Patents
Literature
108 results about "Document filtering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
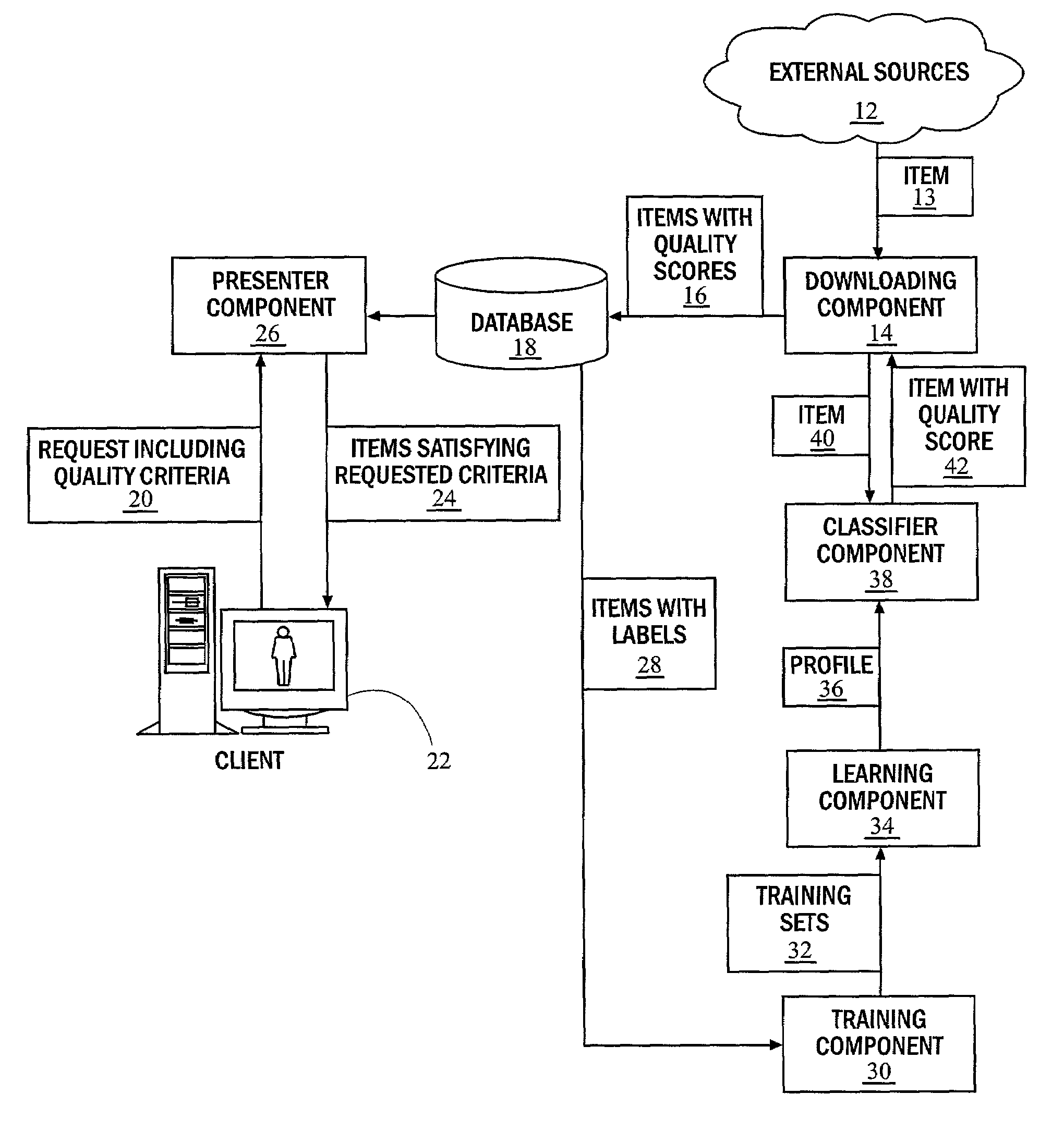
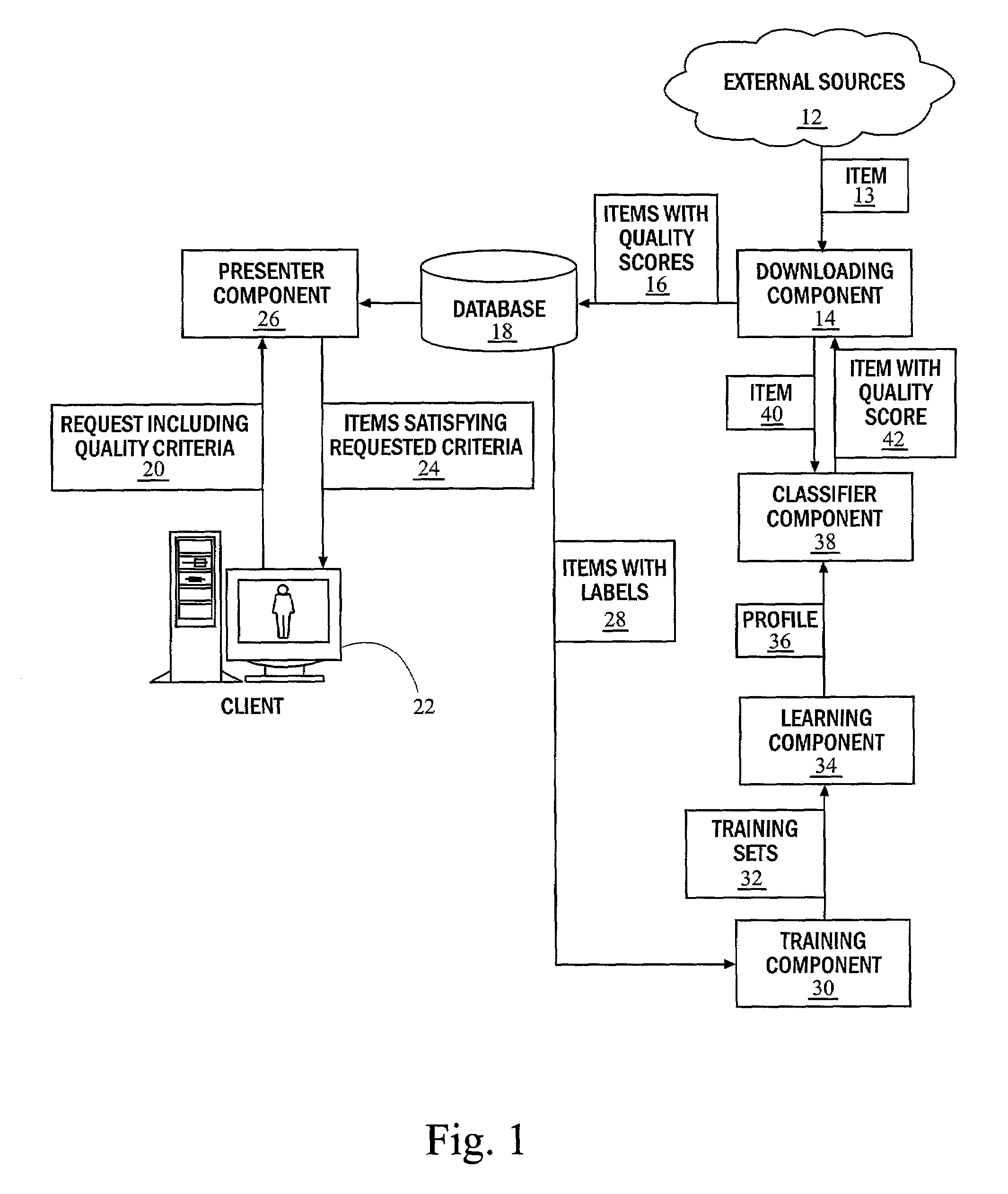
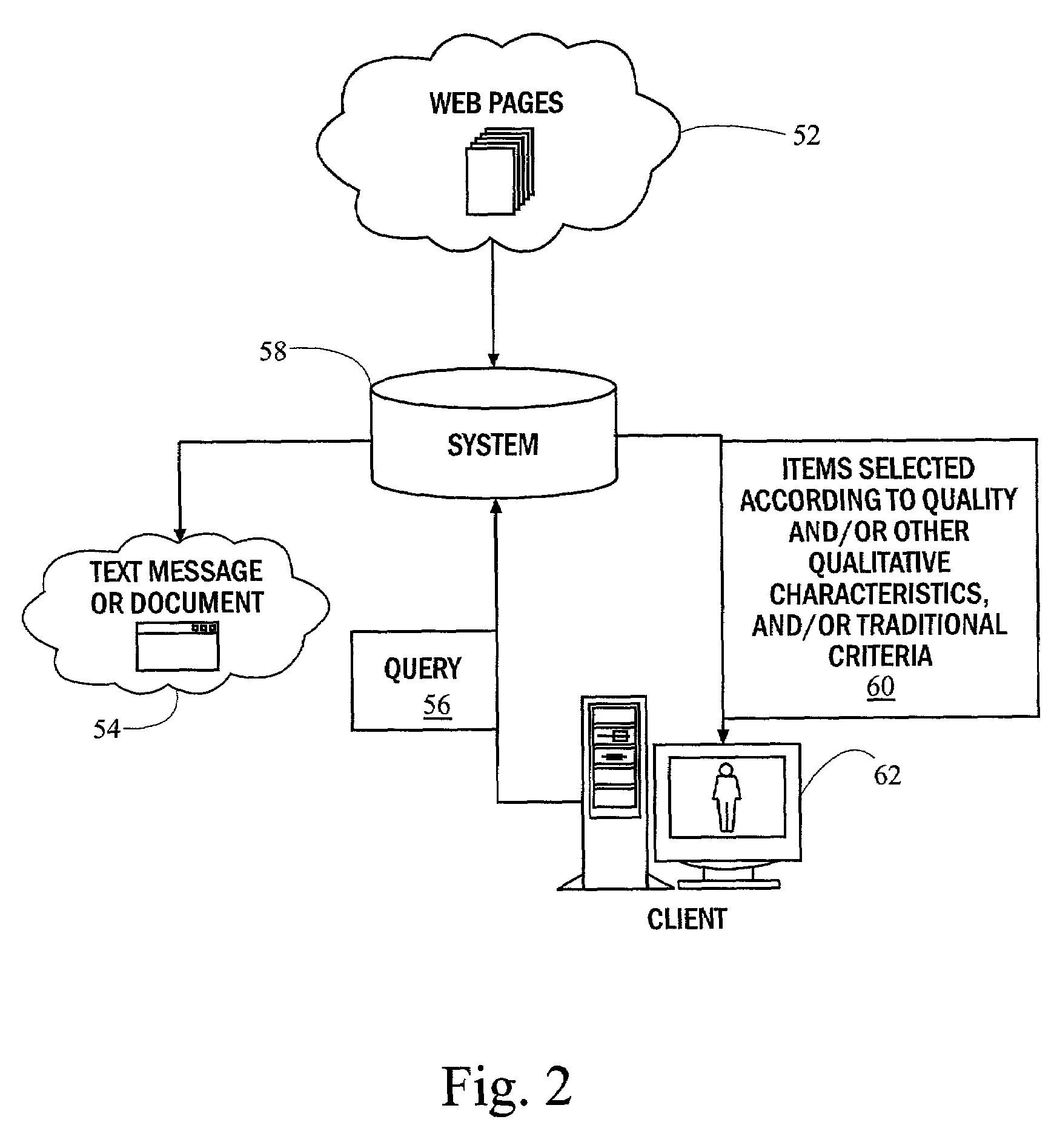
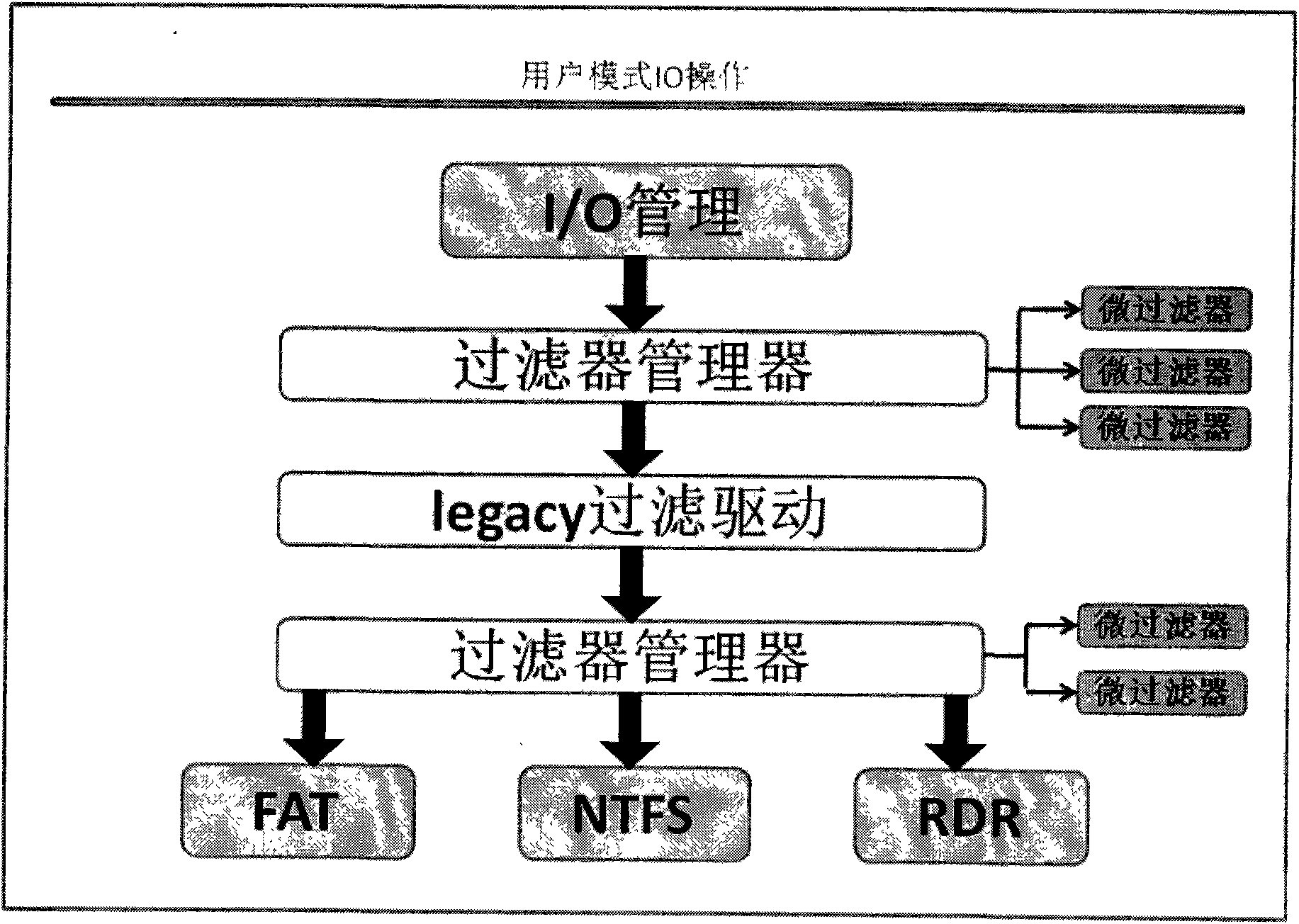
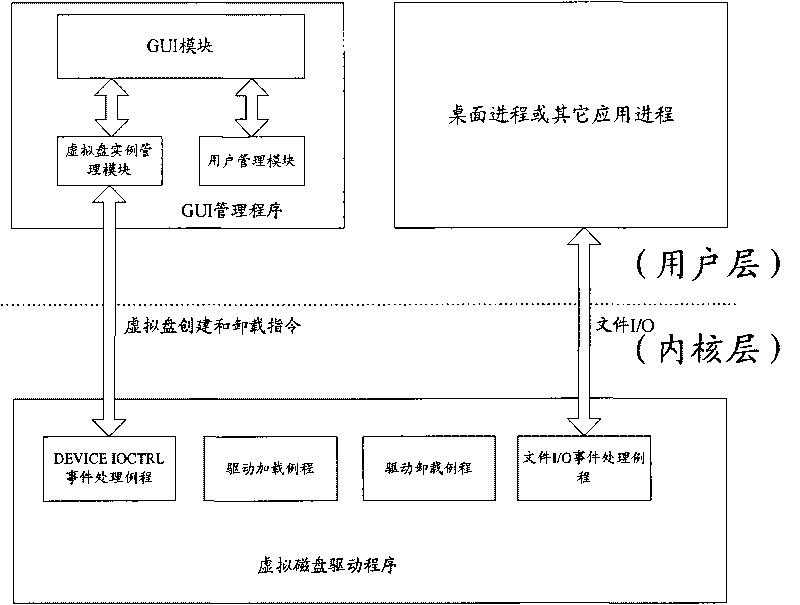
Document filters are responsible for: reading an original document in from a file in a specific format (e.g. different filters exist for handling plain text and OpenDocument/OpenOffice); extracting translatable content from a document;
Method and system for selecting documents by measuring document quality
InactiveUS7200606B2Limited bandwidthReduce capacityData processing applicationsDigital data information retrievalSubject matterDiscussion group
A system and method for document filtering and selection based on quality automatically operates to make value judgments for document retrieval. Items of data, e.g. documents, are automatically associated a value. Items of data may be then selected based upon value, which is not only for the specific subject or topic requested, but also desirable according to certain criteria, including each document's quality. A specific application of the invention is to a filter for computerized bulletin boards. Many of these systems, also known as discussion groups, have thousands of new messages per day. Readers and human editors do not have time to classify new messages by quality quickly. Messages may be ranked by quality automatically, to perform the same function performed by a human editor or moderator. Values and qualities may be assigned by interestingness, appropriateness, timeliness, humor, style of language, obscenity, sentiment, and any combinations thereof, for example.
Owner:RGT UNIV OF CALIFORNIA
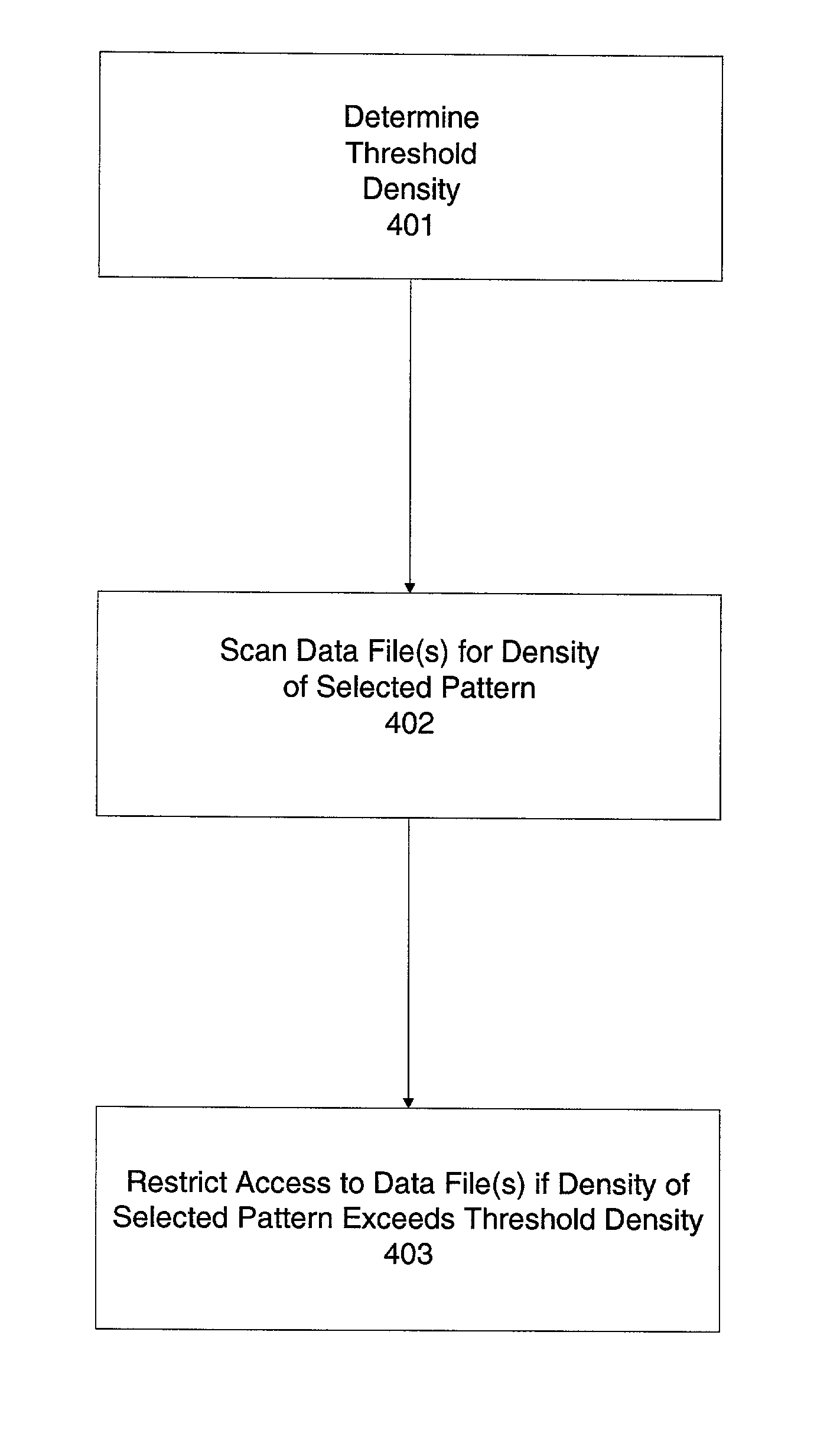
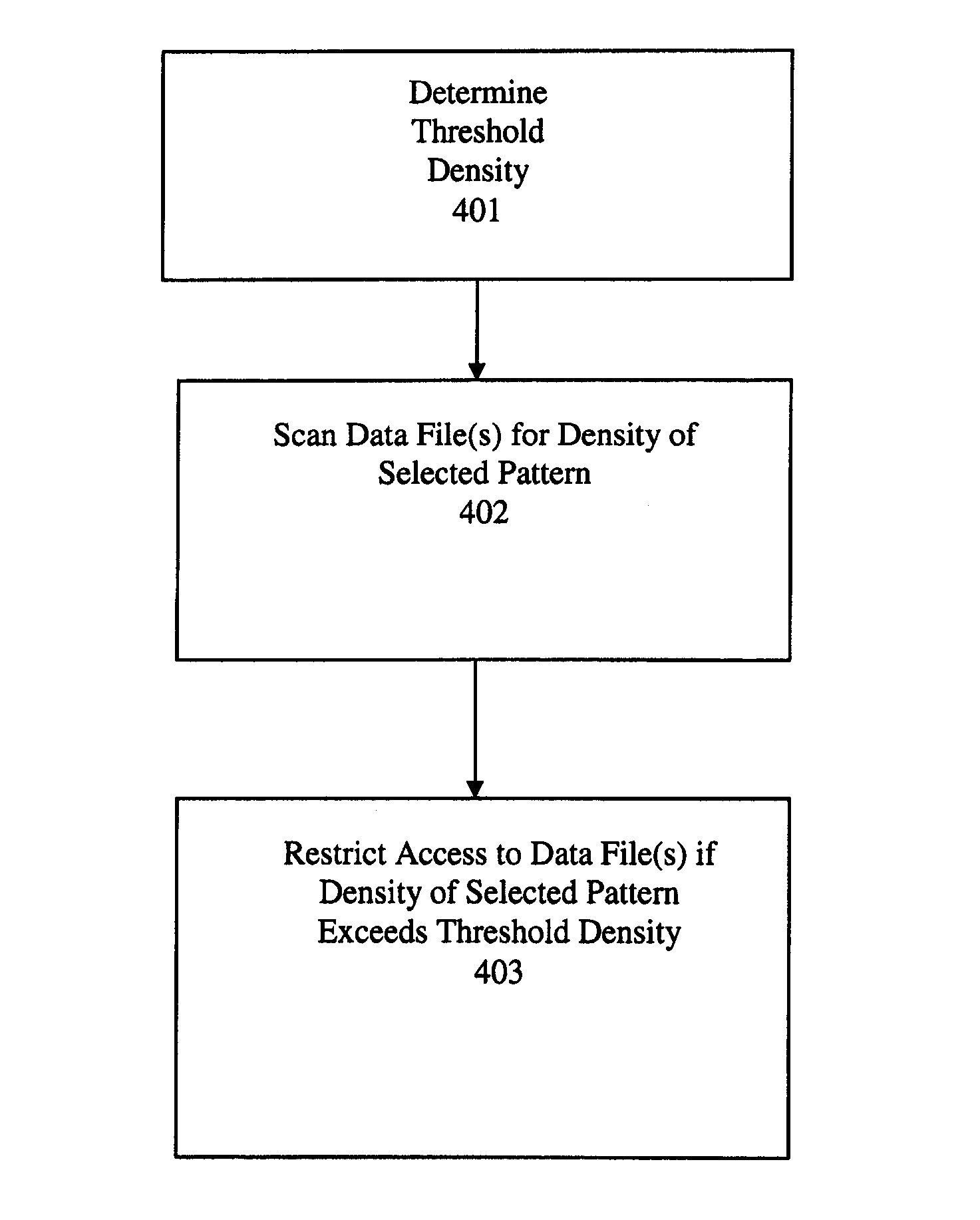
Method/system for preventing identity theft or misuse by restricting access
ActiveUS7272857B1Digital data processing detailsUser identity/authority verificationLimited accessIdentity theft
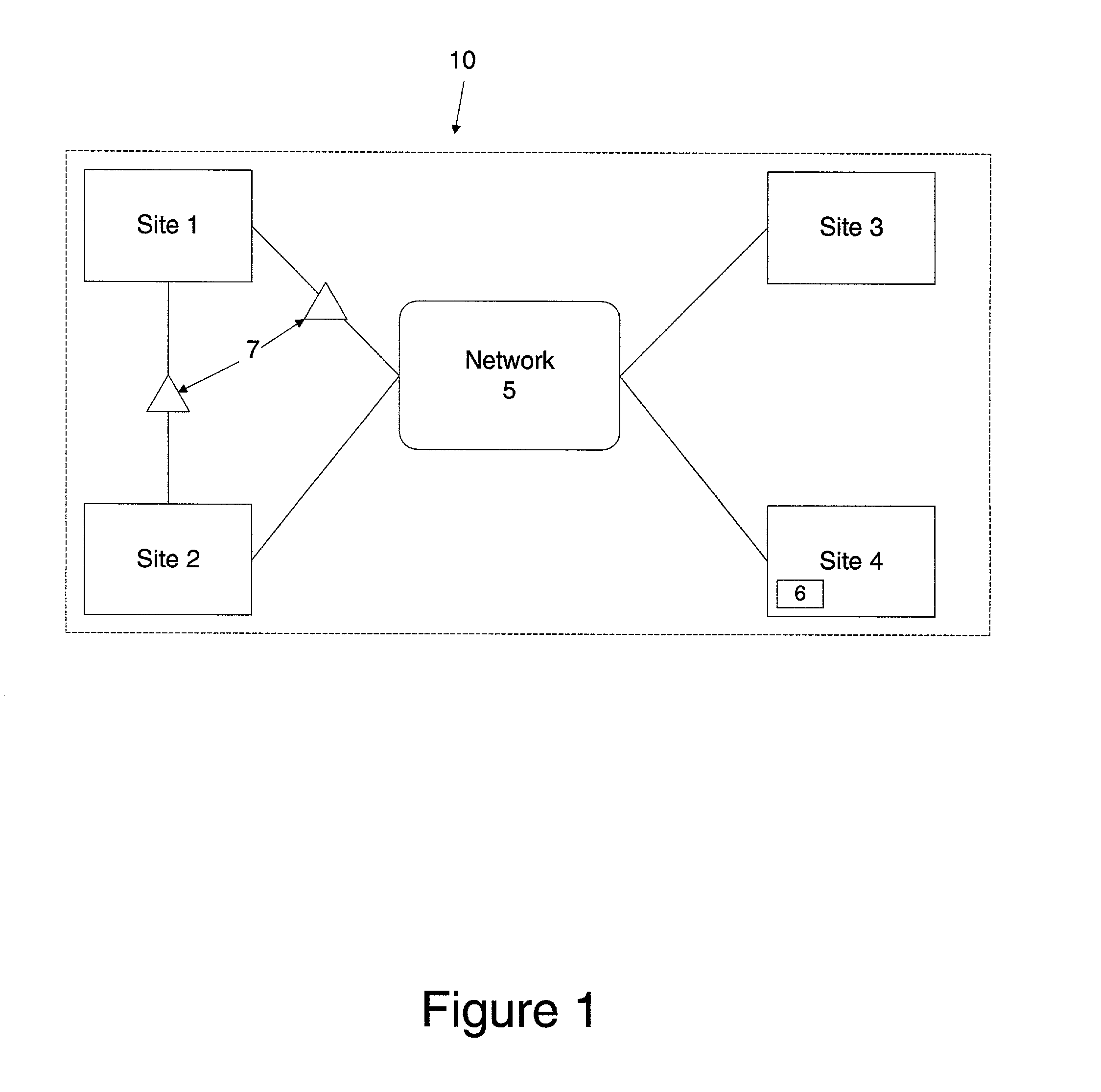
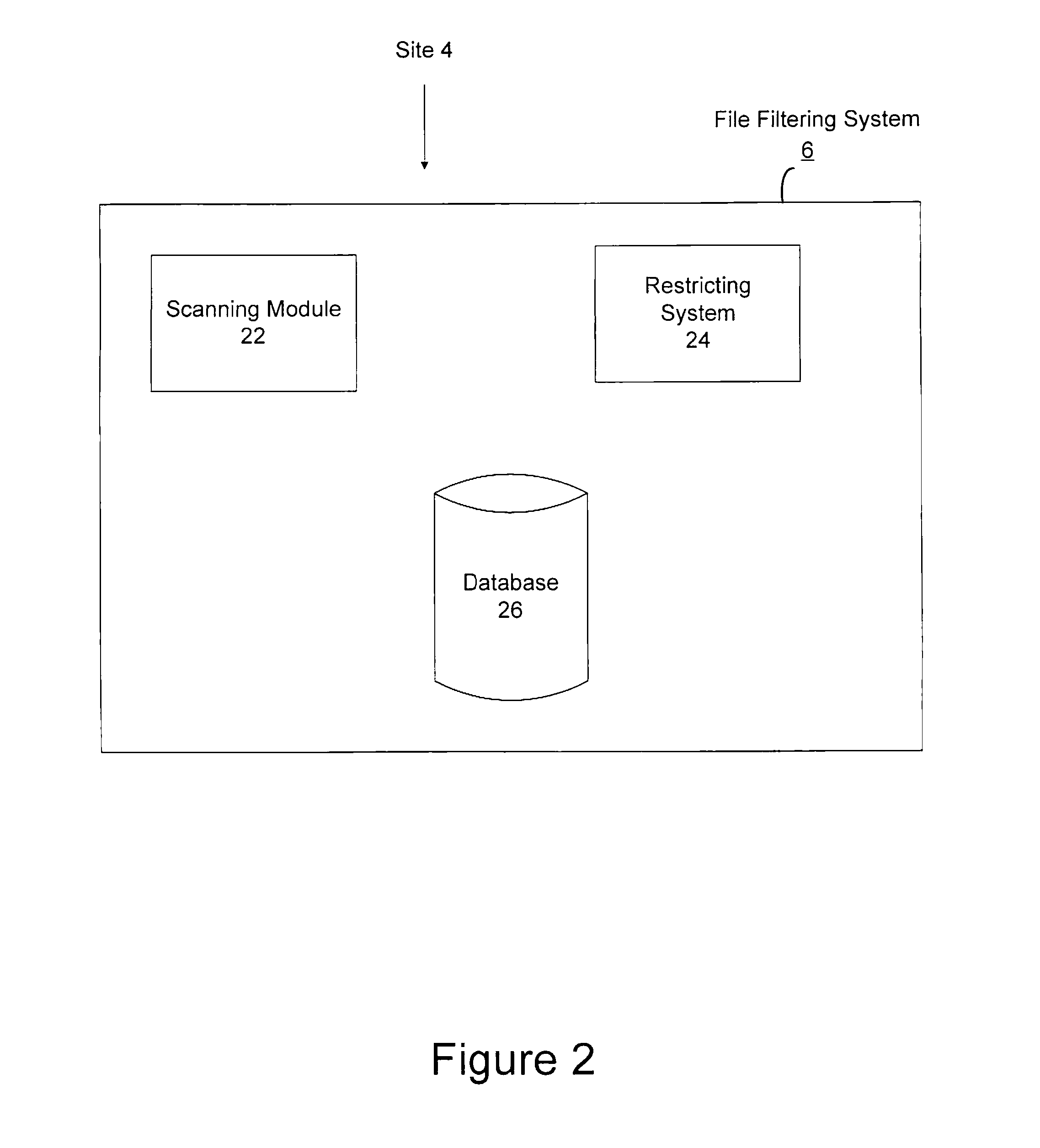
A system and method for network file filtering. The file filtering process includes scanning at least one data file for density of a selected pattern. The process may also include restricting access to the file if the density of the selected pattern in the data file is greater than or equal to a threshold density.
