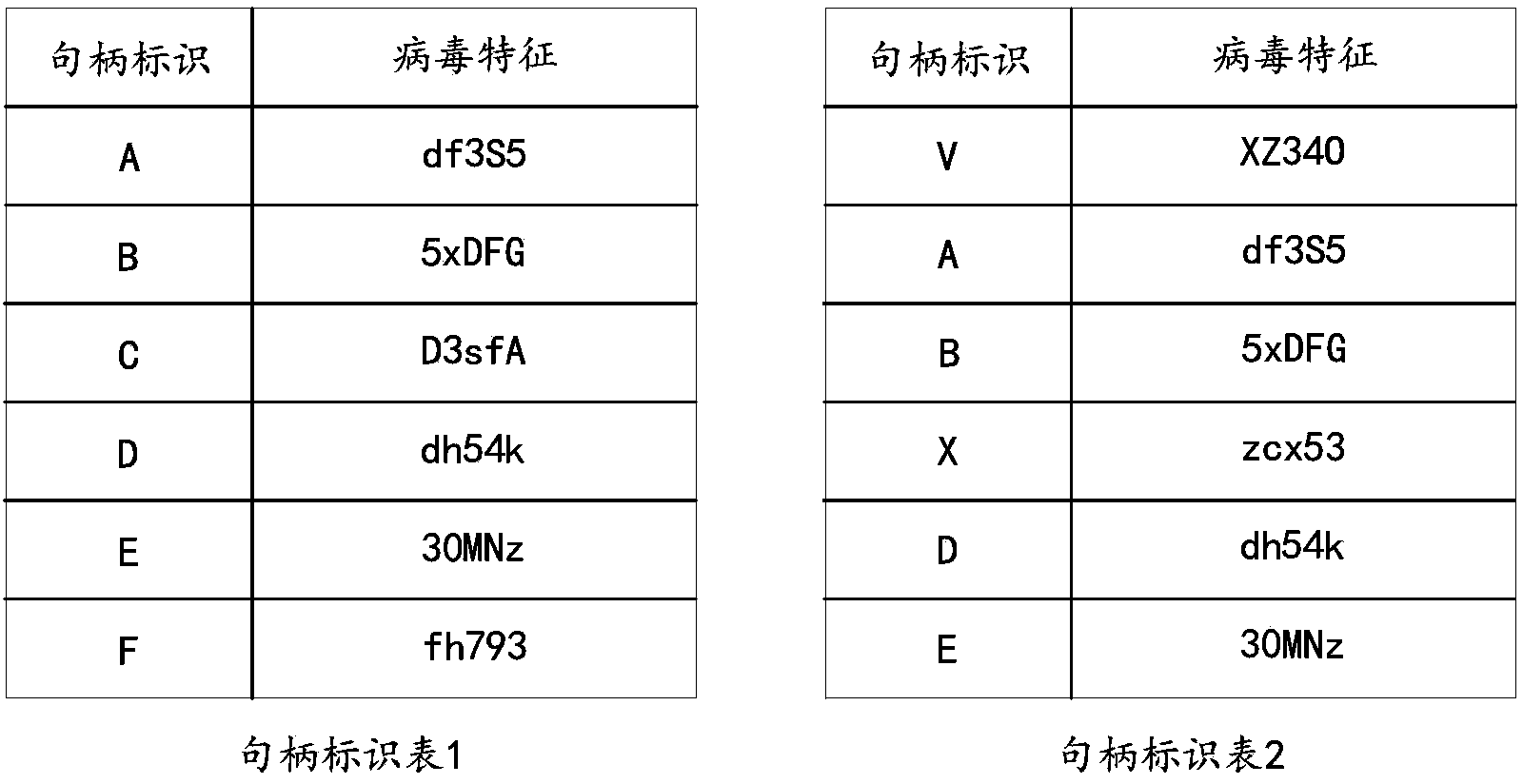
Patents
Literature
47 results about "Killed process" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In probability theory — specifically, in stochastic analysis — a killed process is a stochastic process that is forced to assume an undefined or "killed" state at some (possibly random) time.
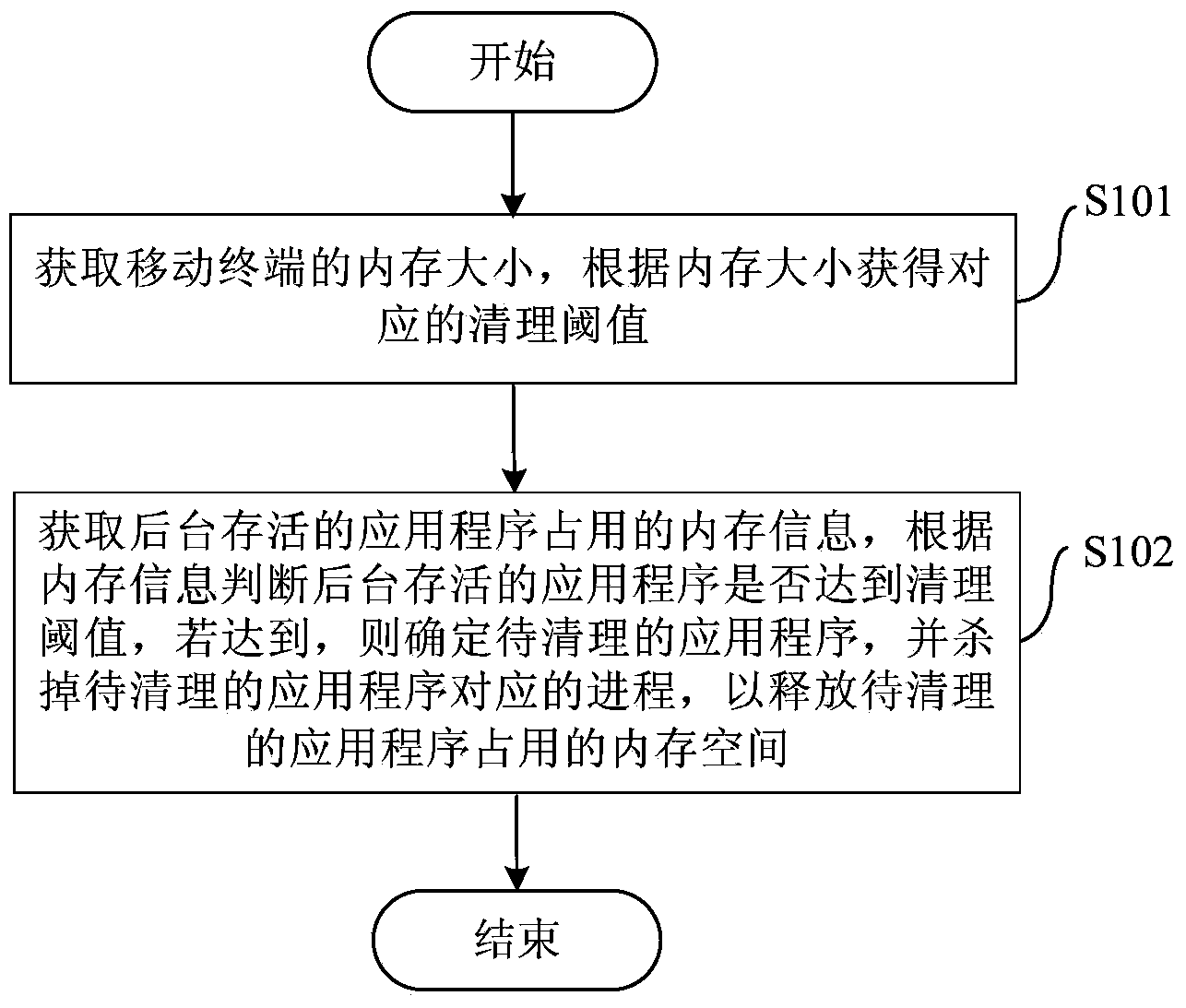
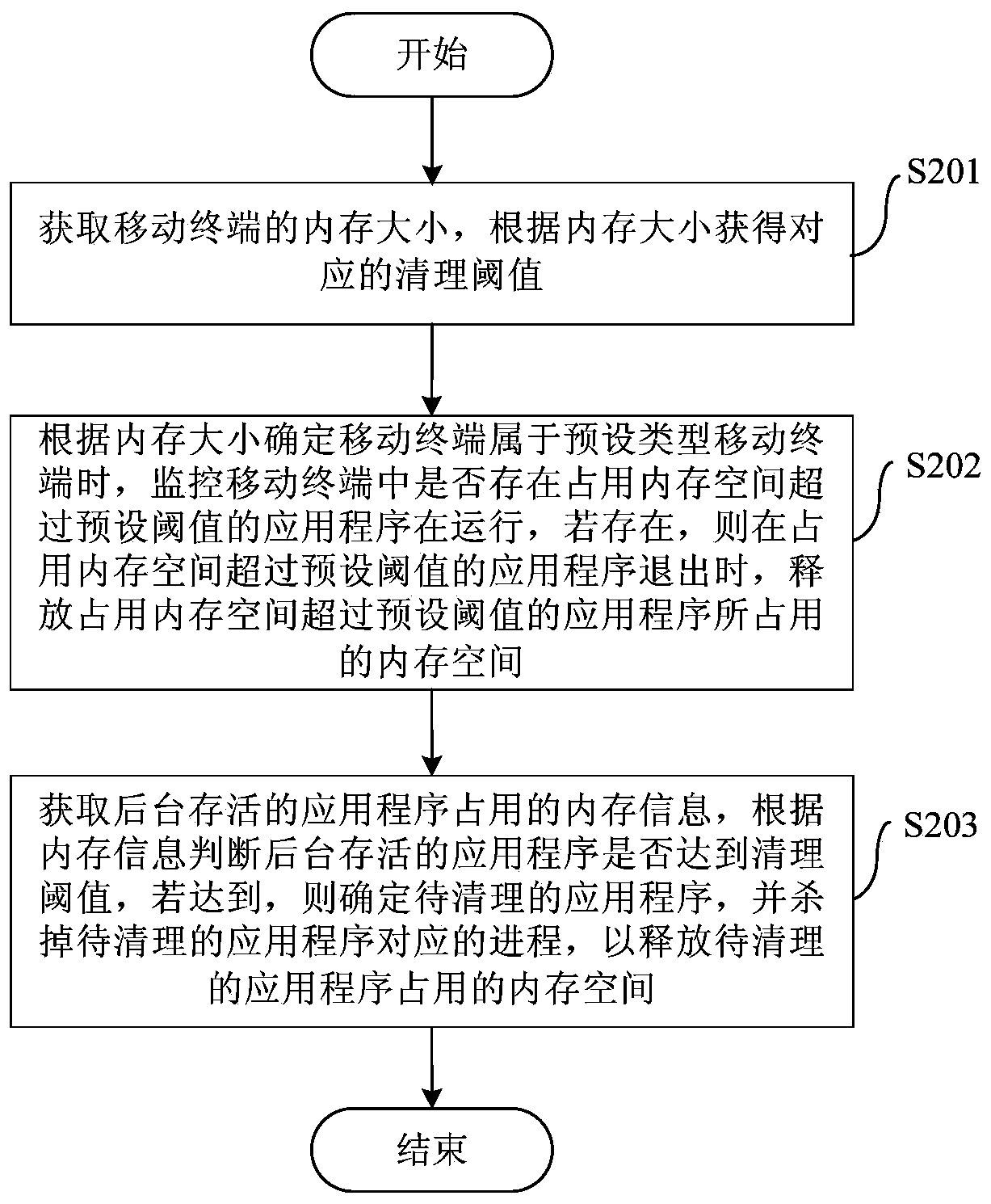
Method and device for clearing memory of mobile terminal and mobile terminal
InactiveCN104298612AReduce occupancyImprove operational efficiencyMemory adressing/allocation/relocationKilled processComputer engineering
Owner:BEIJING KINGSOFT INTERNET SECURITY SOFTWARE CO LTD
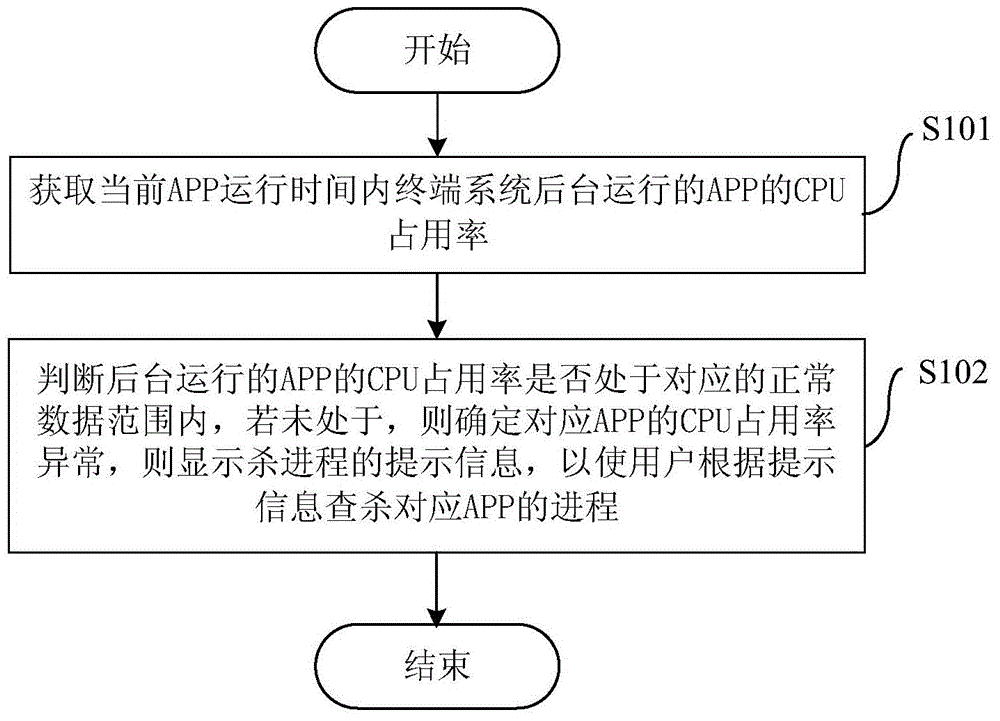
Method and device for processing application APP of terminal and terminal
ActiveCN104317649AReduce the impactImprove operational efficiencyProgram initiation/switchingResource allocationOccupancy rateKilled process
Owner:KINGSOFT
Method, system and device for searching and killing computer virus
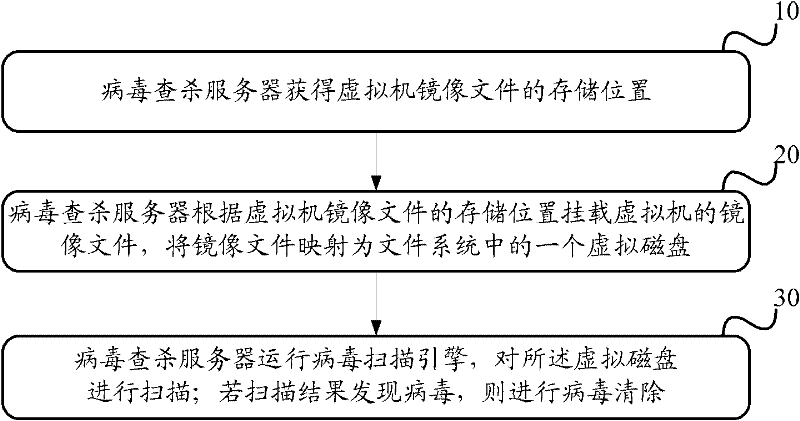
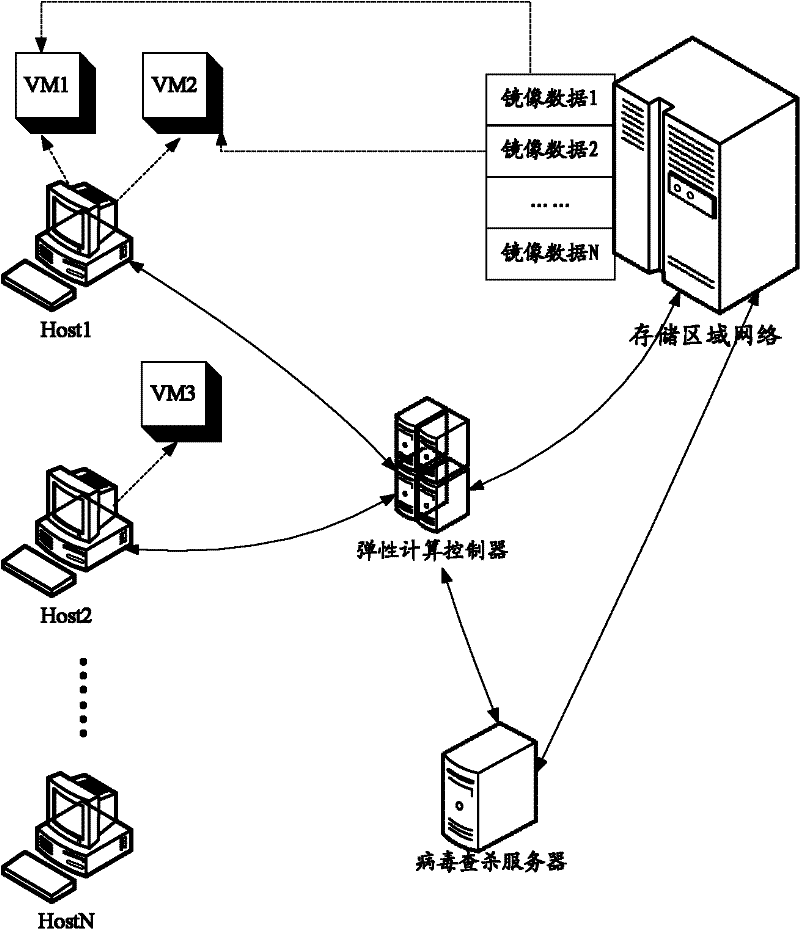
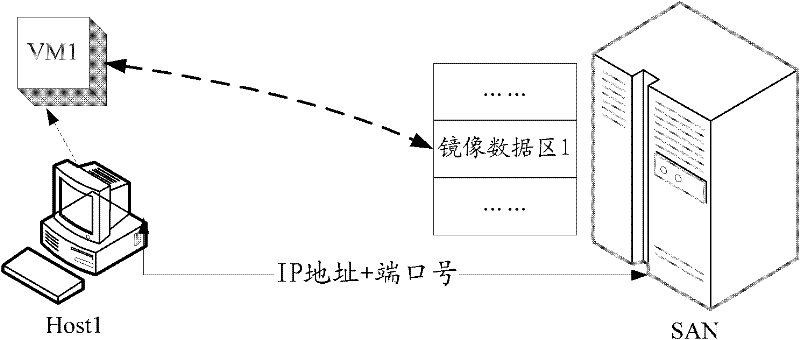
The invention discloses a method, a system and a device for searching and killing a computer virus in order to solve the problem that a virus searching and killing process for a virtual machine is complicated in the prior art. The method comprises the following steps of: acquiring a storage position of virtual machine mirror image data by a virus searching and killing server; mounting the mirror image data of the virtual machine according to the storage position of the virtual machine mirror image data and mapping the mirror image data as a virtual disk in the virus searching and killing server; running a virus scanning engine and scanning the virtual disk according to characteristics of known viruses in a virus characteristic base; and if viruses are found by scanning, removing the viruses. In the scheme, antivirus software is not required to be installed in the virtual machine and antivirus operation is not needed to be performed by a user; therefore, operation of the user is simplified greatly.
