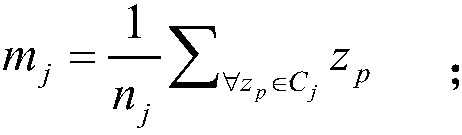Patents
Literature
60 results about "Virus process" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The main idea behind viral processing is to stop the viruses in a given sample from contaminating the desired product. The two most widely used methods of viral processing are viral removal and viral inactivation. The former is a method in which all viruses are simply removed from the sample completely.
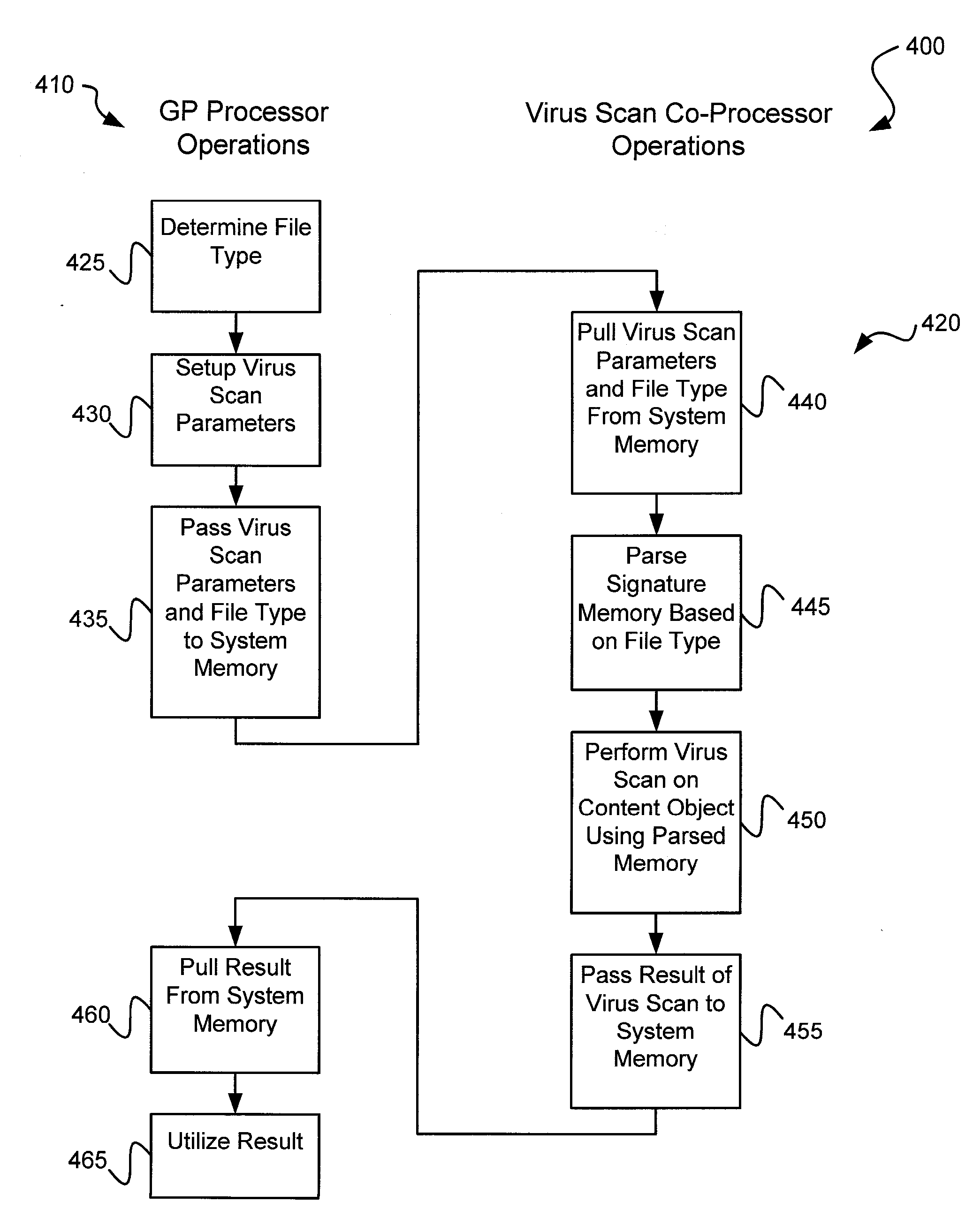
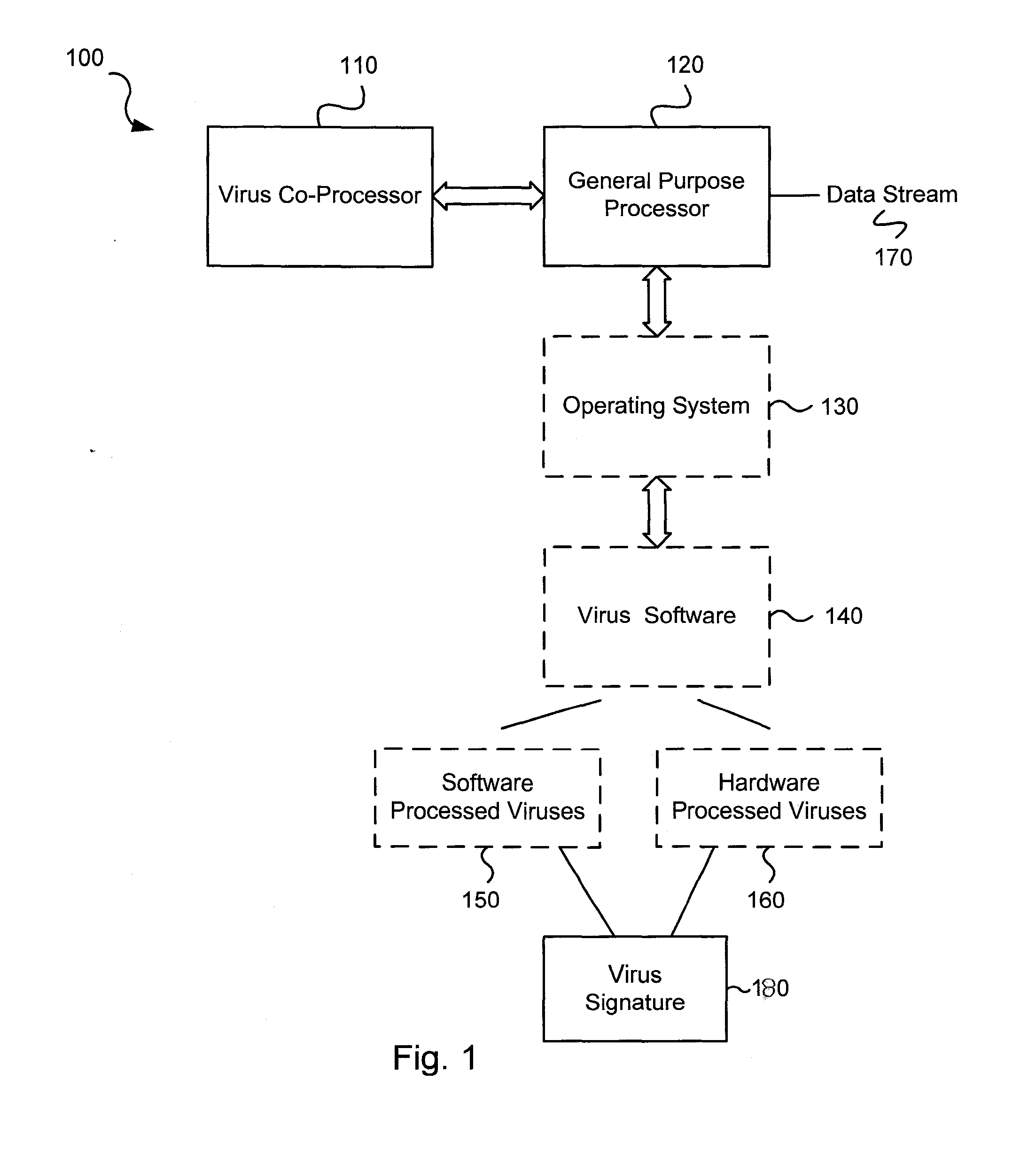
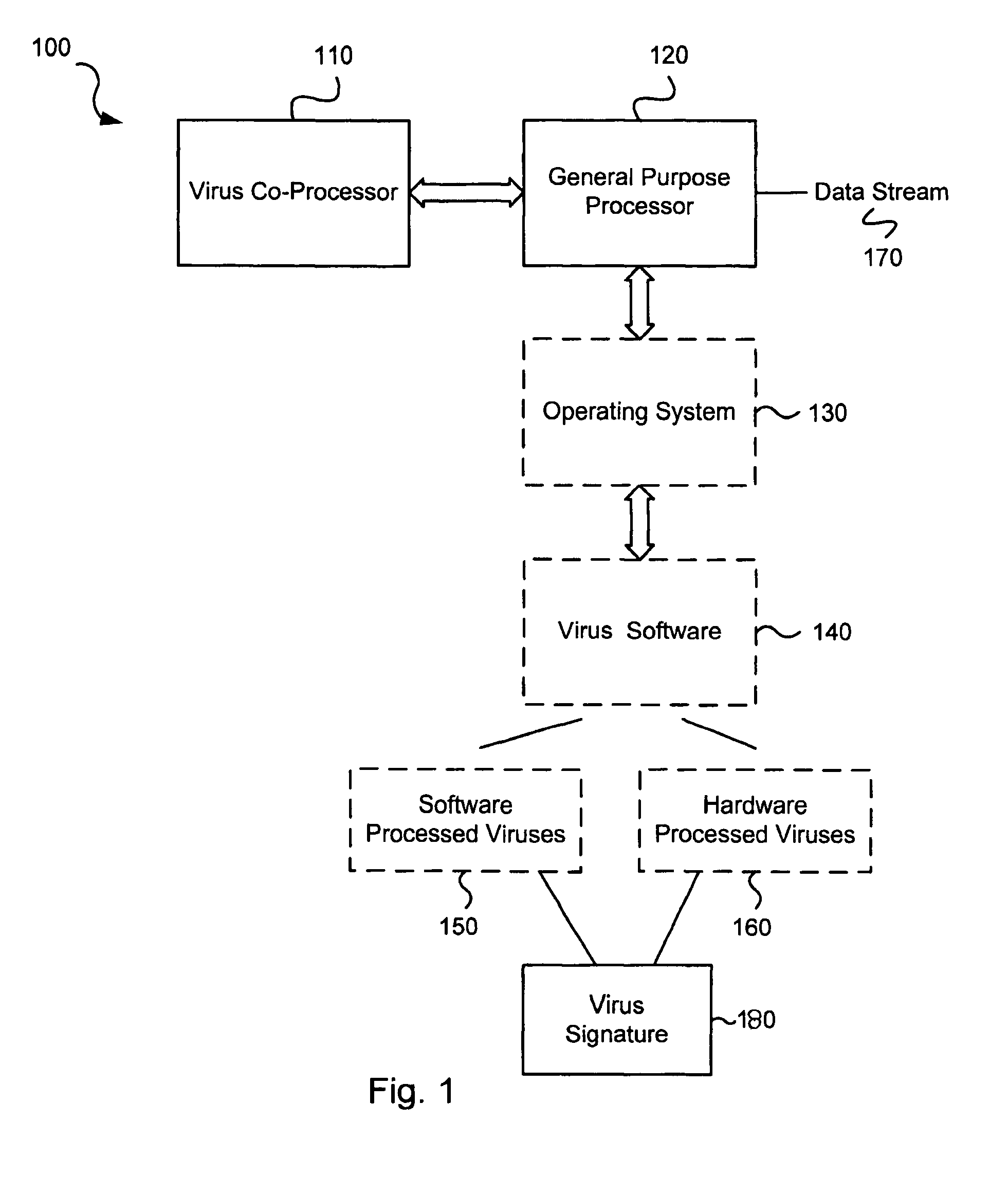
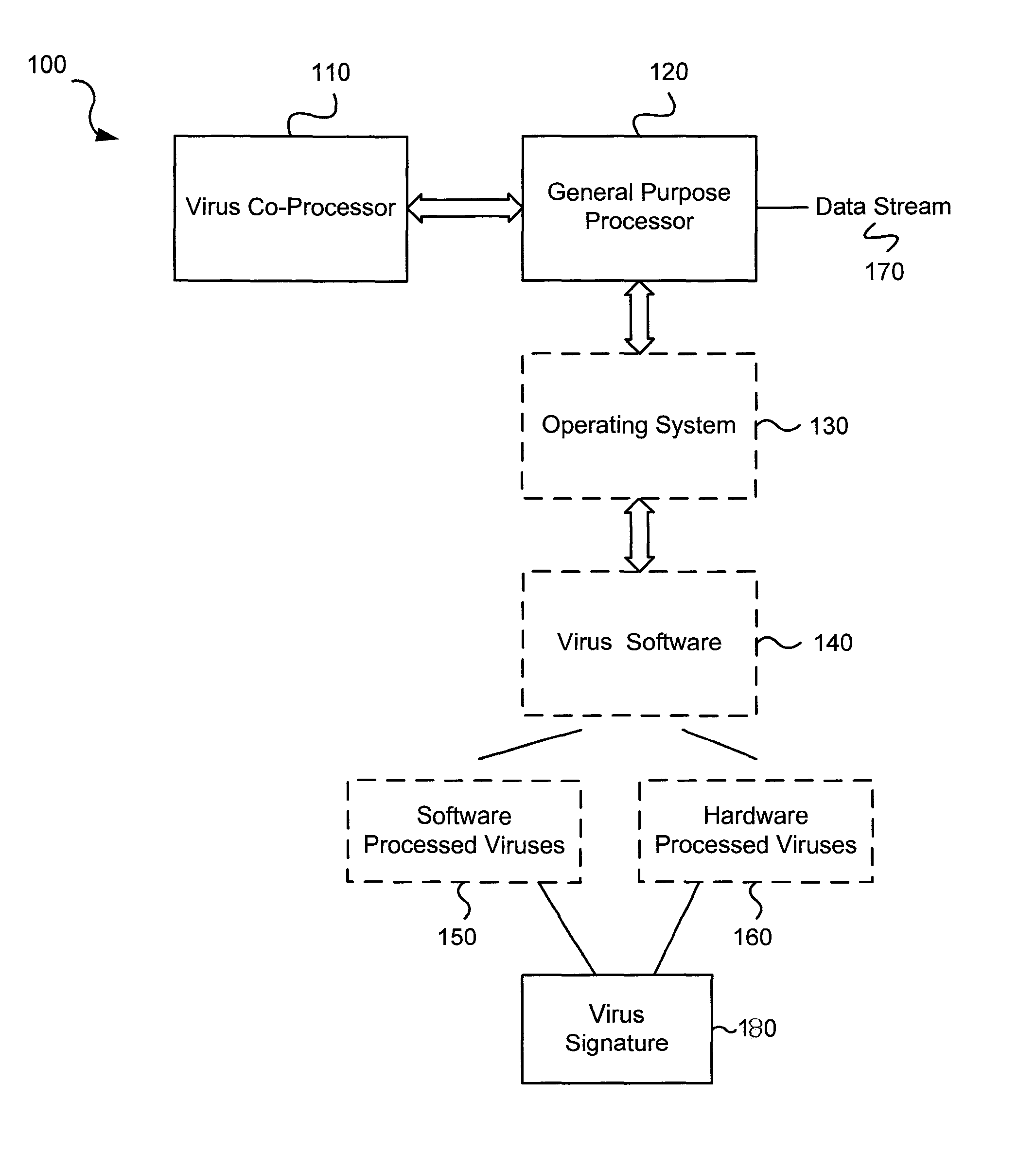
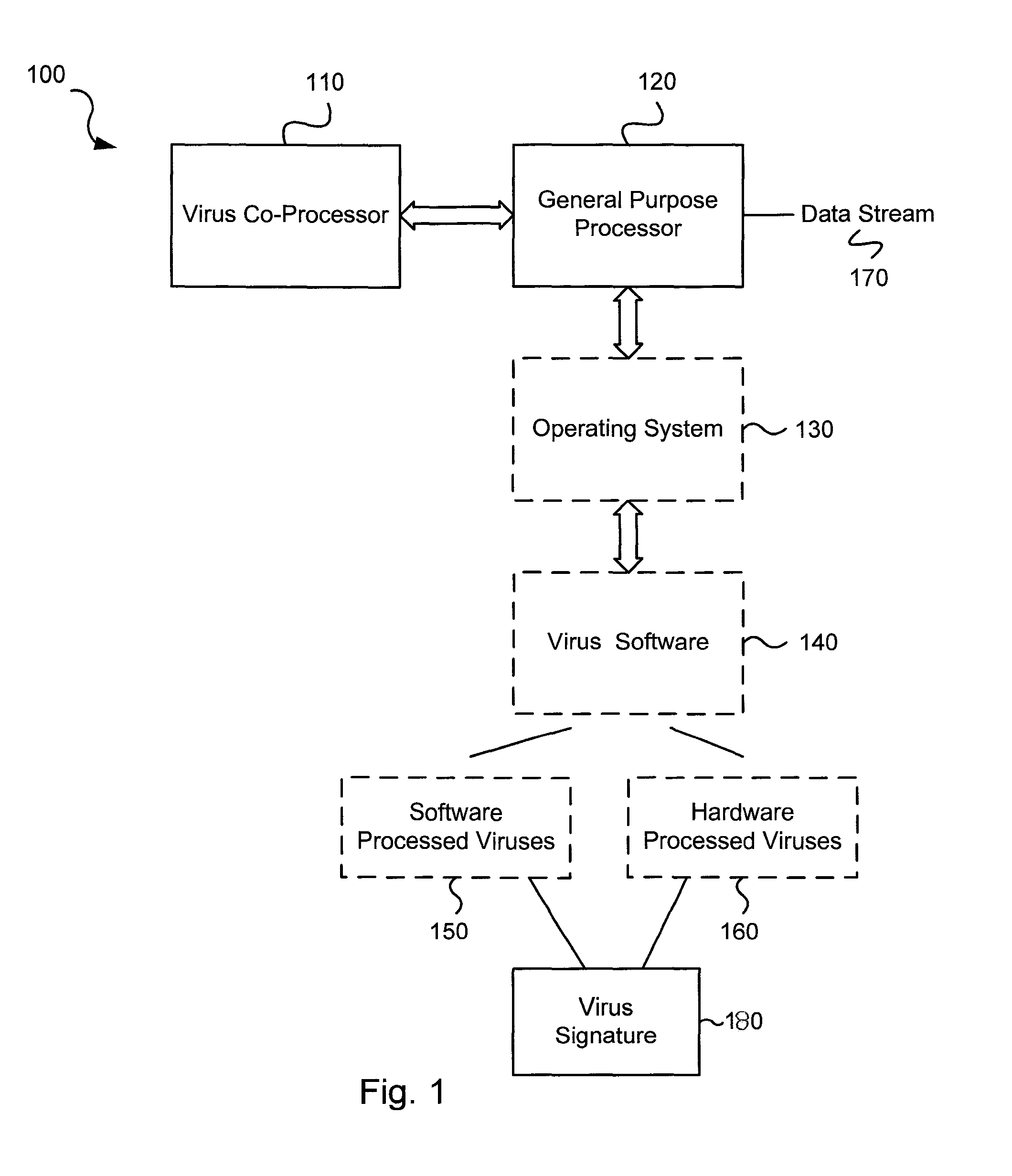
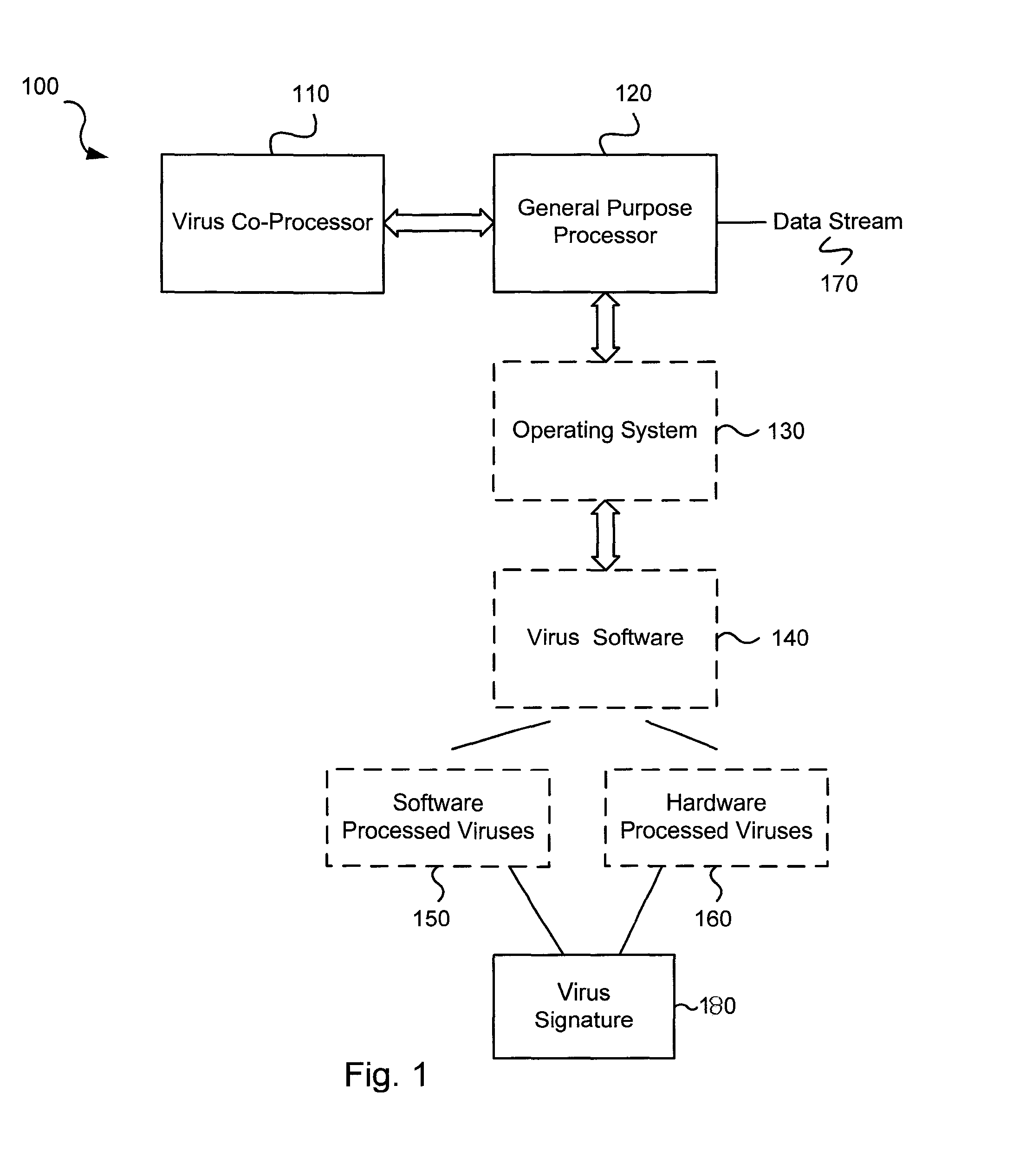
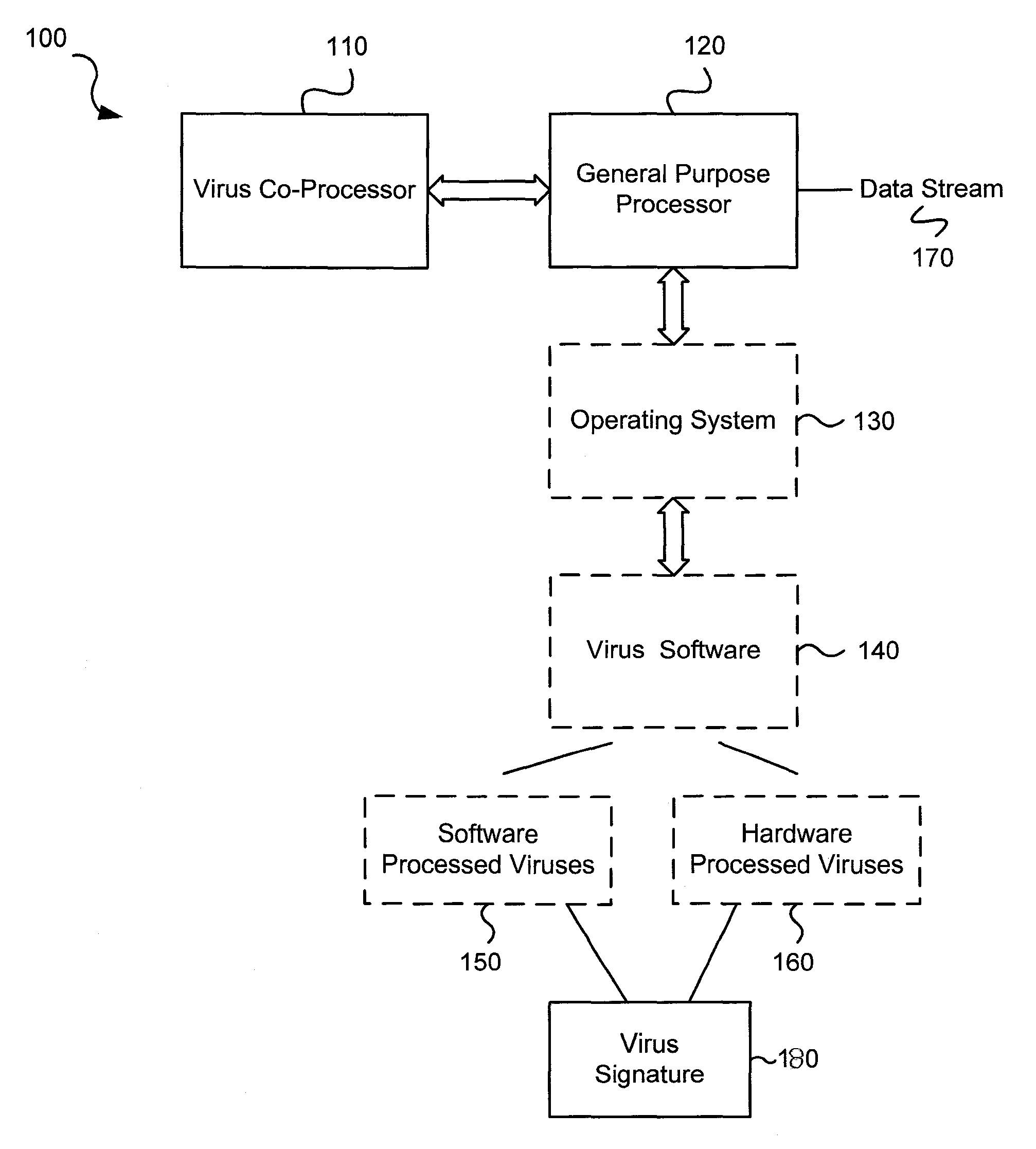
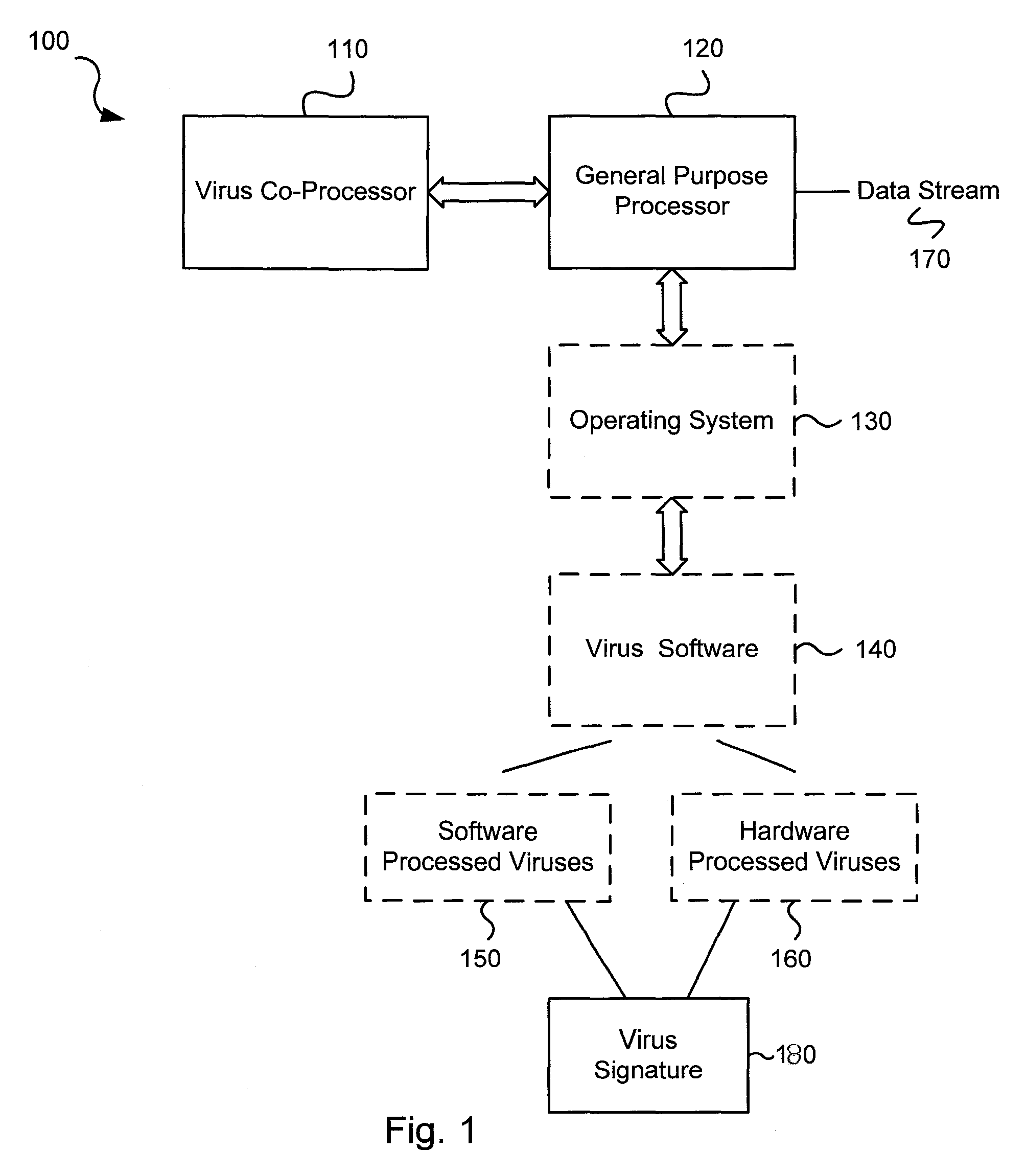
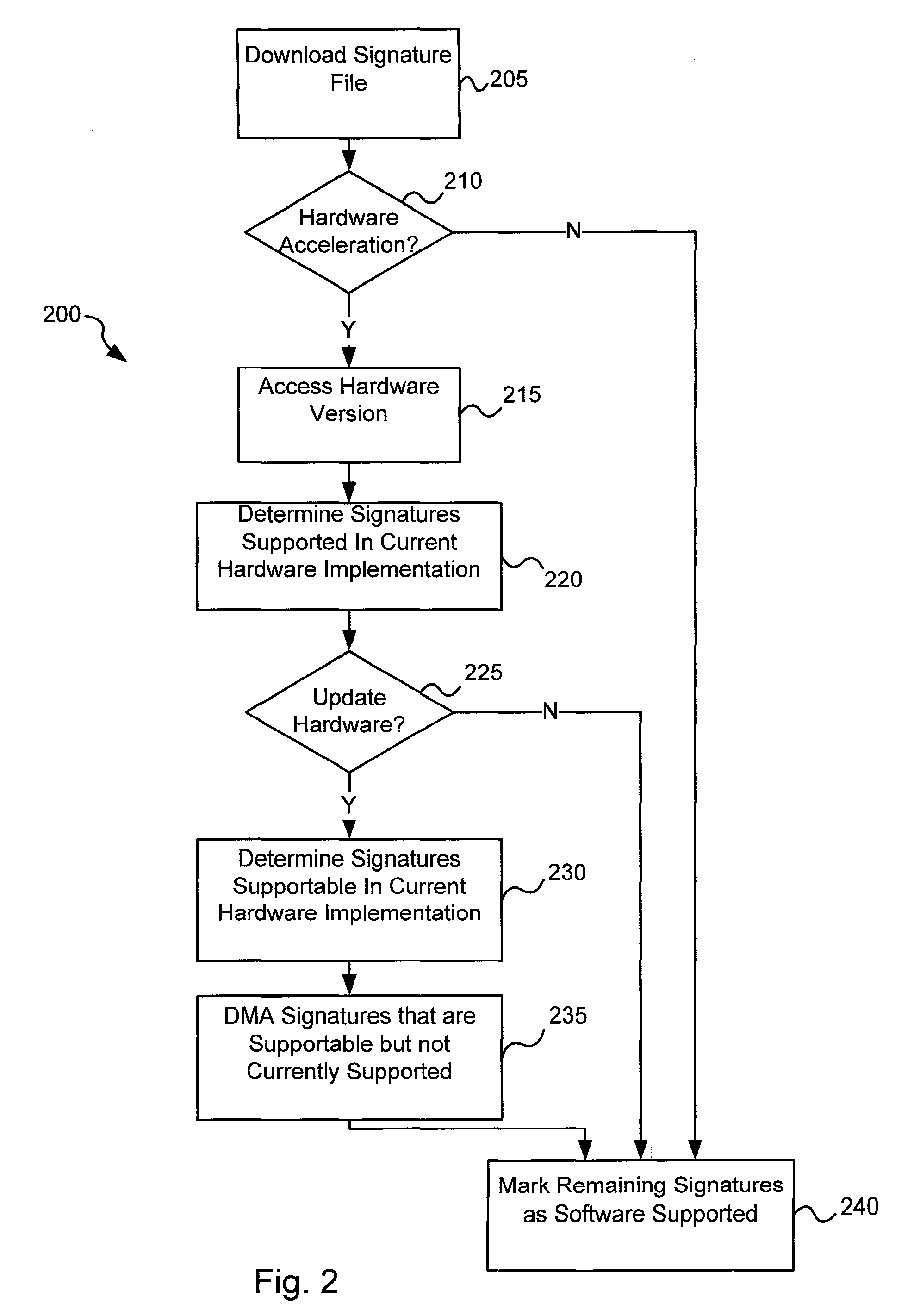
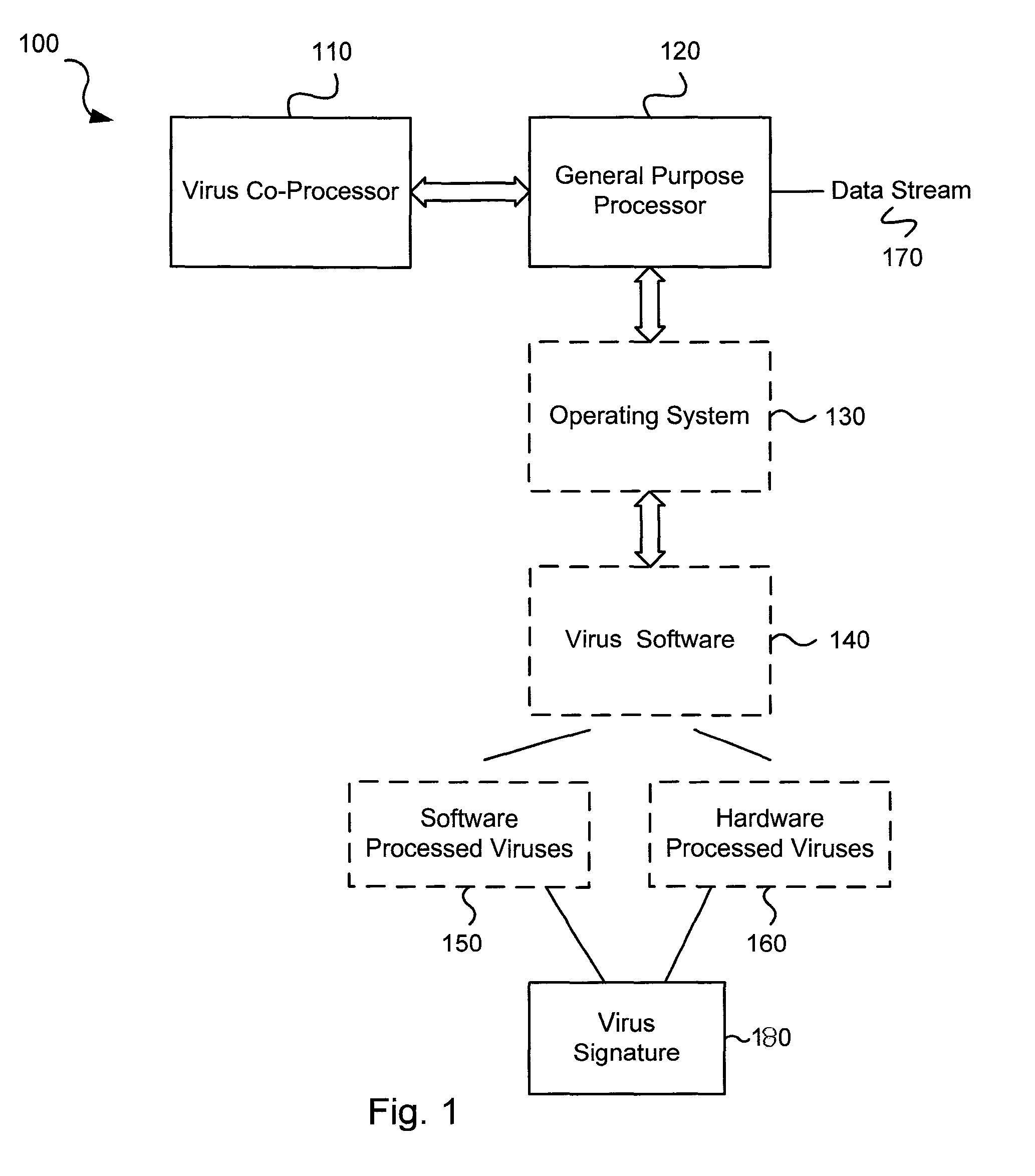
Circuits and methods for efficient data transfer in a virus co-processing system
ActiveUS20090044273A1Memory architecture accessing/allocationMemory loss protectionGeneral purposeData segment
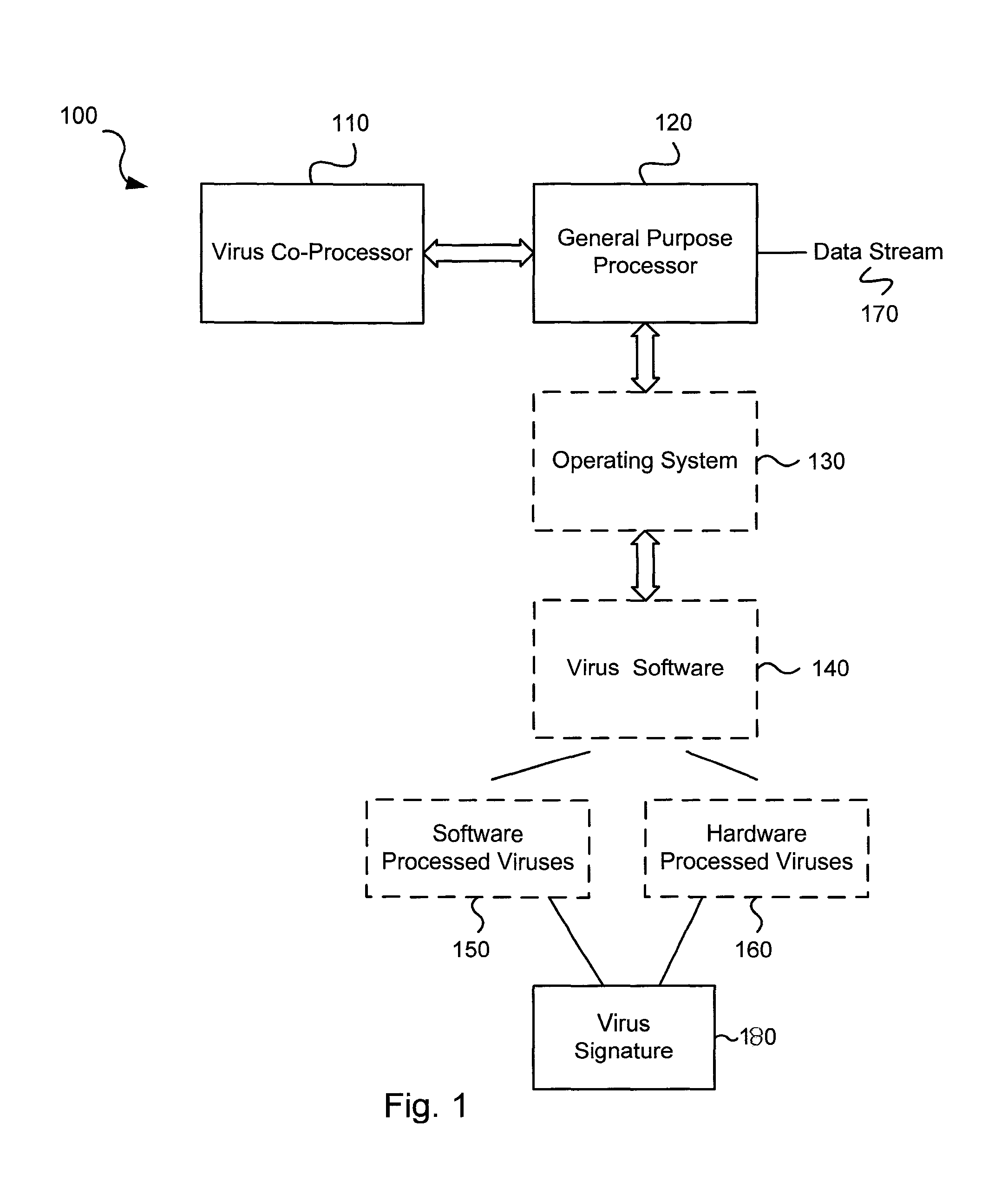
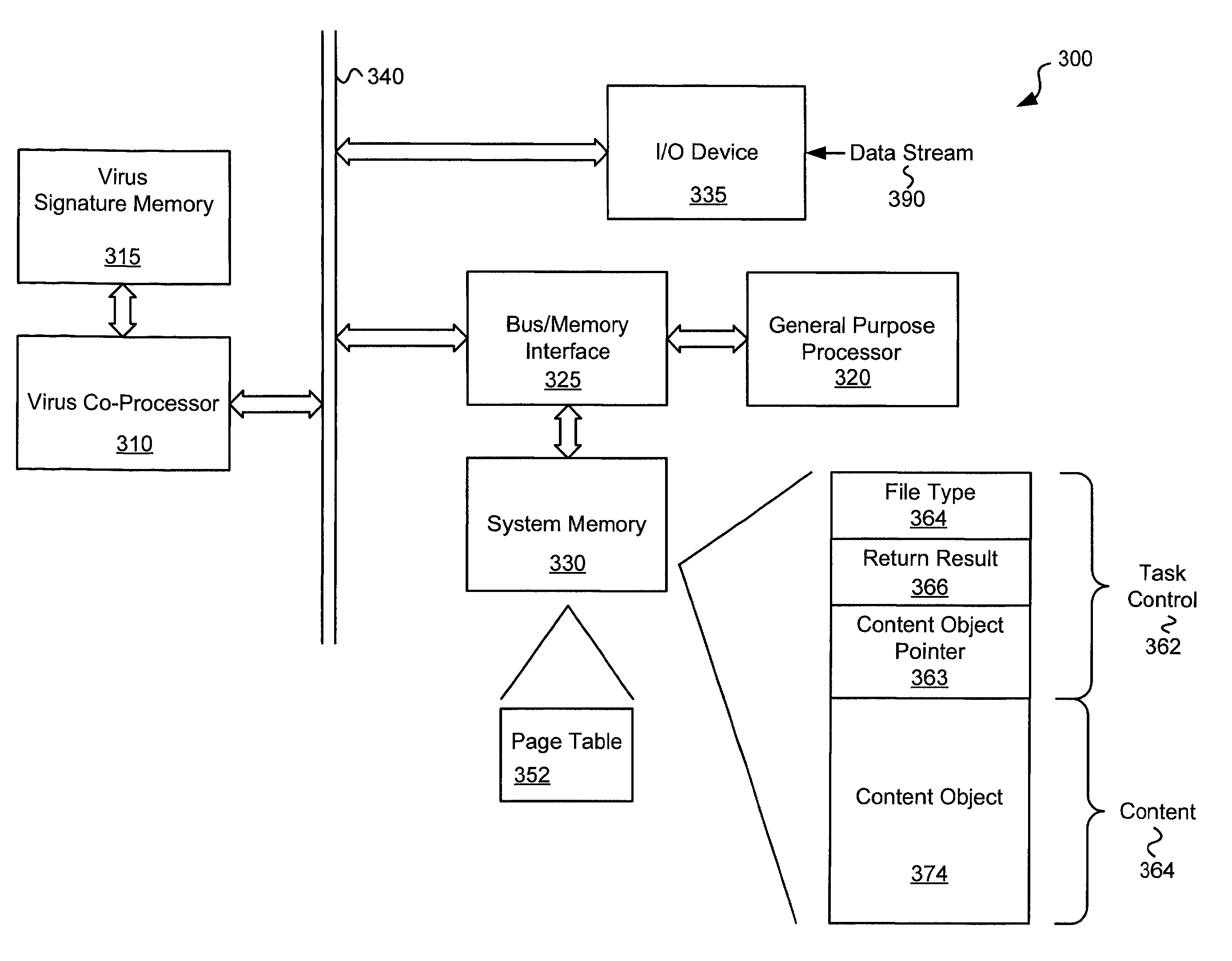