Owner:FIRST USA BANK N A +1
File protection technique based on Windows system files filtering drive
InactiveCN101256570AAddress reliabilityAddress flexibilityPlatform integrity maintainanceSpecial data processing applicationsTamper resistanceProsthesis
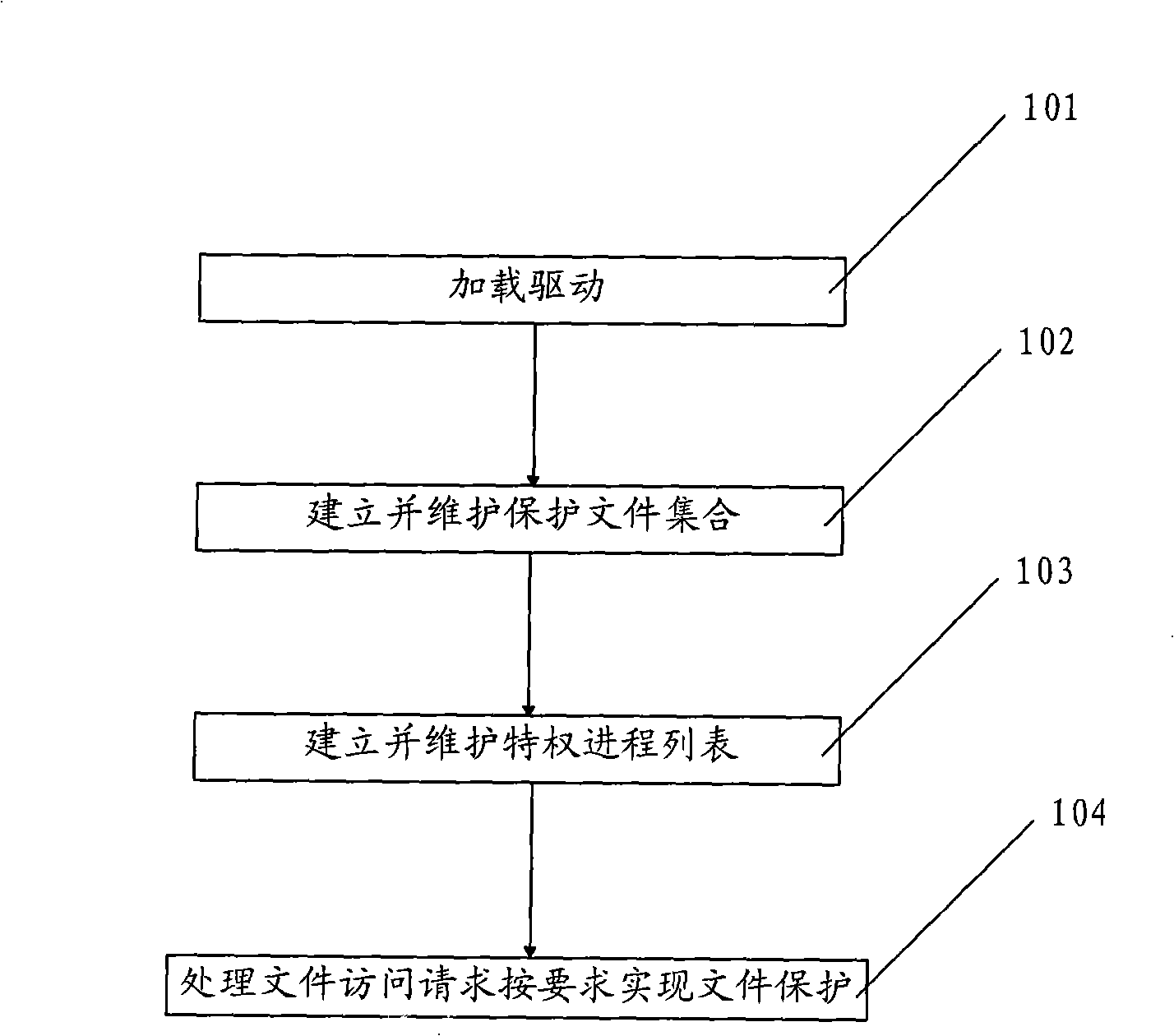
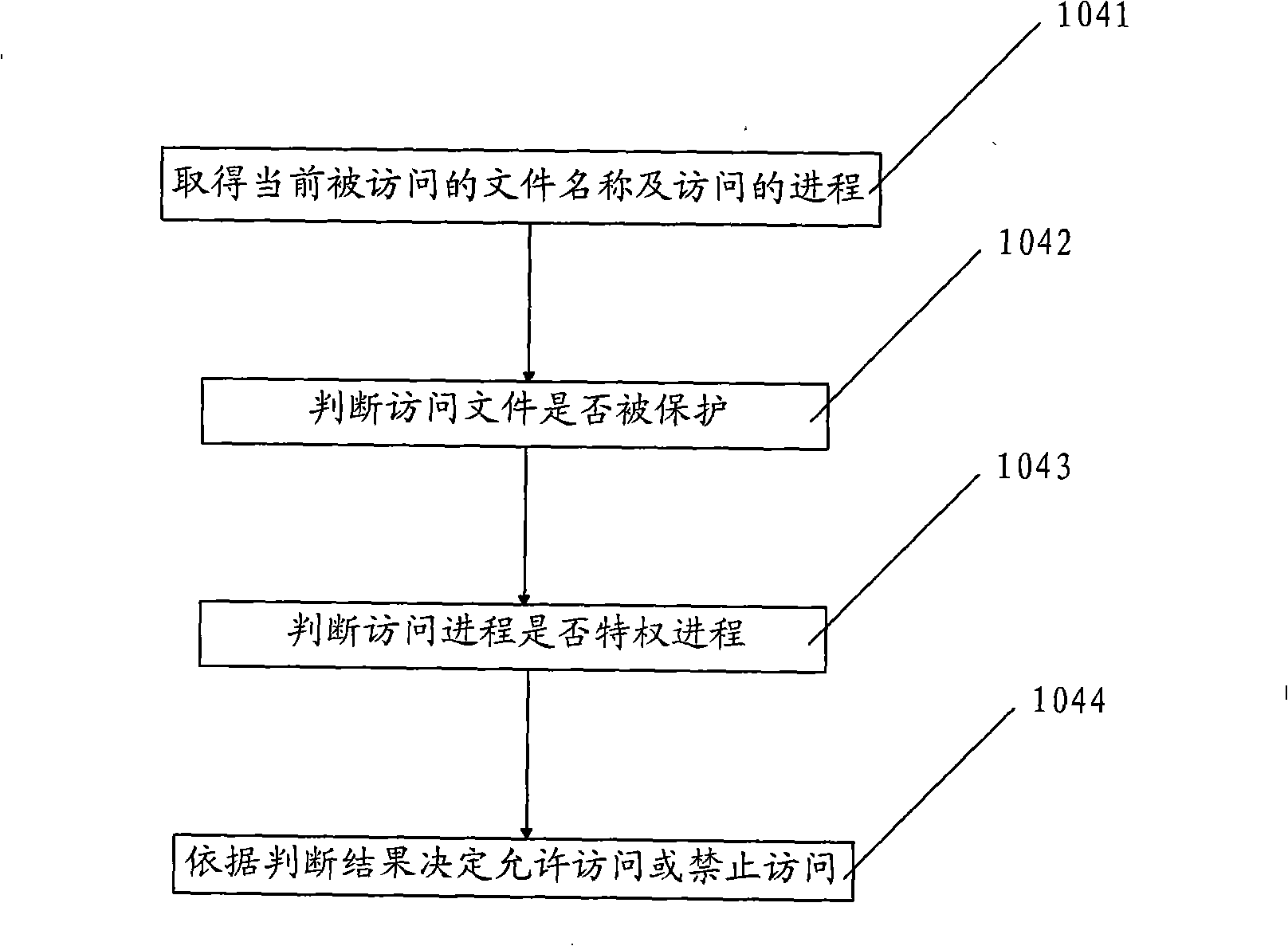
The invention belongs to InforGuard web page tamper-proof system middleware field, particularly is a file protection technology based on Window system file filter drive, which is realized by the following steps: A: loading drive, by calling Service provided by Window system to manage API in order to load a drive file; B: building up and maintaining a protected file assembling to obtain protected file assembling information after loading drive; C: building up and maintaining a privilege progress list to obtain privilege progress information which can visit the protected file after loading the drive; D: processing a file visit request to realize file protection according to claim. The scheme changes previous process ideas of file protection technology, and replaces passive prosthesis with active interception so that invalid act of amending is directly forbidden.
Owner:SHANDONG CVIC SOFTWARE ENG
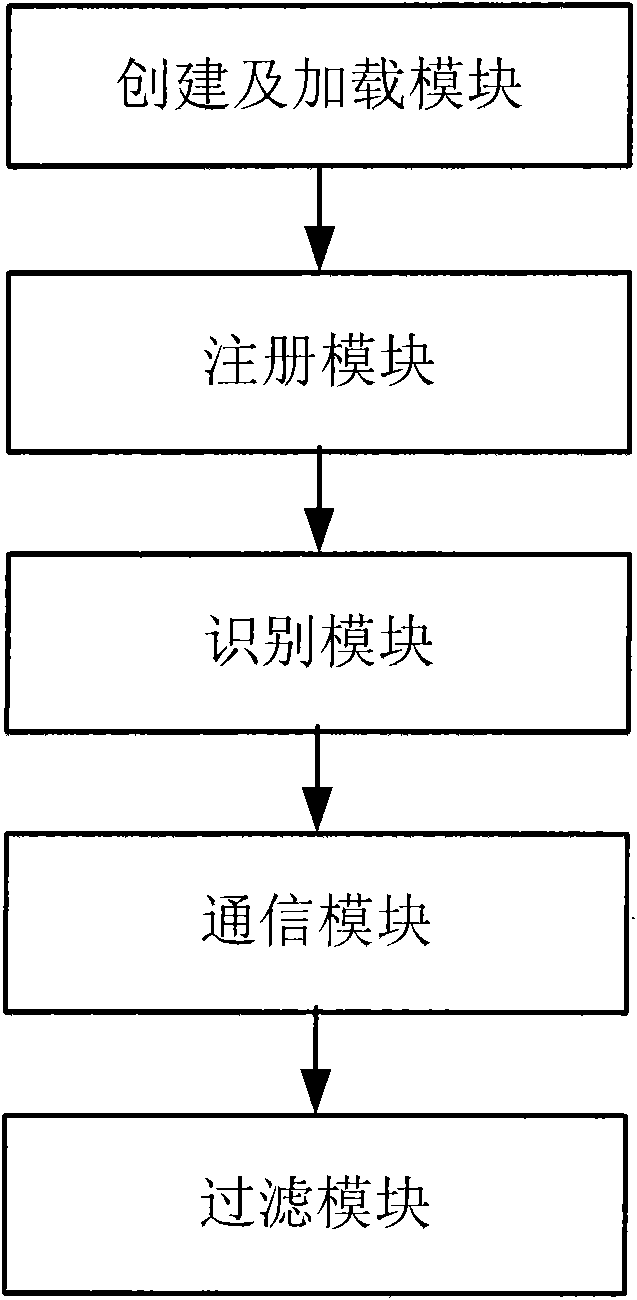
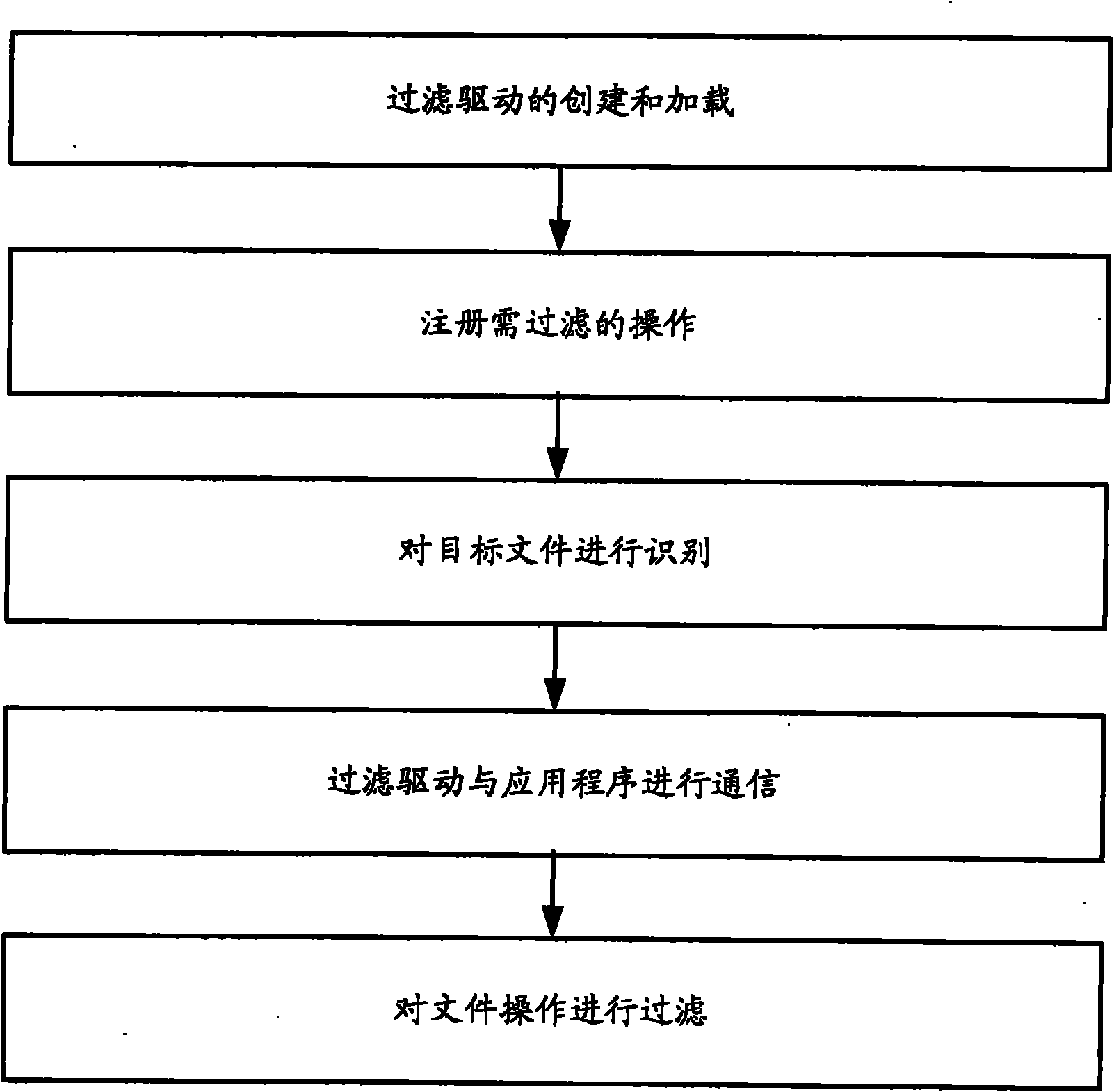
File access control method based on filter driving, system and filer manager
InactiveCN101916349AEnsure safetyImprove compatibilityDigital data protectionSpecific program execution arrangementsControl systemFile system
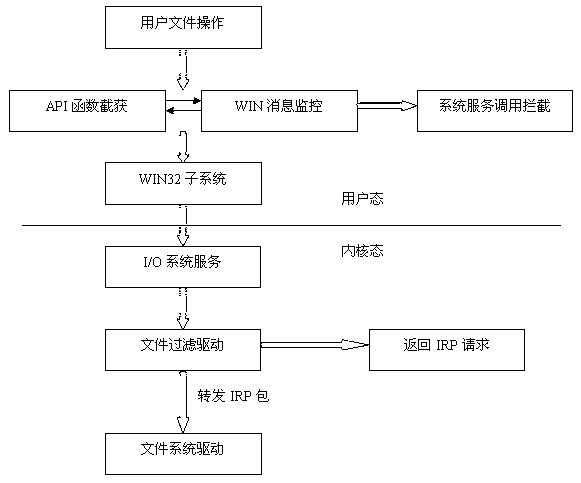
The invention discloses a file access control method based on filter driving, a system and a filer manager. The method comprises: adding a filter manager in an access control system; building and loading filter driving by a building and loading module of the filter manager; registering operation required to filter by the registered module of the filter manager; identifying a target file by the identification module of the filter manager; communicating the filter driving with the application program by the communication module of the filter manager; and filtering the file operation by the filtering module of the filter manager. On the premise that the invention does not need to redesign a file system and bottom layer driving, file filter driving in the Windows system intercepts and monitors file access, and the safety of file data is ensured on the bottom layer of the system.
Owner:SUN YAT SEN UNIV
Host file security monitoring method
InactiveCN103218575AChange behaviorChange performanceInternal/peripheral component protectionSoftware systemScreening method
The invention relates to the technical field of information security, in particular to a host file security monitoring and protecting method. The method is a file transparent encryption method based on a driver layer and is completely transparent to users; the users cannot sense file encryption and decryption in a use process; an application layer encryption method with higher security and quicker speed is used for assisting; and a file transparent encryption scheme based on a conventional file screening method is provided for more complicated software systems. According to the method, the process and files of a local computer are identified, and security files are automatically encrypted and decrypted, so that problems of memory mapping, file buffering and the like are solved, and the safety is increased.
