Method suitable for broadcast authentication of wireless sensor network
A wireless sensor and network broadcasting technology, applied in network topology, wireless communication, broadcast service distribution, etc., can solve the problems of DOS attack, delayed authentication, calculation, communication and storage overhead, etc., to resist DOS attack and overcome authentication delay , The effect of solving broadcast authentication problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
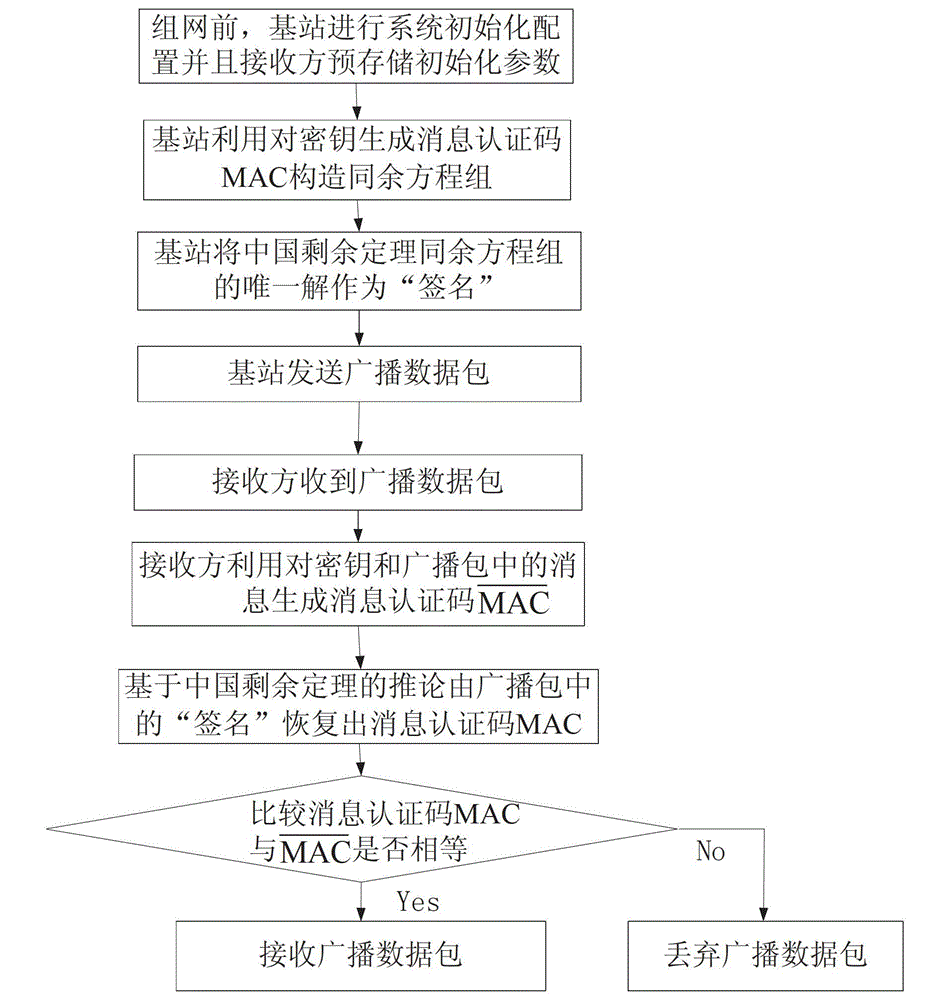
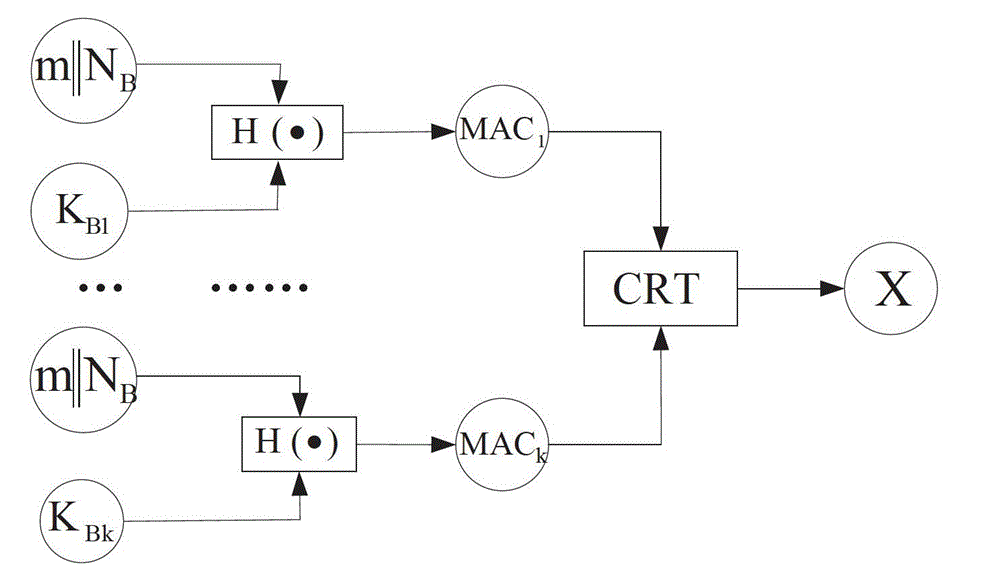
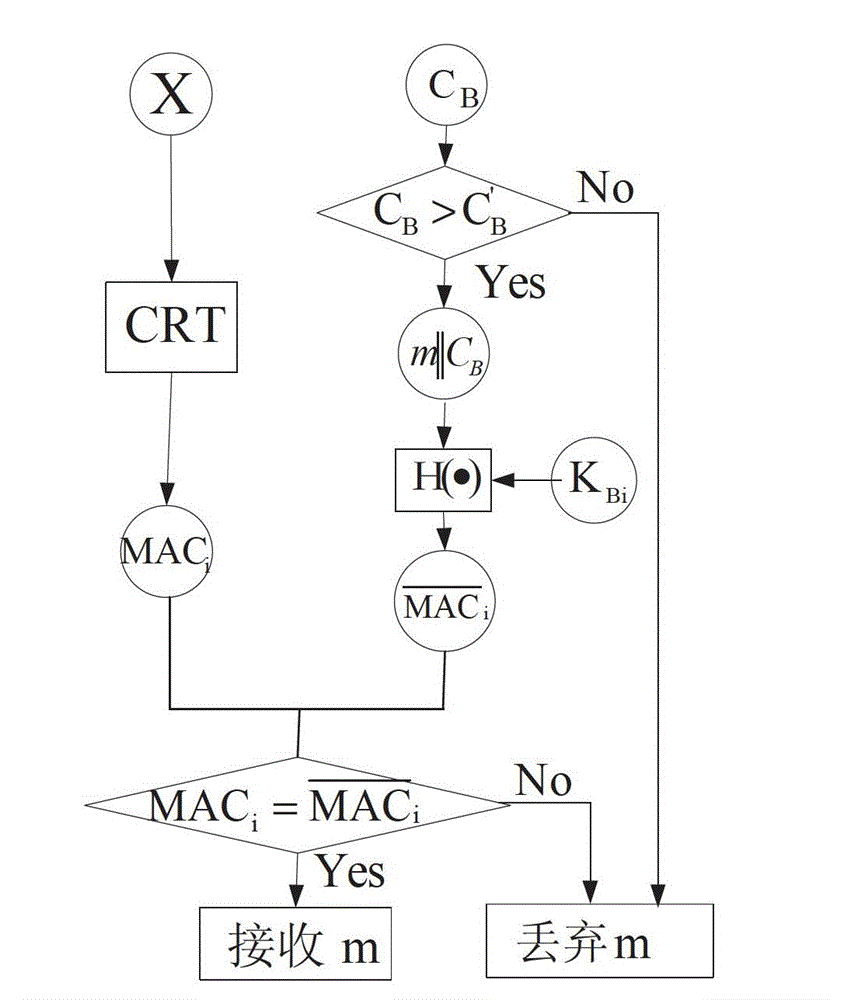
[0026] Since the length of the broadcast message "signature" may increase with the increase of the number of recipients, the present invention is suitable for broadcast application scenarios that are not large in scale, require immediate authentication, have high security, and are not suitable for signatures using public-private key mechanisms. For example, it is used in small wireless sensor networks such as community security or smart home control. In the management and control of community security, the console broadcasts program initialization commands, management commands, alarm commands, etc., and the receiver can filter out illegal nodes. falsification and falsification of information. For a large-scale cluster topology sensor network, the present invention can be applied to the broadcast communication between the base station and the cluster head, and the cluster head node broadcasts to the nodes in the cluster. In this way, broadcast Authentication of packets.
[002...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com