Operation system background process searching and killing method and system and storage device
An operating system and process technology, applied in the direction of multi-program device, program control design, resource allocation, etc., can solve problems such as misjudgment, list detail and accuracy limitations, background killing, etc., to achieve strong operational practicability, Intelligent software management, accurate and reliable data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
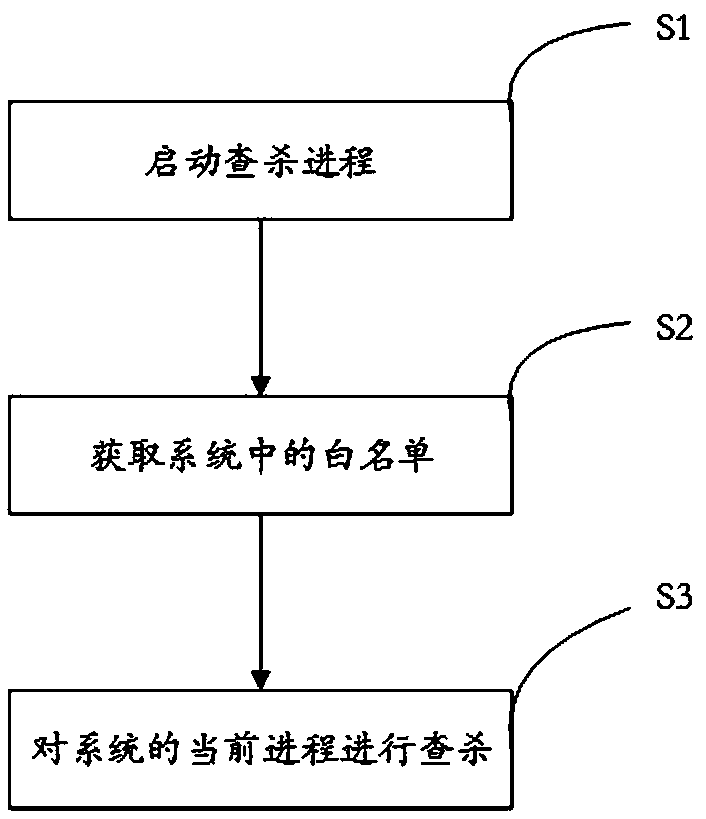
[0038] Such as figure 1 As shown, in Embodiment 1 of the present invention, a method for checking and killing an operating system background process is provided, which includes steps S1-S3. Each will be described below.
[0039] Step S1, start step: start the killing process;
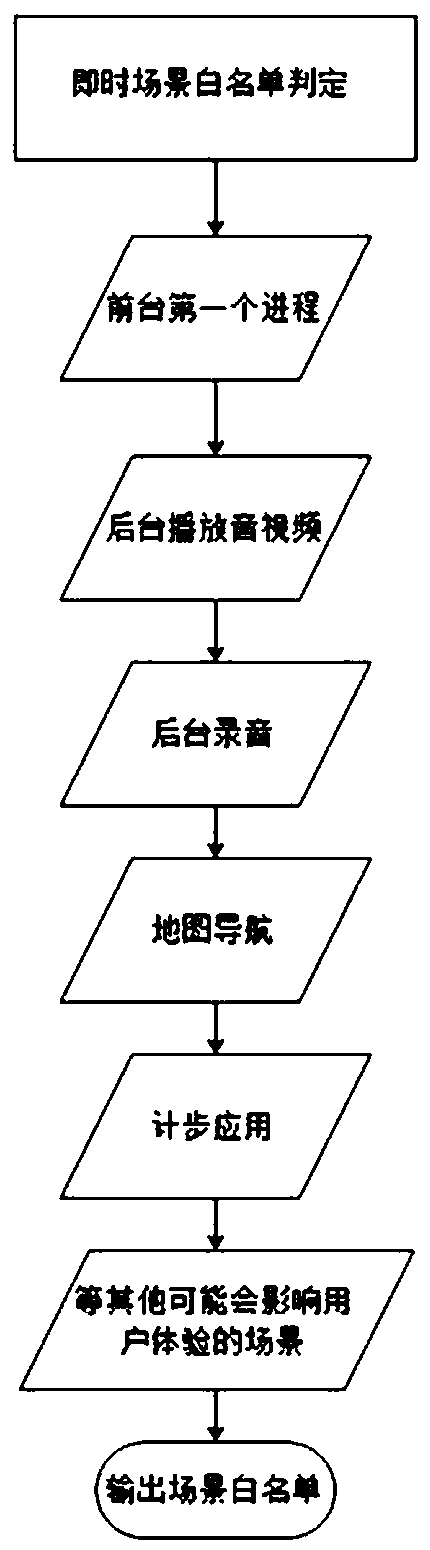
[0040] Step S2, obtaining step: obtaining a white list in the system, the white list includes a preset white list, an instant scene white list and a common application white list, wherein the preset white list is preset in the killing process , the instant scene whitelist is generated according to the application environment of the current system, and the frequently used application whitelist is generated according to the recent user's application usage habits;
[0041] Step S3, the step of checking and killing: checking and killing the current process of the system, keeping the process on the white list, and closing the process not on the white list.
