File protection system and implement method thereof
A technology for protecting systems and files, applied in the field of data security, can solve problems such as systemic file security reduction, and achieve the effect of simple system and good system compatibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
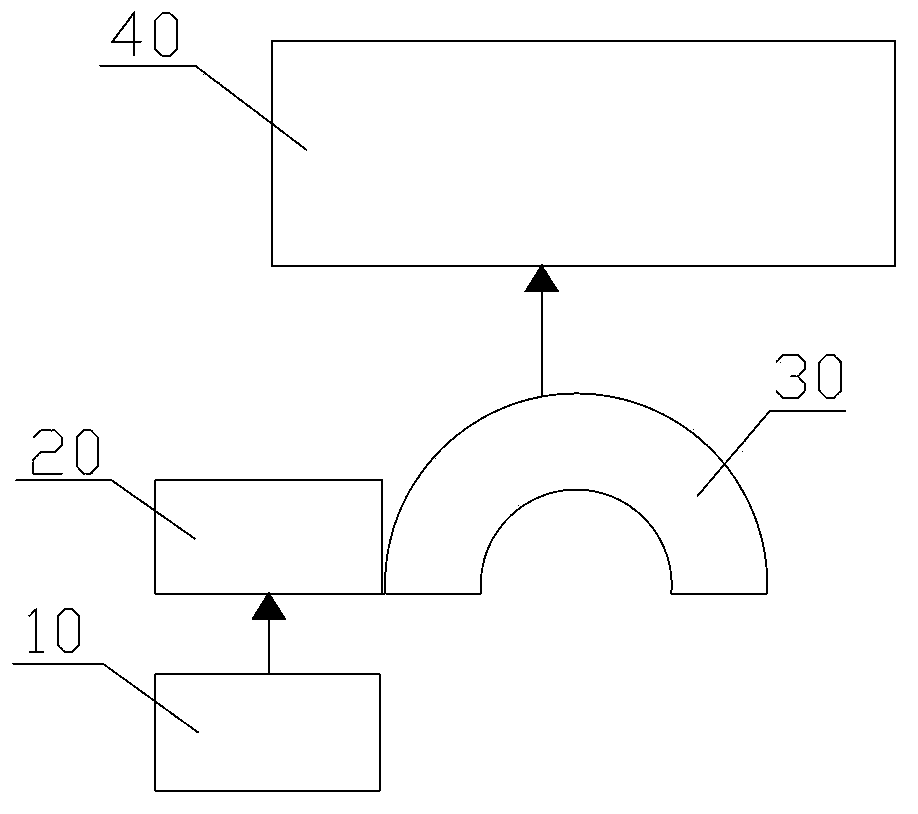
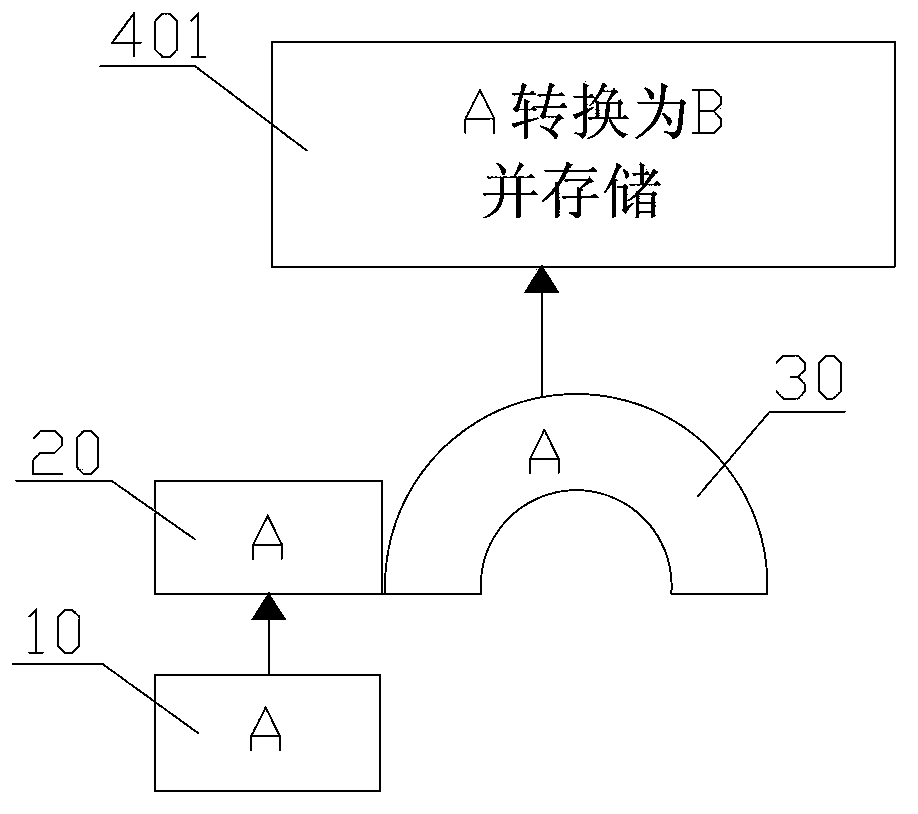
[0069] figure 1 , image 3 , Figure 4 , Figure 7 Shown is the first embodiment of the file protection system and its method of the present invention, its structure is as follows figure 1 Shown include:
[0070] The upper-level user interface application program 10 is used to implement encryption policy setting and other computer interactions, that is, to receive input operation instructions and send messages to the I / O manager 20;
[0071] The I / O manager 20 is configured to receive a request message from the upper layer user interface application program 10, and distribute the data in the form of a request packet;
[0072] The file filtering driver 30 is used to intercept the request packet from the I / O manager 20, and judge the data therein, then forward the data to be processed that meets the conditions, and release if the data does not meet the conditions;
[0073] The independent encryption hardware 40 integrates encryption / decryption algorithms and keys inside, an...
