Method for searching and killing virus of network equipment
A technology of network equipment and equipment, applied in the direction of data exchange network, program control device, transmission system, etc., to achieve the effect of reducing maintenance cost, improving reliability, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
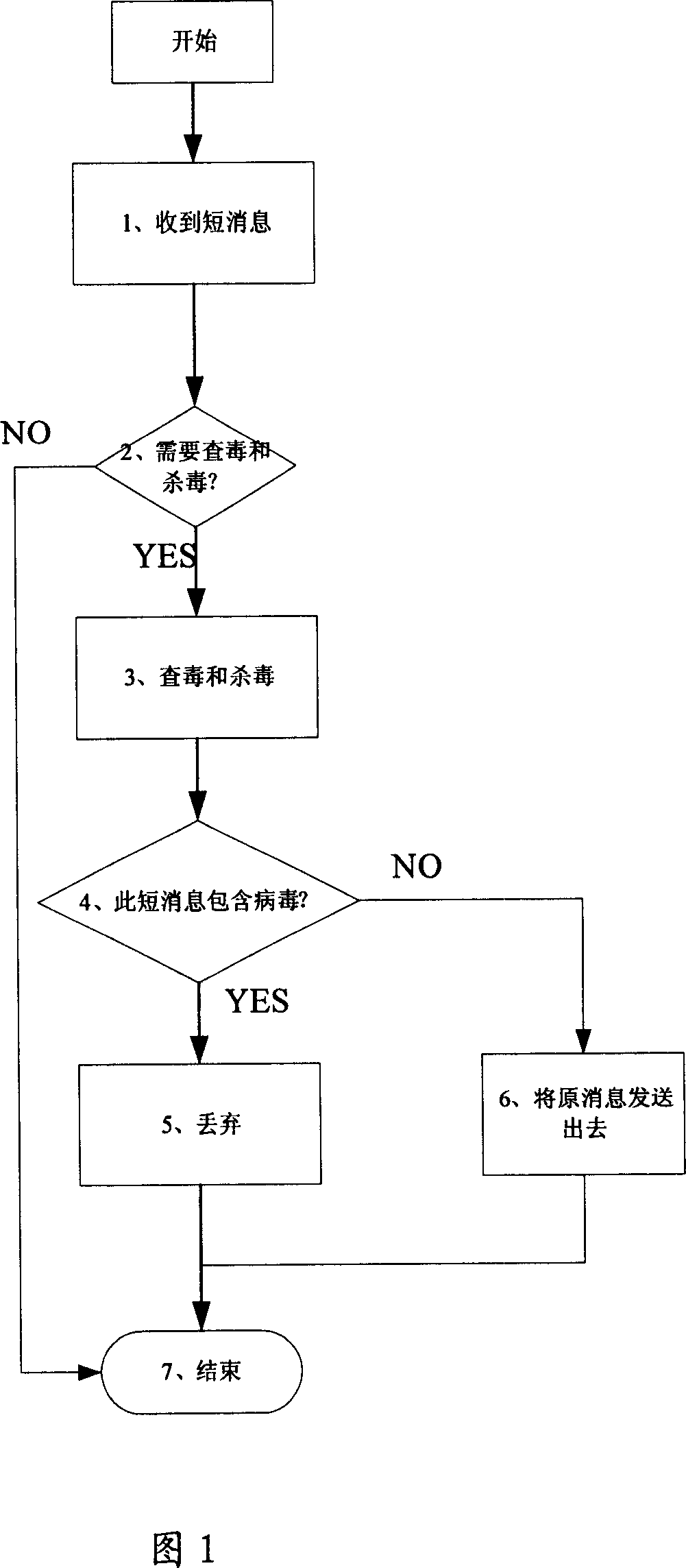
[0048] Embodiment 1: This embodiment takes the MSC in the mobile network as an example, where rule 1 is defined as: general signaling messages do not need to be checked / anti-virus, short message messages are checked / anti-virus; rule 2 is defined as a virus-detected message Discard, messages without viruses are processed according to the original process, the process of checking / antivirus is shown in Figure 1.
[0049] Step 1: The network device receives an external message;
[0050] Step 2: According to rule 1, the network device decides whether to check and disinfect the message. If it does not need to check and disinfect, go to step 7;
[0051] Step 3: If you need to check and kill the virus for this message, use this message as a virus check and antivirus object to call the interface provided by the virus check and antivirus module;
[0052] Step 4: Check and kill viruses to complete the check and kill functions of messages, and feed back the results to the original message pro...
