Authorized file share method and device
A technology for authorizing files and file sharing, applied in the information field, can solve problems such as hidden dangers of cloud storage data security, and achieve the effect of ensuring data ownership and protecting data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
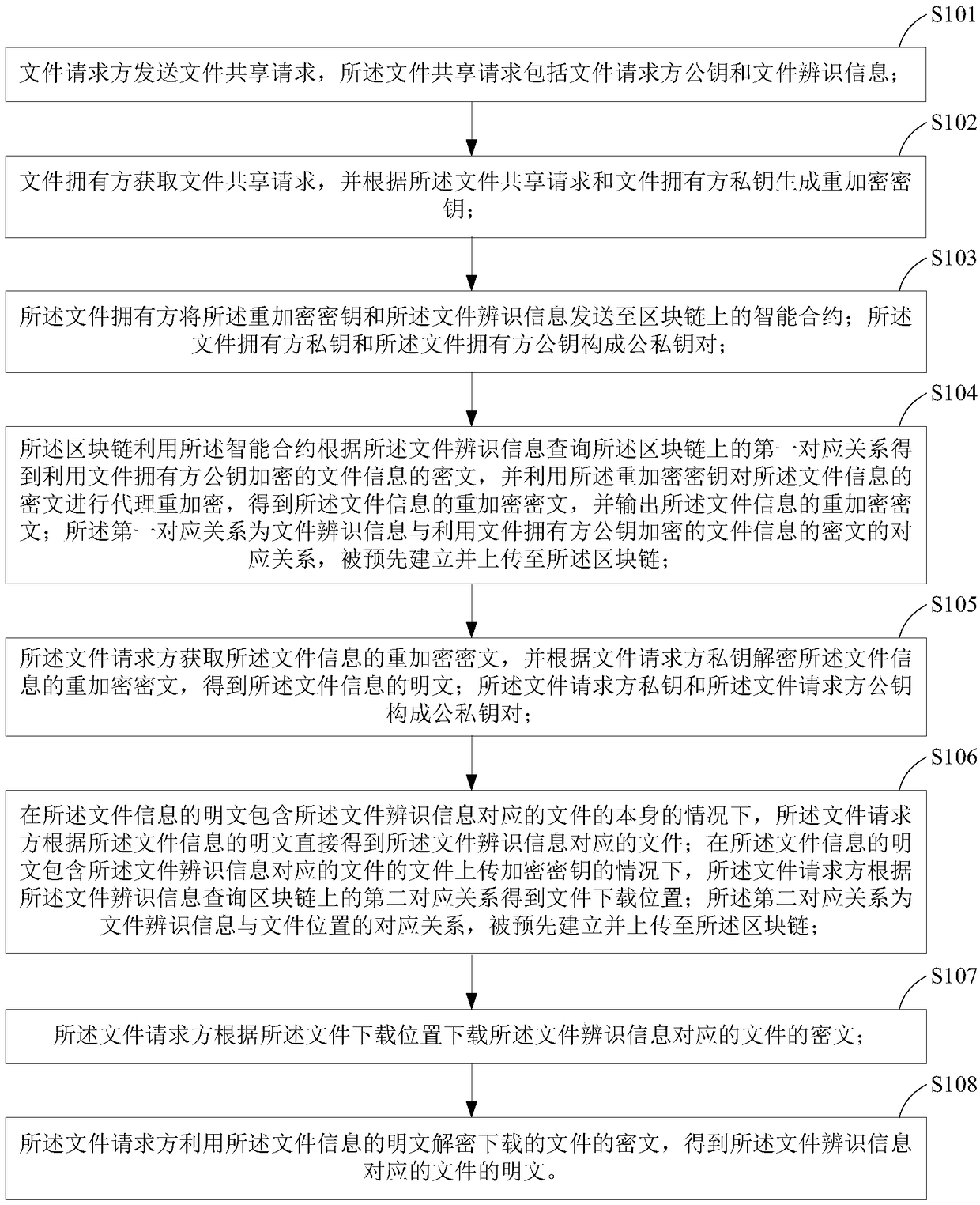
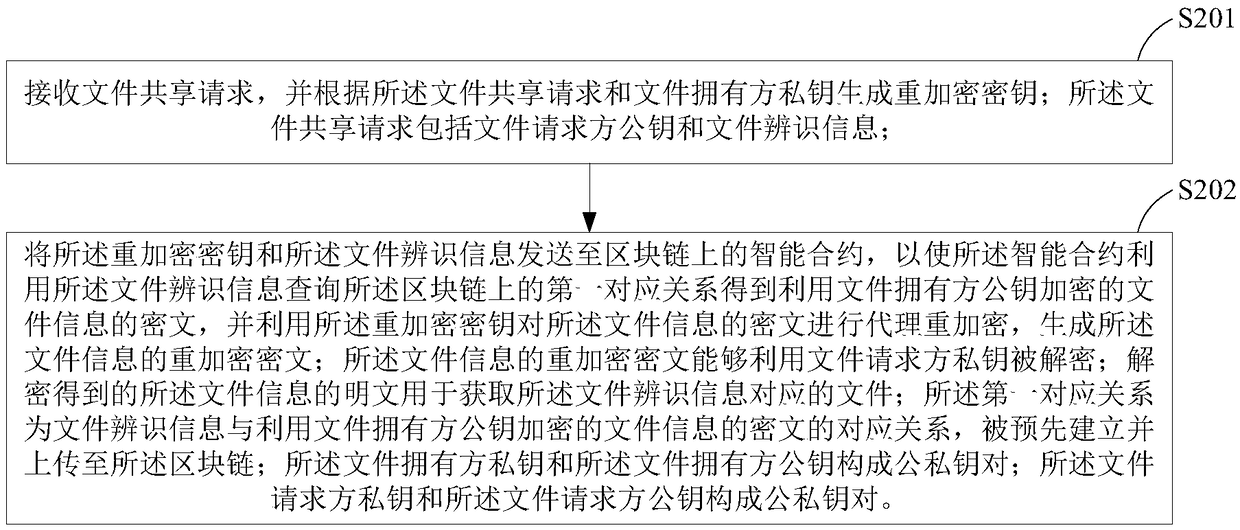
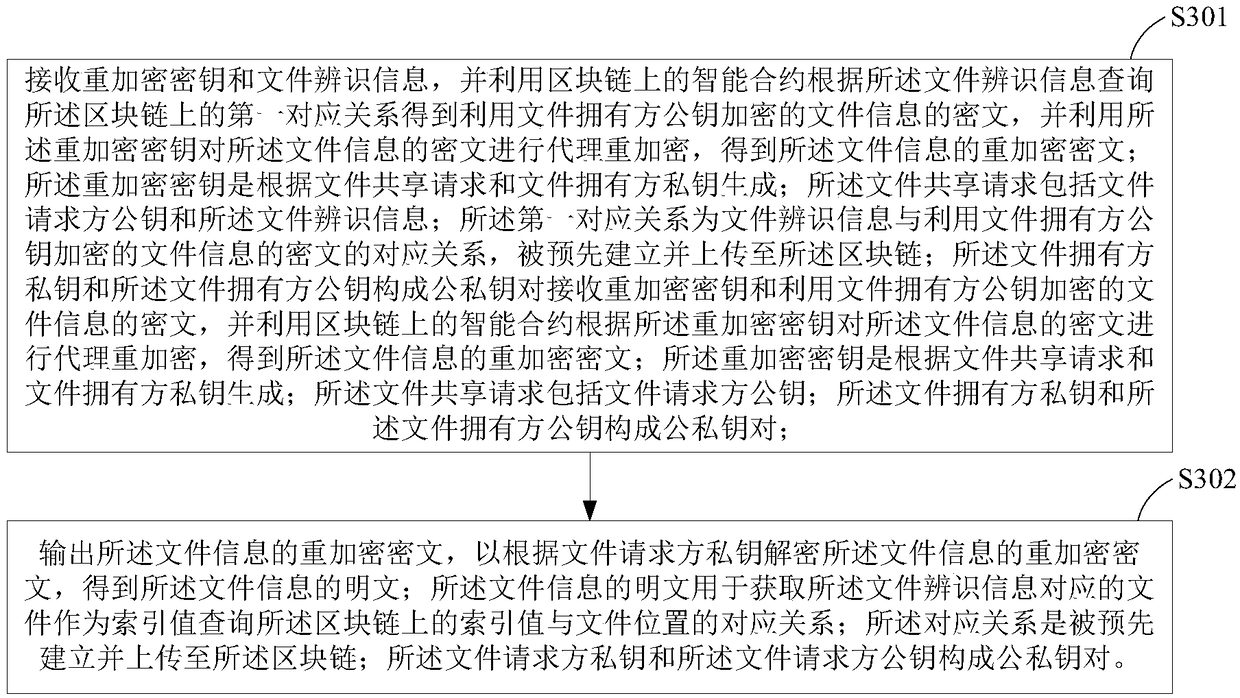
[0024] In order to make the purpose, technical solutions and advantages of the embodiments of the present invention more clear, the embodiments of the present invention will be further described in detail below in conjunction with the accompanying drawings. Here, the exemplary embodiments and descriptions of the present invention are used to explain the present invention, but not to limit the present invention.
[0025] The blockchain derived from the underlying technology of Bitcoin is a chained data structure formed by sequentially connecting data blocks in chronological order, and it is cryptographically guaranteed to be tamper-proof and unforgeable, and realizes decentralized Distributed accounting. Smart contracts running on the blockchain can disseminate, verify or execute contracts in an informationized manner, allowing trusted transactions without a third party, and these transactions are traceable and irreversible.
[0026] Based on the above characteristics of the b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com