Owner:CHENGDU HUAWEI TECH
Preparation method of environment-friendly long-acting antibacterial polylactic acid material
InactiveCN104861120ANo pollution in the processHigh antibacterial efficiencyEnvironmental resistanceHypochlorite
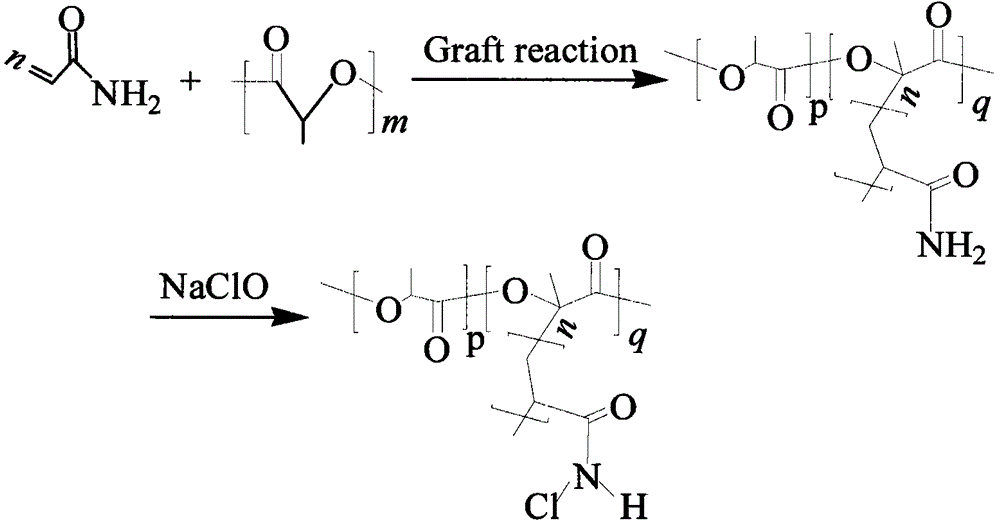
The invention provides a preparation method of an environment-friendly long-acting antibacterial polylactic acid material, which comprises the steps that an acrylamide substance is grafted to a polylactic acid molecular chain under an initiator existence condition by a radical graft polymerization method; and then amino is halogenated by a halogenating agent. In bacterium and virus killing processes of a halogen amide compound, an oxidation-state halogen atom is consumed, so that an N-X bond in an halogen amide molecule is converted into an N-H bond and the activity is lost, but the N-H bond can be oxidized into an N-C1 bond after simple rinsing of dilute-concentration bleaching liquid (with an active ingredient of hypochlorite), and a sterilization function is obtained again. Polylactic acid is grafted with acrylamide and then halogenation is performed, so that a product contains a halogen amide group, is high in antibacterial efficiency, is safe to a human body, has no toxic or side effect, is pollution-free, and can be completely applied to a food packing material and tableware.
Owner:JIANGSU SUPLA BIOPLASTICS CO LTD
Method, device and system for searching and killing viruses
InactiveCN104281809AImprove the killing ratePlatform integrity maintainanceTransmissionThe InternetKilled process
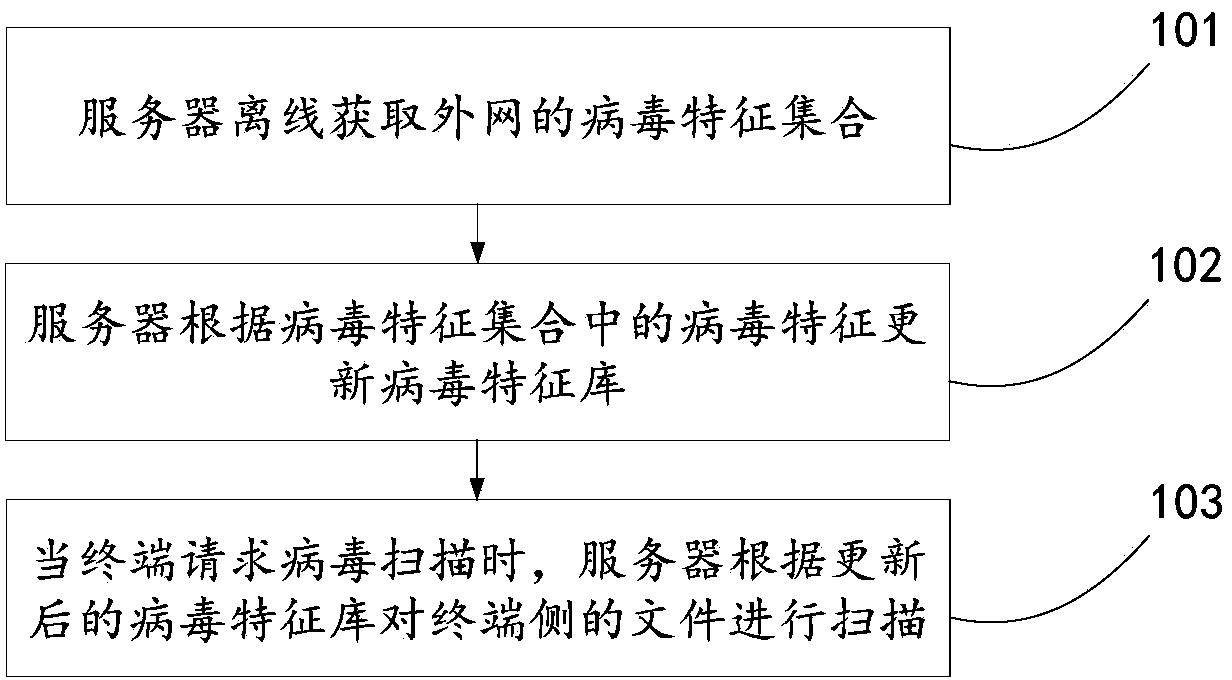
The invention discloses a method, a device and a system for searching and killing viruses, and relates to the technical field of the internet. The problem that the virus searching and killing rate in an environment of a separation network is solved. The method comprises the following steps of acquiring a virus characteristic set, which comprises virus characteristics of virus files in a preset period, of an outer network by using a server in an off-line manner; updating a virus characteristic library by using the server according to the virus characteristics in the virus characteristic set; and scanning files on a terminal side by using the server according to the updated virus characteristic library when a terminal requires to be subjected to virus scanning. The method is mainly used in a private cloud searching and killing process in the environment of the separation network.
Owner:BEIJING QIANXIN TECH
Cistanche deserticola medicinal material processing method
ActiveCN104138420AIncrease contentIncrease usageDigestive systemSexual disorderMedicineKilled process
The invention provides a cistanche deserticola medicinal material processing method including the following steps: 1) impurities in a fresh Cistanche deserticola medicinal material are removed, sediment is rapidly flushed away with water, the fresh Cistanche deserticola medicinal material is cut into thick slices; 2) high temperature enzyme killing process of the thick slices obtained in step 1 is performed for 1 and 15min; 3) after heat treatment the thick slices are lyophilized. Cistanche deserticola decoction pieces processed by the method are white in color, beautiful in appearance and dry in texture, and the content of main effective constituents of echinacoside and verbascoside is 10 times greater than that of a natural drying method.
Owner:PEKING UNIV
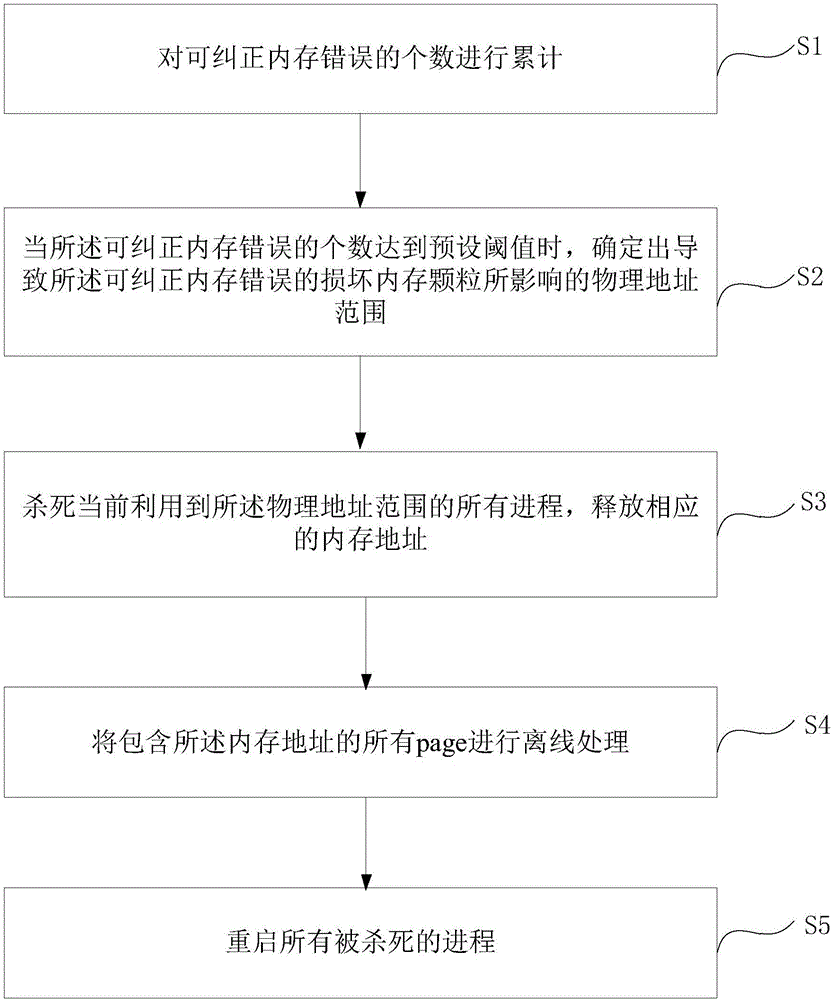
Memory error recovery method and device
InactiveCN106445720AAvoid uncorrectable errorsAvoid downtimeNon-redundant fault processingRedundant data error correctionRecovery methodMemory address