Owner:WUHAN YOUNG TECH CO LTD
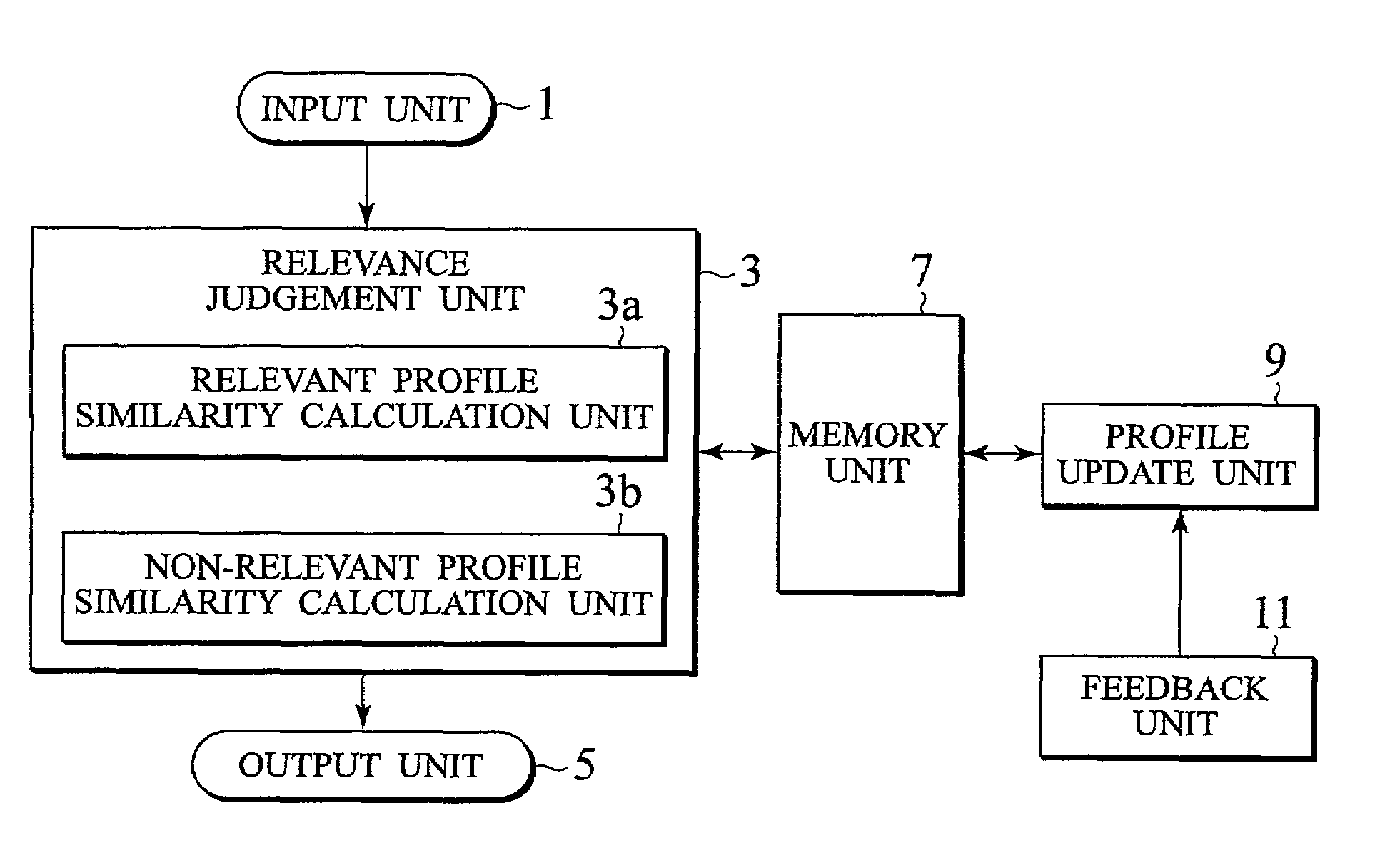
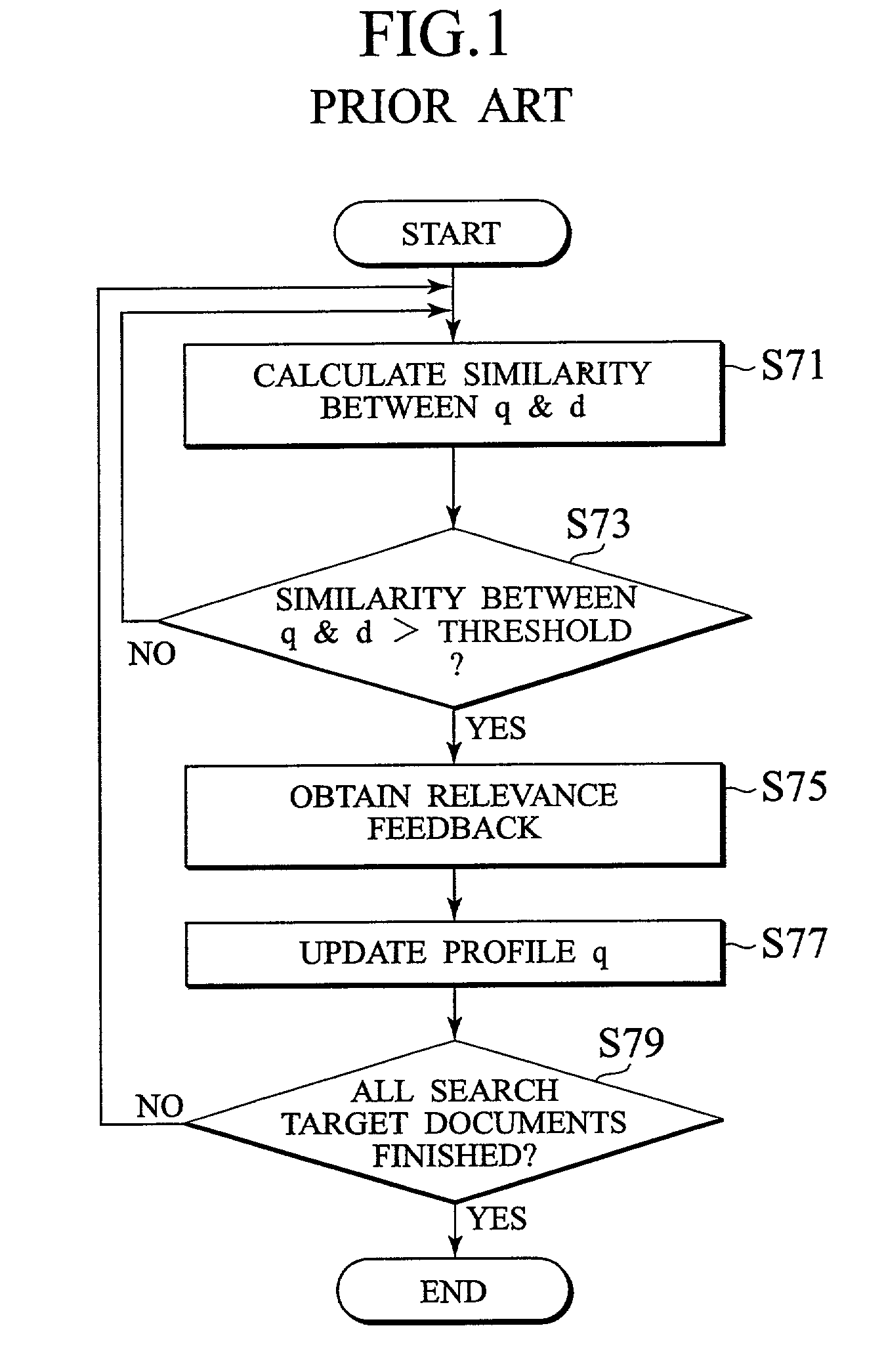
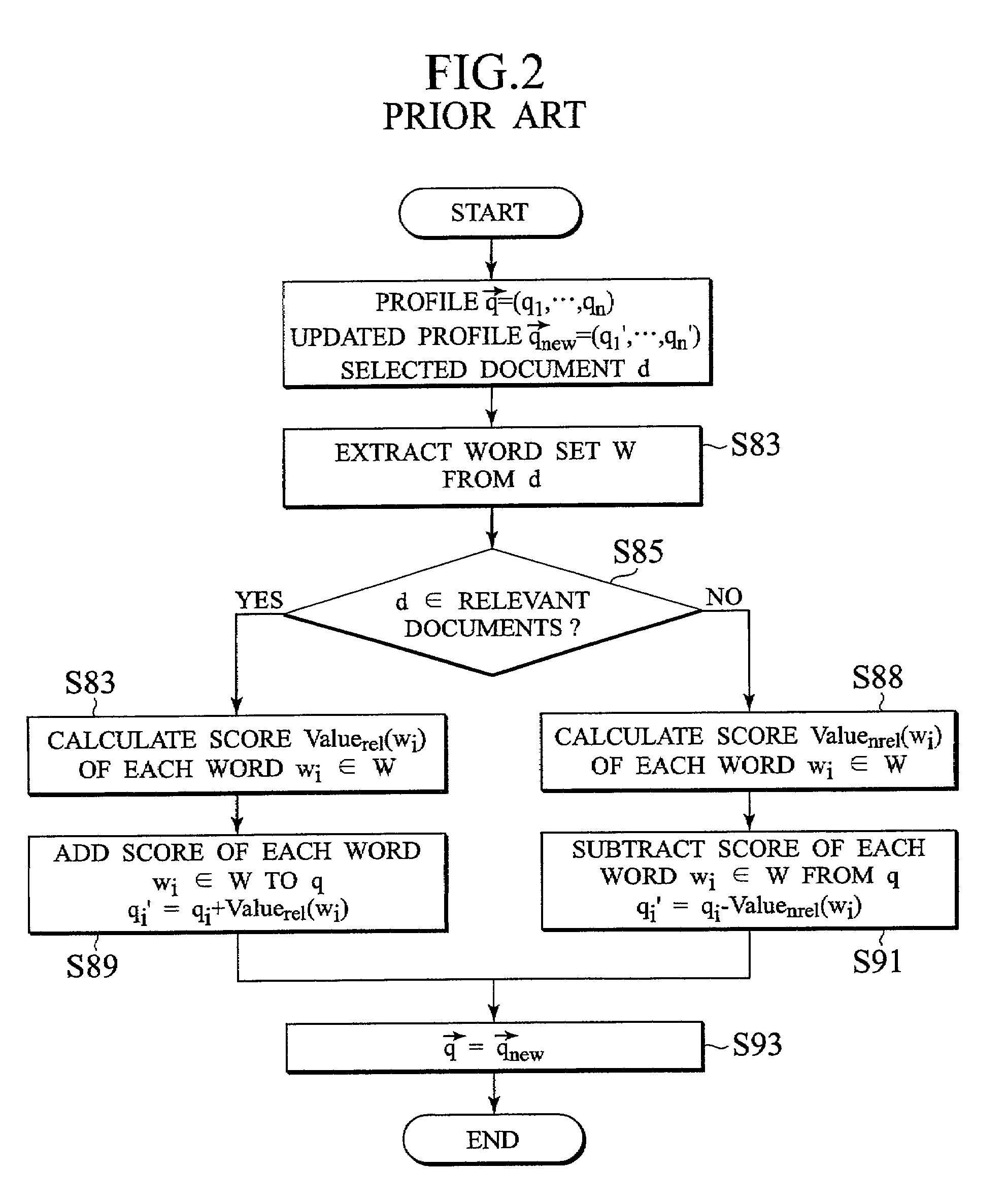
Scheme for filtering documents on network using relevant and non-relevant profiles
InactiveUS7152063B2Reduce in quantityData processing applicationsDigital data information retrievalDocumentation procedureDocument preparation
A document filtering scheme capable of reducing the number of erroneously selected non-relevant documents without reducing the number of correctly selected relevant documents is disclosed. a non-relevant profile expressing non-relevant documents that are judged as having high similarities with respect to a relevant profile expressing a user's request but not matching with the user's request is utilized in addition to the relevant profile, such that each search target document for which the similarity with respect to the relevant profile is higher than a prescribed threshold for the relevant profile and the similarity with respect to the non-relevant profile is higher than a prescribed threshold for the non-relevant profile is removed as a non-relevant document.
Owner:D D I
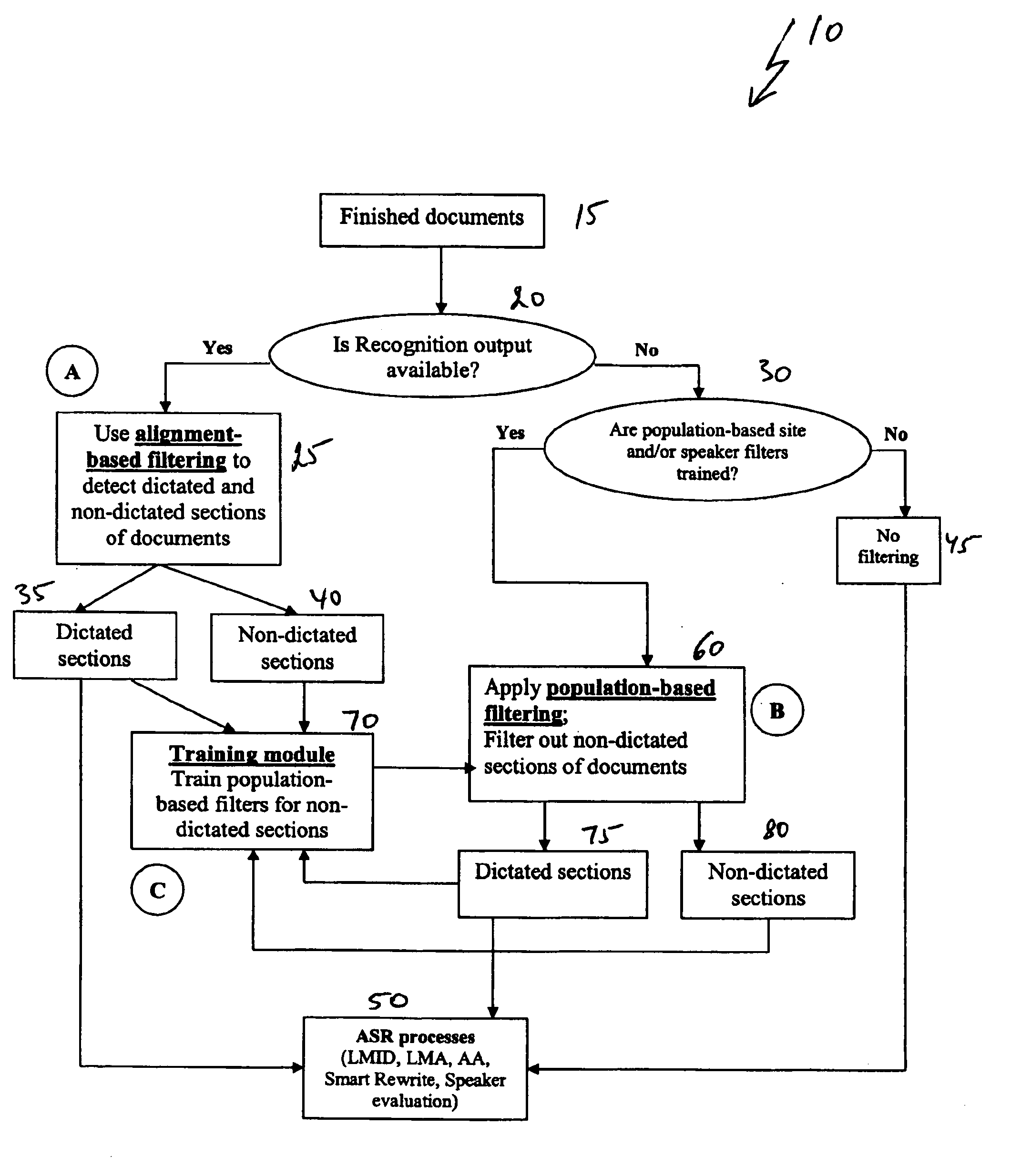
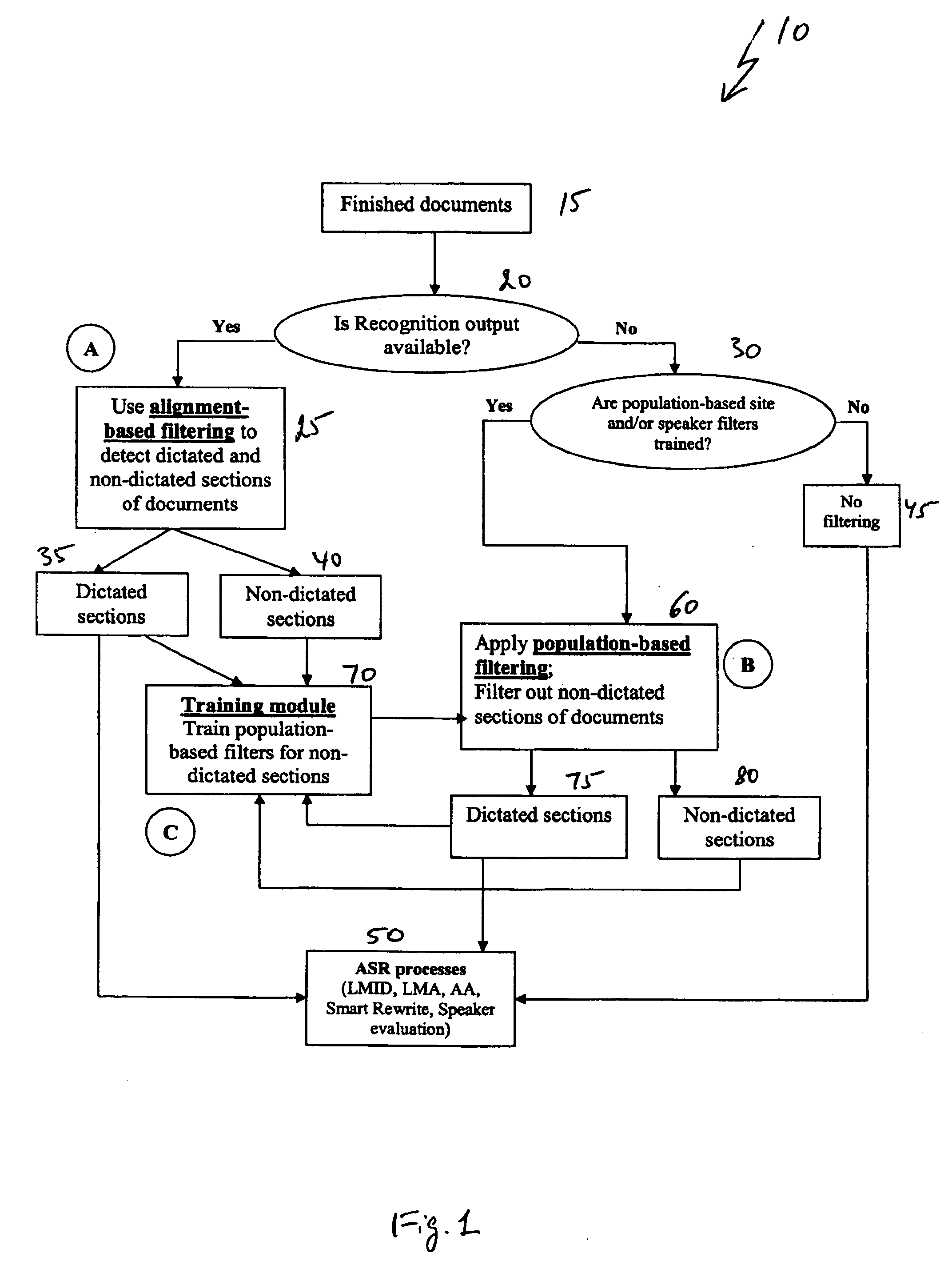
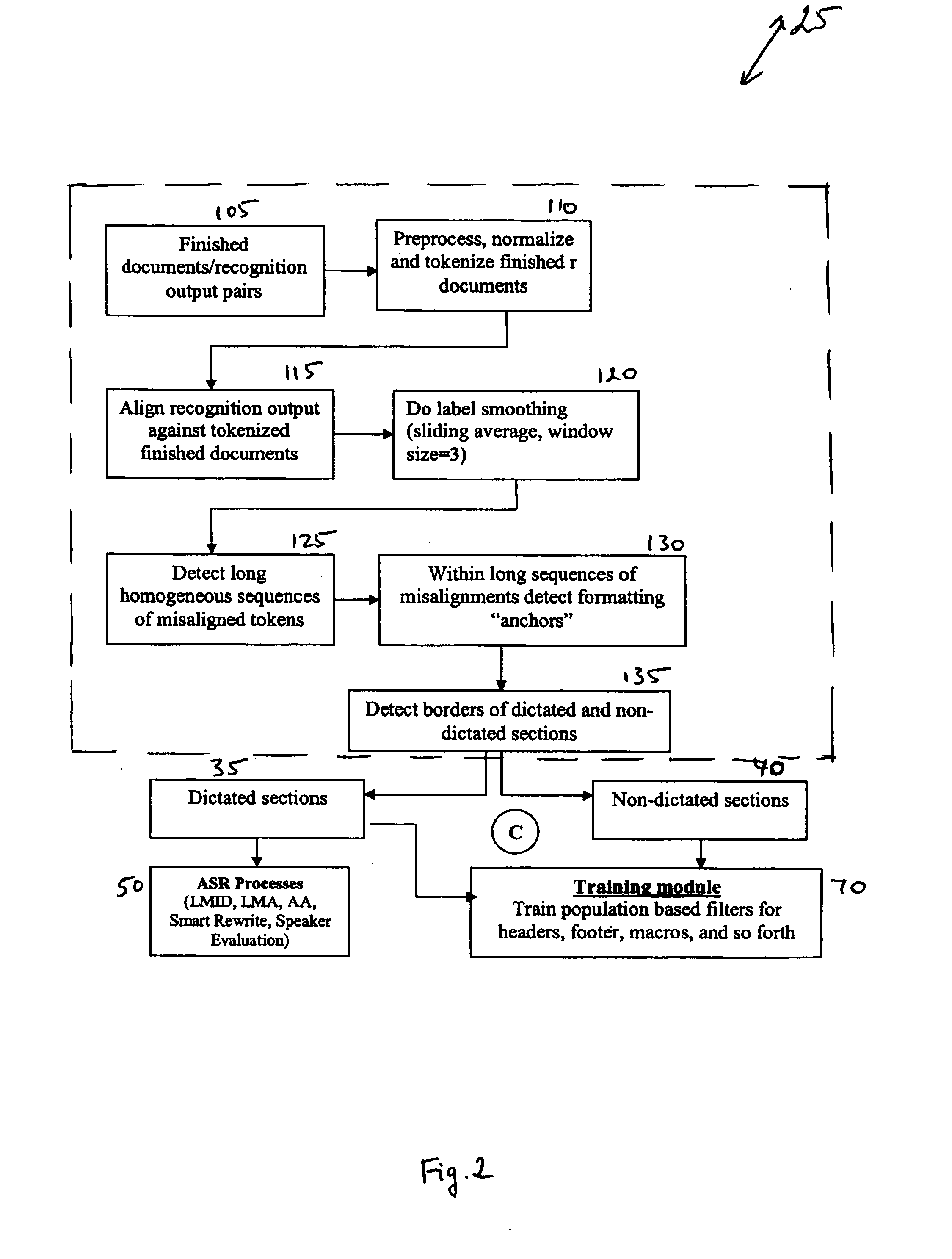
System and method for document filtering
A system and method for filtering documents to determine section boundaries between dictated and non-dictated text. The system and method identifies portions of a text report that correspond to an original dictation and, correspondingly, those portions that are not part of the original dictation. The system and method include comparing tokenized and normalized forms of the original dictation and the final report, determining mismatches between the two forms, and applying machine-learning techniques to identify document headers, footers, page turns, macros, and lists automatically and accurately.