Various embodiments of the present invention circuits and methods for improved virus processing. As one example, such methods may include providing a system memory, a general purpose processor and a virus co processor. The methods further include receiving a data segment at the general purpose processor, and storing the data segment to the system memory using virtual addresses. The date segment is accessed from the system memory by the virus co processor using the virtual addresses. The virus co processor then scans the date segment for viruses and returns results.
Owner:FORTINET
Circuits and methods for operating a virus co-processor
ActiveUS8375449B1Memory loss protectionError detection/correctionInstruction memoryParallel computing
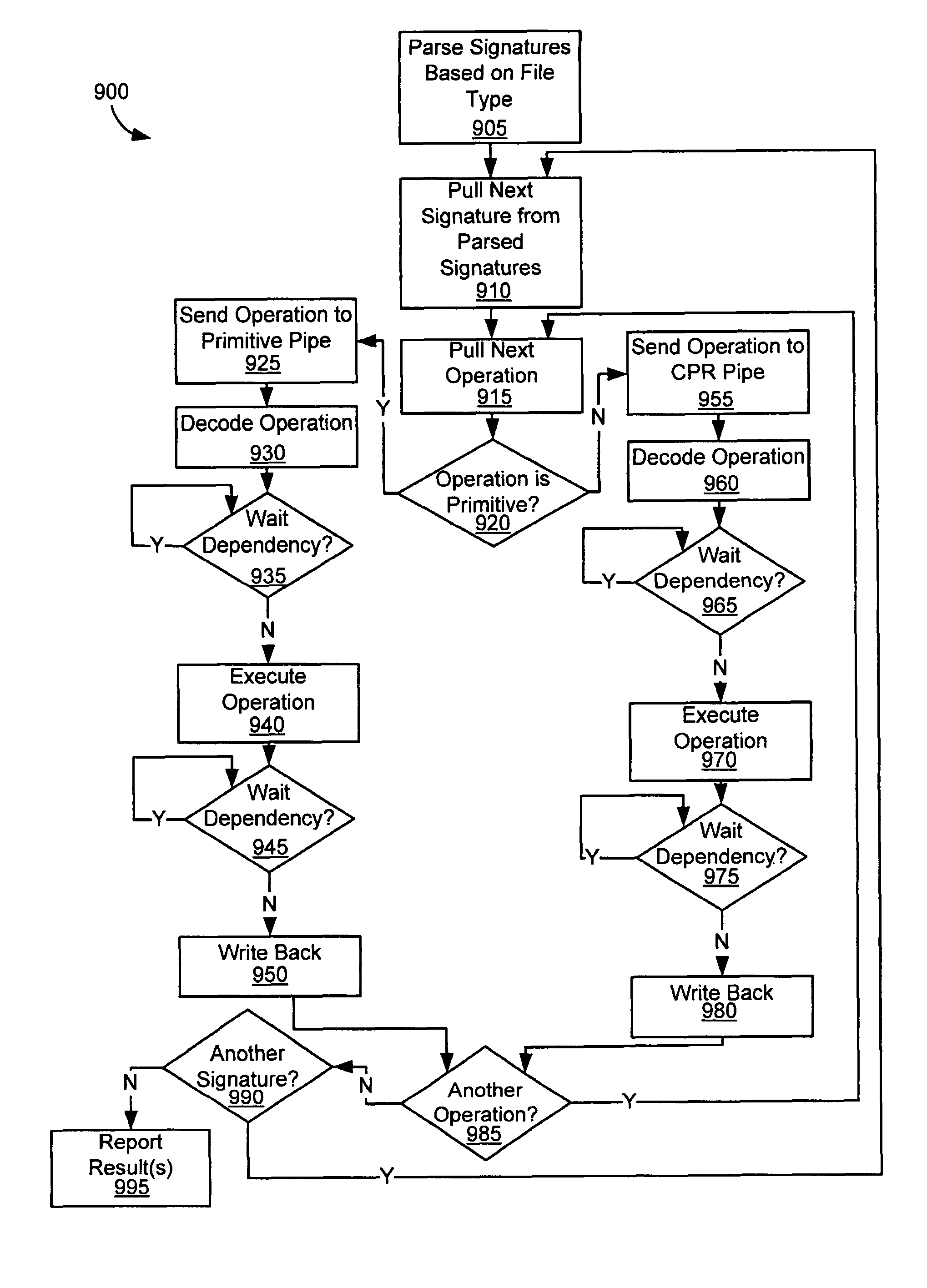
Various embodiments of the present invention provide circuits and methods for improved virus processing. As one example, a virus processing system is disclosed that includes an instruction memory and a virus co-processor. The instruction memory includes a first instruction type and a second instruction type intermixed. The virus co-processor is communicably coupled to the instruction memory, and includes at least a first instruction pipe and a second instruction pipe. The first instruction pipe is operable to execute the first instruction type, and the second instruction pipe is operable to execute the second instruction type.