The application discloses a memory error recovery method and device, wherein the method comprises: adding up memory errors correctable; if the number of the memory errors correctable reaches a preset threshold, determining a physical address range affected by damaged memory particles causing the memory errors correctable; killing all processes using the physical address range, and releasing corresponding memory addresses; subjecting all pages comprising the memory addresses to offline processing; restarting all the killed processes. The method and device enable the memory particles already experiencing continuous correctable errors to be called again by an operating system, and accordingly more severe non-correctable errors due to the memory on the damaged particles are avoided to avoid downtime.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
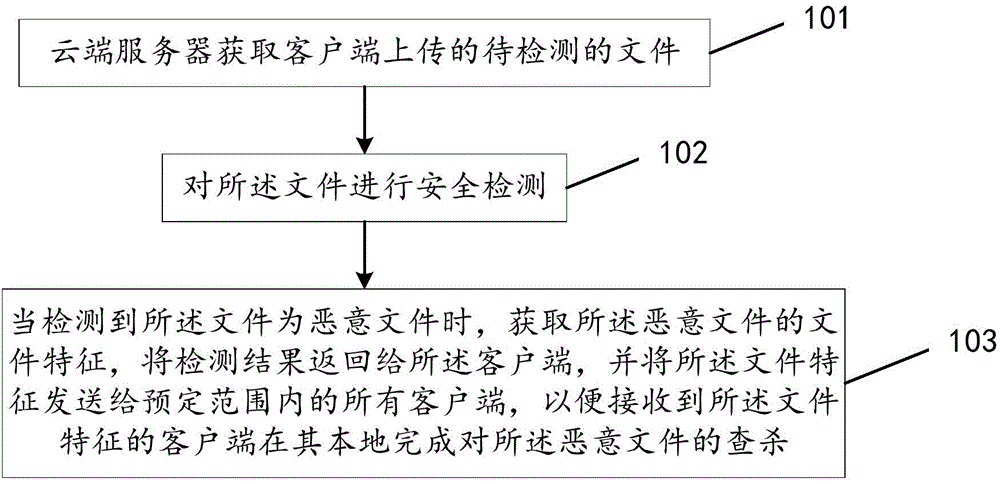
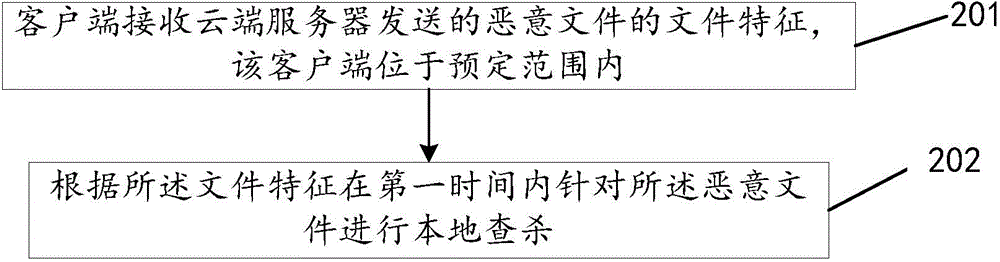
File checking and killing method, device and system
ActiveCN104537304AAccelerate the killing speedInhibited DiffusionPlatform integrity maintainanceTransmissionKilled processClient-side
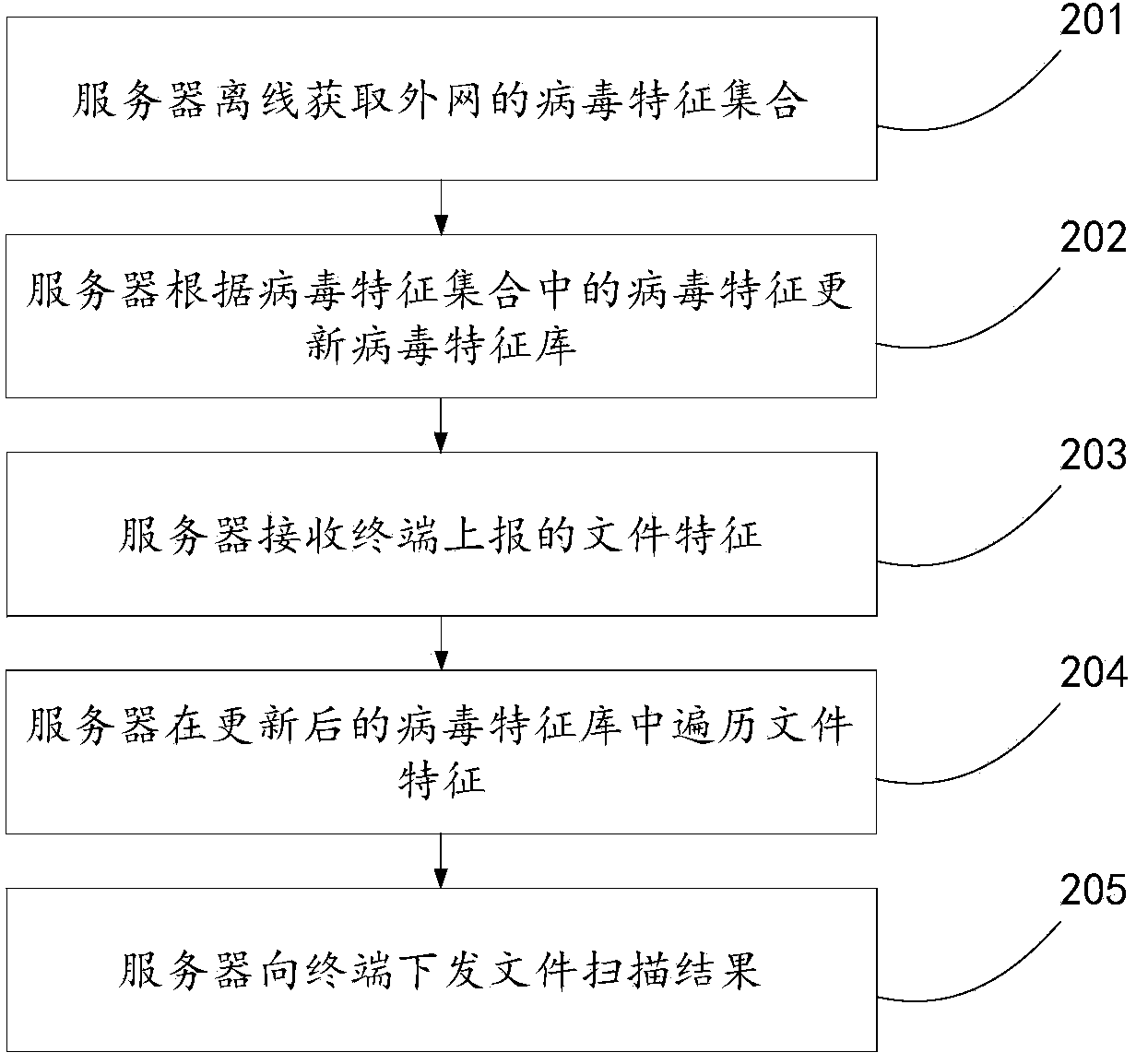
The invention discloses a file security checking and killing method, device and system, and relates to the information security technology. The file security checking and killing method, device and system mainly aim at effectively checking and killing rapidly-diffused vicious files. According to the main technical scheme, the method comprises the steps that a cloud server obtains a to-be-detected file uploaded by clients; security detection is carried out on the file; when it is detected that the file is a vicious file, file features of the vicious file are obtained, the detection result is returned back to the clients, and the file features are sent to all the clients within the preset range so that the clients receiving the file features can locally complete checking and killing of the vicious file. The clients receive the file features of the vicious file sent by the cloud server, the clients are located within the preset range, and the vicious file is locally checked and killed for the first time according to the file features. The file security checking and killing method, device and system are mainly used for the real-time file checking and killing process.
Owner:BEIJING QIANXIN TECH
Method and apparatus for protecting application program data
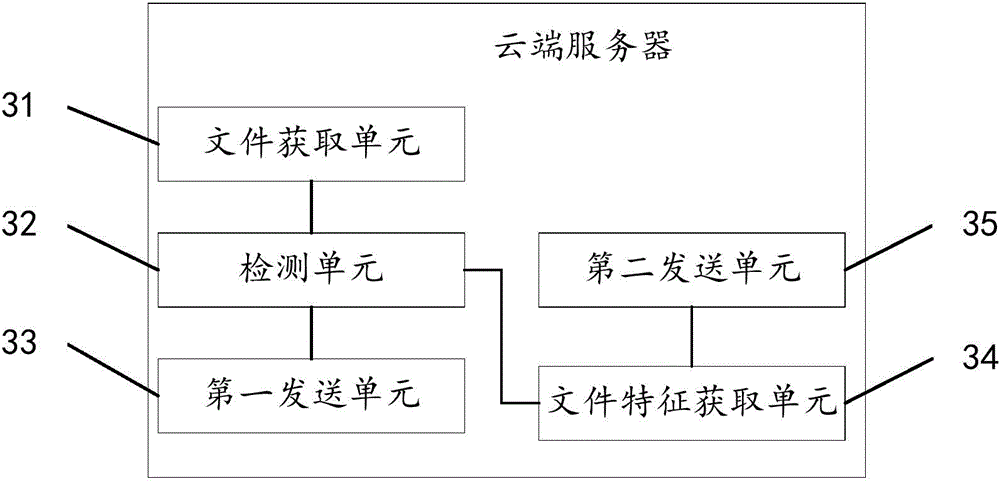
ActiveCN105718791AImprove experienceProtect dataPlatform integrity maintainanceOut of memoryKilled process
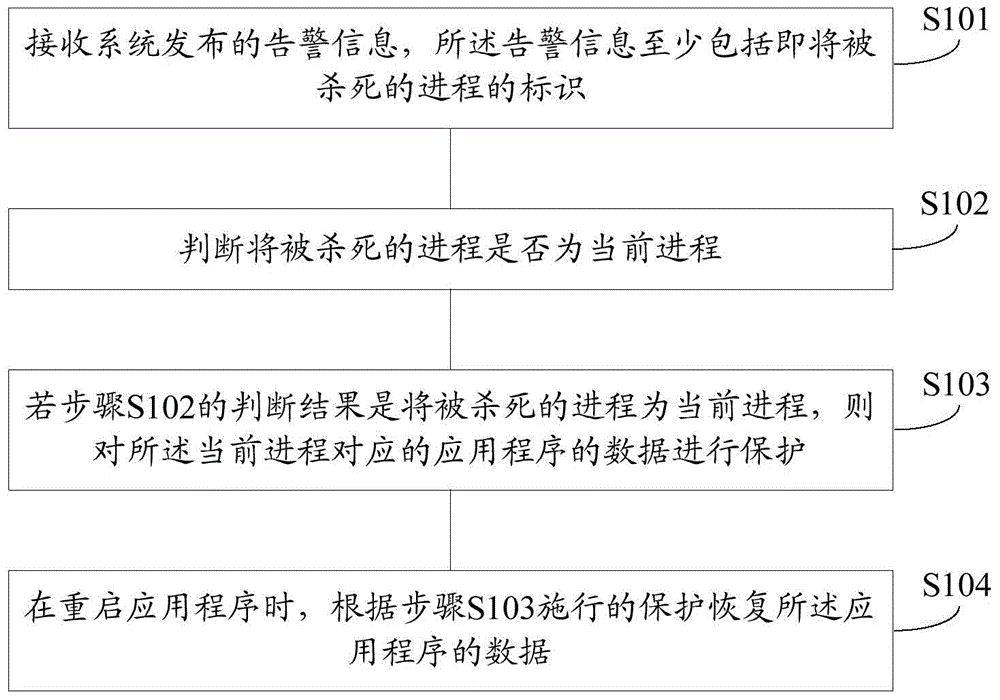
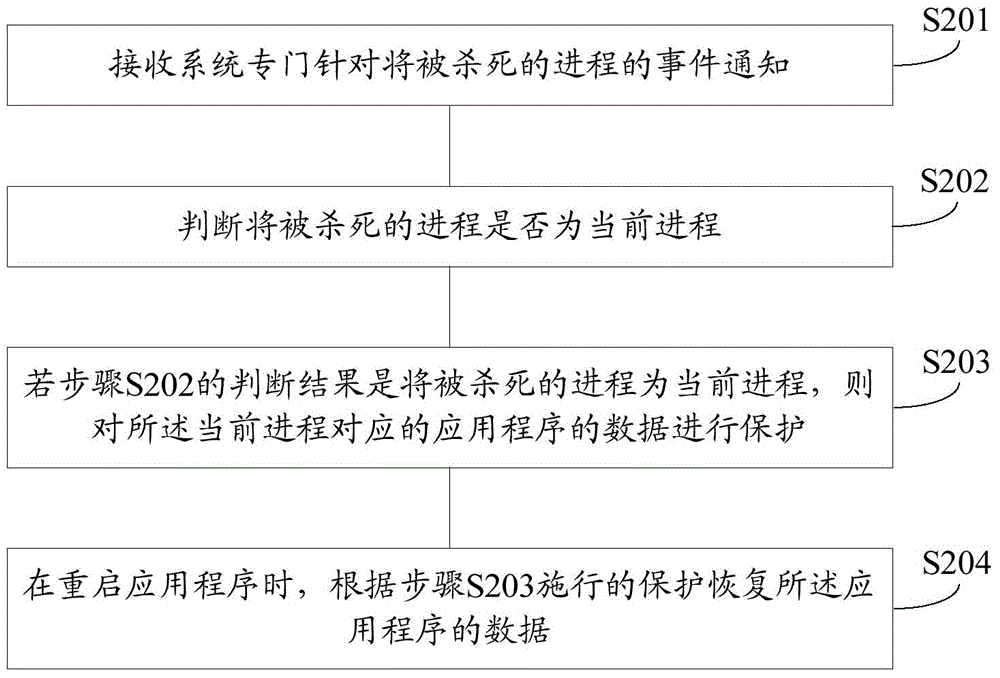
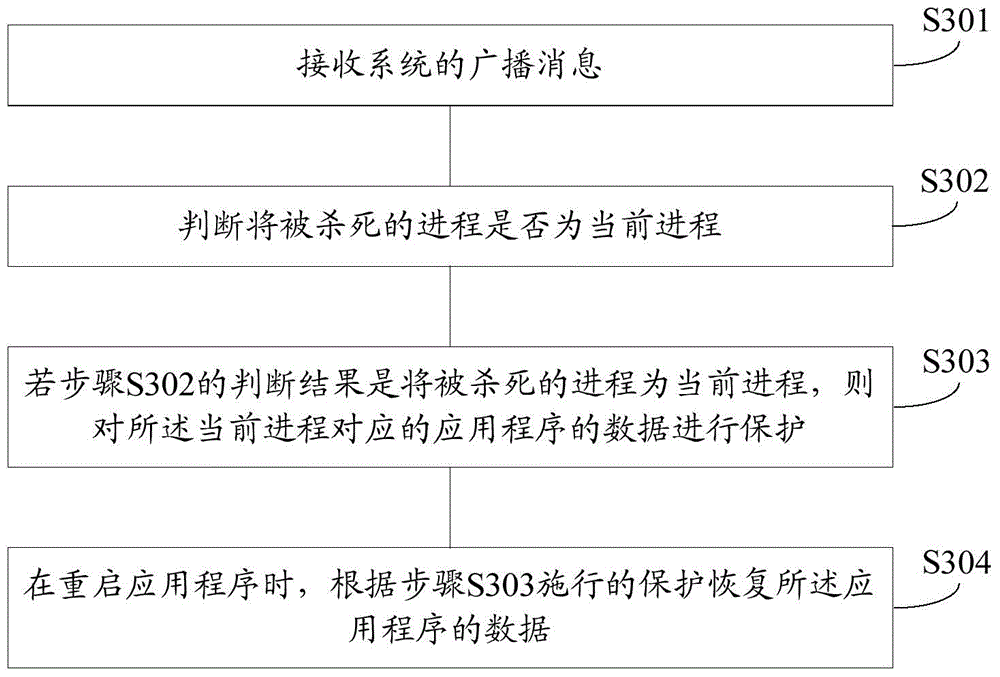
The invention provides a method and an apparatus for protecting application program data, and aims to solve the technical problem that user experience is lowered caused by the reason that certain processes are killed wrongly in the existing Low Memory Killer mechanism. The method comprises the steps of receiving alarm information issued by a system, wherein the alarm information at least comprises identification of a to-be-killed process; judging whether the to-be-killed process is the current process or not; if the to-be-killed process is the current process, protecting the data of the application program corresponding to the current process; and when the application program is restarted, restoring the data of the application program according to the implemented protection. Compared with the Low Memory Killer mechanism which kills certain process ''forcefully'' provided by the prior art, the method provided by the invention can ensure that the process is not killed wrongly even under an out-of-memory state; and instead, measures are taken in advance to effectively protect the data of the currently-operated application program, so that the user experience is improved.
