Classification security-based broadcast authentication design method
A design method and security technology, applied in security devices, broadcast service distribution, electrical components, etc., can solve the problems of high computing overhead and energy consumption, high communication overhead, and low computing overhead, so as to improve security and reduce security requirements , high safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
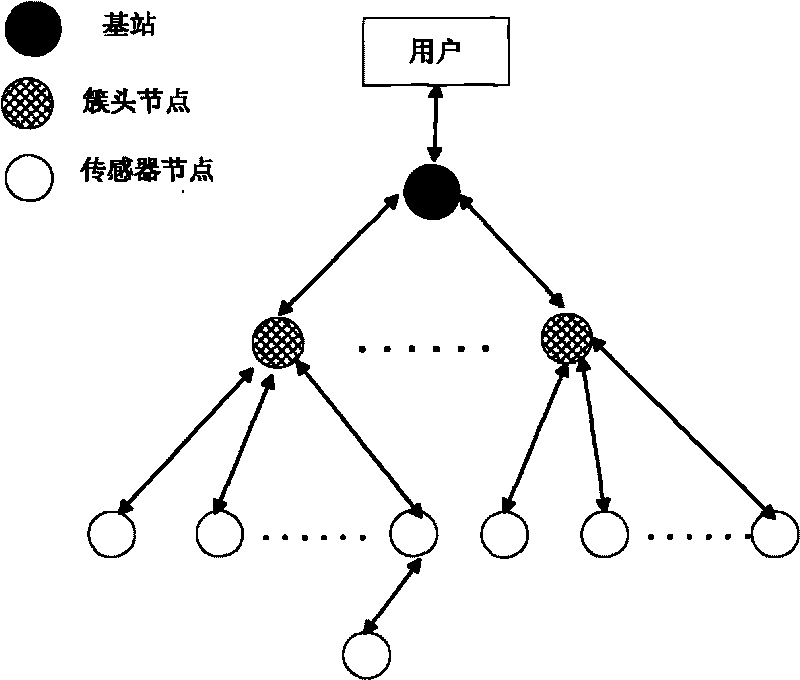
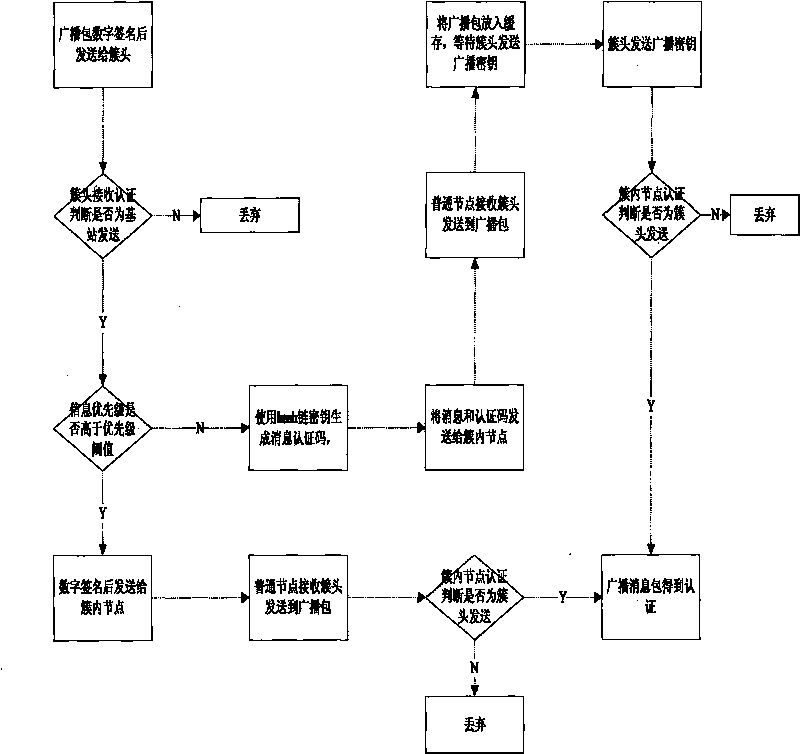
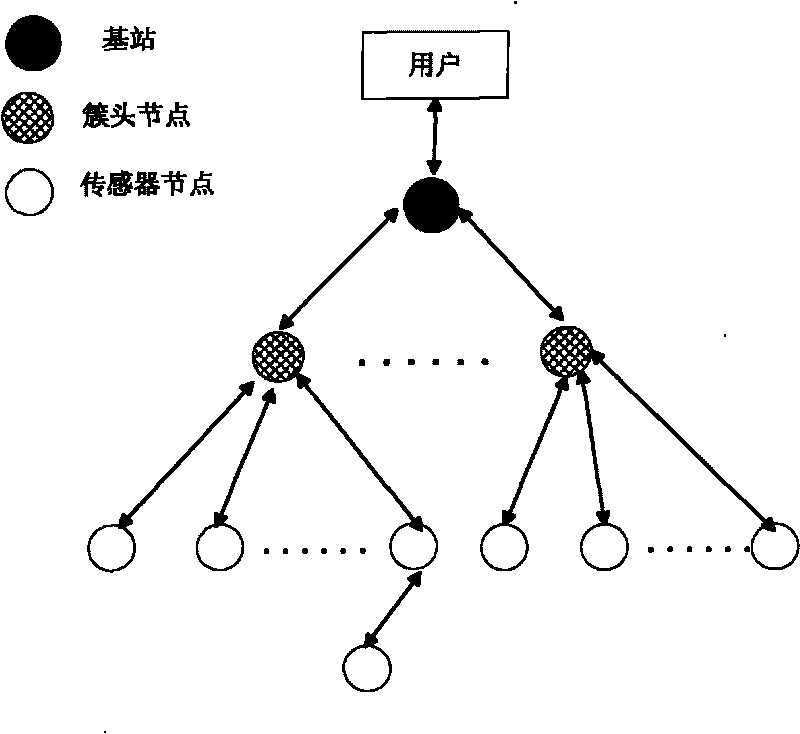
[0045] The design of the broadcast authentication scheme with hierarchical security in the present invention will be described comprehensively below.
[0046] Initialization process:
[0047] 1.1) Each broadcast message packet needs to maintain a priority. Information with high security requirements, such as initialization information and alarm information, has a high priority, while information with low security requirements, such as environmental data that is continuously recorded and sent, has a low priority ,
[0048] 1.2) After the node is initialized, the priority threshold is set according to different application environments. The priority higher than the threshold uses the digital signature technology based on the asymmetric key algorithm for broadcast authentication, and the priority lower than the threshold uses the hash based on the symmetric algorithm. The key chain technology is used for broadcast authentication. When security is important, the threshold can be ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com