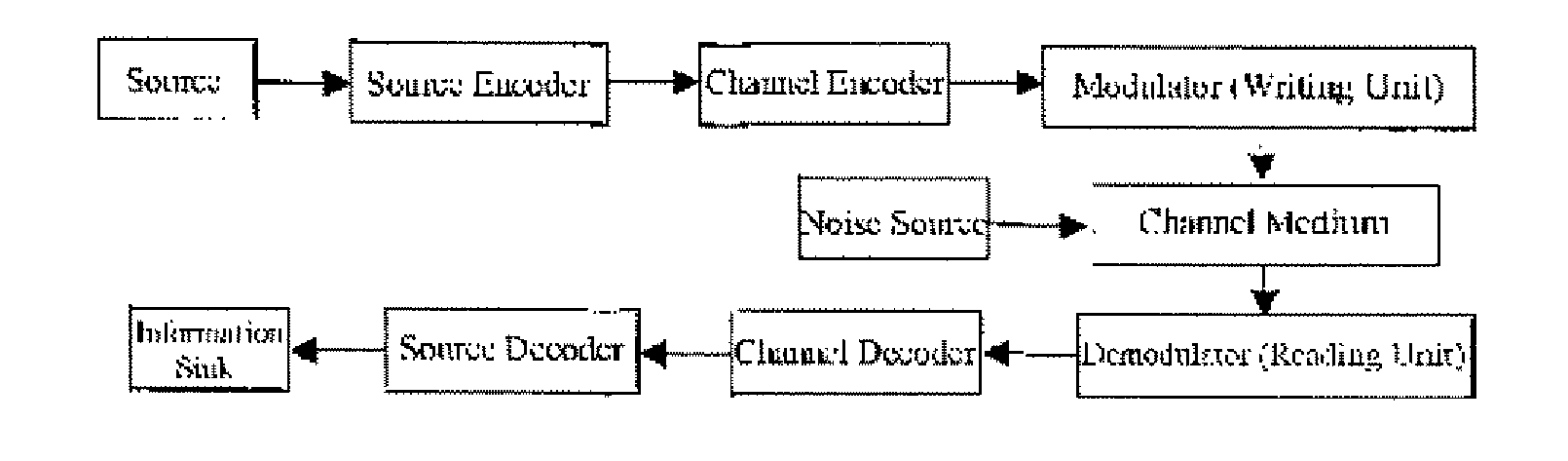
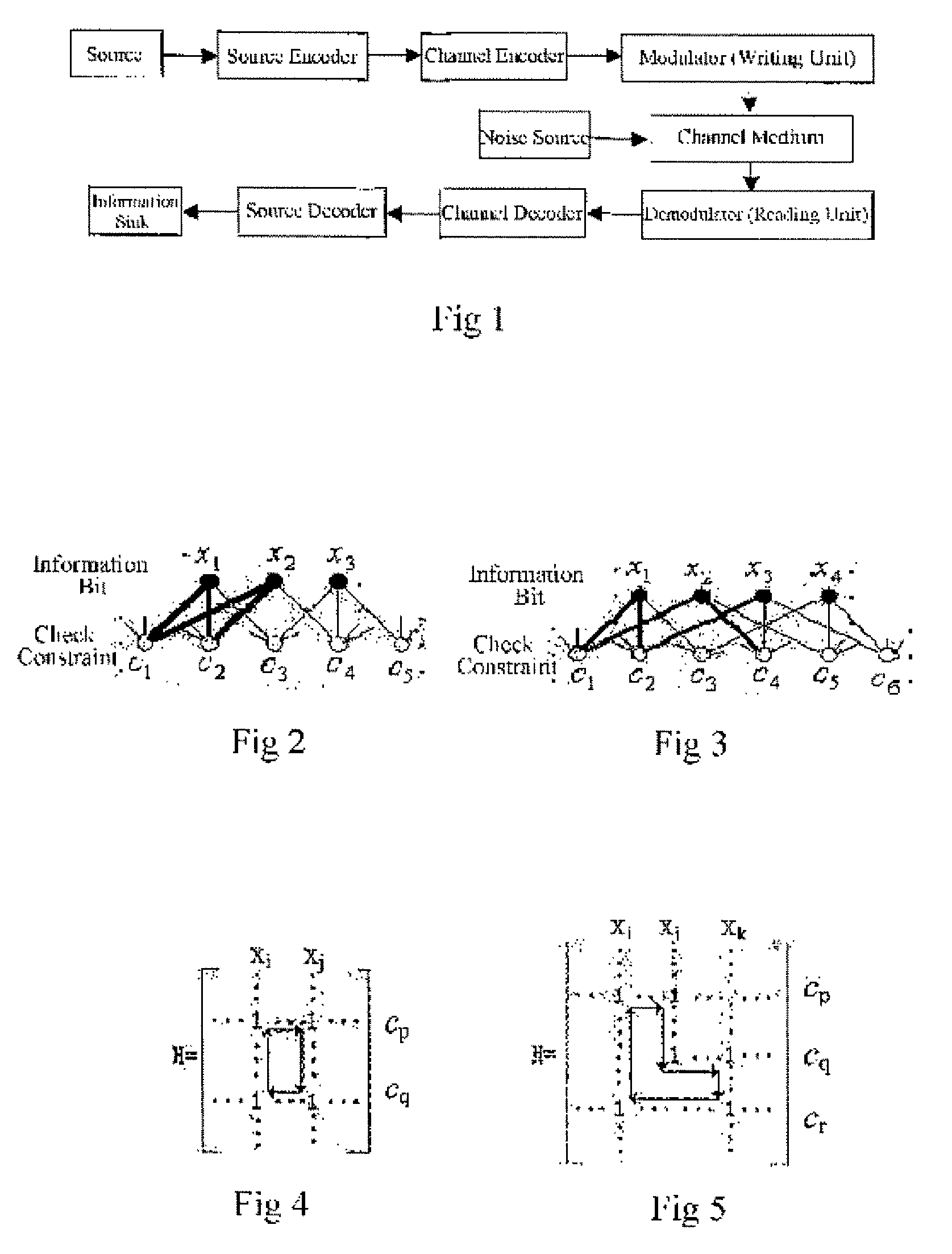
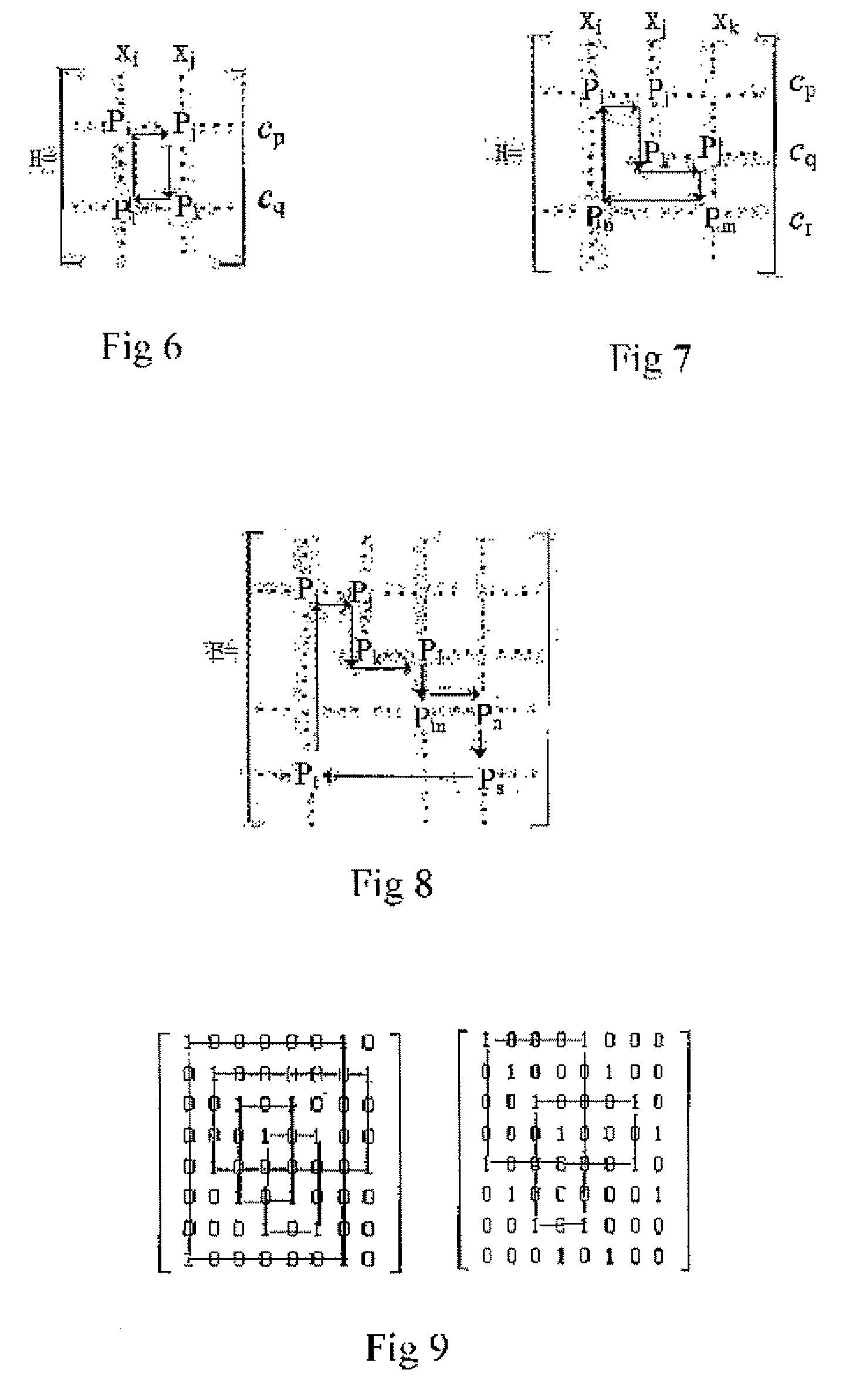
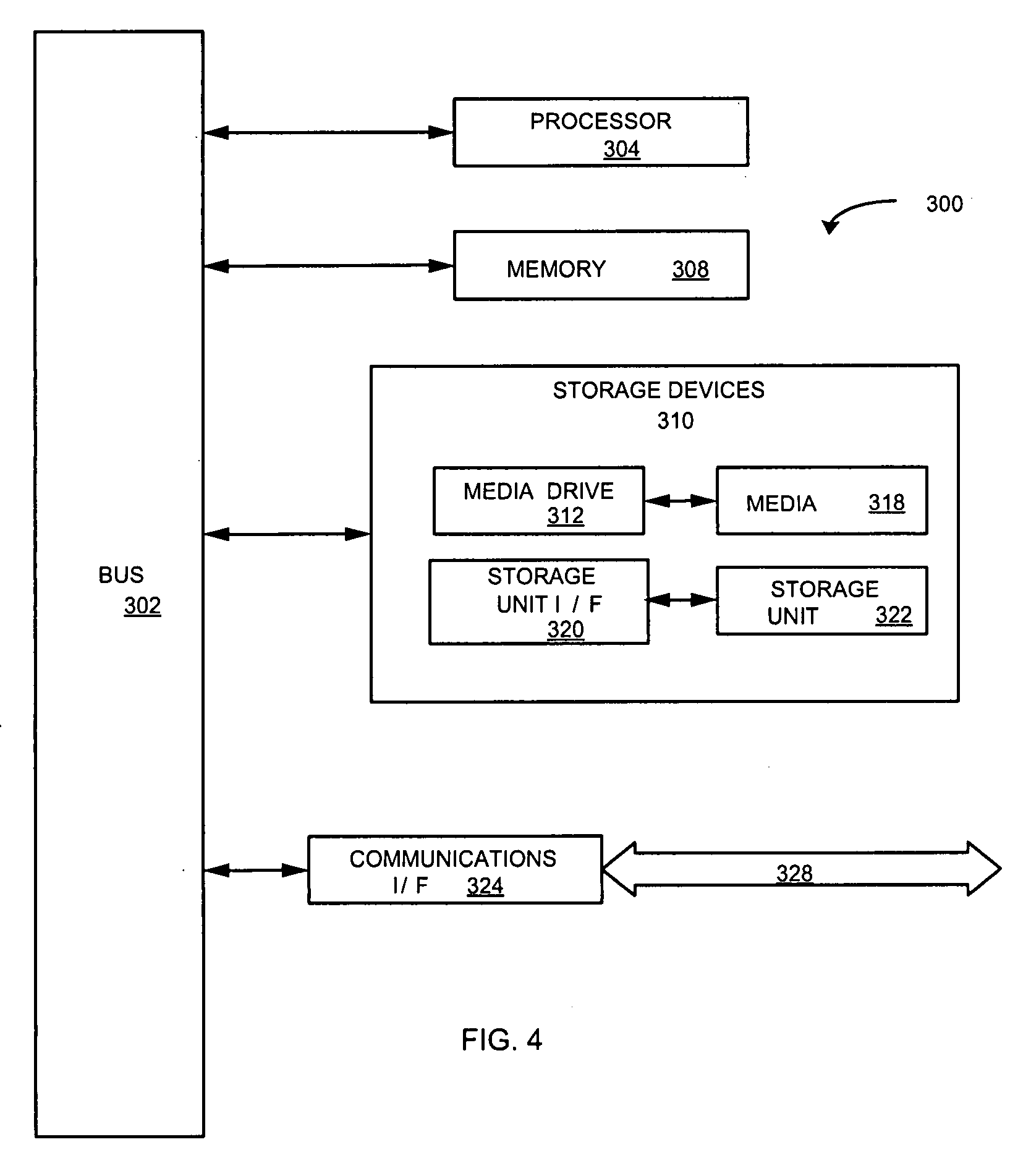
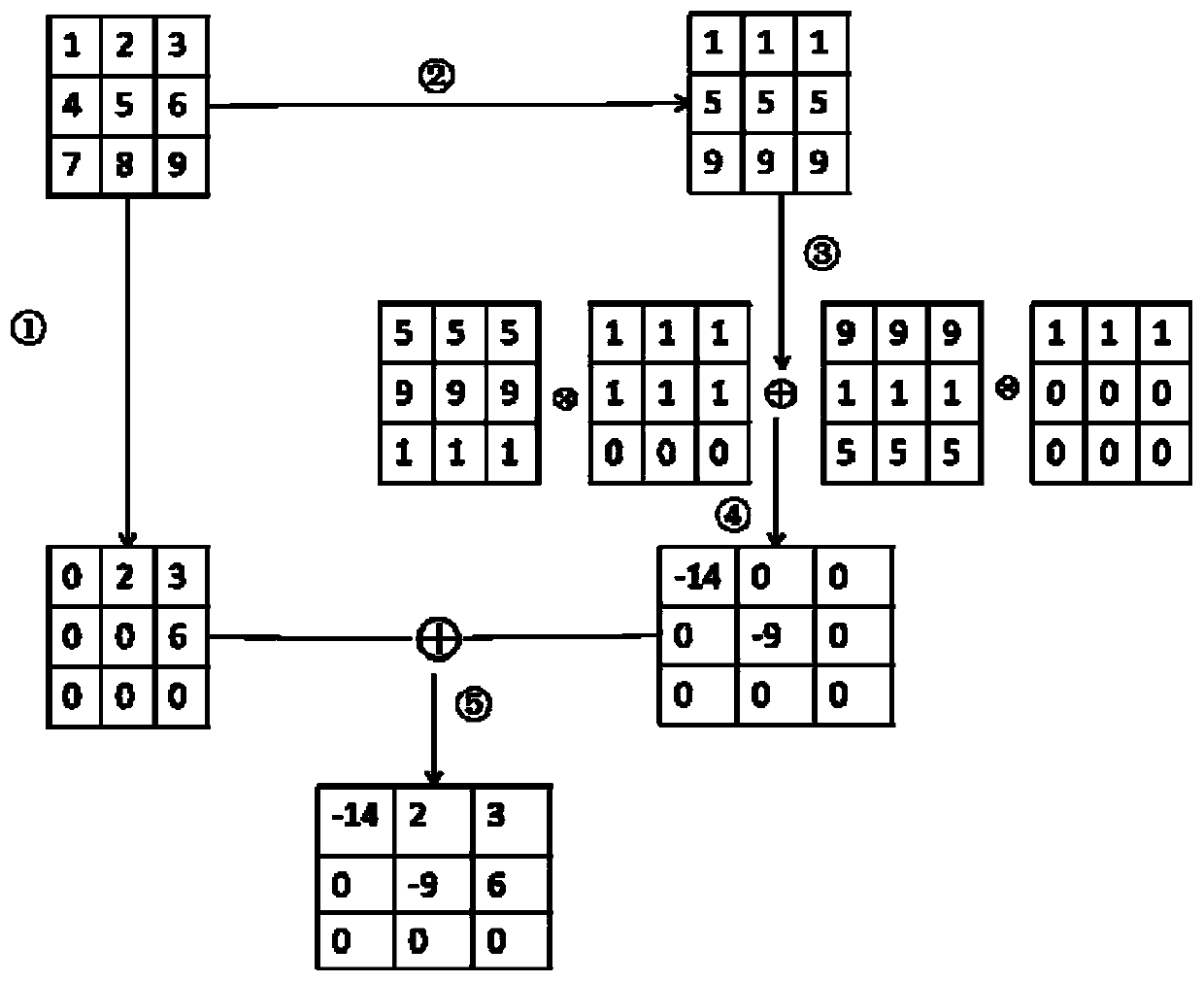
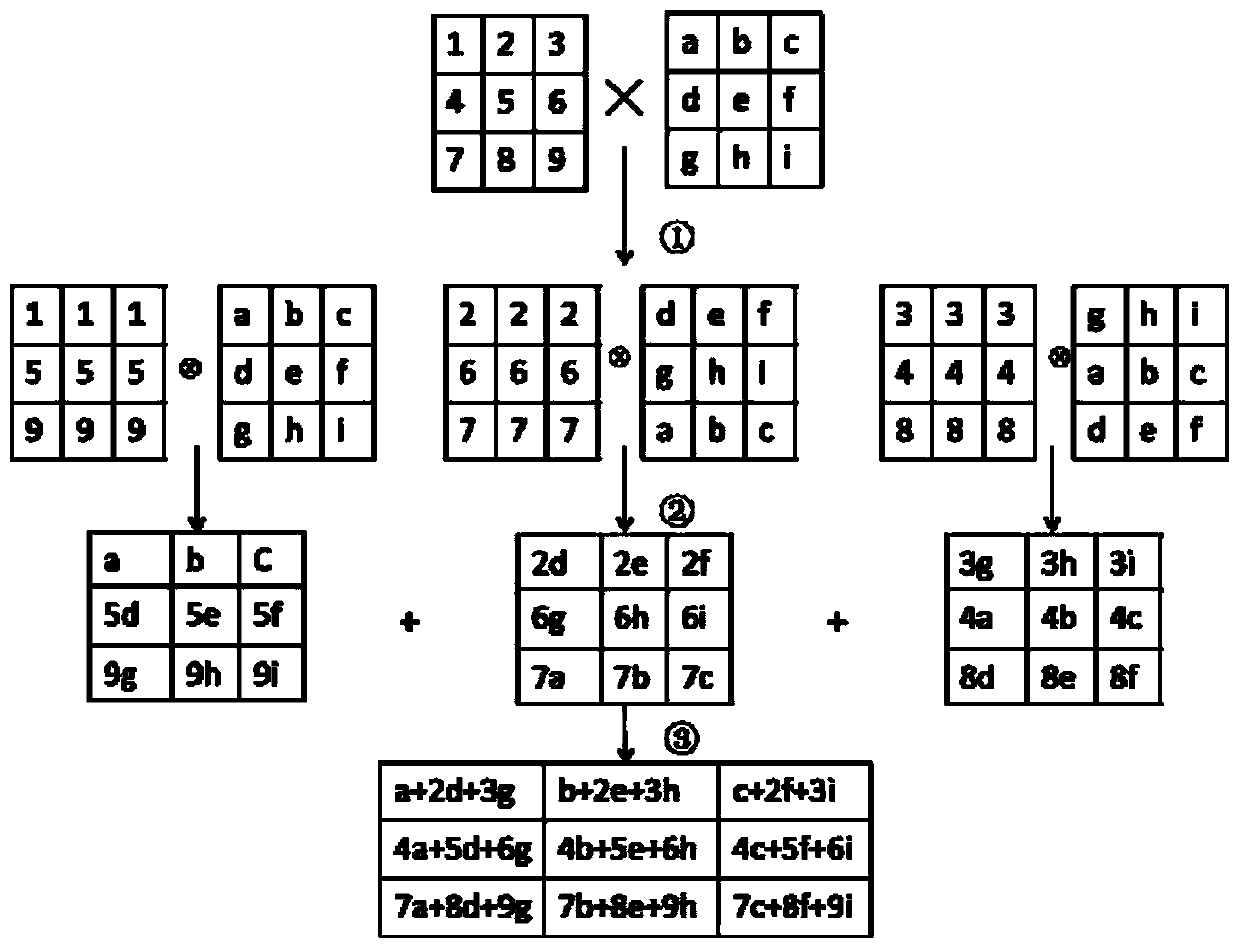
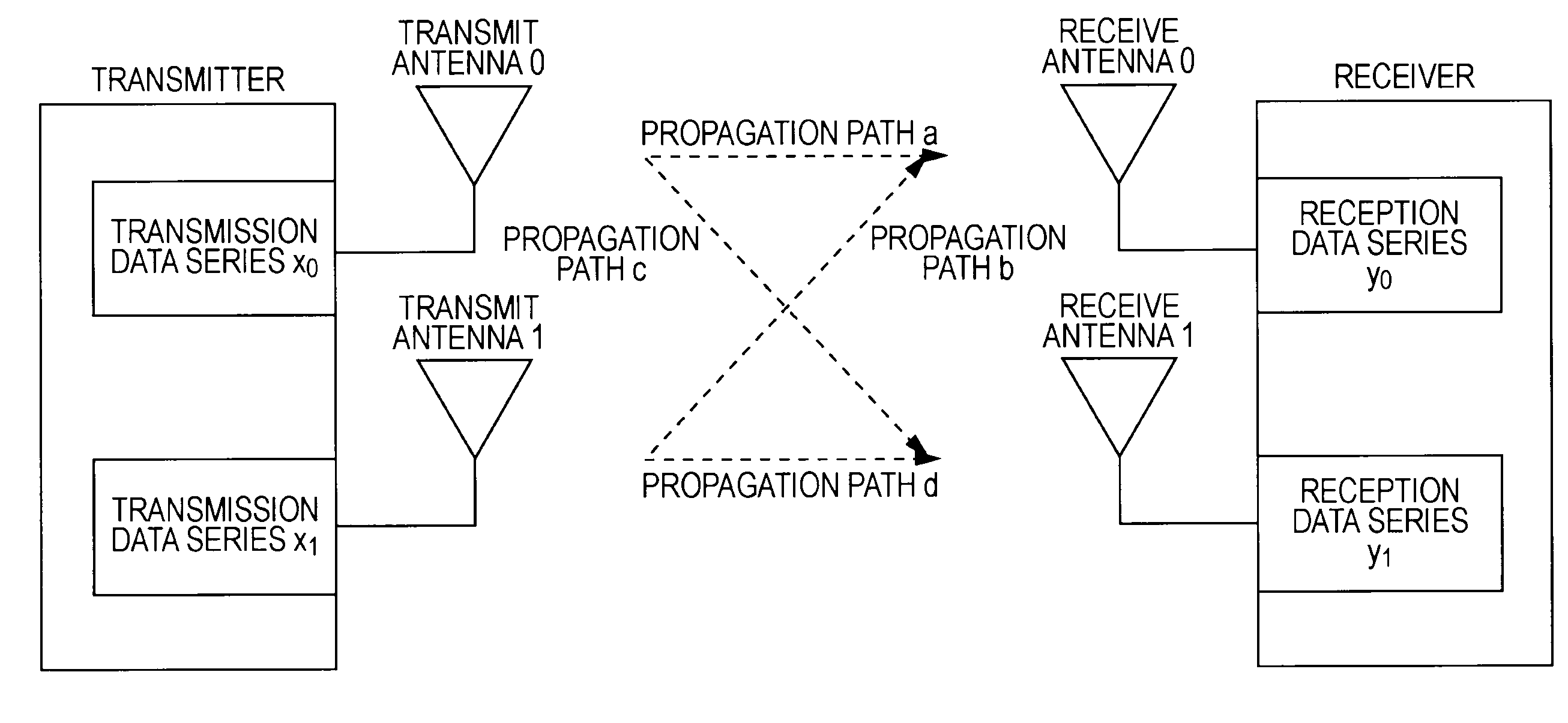
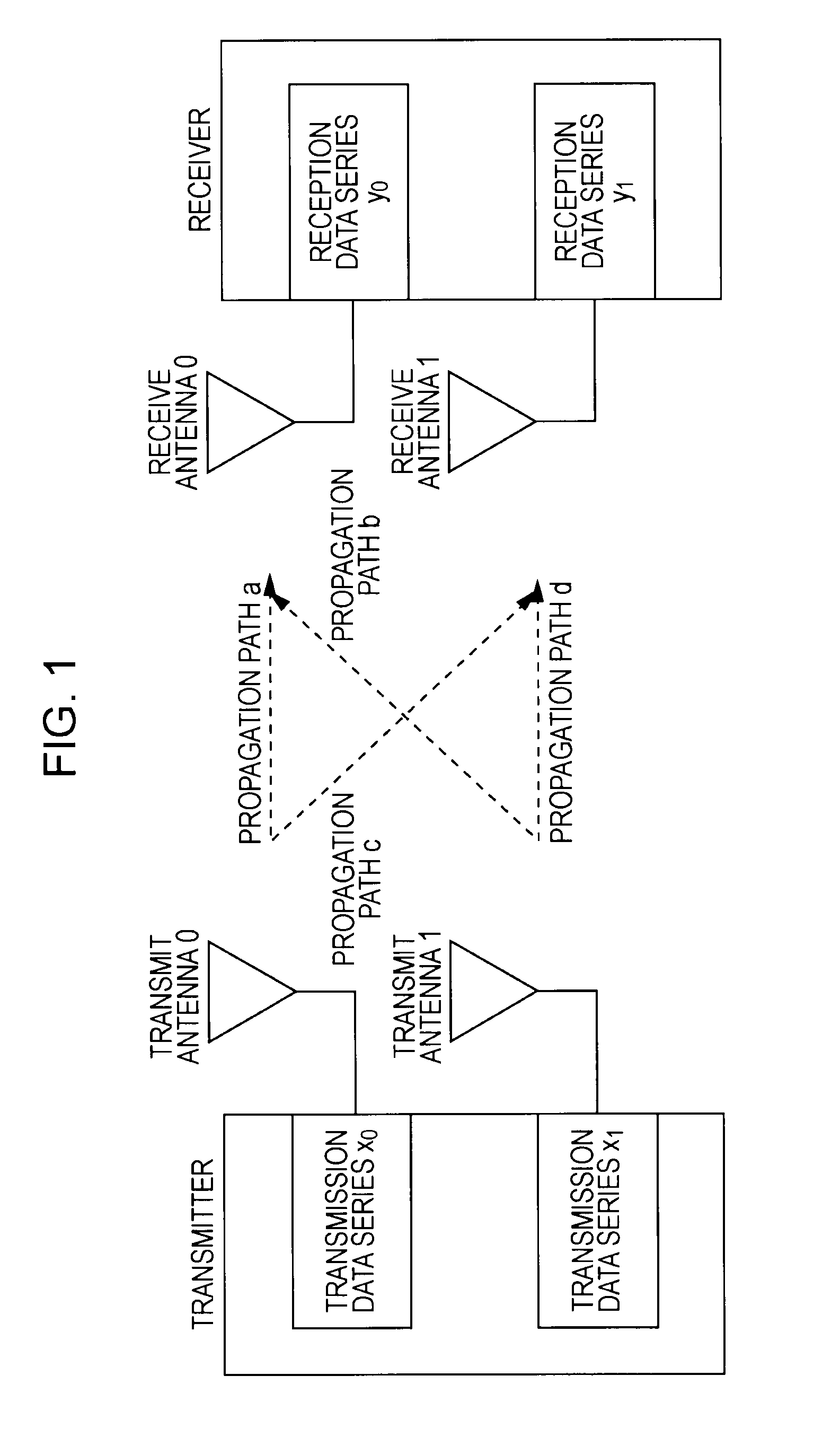