Owner:TCL CORPORATION
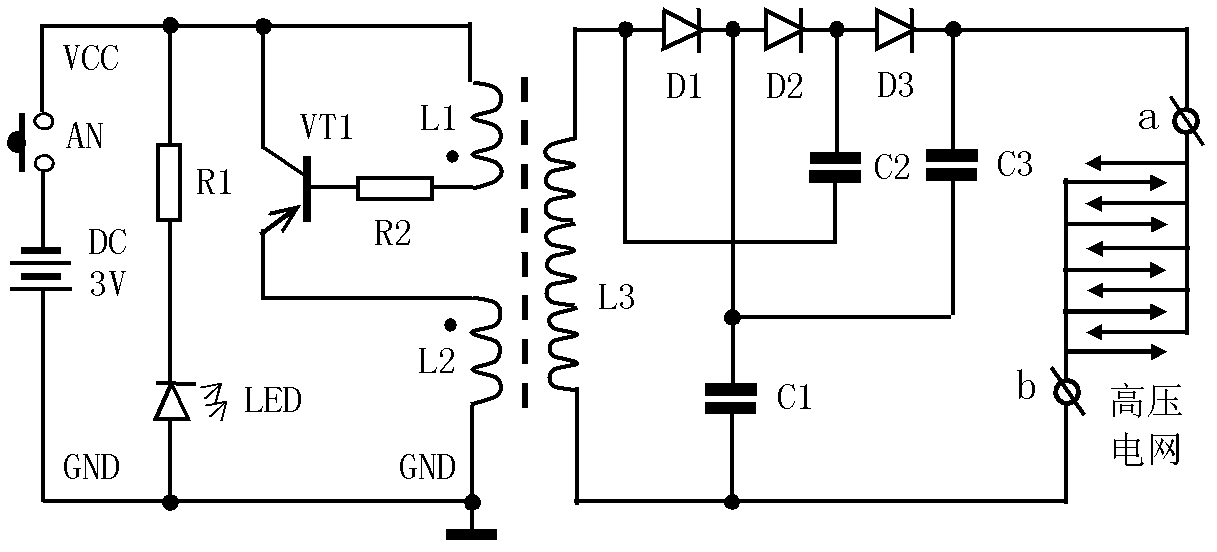
High tension shock type swatter for mosquitoes and flies
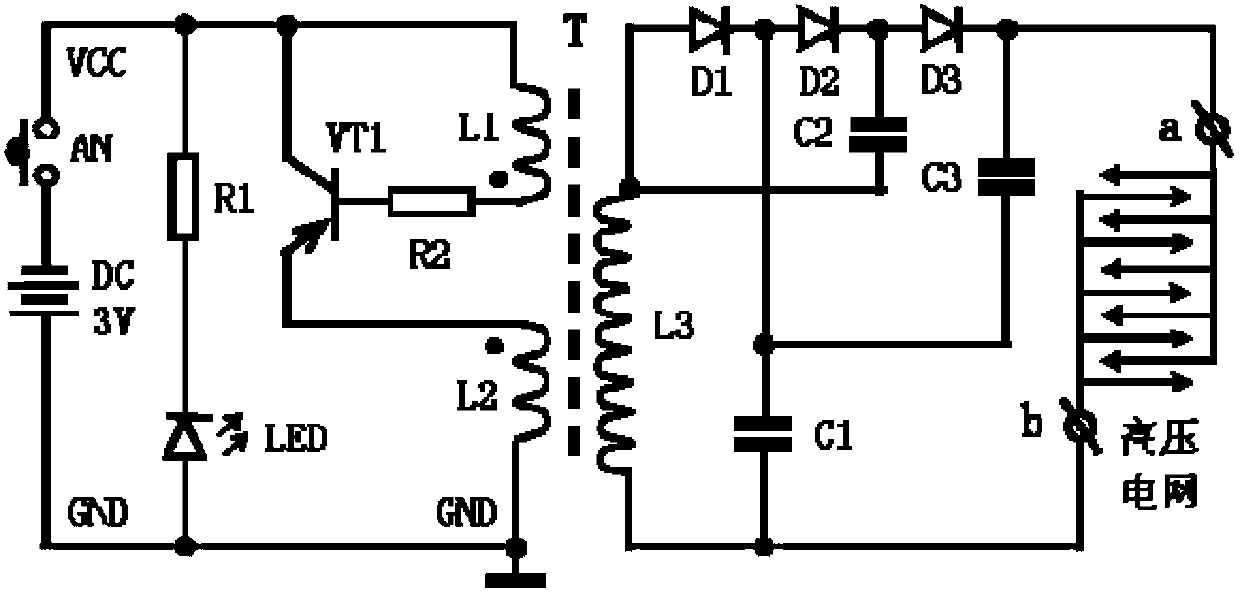
The invention belongs to the field of application of electronics, and relates to a high tension shock type swatter for mosquitoes and flies, which comprises a 3V direct-current power source, a high-frequency oscillating circuit, a booster circuit, a voltage tripler rectifier circuit, a high-tension power net, and a status indicator circuit. For protecting environment, use of physical ways to kill mosquitoes and flies is recommended, namely, no chemicals harmful to human bodies or causing environment pollution, such as mosquito coils, mosquito incense plates, pyrethrum, insecticides, mosquito repellents, flypaper, poison bait and the like, are used to eliminate flies, use of the chemicals is effective but may cause a certain degree of environment pollution, and the chemicals are not easy to use by children, pregnant women or special populations allergic to mosquito terminator chemicals. The high-tension power net on the swatter is used to kill mosquitoes and flies according to the principle of mosquito-fly elimination by high-tension electric shock, the whole mosquito-fly killing process is physical, and accordingly, environmental friendliness, harmlessness and effective prevention or control on various epidemic diseases transmitted by mosquitoes and flies are achieved.
Owner:黄勇
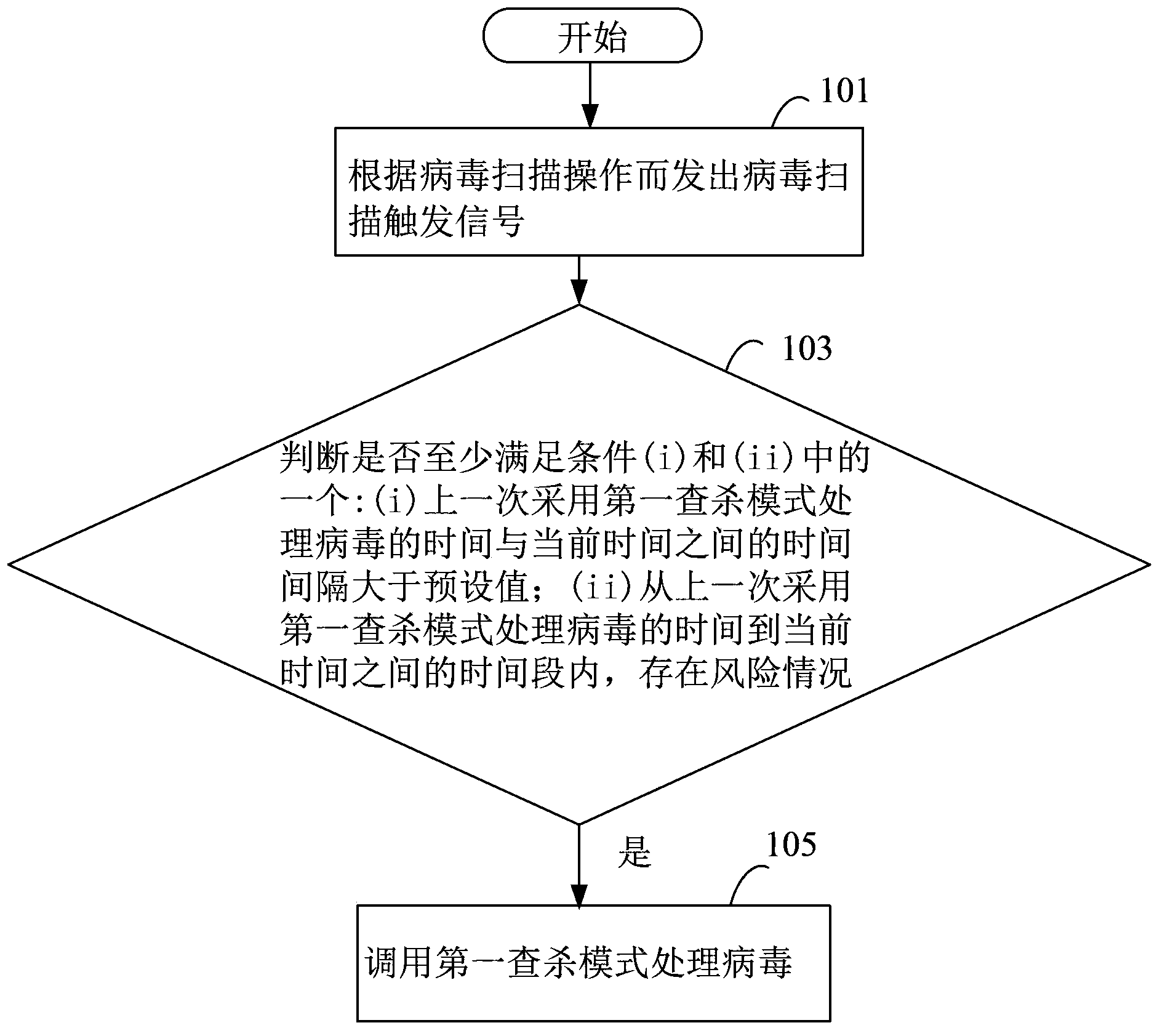
Virus processing method and device
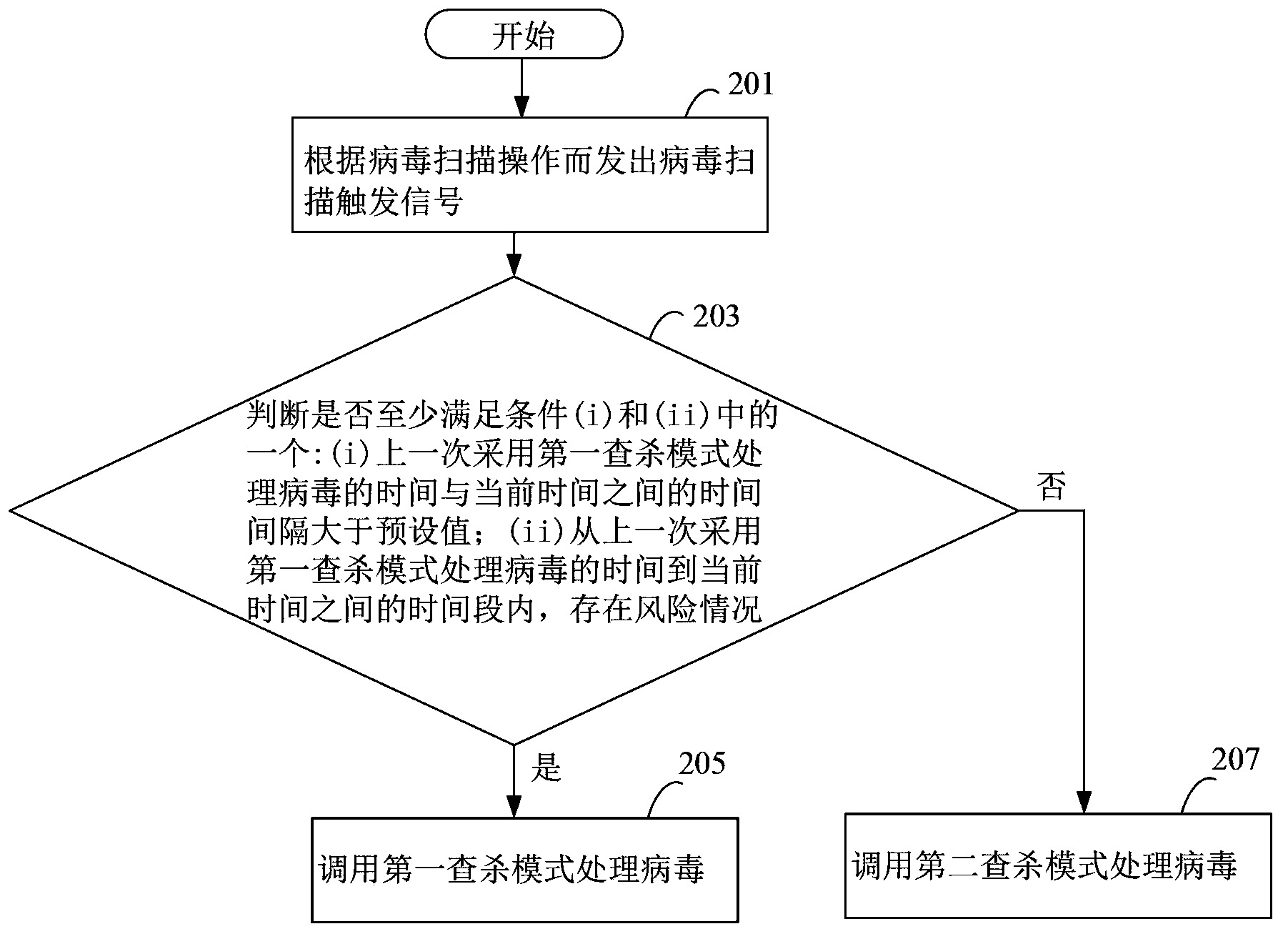
ActiveCN104239790AStop the spreadFast automatic resolutionPlatform integrity maintainanceTime segmentKilled process
The invention discloses a virus processing method and device, and belongs to the safety field. The virus processing method comprises the steps of: sending a virus scanning trigger signal based on a virus scanning operation; receiving the virus scanning trigger signal and judging whether at least one of conditions (i) and (ii) below is satisfied: (i) the time interval between the time taken for processing the virus by adopting a first searching and killing mode in the last time and the current time is greater than a preset value, and (ii) a risk condition exists within the time bucket between the time taken for processing the virus by adopting the first searching and killing mode in the last time and the current time; if at least one of the conditions (i) and (ii) is satisfied, calling the first searching and killing mode to process the virus. Through automatic selection of the virus processing mode, which searching and killing mode is most suitable for the current condition of an electronic device can be recognized rapidly and automatically in the virus searching and killing process, and the viral transmission is prevented in time.
Owner:TENCENT TECH (SHENZHEN) CO LTD
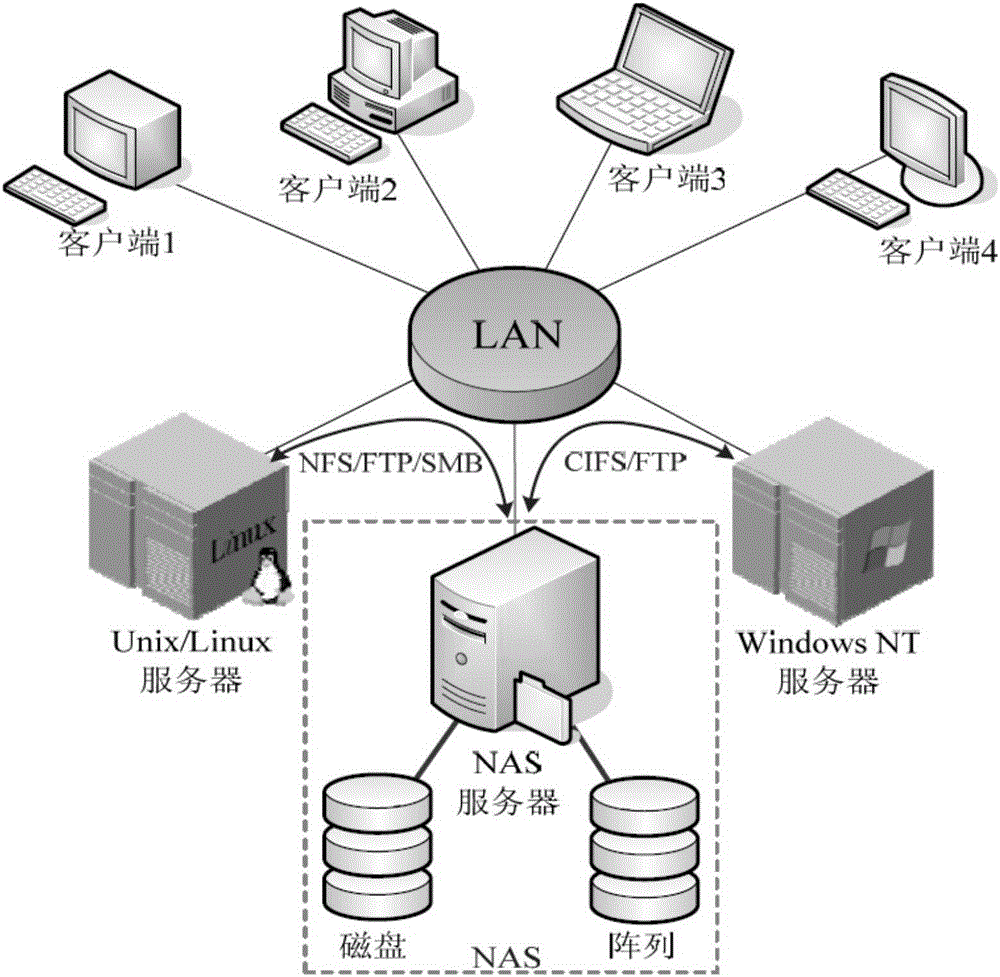
Anti-virus process scheduling method for network attached storage system
The invention discloses an anti-virus process scheduling method for a network attached storage system. The method includes the steps that an anti-virus service subprocess serves as a primary subprocess, and a monitoring process, a monofile real-time virus killing process and a TCP command processing service process serve as secondary subprocesses scheduled by the primary subprocess; when the NAS system runs, the anti-virus service subprocess starts the secondary subprocesses and then monitors the secondary subprocesses; when operation consuming resources seriously occurs, the anti-virus service subprocess makes memory and CPU sources exclusively occupied and used by a preset secondary subprocesses and meanwhile quits the other secondary subprocesses temporarily. According to the method, complex and diverse process control is achieved on network storage equipment with limited NAS resources and other hardware resources through a unique process protection mechanism, an important task exclusive occupation strategy and an unconventional process communication mode, and therefore the key process of the NAS system can occupy system resources exclusively as needed.