Owner:FORTINET
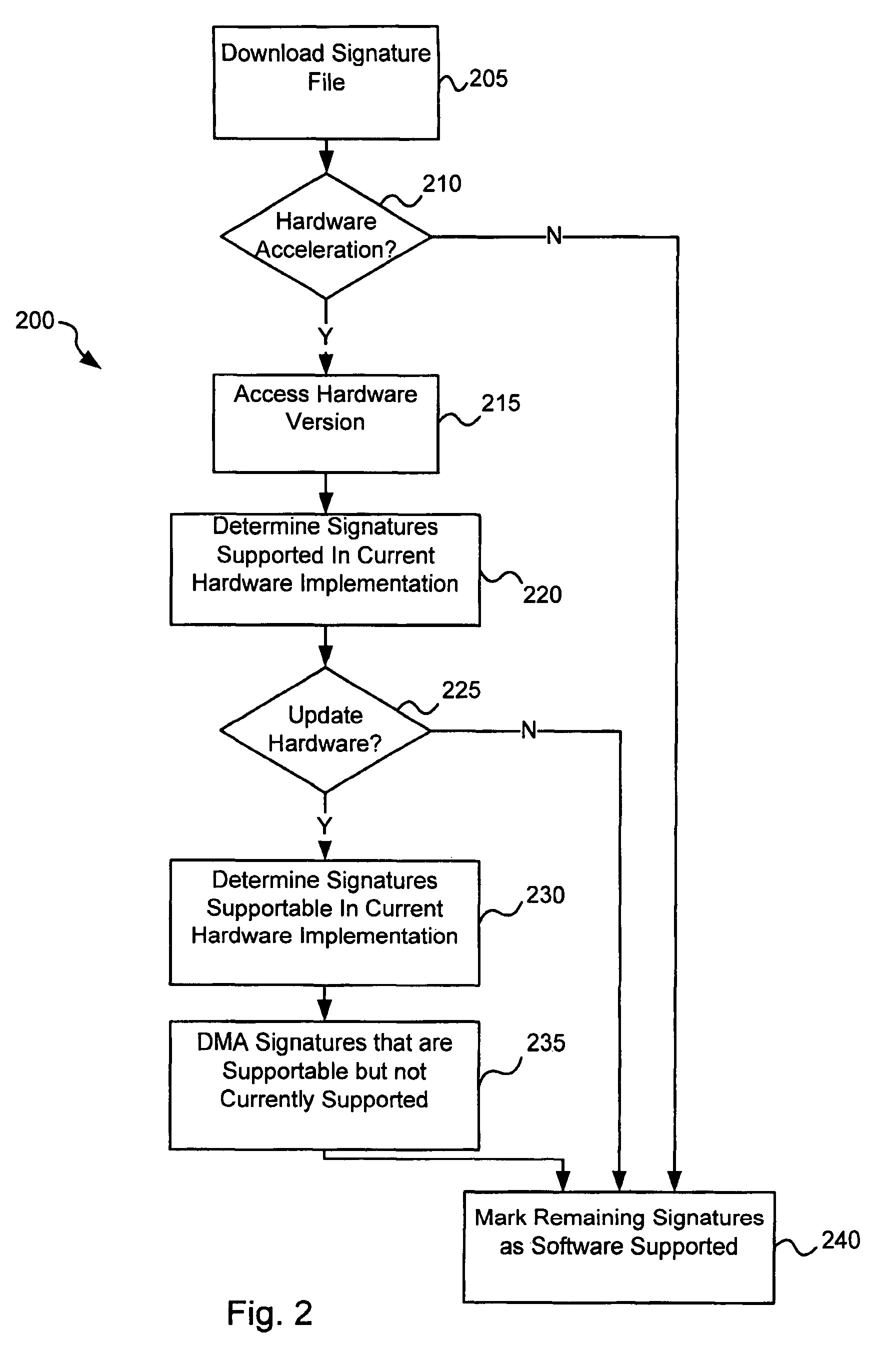
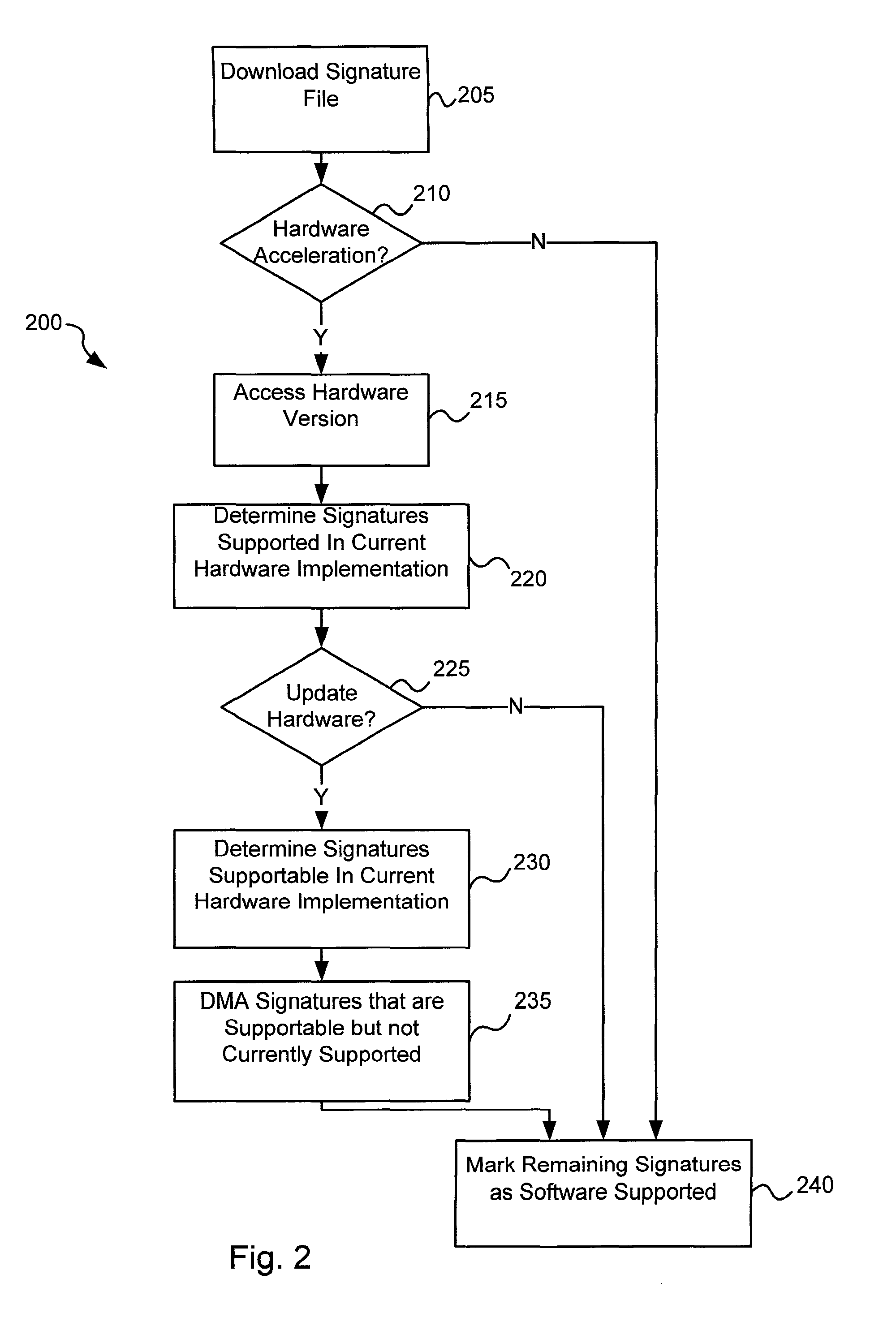
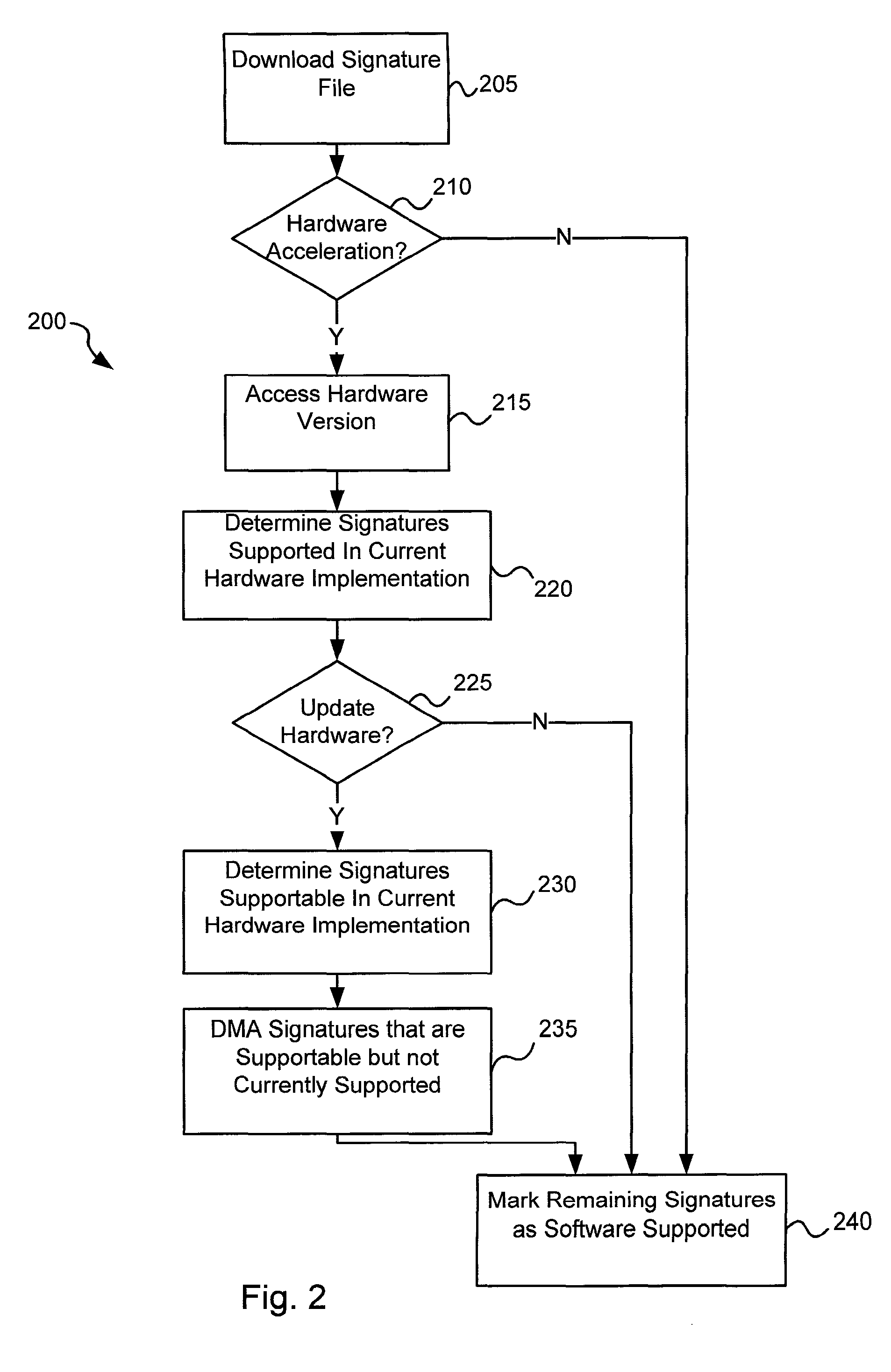
Software-hardware partitioning in a virus processing system
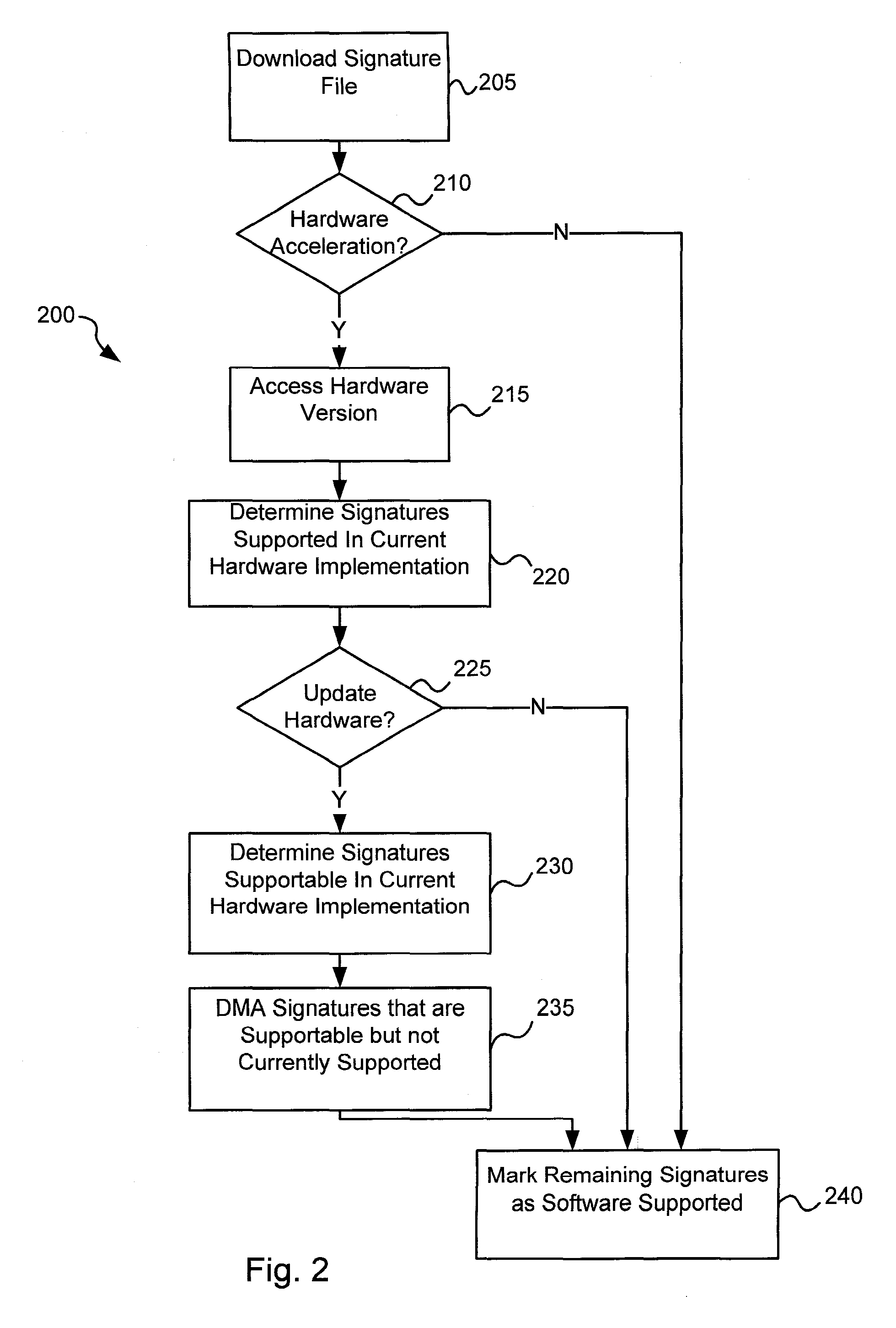
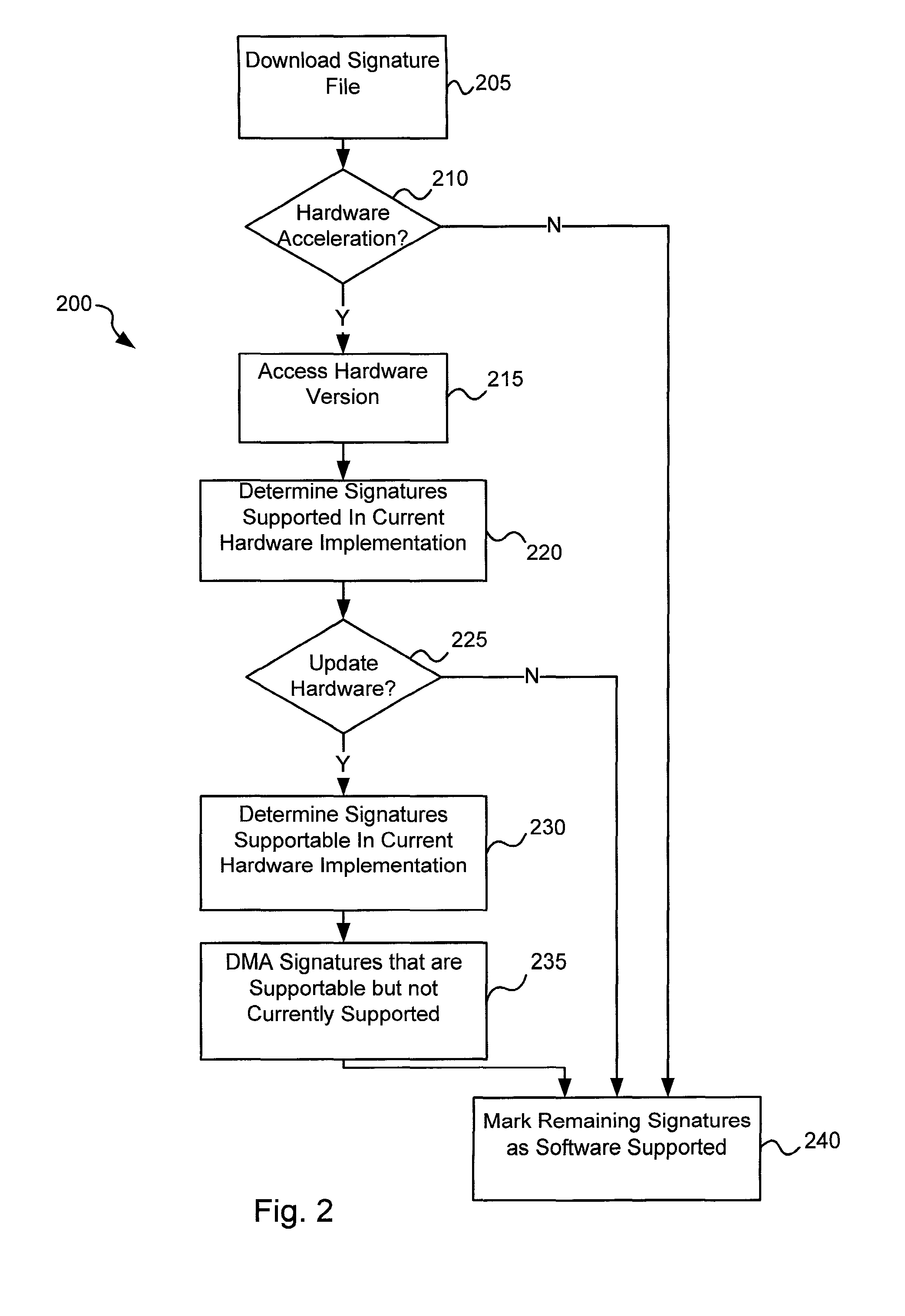
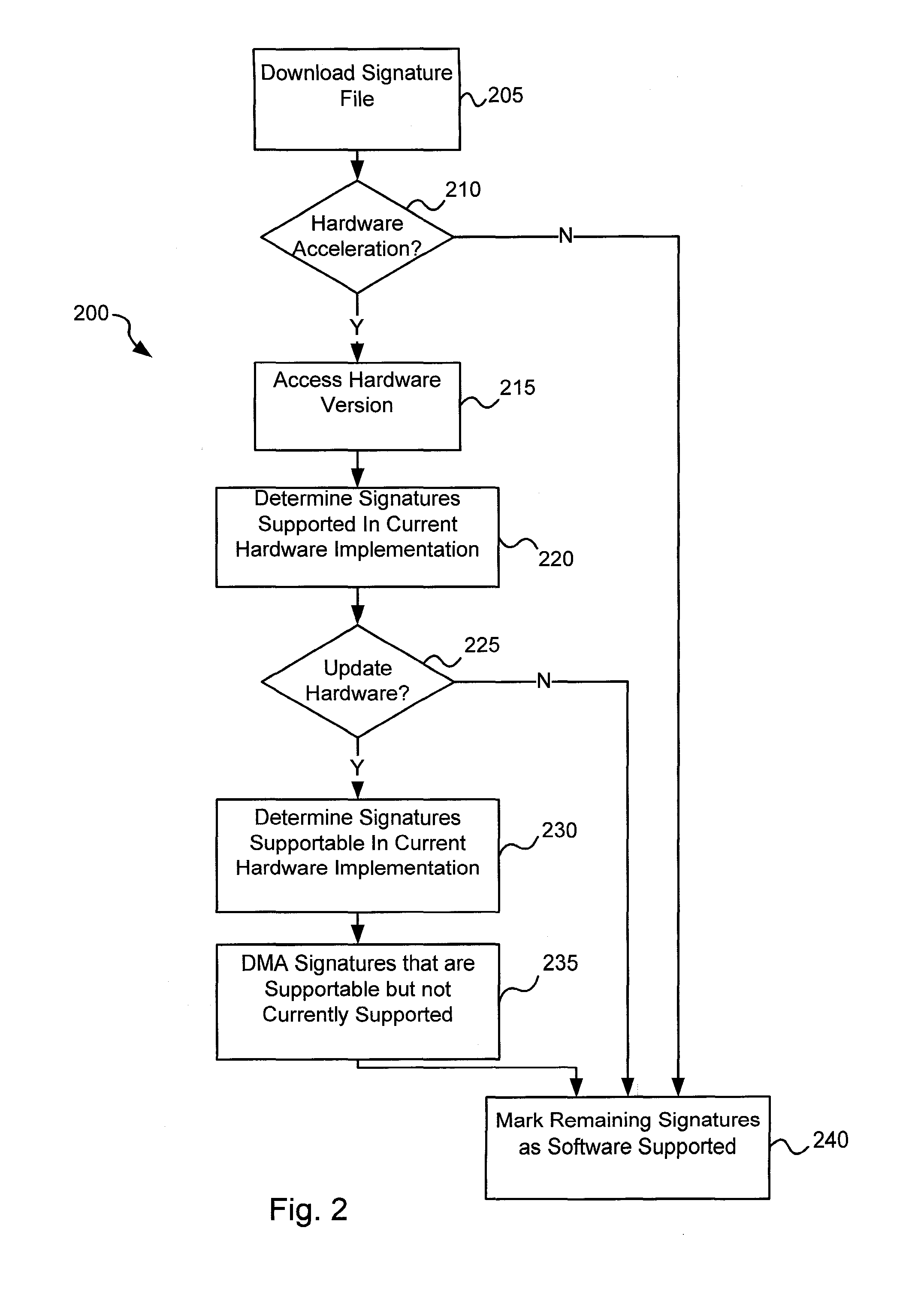
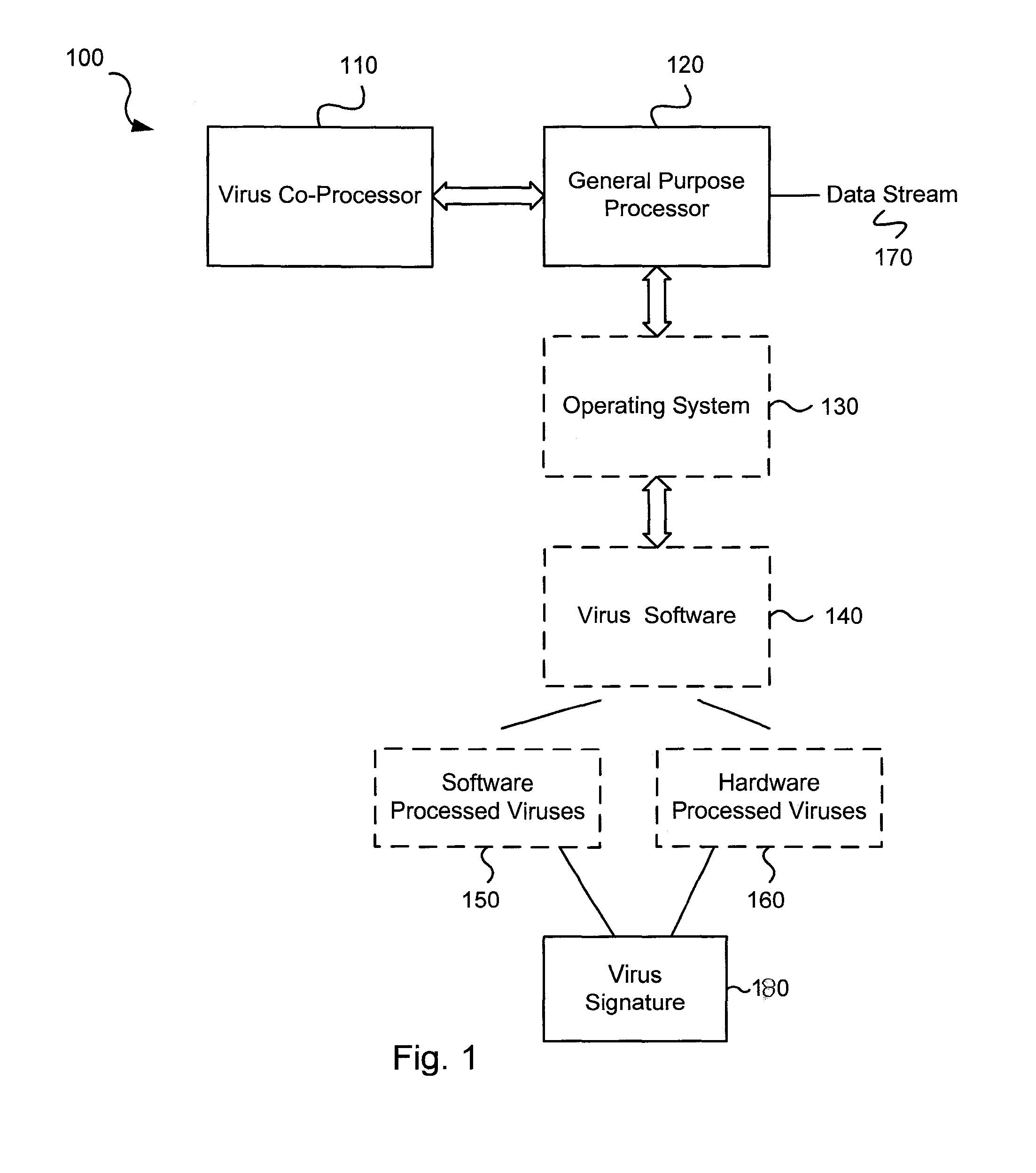
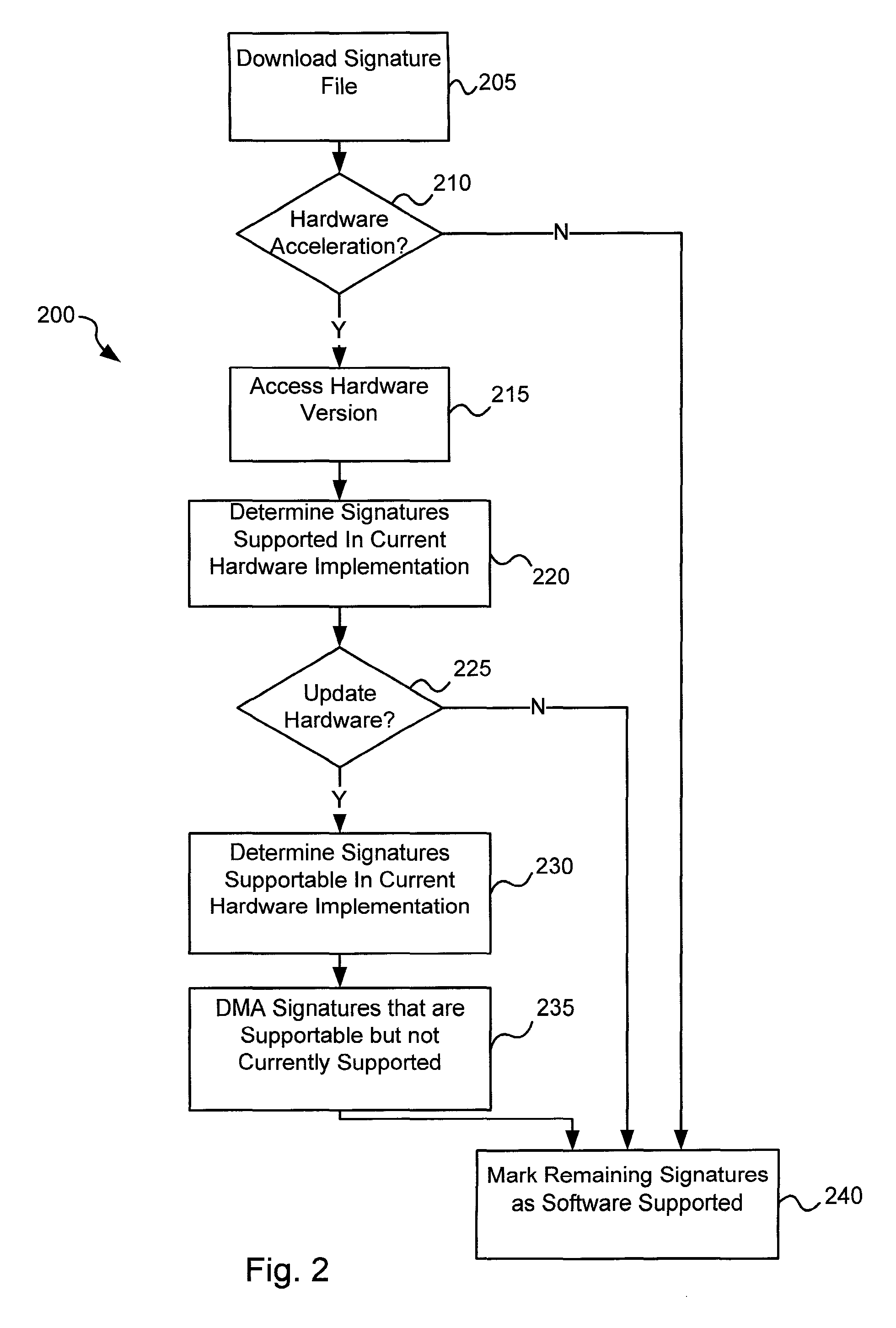
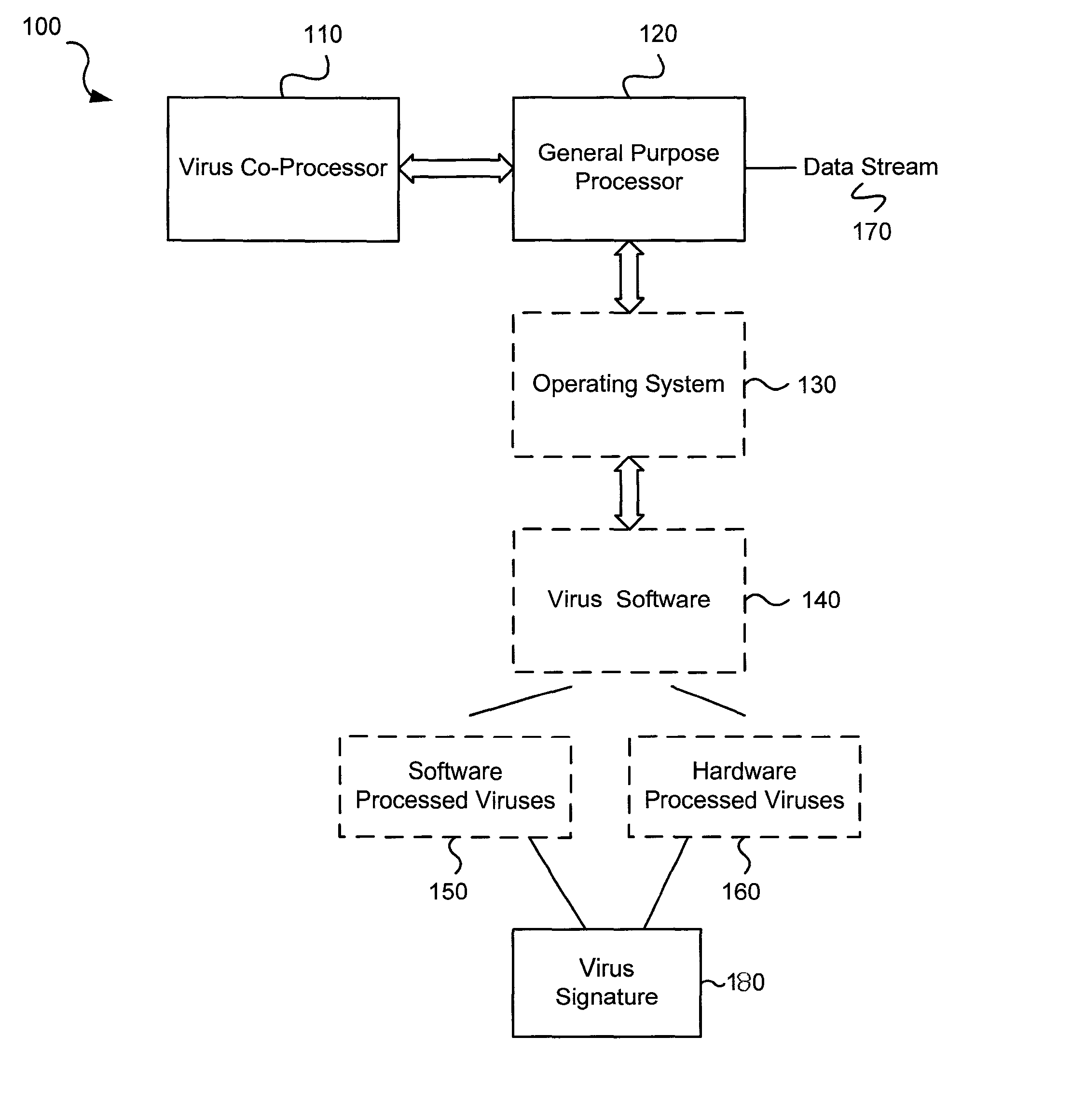
Various embodiments of the present invention provide circuits and methods for improved virus processing. As one example, a method for virus processing is disclosed that includes providing a first memory that includes a first set of virus signatures, and a second memory that includes a second set of virus signatures. In addition, a virus co-processor and a general purpose processor are provided. The virus co-processor is communicably coupled to the first memory, and the general purpose processor is communicably coupled to the virus co-processor and to the second memory. A subset of the second set of virus signatures that is not included in the first set of virus signatures is determined. The subset of the second set of virus signatures is processed on the general processor, and the first set of the virus signatures is processed on the virus co-processor.
