Homomorphic encryption matrix determinant security outsourcing method based on cloud computing
A technology of homomorphic encryption and secure outsourcing, applied in the field of matrix operations, can solve problems such as low efficiency in solving determinants, and achieve the effects of reducing space complexity, improving efficiency, and protecting security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
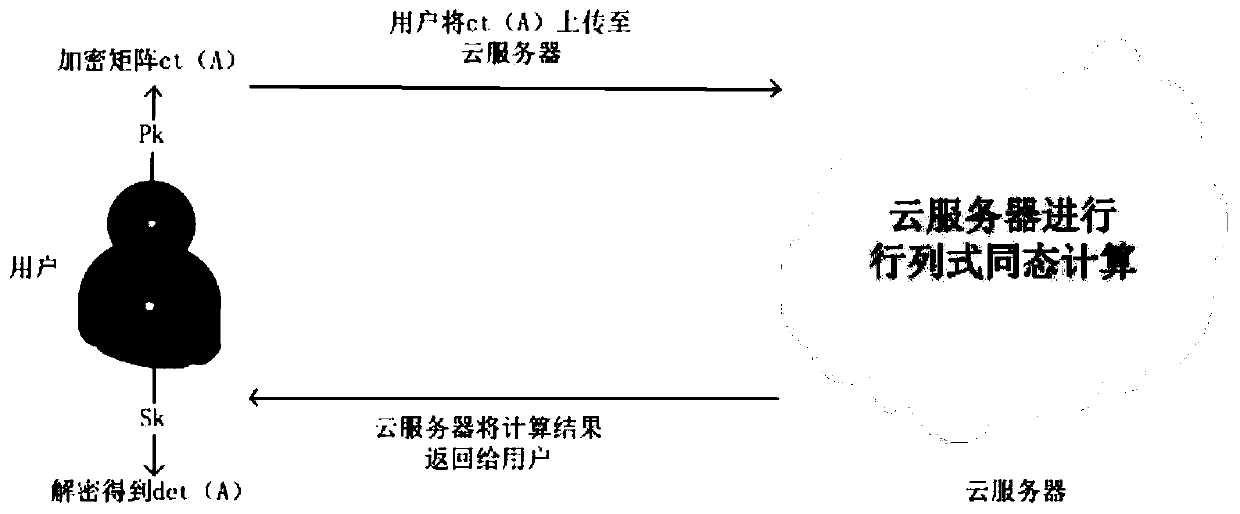
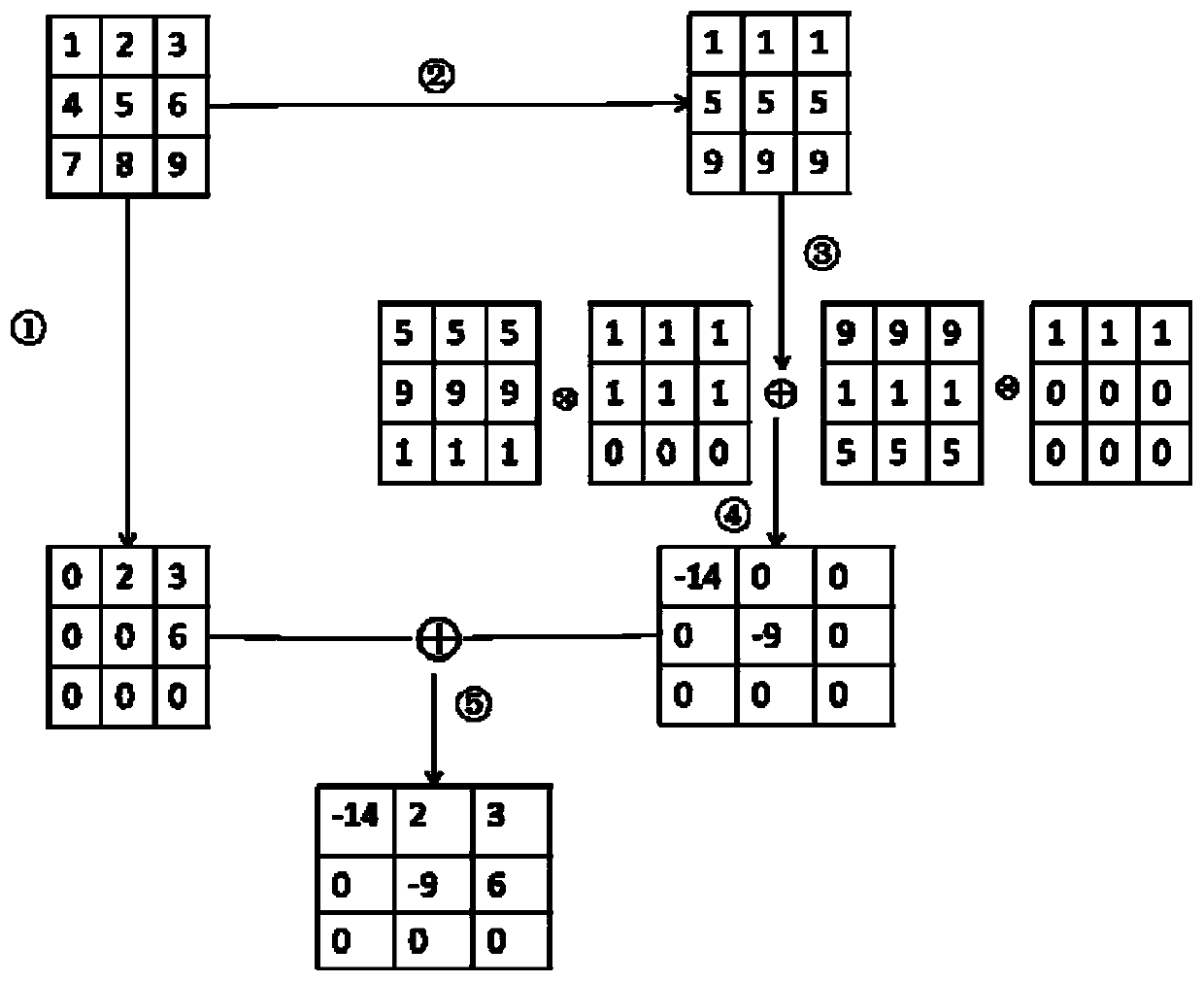
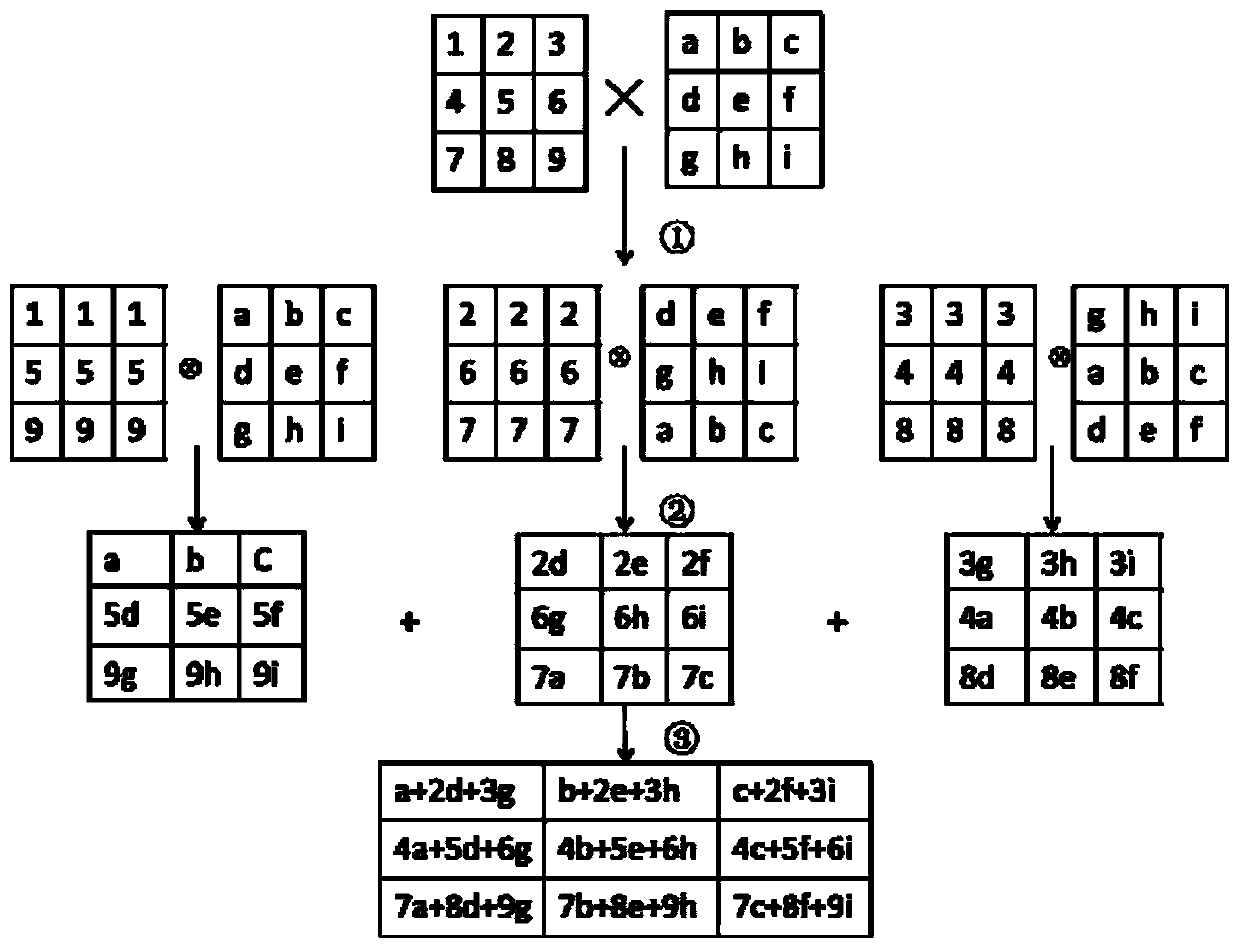
[0049] figure 2 , 3 A schematic diagram of the process of calculating μ(A) and matrix multiplication on the cloud server side (taking the third order as an example), the specific process is as follows:
[0050](Step 1) With the increasing popularity of cloud computing, people outsource a large number of computing tasks to cloud service providers. The client collects industrial data, such as medical data, traffic flow data, customer sales data, financial data and other data that need to be kept confidential; forms the collected data into a matrix A, encodes and encrypts it, and obtains the corresponding ciphertext matrix ct (A), and then upload the ciphertext matrix ct(A) to the cloud server.
[0051]
[0052] The matrix A is a square matrix of order n, n is a positive integer, and ct represents the ciphertext.
[0053] Encoding and encrypting the entire matrix into a ciphertext not only saves storage space, but also only requires a limited number of ciphertext operation...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com