Owner:NUANCE COMM INC
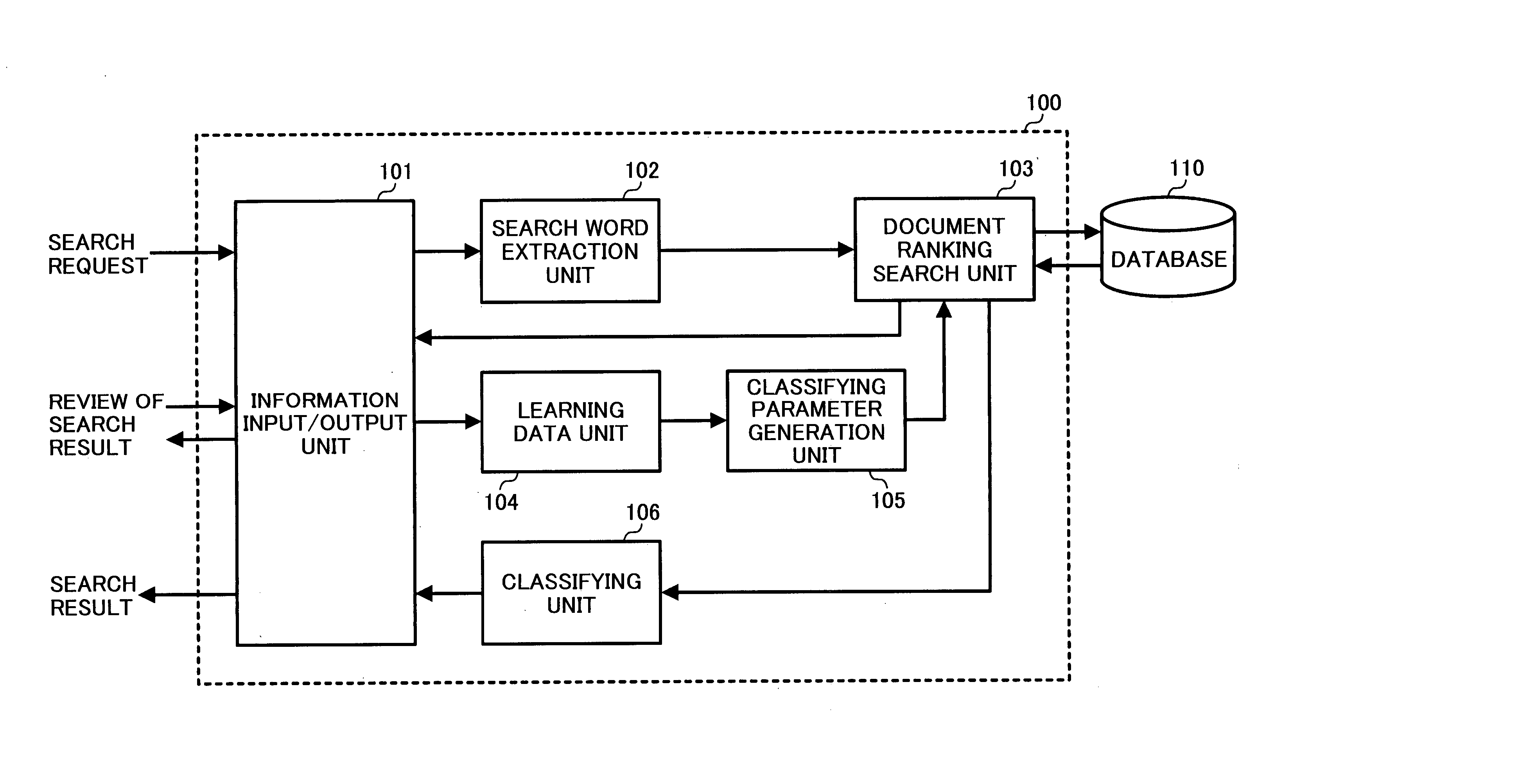
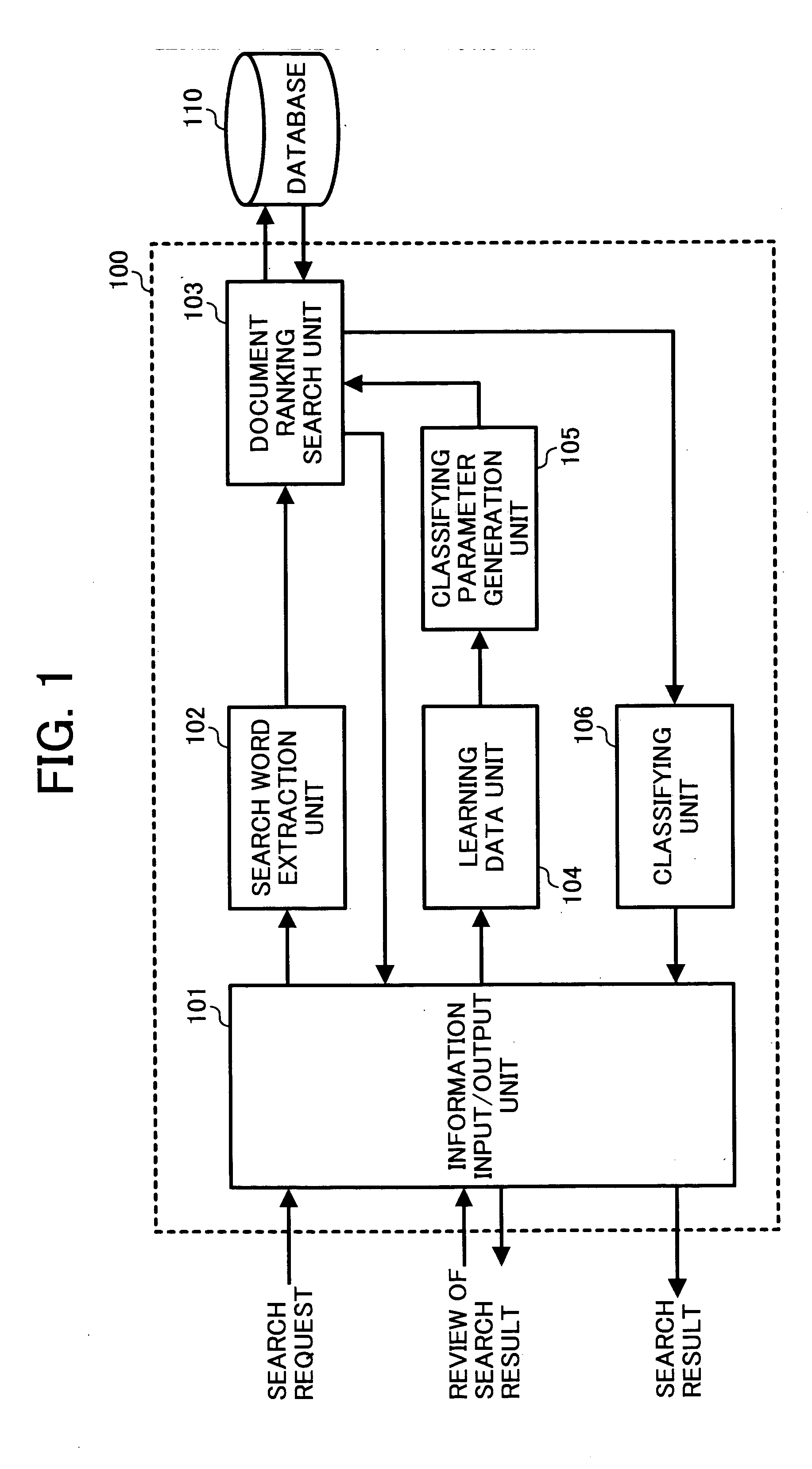
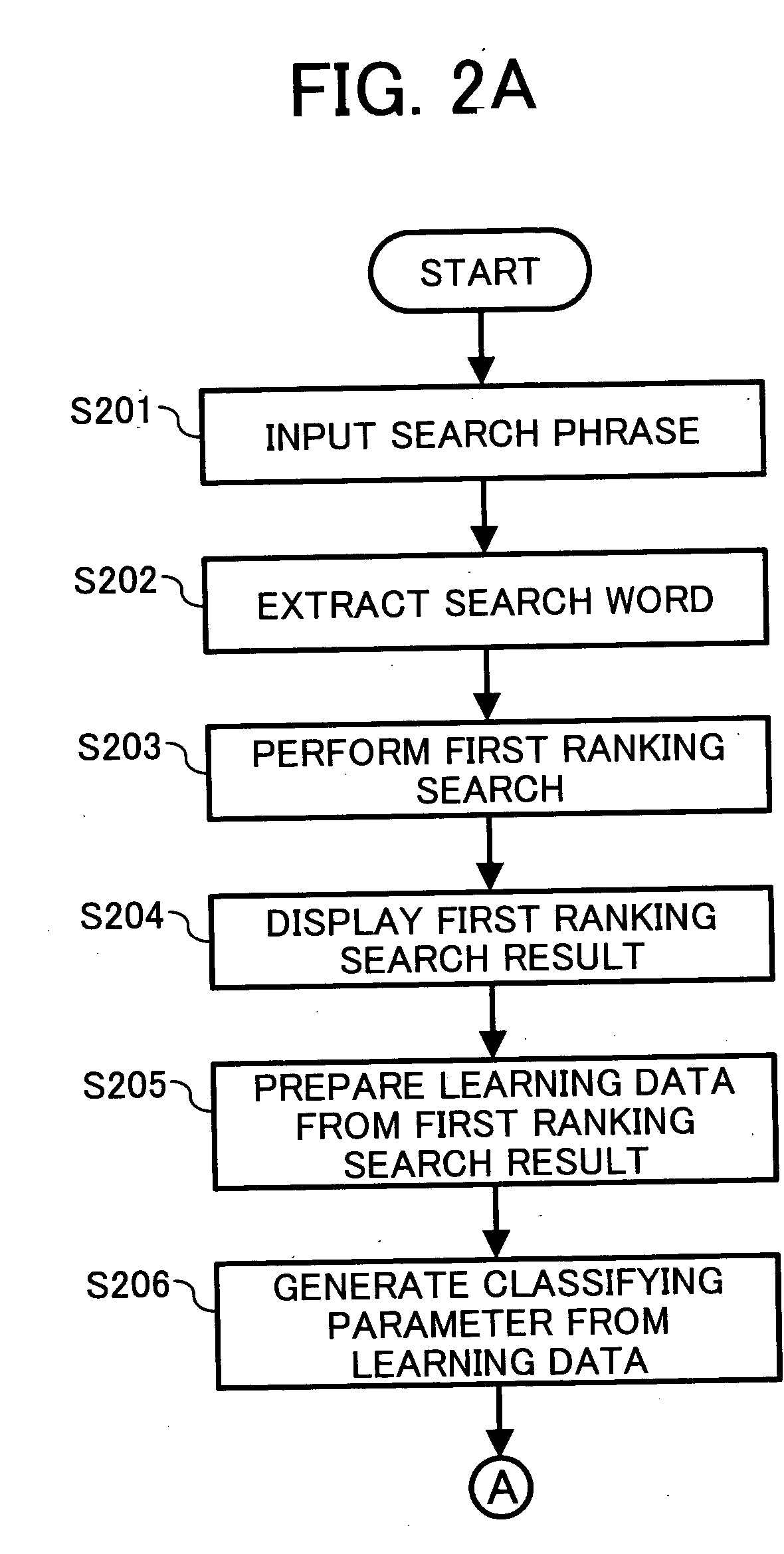
Method and apparatus for document filtering capable of efficiently extracting document matching to searcher's intention using learning data
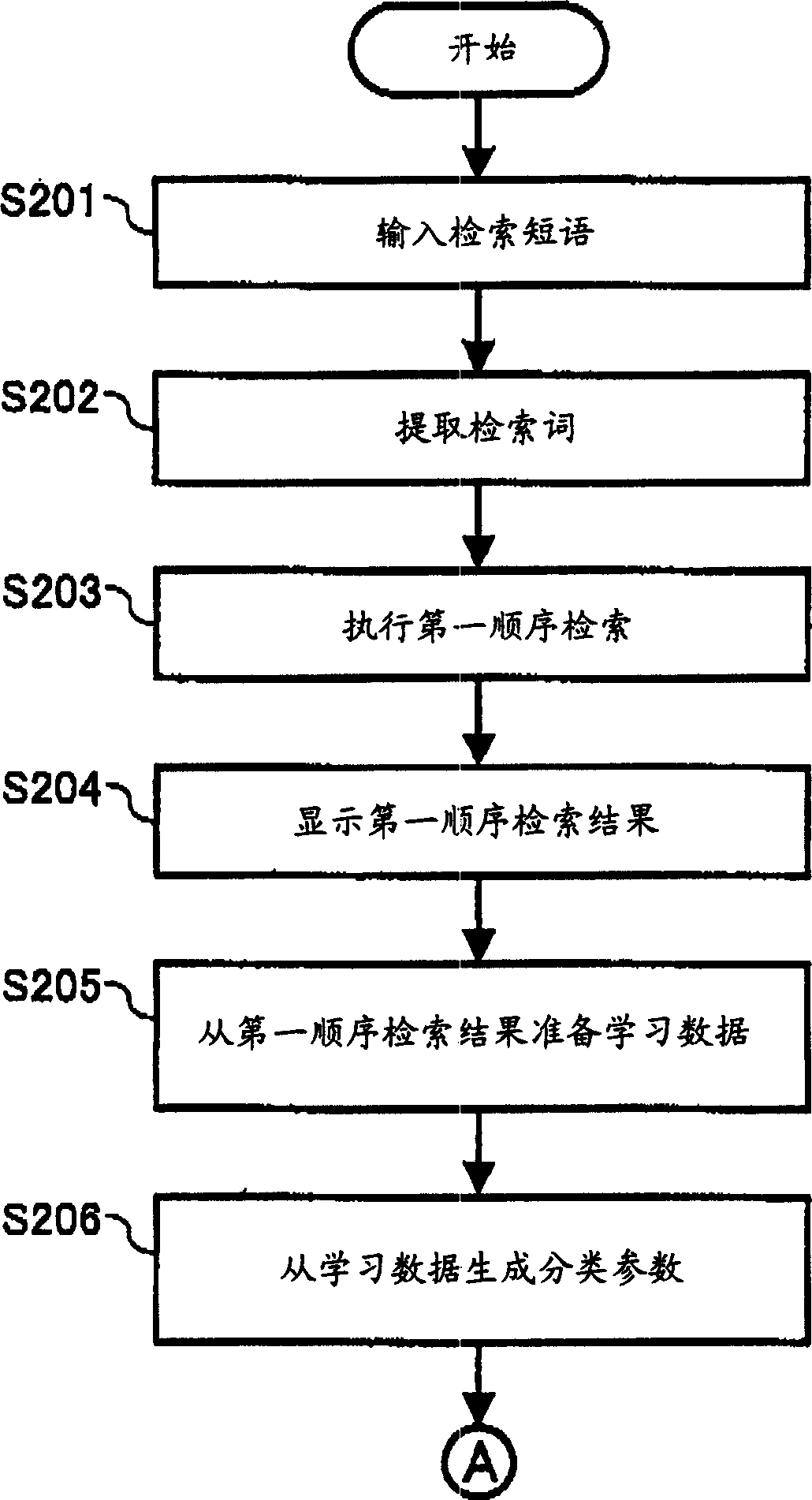
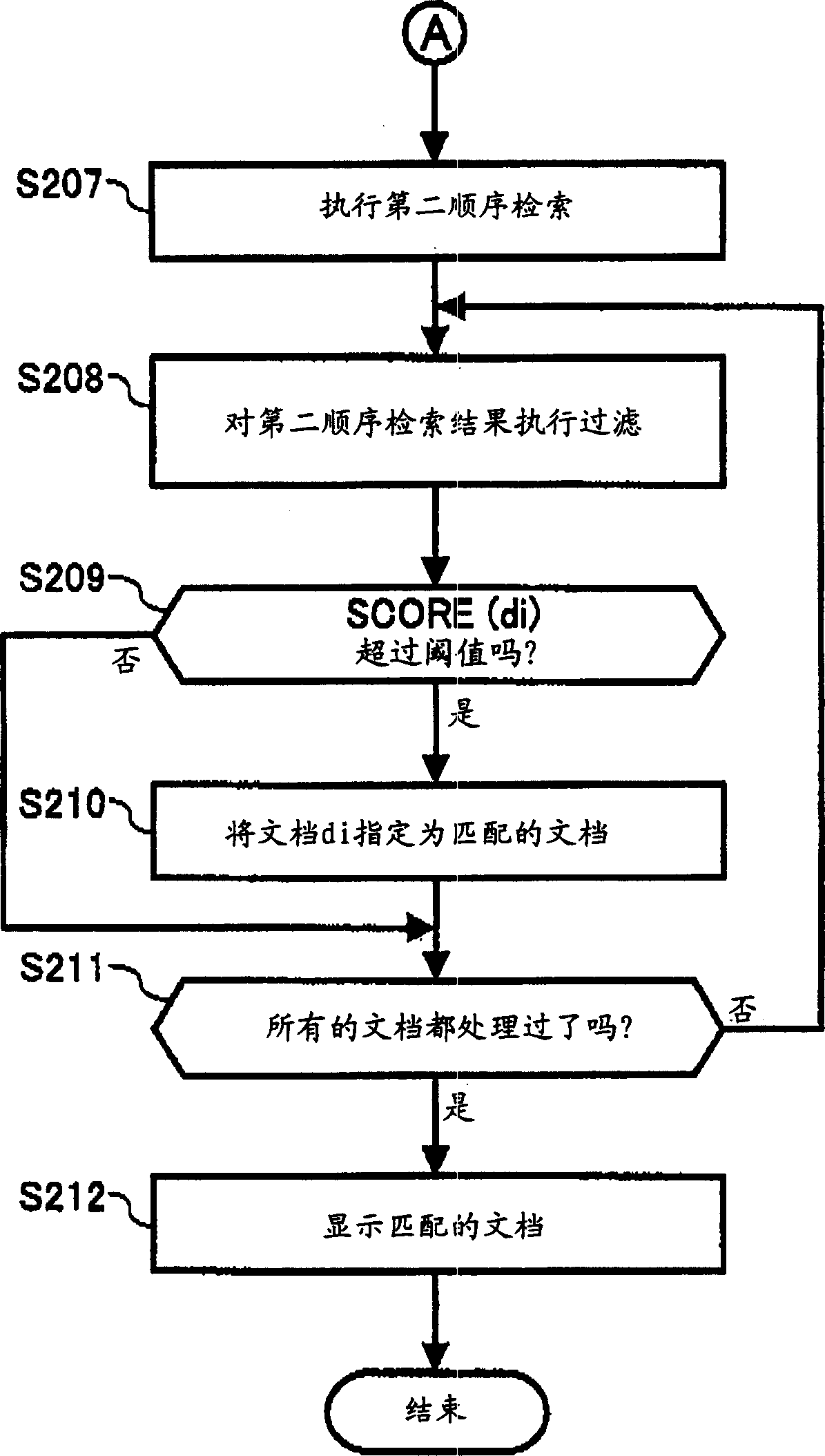
InactiveUS20050065919A1Efficient extractionDigital data information retrievalBiological modelsSearch wordsLearning data
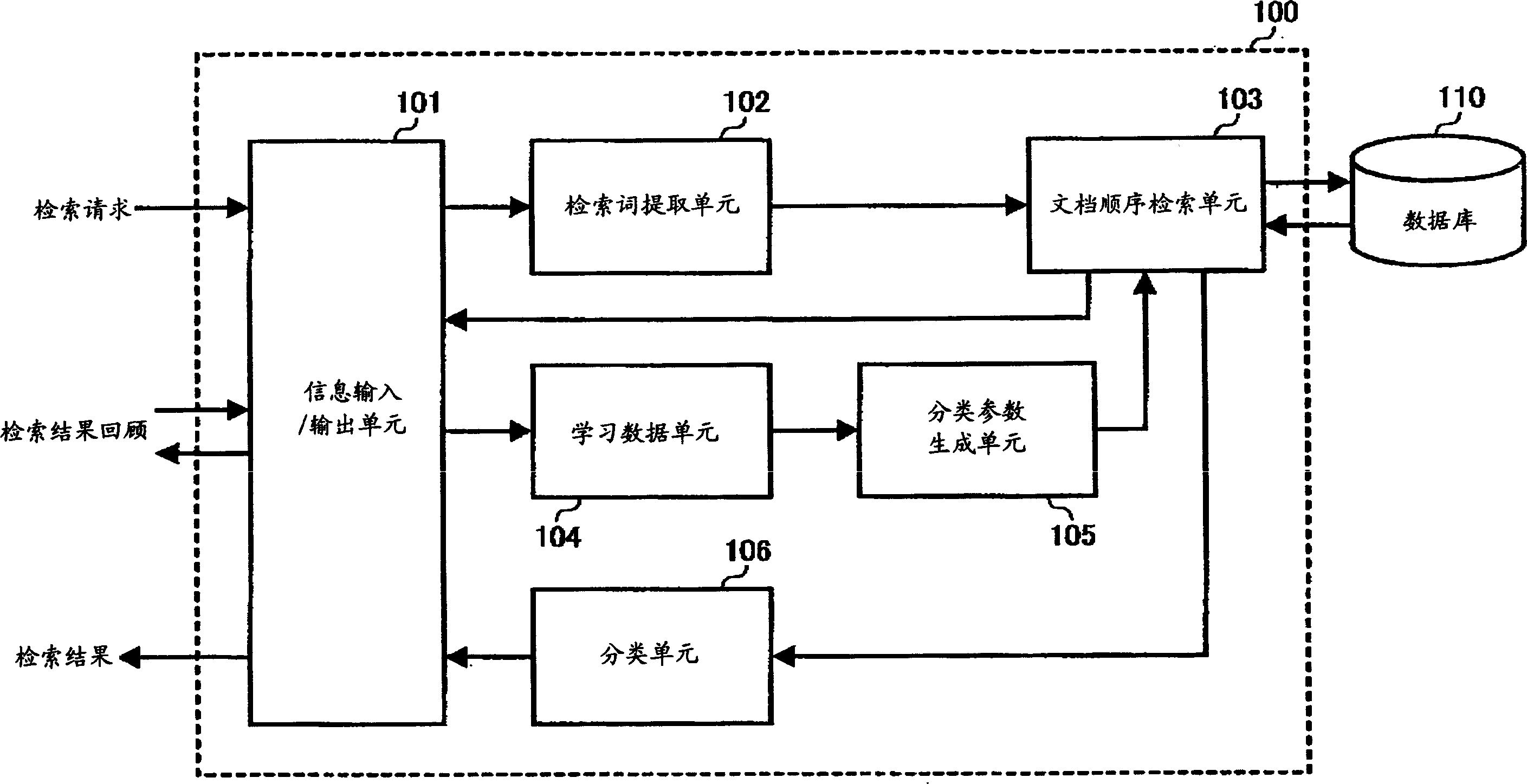
A document filtering apparatus includes an information input / output unit, a search word extraction unit, a first ranking search unit, a learning data unit, a classifying parameter generation unit, a second ranking search unit, and a classifying unit. The information input / output unit inputs phrasal information, and outputs search result information. The search word extraction unit extracts a search word from the phrasal information. The first ranking search unit searches a document having the search word from a database, and outputs a first ranking search result. The learning data unit prepares learning data from the first ranking search result. The classifying parameter generation unit generates a classifying parameter from the learning data. The second ranking search unit searches a document having a word corresponding to the classifying parameter from the database. The classifying unit extracts a document matching to a searcher's intention, and outputs the document as a second ranking search result.
Owner:RICOH KK
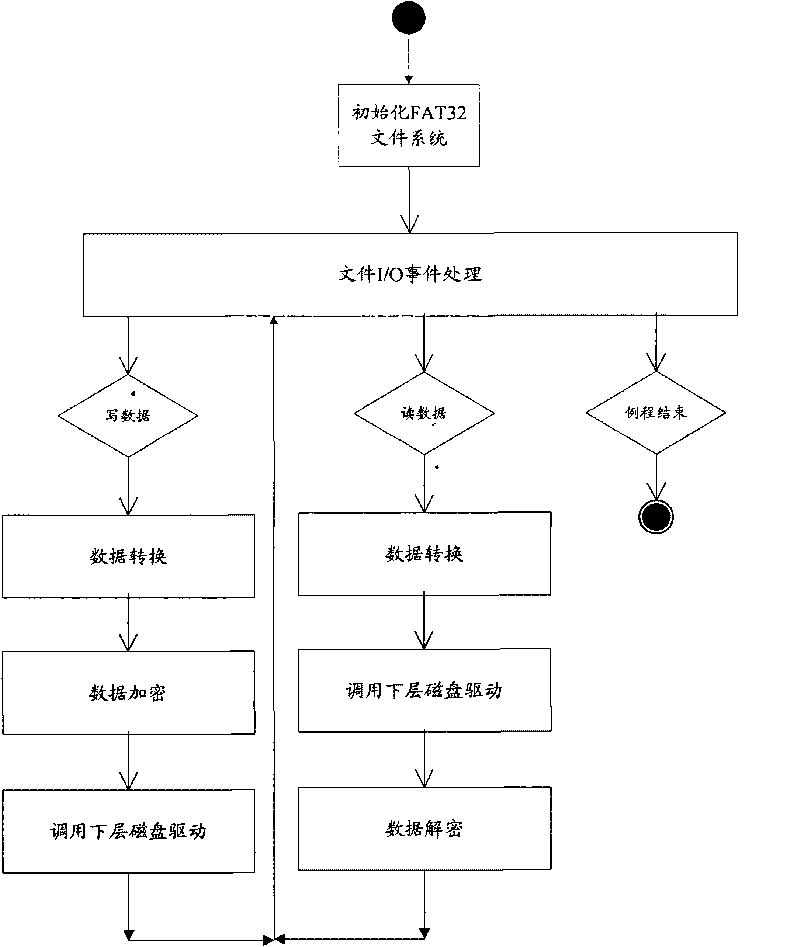
System and method for protecting virtual disk files
InactiveCN101763225AAchieve securityNo destructionInput/output to record carriersUnauthorized memory use protectionFile systemDocument filtering
The invention discloses a system and a method for protecting virtual disk files, relates to the field of network safety and solves the problem that the prior art is short of efficient protection to the virtual disc original files and the imaged virtual disk files. The system comprises a process tactical management which is arranged for allocating a process management tactic, a file filter driving module which is arranged for filtering various operation events of the virtual disc original files and the imaged virtual disk files according to the allocated process management tactic, and a virtual disk driving module which is arranged for transforming the file system of the files pointed by the filtered operation events. The method comprises the steps of: allocating a process management tactic, filtering various operation events of the virtual disc original files and the imaged virtual disk files according to the allocated process management tactic, and transforming the file system of the files pointed by the filtered operation events.
Owner:BLUEDON INFORMATION SECURITY TECH CO LTD
System and method for preventing identity theft or misuse by restricting access
A system and method for network file filtering to prevent identity theft or misuse by restricting access to files likely to contain sensitive data is disclosed. The file filtering process includes scanning at least one data file for density of a selected pattern. Files identified as containing the selected pattern may be further analyzed to determine the likelihood of the presence of sensitive information. The process may also include restricting access to files that are identified as likely to contain sensitive information.
Owner:JPMORGAN CHASE BANK NA
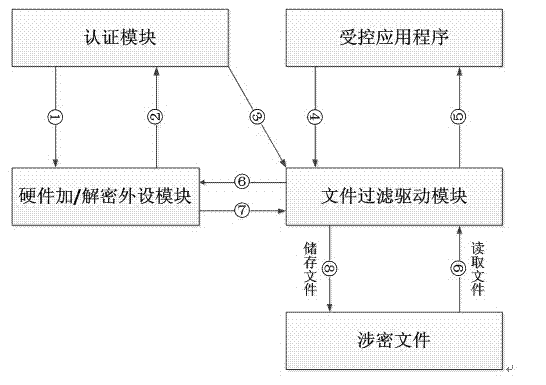
Method and system for file protection
The invention discloses a method and a system for file protection. The system for file protection comprises an authentication module, hardware encryption and decryption peripheral modules, a file filter driving module and a file encryption certificate. The hardware encryption and decryption peripheral modules are connected with a computer through electrical signals, and the file encryption certificate is issued to safety storage space of a hardware encryption peripheral module by legal means. The method and the system for file protection are characterized in that secret files are encrypted forcedly, an encryption key is stored in the hardware encryption peripheral module, encryption is realized by means of hardware in an encryption process, the files are transparently encrypted or decrypted automatically after passing authentication, and no plaintext is remained in disks assuredly, an encryption algorithm is safe, and users can use the files normally after the authentication is passed.
Owner:深圳市紫色力腾科技发展有限公司
File security active protection method based on double-drive linkage
InactiveCN102567659ASolve the damageSolve the stealDigital data protectionTransport Driver InterfaceFile system
A file security active protection method based on double-drive linkage specially includes steps of: installing drives so as to enable service; loading linkage drives through service management items; reading preset file safety protection rules to a rule chain; giving an inlet of an intelligent resource planning (IRP) processing routine function to a Driver Object; filling a Fast input / output (I / O) processing routine; leading a file filtering drive to normally send the routine and monitor cache; building a system thread, obtaining transmission control protocol / internet protocol (TCP / IP) device objects, then starting a network drive comprising a transport driver interface (TDI) layer and a network driver interface standard (NDIS) layer, and performing monitoring action for operating files through network processes; and leading the file filtering drive to filter received IRP according to the rule chain and perform IRP-level monitoring on user action protected by the files. The file security protection technology based on kernel mode file system drive and network drive linkage effectively solves problems of file damage and file stealing caused by malicious file operation, network attack activities and Trojan virus.