Owner:FORTINET
Operation of a dual instruction pipe virus co-processor
Owner:FORTINET
Circuits and methods for efficient data transfer in a virus co-processing system
ActiveUS8286246B2Memory architecture accessing/allocationMemory loss protectionGeneral purposeData segment
Various embodiments of the present invention provide circuits and methods for improved virus processing. As one example, such methods may include providing a system memory, a general purpose processor and a virus co-processor. The methods further include receiving a data segment at the general purpose processor, and storing the data segment to the system memory using virtual addresses. The data segment is accessed from the system memory by the virus co-processor using the virtual addresses. The virus co-processor then scans the data segment for viruses and returns a result.
Owner:FORTINET
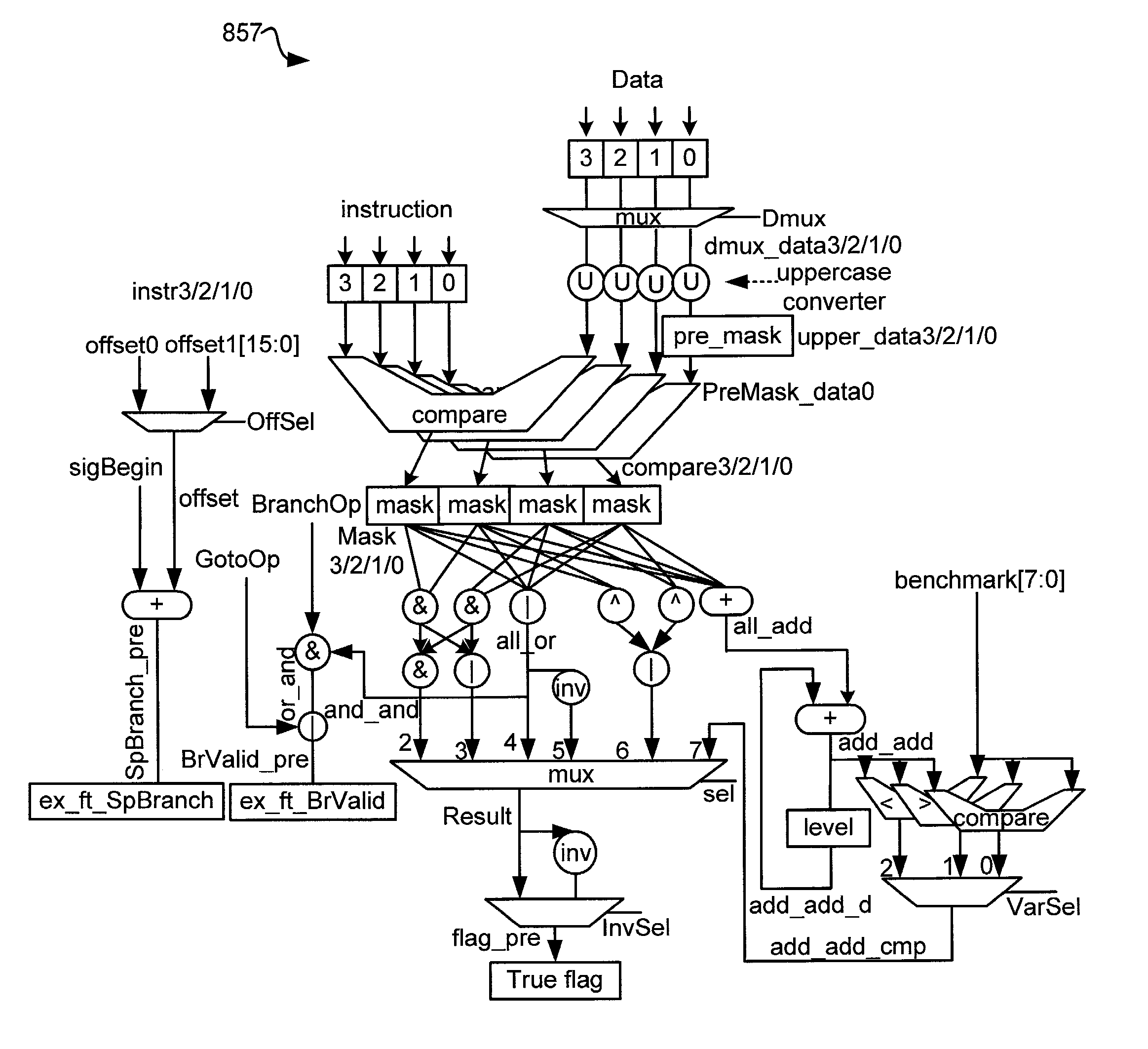
Virus co-processor instructions and methods for using such
ActiveUS8079084B1Memory loss protectionUnauthorized memory use protectionLoad instructionInstruction unit
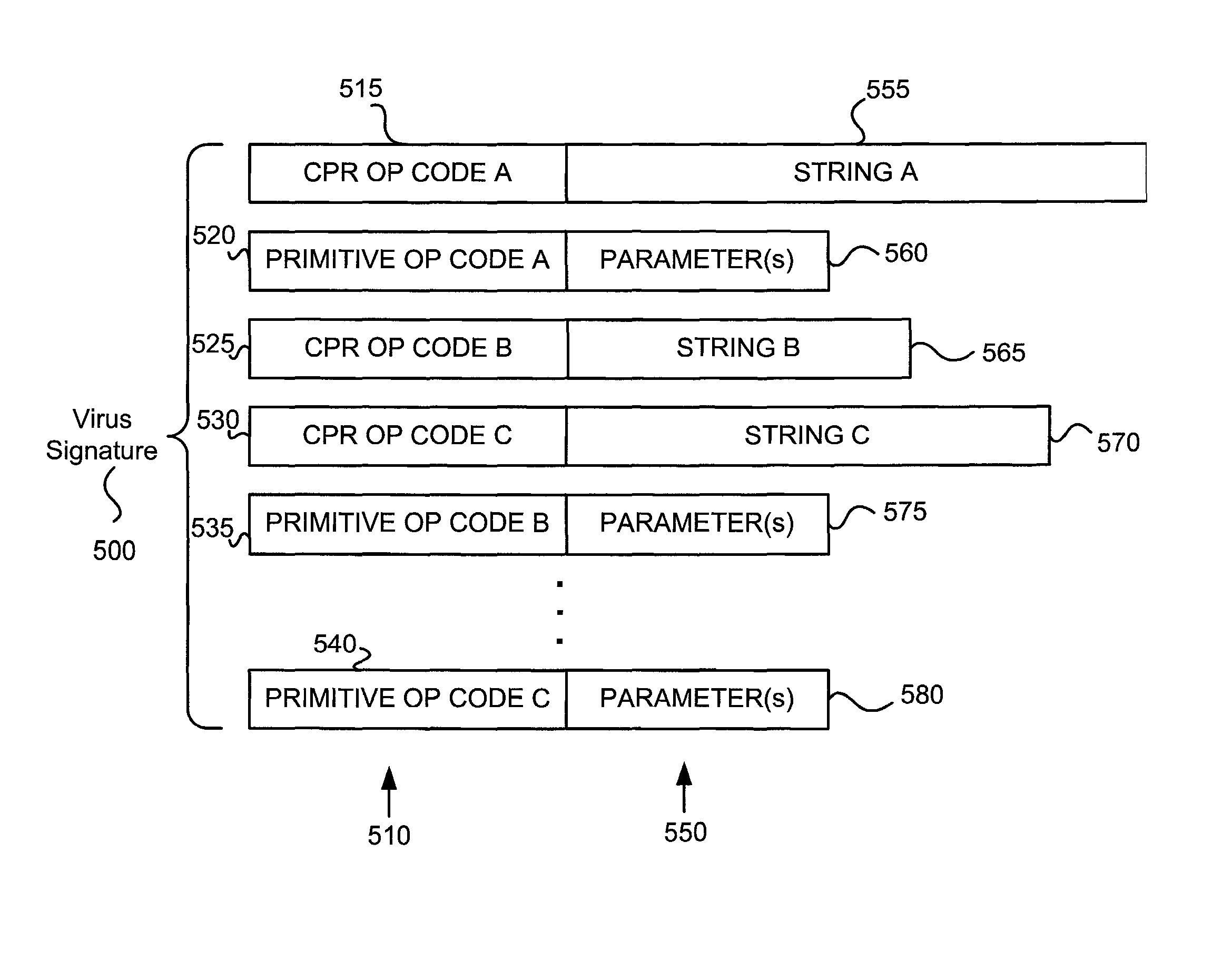
Various embodiments of the present invention provide elements that may be utilized for improved virus processing. As one example, a computer readable medium is disclosed that includes a virus signature compiled for execution on a virus co-processor. The virus signature includes at least one primitive instruction and at least one CPR instruction stored at contiguous locations in the computer readable medium. The CPR instruction is one of an instruction set that includes, but is not limited to: a compare string instruction, compare buffer instruction; perform checksum instruction; a seek instruction; and a test instruction. The primitive instruction may be, but is not limited to, an add instruction, a branch instruction, a jump instruction, a load instruction, a move instruction, a logic AND instruction, a logic OR instruction, and / or a logic XOR instruction.
Owner:FORTINET
Virus co-processor instructions and methods for using such
ActiveUS8239950B1Memory loss protectionUnauthorized memory use protectionGeneral purposeComputer hardware
Circuits and methods are provided for detecting, identifying and / or removing undesired content. According to one embodiment, a method for virus processing is provided. A general purpose processor, communicably coupled to a virus processing hardware accelerator, receives a data segment. The general purpose processor causes the data segment to be stored to a first memory. The general purpose processor directs the virus processing hardware accelerator, communicably coupled to the first memory and to the second memory, to perform a virus scan of the data segment based on one or more virus signatures stored in a second memory. The first memory includes a first virus signature compiled for execution on the general purpose processor. The second memory includes virus signatures, each of which include at least one primitive instruction and at least one Content Pattern Recognition (CPR) instruction stored at contiguous locations, compiled for execution by the virus processing hardware accelerator.
Owner:FORTINET
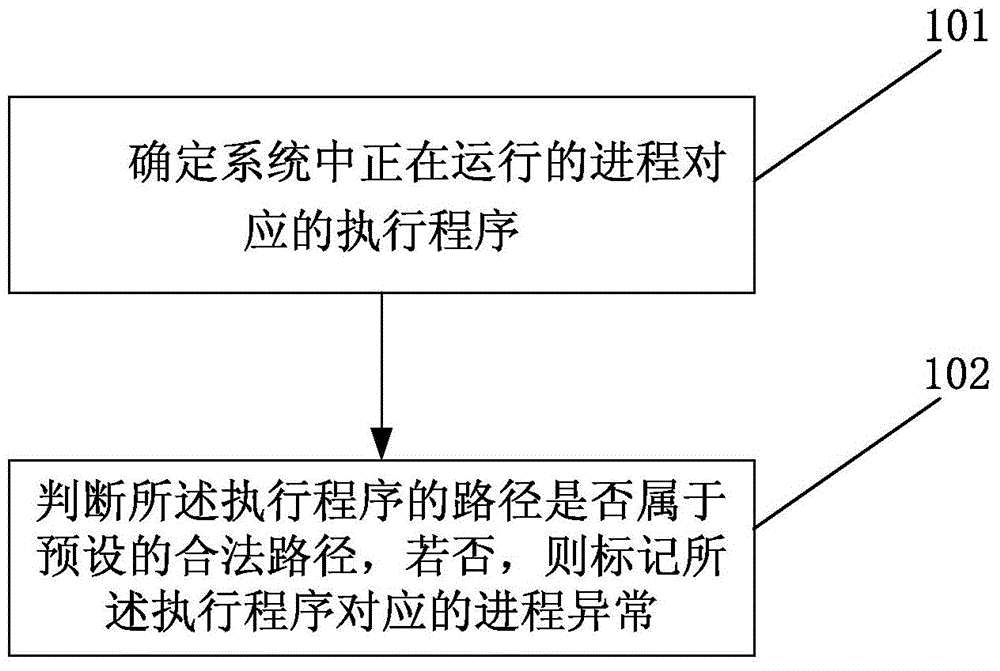
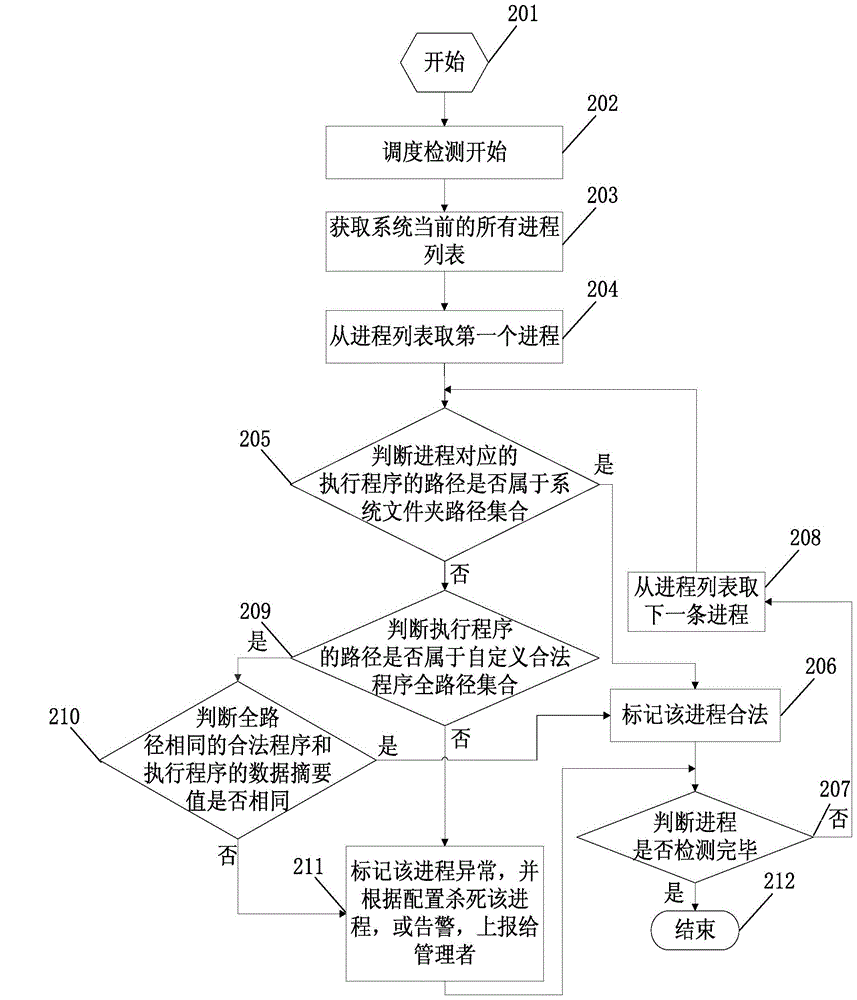
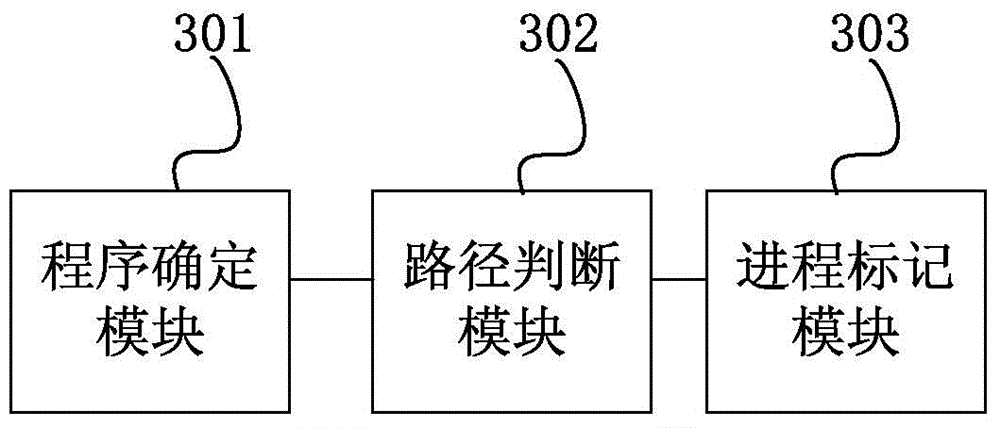
Abnormal process detection method and apparatus
The present invention discloses an abnormal process detection method and apparatus. The abnormal process detection method provided by the present invention comprises: determining an executive program corresponding to a running process in an apparatus; and determining whether a path of the executive program belongs to a preset valid path, if no, marking that the process corresponding to the executive program is abnormal. According to the method provided by the present invention, the preset valid path is set in advance, and is a path for storing a valid program. If the executive program corresponding to a currently allowed process is not in the valid path, it proves that the executive program of the process is invalid, and therefore, the process is abnormal. According to the method provided by the present invention, a state of the process can be determined only by determining whether the path of the executive program of the process belongs to the preset valid path, so as to determine whether the process is a virus process, thereby searching and killing a virus. Therefore, according to the abnormal process detection method provided by the present invention, a virus can be searched and killed without knowing a property of the virus.
Owner:ZTE CORP
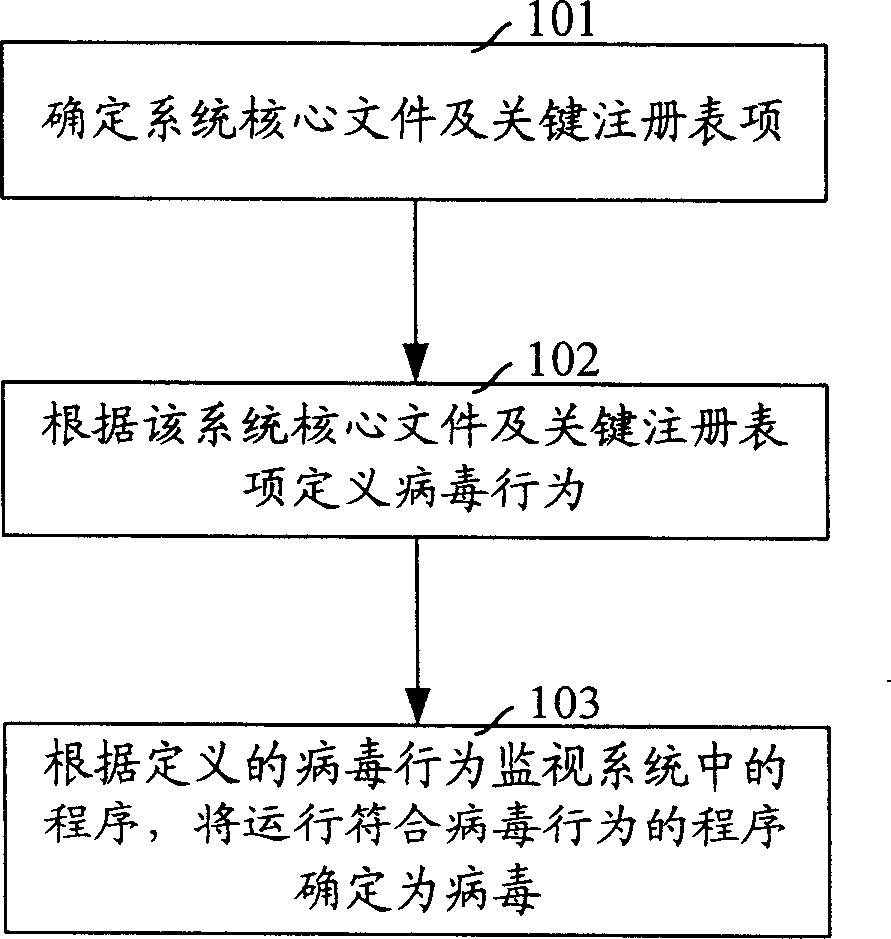
Virus processing method
InactiveCN1889004AImprove prevention capabilitiesReduce system riskDigital data processing detailsComputer scienceSystem safety
The invention discloses a virus processing method. It determines the key data relates to the system safety in the system firstly and regards the operation to the key data as the virus behavior; then to judge the working procedure. If it is the virus, then the procedure is the virus procedure. The invention can prevent the unknown virus to attack the system, so it can decrease the hazard to the system and the user data by the virus.
Owner:LENOVO (BEIJING) CO LTD
Efficient data transfer in a virus co-processing system
ActiveUS8560862B1Memory architecture accessing/allocationMemory loss protectionGeneral purposeVirtual memory
Circuits and methods are provided for detecting, identifying and / or removing undesired content. According to one embodiment, a method for virus co-processing is provided. A general purpose processor stores a data segment to a system memory of the general purpose processor using virtual addresses. A virus processing hardware accelerator coupled to the general purpose processor via an interconnect bus accesses the data segment by performing direct virtual memory addressing of the system memory using the virtual addresses. The virus processing hardware accelerator scans the data segment for viruses by executing pattern comparisons against the data segment. The virus processing hardware accelerator returns a result of the scanning to the general purpose processor by writing the result to the system memory. The general purpose processor may scan the data segment for viruses of a first type in parallel or serially with virus processing hardware accelerator scanning for viruses of a second type.