Owner:北京北方新宇信息技术有限公司
Operation system background process searching and killing method and system and storage device
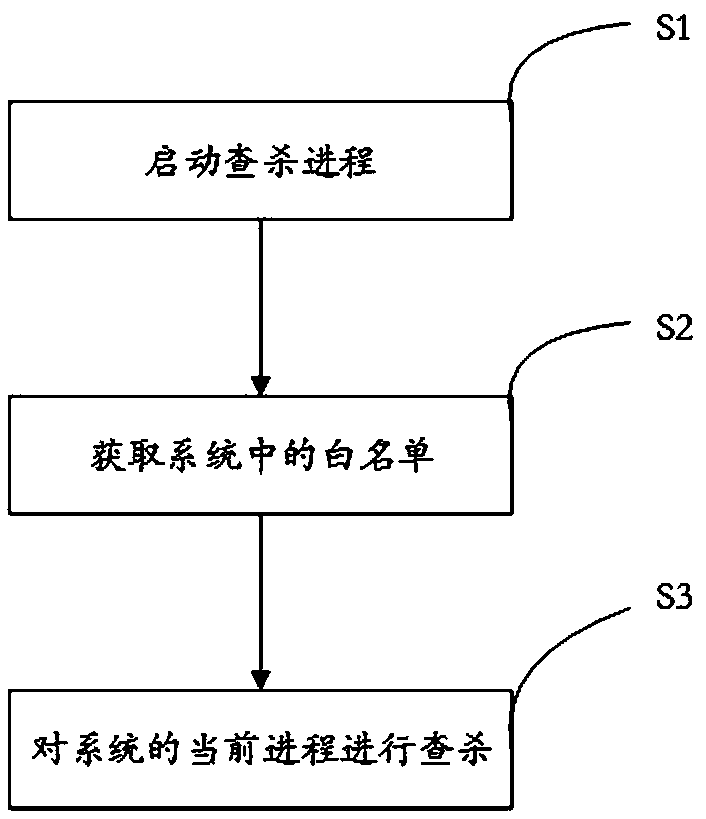
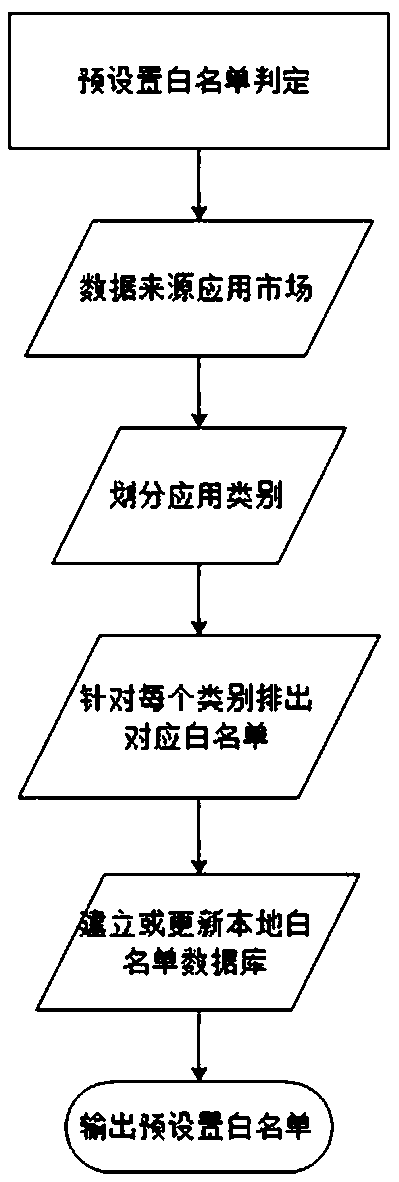
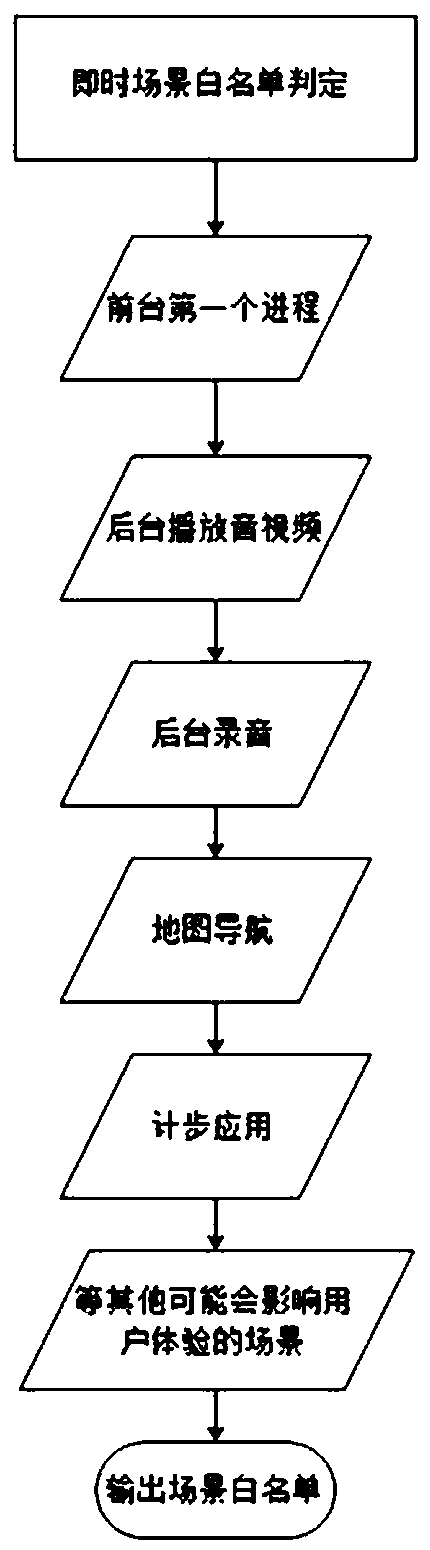
InactiveCN108304263AIntelligent managementGuaranteed practicalityResource allocationOperational systemSimulation
The invention discloses an operation system background process searching and killing method and system and a storage device. The method comprises a starting step: starting a searching and killing process; an obtaining step: obtaining whitelists in the system, wherein the whitelists comprise a preset whitelist, an instant scene whitelist and a common application whitelist, the preset whitelist is preset in the searching and killing process, the instant scene whitelist is generated according to the application environment of the current system, and the common application whitelist is generated according to application using habits of recent users; and a searching and killing step: searching and killing the current process of the system, retaining processes on the whitelists and closing processes not on the whitelists. According to the method, whitelists can be automatically set and processes can be prevented from being mistakenly killed to influence the user experience.
Owner:XOLO TECH (SHENZHEN) LTD
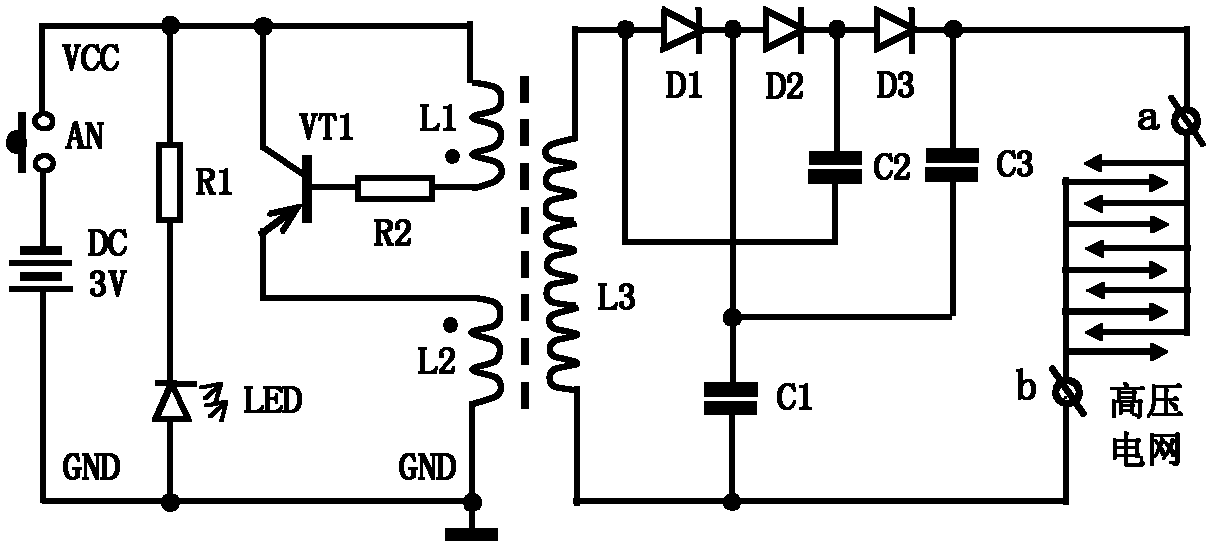
Handheld high-tension flyswatter
The invention provides a handheld high-tension flyswatter. The handheld high-tension flyswatter is technically characterized by comprising a 3V direct current source, a high-frequency oscillating circuit, a booster circuit, a triple voltage rectifier circuit, a high-tension net, and an operating state indicator circuit. Killing flies in physical ways are advocated to protect the environment, namely no chemicals harmful to human bodies and pollutive to environment, such as pyrethrum, various insecticides, flypaper and poison baits, are used to kill the flies. Using the chemicals are of certain effect but are of certain pollution to the environment, and are less easy to use for children, pregnant women or special populations sensitive to fly chemicals. According to the principle of killing flies by high-tension shock, the high-tension net on the flyswatter is used to kill the flies. The whole fly killing process is physical. Therefore, effectively preventing or controlling various epidemics, spread by flies, and environmental friendliness are achieved.
Owner:魏传永
A rapid kill method for blowout wells
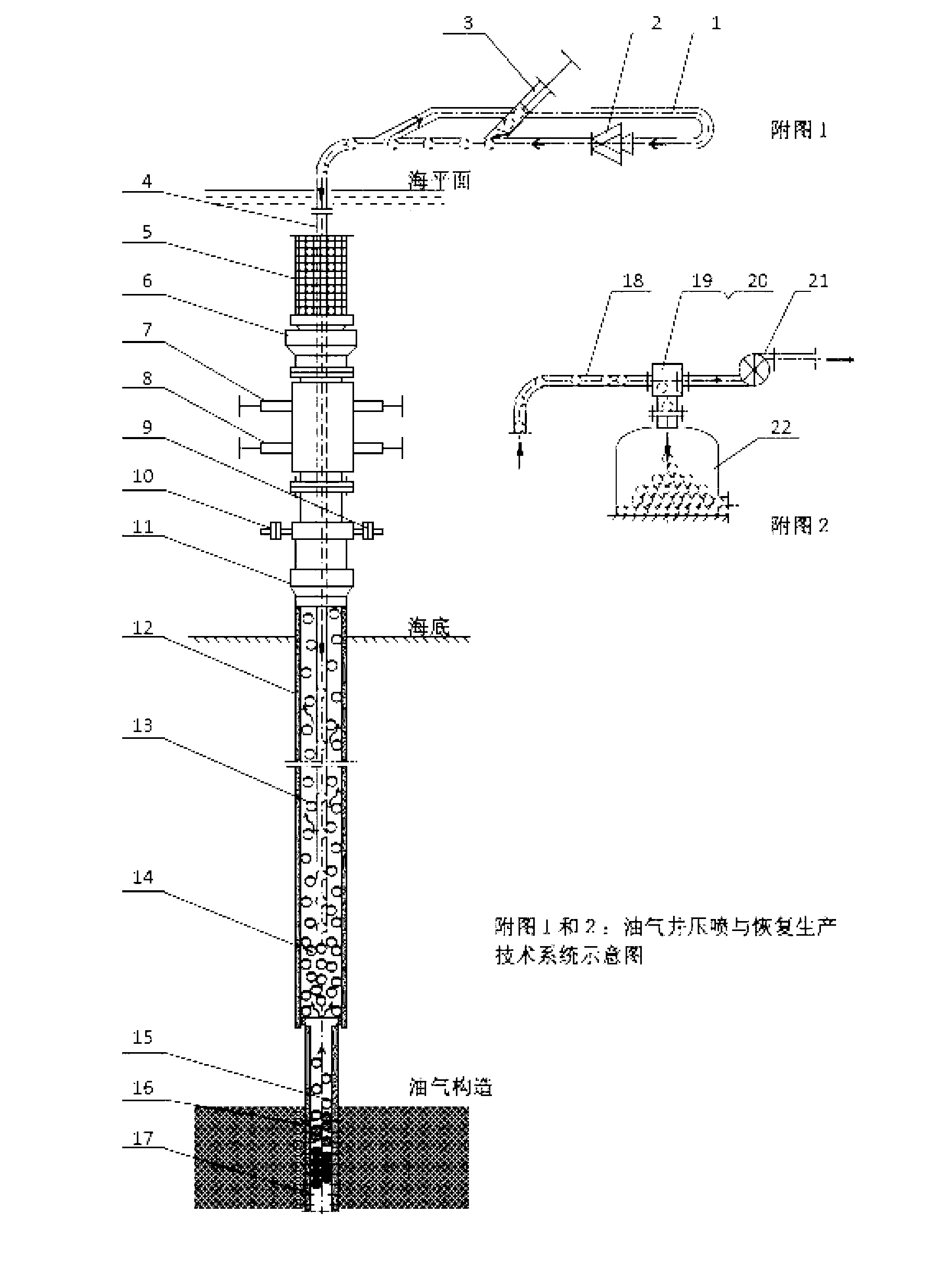
ActiveCN103080464AEffective pressure injectionGuaranteed reliabilityFlushingSealing/packingSolid particleKilled process
This invention is a rapid and reliable kill and restoration technique and its implementation system for the well blowout accidents. It uses solid particles to block, suppress and greatly reduce the blowout flow to gain time for repair or replacement of the damaged blowout preventer and other devices, and connection of production pipelines. It then takes out some of the solid particles to restore well production. In such a way, environmental damage is greatly reduced and the well is kept as a valuable production asset. While any shape of solid particles may be used, the ball shape is an optimum for the kill and restoration operation; hence kill balls are the recommended solid particles. An implementation system for the ball kill procedure consists of a tubing system, a blower or a pump, a ball injection device and a cage. The cage mounted on the tubing and sits on top of the well will temporally contain the blown out balls at the early stage of the kill process. Balls in the cage will fall down to the well as the flow is reduced. An implementation system for the restoration process consists of a tubing system, a pump and a balls storage tank.