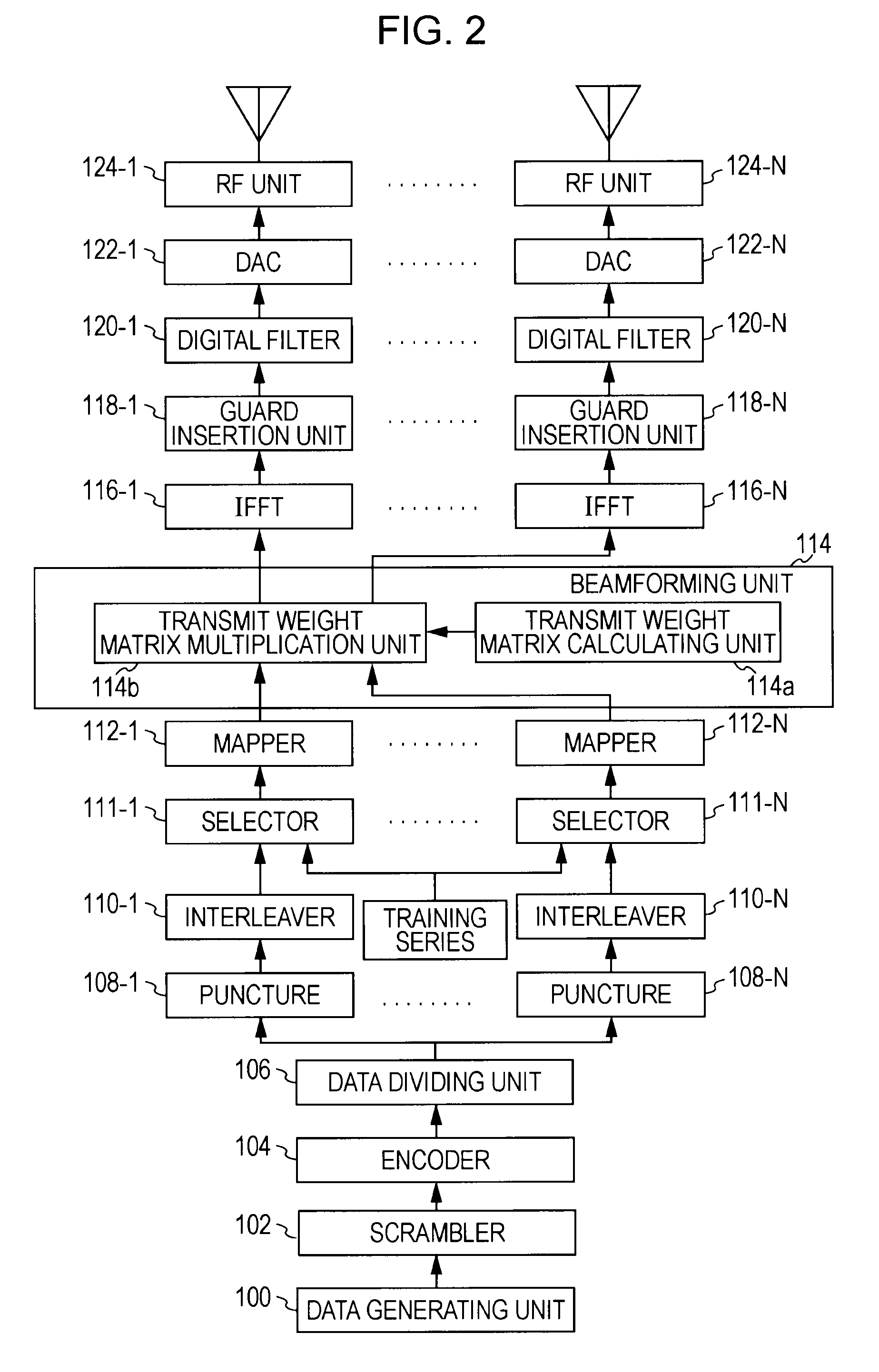
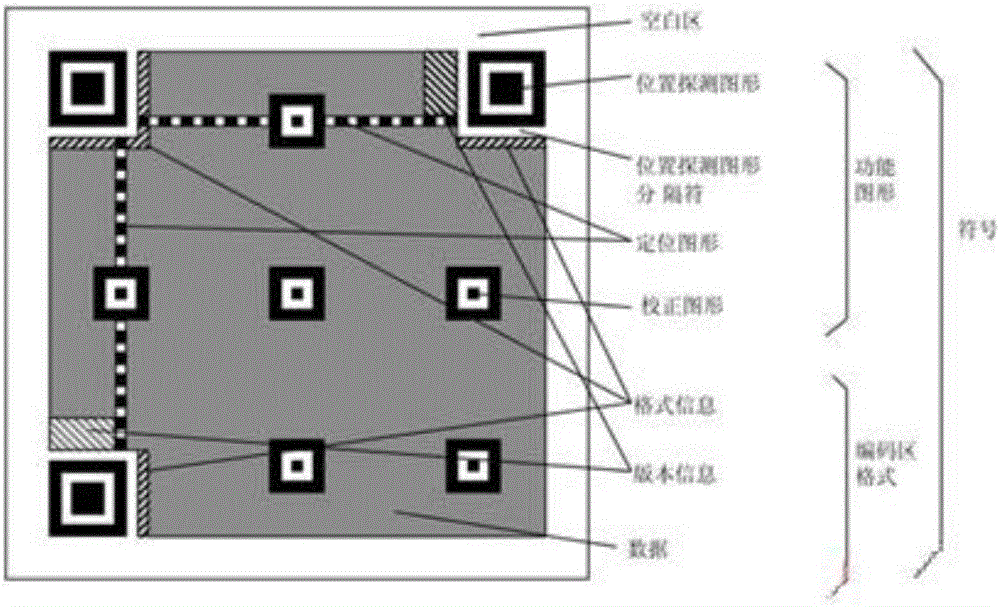
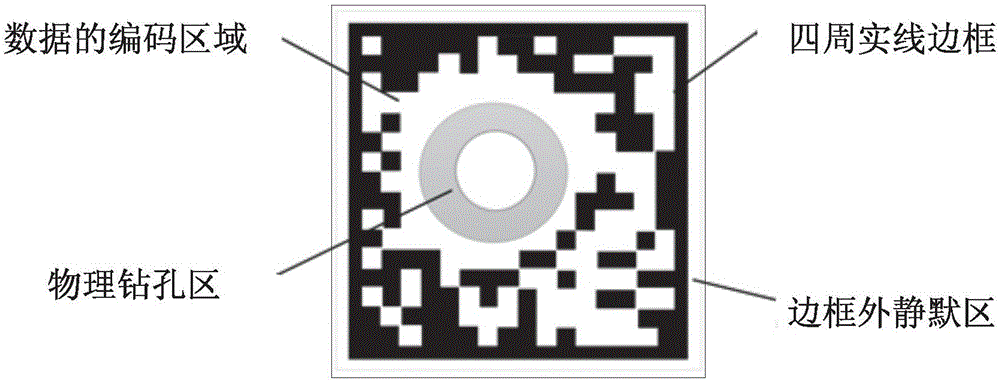
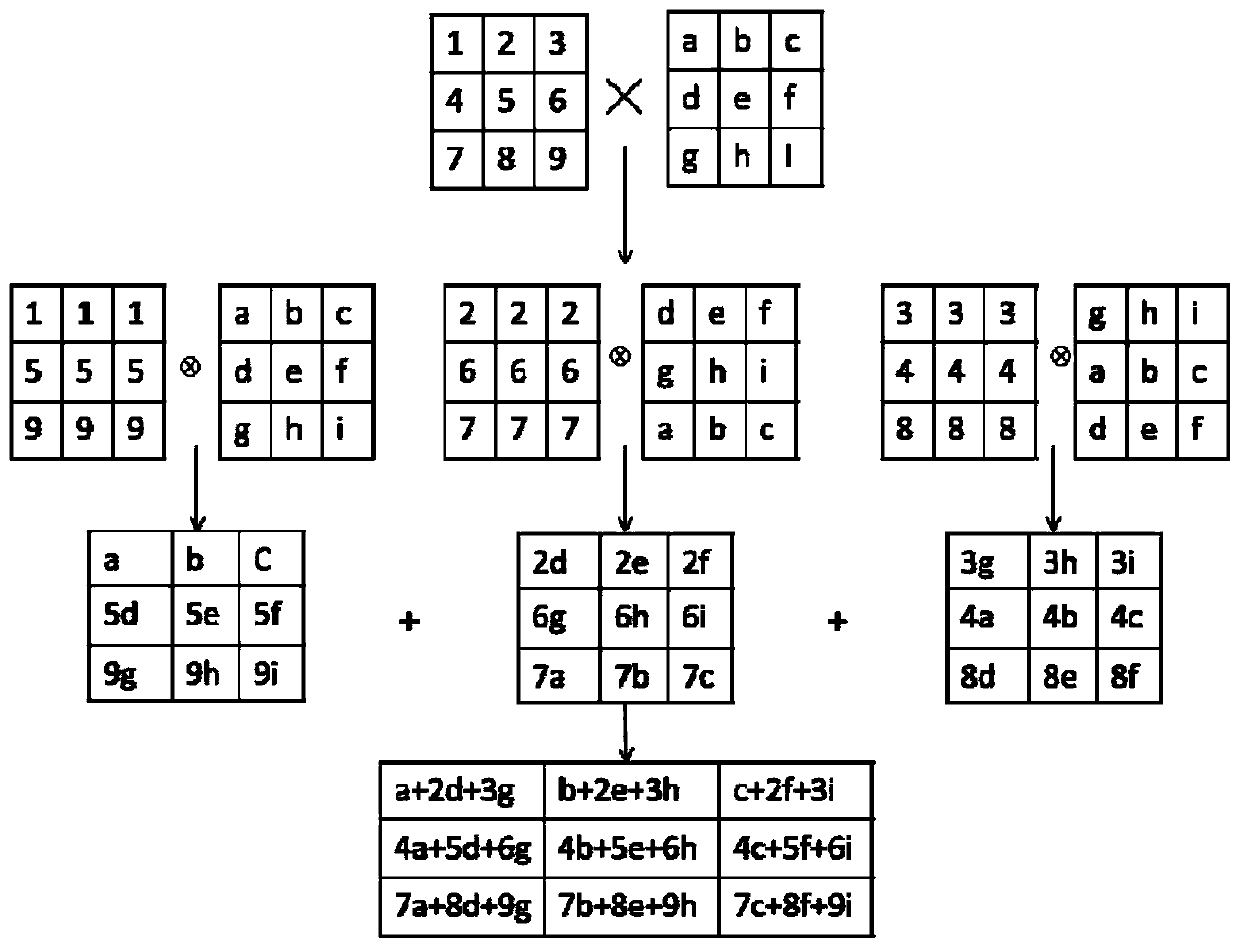
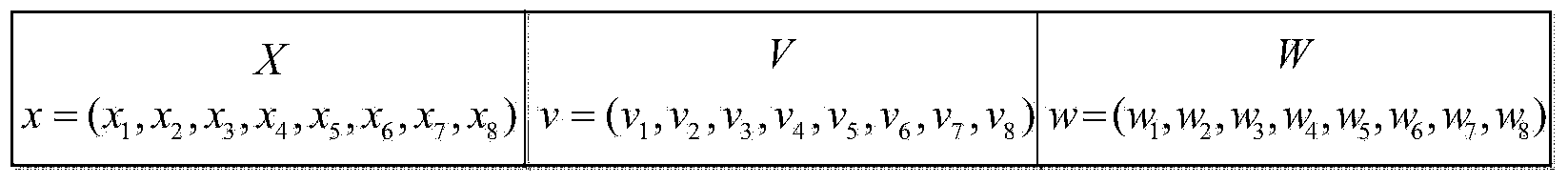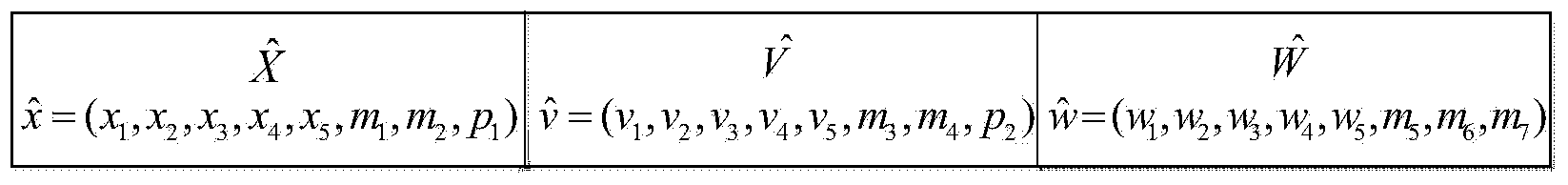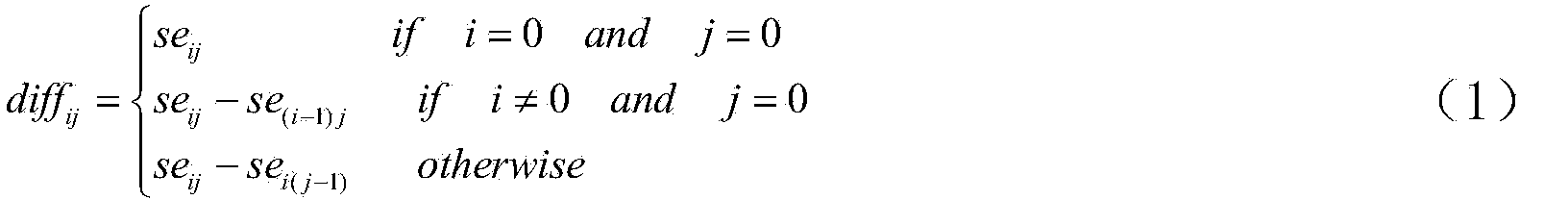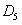