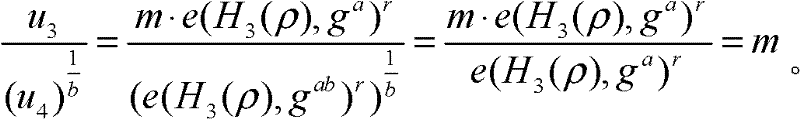Method and device with privacy protection function for data sharing and publishing
A data sharing and privacy protection technology, applied in the field of information security to achieve the effect of data privacy protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0041] refer to figure 1 , which shows a flow chart of a method for sharing and publishing data with privacy protection according to the present invention, the method specifically includes:
[0042] Step S101, the data owner encrypts the owned data and keywords related to the data with a public key according to the preset requirements, and stores them in the storage server provided by the service provider;
[0043] Preferably, the encryption of the owned data and keywords related to the data with a public key is specifically divided into the following sub-steps:
[0044] Encrypt the data you own with a public key;
[0045] Key words related to owned data are encrypted with a public key.
[0046] Step S102, the user sends keyword query request information to the service provider; the request information is composed of trapdoor information that implies query keywords;
[0047] Step S103, the service provider forwards the received keyword query request information to the data ...
Embodiment 2
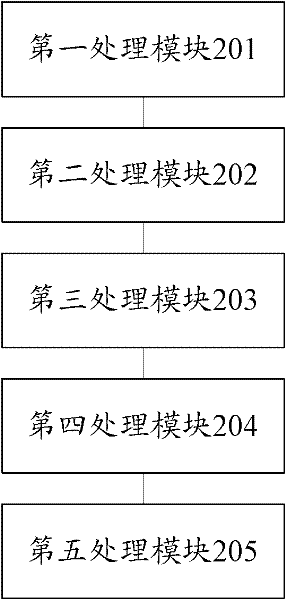
[0093] refer to figure 2 , shows a structure diagram of a data sharing and publishing device with privacy protection according to the present invention, and the device specifically includes:
[0094] The first processing module 201 is used for the data owner to encrypt the owned data and keywords related to the data with a public key according to preset requirements, and store them in the storage server provided by the service provider;
[0095] The second processing module 202 is configured to send keyword query request information from the user to the service provider; the request information is composed of trapdoor information that implies query keywords;
[0096] The third processing module 203 is used for forwarding the received keyword query request information to the data owner by the service provider;
[0097] The fourth processing module 204 is used for the data owner to authorize the service provider by issuing a proxy re-encryption key to the service provider;
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com