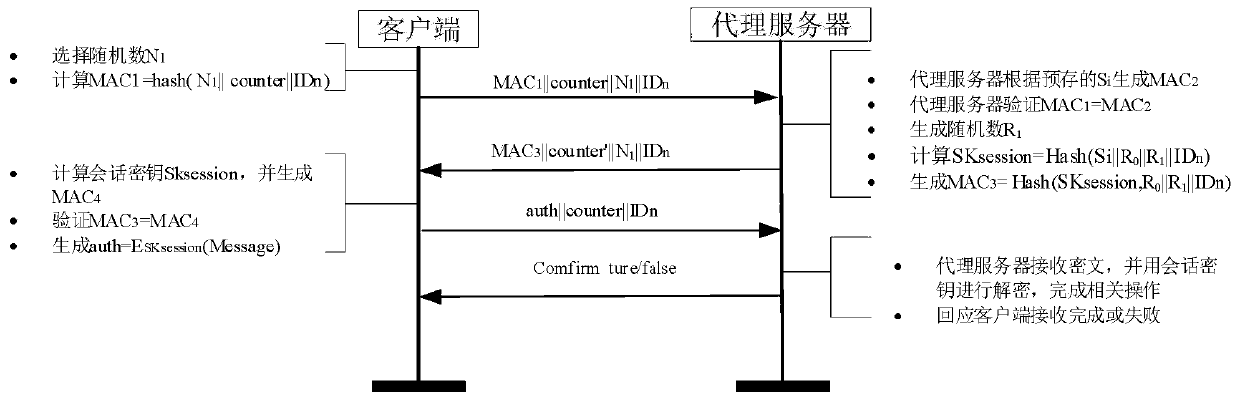
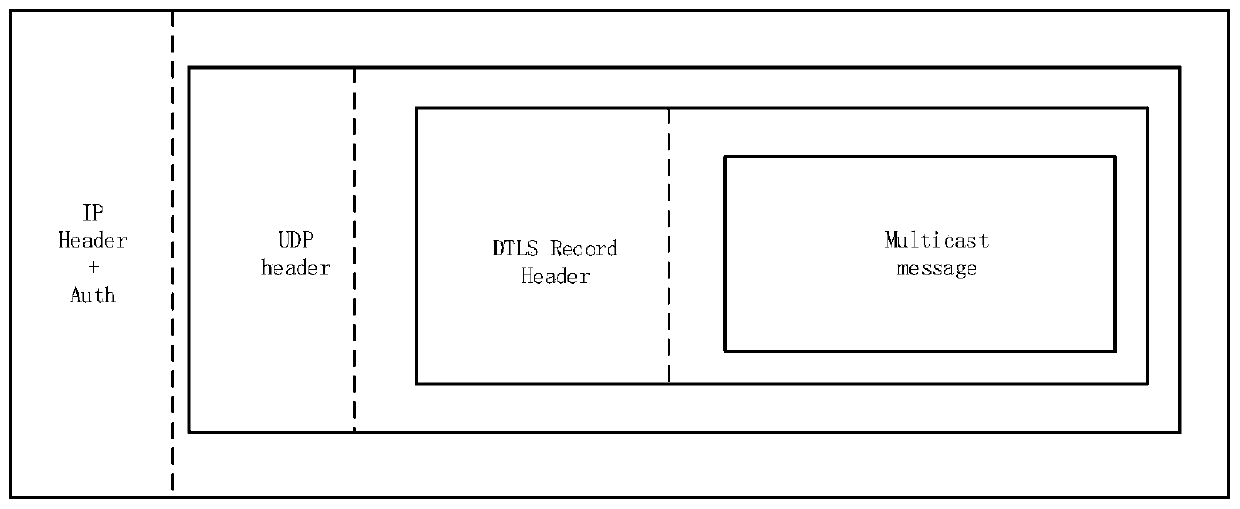
[0041] Such as Figure 1-Figure 3 As shown, a multicast authentication method based on authentication encryption algorithm and Boolean array, when implementing CoAP networking through unicast, the operation is more complicated, and it is only applicable when the number of receiving servers is small. If the number of receiving ends in the system is large , it is prone to the problem that the server receives too much information at an interval, or the message is leaked. Using this method can ensure the security of the CoAP protocol network in the case of multicasting. It is also applicable to the proxy server mechanism of the CoAP protocol itself. The process includes the following Several steps:
[0042] S1 system initialization
[0043] According to the proxy cache mechanism of the CoAP protocol itself, the authentication and key manageme...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com