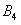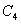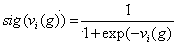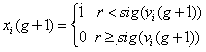Patents
Literature
111 results about "Matrix encoding" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
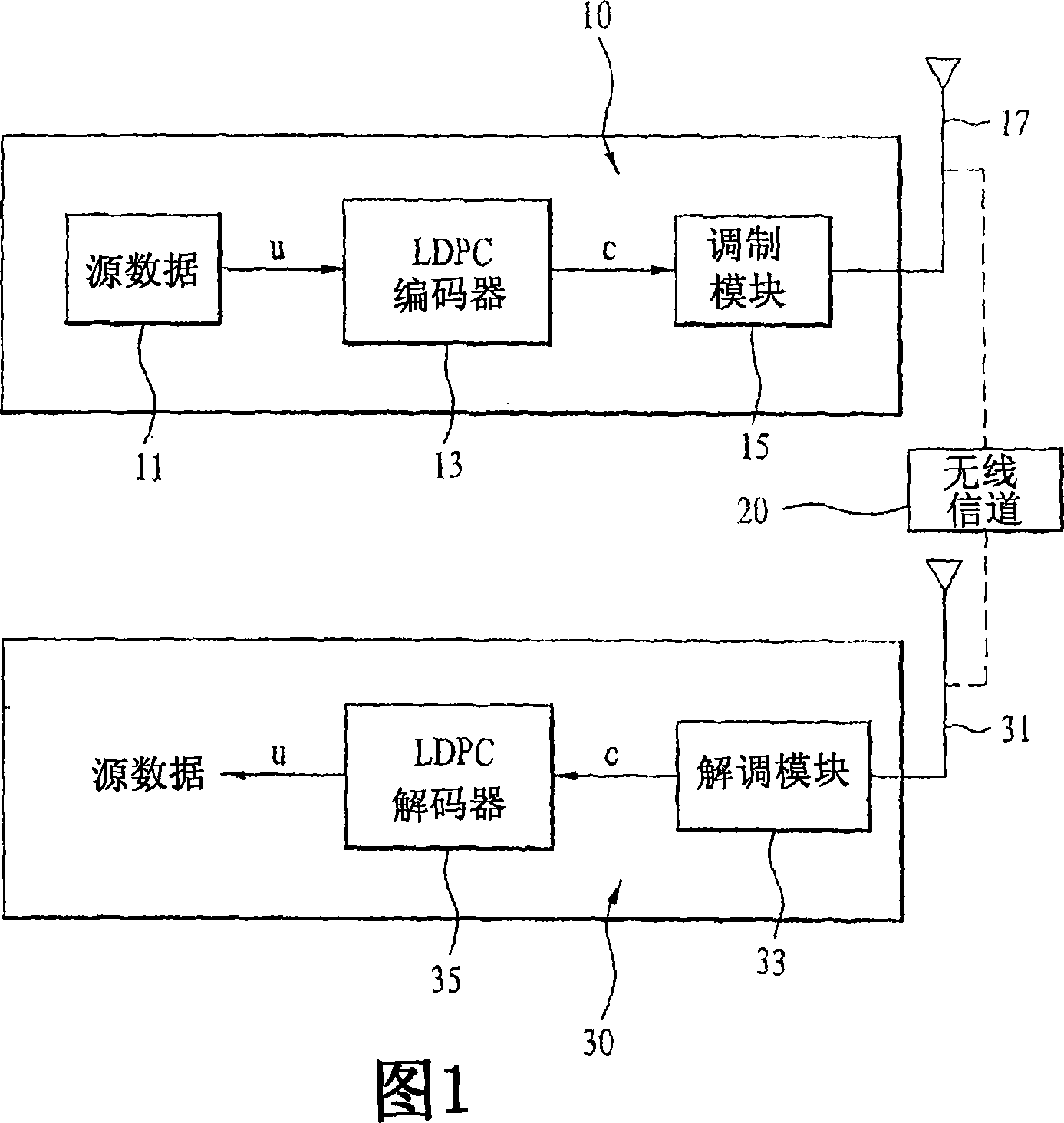
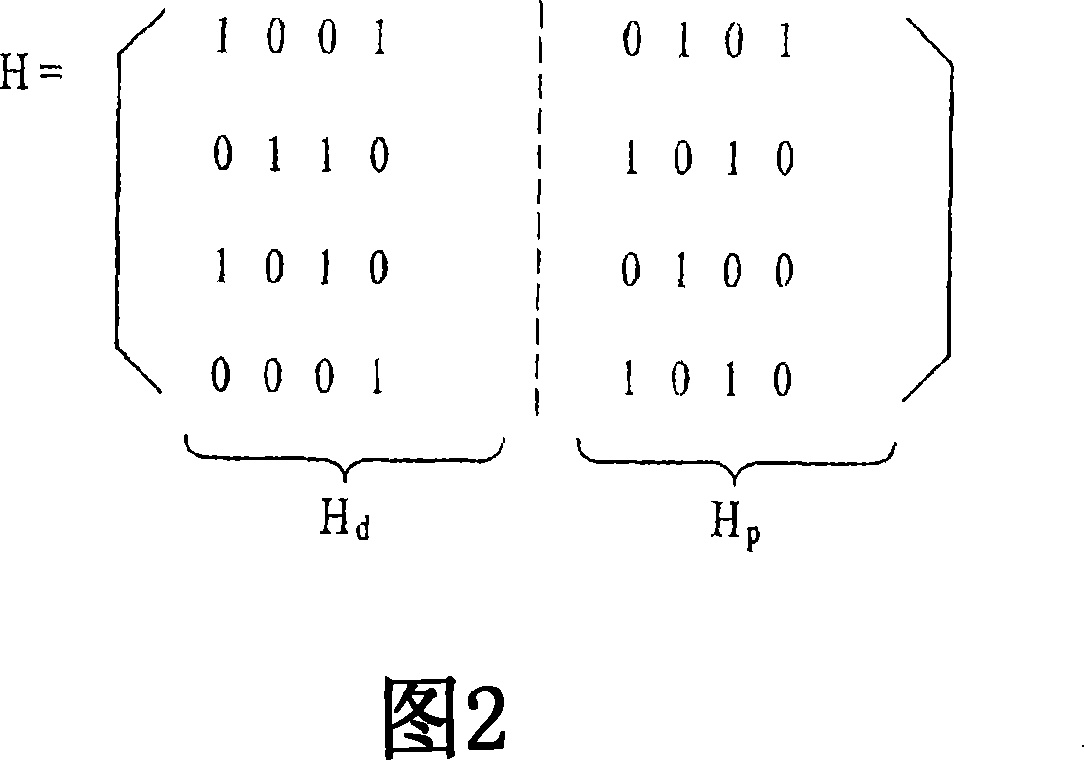