Owner:FORTINET
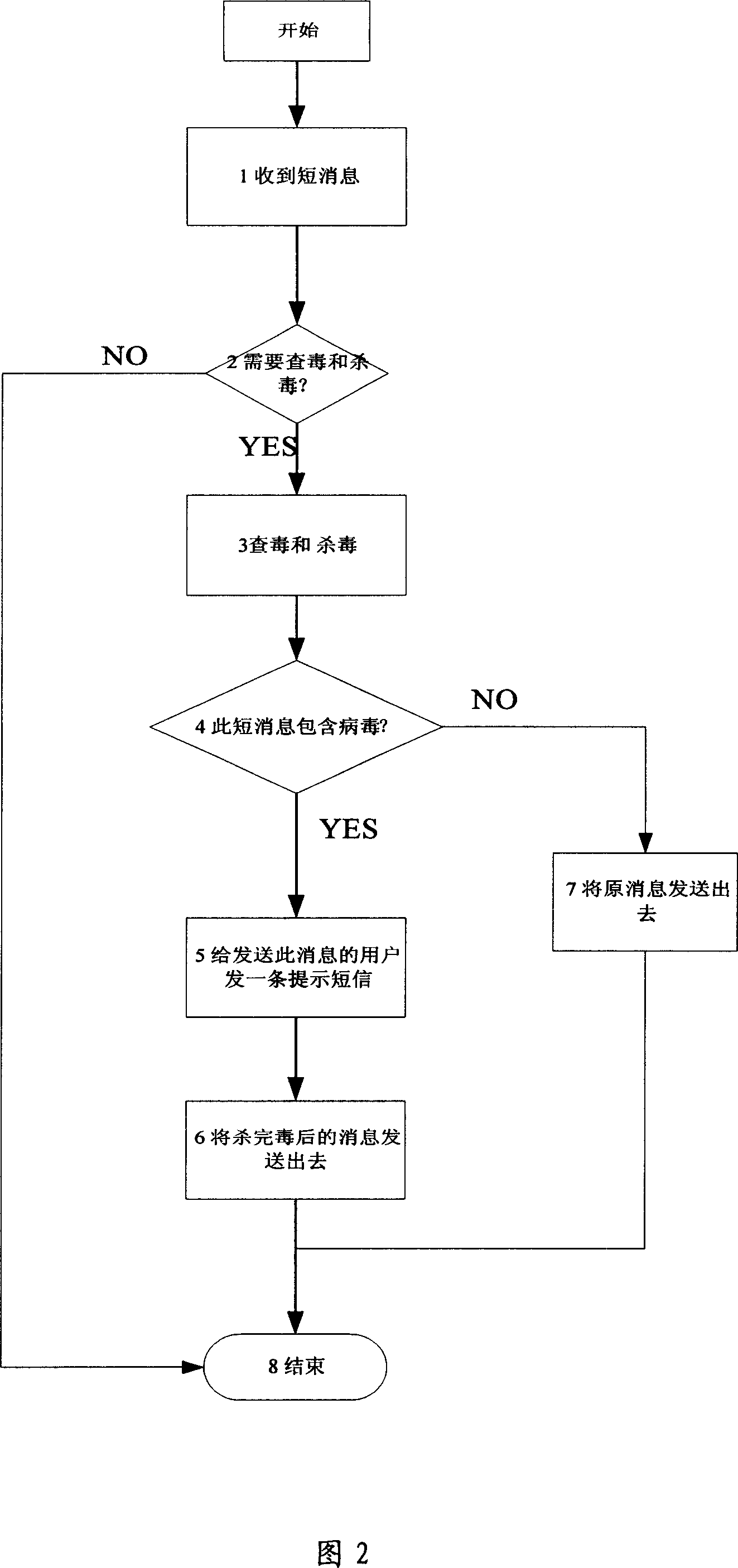
Method, device and storage medium for processing virus
ActiveUS20140366138A1Avoid spreadingMemory loss protectionError detection/correctionComputer scienceVirus processing
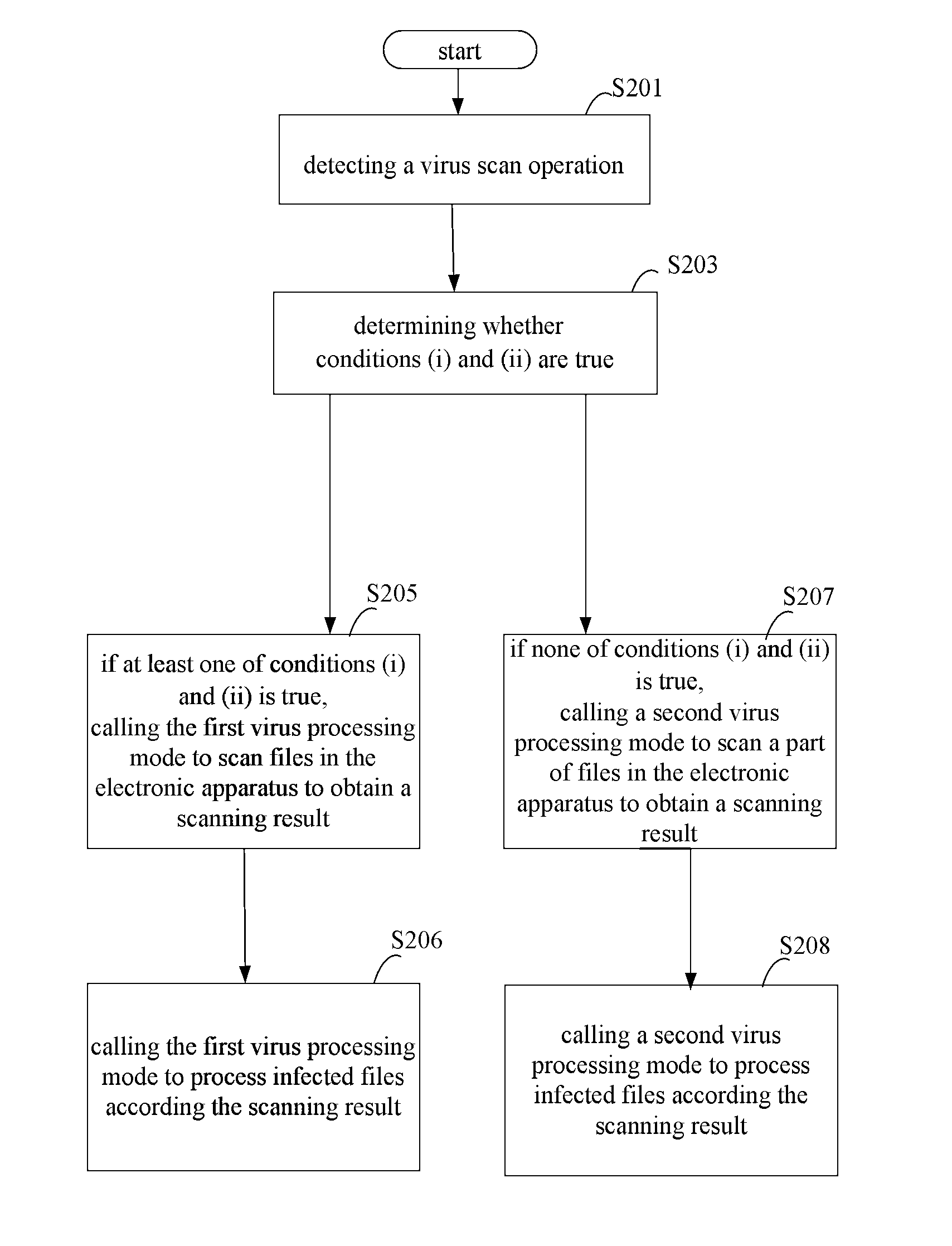
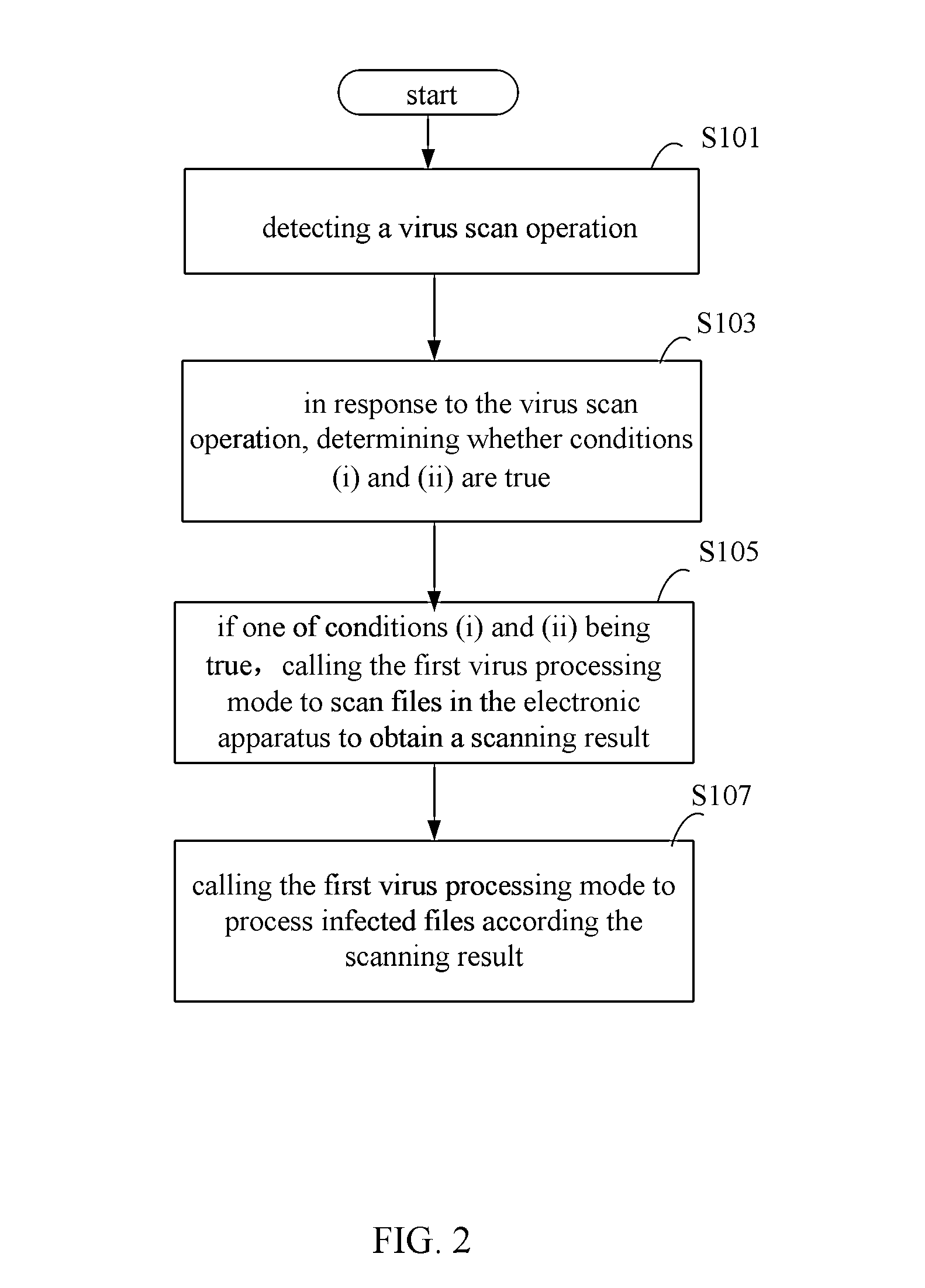
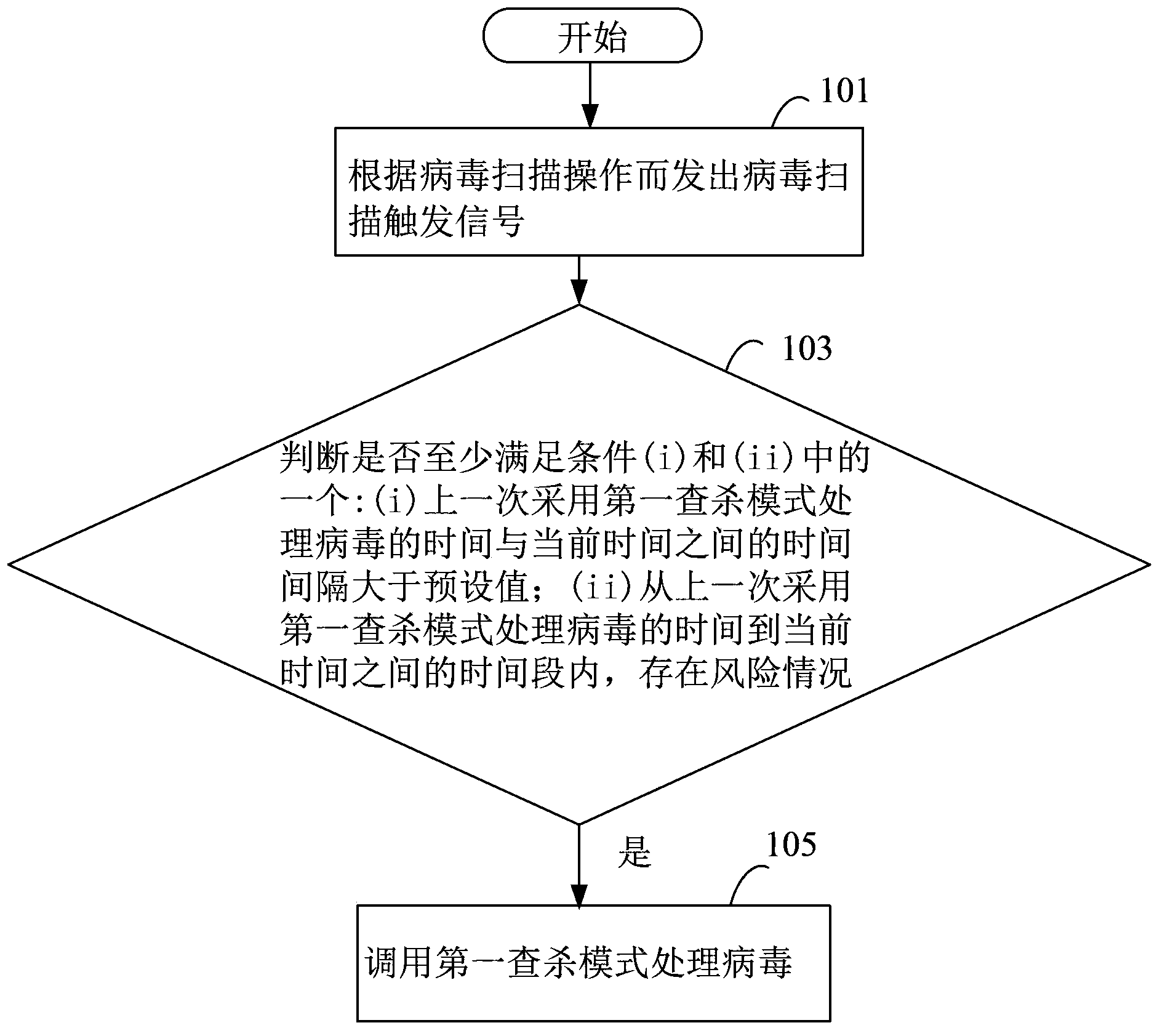
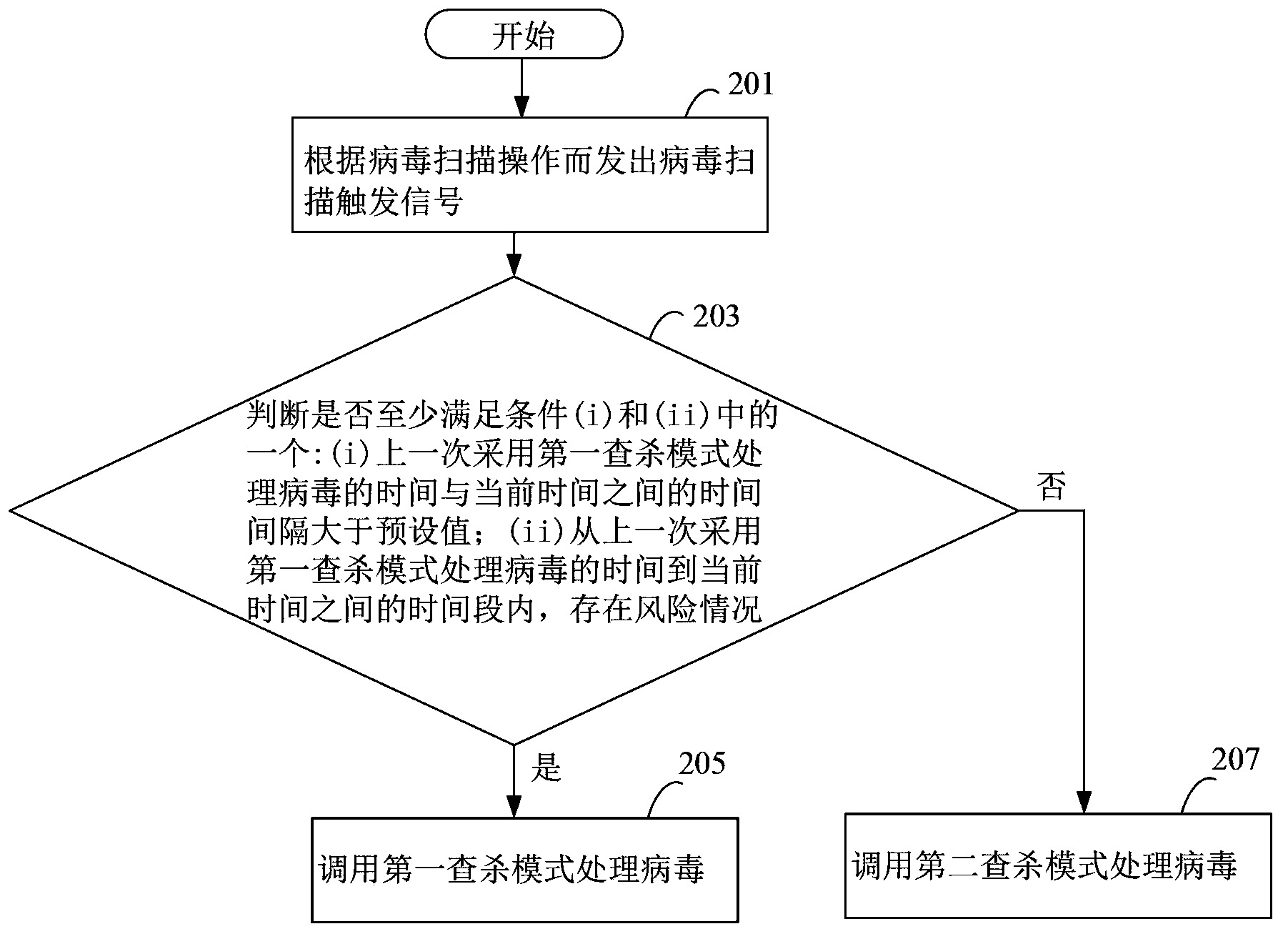
The present disclosure relates to a method, a device and a storage medium for processing virus which can automatically distinguish which of processing mode is best for the current status of the electronic apparatus. The method includes: detecting a virus scan operation; in response to the virus scan operation, determining whether conditions (i) and (ii) are true, wherein the condition (i) is true when a time interval between a last time of processing virus using a first virus processing mode and the current time is larger than a preset interval, the condition (ii) is true when at least one of risk situations exist during a time period between the last time of processing virus using the first virus processing mode and the current time; if one of conditions (i) and (ii) being true, calling the first virus processing mode to scan files in the electronic apparatus.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Remote antivirus method
ActiveCN102945350ADelete make sureImprove antivirus effectPlatform integrity maintainanceTransmissionSecurity softwarePersonal computer
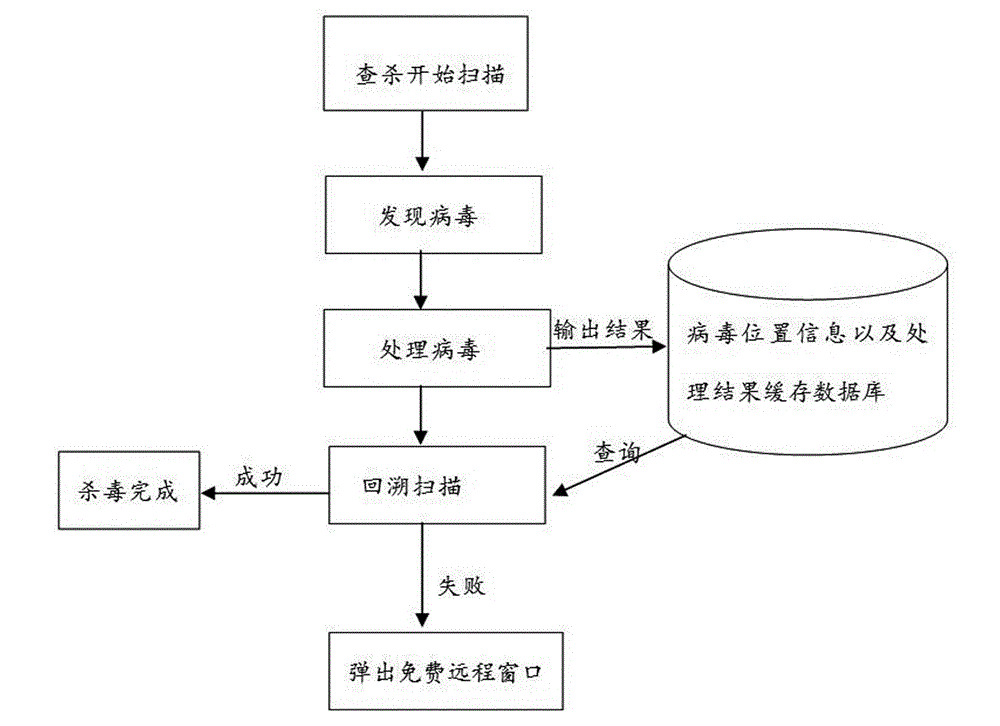
The invention provides a remote antivirus method, which comprises the following steps: processing virus after finding out the virus, and outputting virus behavior information and processed results to a cache database to establish an antivirus record; after finishing said virus processing operation, calling a scanning engine to perform scanning antivirus (backtracking antivirus) on the virus again; after performing the backtracking antivirus, judging antivirus results; reporting to a user that the antivirus is completed and finishing the operation if the virus is thoroughly cleaned; and triggering a remote help module so that a security software engineer performs manual antivirus in a personal computer by the remote help module if the virus is unable to be thoroughly cleaned. Compared with a traditional antivirus mechanism simply relying on software, the method provided by the invention is characterized by directly using professional knowledge of the professional security engineer to manually kill the virus in the personal computer and greatly enhancing the capability of the antivirus software to kill the virus and protect the personal computer.
Owner:ZHUHAI BAOQU TECH CO LTD
Virus processing method and device capable of aiming at file package
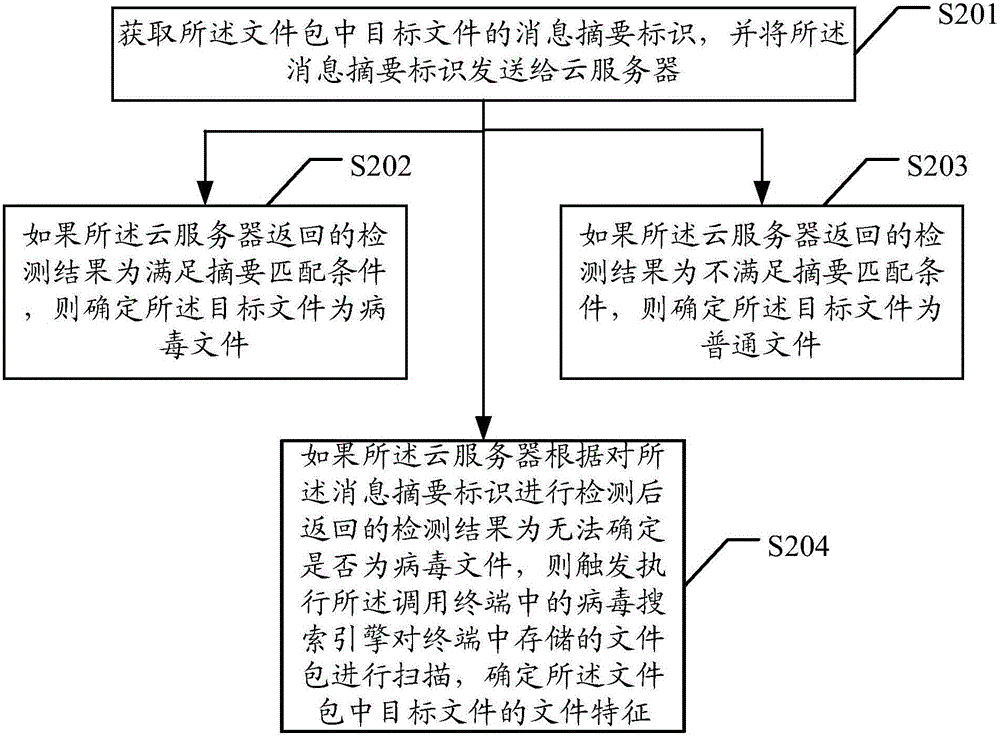
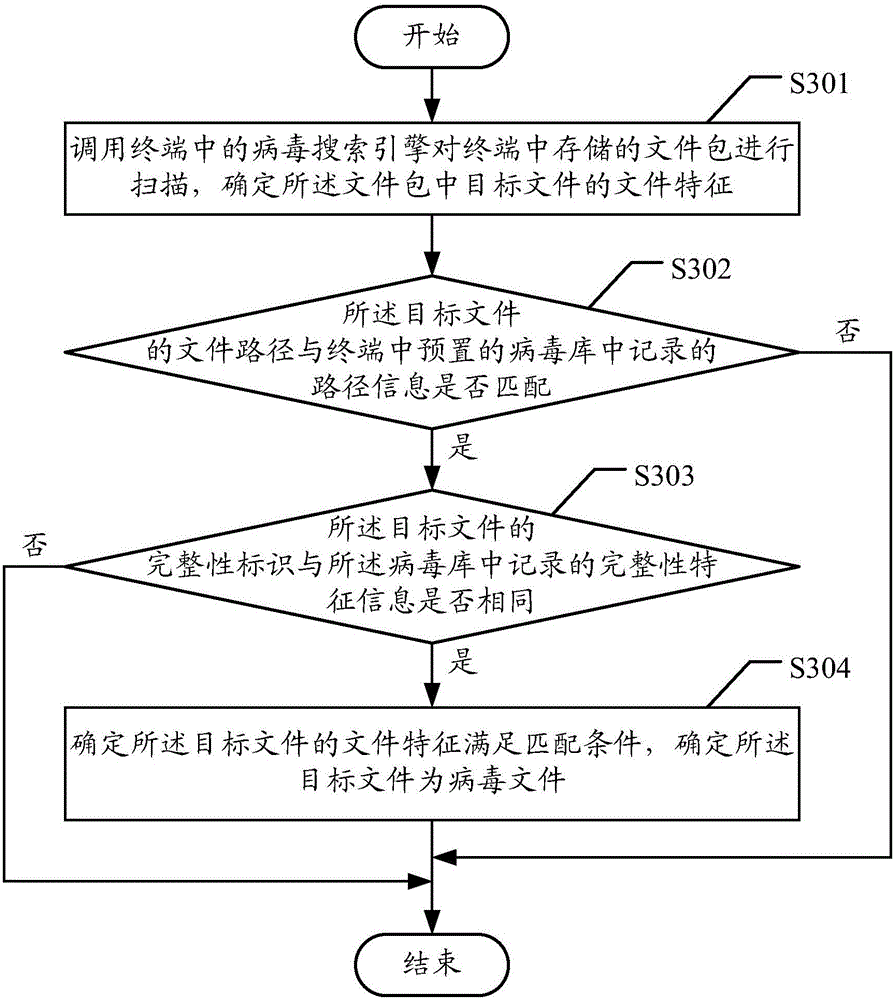
ActiveCN106709341AImprove the kill rateReduce false positivesPlatform integrity maintainanceFalse alarmPackage store
The embodiment of the invention discloses a virus processing method and device capable of aiming at a file package. The method comprises the following steps that: calling a virus search engine in a terminal to scan the file package stored in the terminal, and determining the file characteristics of a target file in the file package, wherein the file characteristics at least comprise the file path of the target file and / or the integrity identification of the target file; according to the characteristic information in a preset virus reservoir in the terminal, carrying out detection comparison on the determined file path and / or integrity identification, and when a detection comparison result shows that the file characteristics meet a matching condition, determining the target file as a virus file; and according to a virus checking and killing rule, carrying out checking and killing processing on the virus file. When the method is adopted, the virus checking and killing success rate of the file package can be conveniently and quickly improved, a variant sample checking and killing rate is improved, and false alarms are reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
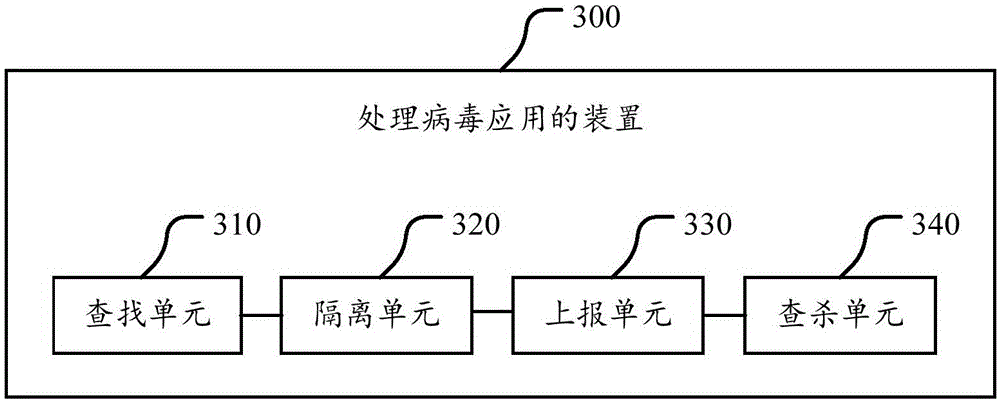
Method, device and mobile terminal for processing virus applications
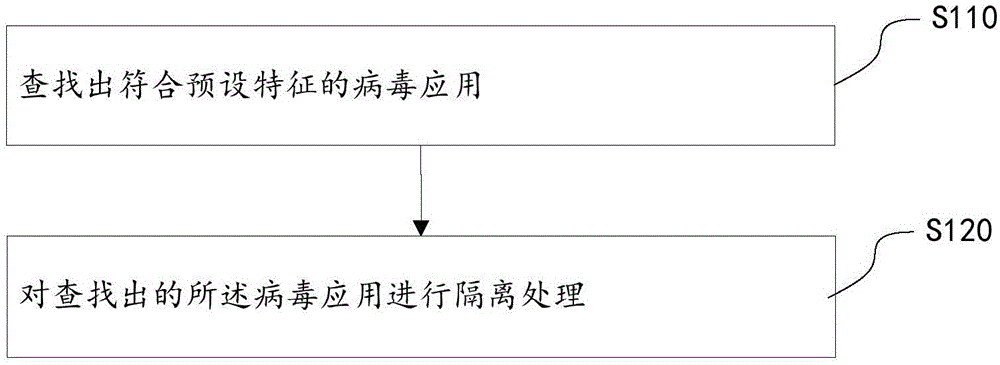
InactiveCN105095754AStop runningAvoid harmPlatform integrity maintainanceComputer scienceVirus processing
The invention discloses a method, device and mobile terminal for processing virus applications. The method comprises the following steps: searching for virus applications which conform to a preset feature; and performing isolation processing on the searched virus applications. According to the technical scheme of the invention, certain stubborn virus applications are isolated when the virus applications cannot be deleted, so that the virus applications are prevented from running; the harms of the virus applications to a user are avoided; and a rapid virus processing scheme and a safer use environment are provided for the user.