Owner:HENAN GONGXING INFORMATION TECH
Universal digital rights protection method under Windows platform
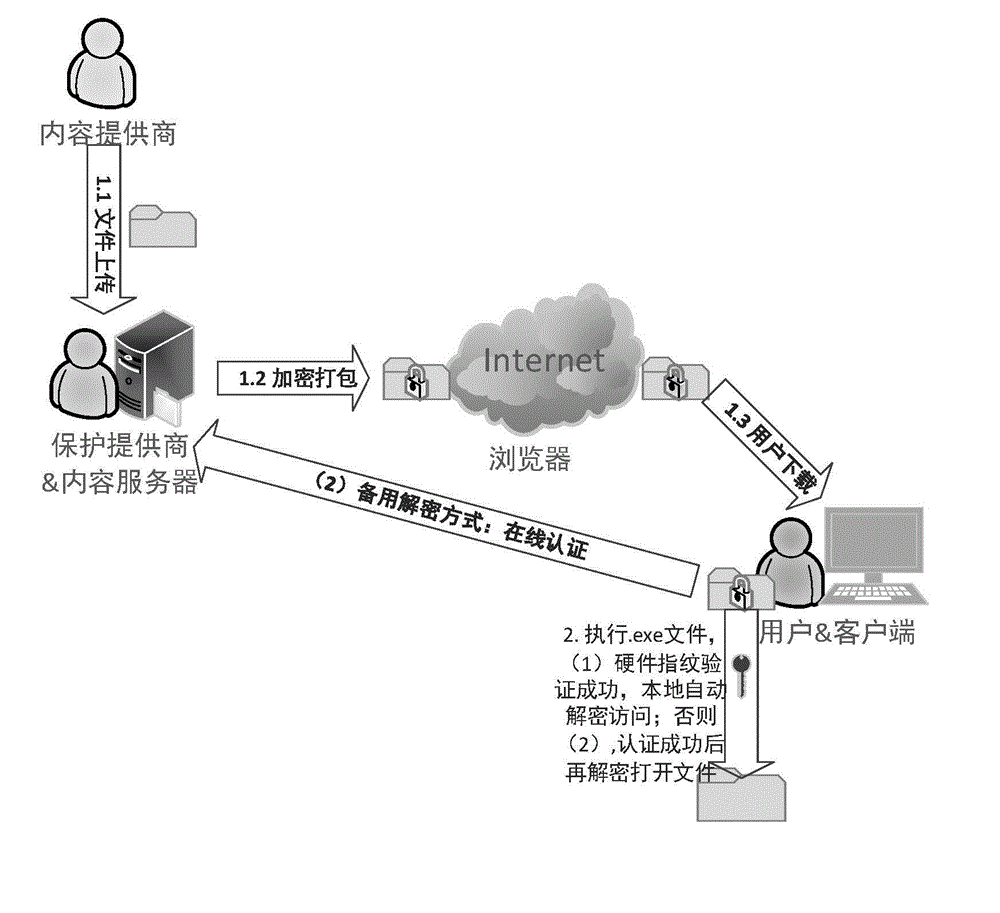
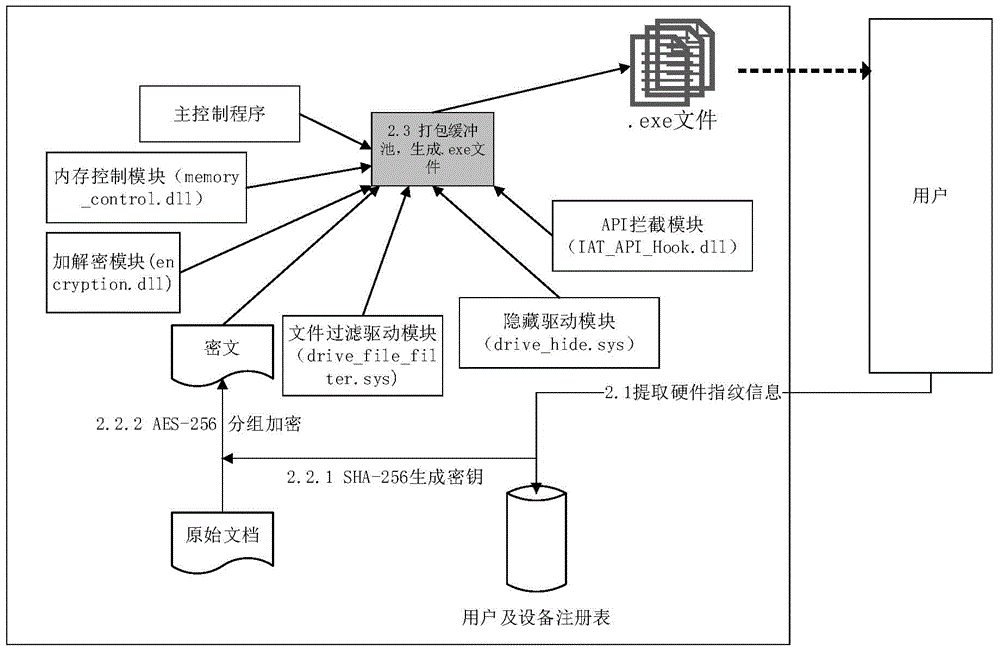
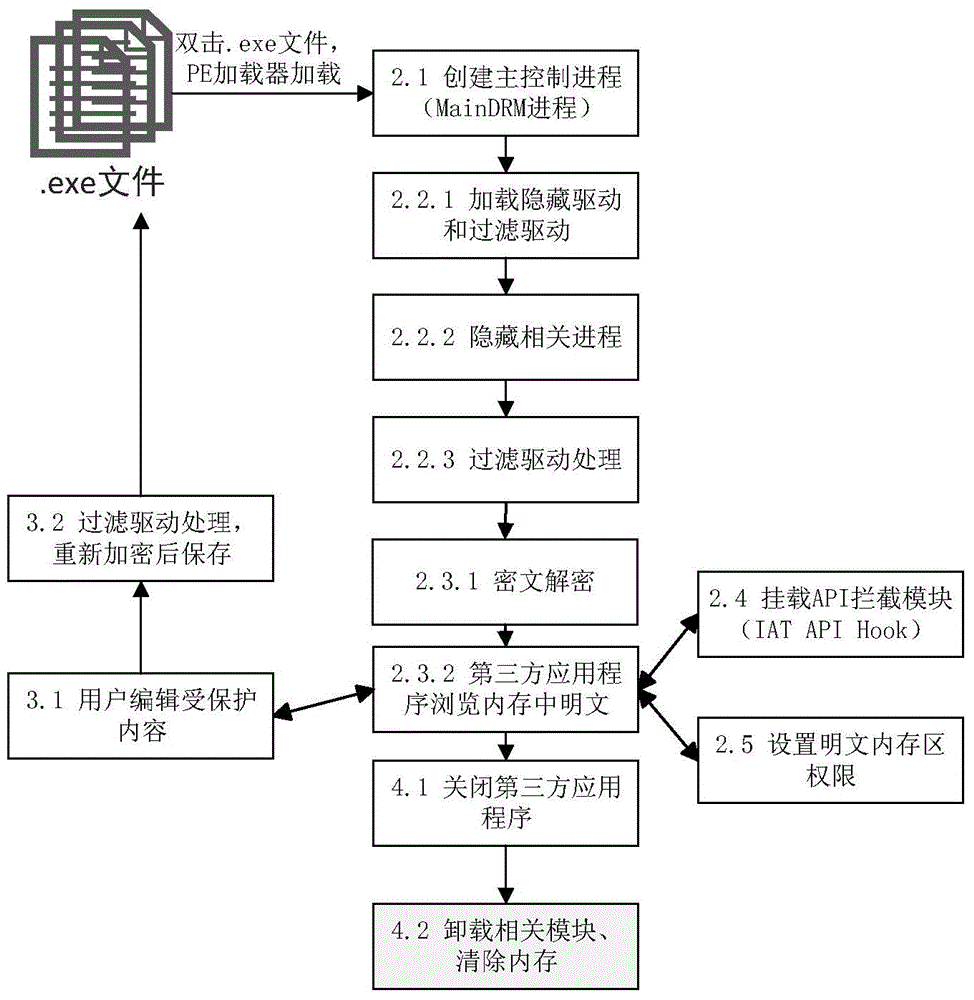
InactiveCN104834835AImprove protectionSelf-satisfactionProgram/content distribution protectionComputer hardwarePlaintext
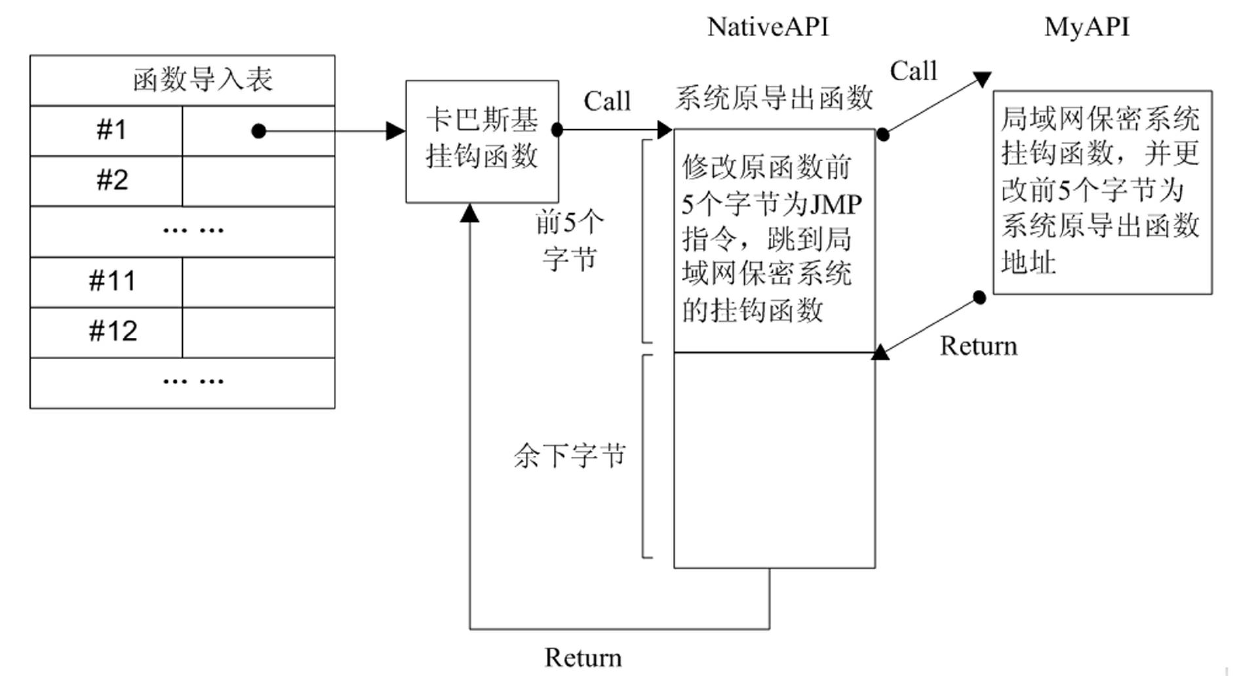
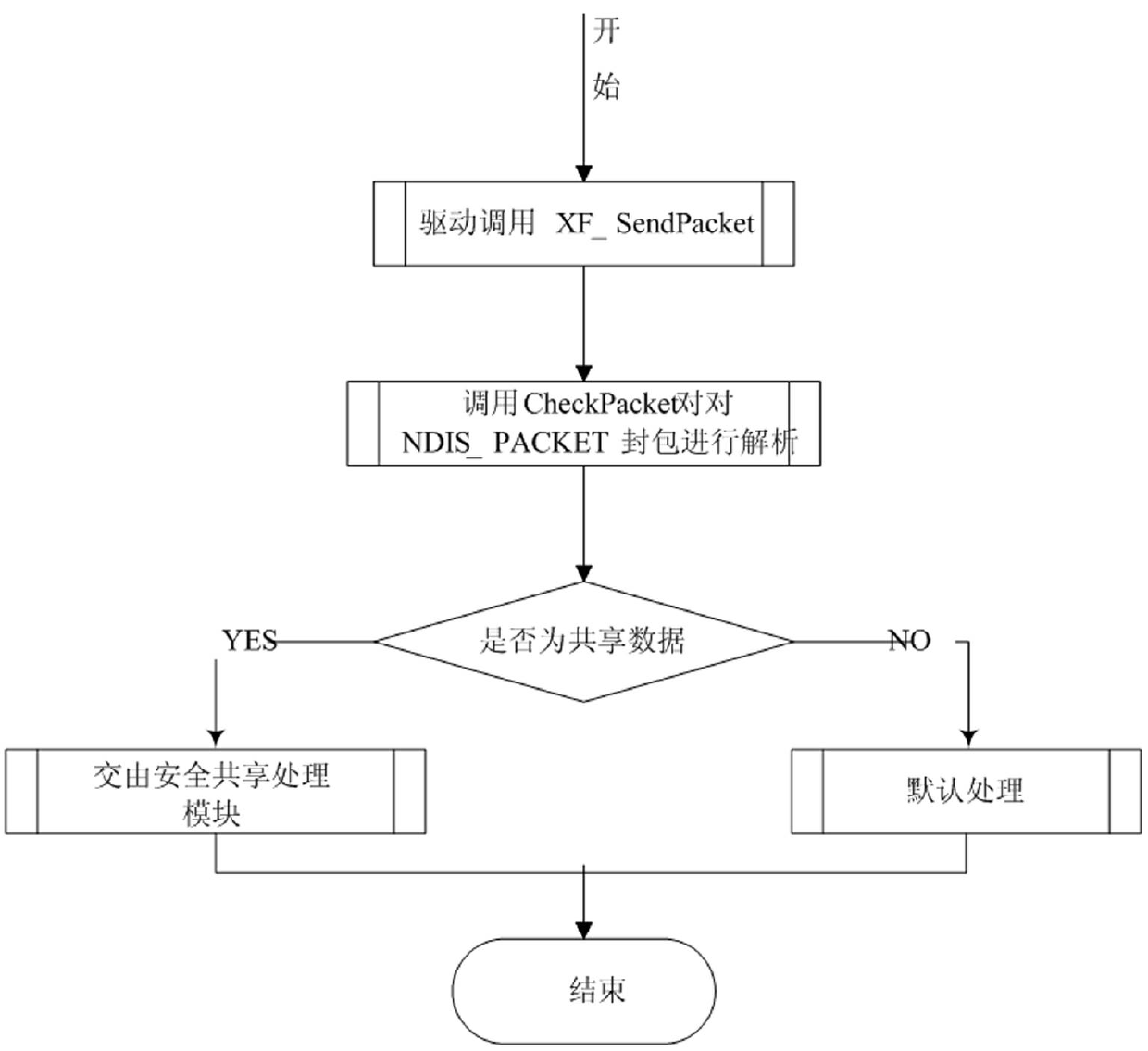
The invention discloses a universal digital rights protection method under a Windows platform; The method disclosed by the invention, through hardware fingerprint verification, can realize locally and automatically decrypting and authorizing to use a protected file; when the hardware verification is not passed, an online authentication way is further provided to meet parts of autonomies of a user, such as multi-equipment sharing, hardware change and the like; on I / O intercept processing of the file, file filtering and driving on an inner nuclear layer are adopted and are cooperatively used with an IAT (import address table) API (application program interface) Hook technology on an application layer; when the inner nuclear layer intercepts a read-write content of the file, any file read-write detail on the application layer can be neglected, thereby enabling the method more accurate and efficient; the IAT API HOOK is closely linked with a specific application program, so in relative to the monitoring that is realized by a keypad mouse hook of the application layer, the method is more targeted to carry out monitoring and limiting on file operations such as copy, paste, file save as and the like on the application layer; in addition, by the method of file filtering and driving, and plaintext memory area authority setting, the plaintext in a memory is protected nicely and the probability which the plaintext in the memory is leaked is greatly reduced.
Owner:WUHAN UNIV
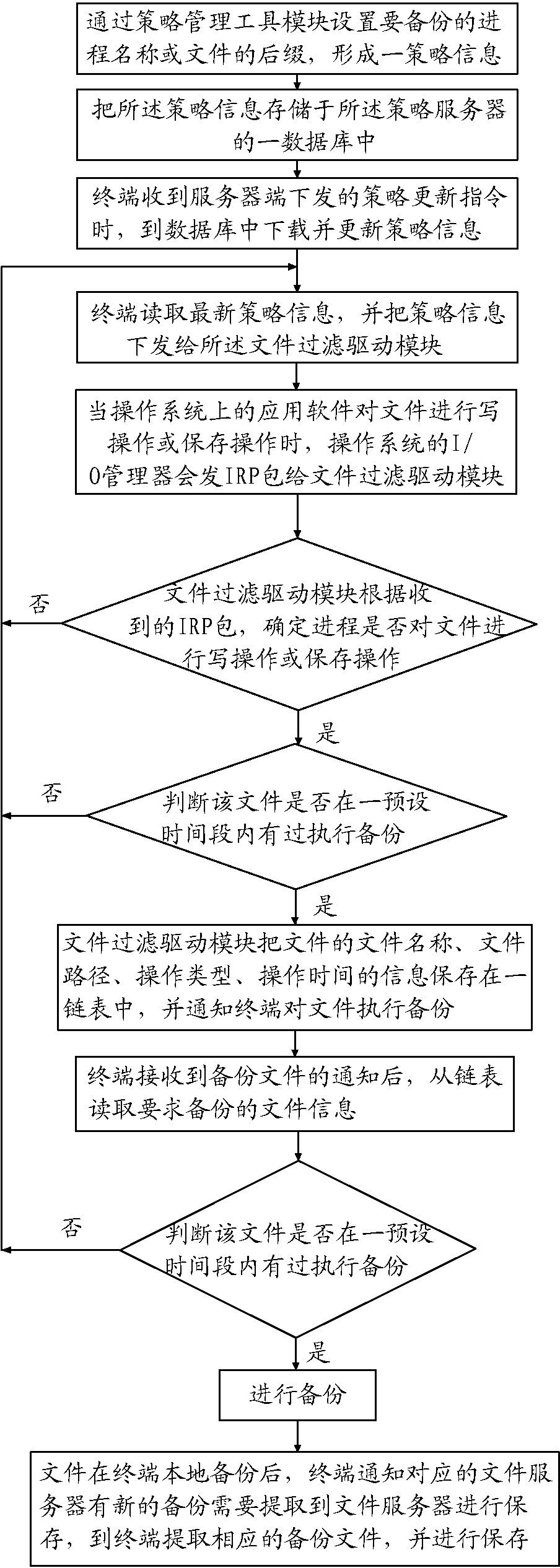
Method for file backup based on process identification file
ActiveCN103412801ABackup transparentBackup forceRedundant operation error correctionManagement toolComputer terminal
The invention provides a method for file backup based on a process identification file. The method includes the steps: setting a process name or file suffix to be backed up by a policy management tool module to form policy information; transmitting an IRP (I / O request packet) to a file filter driver module by an I / O manager when performing write operation or save operation on the file by application software, determining whether to perform the write operation or save operation on the file or not by a process according to the received IRP by the file filter driver module, judging whether to back up the file or not according to the policy information, and informing a terminal of backing up the file when the file needs to be backed up; informing a corresponding file server of a new backup file needing to be extracted and saved in the file server by the terminal after the file is locally backed up in the terminal, and extracting and saving the corresponding backup file by the terminal. By the method, the file with a certain process or type can be backed up, and local backup can be effectively executed when a client side is disconnected from a server side, so that the pressure of the server is reduced.
Owner:厦门天锐科技股份有限公司
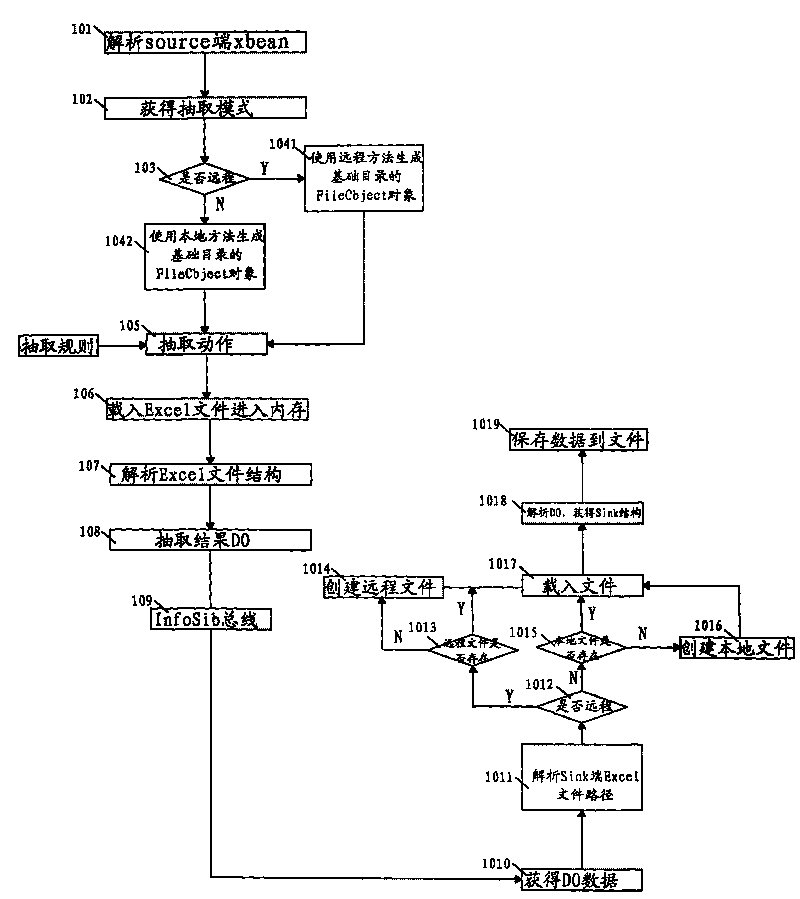
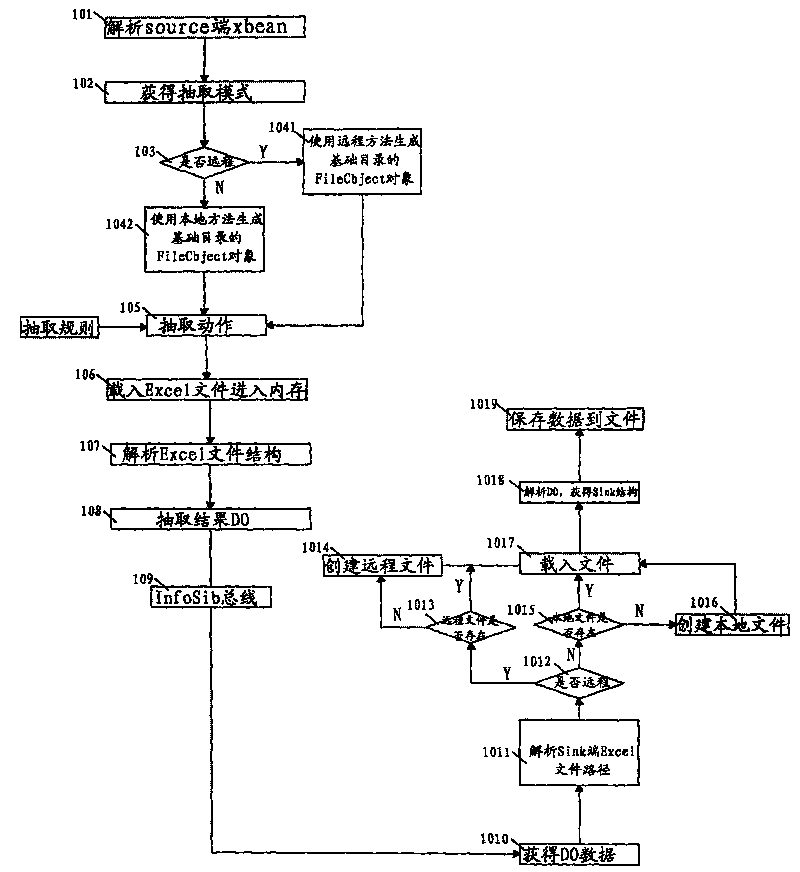
ETL realization method for incremental data of Excel file
ActiveCN101697126AIncrease flexibilityEasy to operateSpecific program execution arrangementsOpen sourceDatabase
The invention discloses an ETL realization method for incremental data of an Excel file, which comprises the following steps of: based on InfoSib-ExcelSource and InfoSib-ExcelSink components on an open source JavaApi, extracting file increment and whole volume of file content; and supporting the extraction of the file content of a specified part; supporting the extraction of a common file and a file in a special format separately; supporting file filtering, Sheet form filtering and data column filtering; supporting an Excel to an Excel, the Excel to database, and the database to the Excel; supporting long-distance Excel data extraction; supporting a repeated operations of one-time configuration; and supporting three extraction patterns, namely a real-time extraction pattern, a timely extraction pattern and a triggering extraction pattern.
Owner:山东中创软件商用中间件股份有限公司
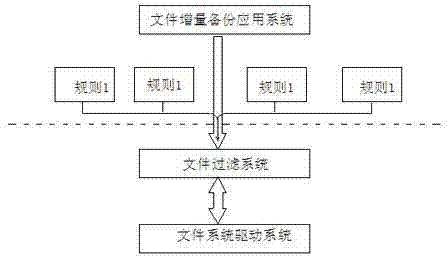
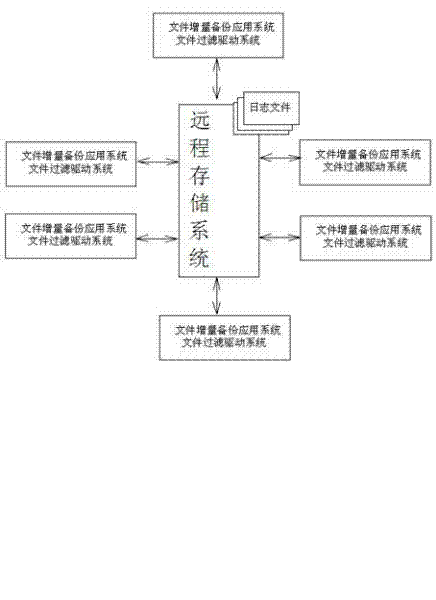
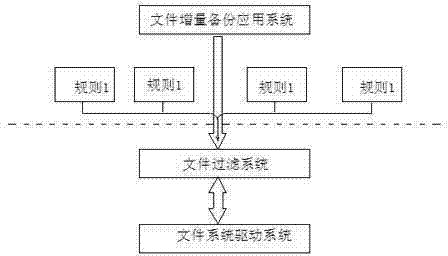
Fast and reliable file incremental backup method
InactiveCN102521075ARecord in timeEnsure incremental backupsInput/output to record carriersRedundant operation error correctionFile systemIncremental backup
The invention provides a fast and reliable file incremental backup method. A system comprises a file incremental backup application system, a file filter driving system and a long-distance storage system. The file incremental backup application system is a main carrier for achieving a strategy, is responsible for scheduling and making the file filter driving system and the long-distance storage system coordinate with each other and comprises rule setting and strategy achieving, the file filter driving system is a core achieving module of the method and is responsible for intercepting generation of change information and log files of files in a file system, and the long-distance storage system is responsible for storing log file information of file changes.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
System and Method for Preventing Identity Theft or Misuse by Restricting Access
A system and method for network file filtering to prevent identity theft or misuse by restricting access to files likely to contain sensitive data is disclosed. The file filtering process includes scanning at least one data file for density of a selected pattern. Files identified as containing the selected pattern may be further analyzed to determine the likelihood of the presence of sensitive information. The process may also include restricting access to files that are identified as likely to contain sensitive information.
