Computer virus recognition method and system based on cloud computing
A computer virus and identification method technology, applied in the field of computer security, can solve the problems of reducing user experience, consuming large traffic, occupying terminals, etc., and achieve the effect of reducing data processing pressure, reducing traffic consumption, and reducing adverse effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
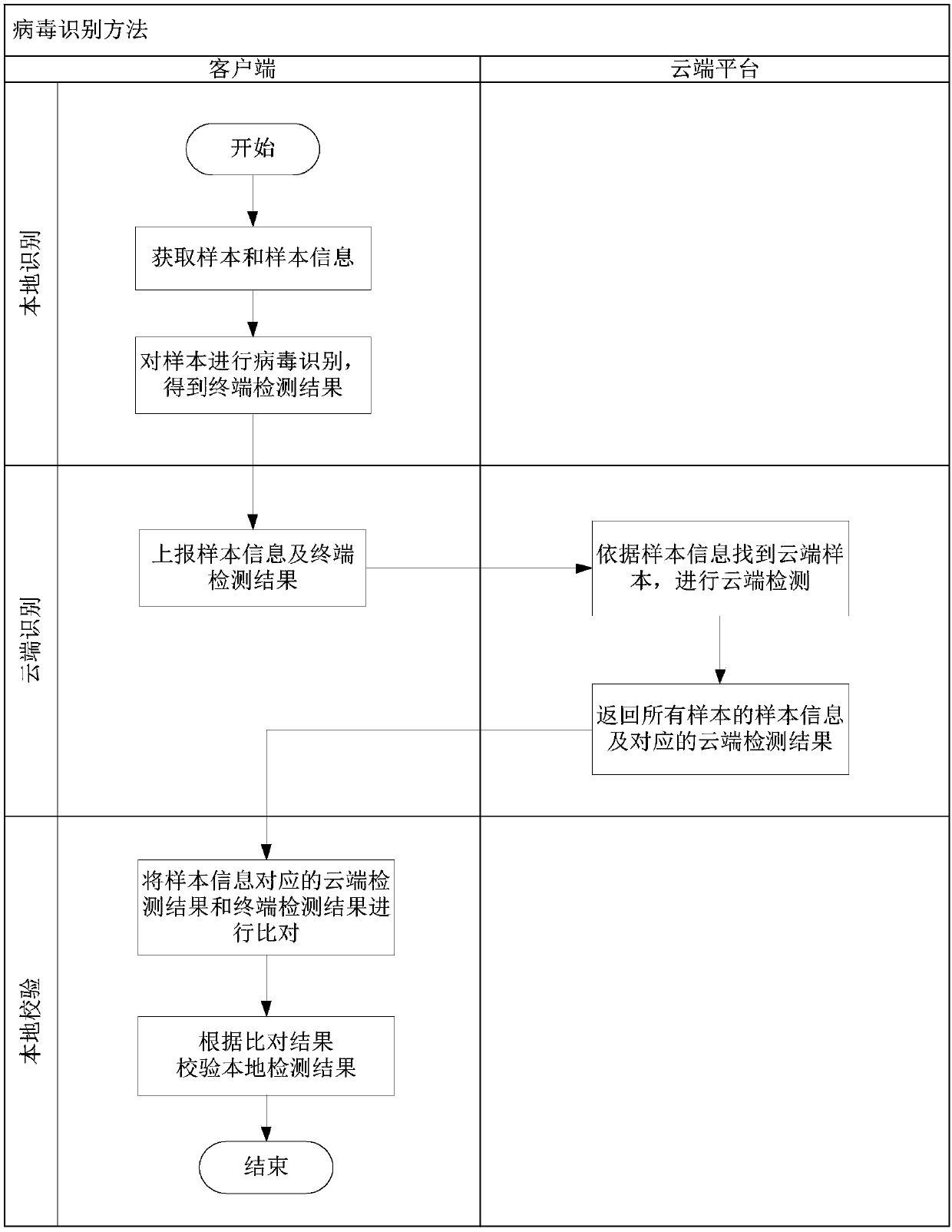
[0037] See image 3 and Figure 4 , image 3 and Figure 4 A flow chart of an embodiment of the computer virus identification method based on cloud computing according to the present invention is shown. Described computer virus identification method based on cloud computing, comprises the steps:
[0038] S301. The cloud server receives the detection information uploaded by the terminal. The detection information includes sample information, sample ID and terminal detection result. The terminal detection result represents the virus identification result of the terminal's virus identification on the sample.
[0039] In this embodiment, the virus identification method runs on the cloud server and the terminal, and the terminal sends a request for virus identification using the cloud server (that is, a cloud scanning and killing request) to the cloud server through a wired connection or a wireless connection. Before sending a request to the cloud server, use the virus scanning...
Embodiment 2
[0052] Please refer to Figure 5 , Figure 5 A flow chart of another embodiment of a computer virus identification method based on cloud computing is shown. This embodiment describes the virus identification method running on the terminal, including:
[0053] S501. Obtain a sample to be detected and corresponding sample information, perform virus identification on the sample, and obtain a virus identification result.
[0054] In this embodiment, the user installs the antivirus engine on the terminal device in advance, and the terminal uses the antivirus engine to obtain the installation package of the application to be detected that has been installed or is about to be installed on the terminal device, and uses the installation package as a sample to extract sample information , and use the killing engine to identify the virus, and obtain the virus identification result.
[0055] Among them, the sample information includes information such as the installation package name, ...
Embodiment 3
[0066] Please refer to Figure 6 , Figure 6 A flow chart of another embodiment of a computer virus identification method based on cloud computing is shown. This embodiment describes a virus identification method running on a cloud server, including:
[0067] S601. Receive the detection information uploaded by the terminal, the detection information includes sample information, sample ID and terminal detection result, the sample ID is used to identify the sample, and the terminal detection result indicates that the terminal performs virus identification on the sample result.
[0068] Specifically, the sample ID is the unique identifier assigned by the terminal to the sample corresponding to the sample information. The sample information includes information such as the installation package name, certificate, file size, and MD5 code of the file; the terminal virus identification results include risk name, risk type, risk Level, virus ID, detailed description of the virus and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com