Owner:BEIJING QIHOO TECH CO LTD +1
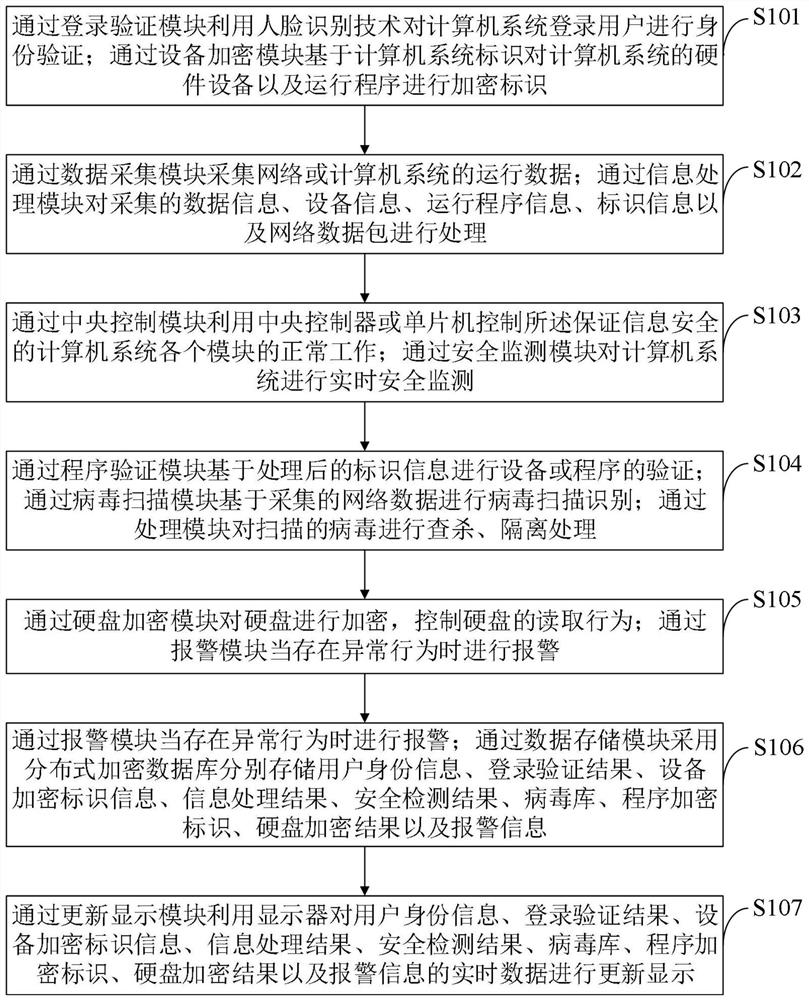
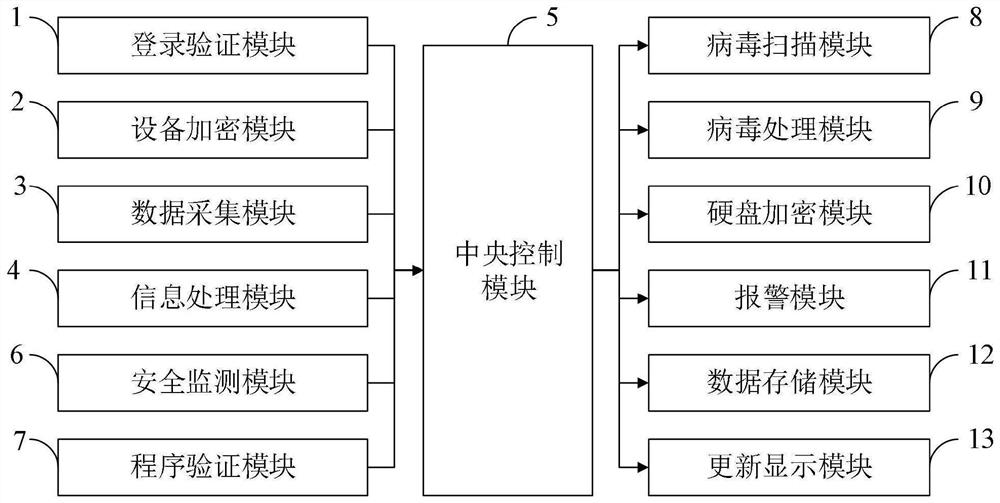
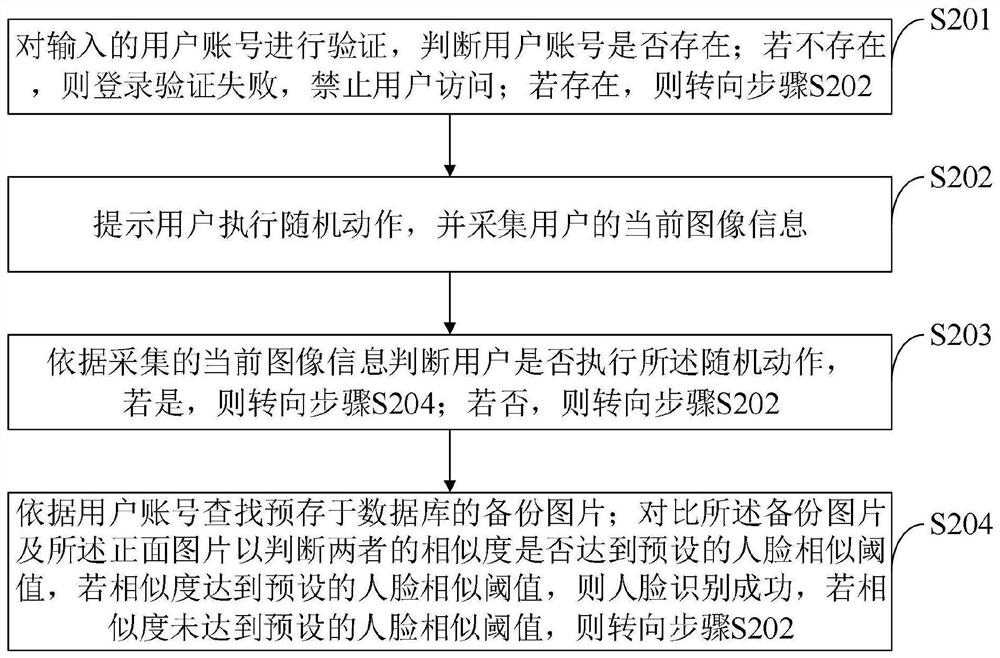
Computer system for ensuring information security and control method thereof
ActiveCN112487383AEnsure information securityGuarantee the safety of useCharacter and pattern recognitionDigital data protectionInformation processingData acquisition
The invention belongs to the technical field of computer security, and discloses a computer system for ensuring information security and a control method thereof. The computer system capable of ensuring information security comprises a login verification module, an equipment encryption module, a data acquisition module, an information processing module, a central control module, a security monitoring module, a program verification module, a virus scanning module, a virus processing module, a hard disk encryption module, an alarm module, a data storage module and an update display module. According to the invention, the use security of the computer can be effectively ensured, data leakage and network virus invasion are prevented, and the information security of a user is effectively ensured. The computer system capable of ensuring the information security can protect the computer data security, effectively protect viruses and ensure the hard disk data security; by performing autonomousencryption verification on the hard disk, the tedious operation of manual password input is avoided, the encryption verification efficiency is improved, and the data security of the hard disk can alsobe ensured.
Owner:CHONGQING UNIV OF EDUCATION
Virus processing method and device
ActiveCN104239790AStop the spreadFast automatic resolutionPlatform integrity maintainanceTime segmentKilled process
The invention discloses a virus processing method and device, and belongs to the safety field. The virus processing method comprises the steps of: sending a virus scanning trigger signal based on a virus scanning operation; receiving the virus scanning trigger signal and judging whether at least one of conditions (i) and (ii) below is satisfied: (i) the time interval between the time taken for processing the virus by adopting a first searching and killing mode in the last time and the current time is greater than a preset value, and (ii) a risk condition exists within the time bucket between the time taken for processing the virus by adopting the first searching and killing mode in the last time and the current time; if at least one of the conditions (i) and (ii) is satisfied, calling the first searching and killing mode to process the virus. Through automatic selection of the virus processing mode, which searching and killing mode is most suitable for the current condition of an electronic device can be recognized rapidly and automatically in the virus searching and killing process, and the viral transmission is prevented in time.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Virus searching and killing method, device, equipment and storage medium
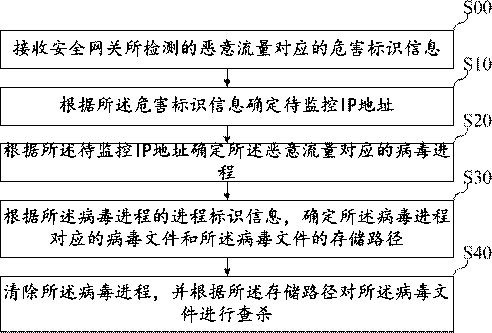
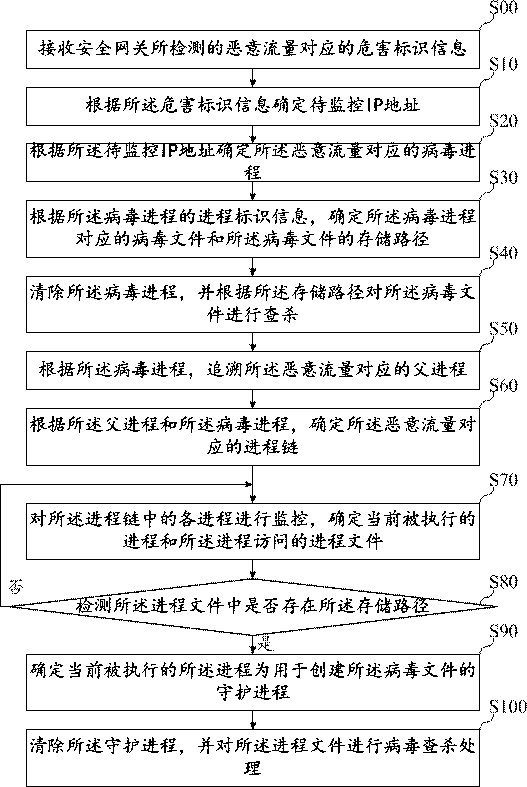
ActiveCN110717183AKilling implementationGood killing effectPlatform integrity maintainanceVirus typeIp address
The invention belongs to the technical field of information safety, and discloses a virus searching and killing method, a virus searching and killing device, equipment and a storage medium. The methodcomprises the following steps: receiving hazard recognition information corresponding to malicious traffic detected by a safety gateway; determining a to-be-monitored IP address according to the hazard recognition information; determining a virus process corresponding to the malicious traffic according to the IP address to be monitored; determining a virus file corresponding to the virus processand a storage path of the virus file according to the process recognition information of the virus process; and clearing the virus process, and searching and killing the virus file according to the storage path. By means of the mode, limitation of virus types is avoided, viruses are searched and killed from the source, and therefore the searching and killing effect on the viruses is greatly improved.
Owner:SANGFOR TECH INC
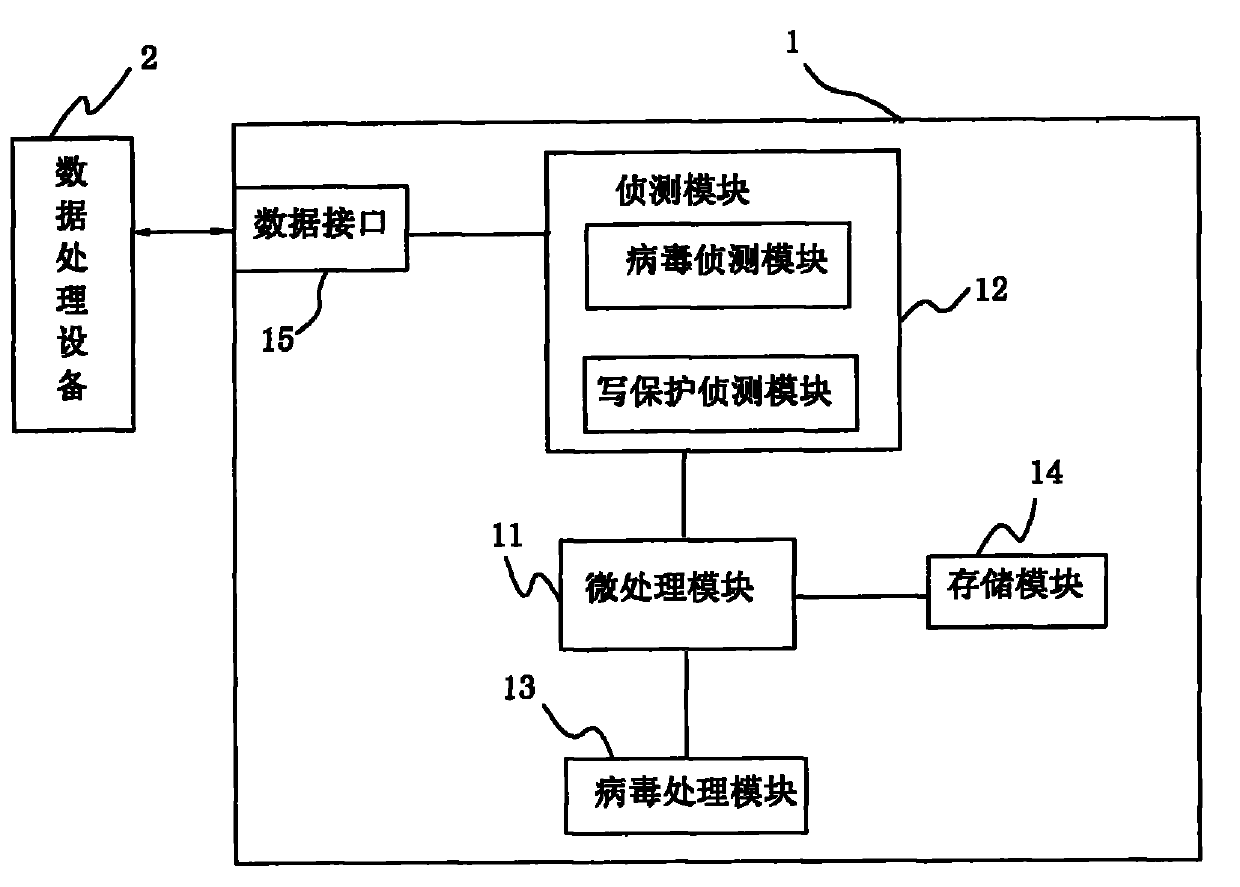
Anti-computer virus mobile storage apparatus and anti-computer virus method
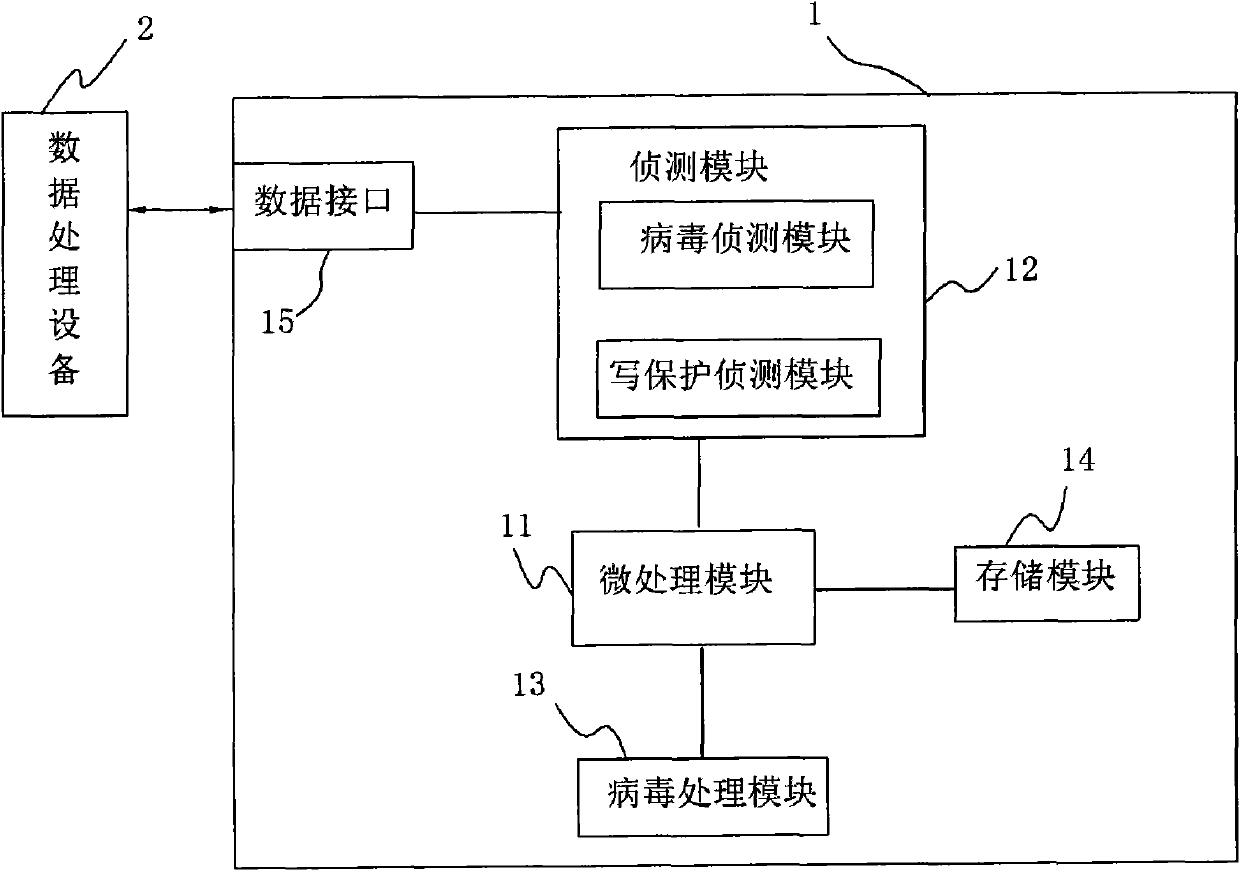
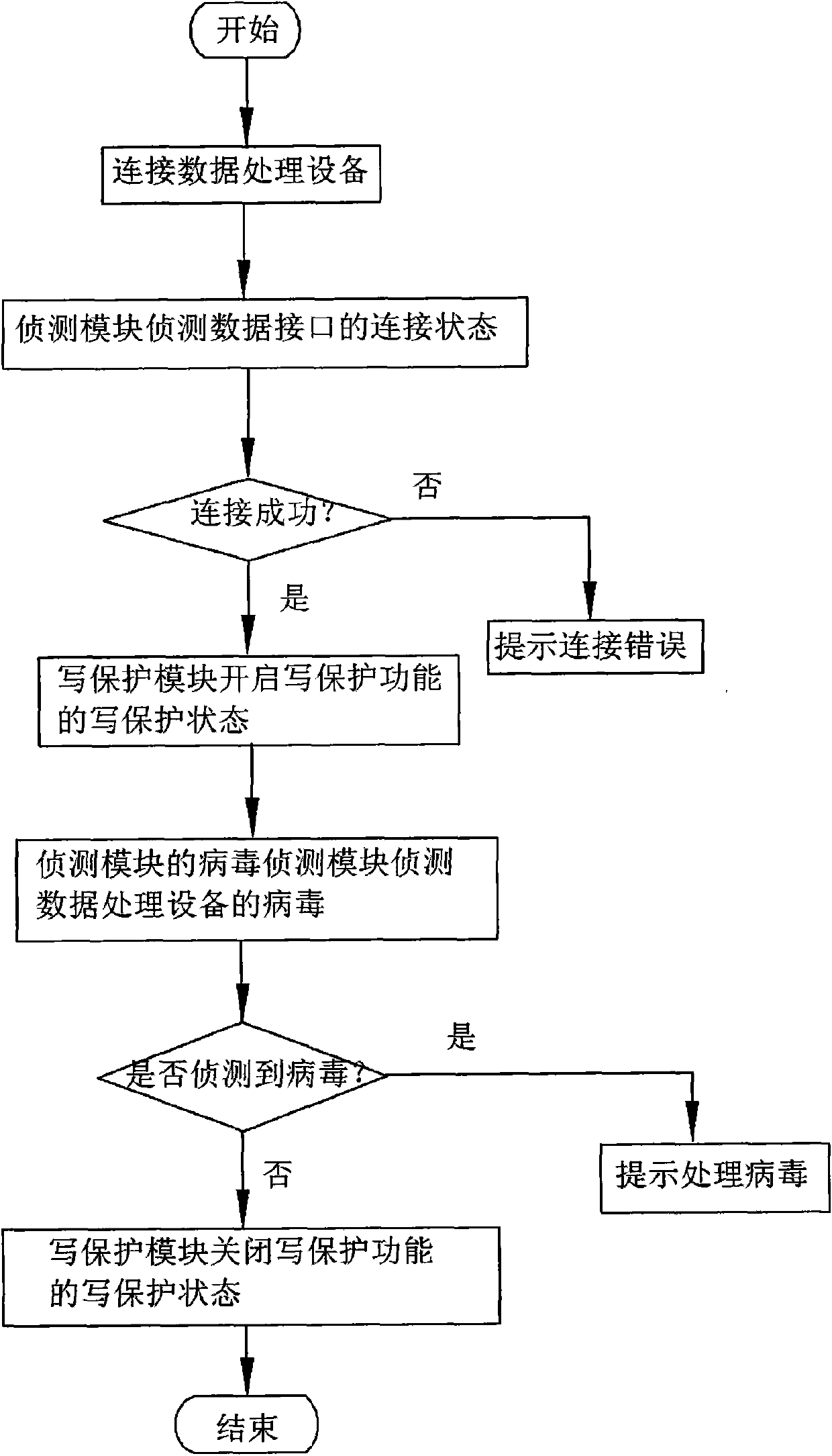
InactiveCN102023933AAvoid transmissionPrevent proliferationUnauthorized memory use protectionWrite protectionRemovable media
The invention discloses an anti-computer virus mobile storage apparatus and an anti-computer virus method. The mobile storage apparatus comprises a virus detecting module and a virus processing module. The original state of the mobile storage apparatus is set as a write-protection state through the processing module. After the mobile storage apparatus is connected with a piece of data processing equipment and safety is determined through scan programs, the virus processing module calls a write-protection module of a micro processing module to close the write-protection function, and furthermore the mobile storage apparatus can carry out data transmission with the data processing equipment. The invention adds the detecting module and the virus processing module to the mobile storage apparatus, which prevents the virus from passing through data read-write transmission of the mobile storage apparatus, raises data security of the mobile storage apparatus and avoids further virus infection.
Owner:AIGO ELECTRONICS TECH
Virus purifying and amplification method
The invention discloses a virus purifying and amplification method. The method comprises steps: firstly, cell fragments in viruses are removed; secondly, the viruses are captured through a chromatography; thirdly, the viruses captured in the second step are processed by nucleases, host cell nucleic acids in the viruses are subjected to enzymolysis; fourthly, the viruses processed in the third steps are subjected to fined purifying, host cell protein and nucleic acid fragments are removed. The chromatography is employed to achieve virus purifying and amplification, and optimization is carried out at the chromatography column and chromatography filling material aspects. When the provided method is compared with traditional virus purifying method, the purity and the titer of the viruses after purifying are raised, and the provided method has advantages of easy amplification and low cost. The obtained viruses with low residues, high purity and high titer are used for virus removal verification, a flux of a virus filtering membrane can be raised, and the cost investment of the virus filtering membrane is lowered.
Owner:SUZHOU YAOMING KANGDE INSPECTION TESTING +1
Method for searching and killing virus of network equipment
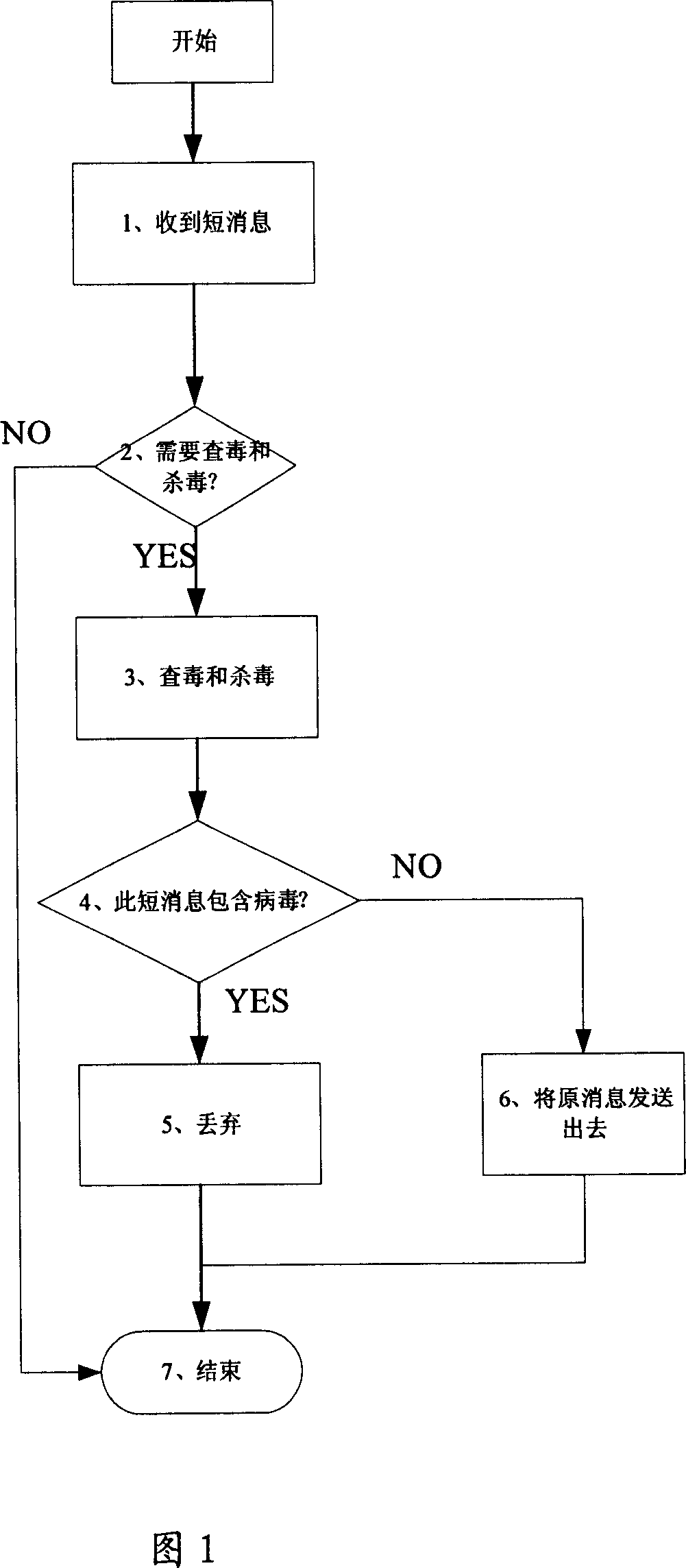
InactiveCN1983927AImprove securityReduce attackDigital data processing detailsUser identity/authority verificationAnti virusSelf reduction
This invention is concerned with the method for checking and killing virus for network equipment includes: 1) the network equipment receives the information and calls the checking and killing virus module to processes the virus processing; 2) the checking and killing virus module sends the feedback information to the network equipment information handling module after the virus treatment for continuing disposal. The invention can use the network equipment checking and killing virus technique project on the information that sends to the terminal, reduce the attack to the terminal equipment by the virus and the maintenance the cost for the terminal, improve the reliability of the terminal; because of the equipment includes anti-virus software, and virus self-reduction, which reduces attack from the virus to the equipment, improve network safety.