Owner:JPMORGAN CHASE BANK NA
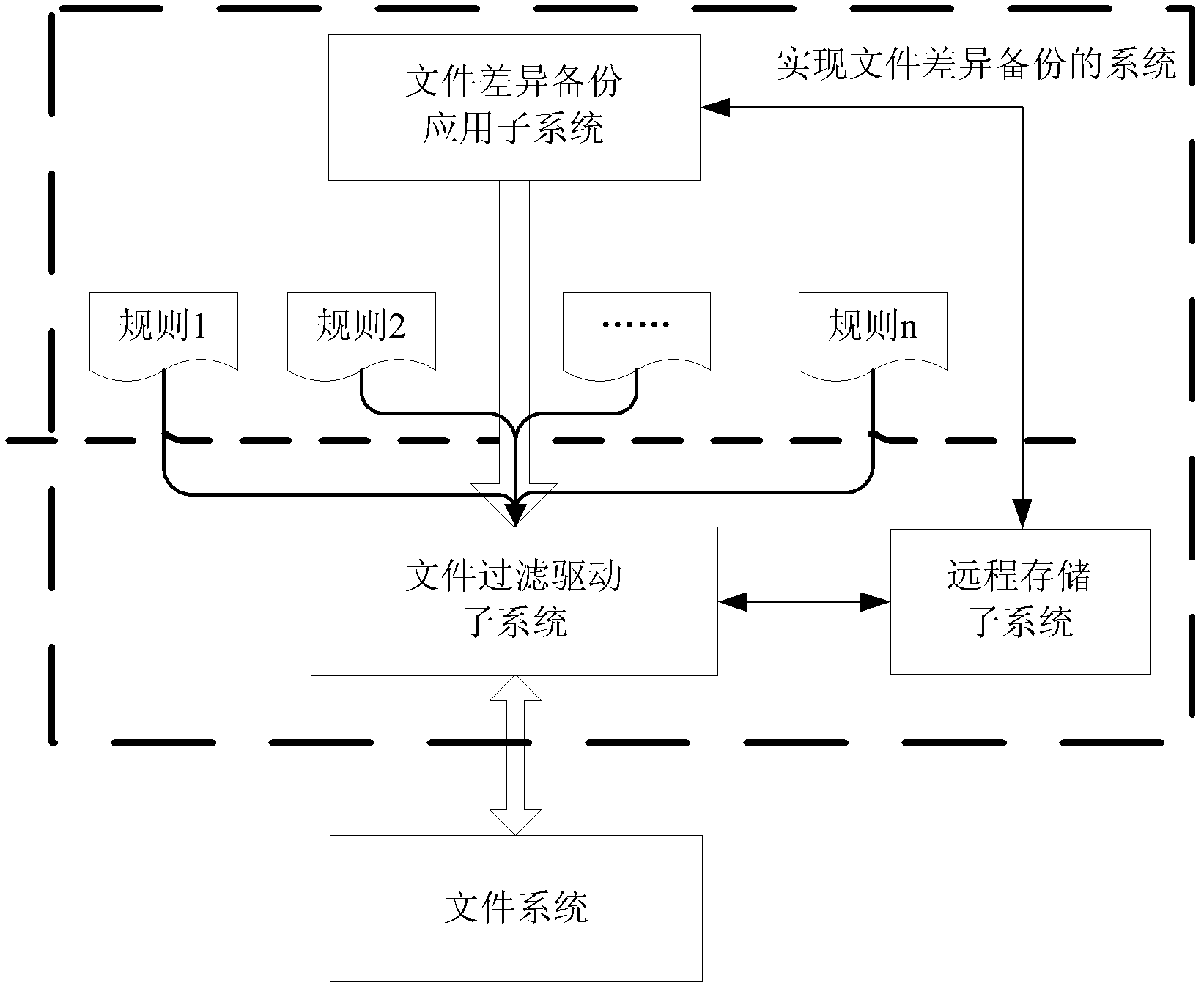
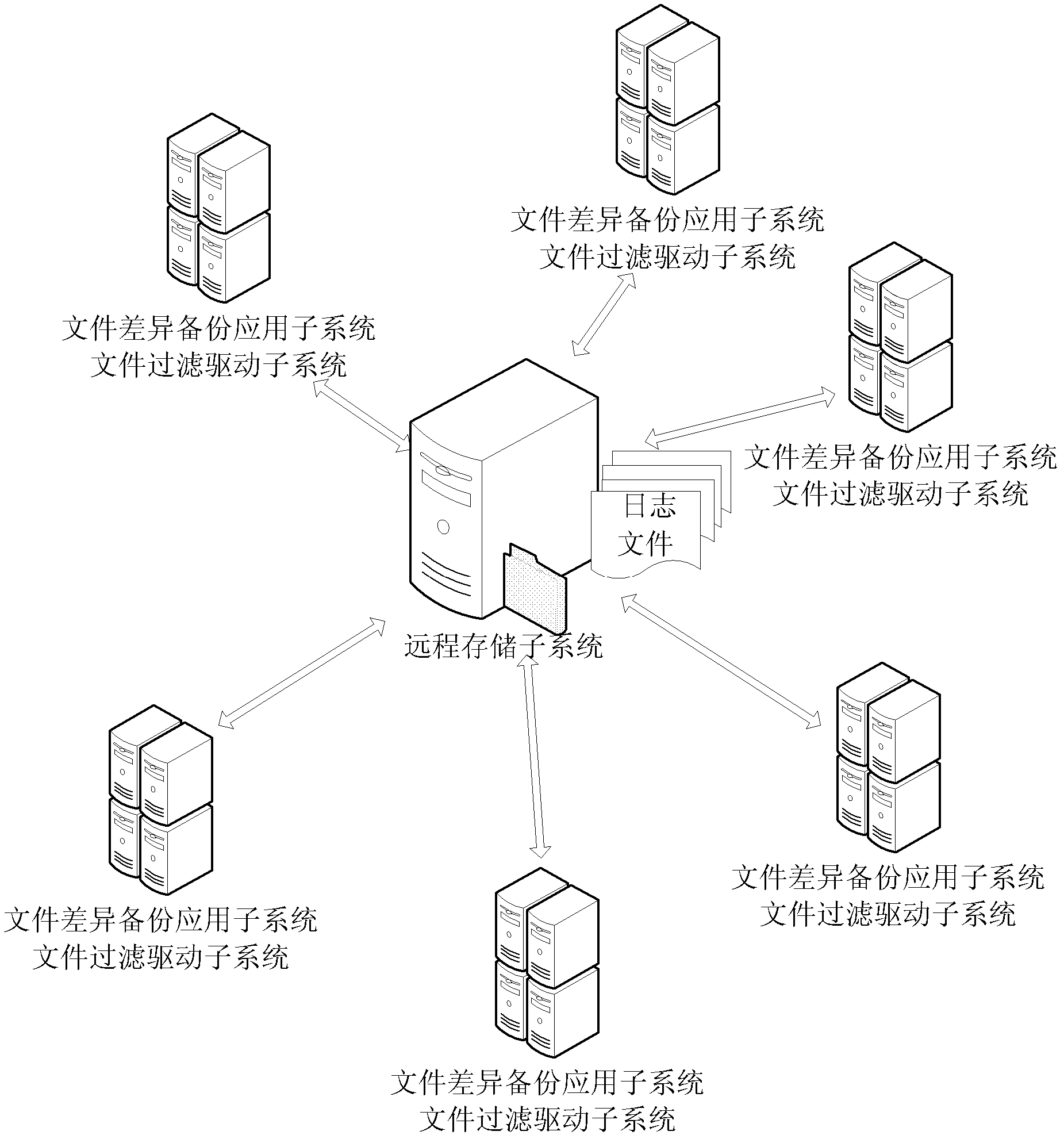
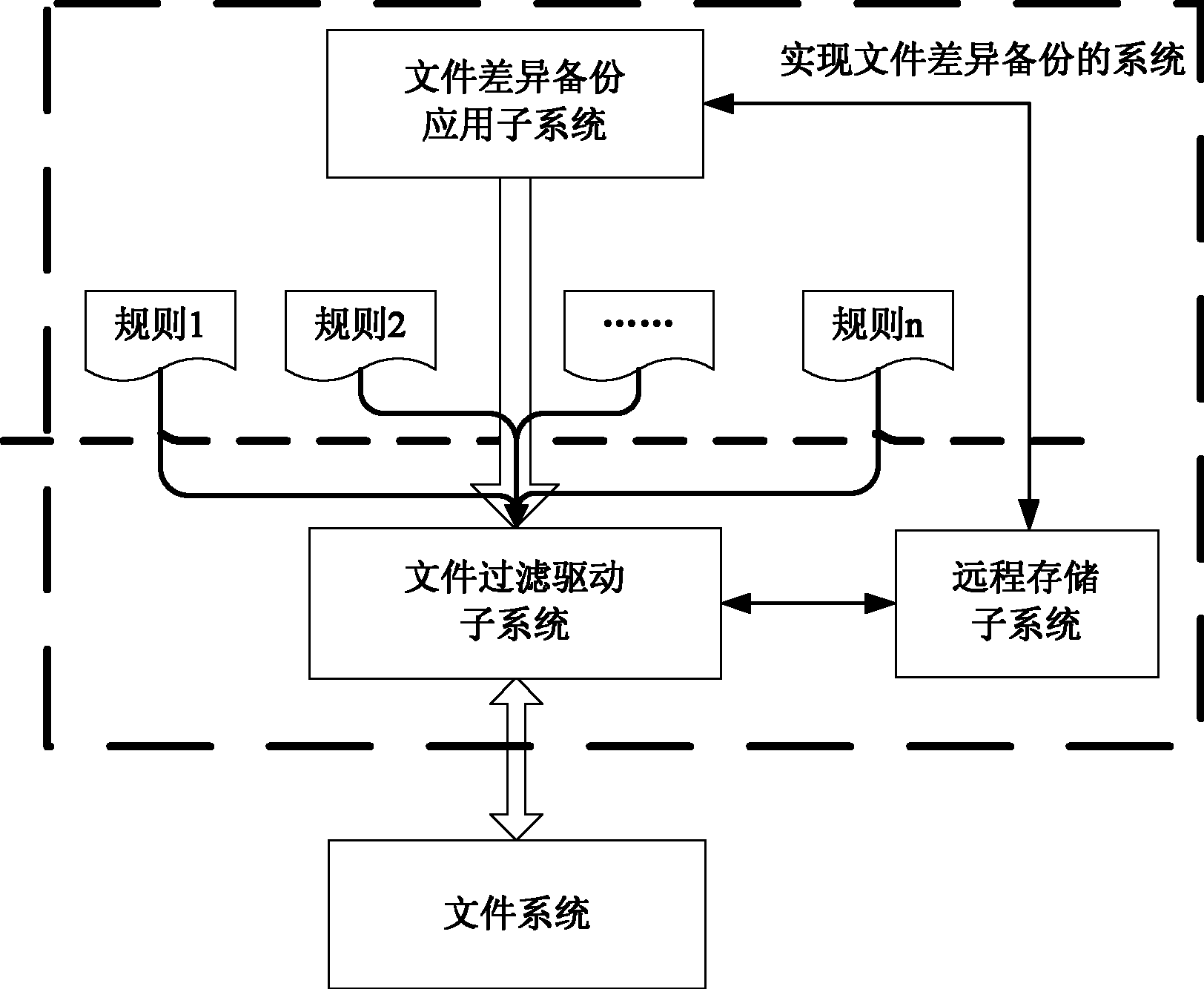
File differential backup system and method
ActiveCN102354293AReliable recoveryRedundant operation error correctionFile systemDocument filtering
The invention discloses a file differential backup system and method. The system comprises a file differential backup application subsystem, a file filtering driving subsystem and a remote storage subsystem, wherein the file differential backup application subsystem outputs a preset file differential backup strategy to the file filtering driving subsystem, and performs file differential backup according to a log file generated by the file filtering driving subsystem; the file filtering driving subsystem intercepts the change information of a file in a file system according to the input file differential backup strategy, locally generates and / or stores a log file and simultaneously transmits the log file to the remote storage subsystem; and the remote storage subsystem stores the log file transmitted by the filtering driving subsystem. By the system and the method, the log file can be retrieved from the remote storage subsystem when the local log file is damaged or lost, thereby rapidly and reliably realizing recovery to a current file for a full backup file.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
File protection system and implement method thereof
InactiveCN103390135AAutomate processingDo not change operating habitsDigital data protectionInternal/peripheral component protectionComputer hardwareComing out
The invention provides a file protection system and an implement method thereof. The file protection system structurally comprises an upper layer user interface application program, an I / O manager, a file filter driver and independent encryption hardware, wherein the upper layer user interface application program is configured to realize encryption policy setting and other man-machine interaction; the I / O manager is configured to receive request information from the upper layer user interface application program and to distribute data in a request packet form; the file filter driver is configured to intercept request packets from the I / O manager, judge the data in the request packets and transmit eligible to-be-processed data; and an encryption / decryption algorithm and a secret key are stored in the independent encryption hardware and act on the file filter driver, and the independent encryption hardware is configured to receive and process the to-be-processed data from the file filter driver. According to the file protection system and the implement method thereof, the encryption and decryption processes are both completed in the independent encryption hardware, the secret key cannot come out of the encryption hardware in the whole encryption / decryption process, and the safety of files is improved.
Owner:BEIJING SUCIZ SCI & TECH DEV
Privilege control method of encryption document in terminal and terminal
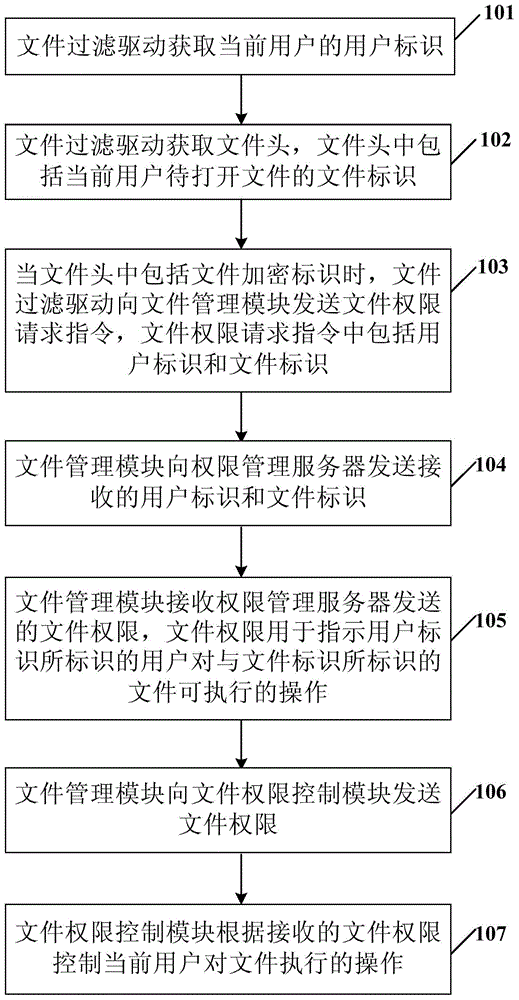
InactiveCN105787375ADigital data protectionDigital output to print unitsDocument handlingRights management
The invention provides a privilege control method of an encryption document in a terminal and the terminal. The method comprises that a file filter drive obtains the user identifier of a current user and a file header containing the file identifier of the current to-be-opened file of the user; when the file header comprises a file encryption identifier, the file filter drive sends a file privilege request instruction containing the user identifier and the file identifier to a file management module; the file management module sends received file privilege request instruction to a privilege management server, receives file privileges sent by the privilege management server and finally sends the file privileges to a file privilege control module; and the operations of the current user carried out to the file are controlled according to the file privileges, wherein the file management module sends the received file privileges sent by the privilege management server to the file privilege control module, thus enabling the privilege control module to control the privileges of the application layer needing to be carried out to the file currently by the user, and the processing demand of the user on the file is satisfied.
Owner:HUAWEI TECH CO LTD
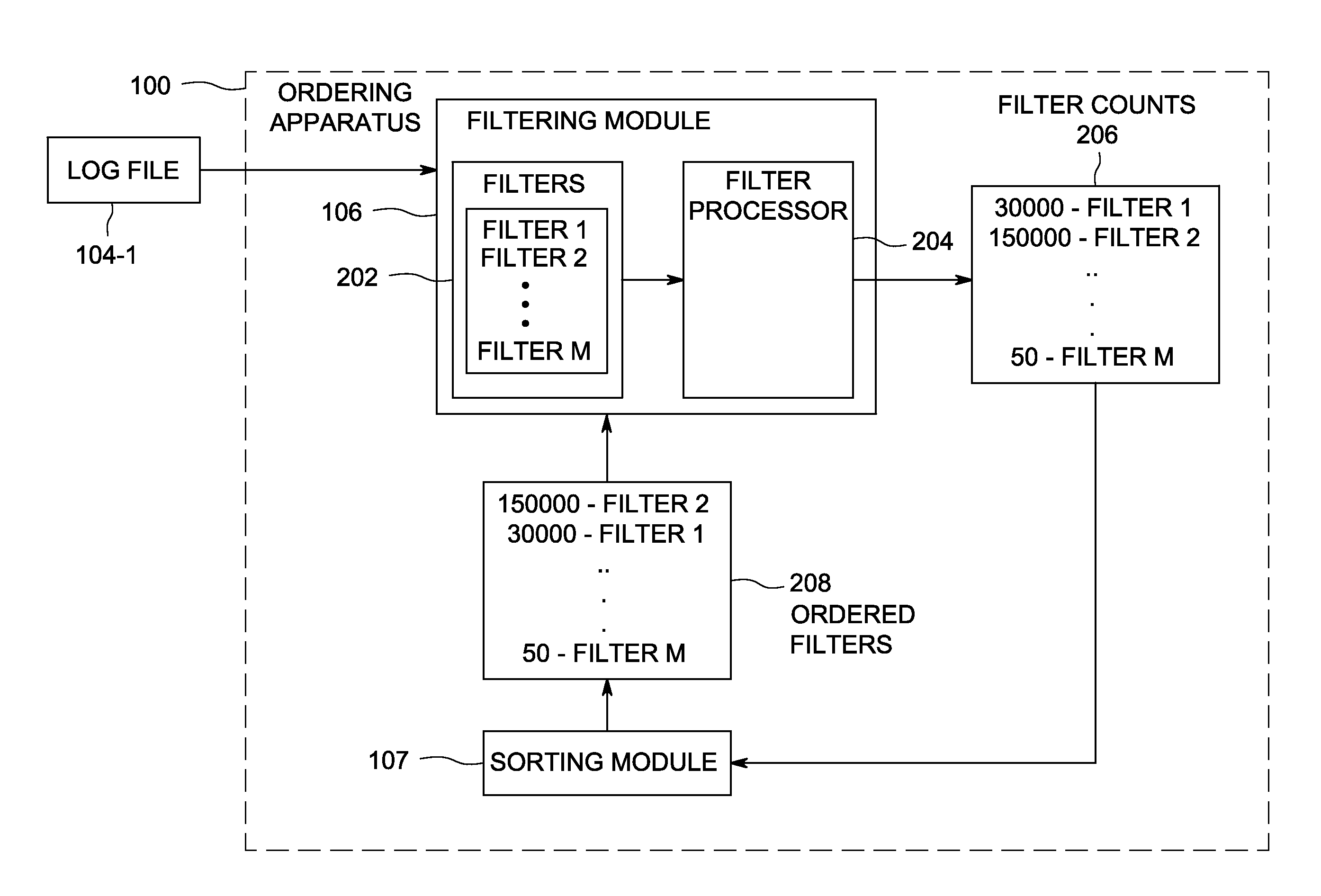
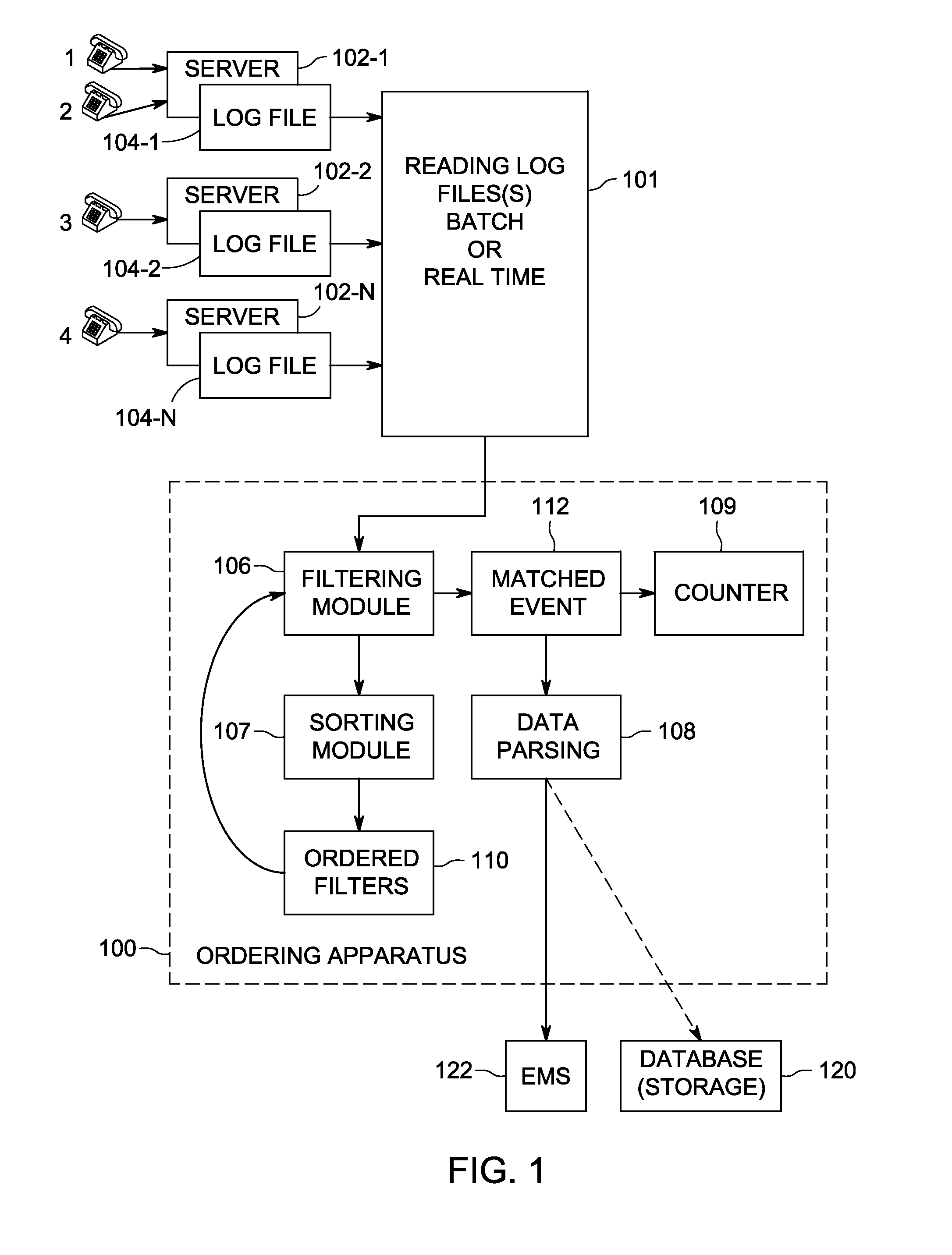
Method and apparatus for optimizing log file filtering
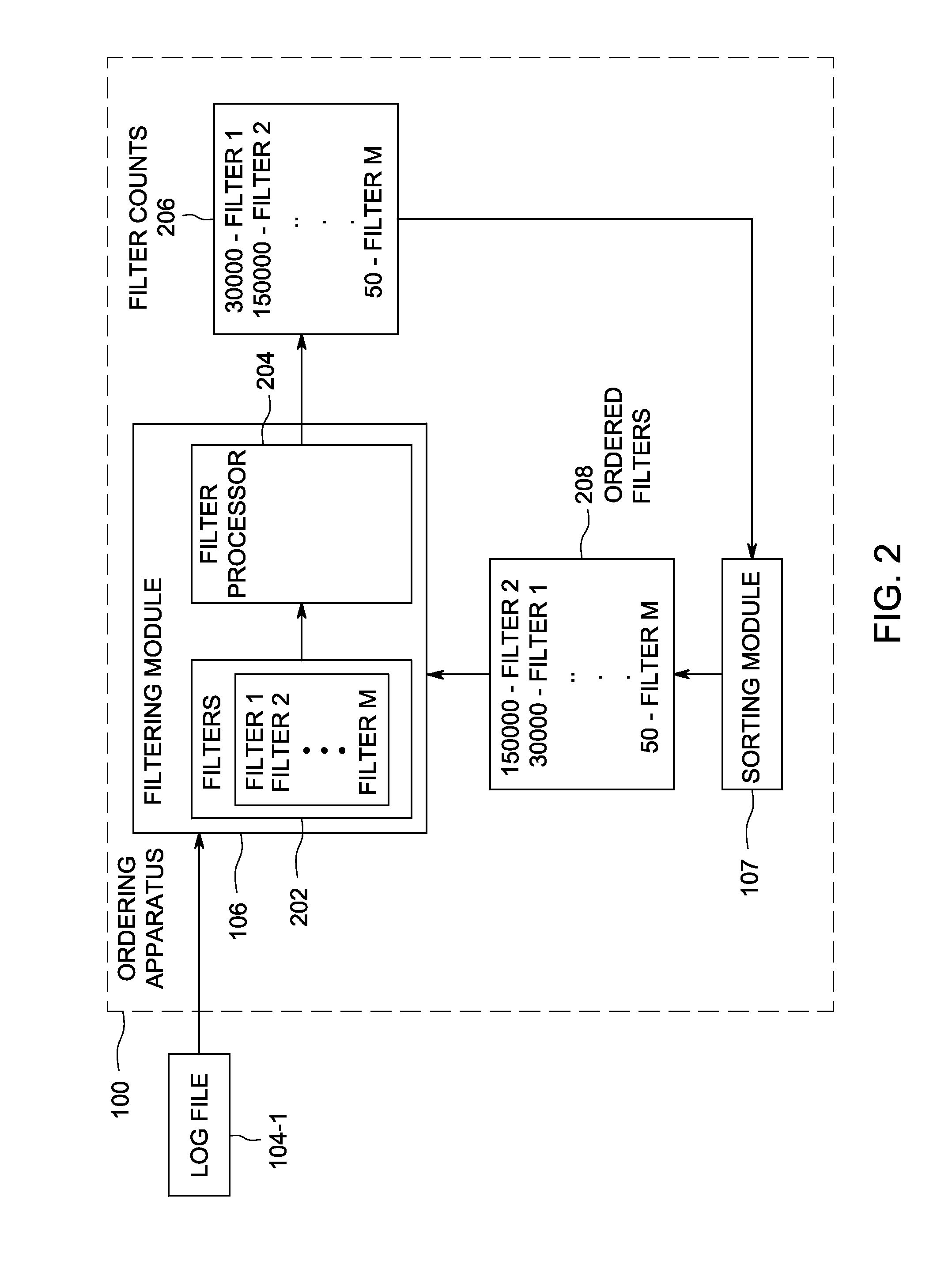
InactiveUS20140250138A1Digital data information retrievalDigital data processing detailsOrder setData mining
A method and apparatus for optimizing list filtering comprising receiving a list of items from one or more servers, matching the list of items against a set of filters, ordering the set of filters based on the frequency of matches for the set of filters for each filter in the set of filters and applying the ordered set of filters for matching on a next received list of items.