Embodiment 2
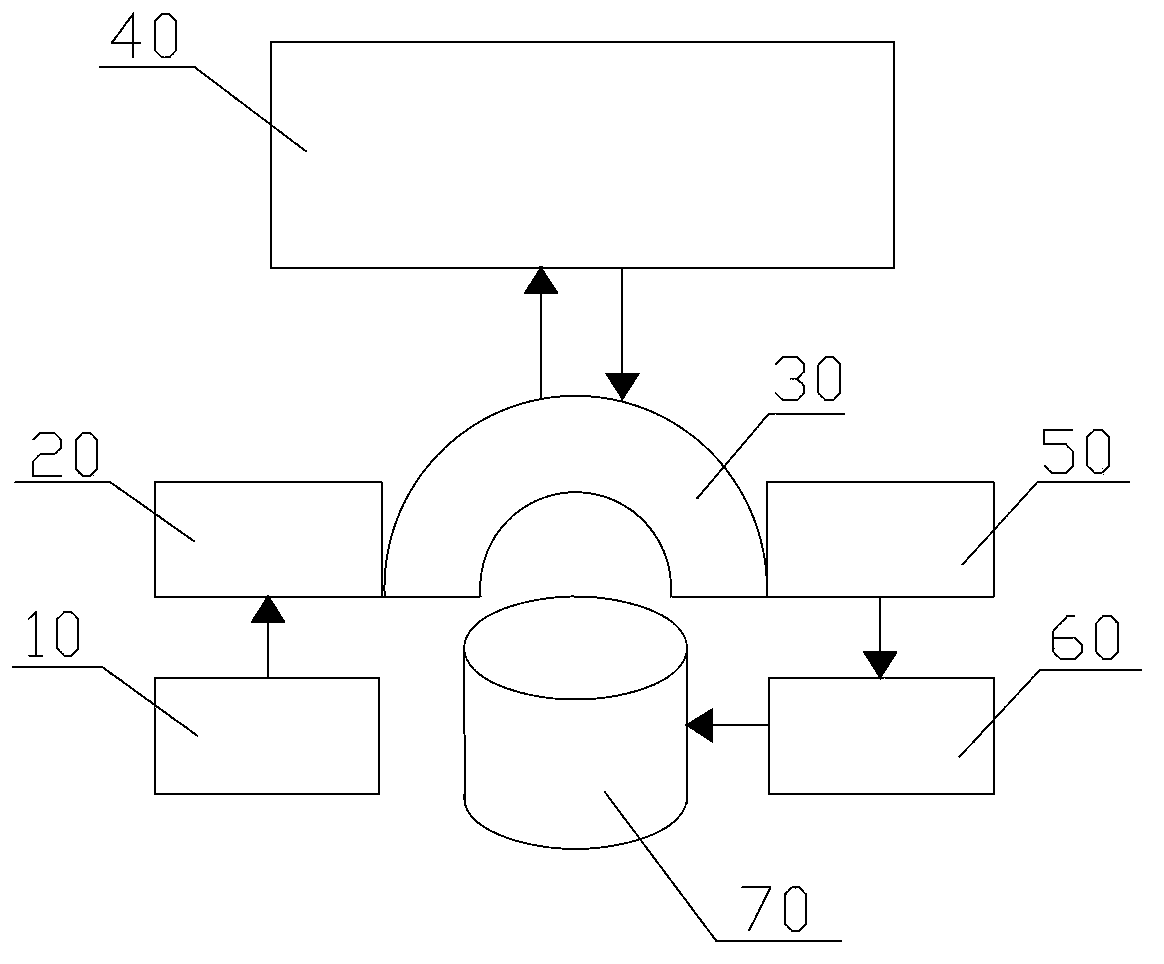
[0104] figure 2 , Figure 5 , Figure 6 and Figure 8 It is the second embodiment of the file protection system and method of the present invention, and its structural difference from the first embodiment lies in:
[0105] The independent encryption hardware 40 also has the function of sending the processed data to the file filter driver 30, and the file filter driver 30 forwards the processed data to the corresponding storage device for storage.
[0106] When the independent encryption hardware 40 sends the processed data to the file filter driver 30, the file filter driver 30 forwards it to the corresponding storage device for storage. In this technical solution, the system may also include:
[0107] The file driver 50 is used to receive and process the data from the file filter driver 30 and forward it;
[0108] The storage device driver 60 is used to receive the data from the file driver 50 and forward it;
[0109] The physical storage device 70 is configured to rece...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com