Owner:HUAWEI TECH CO LTD
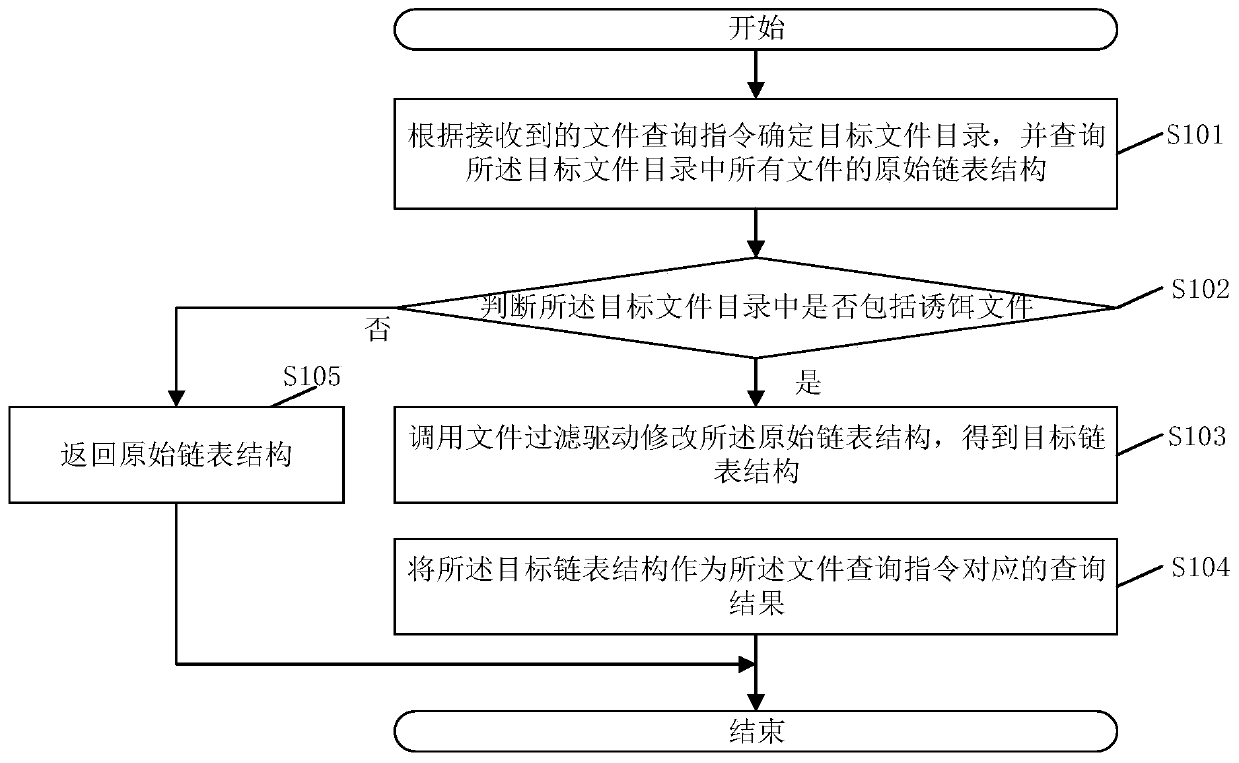
Bait file hiding method and device, electronic device and storage medium
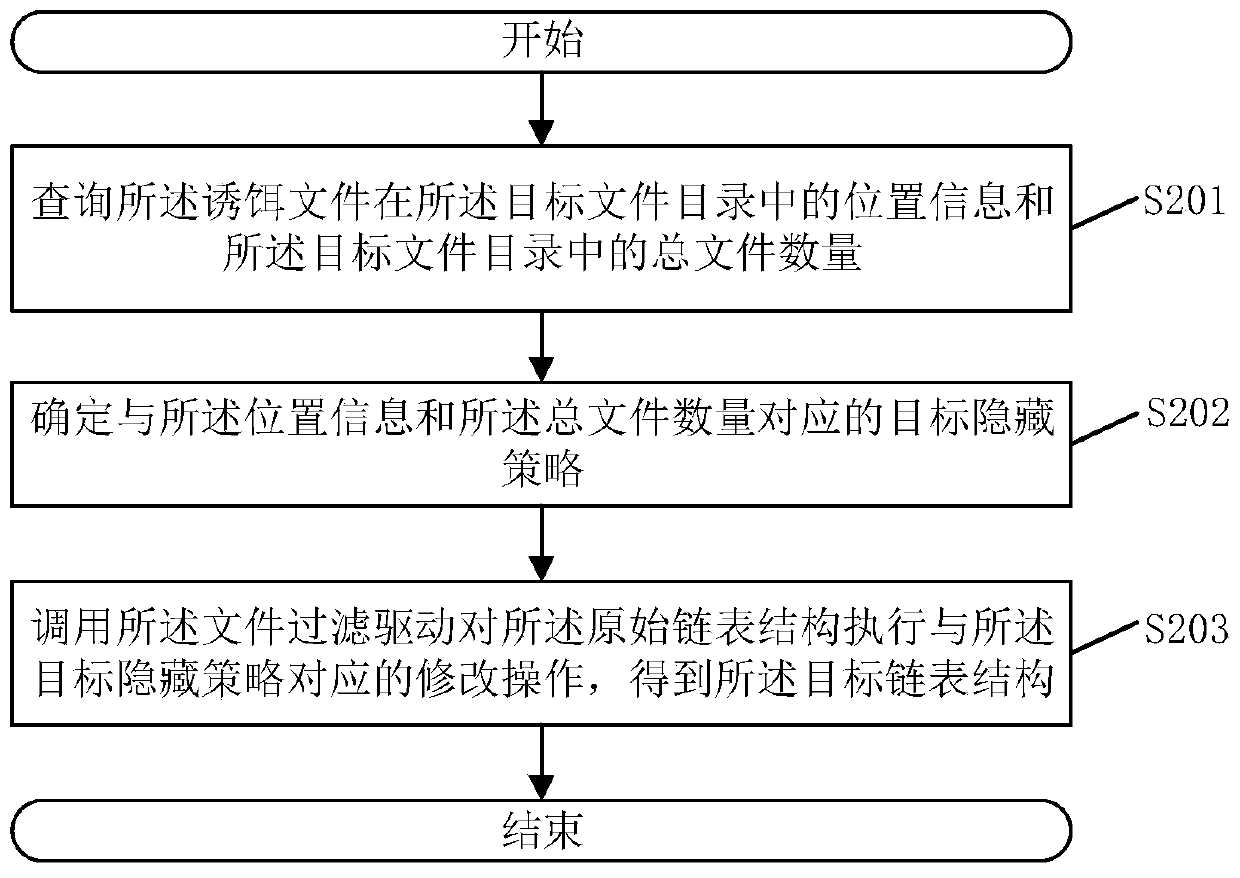
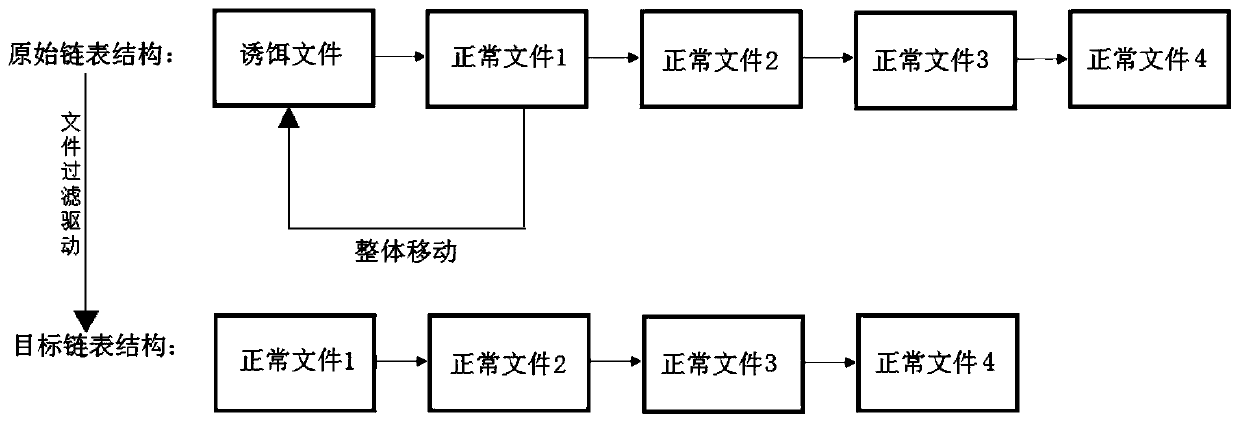
InactiveCN110826070AReduce stepsImprove concealmentDigital data protectionPlatform integrity maintainanceDirectoryDatabase
The invention discloses a bait file hiding method, and the bait file hiding method comprises the steps: determining a target file directory according to a received file query instruction, and queryingthe original linked list structures of all files in the target file directory; judging whether the target file directory comprises a bait file or not; wherein the bait file is a file used for detecting a virus process; if yes, calling a file filtering driver to modify the original linked list structure to obtain a target linked list structure; wherein the target linked list structure does not include file linked list information of the bait file; and taking the target linked list structure as a query result corresponding to the file query instruction. The method can improve the concealment ofthe bait file and prevent a user from deleting the bait file by mistake. The invention further discloses a bait file hiding device, an electronic device and a storage medium, which have the above beneficial effects.
Owner:SANGFOR TECH INC
Polymorphic virus analyzing method and device and virus processing method and device
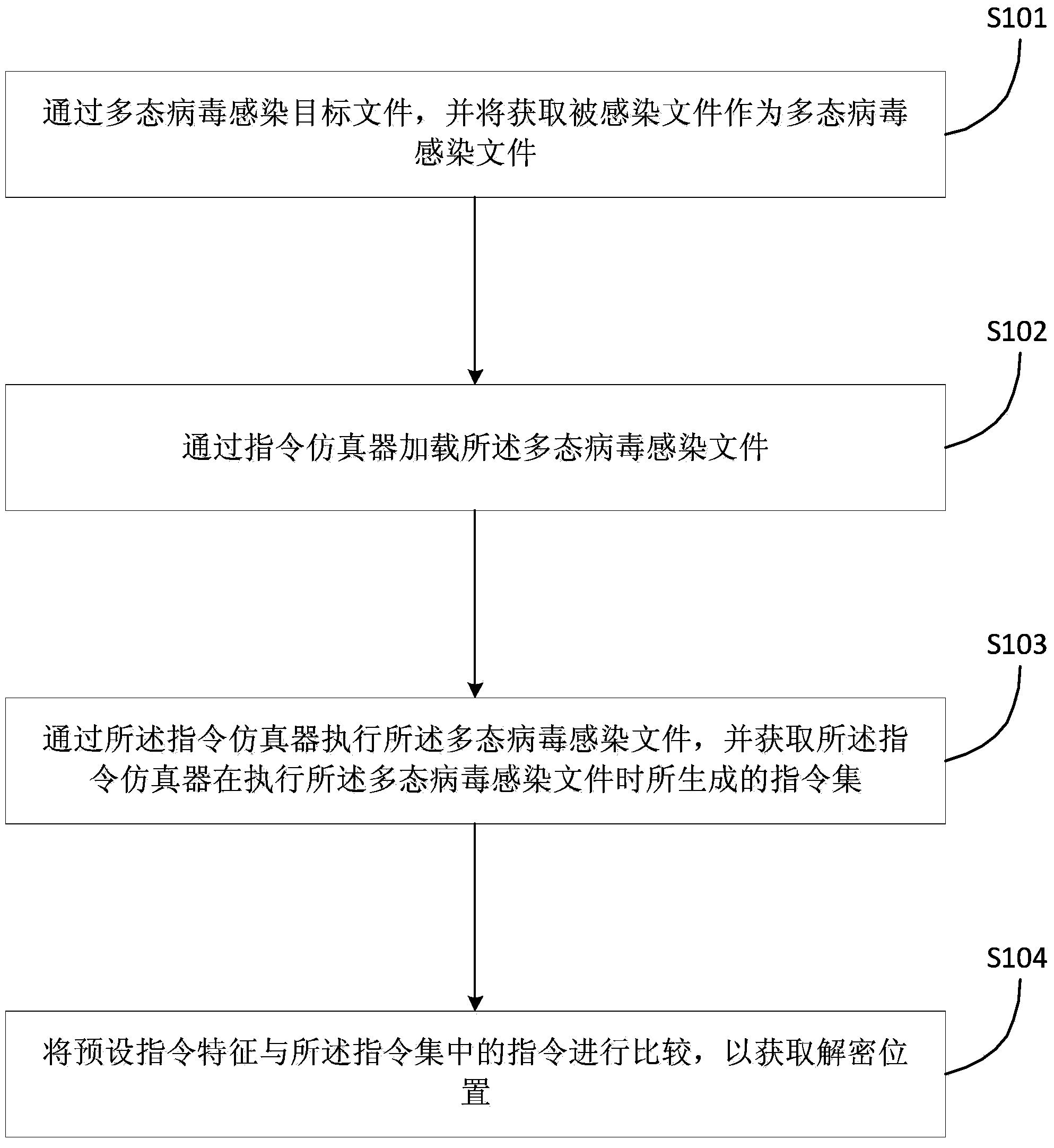
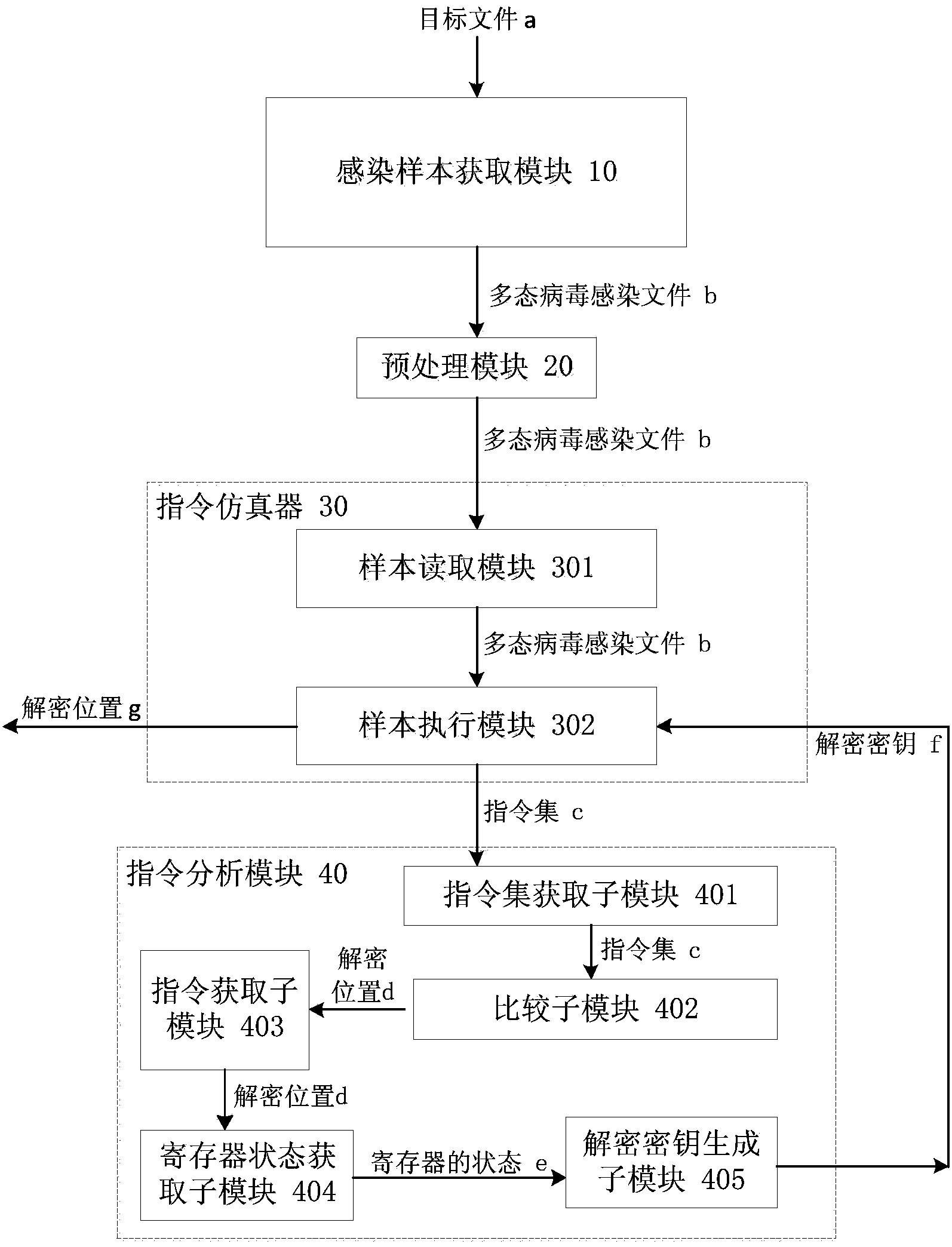
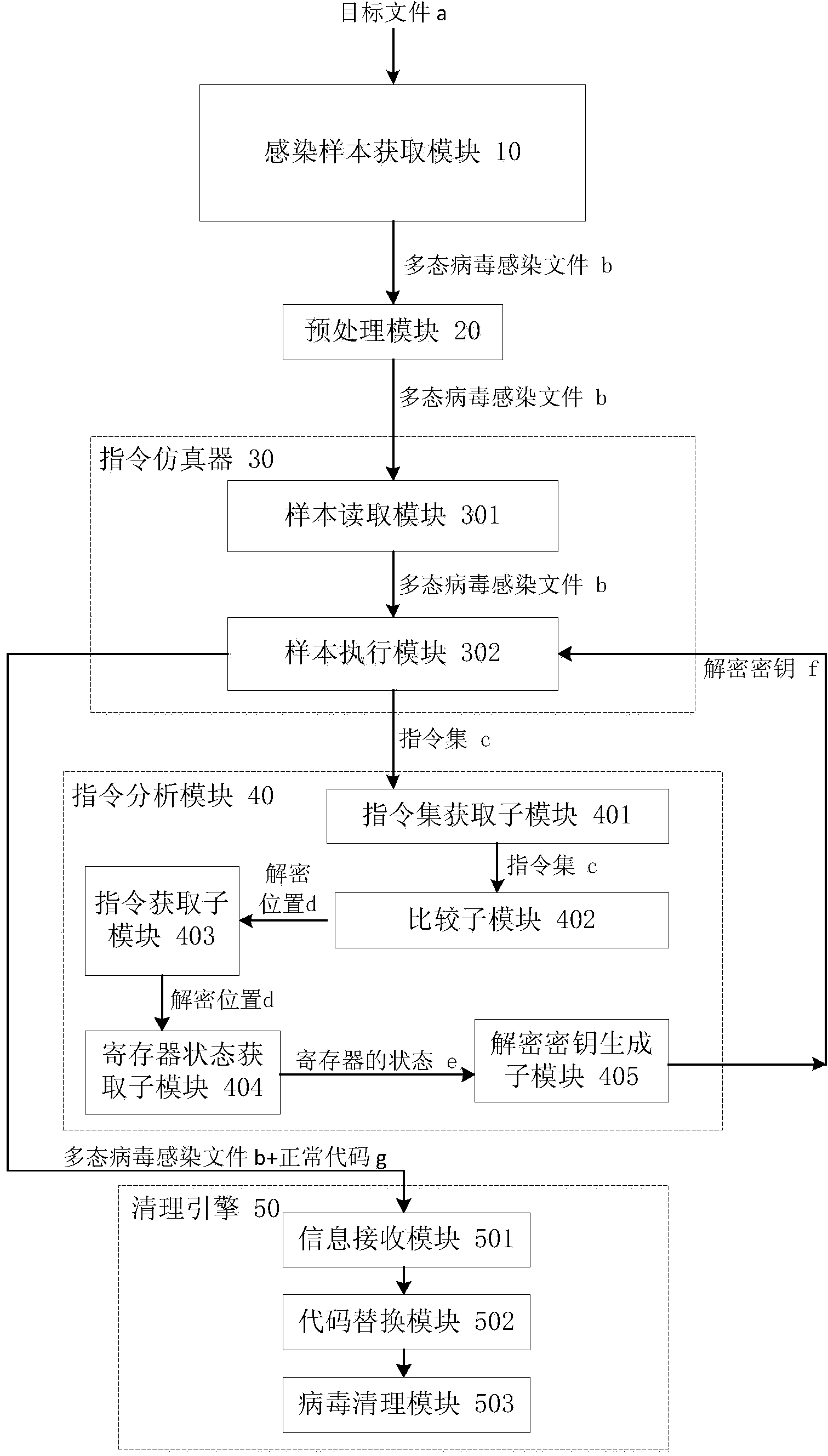
ActiveCN104077526ASimple processing methodReduce workloadPlatform integrity maintainanceInfectious virusWorkload
The invention discloses a polymorphic virus analyzing method and device and a virus processing method and device. The polymorphic virus analyzing method includes infecting a target file through polymorphic virus and utilizing the acquired infected file as a polymorphic virus infected file; loading the polymorphic virus infected file through a command simulator; utilizing the command simulator to execute the polymorphic virus infected file and acquiring a command set generated by the command simulator during execution of the polymorphic virus infected file; comparing the preset command characteristic and concentrated commands to acquire the decryption position. The polymorphic virus analyzing method simplifies the polymorphic infectious virus processing method, reduces the workload of analysis of polymorphic infectious virus, and improves the analyzing efficiency.
Owner:ZHUHAI BAOQU TECH CO LTD
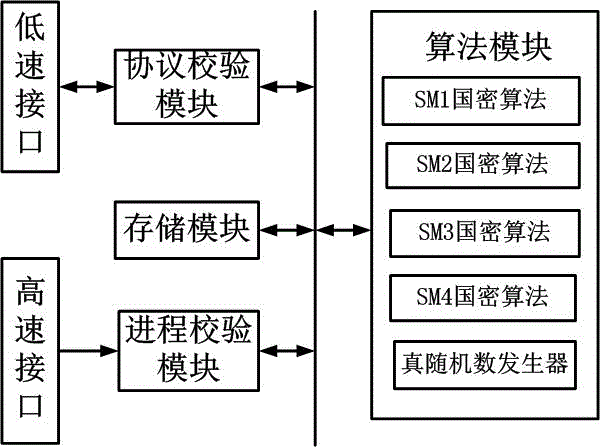
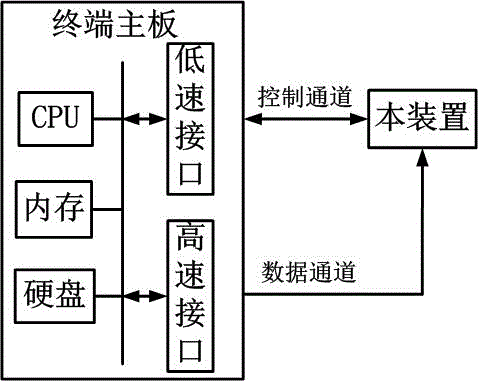
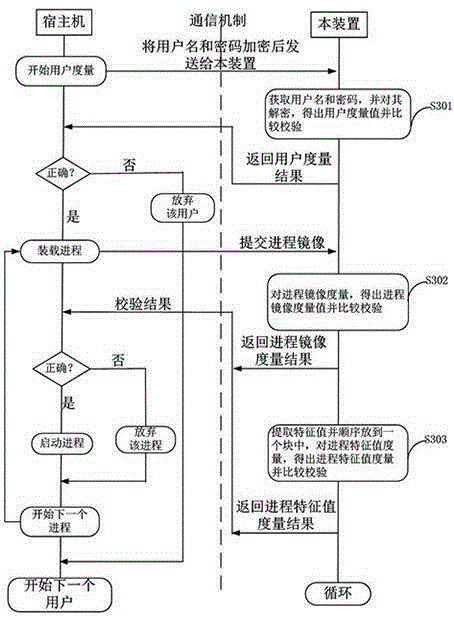
Encryption module and process trusted measurement method
The invention relates to a trusted computing technology, in particular to an encryption module and a process trusted measurement method. The encryption module includes interfaces, an algorithm module, a protocol verification module, a process verification module, and a storage module. The encryption module is mainly arranged on a terminal main board of a host machine such as a PC terminal or a mobile terminal, and is used for performing trusted measurement on an application process of a host system, and monitoring the integrity of the application process by verification and comparison of the a process user measurement value, a process image measurement value, and a process feature measurement value. The host machine uses the verification and comparison result of the process measurement value as a basis so as to determine whether a process is loaded or operated, virus processes and virus infection processes cannot pass trusted measurement and will not be loaded, processes which are infected by a virus will be stopped, and virus spread and attacks can be avoided.
