Hybrid cloud-oriented multi-keyword Top-k ciphertext retrieval method and system of privacy protection
A privacy-protecting, top-k technology, applied in file management systems, transmission systems, and other database retrievals, can solve problems such as complex index tree construction, low retrieval efficiency, and reduced retrieval computing overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
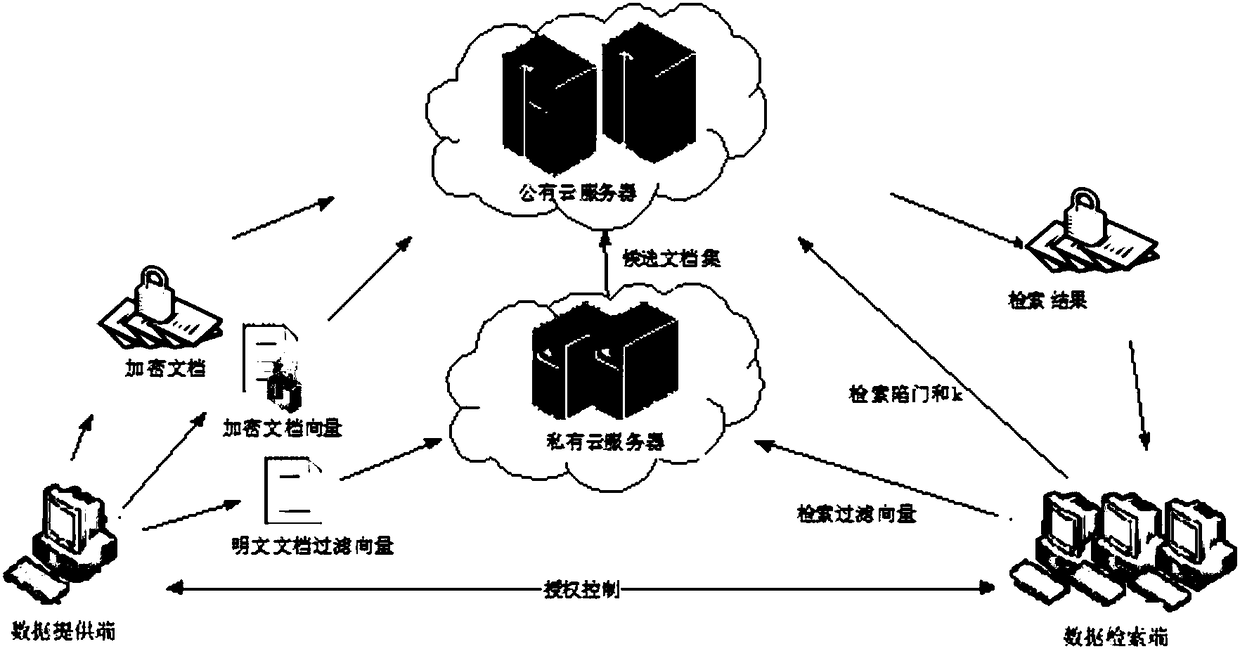
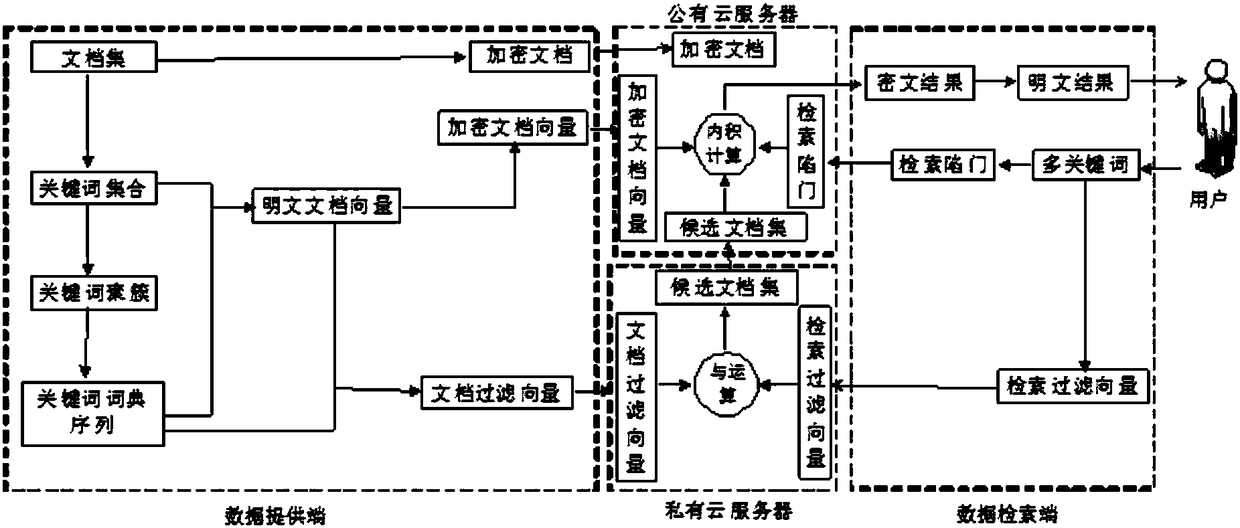
[0068] This embodiment provides a hybrid cloud-oriented privacy protection multi-keyword Top-k ciphertext retrieval method, such as figure 1 and figure 2 shown, including the following steps:
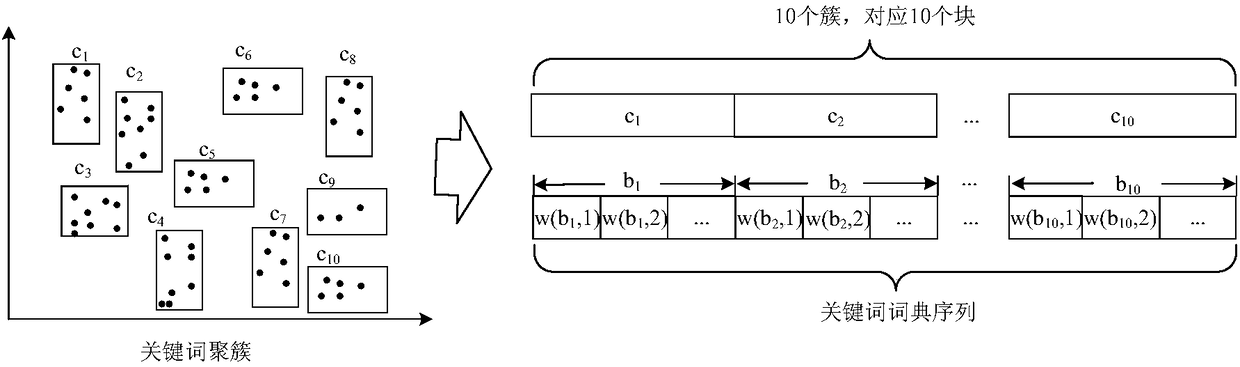
[0069] (1) The data provider extracts the keyword set from the provided document set, and generates a keyword dictionary sequence by clustering and partitioning; then generates a corresponding plaintext document vector for each document in the document set according to the keyword dictionary sequence, and based on Blocking of Keyword Dictionary Sequence Divide the plaintext document vector into blocks to form a document filter vector; then encrypt the plaintext document vector to form an encrypted document vector, encrypt each document in the document set to form an encrypted document set; finally transmit the document filter vector to the private cloud server, and transmit the encrypted document vector and the encrypted document set to the public cloud server.
[0070] This step spe...
Embodiment 2
[0094] This embodiment provides a hybrid cloud-oriented privacy protection multi-keyword Top-k ciphertext retrieval system, including a data provider, a data retrieval terminal, a private cloud server and a public cloud server, wherein:
[0095] The data provider is used to extract the keyword set from the provided document set, and generate a keyword dictionary sequence by clustering and partitioning; and generate a corresponding plaintext document vector for each document in the document set according to the keyword dictionary sequence, and generate a corresponding plaintext document vector according to the key word Blocking of the word dictionary sequence blocks the plaintext document vector to form a document filter vector; and encrypts the plaintext document vector to form an encrypted document vector, encrypts each document in the document set to form an encrypted document set; and transmits the document filter vector to Private cloud server, which transmits the encrypted...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com