Embodiment 2
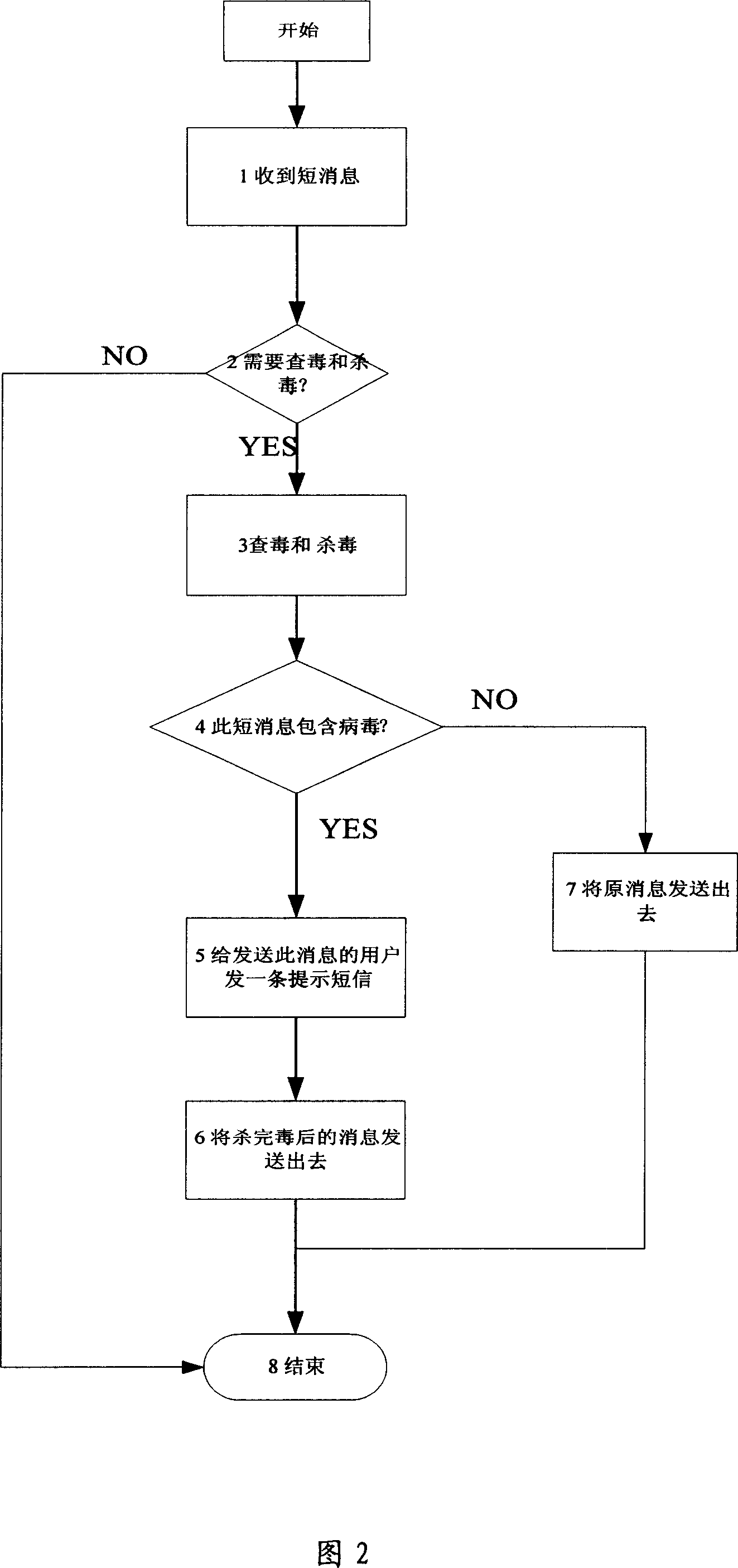
[0056] Embodiment 2: This embodiment takes the MSC in the mobile network as an example, where rule 1 is defined as: general signaling messages do not need to be checked / killed, and short message messages are checked and disinfected; rule 2 is defined as virus detection The message is sent to the user who sent the message and disinfected the message. After the disinfection is completed, the message will continue to be processed, and the message that no virus is found will be processed according to the original process. The process of checking / antivirus is shown in Figure 2:
[0057] Step 1: The network device receives an external message;
[0058] Step 2: According to rule 1, the device decides whether to check and disinfect the message. If it does not need to check and disinfect, go to step 8;
[0059] Step 3: If you need to check and kill the virus for this message, use this message as the object that needs to check and kill the virus and call the interface provided by the need t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com