Owner:深圳耀东安全科技有限公司
Intelligent virus invasion detection system for cloud platform server and method thereof
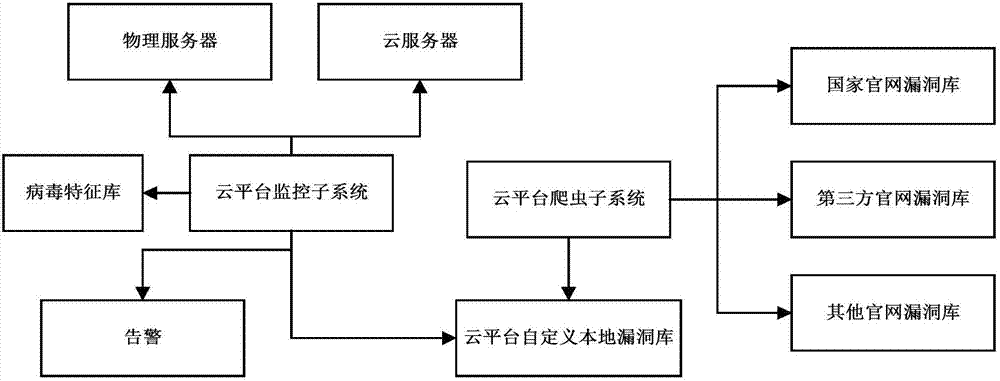
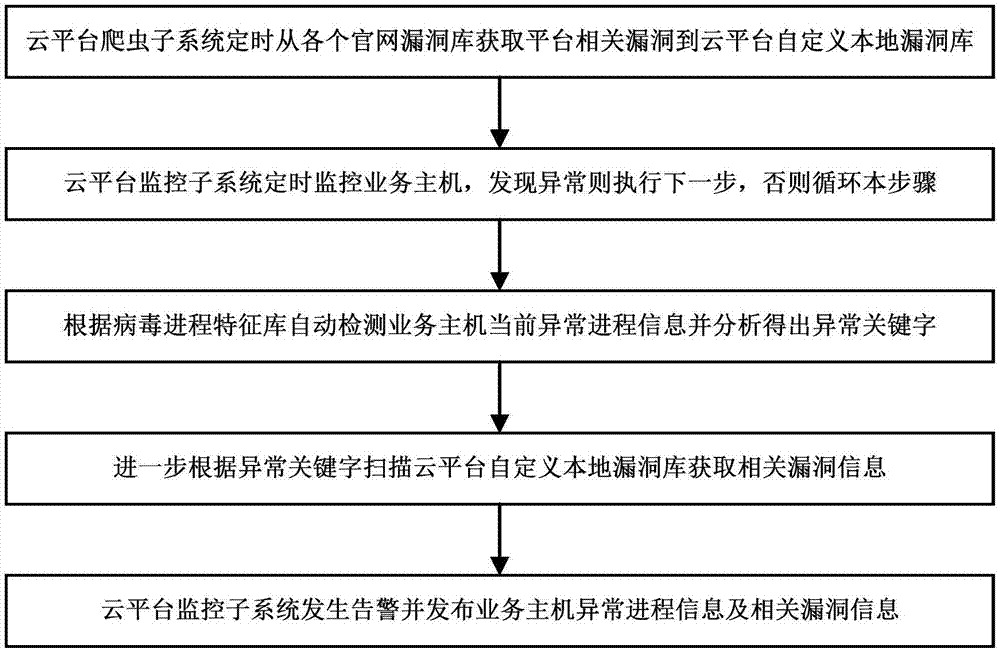
InactiveCN107888601AQuick buildRealize real-time detectionTransmissionProcess informationOperating system
The invention relates to the technical field of cloud computing security, and particularly relates to an intelligent virus invasion detection system for a cloud platform server and a method thereof. The system disclosed by the invention comprises a cloud platform monitoring subsystem, a cloud platform custom local vulnerability library and a cloud platform crawler subsystem. The method includes the following steps: enabling the cloud platform crawler subsystem to regularly obtain platform-related vulnerabilities from various official website vulnerability libraries to send to the cloud platform custom local vulnerability library; enabling the cloud platform monitoring subsystem to regularly monitor process information of a service host, performing the next step if abnormalities are found,and otherwise, repeating the current step; automatically detecting current abnormal process information of the service host according to a virus process feature library, and performing analysis to obtain abnormal keywords; further scanning the cloud platform custom local vulnerability library based on the abnormal keywords to obtain related vulnerability information; and enabling the cloud platform monitoring subsystem to generate alarms and publish the abnormal process information of the service host and the related vulnerability information. According to the scheme of the invention, a cloudplatform can intelligently monitor the virus invasion of the service host, and a method for quickly solving intrusive viruses can be provided for cloud platform administrators and users.
Owner:G CLOUD TECH
Process and culture medium for the production of cells infected by a multiple sclerosis-associated virus
Process for in vitro production of a culture or cell line infected by a viral strain associated with multiple sclerosis (MS), according to which a body sample is taken from an individual suffering from MS, the sample is cultivated in a culture medium which promotes the growth of infected cells to obtain a culture of primary infected cells, and a sample of the culture of primary cells or of a subculture of the latter is cultivated in series, that is to say by successive passages, in the culture medium to obtain the culture or cell line infected by a virus associated with MS. The process includes a procedure in which the culture medium also contains a beta anti-interferon antibody or an antibody which is directed against an antigenically close molecule, the antibody playing an inhibiting role in viral expression and allowing long-lasting expression and propagation of the viral strain in the culture or cell line.
Owner:BIOMERIEUX SA
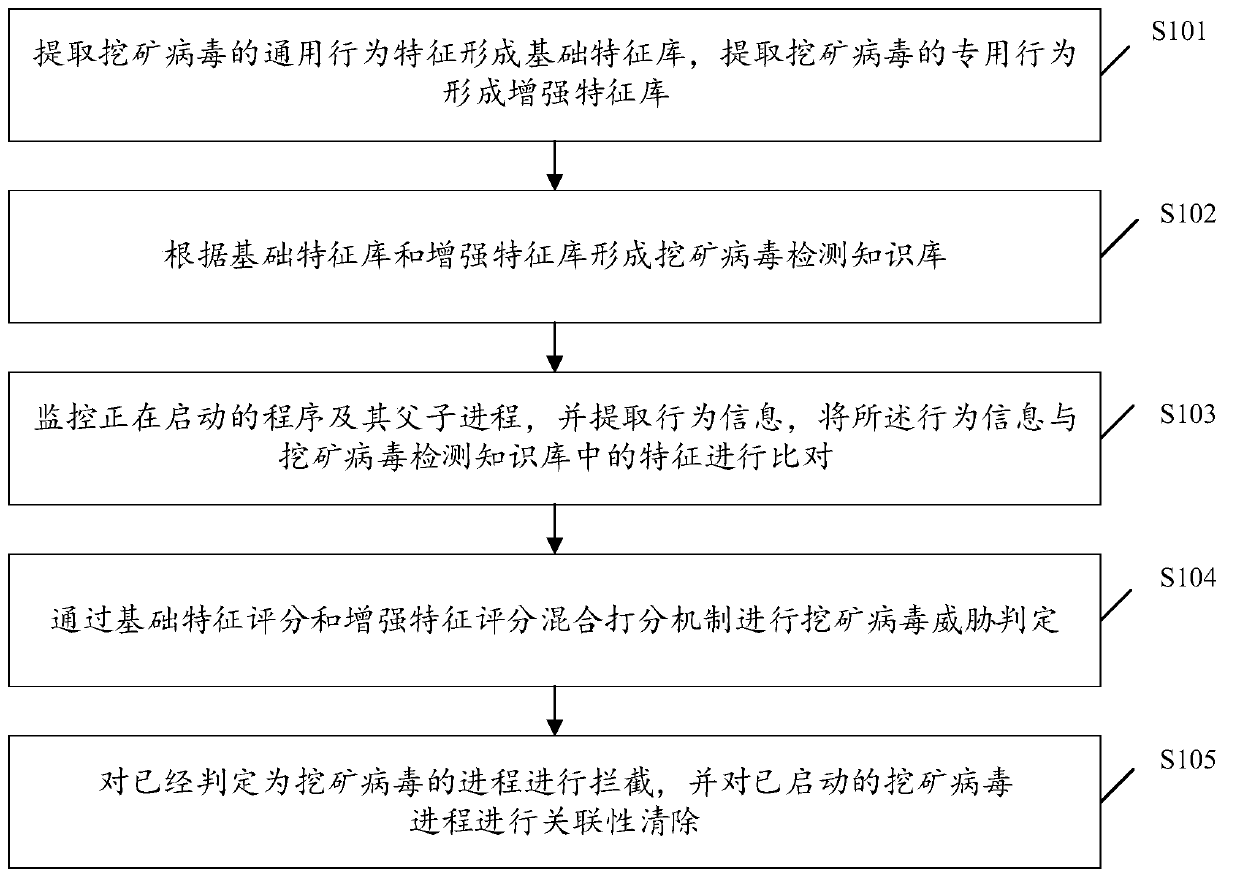
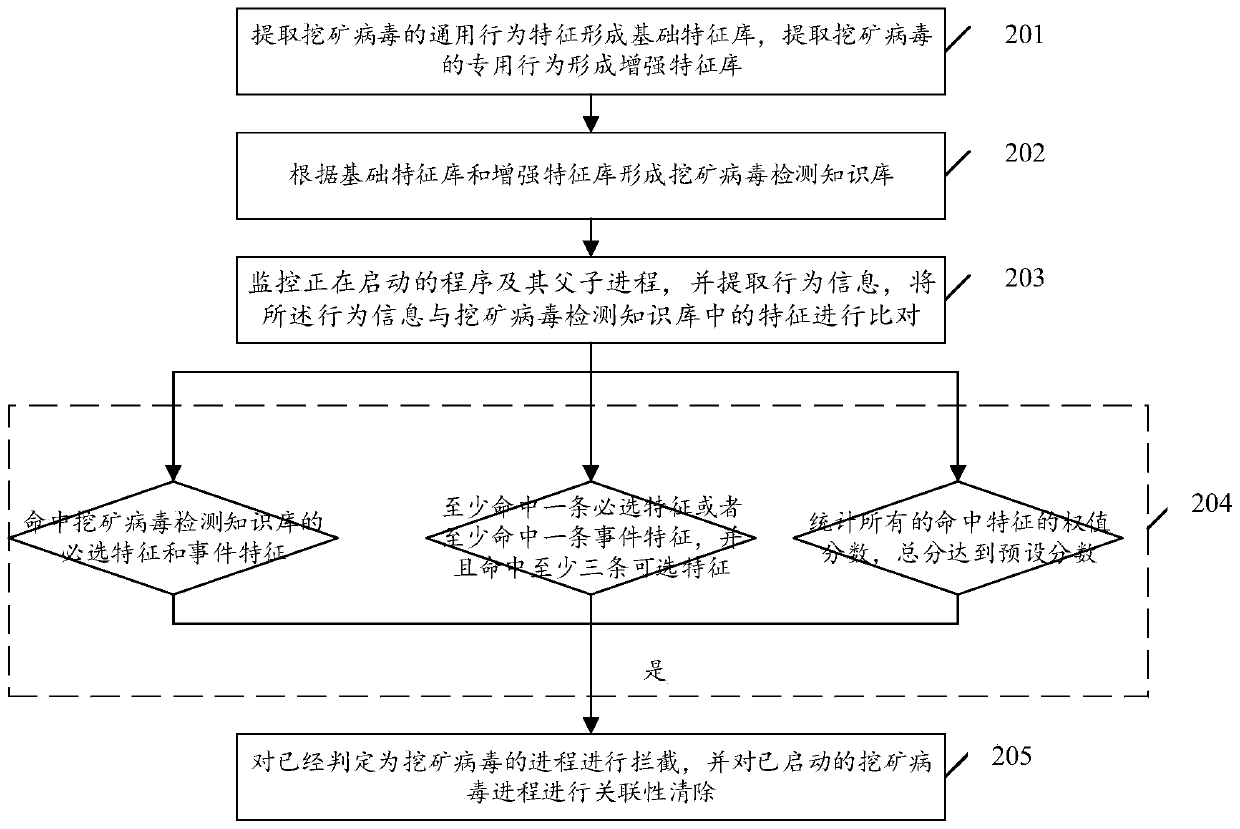
Method and device for preventing and removing mining viruses under Linux platform and storage equipment
The embodiment of the invention discloses a method and device for preventing and removing mining viruses under a Linux platform and storage equipment, relates to the technical field of network security, and provides a method for preventing and removing general mining viruses under a Linux system. The method comprises the following steps: extracting universal behavior characteristics of mining viruses to form a basic characteristic library, and extracting special behaviors of the mining viruses to form an enhanced characteristic library; forming a mining virus detection knowledge base accordingto the basic feature library and the enhanced characteristic library; monitoring a program which is being started and parent and child processes thereof, extracting behavior information, and comparing the behavior information with characteristic s in the mining virus detection knowledge base; carrying out mining virus threat judgment through a basic characteristic scoring and enhanced characteristic scoring mixed scoring mechanism; and intercepting the process which is judged to be the mining virus, and carrying out relevance clearing on the started mining virus process.
Owner:BEIJING ANTIY NETWORK SAFETY TECH CO LTD
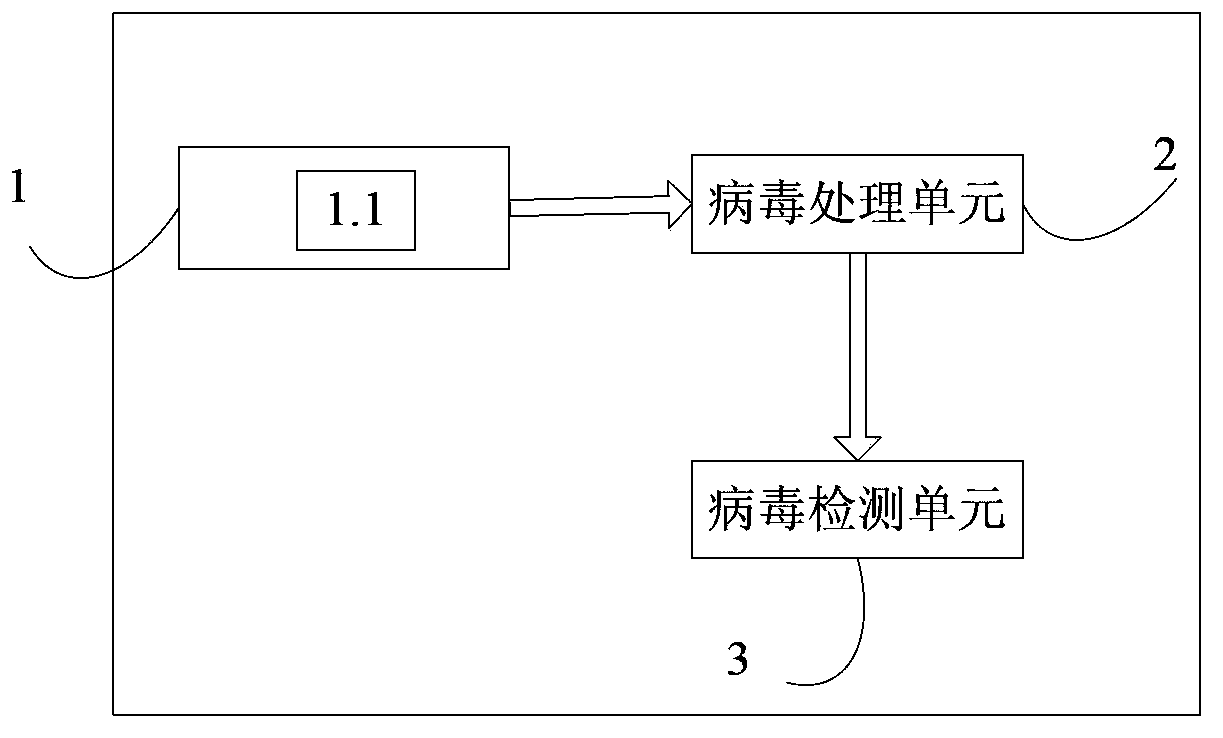
Anti-virus E-mail processing system and method
The invention discloses an anti-virus E-mail processing system and method. The anti-virus E-mail processing system comprises a virus detecting unit, a virus isolating unit and a virus processing unit, wherein the virus detecting unit is installed on a computer; the virus isolating unit is used for receiving virus detected information uploaded by the virus detecting unit and isolating the virus; the virus processing unit is used for receiving the virus detected information uploaded by the virus detecting unit and eliminating the virus. The anti-virus E-mail processing method comprises the following steps: a) detecting if the virus exists: utilizing a virus detecting module to detect if the virus exists in the E-mail when the E-mail is received by the computer; b) isolating the virus: refusing to open the E-mail and utilizing a virus isolating module of the computer to isolate the virus when the virus is detected; c) processing the virus: utilizing an antivirus program on the computer to perform anti-virus treatment on the E-mail.
Owner:DALIAN HONGYU TECH
Virus processing method and device, computer device and computer readable storage medium
ActiveCN110851831ATimely processingTimely protectionPlatform integrity maintainanceEnergy efficient computingProcessing InstructionShut down
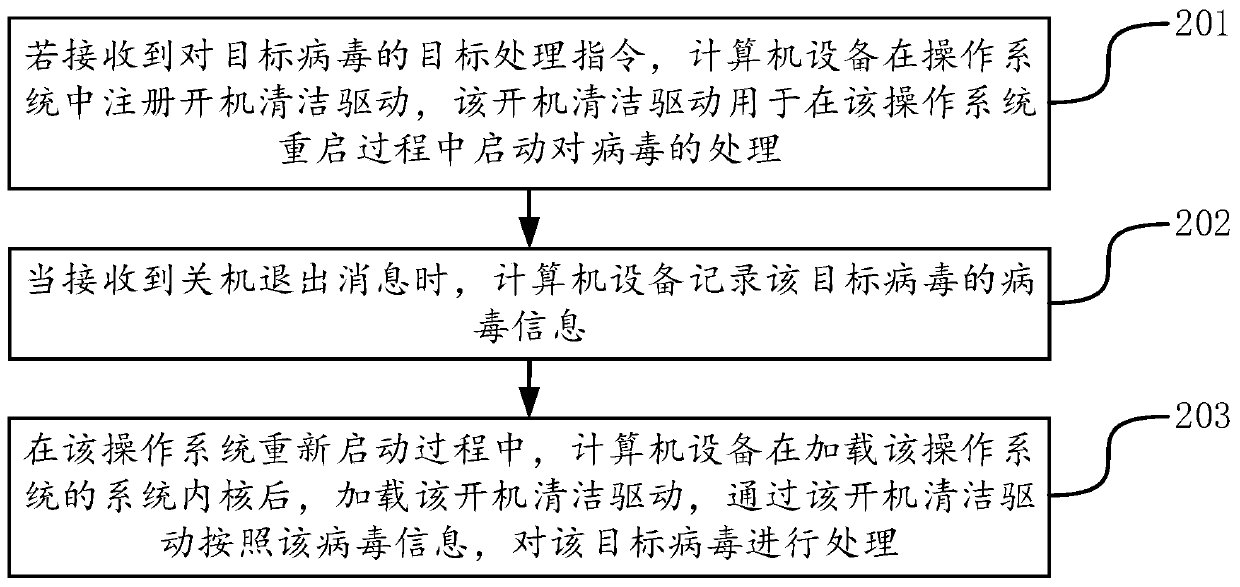
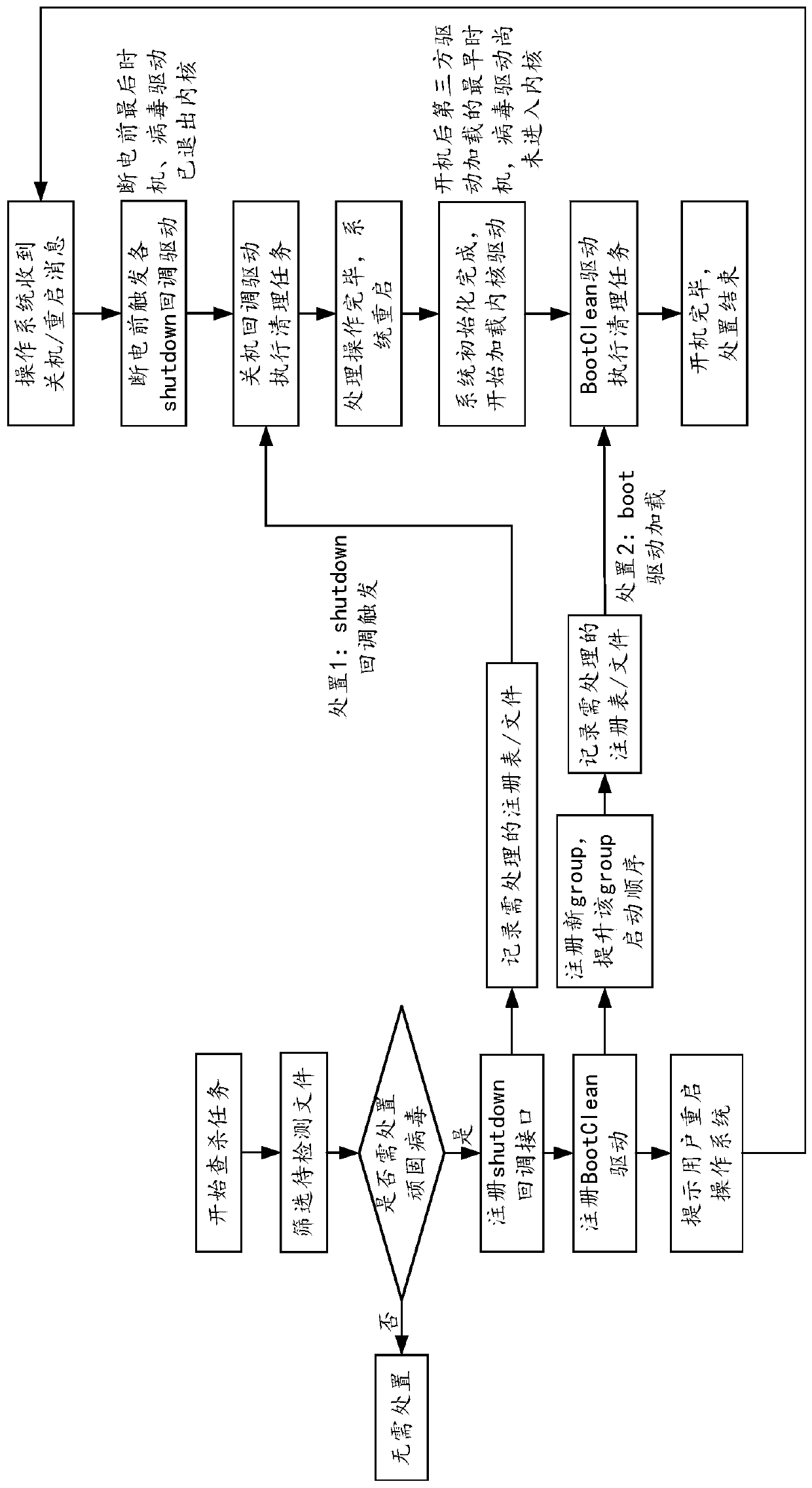
The invention provides a virus processing method and device, a computer device and a computer readable storage medium, and belongs to the technical field of computers. The method comprises the following steps: when a target processing instruction for a target virus is received, registering a startup cleaning drive for processing the virus in the restarting process of the operating system in the operating system, and loading the startup cleaning drive to process the target virus according to the recorded virus information of the target virus after the system kernel is completely loaded in the restarting process of the operating system. According to the method, through loading a system kernel, a startup cleaning drive registered before shutdown is loaded, and viruses are treated. Since the virus does not enter the kernel and is in the vacuum period of virus protection at the moment, deletion or blocking of virus loading is facilitated, the processing success rate is greatly increased. Inaddition, the virus can be processed in time without analyzing the hiding principle of the virus, and a computer system and computer data are protected.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Computer network defense decision-making system
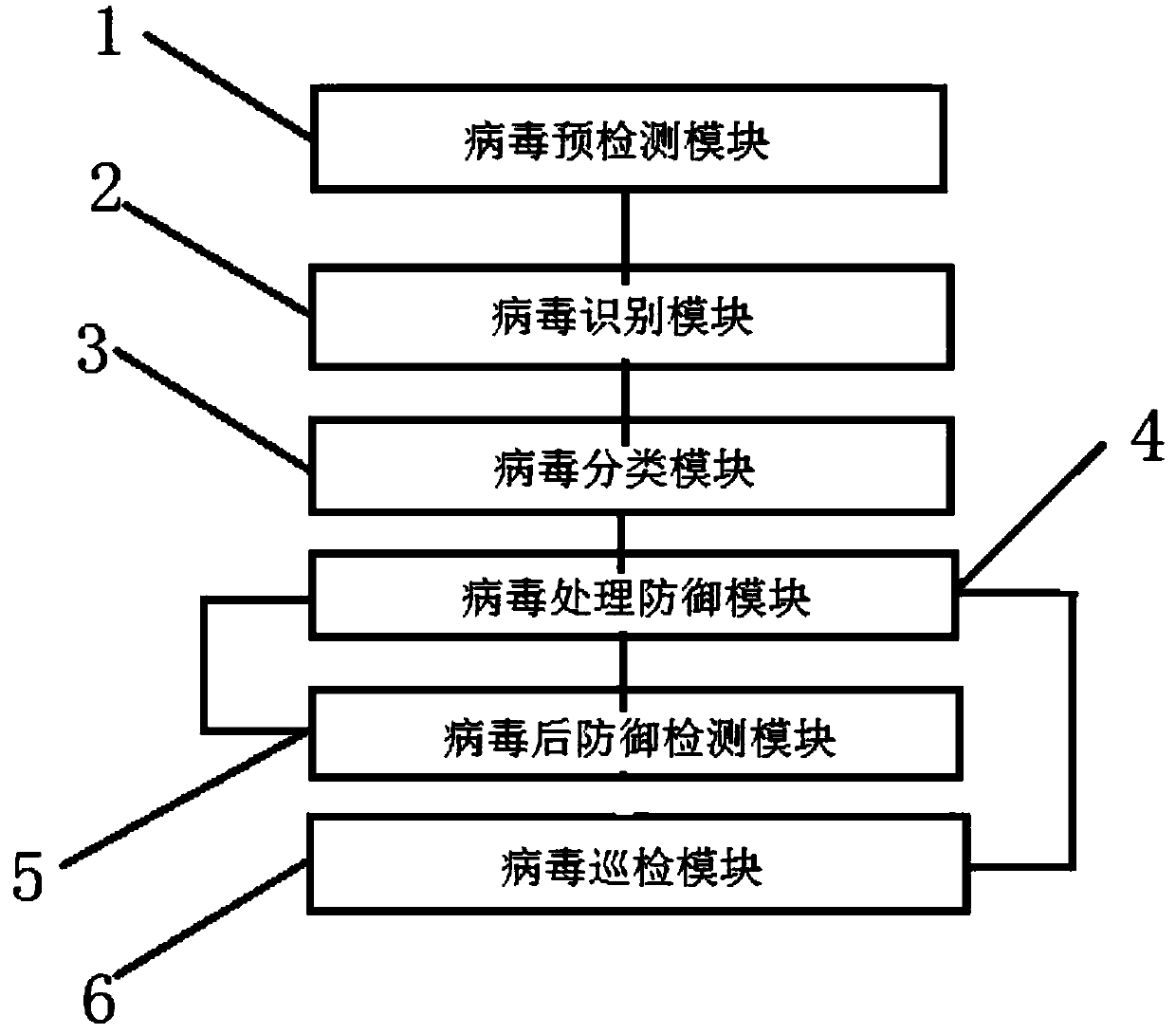
ActiveCN108540474AImprove securityClear division of laborTransmissionDecision systemVirus classification
The invention belongs to the technical field of network security and discloses a computer network defense decision-making system. A virus pre-detection module, a virus identification module, a virus classification module, a virus processing defense module and a virus post-defense detection module are connected in sequence, and a virus patrol inspection module is used for patrol monitoring. The residual virus condition is detected by the virus post-defense detection module, and the residual virus can be directly sent to the virus processing defense module to continue checking and killing. In another classification, the virus patrol inspection module exists to monitor various viruses at any time, and the virus of the same species before can be directly sent to the virus processing defense module for checking and killing. The defense decision-making system module has a clear logical hierarchy, and each module has a clear division of labor. Each module automatically monitors the virus at any time to ensure high network security and ensure permanent and complete checking and killing of the same virus.
Owner:CHENGDU UNIVERSITY OF TECHNOLOGY
Control method and device of mobile storage device and storage medium
PendingCN109857587AInternal/peripheral component protectionPlatform integrity maintainanceAnti virusFile system
The invention relates to the technical field of information security, and especially relates to a control method, device and system for a mobile storage device, and aims to effectively prevent security risks caused by use of the mobile storage device. The device comprises a mobile storage device interface; a memory configured to store a device management program; and a processor configured to be used for calling the device management program, detecting whether the mobile storage device interface is connected with a mobile storage device or not, and destroying a file system on the connected mobile storage device after detecting that the mobile storage device interface is connected with the mobile storage device; In response to a file copying instruction, generating a first mirror image fileof a file system of the mobile storage device containing the target file; And recovering the file system of the mobile storage device by using the first mirror image file. As the equipment managementdevice recovers the file system of the mobile storage equipment by using the mirror image file, virus propagation caused by pulling out the mobile storage equipment in the anti-virus process can be effectively avoided.
Owner:SIEMENS AG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com