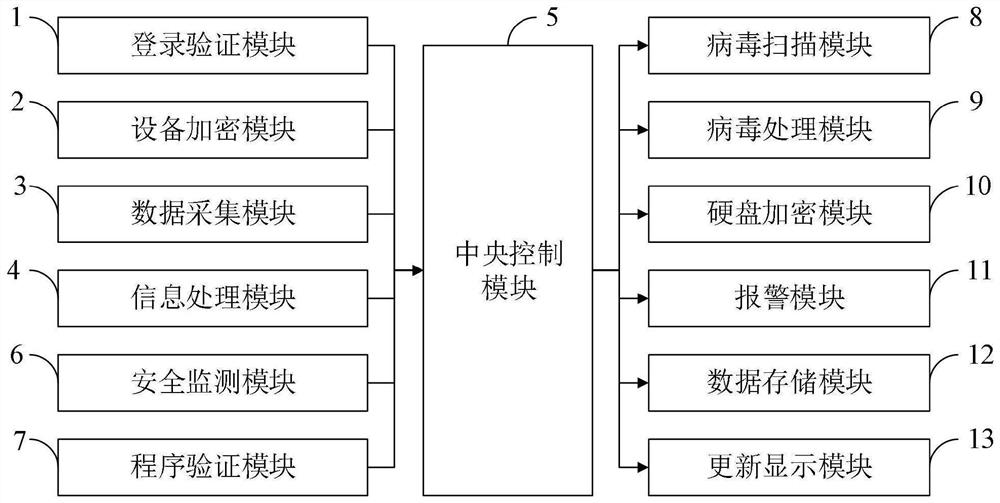
Computer system for ensuring information security and control method thereof
A computer system and information security technology, applied in computer components, computer security devices, computing, etc., can solve problems such as low computer security, loss of tangible assets, and inability to protect against viruses, so as to prevent network virus intrusion, improve efficiency, The effect of protecting security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
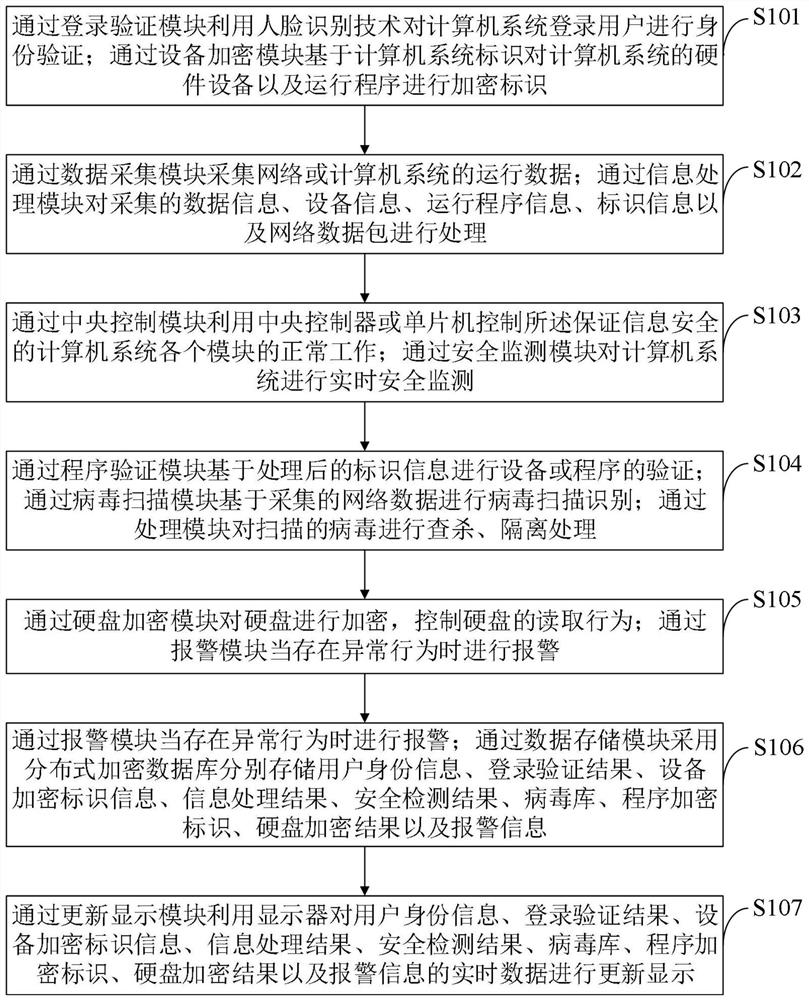
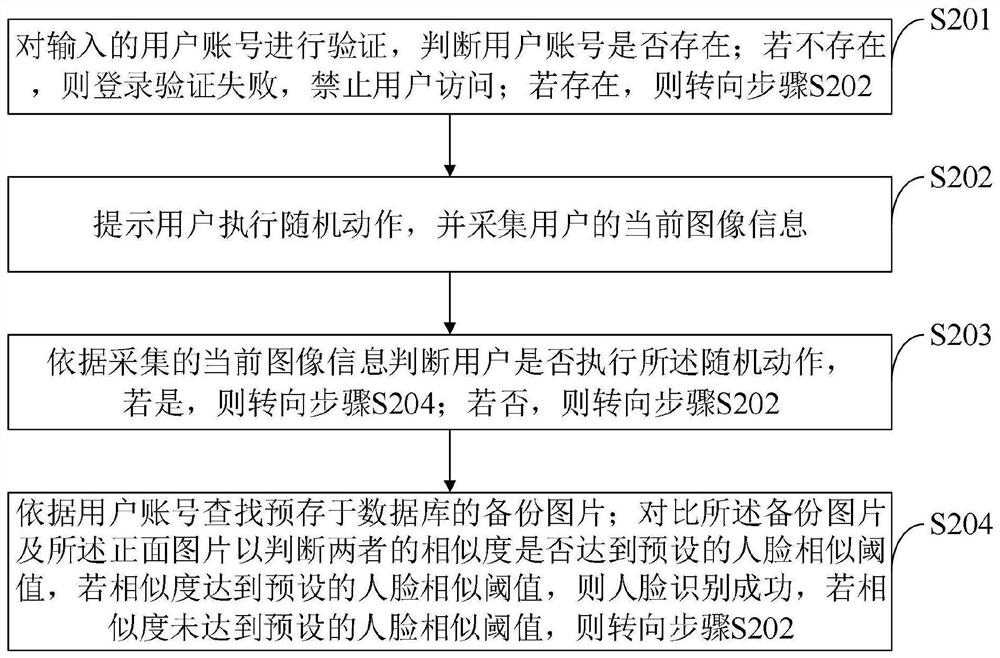
[0095] The control method of the computer system for ensuring information security provided by the embodiment of the present invention is as follows: figure 1 shown, as a preferred embodiment, as image 3 As shown, the method for performing identity verification on a computer system login user through a login verification module using face recognition technology provided by the embodiment of the present invention includes:
[0096] S201, verify the input user account, and determine whether the user account exists; if not, the login verification fails, and the user is prohibited from accessing; if it exists, turn to step S202;
[0097] S202, prompting the user to perform a random action, and collecting the current image information of the user;
[0098] S203, according to the collected current image information, determine whether the user performs the random action, if so, go to step S204; if not, go to step S202;
[0099]S204, search for the backup picture pre-stored in the ...
Embodiment 2
[0103] The control method of the computer system for ensuring information security provided by the embodiment of the present invention is as follows: figure 1 shown, as a preferred embodiment, as Figure 4 As shown, the method for virus scanning and identification based on the collected network data by the virus scanning module provided by the embodiment of the present invention includes:
[0104] S301, using big data mining technology to obtain relevant virus feature data of each network virus database, and creating a network virus feature database based on the obtained virus feature data;
[0105] S302, after the collected network data packets are reassembled and parsed, a multi-pattern matching algorithm is used to match the virus features in the virus feature database;
[0106] S303, when a virus signature is matched, it is determined whether one or more complete virus information pieces can be formed by combining the matched virus signatures. If yes, the virus informatio...
Embodiment 3
[0110] The control method of the computer system for ensuring information security provided by the embodiment of the present invention is as follows: figure 1 shown, as a preferred embodiment, as Figure 5 As shown, the method for encrypting the hard disk by using the hard disk encryption module provided by the embodiment of the present invention, and controlling the reading behavior of the hard disk includes:
[0111] S401, obtain the service serial number of the computer system and the serial number of the hard disk; according to the self-defined coding rule, obtain the first hard disk password for the obtained service serial number and hard disk number;
[0112] S402, when the computer system is powered on, obtain the service serial number of the computer system and the serial number of the currently running hard disk;
[0113] S403, according to the same coding rule as S401, encode the serial number of the computer system service obtained in S402 and the serial number of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com