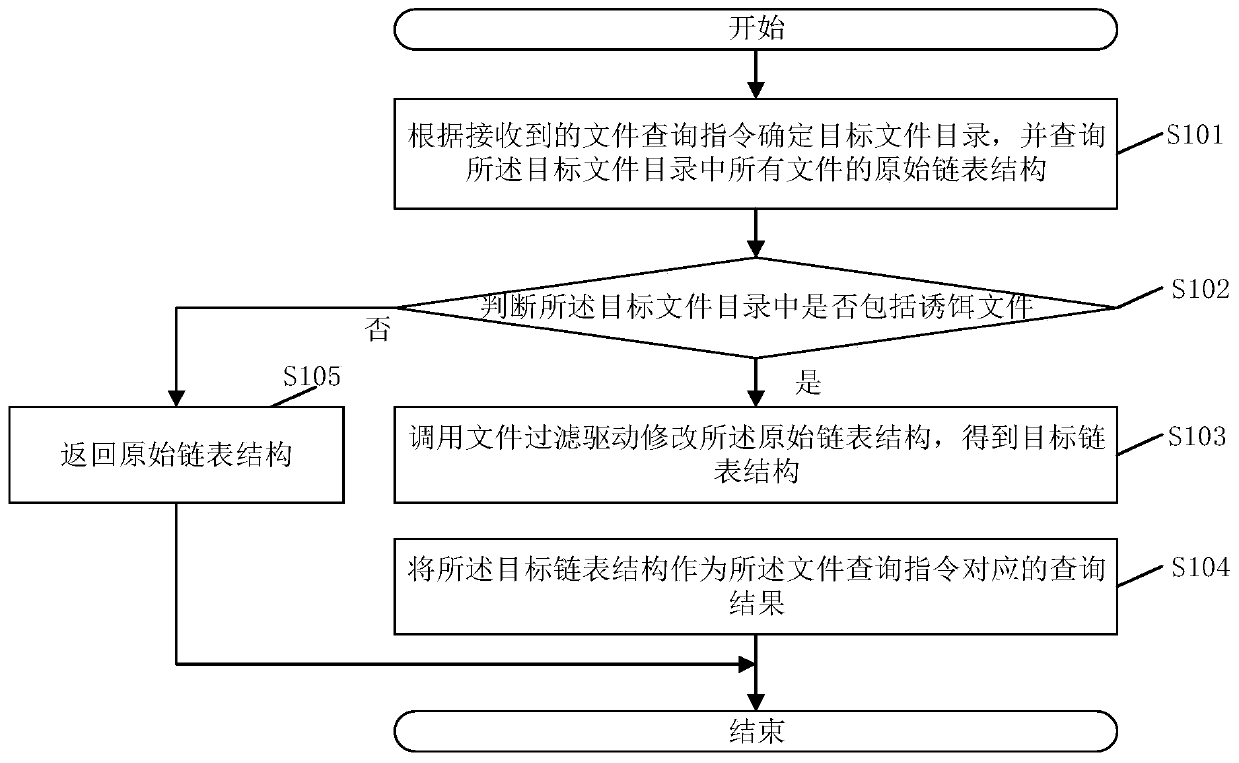
Bait file hiding method and device, electronic device and storage medium
A file and bait technology, applied in the field of information security, can solve the problems of blackmail virus detection and protection, and achieve the effect of improving protection ability, avoiding operation, and improving concealment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
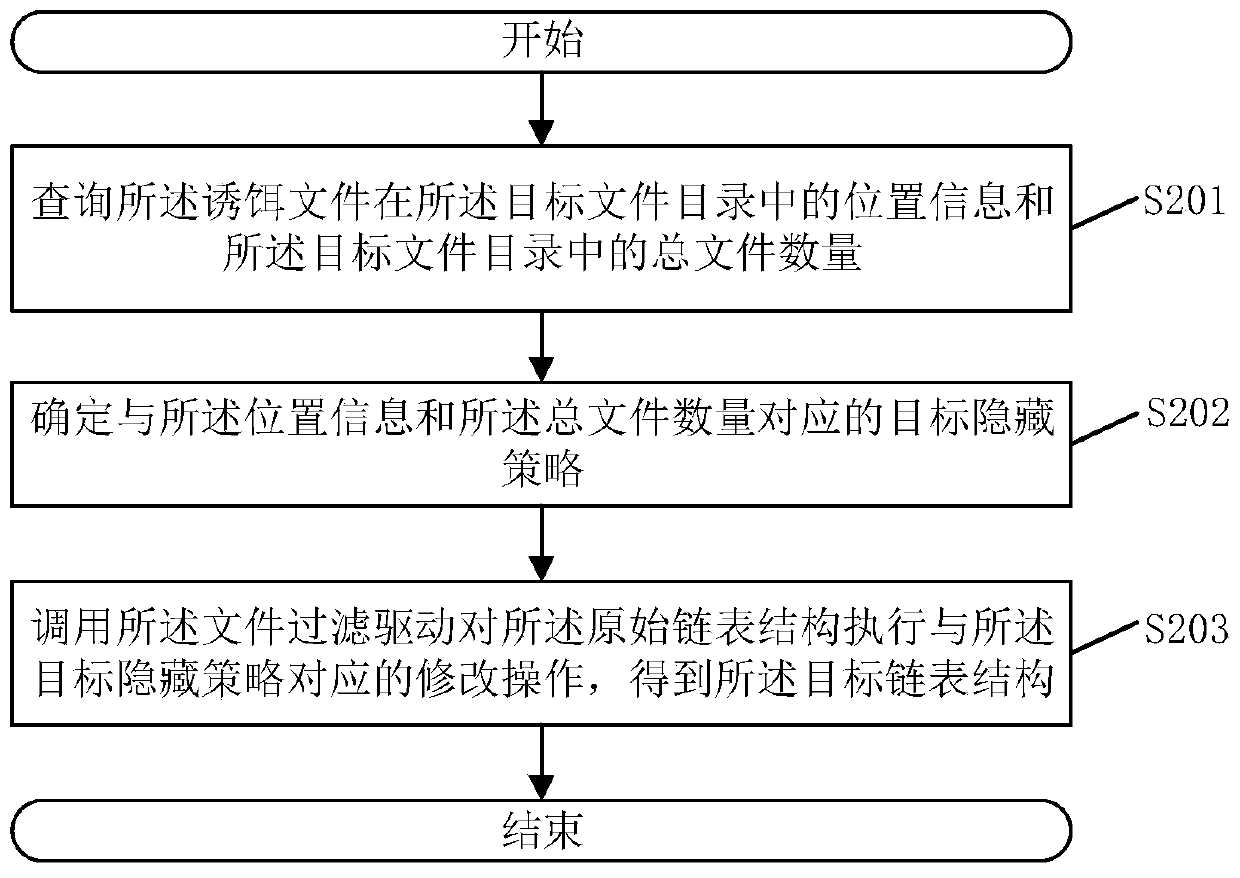
[0082] Embodiment 1: when the target hiding strategy includes the first hiding strategy, call the file filter driver to send a preset query command to the underlying IO system, and use the query result corresponding to the query request as the target linked list structure; Wherein, the preset query command is an command to control the underlying IO system to query files in the target file directory except the decoy file;
[0083]In Embodiment 1, there is only one decoy file that needs to be hidden in the original linked list structure. If an empty result is returned in the file filter driver, the content under the directory will be displayed abnormally. The processing method of this embodiment is to filter The driver executes another request to the underlying IO system and returns the result. Specifically, the above-mentioned re-execution request to the underlying IO system is a request for querying files other than the decoy file, so that the underlying IO system automaticall...
Embodiment approach 2
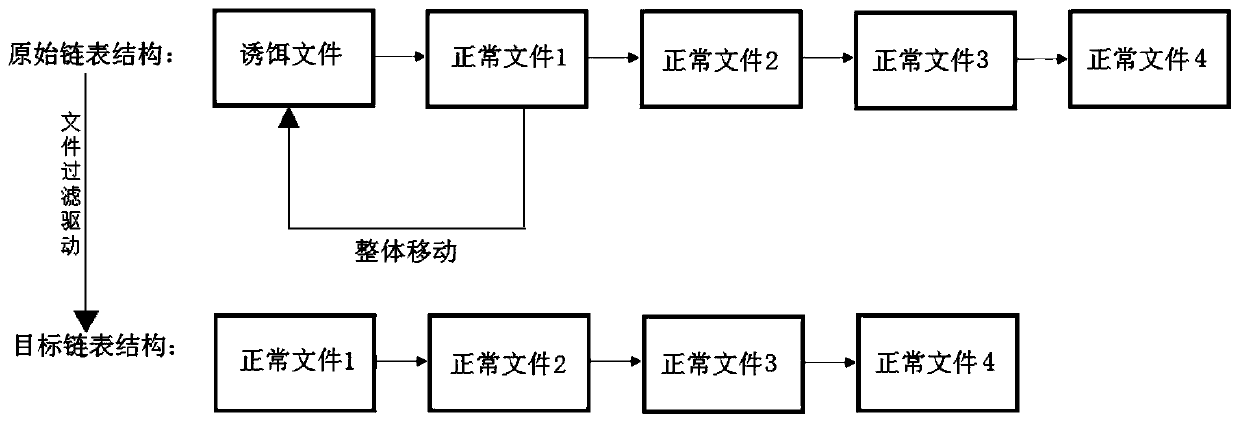
[0084] Embodiment 2: When the target hiding strategy includes the second hiding strategy, call the file filtering driver to perform an overall forward operation on the original linked list structure to obtain the target linked list structure, so that the next The item file is moved forward as a whole to the position of the decoy file in memory;
[0085] See image 3 , image 3 It is a schematic diagram of the hiding principle of the head decoy file provided by the embodiment of this application. In Embodiment 2, the decoy file information that needs to be hidden is in the first item of the original linked list structure, so the data of the next item of the decoy file can be moved forward as a whole in memory to the position of the decoy file information.
Embodiment approach 3
[0086] Embodiment 3: When the target hiding strategy includes the third hiding strategy, call the file filter driver to perform a link extraction operation on the original linked list structure to obtain the target linked list structure, so that the target linked list structure The previous item of the bait file points to the next item of the bait file;
[0087] See Figure 4 , Figure 4 It is a schematic diagram of the hiding principle of the middle decoy file provided by the embodiment of this application. In Embodiment 3, the decoy file information that needs to be hidden is in the middle of the original linked list structure, and the chain removal operation in Embodiment 3 can make the previous item of the decoy file directly point to the next item of the decoy file.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com