Owner:刘现华
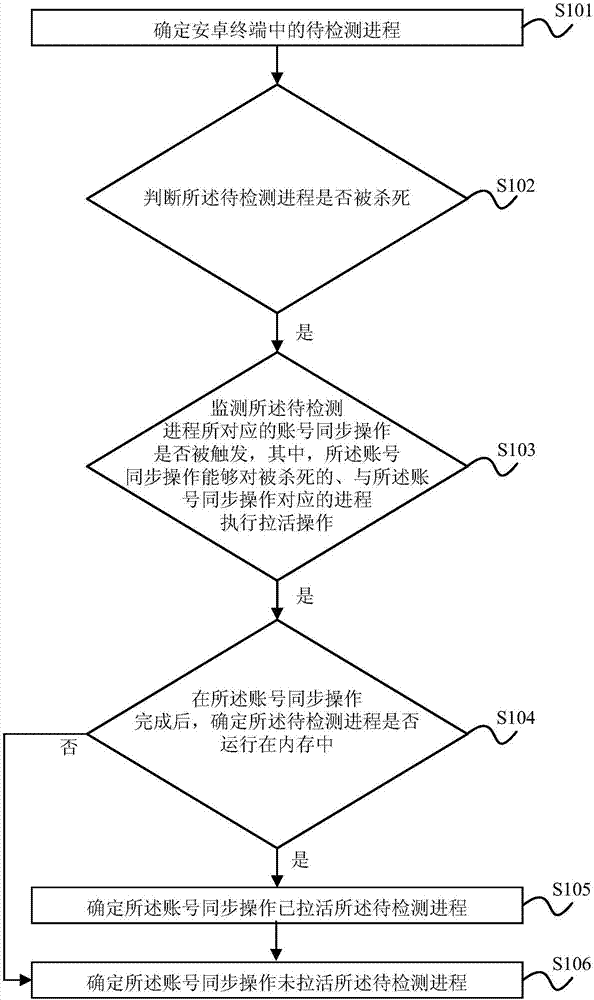
Process detection method and apparatus, electronic device, and readable storage medium
Embodiments of the invention provide a process detection method and apparatus, an electronic device, and a readable storage medium. The method comprises the steps of determining a to-be-detected process in an android terminal; judging whether the to-be-detected process is killed or not; if yes, monitoring whether account synchronization operation corresponding to the to-be-detected process is triggered or not, wherein the account synchronization operation can execute restoration operation on the killed process corresponding to the account synchronization operation; if the account synchronization operation is triggered, determining whether the to-be-detected process runs in a memory or not after the account synchronization operation is finished; if the to-be-detected process runs in the memory, determining that the account synchronization operation already restores the to-be-detected process; and if the to-be-detected process does not run in the memory, determining that the account synchronization operation does not restore the to-be-detected process. By applying the method and the apparatus, whether the killed process corresponding to the account synchronization operation is successfully restored or not after the account synchronization operation is executed can be detected.
Owner:KINGSOFT
Reclaimed water supplying-type surface water deep purification combined process method and device
ActiveCN102531230AGood removal effectGood coagulation effectWater/sewage treatment by ion-exchangeWater/sewage treatment bu osmosis/dialysisFiltrationSurface water
The invention relates to a reclaimed water supplying-type surface water deep purification combined device comprising a magnetic ion exchange resin mixing reaction precipitation system, a coagulation reaction precipitation system, an ozone contact reaction tank, and an ultrafiltration membrane filtration system which are connected in order. The invention also relates to a method for purifying water by using the device, which comprises the following steps: pumping sewage into the magnetic ion exchange resin mixing reaction precipitation tank through a pipeline, removing part of suspensions and soluble organic matter; delivering the supernatant into the coagulation reaction precipitation tank, removing most suspensions, total phosphor and part of organic matter under the action of a coagulant; delivering the supernatant into the ozone contact tank, completing algae cell lysis and algae killing process by ozone, delivering ozone oxidation effluent into the ultrafiltration membrane filtration system, filtering the effluent through the membrane surface under the action of a vacuum suction pump, delivering the effluent into a clean water tank.
Owner:BEIJING WATER SCI & TECH INST
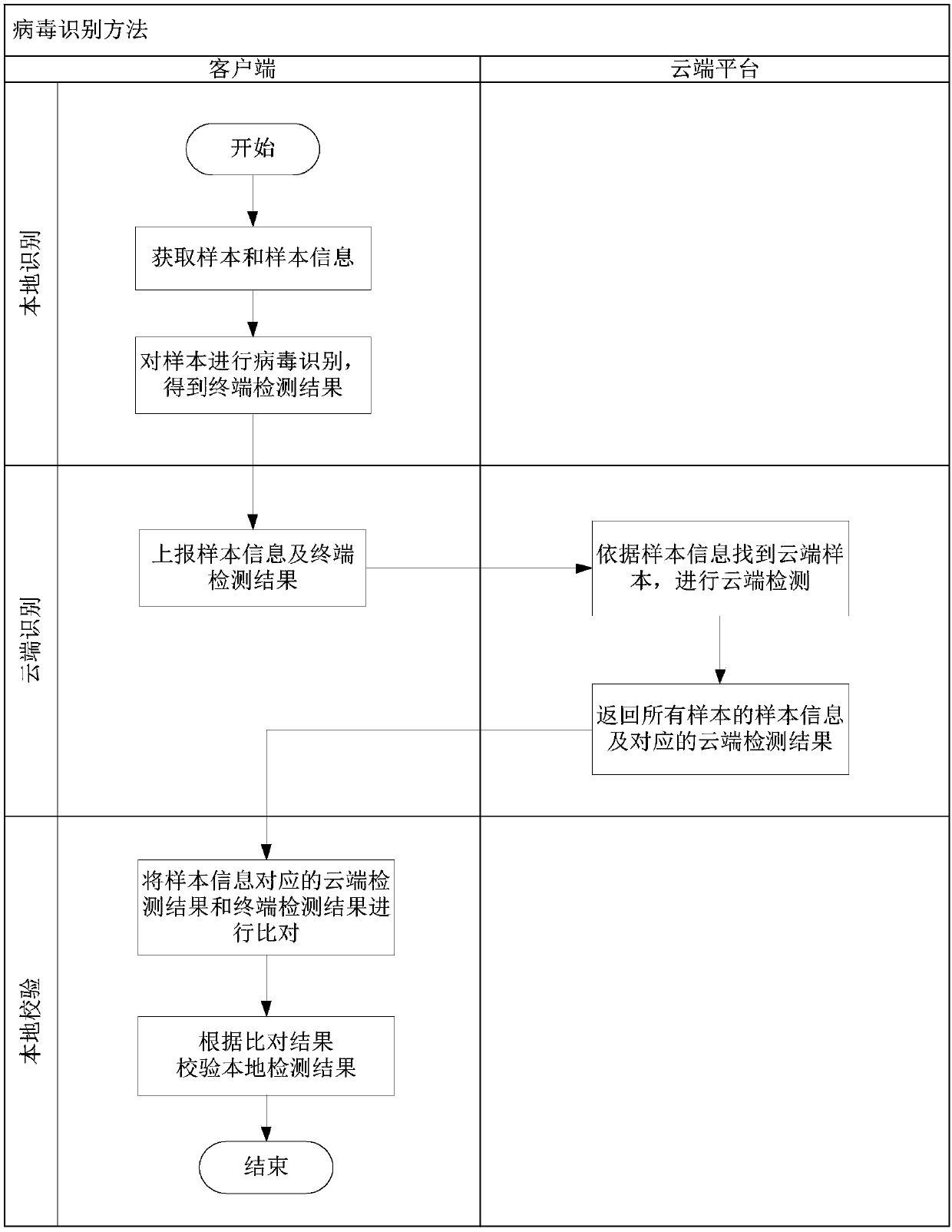
Computer virus recognition method and system based on cloud computing
ActiveCN107689975AImprove experienceReduce consumptionPlatform integrity maintainanceTransmissionCloud detectionKilled process
The invention relates to the field of computer security, in particular to a computer virus recognition method and system based on cloud computing. The method comprises the steps that a cloud server receives detection information uploaded by a terminal, wherein the detection information comprises sample information and a terminal detection result, and the terminal detection result represents a virus recognition result obtained after the terminal conducts virus recognition on samples; the cloud server conducts virus detection on the samples corresponding to the sample information to obtain a cloud detection result; and the terminal detection result and the cloud detection result are compared to judge whether or not the terminal detection result and the cloud detection result are consistent,and if the terminal detection result and the cloud detection result are consistent, the cloud server does not return content to the terminal. According to the computer virus recognition method and system, the terminal detection result and the cloud detection result are compared by a cloud, and the data processing stress of the terminal is relieved; and meanwhile, only the necessary information occupying a little traffic is transmitted in the packet transmitting and returning stages, and the traffic consumption in the cloud killing process is reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Control method of summer shoots at fruiting period of citruses
InactiveCN107750802AReduce usageImprove qualityCultivating equipmentsHorticulture methodsFruit treeMain branch
The invention discloses a control method of summer shoots at a fruiting period of citruses and relates to the technical field of fruit tree planting. The control method comprises the following steps:forbidding fertilizer: forbidding application of the fertilizer with high nitrogen content; carrying out first-time layering: in a layering process, adopting a sectional two-grade layering method; inthe layering process, starting from a base part of a selected branch; supporting the adjacent part of the base part by one hand as a supporting point and downward pressing the branch at a part which is 20cm to 30cm above the supporting point by the other handle until the section is bent; carrying out second-time layering; after the first-time layering is carried out for 20 to 25 days, carrying outthe second-time layering; carrying out first-time girdling: after carrying out the second time of layering for 7 to 10 days, carrying out girdling on main branches by utilizing a girdling knife; onlypeeling a phloem with the width of 1mm to 3mm and not injuring a xylem, wherein the distance between the two times of girdling is 5cm to 7cm; carrying out second-time girdling: after the first-time girdling is carried out for 20 days, carrying out the second-time girdling. By adopting the control method disclosed by the invention, the problems in manual shoot removing and medicine shoot killing processes can be solved.
Owner:鹿寨县浦发水果专业合作社
Method for preventing quick-frozen taro from browning
InactiveCN103636745APrevent browningEnsure safetyFruits/vegetable preservation by heatingFruits/vegetable preservation by freezing/coolingFood safetyPreservative
A disclosed method for preventing quick-frozen taro from browning comprises the following steps: performing end-cutting and peeling on fresh taro, then cutting fresh taro into cuboid taro strips with the dimension of 50 mm*50 mm*100 mm or less; dipping the cut taro strips within 1 min into water with a temperature of 80 DEG C-100 DEG C and blanching for 1-5 min, and taking out; performing vacuum packaging by utilizing vacuum boiling packaging bags; putting into a high-temperature sterilization pot and killing enzyme with a temperature of 90 DEG C-110 DEG C for 3-8 min; after enzyme killing process is finished, immediately performing quick-freezing at -22 DEG C to -25 DEG C until the center temperature reaches -18 DEG C; and storing in a -18 DEG C low-temperature warehouse. According to the method, no any preservatives or bleaching agents are used, so that the purpose of preventing the product from browning is realized and the foodstuff safety is guaranteed.
Owner:JIANGSU AGRI ANIMAL HUSBANDRY VOCATIONAL COLLEGE
Preparation method of dandelion functional tea
The invention discloses a preparation method of dandelion functional tea. The preparation method comprises enzyme killing, fumigation, enzyme deactivation, freezing, moisture regaining, and shaping; the enzyme killing process is as follows: non-flowering or primary-flower dandelion tender seedlings are subjected to anaerobic conditions at the temperature of 80-100 DEG C for 1-5 minutes; the fumigation is carried out in a closed heat preservation box, an acetic acid aqueous solution is used for fumigation to ensure that the moisture content of the dandelion is kept at 40-60%; the enzyme deactivation is as follows: carrying out rapid enzyme deactivation on the fumigated dandelion for 0.5-2 hours at the temperature of 70-80 DEG C under the condition of vacuum pumping by using a microwave enzyme deactivation machine, wherein the moisture content of the dandelion after the enzyme deactivation is 5-15%; the freezing is as follows: keeping the dandelion at 0 DEG C for 2-4 hours in a refrigerator, and then taking out; the moisture regaining is that frozen dandelion tea is placed in air for 1-2 hours; and then shaping is carried out after the moisture regaining is carried out, wherein the temperature of a pot for the shaping is 100-120 DEG C;, and the moisture content of the tea is 10% or less after the shaping is finished.
Owner:CHANGCHUN UNIV
Mercy killing device for small animals
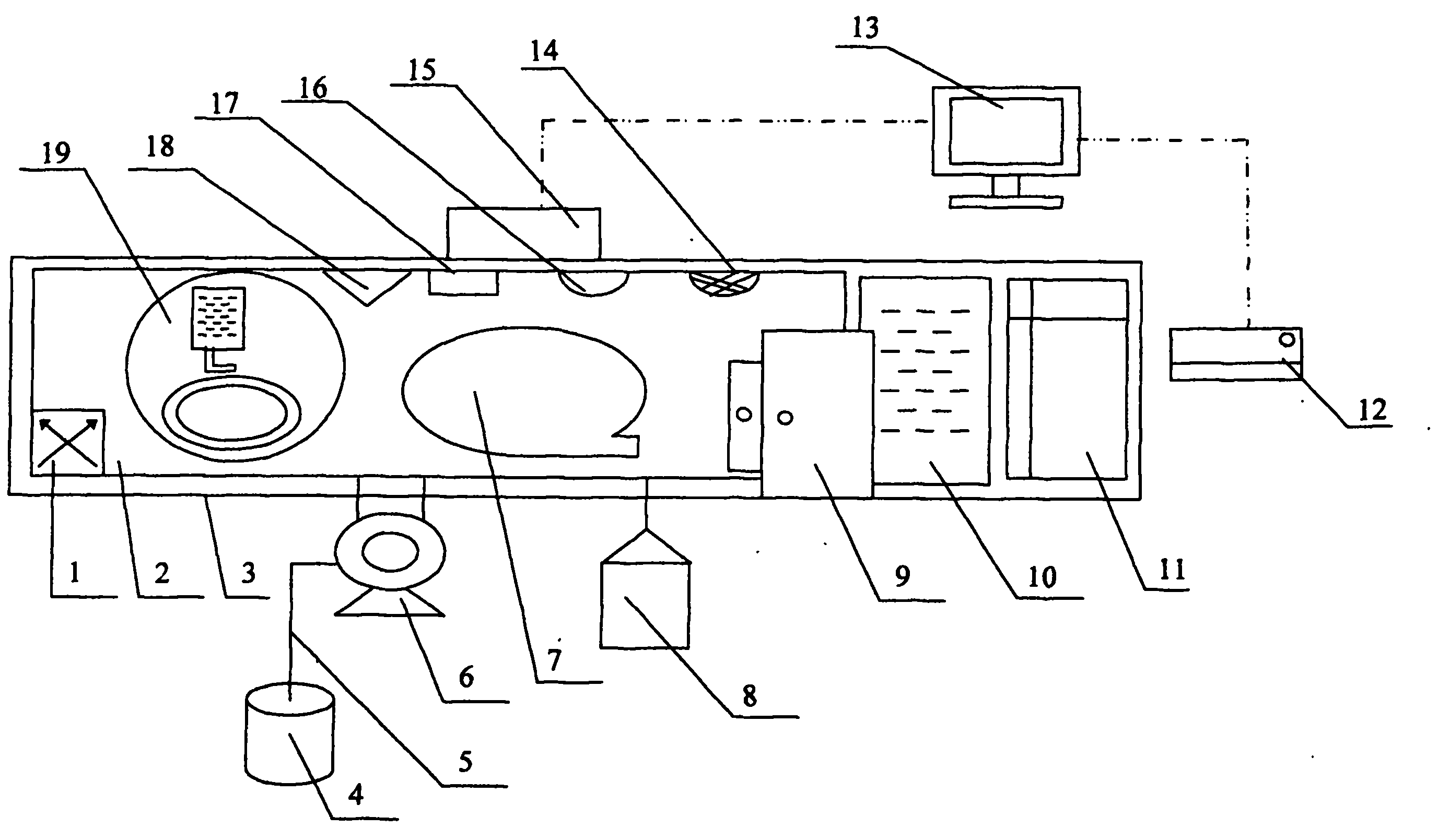
ActiveCN102007896AEuthanasia is quick and painlessSolve technical problemsFumigatorsFresh airEngineering
The invention provides a mercy killing device for small animals, comprising an airtight fixed-volume animal cabin with an isolating door, wherein a food area, a drinking area and a playing area are arranged in the airtight fixed-volume animal cabin; a computer main control instrument is used for controlling a background music, light and light color regulating system, a temperature and humidity regulating system, an anesthesia gas generator, a quick filling system of nitrogen or other inert gases, a fresh air quick replacing device, an internal cleaning and sterilizing system of the animal cabin, and the like to complete the killing process of animals; a negative-pressure shielding cabin is arranged outside the animal cabin, a cleaning and sterilizing tank and a sealed packing system are arranged in the negative-pressure shielding cabin, and certain negative pressure exists in the negative-pressure shielding cabin relative to an operator so that harmful and odorous gas pollution can be prevented; a computer is used for automatically recording the whole mercy killing process and printing a report; and exhausted gas from the animal cabin and the negative-pressure shielding cabin can be safely exhausted after being treated by a purifying and adsorbing system. The device has the effect of realizing a humane killing function when small animals, such as experimental animals, work animals, deserted animals, and the like must be killed and solves the technical problem on an animal welfare aspect.