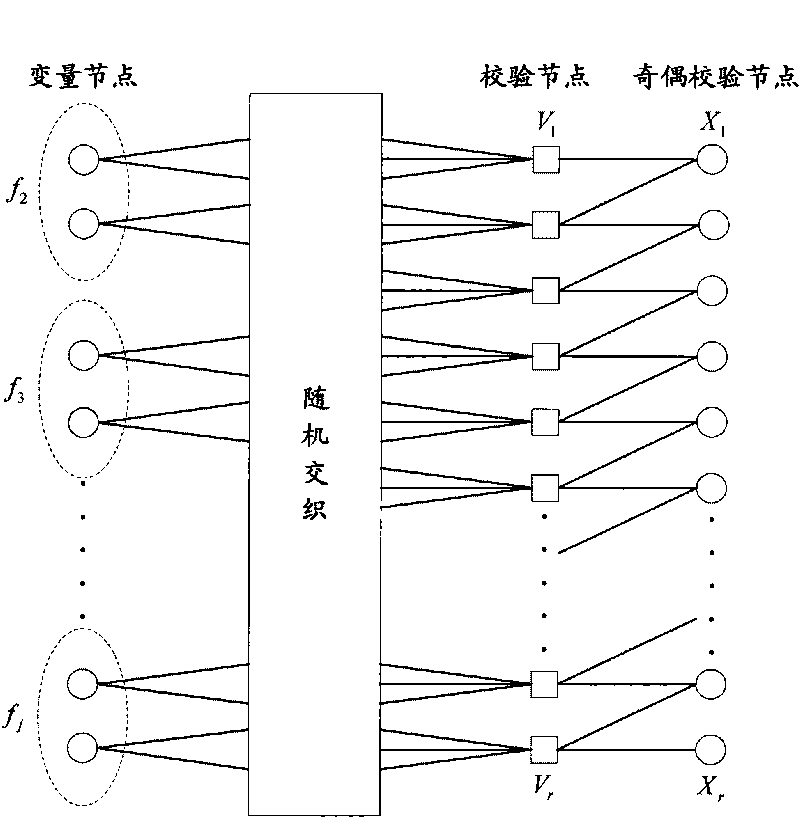
Basic Matrix, Coder/Encoder and Generation Method of the Low Density Parity Check Codes
ActiveUS20090106625A1Eliminate errorAccelerate decrease speedError correction/detection using multiple parity bitsCode conversionError ratioParity-check matrix
The invention relates to a base matrix, a encoder / decoder of Low Density Parity Check (LDPC) codes and a generation method thereof. The encoder / decoder is determined uniquely by the parity check matrix of the LDPC codes. With different code sizes, said parity check matrix can be obtained by expanding different base matrixes, and also can be obtained by expanding a unique base matrix after correction. Elements of said base matrix must meet an inequation in which the girth value is up to the standard, e.g. when girth ≧6, for any element i, j, k, l in the matrix which forms the short loop having a length of 4 in anticlockwise, there are always mod(i−j+k−l, z) unequal to 0. By this invention, the girth of the constructed base matrix is made as large as possible, the amount of the shortest loops is as few as possible when it is the same girth, thus the curve of bit error ratio (BER) is dropped quickly, the error floor of the LDPC codes is eliminated effectively, and the optimal performance of the LDPC codes is obtained.
