File security active protection method based on double-drive linkage
An active protection and security protection technology, applied in computer security devices, digital data protection, instruments, etc., can solve problems such as poor selection of security protection opportunities, insufficient file protection strategies, and insufficient thorough file operation monitoring, etc., to achieve the resolution of malicious files. Operational and Effects of Cyber Attack Campaigns
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
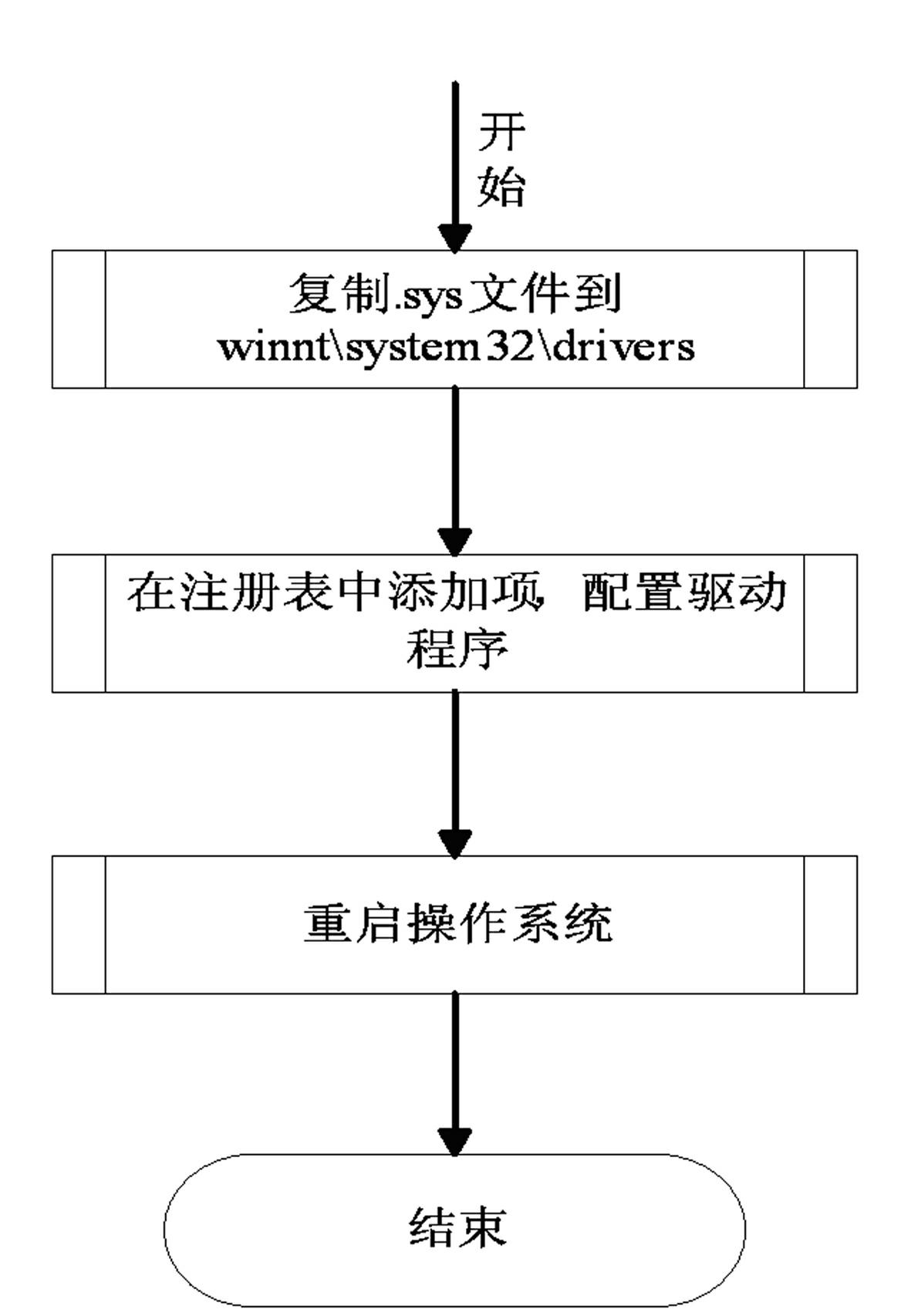
