System and method for protecting virtual disk files
A technology of virtual disk and virtual disk, which is applied in the field of network security, can solve the problem of lack of effective protection of files, and achieve the effect of controllability and data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0021] Embodiment 1, see Figure 4 As shown, the system of this embodiment includes: a process policy management module, a file filter driver module and a virtual disk driver module.
[0022] Wherein, the process policy management module is used to configure the process management policy;
[0023] Wherein, the file filtering driver module is used to filter various operation events of the original image file of the virtual disk and the virtual disk file after the image according to the configured process management strategy;
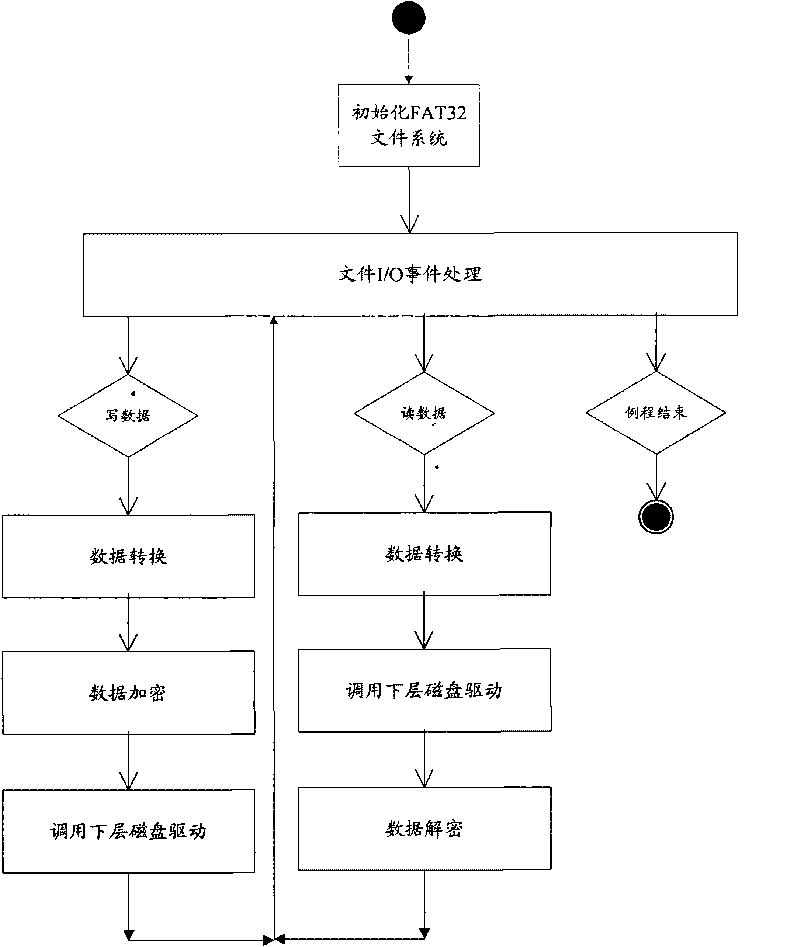
[0024] Wherein, the virtual disk driver module is used for converting the file system to the file pointed to by the filtered operation event.
