Certificateless condition based proxy re-encryption system and method
A proxy re-encryption and no-certificate technology, which is applied in transmission systems, electrical components, usage of multiple keys/algorithms, etc., can solve problems such as third-party inquiries, high cost of certificate verification, complex certificate management, etc., and achieve excellent performance Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
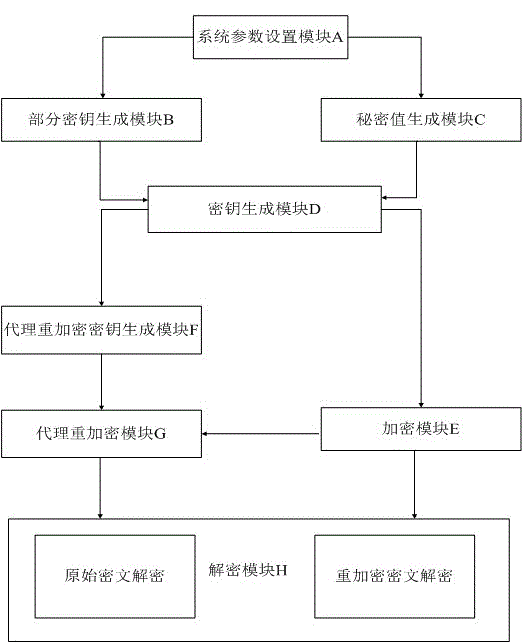
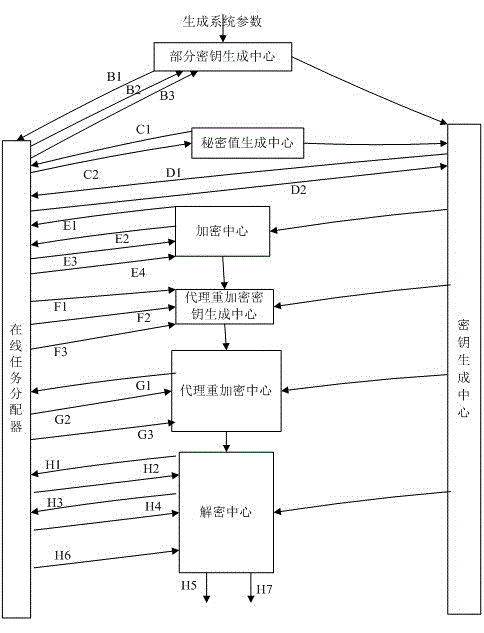
[0032] The technical scheme of the present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments, so that those skilled in the art can better understand the present invention and implement it, but the examples given are not intended to limit the present invention.
[0033] In this system:
[0034] (1) Key generation center: responsible for system parameter generation, that is, generating system master key (private key of key generation center) and system public parameter set (including cyclic group, generator, master public key and hash function, etc. ), and a trusted third party that generates some public-private key pairs for system users;
[0035] (2) Client: The original receiver of the encrypted message is the entity that entrusts the receiver to exercise the decryption right;
[0036] (3) Accepting party: the entity that receives the authorization of the entrusting party and exercises the decryption ri...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com