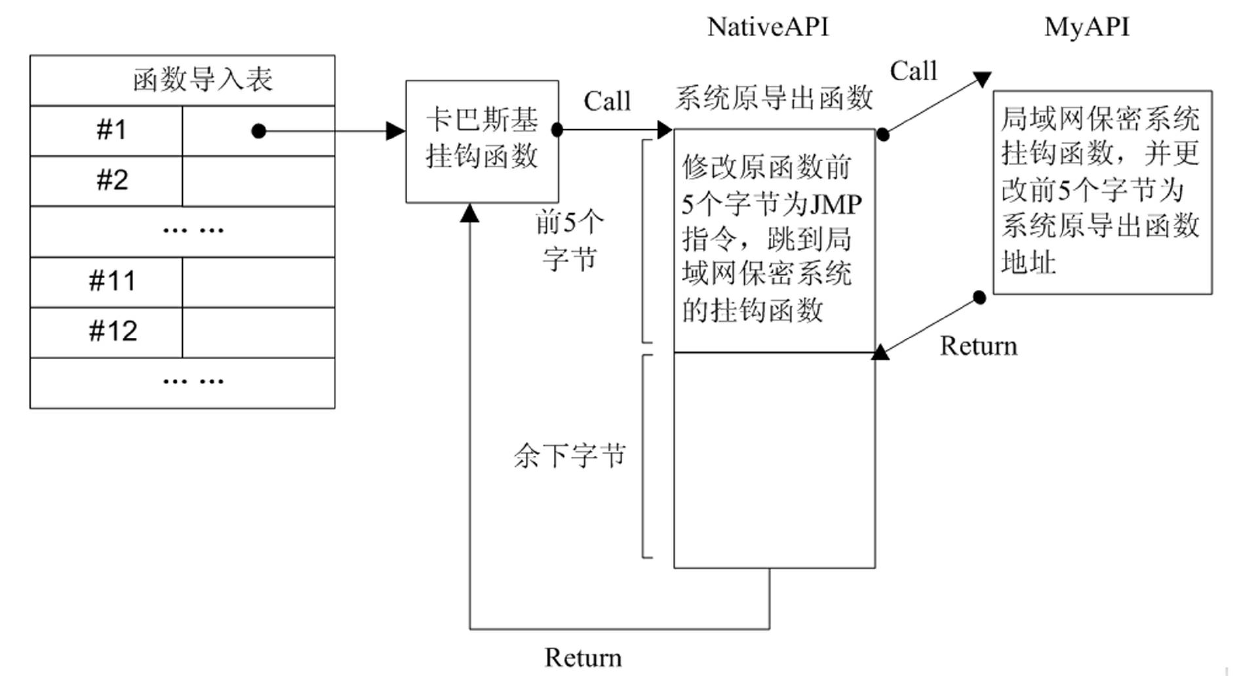
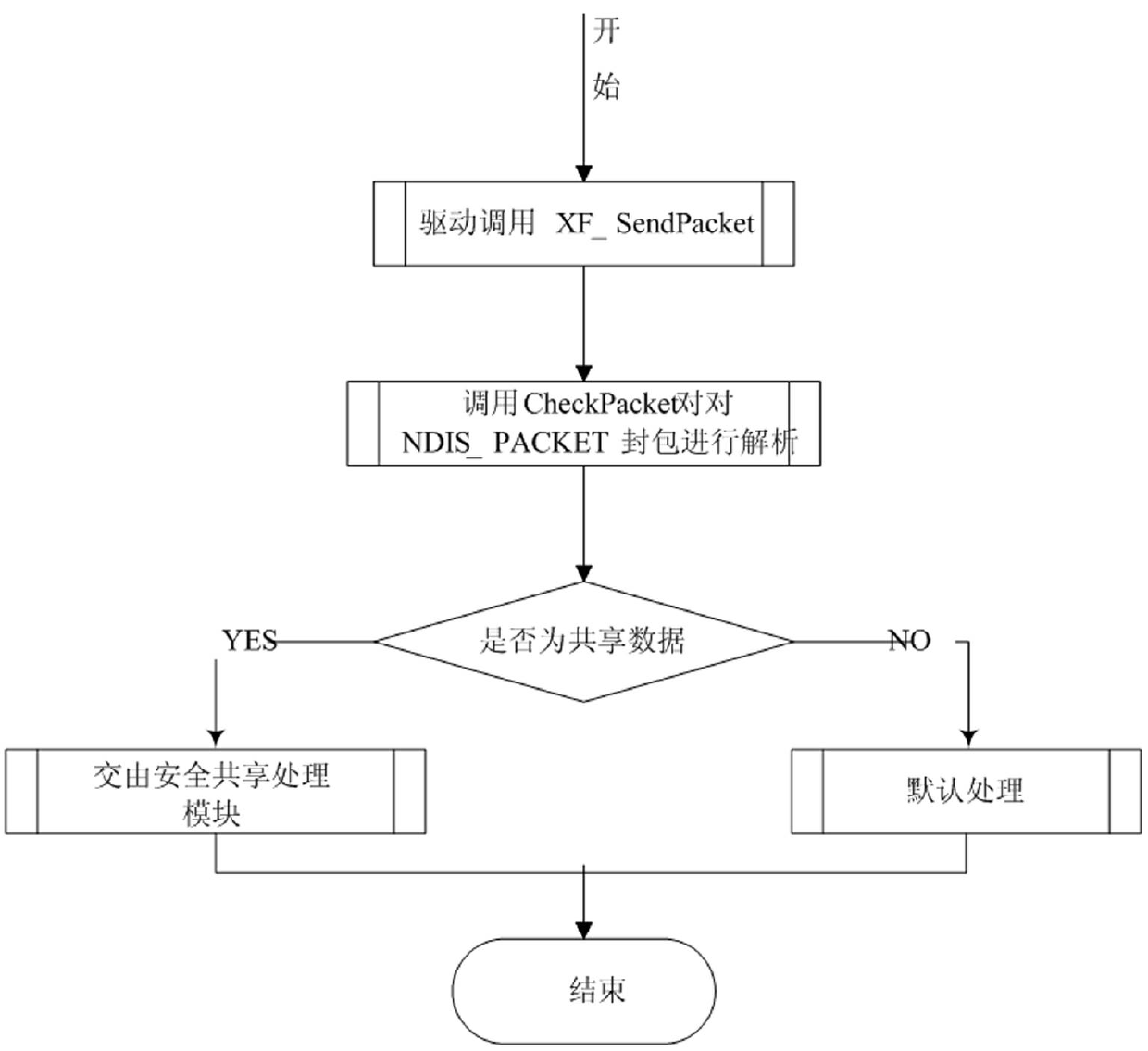
[0043] Example: such as figure 1 As shown in -6, the specific steps of the file security active protection method based on dual-drive linkage are as follows:
[0044] a) Use the INF file to install the driver to the target operating system, the driver exists as a service, and is set to start with the operating system;
[0045] b) Load the driver through the service management item of the operating system;
[0046] c) Read the preset file security protection rules into the rule chain;
[0047] d) Assign the IRP processing routine function entry to the corresponding dispatch routine array of DriverObject (driver object);
[0048] e) Fill in the Fast I / O processing routine, Fast I / O is a request without IRP caused by the cache manager call; the file filter driver writes for the DriverObject (driver object) in addition to the normal dispatch routine Another set of Fast I / O functions to monitor the cache;
[0049] f) Create a system thread, after obtaining the TCP / IP device obj...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com