Owner:VONAGE NETWORKS LLC
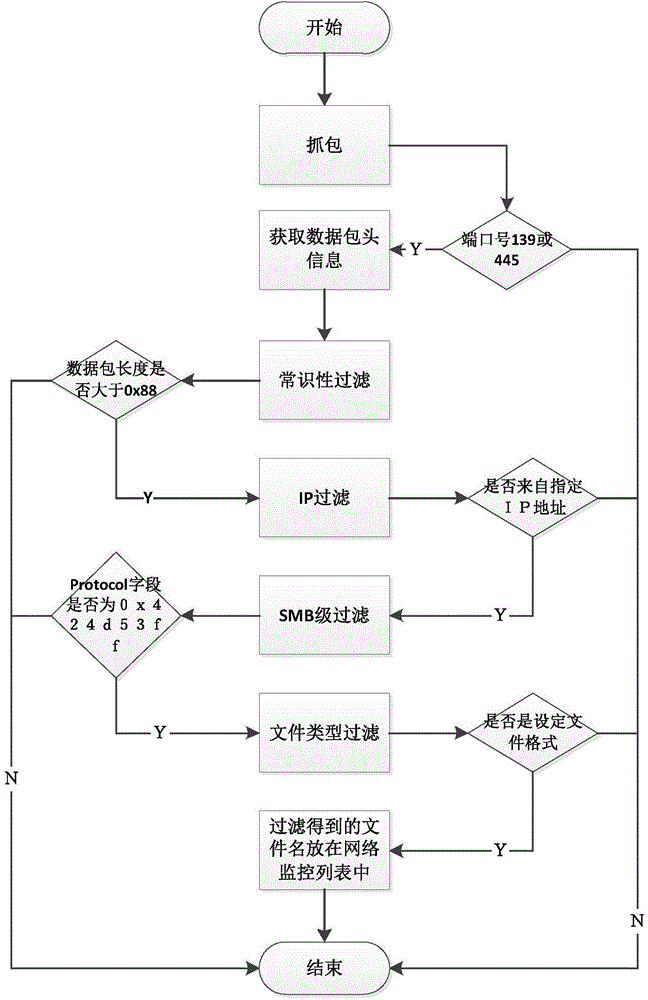
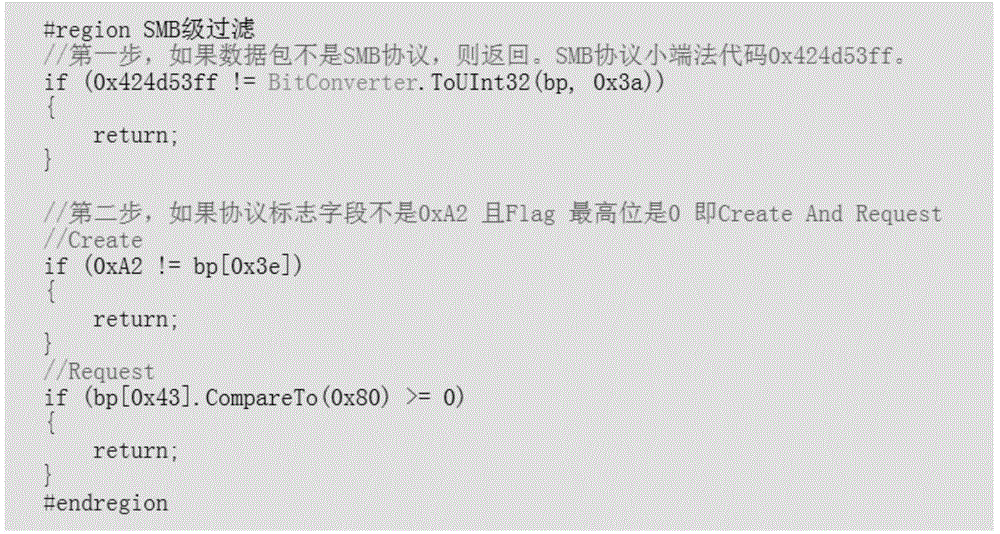
Sharing file operation filtering method based on SMB protocol
The invention relates to a method for file filtration, in particular to a sharing file operation filtering method based on the SMB protocol. The sharing file operation filtering method comprises the following steps: holding monitoring and data packet analysis on the ports (139 and 445) of a system; performing step-by-step operation of IP filtration, SMB-step filtration and file name acquisition on a captured data packet; automatically adding file types which meet user-defined monitoring rules and corresponding file names into an operation filtration monitoring list; converting a network data packet to local monitoring, continuously monitoring the progress of a local drive through the system, acquiring file creation information, and acquiring newly created file names; comparing basic information such as names and capacities of local newly created files with those of files in the monitoring list; monitoring the local progress through a resident system, and acquiring operation information of files. As the method is based on analysis filtration strategies of application layer protocol and nucleus filtration driving of an operation system, the operation is visible, hard to interfere and high in security.
Owner:HARBIN ENG UNIV
Method and device for creating invoice filtrating condition
InactiveCN101334794AAvoid the problem of very redundant processesImprove usabilityCommerceSpecial data processing applicationsUsabilityDocument filtering
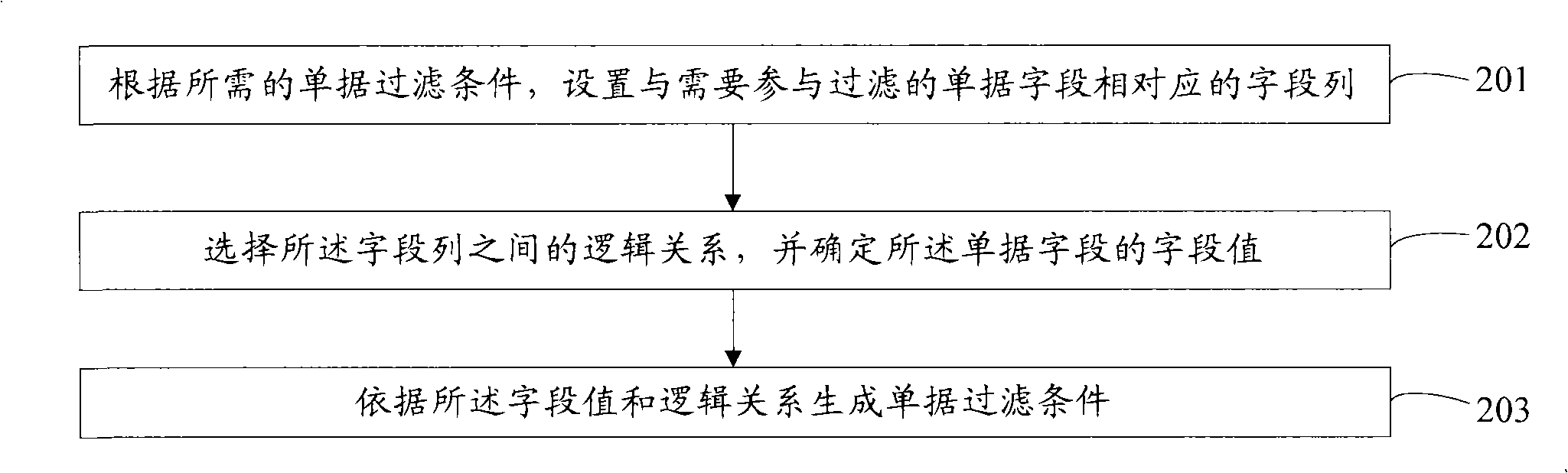
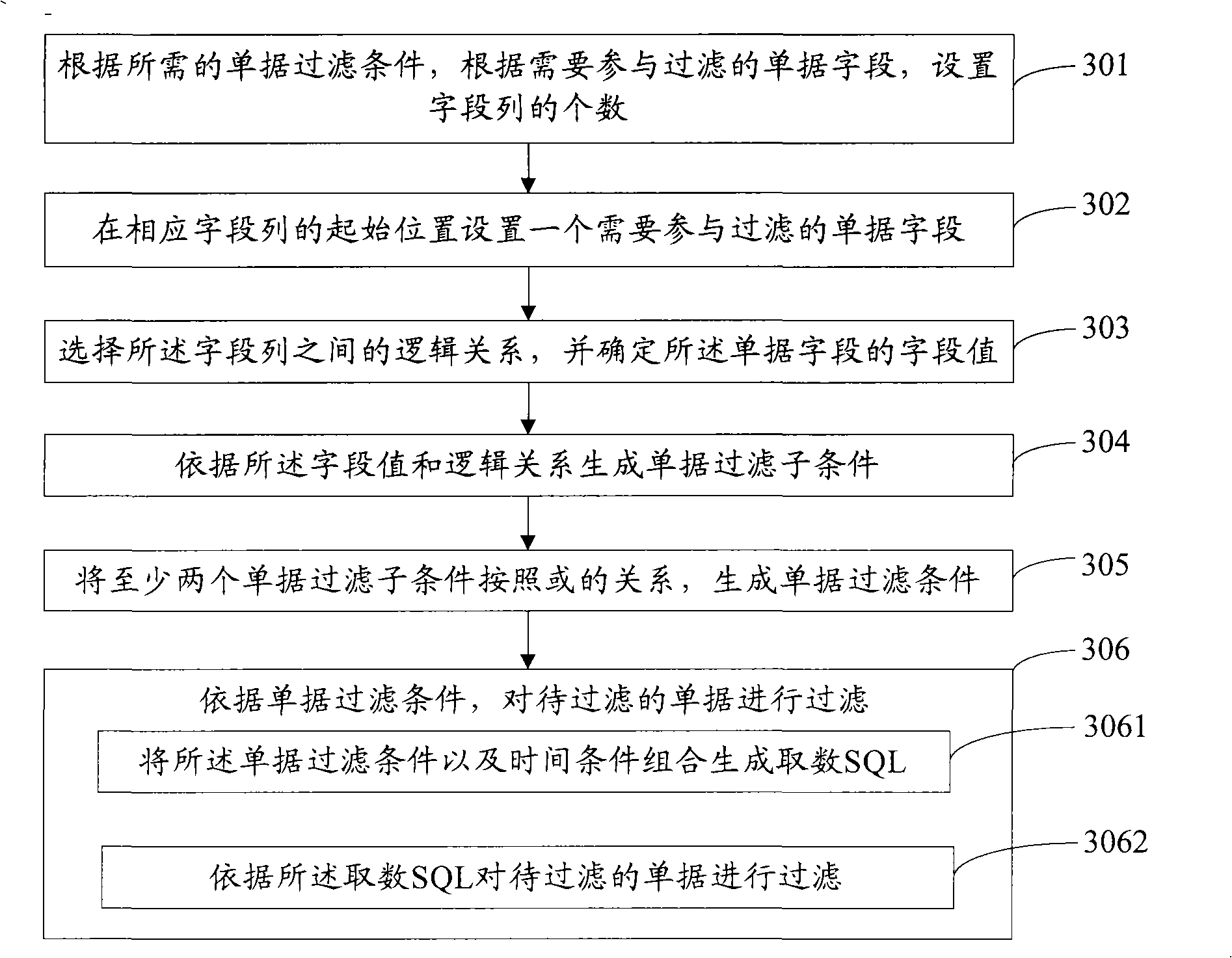
The invention provides a document filtering condition generation method including the following steps: field rows matching document fields needing to be involved in filtering are arranged according to required document filtering conditions; logic relations between the filed rows are selected and field values of the document fields are defined; the document filtering condition is generated according to the field values and the logic relations; furthermore, the documents to be filtered can be filtered according to the document filtering conditions. With the method of the invention, users can fill corresponding field value in the field row according to the filtering conditions after arranging the fields involved in filtering so as to reduce the redundancy of arranging the logic relation definitions between document fields involved in filtering and further to enhance the usability of arranging filtering conditions when the documents are filtered under a complex condition. The invention also provides an apparatus generating the document filtering conditions.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
File filtration method and system
ActiveCN105302839ALow costImprove work efficiencyTransmissionSpecial data processing applicationsFiltrationDatabase
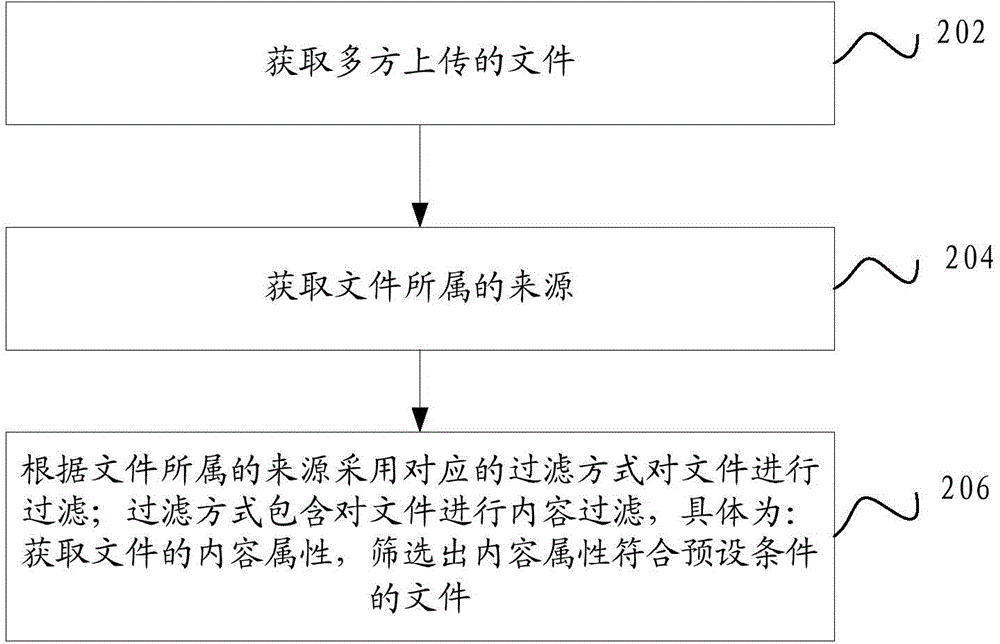
The invention discloses a file filtration method. The method comprises: obtaining files uploaded by multiple parties; obtaining sources that the files belong to; and filtering the files in a corresponding filtration mode according to the sources that the files belong to, wherein the filtration mode contains the filtration of the content of the files, specifically, content attributes of the files are obtained and the files with the content attributes meeting a preset condition are screened out. With the adoption of the method, a large amount of unqualified files are filtered out before the files are released, so that the cost for checking the files one by one is reduced and the working efficiency is improved. In addition, the invention furthermore provides a file filtration system.
Owner:TENCENT TECH (SHENZHEN) CO LTD
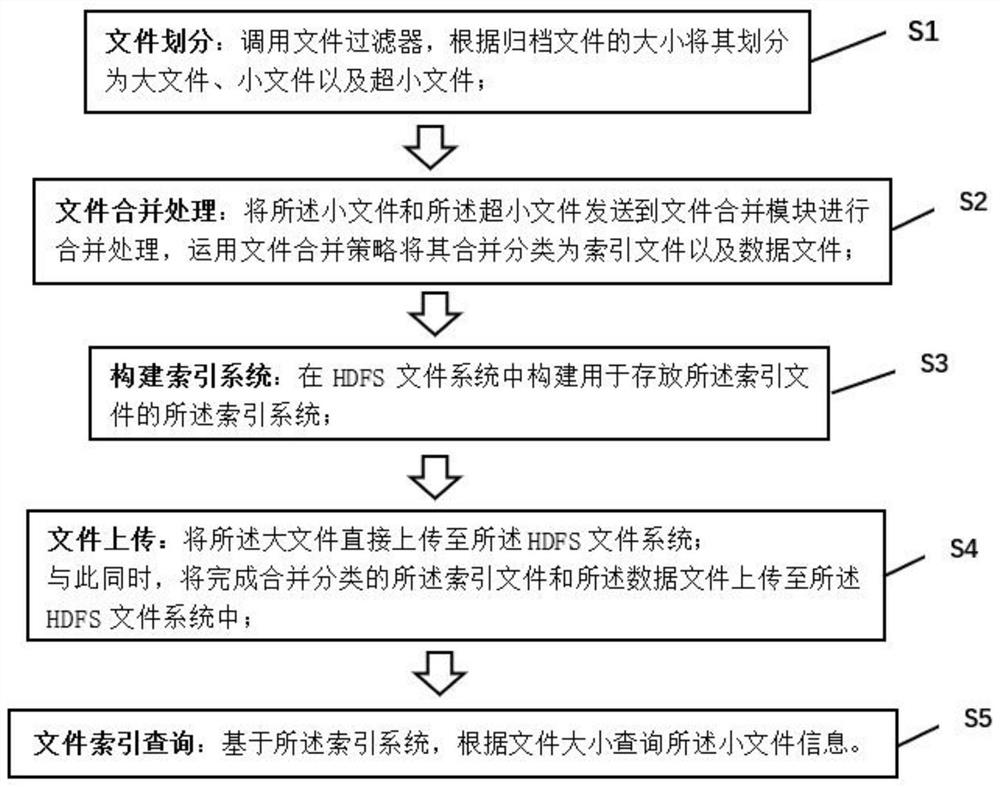
Method for accessing archived file based on B + tree index
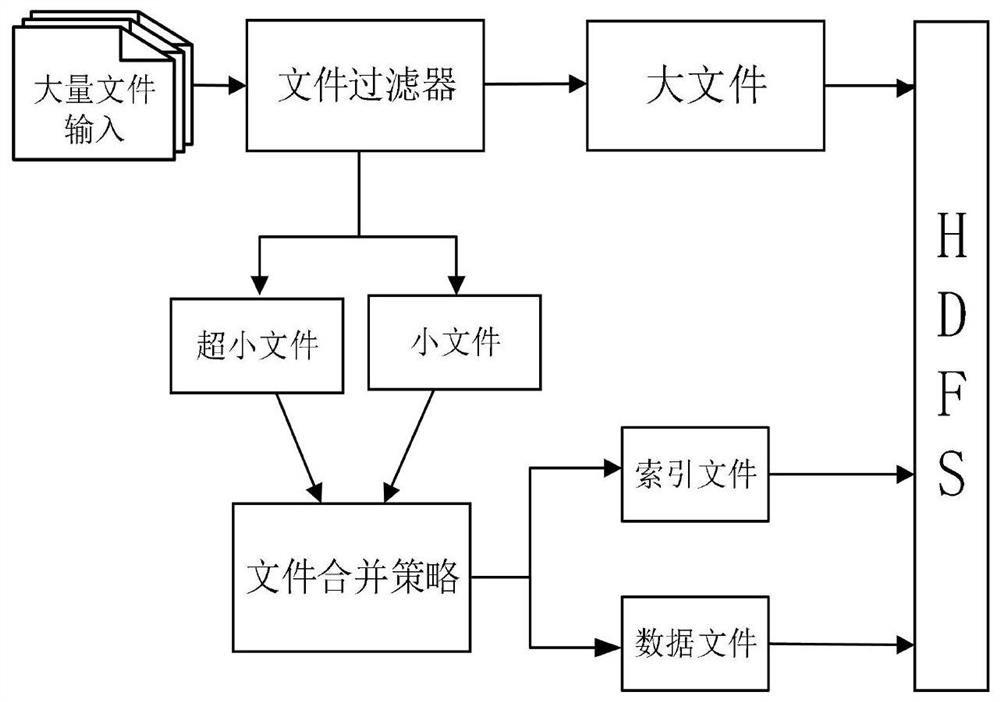
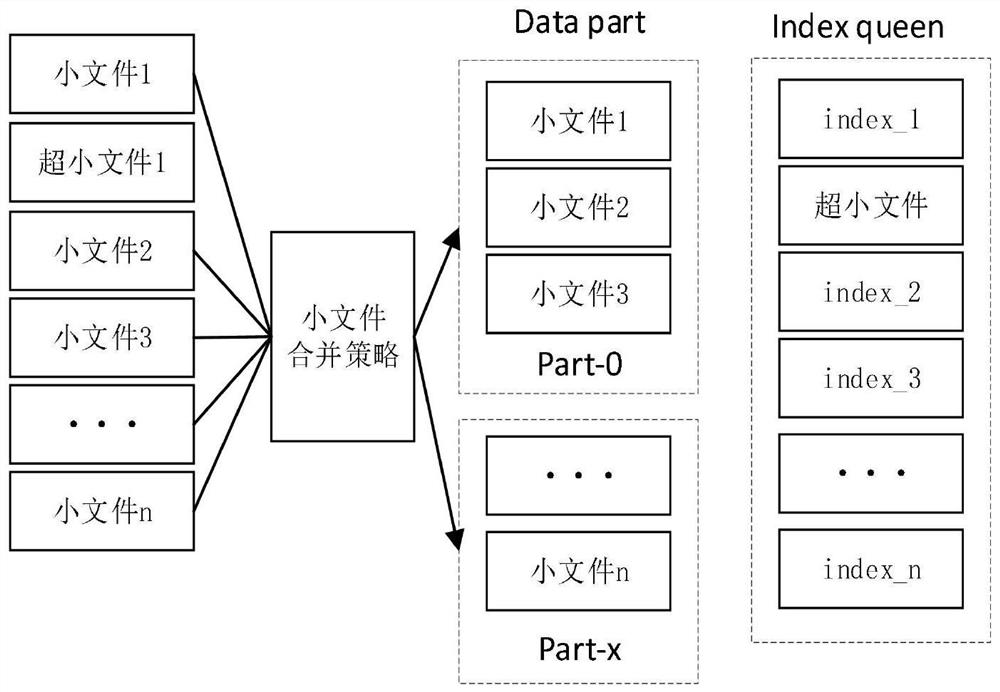
PendingCN114116612AImprove access performanceSolve the problem of poor access performanceFile access structuresOther databases indexingAccess methodDistributed File System
The invention discloses a B + tree index-based archived file access method, which comprises the following steps of: file division: calling a file filter, and dividing an archived file into a large file, a small file and an ultra-small file according to the size of the archived file; file merging processing: sending the small files and the ultra-small files to a file merging module, and merging and classifying the small files and the ultra-small files into index files and data files by using a file merging strategy; constructing an index system: constructing the index system for storing the index file in an HDFS (Hadoop Distributed File System); file uploading: directly uploading a large file to the HDFS file system; meanwhile, the index file and the data file which are merged and classified are uploaded to the HDFS file system; and file index query: querying the small file information according to the file size based on the index system. According to the technical scheme, the problem that in an original scheme, the small file access performance is poor can be solved, and the small file retrieval speed is increased while NameNode memory consumption is reduced.
