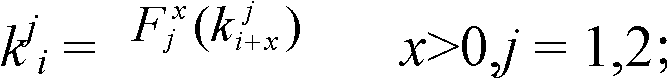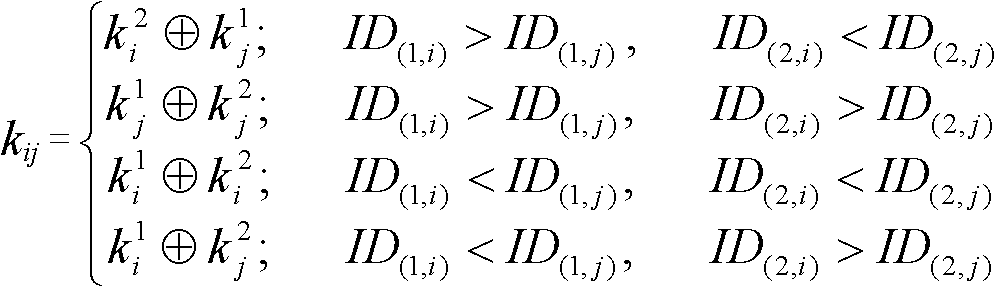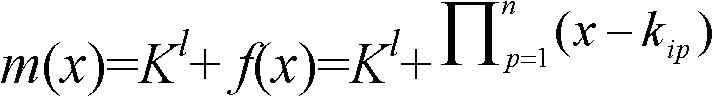Wireless sensor network key distribution and management protocol based on multiple hash chains
A wireless sensor and network key technology, which is applied in the field of wireless sensor network key distribution and management protocols based on multi-hash chains, can solve the problems of low ability to resist capture attacks, high update communication overhead, and reduce storage overhead.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The calculation of the hash function is simple and the one-way key chain is very secure. In order to meet the requirements of sensor node resource constraints, in recent years, the one-way key chain generated by the hash function has become a main method for distributing node keys in wireless sensor networks. ways and means. However, the finiteness of hash chain elements will inevitably lead to the problem of key reuse in multiple links in the network. Therefore, once a node is compromised, the security of all links using the same key in the network will be greatly reduced. In order to eliminate the problem of using the same key in different links in the network, this paper conducts a In addition, the present invention establishes the source of the node key on multiple key chains, and then calculates the keys from the multiple key chains according to a predetermined algorithm to finally determine the node pair key. Theory proves that under this method, the probability ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com