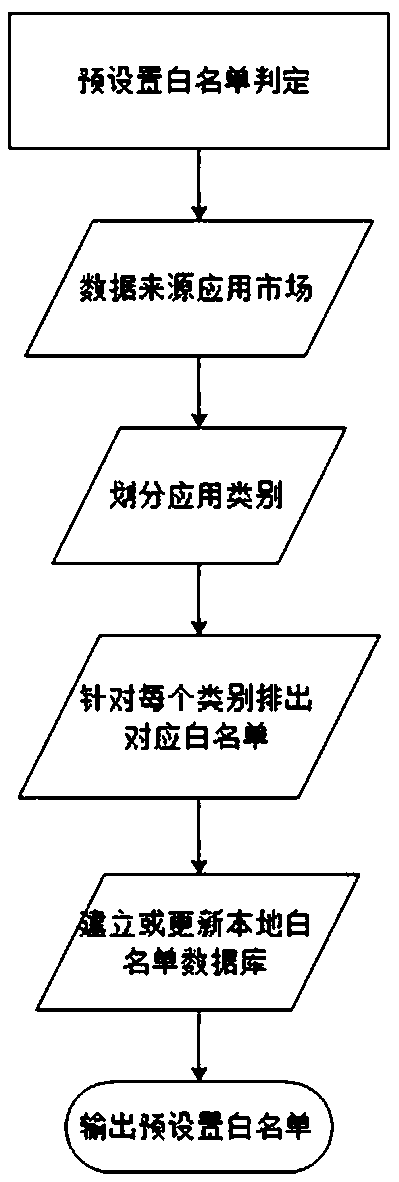
[0042] Such as figure 2 As shown, the preset ...
Embodiment 2
[0058] Such as Figure 5 As shown, in the present invention, a kind of operating system background process checking and killing system is provided, and it comprises:
[0059] A whitelist acquisition module, configured to acquire a whitelist in the system, the whitelist includes a preset whitelist, an instant scene whitelist and a commonly used application whitelist, wherein the preset whitelist is preset in the killing process Wherein, the instant scene whitelist is generated according to the application environment of the current system, and the frequently used application whitelist is generated according to the recent user's application usage habits;
[0060] The checking and killing module is used for checking and killing the current process of the system, keeping the processes on the white list, and closing the processes not on the white list.
[0061] It should be noted that the system for checking and killing the background process of the operating system in Embodiment ...
Embodiment 3
[0063] In this embodiment, a storage device is provided, on which a computer program is stored, and when the computer program is executed by a processor, the method for checking and killing an operating system background process described in Embodiment 1 is implemented.
[0064] Through the above description about the implementation mode, those skilled in the art can clearly understand that the present invention can be realized by means of software and necessary general-purpose hardware, and of course it can also be realized by hardware, but in many cases the former is a better implementation mode . Based on this understanding, the essence of the technical solution of the present invention or the part that contributes to the prior art can be embodied in the form of a software product, and the computer software product can be stored in a computer-readable storage medium, such as a floppy disk of a computer , Read-only memory (Read-Only Memory, ROM), random access memory (Random...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com