Owner:CHANGSHA UNIVERSITY OF SCIENCE AND TECHNOLOGY
A case-related electronic data evidence obtaining management system
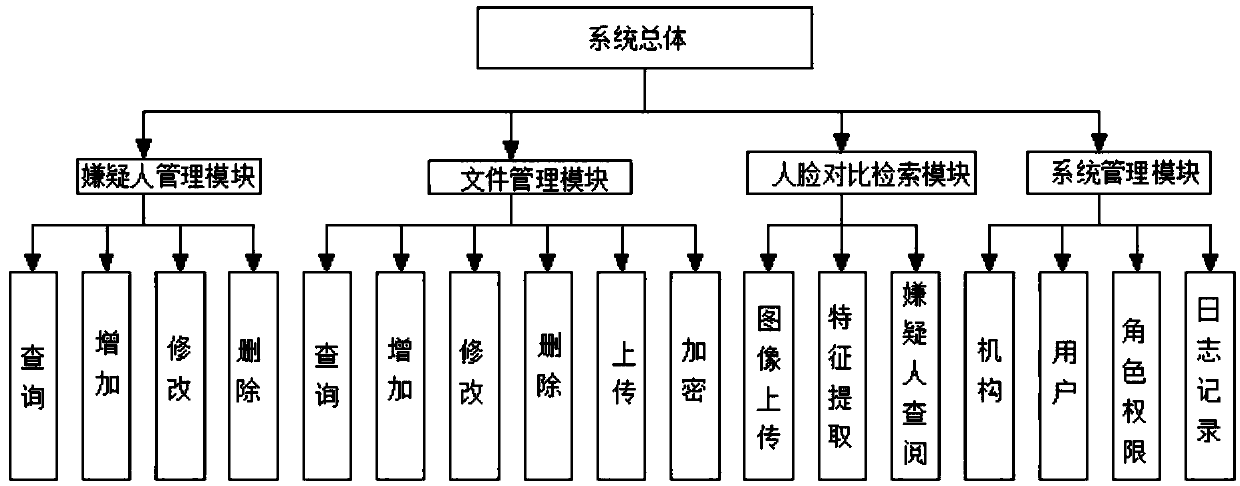
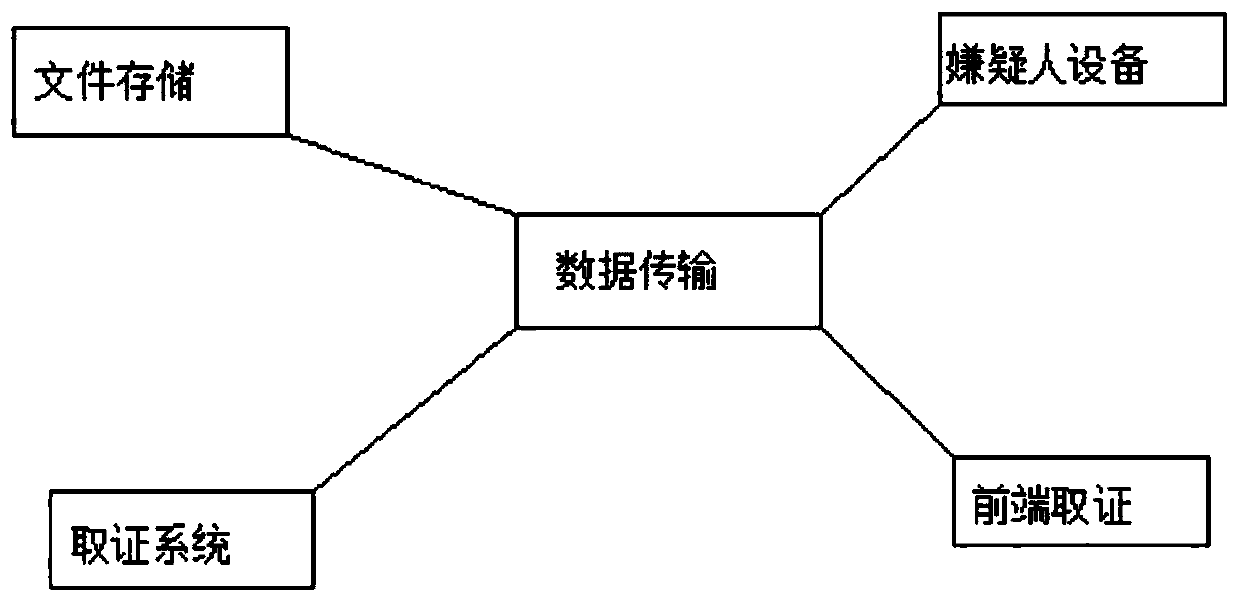
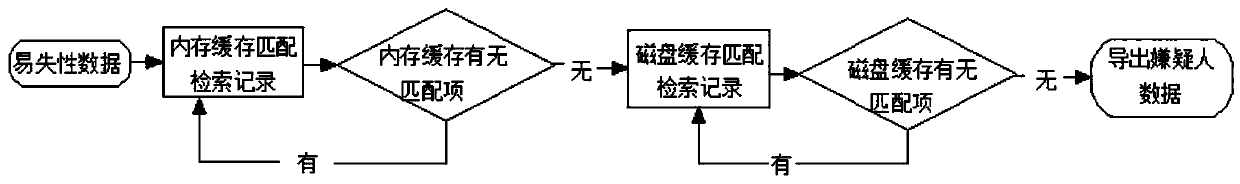
PendingCN109635099AImprove the judicial basisCharacter and pattern recognitionDigital data protectionData informationData acquisition
The invention discloses a case-related electronic data evidence obtaining management system, and relates to the technical field of electronic evidence collection and face recognition. The system comprises a suspect management module, a file management module, a system module and a face comparison retrieval module; the suspect management module comprises data query, addition, modification and deletion; and the file management module comprises data query, addition, modification, deletion, uploading and encryption. according to case-related electronic data forensics management system. A suspect management module, the File management module, the system module and the face comparison retrieval module are arranged; The image and video file data are acquired from a suspect mobile phone through volatility data acquisition, electronic data analysis, file filtering, electronic data file encryption and decryption and face comparison retrieval, concentrated storage management is carried out, query, filtering and analysis can be carried out, associated suspect data information is queried through face comparison analysis, and a more perfect judicial basis is provided for criminal investigation work.
Owner:山东华夏高科信息股份有限公司
Method and apparatus for document filtering capable of efficiently extracting document matching to searcher's intention using learning data
A document filtering device includes an information input / output unit, a search word extraction unit, a first sequence retrieval unit, a learning data unit, a classification parameter generation unit, a second sequence retrieval unit, and a classification unit. The information input / output unit inputs phrase information and outputs retrieval result information. The search word extraction unit extracts the search word from the phrase information. The first sequence retrieval unit retrieves documents having the search terms from the database, and outputs the first sequence retrieval results. The learning data unit prepares learning data from the first sequence retrieval result. A classification parameter generation unit generates classification parameters from the learning data. The second sequential retrieval unit retrieves documents having words corresponding to the classification parameters from the database. The classification unit extracts documents that match the searcher's intention and outputs the documents as second-order search results.
Owner:RICOH KK
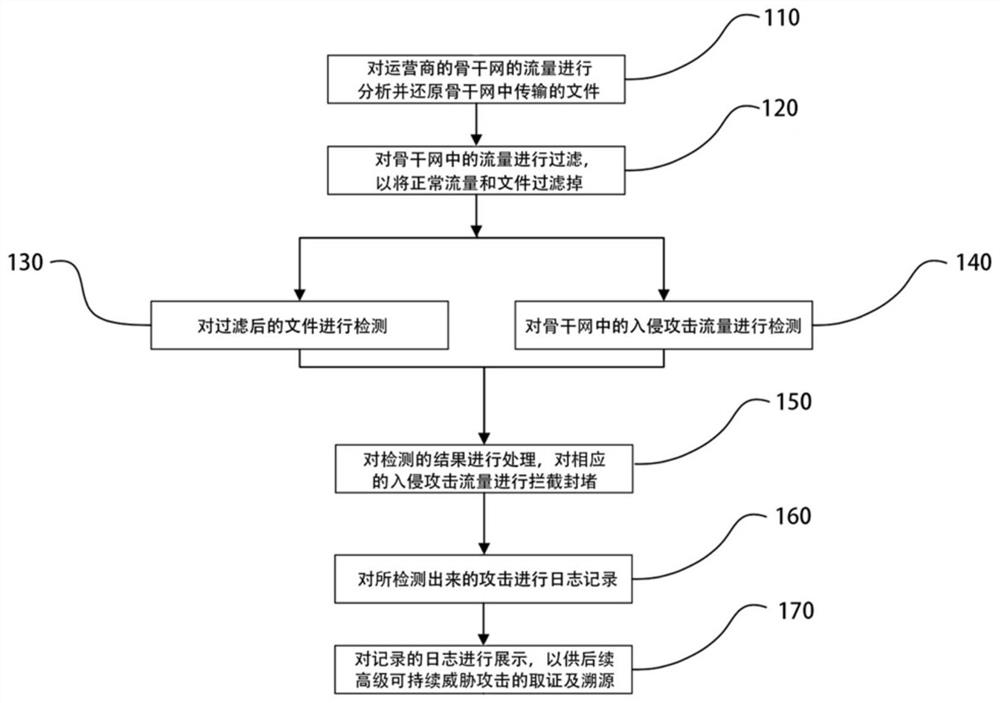
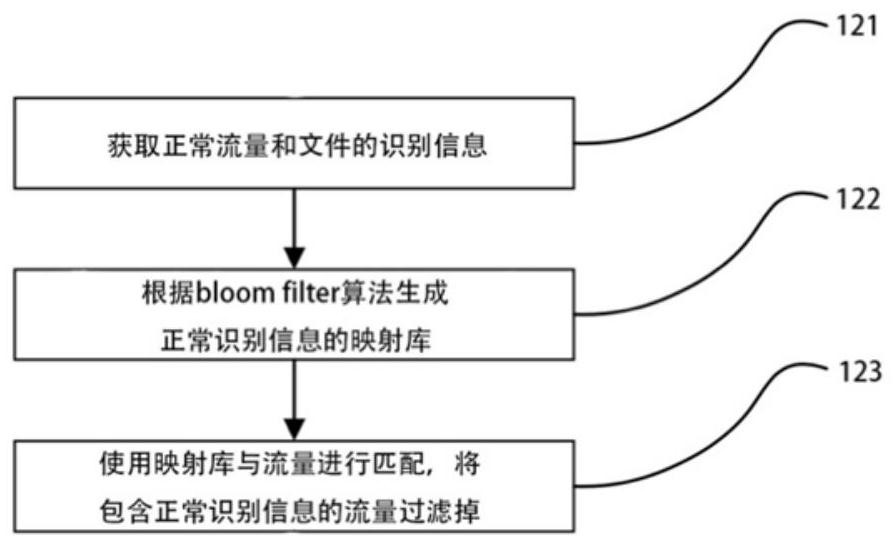
Advanced persistent threat detection method, system, computer and storage medium
The invention discloses an advanced persistent threat detection method, a system, a computer and a storage medium. The advanced persistent threat detection method comprises the steps of: analyzing traffic of a backbone network of an operator, and restoring files transmitted in the backbone network; filtering the traffic in the backbone network so as to filter normal traffic and files; detecting the filtered files; detecting intrusion attack traffic in the backbone network; processing the detection result, and intercepting and blocking the corresponding intrusion attack traffic; performing logrecording on the detected attack; and displaying the recorded logs for evidence acquisition and tracing of subsequent advanced persistent threat attacks. According to the advanced persistent threat detection method provided by the invention, the advanced persistent threat (APT) attack can be detected in a multi-directional manner; and powerful data support and detailed traceability information areprovided for the operator for APT detection, meanwhile, network attacks can be blocked, and benefits of users are guaranteed.
Owner:CHINA MOBILE COMM GRP CO LTD +3
Bait file hiding method and device, electronic device and storage medium
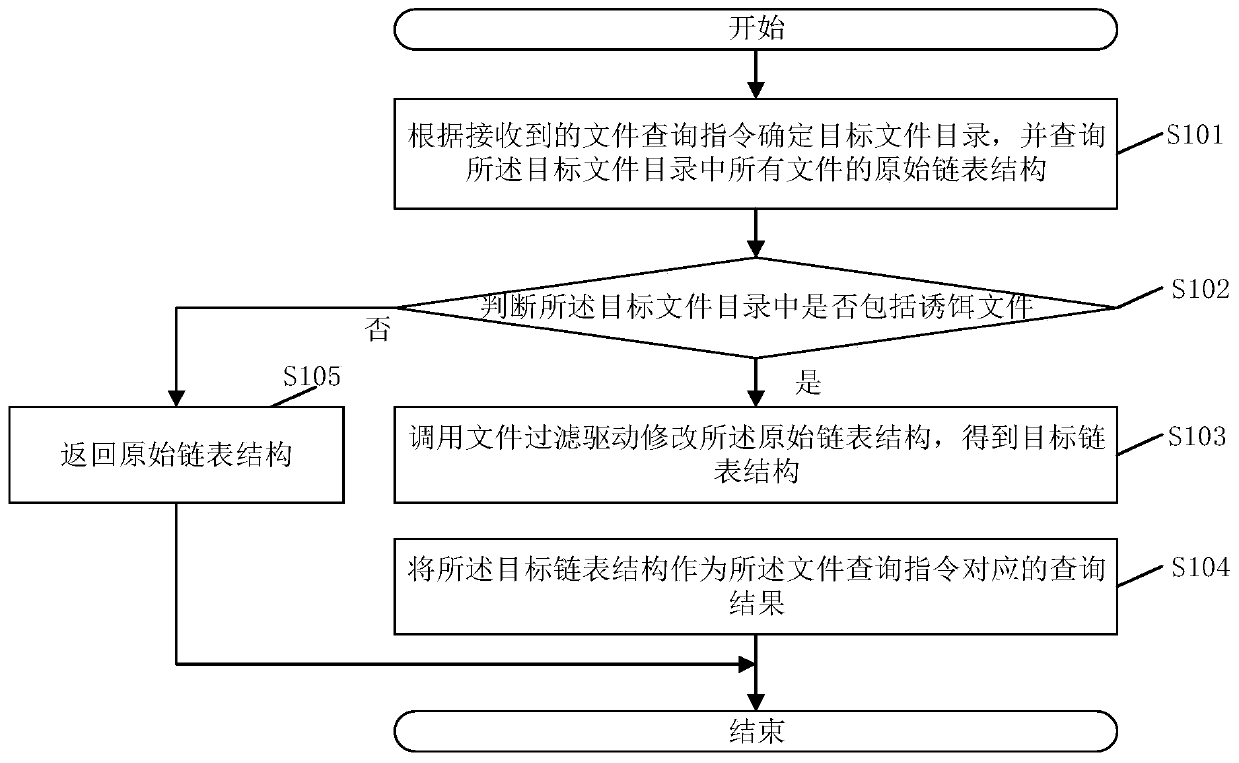
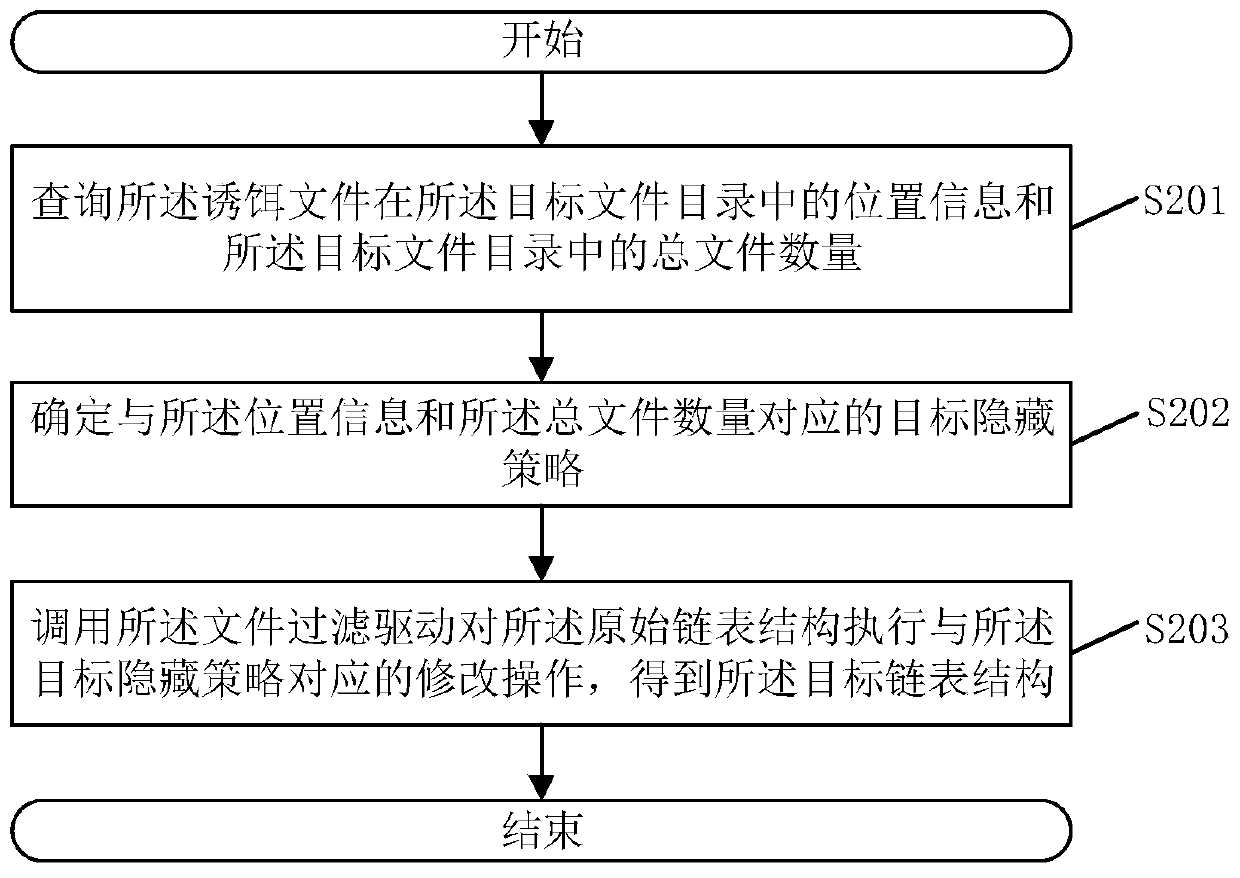
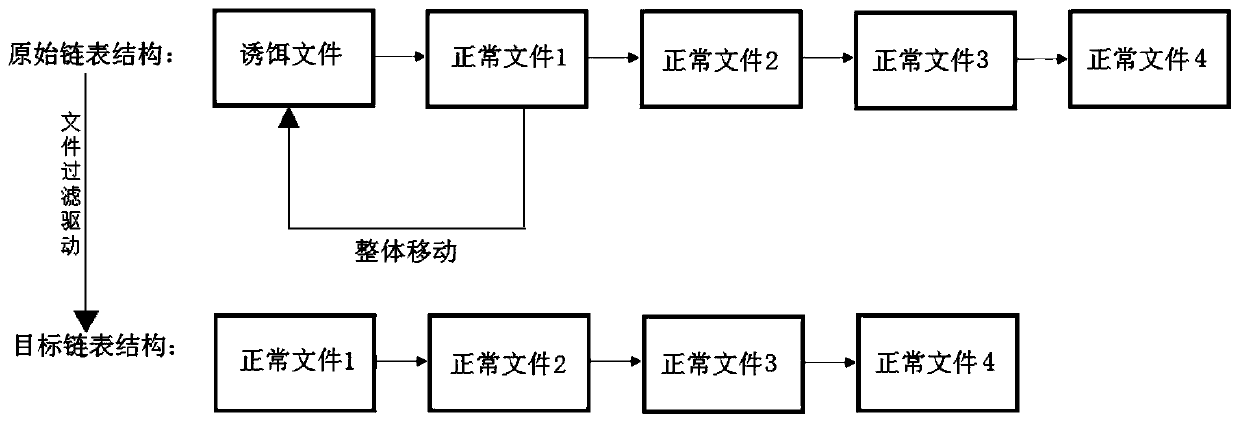
InactiveCN110826070AReduce stepsImprove concealmentDigital data protectionPlatform integrity maintainanceDirectoryDatabase
The invention discloses a bait file hiding method, and the bait file hiding method comprises the steps: determining a target file directory according to a received file query instruction, and queryingthe original linked list structures of all files in the target file directory; judging whether the target file directory comprises a bait file or not; wherein the bait file is a file used for detecting a virus process; if yes, calling a file filtering driver to modify the original linked list structure to obtain a target linked list structure; wherein the target linked list structure does not include file linked list information of the bait file; and taking the target linked list structure as a query result corresponding to the file query instruction. The method can improve the concealment ofthe bait file and prevent a user from deleting the bait file by mistake. The invention further discloses a bait file hiding device, an electronic device and a storage medium, which have the above beneficial effects.
Owner:SANGFOR TECH INC
Encrypted file read-write method and device, electronic equipment and storage medium
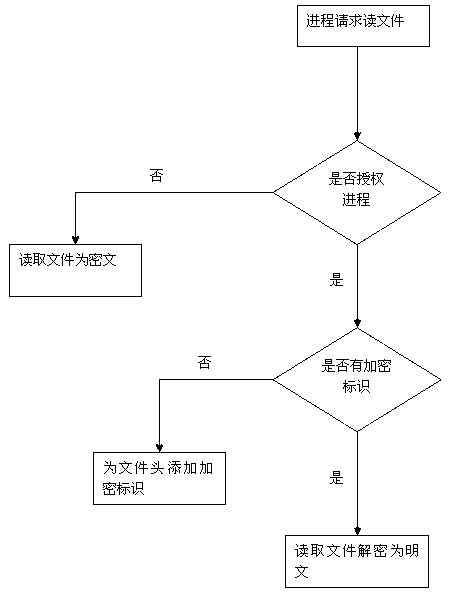
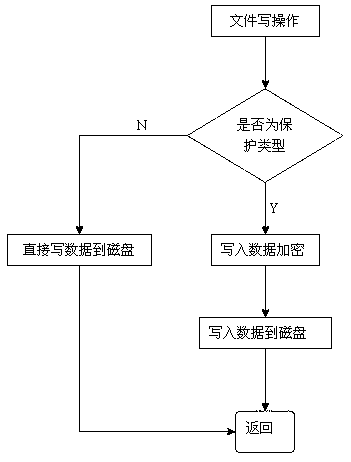
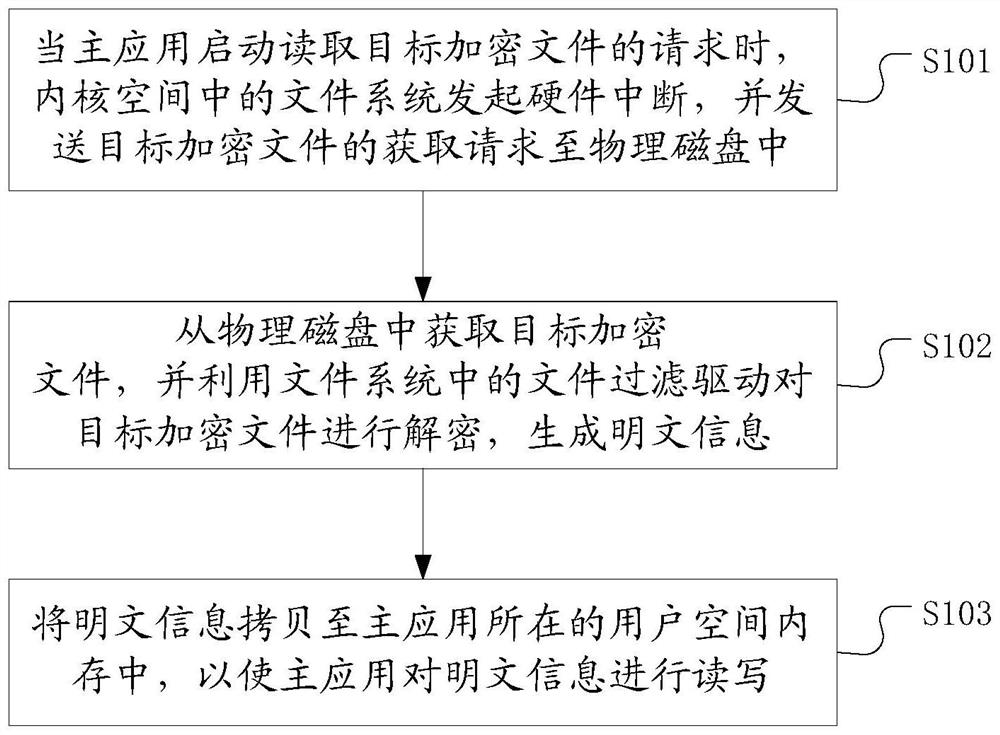
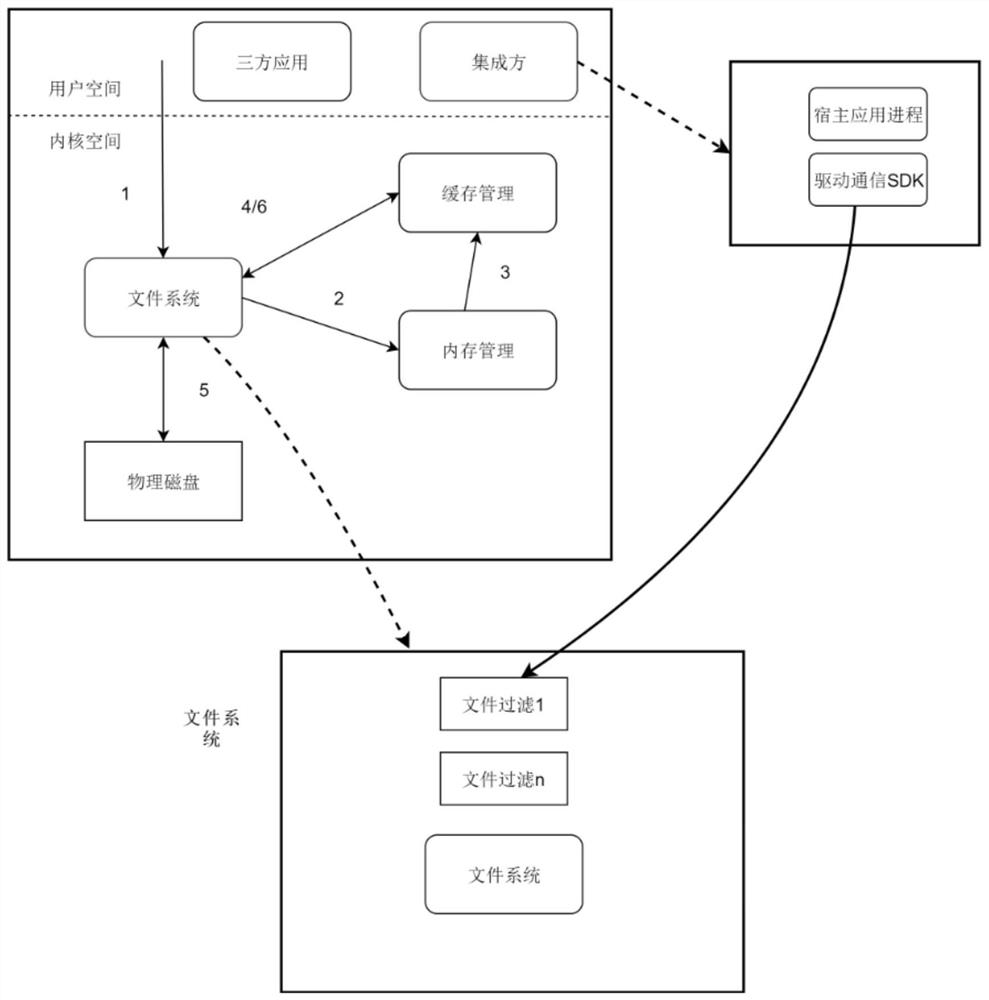
PendingCN113221171AEnsure security and confidentialityDoes not affect normal useDigital data protectionComputer hardwareConfidentiality
The invention discloses an encrypted file read-write method and device, electronic equipment and a storage medium, and the method comprises the steps: when a main application starts a request for reading a target encrypted file, a file system in a kernel space initiates hardware interruption, and sends an acquisition request of the target encrypted file to a physical disk; the target encrypted file is obtained from the physical disk, and the target encrypted file is decrypted by using a file filter driver in the file system to generate plaintext information; and the plaintext information is copied to a user space memory where the main application is located, so that the main application reads and writes the plaintext information. According to the method, the target encrypted file is encrypted and decrypted in the driving layer, plaintext information can be read without changing application software, and the target encrypted file is always in an encrypted state in a file system, so that the security and confidentiality of the file are ensured, the required file can be read without perception for the application layer, namely a main application, and the user use is not influenced.
Owner:杭州弗兰科信息安全科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com