Multiple users-based outsourcing database audit method
A multi-user and database technology, applied in the field of data processing, can solve problems such as increased user burden and low verification efficiency, and achieve the effect of reducing burden, reducing calculation cost and communication overhead, and reducing one interaction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
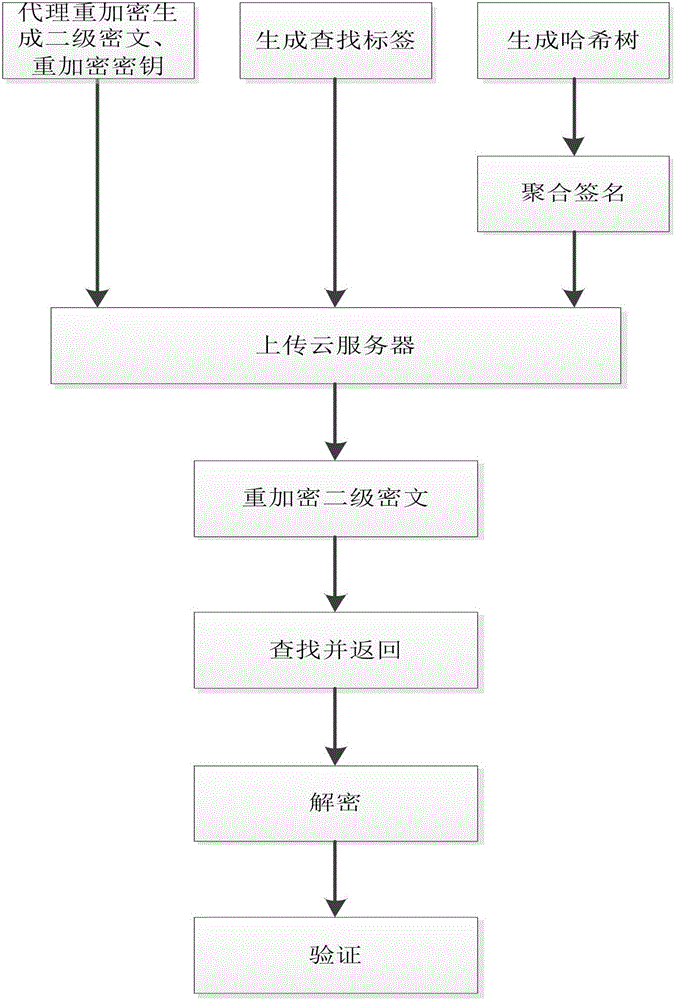
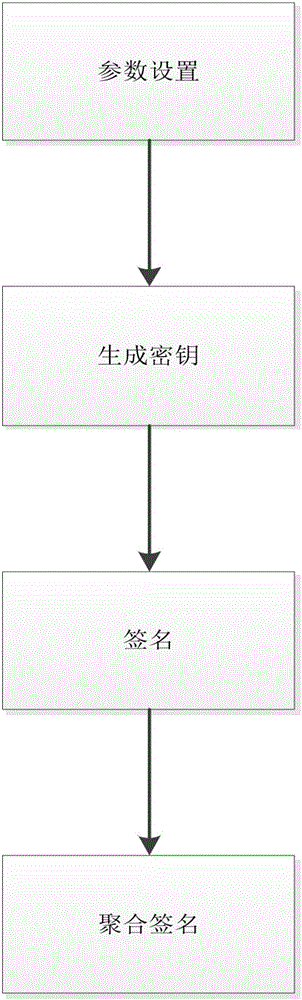
[0027] refer to figure 1 , the implementation steps of the present invention are as follows:
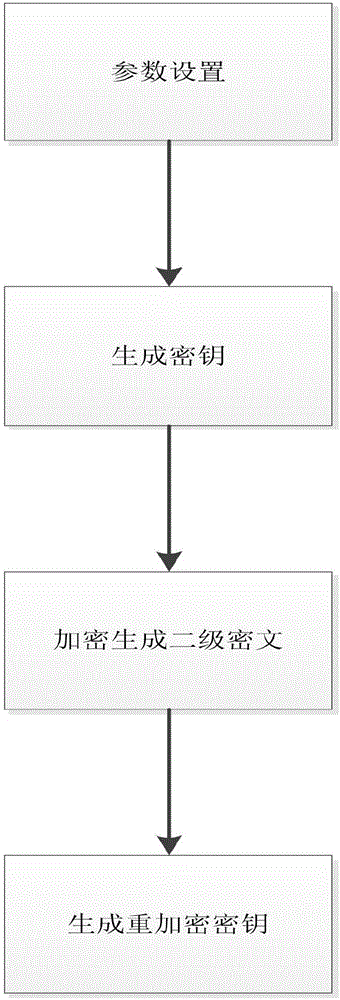
[0028] Step 1. The data owner encrypts the data by proxy re-encryption to form a secondary ciphertext C 1 , and generate the re-encryption key sk′ according to the public key of the querying user.
[0029] Proxy re-encryption is a cryptographic concept proposed by cryptographers Blaz, Bleumer and Strauss in 1998. According to the nature of the proxy key, proxy re-encryption can be divided into two-way proxy re-encryption and one-way proxy re-encryption. According to the nature of whether the proxy ciphertext can be converted multiple times, proxy re-encryption is divided into two types: multi-hop proxy re-encryption and single-hop proxy re-encryption. What the present invention adopts is the single-hop one-way proxy re-encryption scheme that Ateniese et al. utilize bilinear construction.
[0030] refer to figure 2 , the specific implementation of this step is as follows:
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com