Systems and methods of blockchain platform for intermediaries and passwordless login
a blockchain and intermediary technology, applied in the field of cloud computing, can solve the problems of system susceptible to single point failure, permanent loss of data, and no mechanism known in the industry that allows flexible user control to proxy reencryption,
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
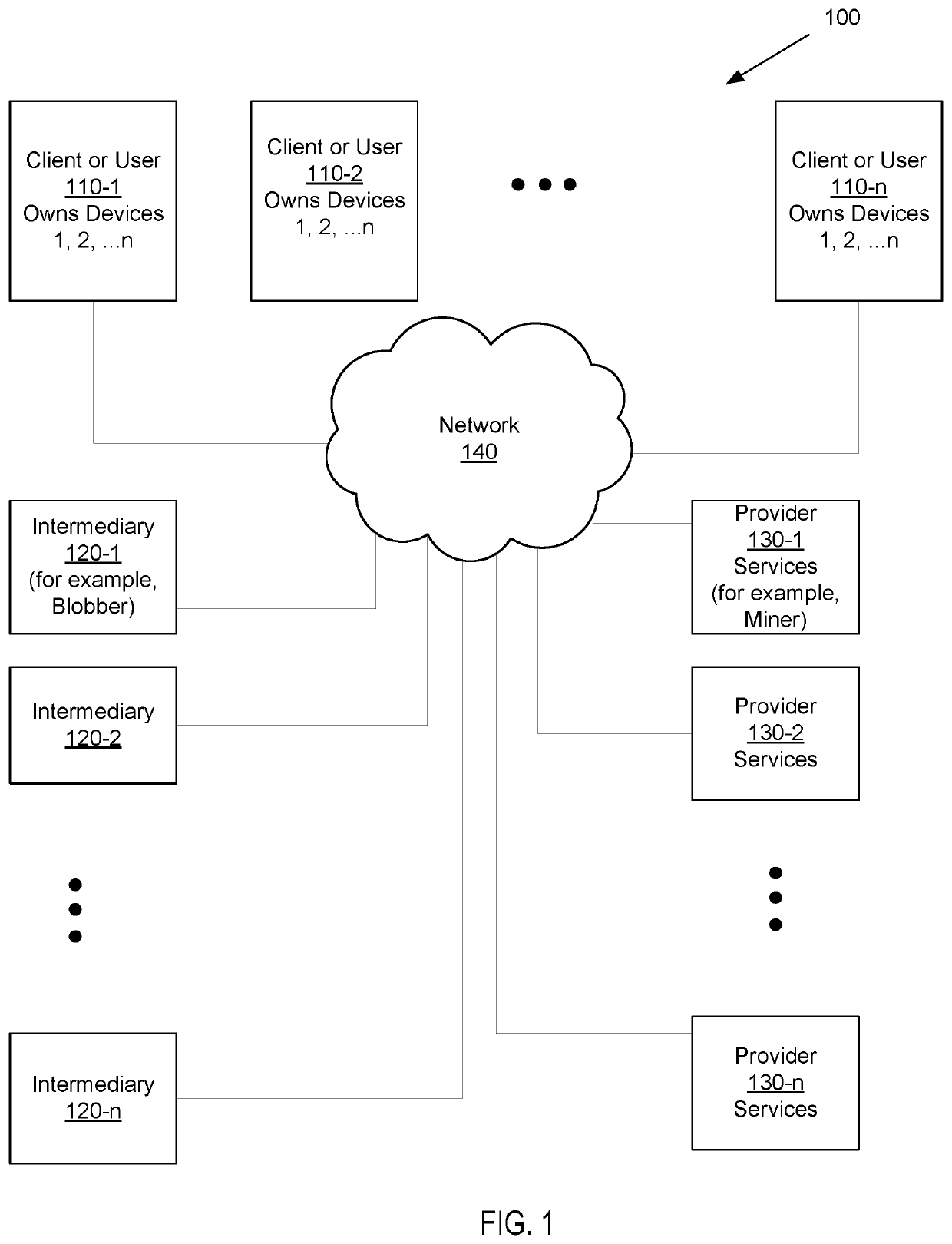
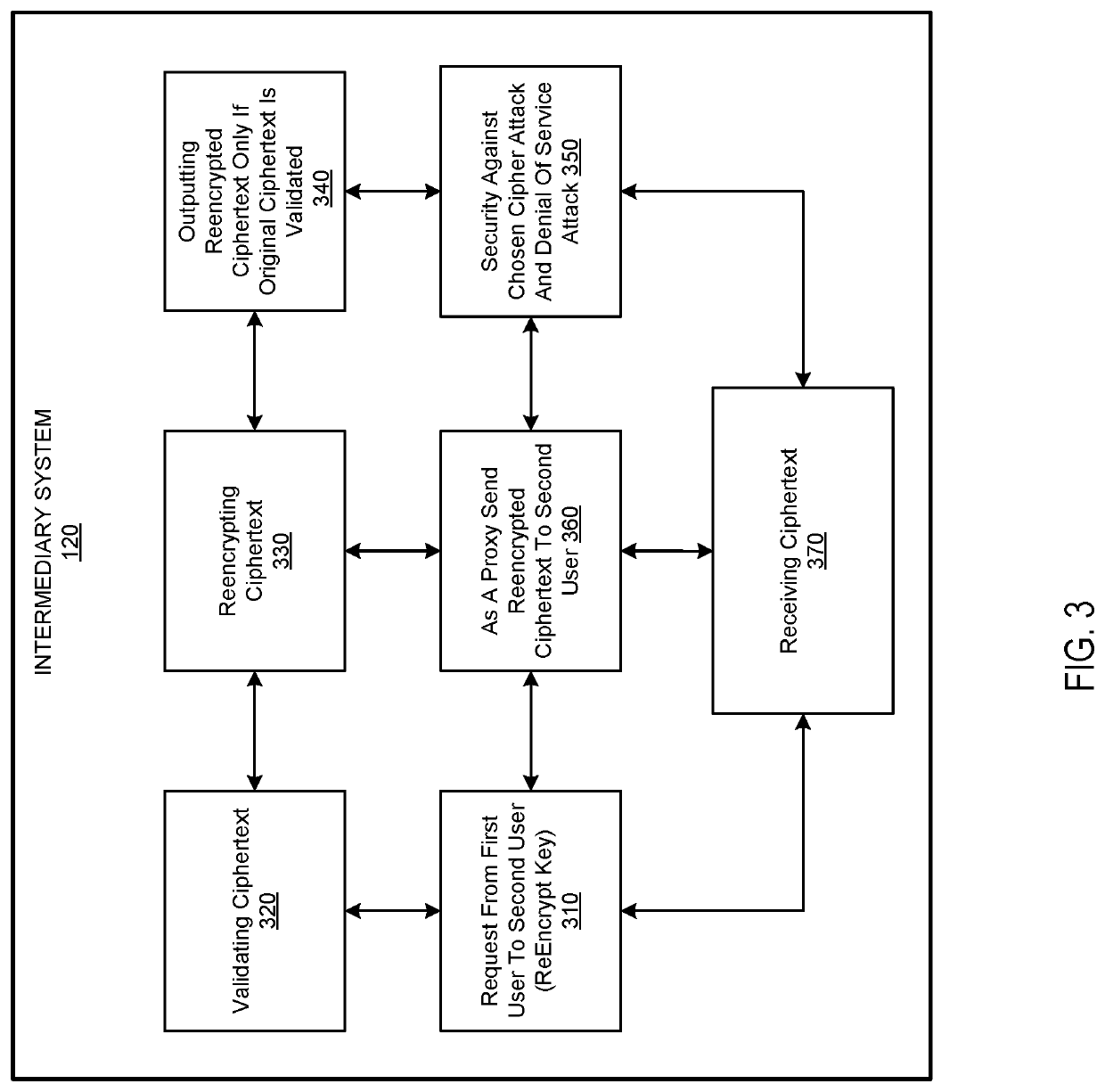
[0033]The systems and methods on a blockchain platform for intermediaries and passwordless login allow for intermediary proxy re-encryption, independent audits, secure multiple persons controlled smart contract or smart wallet, and split-keys short-range wireless device-based and passwordless client authentication. One or more entities (or service providers) that help or manage the self-regulation on the blockchain platform are miners. A client is an end-user with two or more computing devices who initiates the requests and wants to commit transactions on the blockchain platform. An intermediary may be a blobber or a sharder who uses a computing device that processes the applications on the blockchain platform.
[0034]Different embodiments described herein include components or structures to perform the described functionality. A “component” or a “module” as used in this invention disclosure, includes a dedicated or shared processor and, typically, firmware or software modules execute...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com