Semantic searchable encryption method for proxy re-encryption resistant to post quantum attack
A proxy re-encryption and encryption method technology, applied in the field of proxy re-encryption semantic searchable encryption against post-quantum attacks, can solve the problems of limited search authority, inability to resist quantum attacks, low query efficiency, etc., and achieve enhanced flexibility Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] The technical solution of the present invention will be specifically described below in conjunction with the accompanying drawings.
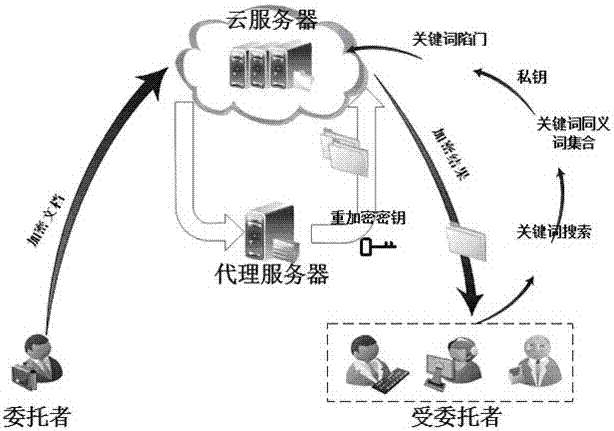
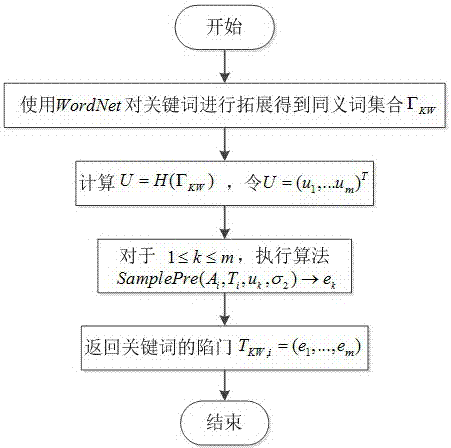
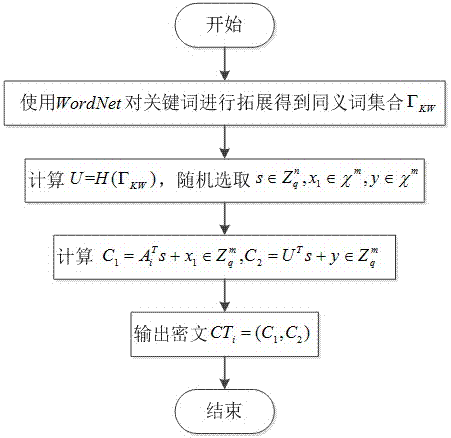
[0053] Such as Figure 1-3 As shown, a proxy re-encryption semantically searchable encryption method for anti-post-quantum attack of the present invention includes four entities: cloud server, proxy server, delegator and trustee, and the specific implementation of the method is as follows,
[0054] S1. New user registration: When a new user joins the system, the trusted third-party TTP will verify the user's identity; if the identity is false, TTP will reject the request; otherwise, TTP will run the following key generation algorithm to generate the public key and private key pair;
[0055] KeyGen(κ)→(pk,sk): With the security parameter κ as input, execute the TrapGen algorithm to generate a random matrix He case The basis T ∈ Z m×m , the lattice set T satisfies The secret key generation algorithm outputs the user's public key pk=...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com