Owner:范维林
Biological film cleaner, preparation thereof and application of cleaner
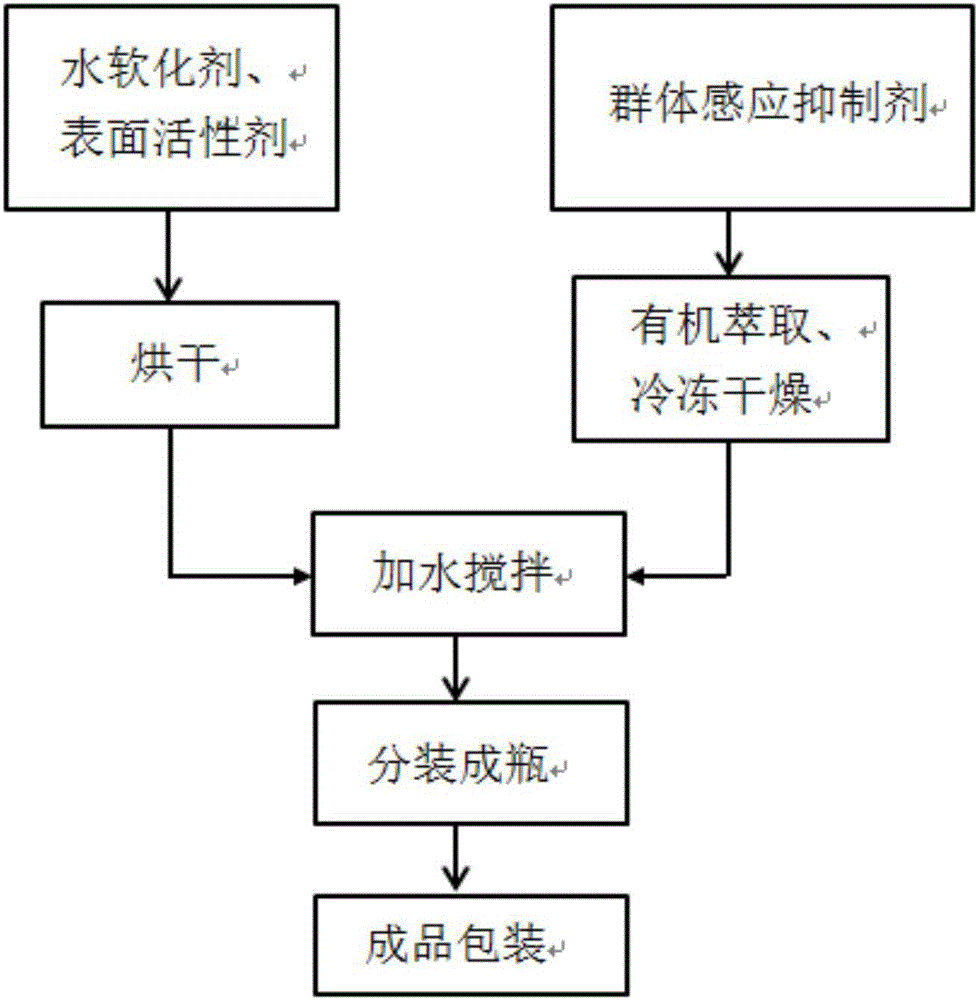
ActiveCN106635446AGuaranteed validityReduce usageInorganic/elemental detergent compounding agentsCationic surface-active compoundsMentholMicroorganism
The invention discloses preparation of a biological film cleaner and an application of the cleaner. The biological film cleaner is prepared from, in weight percentage, 45-55% of quorum sensing inhibitors, 25-35% of surface active agents and 15-20% of water softeners. The quorum sensing inhibitors are prepared by mixing, in weight percentage, 30-40% of pineapple-ketone, 30-40% of menthol and 30-40% of vanillic aldehyde. The quorum sensing inhibitors serve as main components, biological film generation of pathogenic bacteria and growth of bacteria are inhibited by inhibiting quorum sensing behaviors of microorganisms instead of resisting and killing the bacteria by compounds according to existing most cleaners, and the problem of drug resistance in the bacteria killing process is avoided.
Owner:杭州众立化工科技有限公司
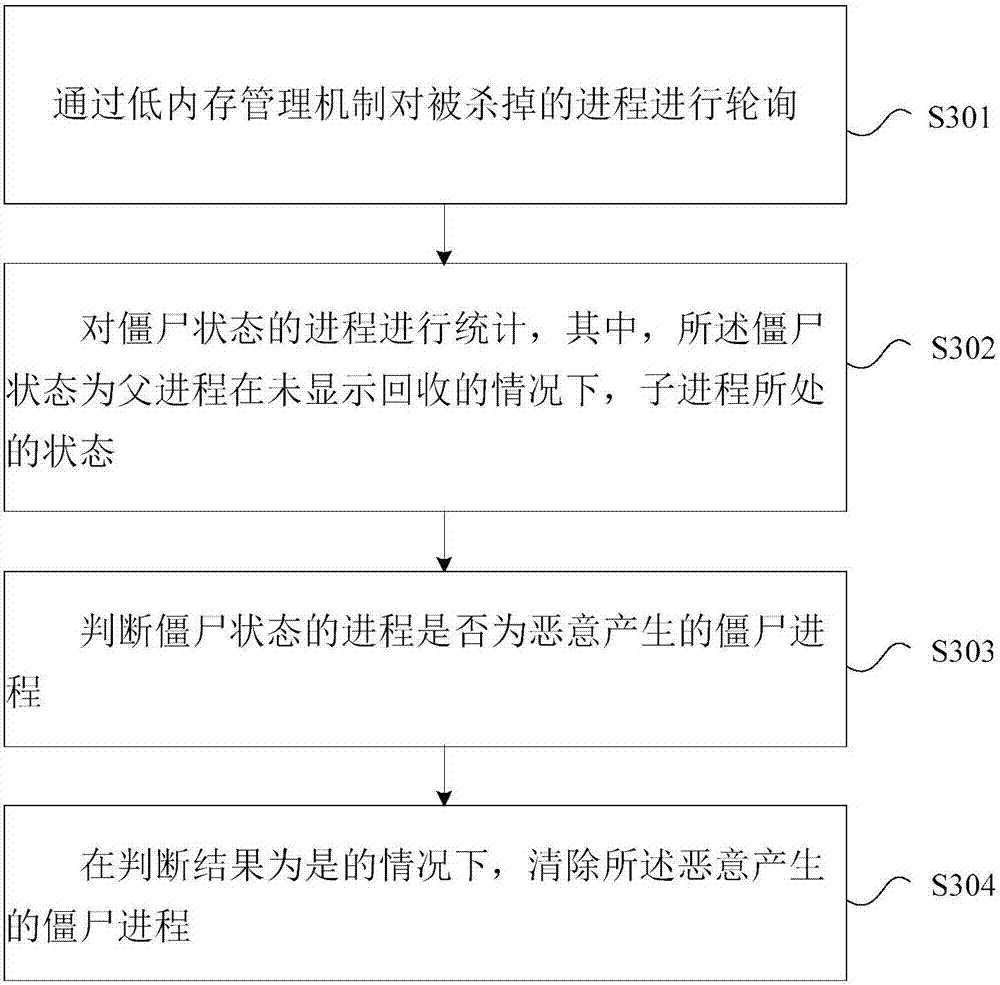
Process processing method, mobile terminal and computer readable storage medium
InactiveCN107239332AImprove experienceFix not workingProgram initiation/switchingResource allocationKilled processZombie process
The invention discloses a process processing method. Roll polling is conducted on killed processes through a low-memory management mechanism, and statistics is conducted on processes in a zombie state, wherein the zombie state is the state of child processes under the situation that parent process recovery is not displayed; whether the processes in the zombie state are maliciously produced zombie processes or not is judged; under the situation that a judgement result is yes, the maliciously produced zombie processes are removed. The invention further discloses a mobile terminal and a computer readable storage medium. The problem that in the related arts, limited process numbers are rapidly consumed if the malicious processes constantly produce a large number of zombie processes and accordingly a system cannot work normally is solved, the process numbers are not maliciously consumed by finding out and removing the maliciously produced zombie processes, and the user experience is improved.
Owner:NUBIA TECHNOLOGY CO LTD
Valuation method for specific killing function of specific cytotoxicity T lymphocyte
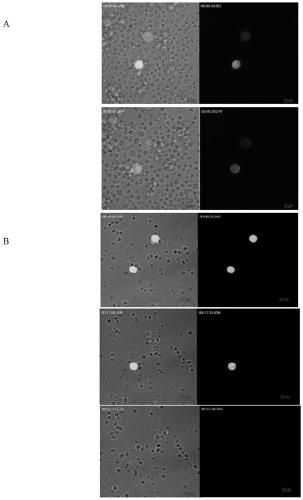
InactiveCN110358805AGood treatment effectImproved prognostic analysisMicrobiological testing/measurementMaterial analysisCytotoxicityLive cell imaging
The invention provides a valuation method for a specific killing function of a specific cytotoxicity T lymphocyte, which belong to the field of immunotherapy. The method comprises the following steps:(1) treating the target cells with specific cytotoxicity T lymphocyte constructed aiming at the target cells to-be-killed; (2) detecting the killing process of specific cytotoxicity T lymphocyte on the target cells by Live-Cell Imaging; and (3) employing real-time unlabeled cell analysis (RTCA) to detect the killing efficiency and killing ability of specific cytotoxicity T lymphocyte to target cells; wherein steps (2) and (3) are not ordered, or can be carried out at the same time.
Owner:BEIJING UNIV OF TECH
Method for cleaning space of set top box
InactiveCN106331861AEasy to useSolve the problem of insufficient memory spaceSelective content distributionKilled processComputer science
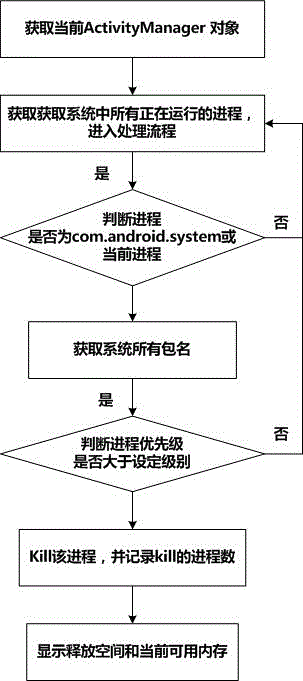
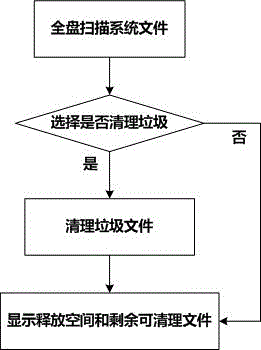
The present invention discloses a method for cleaning a space of a set top box. The method comprises memory cleanup and garbage cleanup. The memory cleanup comprises the following steps of acquiring a current Activity Manager object; acquiring all running processes in a system, and going to a processing flow; determining whether the processes are a com. android. system or a current process; if the processes are the com. android. system or the current process, going back and reacquiring all running processes in the system; if the processes are not the com. android. system or the current process, acquiring all package names of the set top box system; determining whether process priorities are higher than a set level; if the process priorities are higher than the set level, killing the processes, and recording a quantity of killed processes; and if the process priorities are not higher than the set level, going back and reacquiring all running processes in the system, and displaying the freed space and the currently available memory after cleanup.
Owner:SICHUAN TIANYI COMHEART TELECOM
Artificial cultivation method for American cockroaches
ActiveCN101427665BIncrease productionImprove hatchabilityAnthropod material medical ingredientsFood processingIlluminanceKilled process
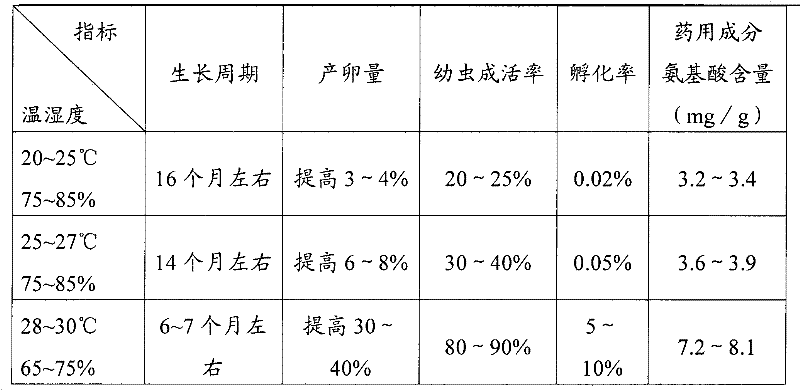
The invention discloses an artificial breeding method of bombay canary. The eggs separation, indoor breeding way is used, and a ventilated, light penetrated chips breeding rack with transversal multi-gaps and vertical multi-layers is used; the temperature keeps at 28-30degree and the humidity keeps at the range of 65-75%; the illuminance keeps at the range of 10-15LUX, wherein the natural illumination is main and the lamplight illumination is subsidiary; the illumination time is 10-14hour. The bombay canary is fed using cooked food and killed in batch one month after the peak time of the adult copulation and eggs-laying and the temperature rises to 38-40degree during killing process and the killing time is about 30minute, therefore the bombay canarys die and are used as medicine after post processing. The artificial breeding method of bombay canary can artificially adjust and control all the index on the base of the natural growth rhythm of bombay canary, thus the medical component isincreased and the growth cycle is reduced and the artificial breeding method is suitable for large-scale industrialization breeding.