Embodiment 2
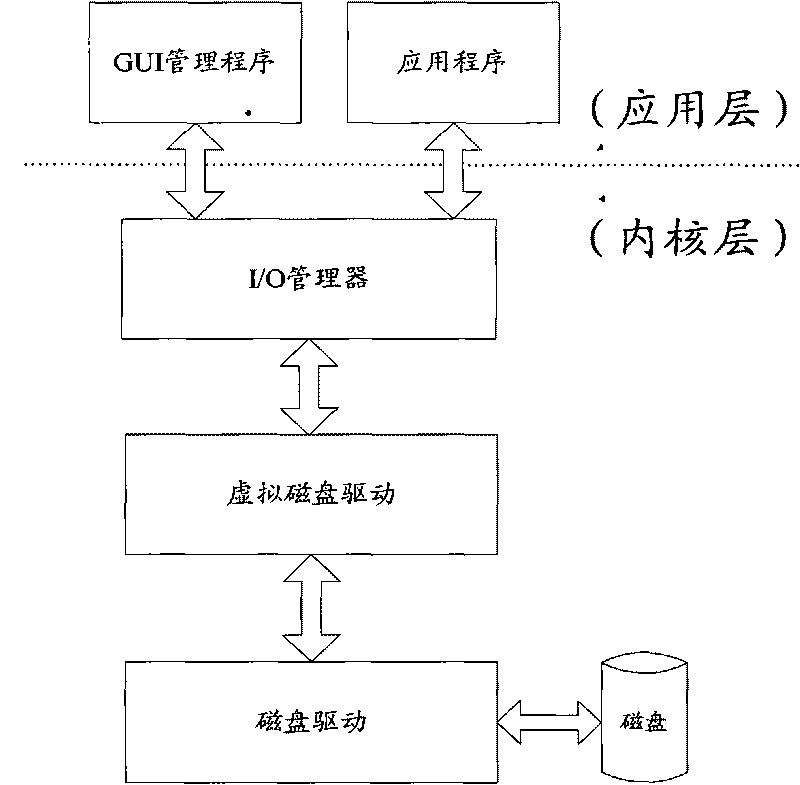
[0025] Embodiment 2. In specific implementation, the above-mentioned process policy management module, file filter driver module and virtual disk driver module can be replaced by application layer management program, file filter driver program and virtual disk driver respectively. The system of this embodiment adds the process policy management part of the application layer and the file filter driver of the kernel layer on the basis of the existing system. see Figure 5 As shown, the specific system structure is mainly composed of three parts: application layer management program, file filter driver and virtual disk driver.
[0026] The GUI management program at the application layer interacts with users and is responsible for managing virtual disks, including creation and deletion of virtual disk instances, authentication of virtual disk usage, virtual disk images, and management of login accounts and permissions. And the process management strategy can be configured by the ...
Embodiment 3
[0030] Embodiment 3. Based on Embodiment 2, this embodiment describes the working principle of the system of the present invention in detail.
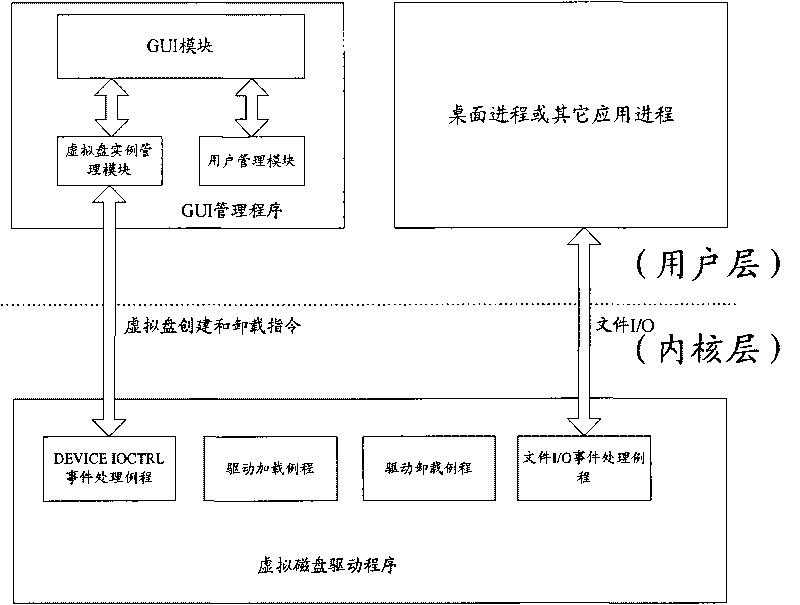
[0031] see Image 6 As shown, the GUI management program is composed of a GUI module, a virtual disk instance management module, a user management module and a newly added process policy management module. Among them, the GUI module is responsible for interacting with users in the form of window interface, including login interface, virtual disk instance management interface, user management interface, etc.; user management module is responsible for the configuration, loading and saving of users and their permissions; virtual disk instance management The module is responsible for the management of virtual disk instances, including functions such as adding, deleting, loading and unloading virtual disk instances. The loading and unloading of virtual disk instances sends relevant subcommands to the kernel layer virtual disk driver through...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com