Owner:SICHUAN GOODDOCTOR PANXI PHARMA
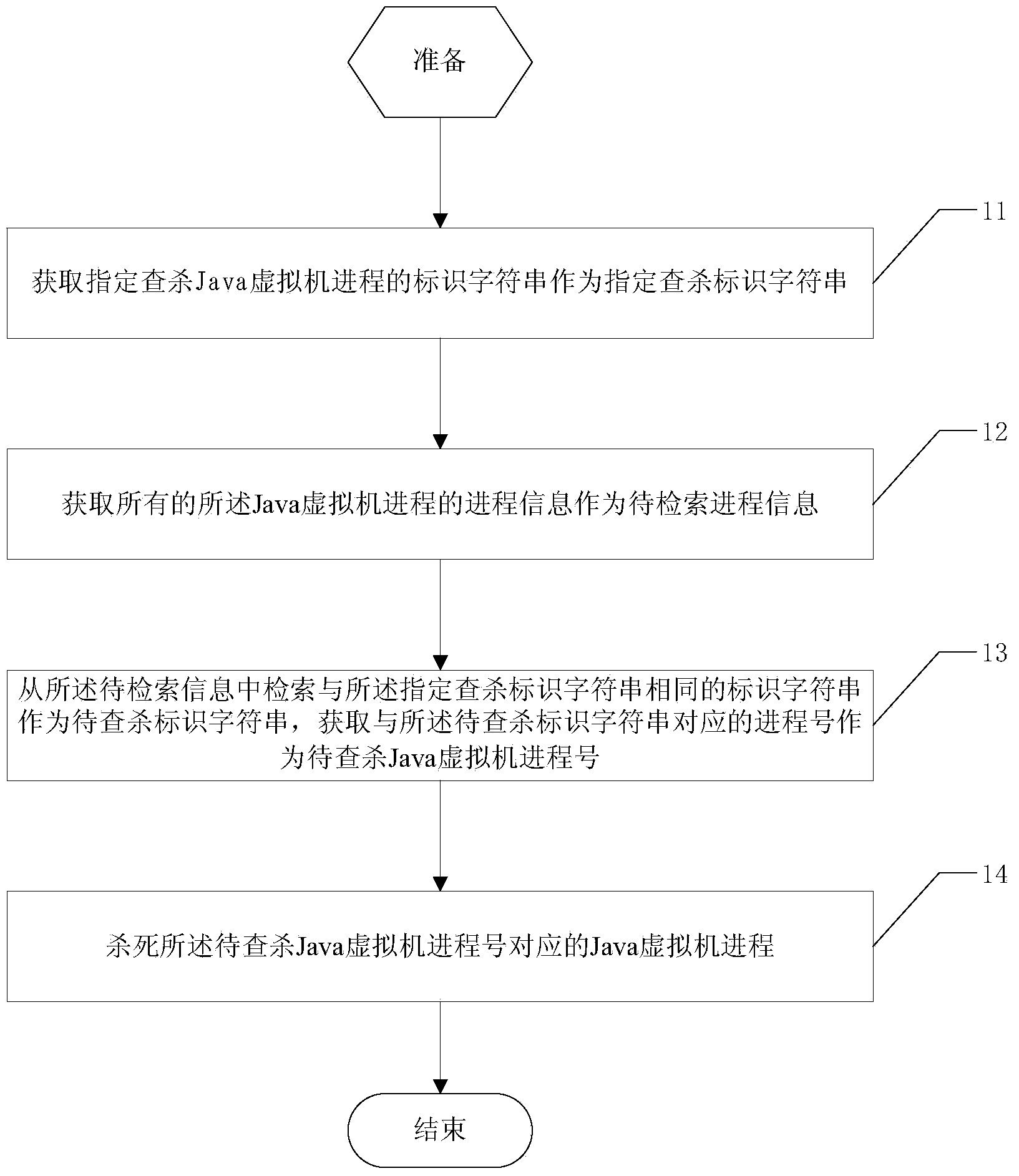
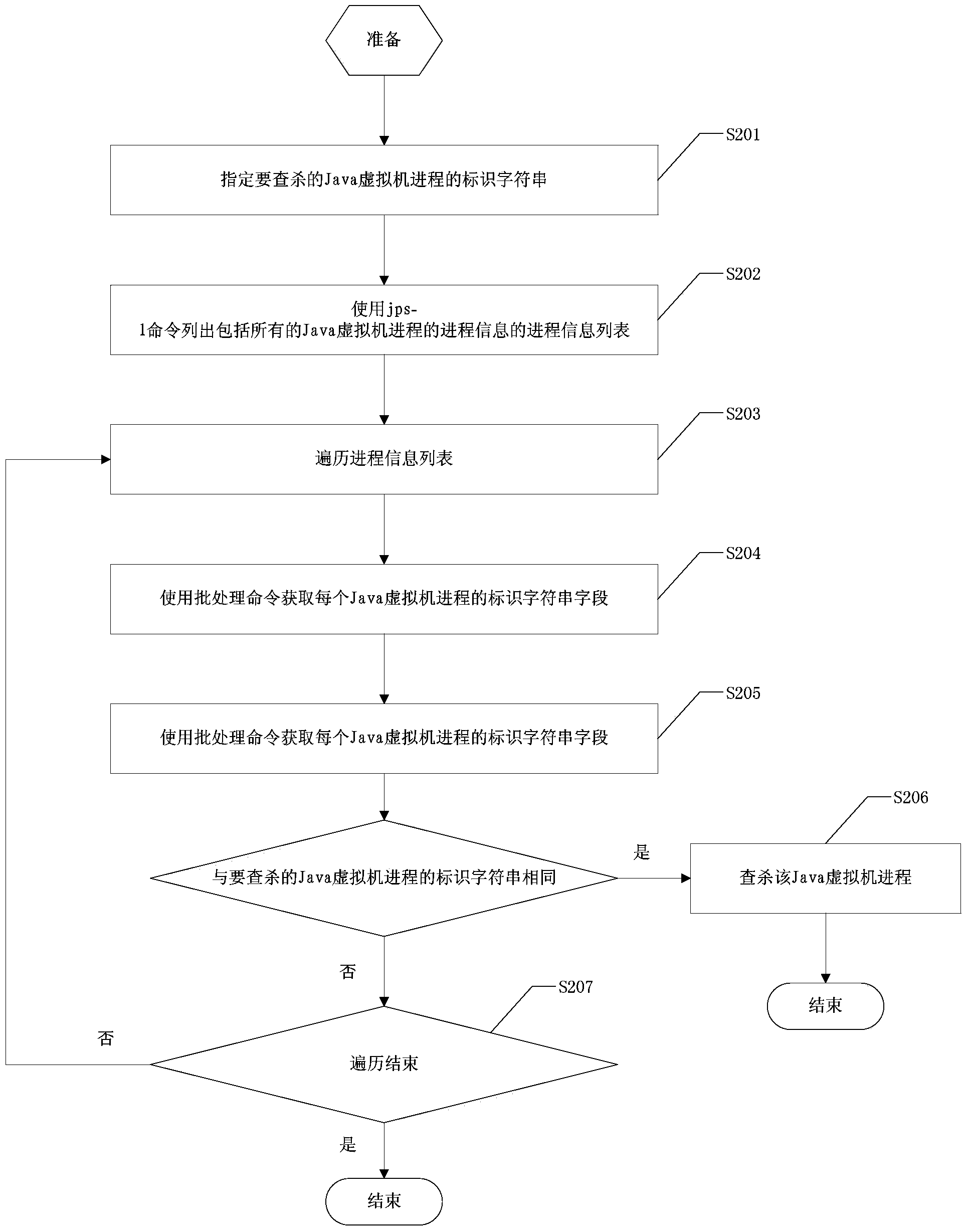
Management method and management system for Java virtual machine process in Windows system
ActiveCN103823710AEasy to automate managementEasy to integrateSoftware simulation/interpretation/emulationKilled processProcess information
The invention discloses a management method and a management system for a Java virtual machine process in a Windows system. The management method comprises the following steps of acquiring a designated identifier string for searching and killing the Java virtual machine process as a designated searching and killing identifier string; acquiring the process information of all the Java virtual machine processes as the process information to be retrieved, wherein the process information to be retrieved comprises a process number associated with the Java virtual machine process and the identifier string; retrieving the identifier string which is the same as the designated searching and killing identifier string from the information to be retrieved as the identifier string to be searched and killed, and acquiring the process number corresponding to the identifier string to be searched and killed as the process number of the Java virtual machine to be searched and killed; killing the Java virtual machine process corresponding to the process number of the Java virtual machine to be searched and killed. The whole searching and killing process of the invention is totally scripted, which is very beneficial to the application integration, and realize the intelligent control without any manual intervention.
Owner:BEIJING JINGDONG 360 DEGREE E COMMERCE CO LTD
Eel killer and auxiliary eel catcher
InactiveCN103907663ASimple structureEasy to usePoultry/fish slaughtering/stunningAquatic productEngineering
The invention relates to an eel killing tool and belongs to the field of processing tools for aquatic products. An eel killer is composed of a fixing position device and a disemboweling device. The fixing position device is composed of a frame, a handle, a reset spring, a pincer control key, a pull rod and pincer blades. The disemboweling device consists of a movable disemboweling cutter, a disemboweling cutter control key and a reset spring. The auxiliary eel catcher consists of metal nails and tongs. The eel killer solves the problems of high labor intensity, poor safety, low effectiveness and the like in the prior art of utilizing knives and plates to kill eels and the problem that recently invented automatic eel killing machines are high in production cost, heavy, non-portable, energy consuming and is inconvenient for households, medium- and small-size markets. The eel killer has the advantages of simple structure, low production cost, portability, simplicity in use, high killing efficiency and the like. The integral eel killing process can be completed by catching, clamping, pressing and pulling. The operation is time saving and labor saving, safe, sanitary and applicable to markets and households.
Owner:周建钊
RFID tag with user-controlled kill mechanism
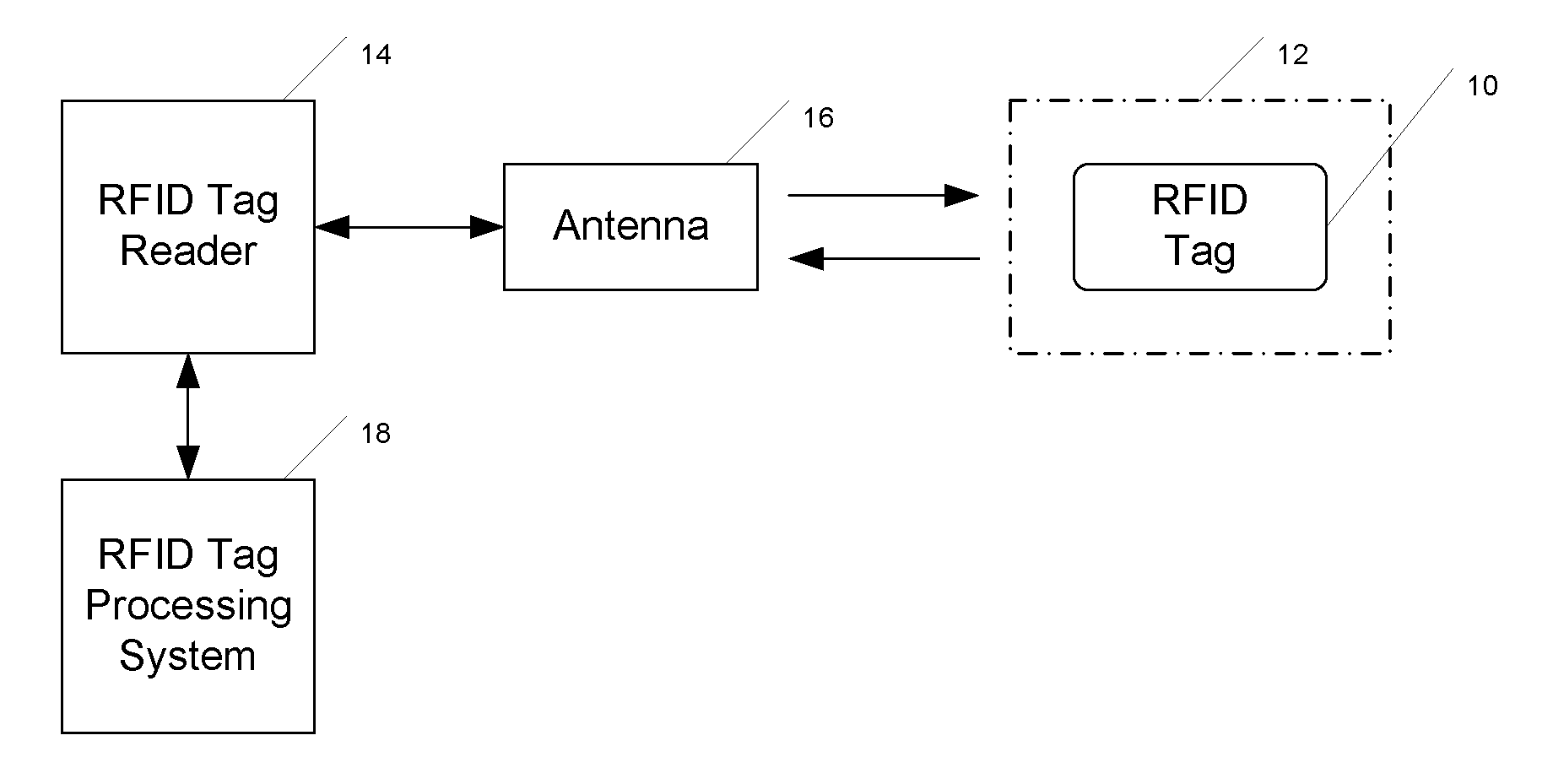
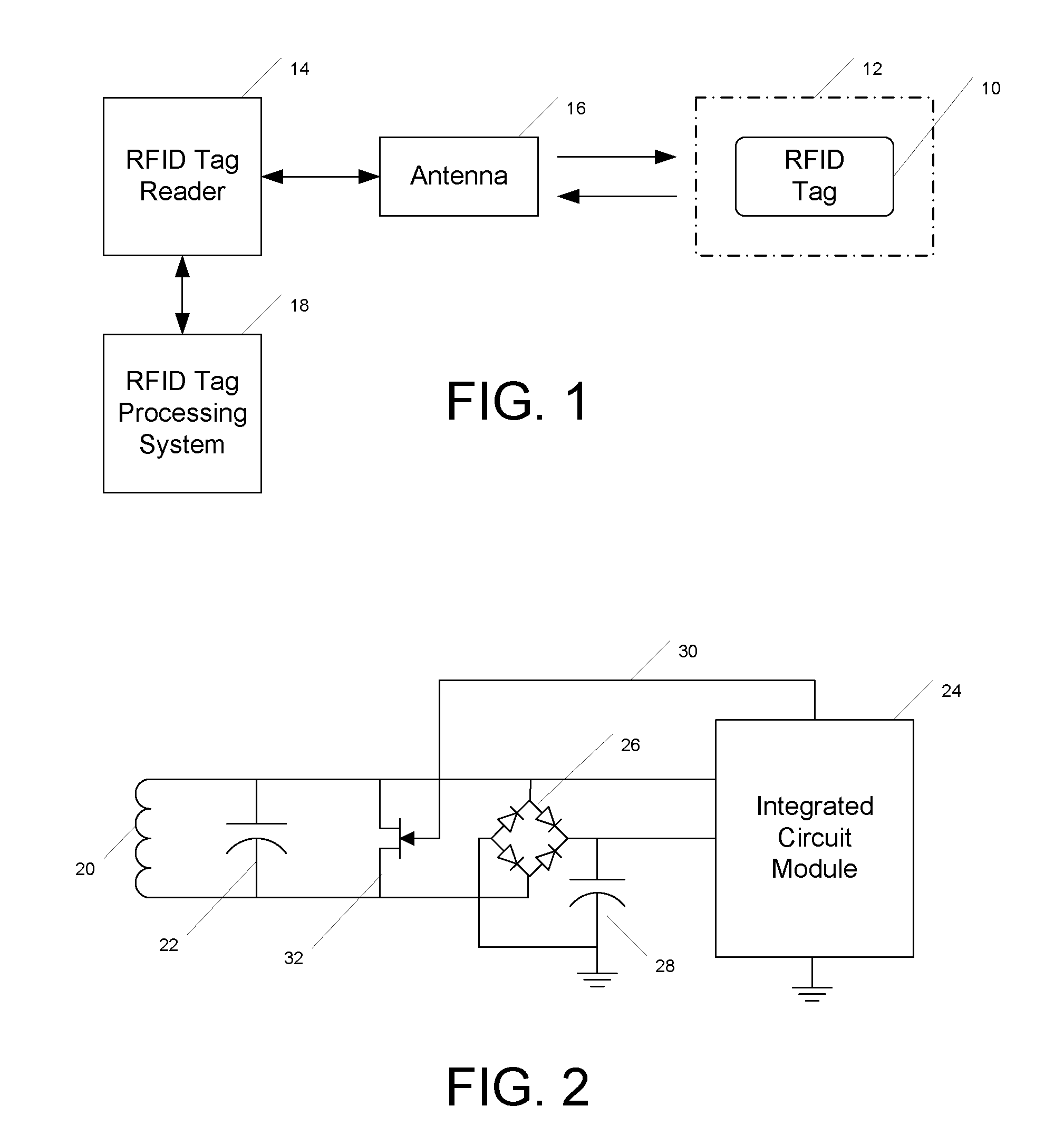
InactiveUS20090201130A1Memory record carrier reading problemsSubscribers indirect connectionTag antennaKilled process
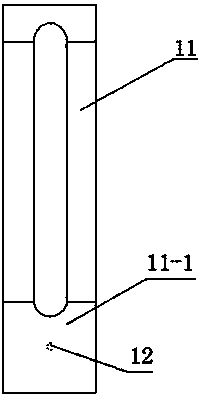
An inexpensive disabling or kill mechanism is provided for an RFID tag to allow a user to decide when to disable the tag and to initiate the kill process. RFID tag antenna circuitry is partially or wholly covered with an oxidation-retardant coating. The activation-retardant coating includes a grippable pull tab. When a user decides he or she no longer wants a functional RFID tag, the user can use the pull tab to remove the least a selectable area of the oxidation-retardant coating. Removing the selectable area will expose at least part of the antenna to begin an oxidizing process that will eventually disable the antenna. An oxidizing agent may be deposited on the antenna before the oxidation-retardant coating is put in place. When exposed to ambient environment, the oxidizing agent may accelerate the oxidation process that disables the antenna.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com