Owner:ZTE CORP
Image hiding and authentication method based on secret sharing
ActiveCN103761702AImprove securityDifferences in Statistical PropertiesImage data processing detailsPattern recognitionHash function
The invention discloses an image hiding and authentication method based on secret sharing, and belongs to the technical field of secret image sharing. The image hiding and authentication method is characterized by comprising the steps that firstly, difference Huffman encoding is conducted on a secret image, every three generated bit sequences are set to be one group to be converted into decimal numbers which are used as coefficients of a sharing polynomial in the Shamir (k, n) threshold scheme, the k and the n are positive integers, the k is smaller than or equal to the n, and n shadow images are generated; secondly, n significant carrier images are selected, the generated shadow images are embedded into the carrier images in a matrix encoding mode, authentication bits generated by the hash function are also embedded into the carrier images, and n disguise images are formed and are in the charge of n different participants respectively. The disguise images generated through the image hiding and authentication method has higher visual quality, existence of secret information cannot be perceived by attackers easily, and the safety of the secret information is ensured. Meanwhile, before the secret information is recovered, the disguise images provided by each participant need to be authenticated, only the disguise images passing through authentication can participate in recovery of the secret information, and the safety of the secret information is further strengthened.
Owner:TAIYUAN UNIVERSITY OF SCIENCE AND TECHNOLOGY
Method of training a neural network
A method of training a neural network having at least an input layer, an output layer and a hidden layer, and a weight matrix encoding connection weights between two of the layers, the method comprising the steps of (a) providing an input to the input layer, the input having an associated expected output, (b) receiving a generated output at the output layer, (c) generating an error vector from the difference between the generated output and expected output, (d) generating a change matrix, the change matrix being the product of a random weight matrix and the error vector, and (e) modifying the weight matrix in accordance with the change matrix.
Owner:OXFORD UNIV INNOVATION LTD
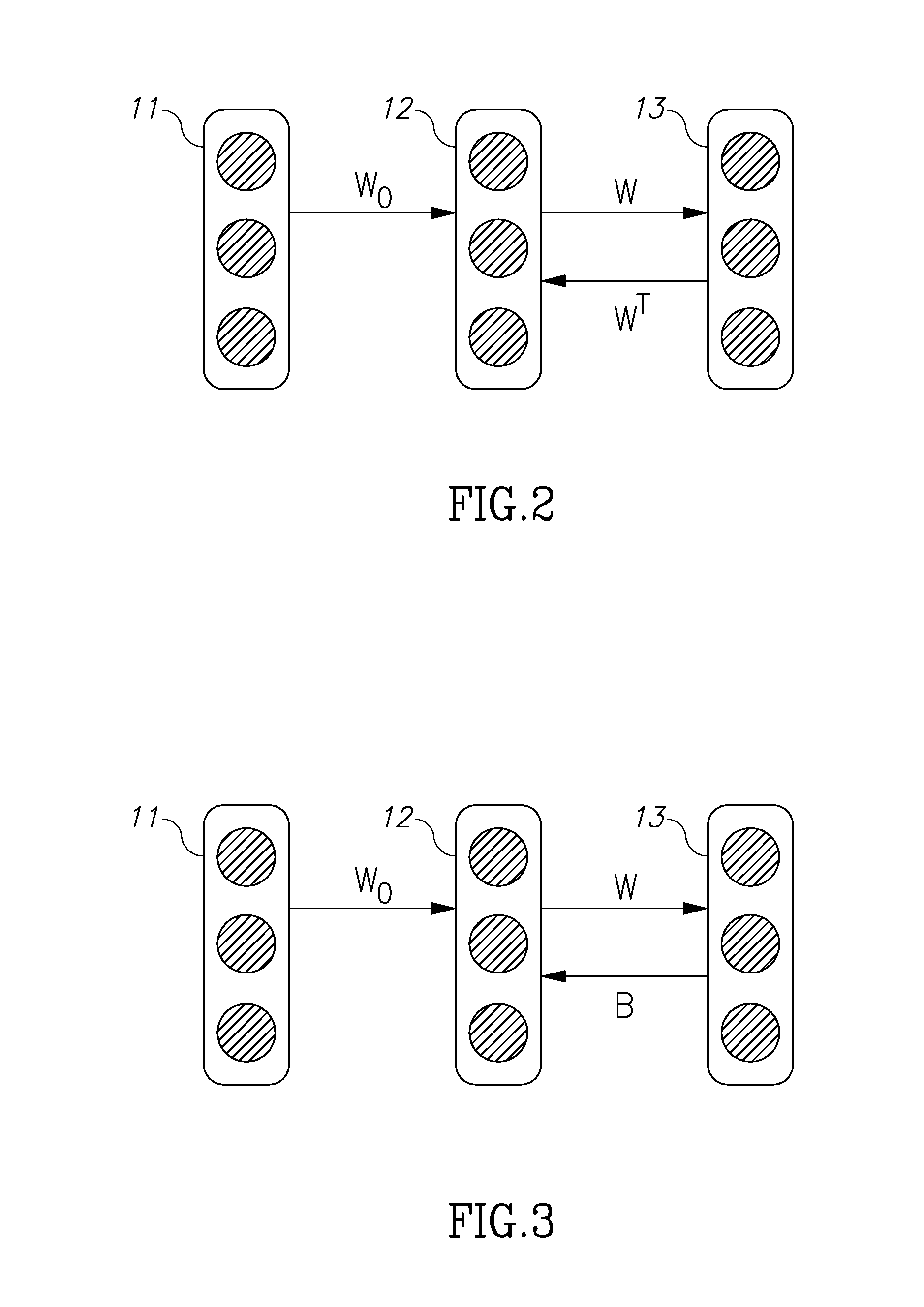
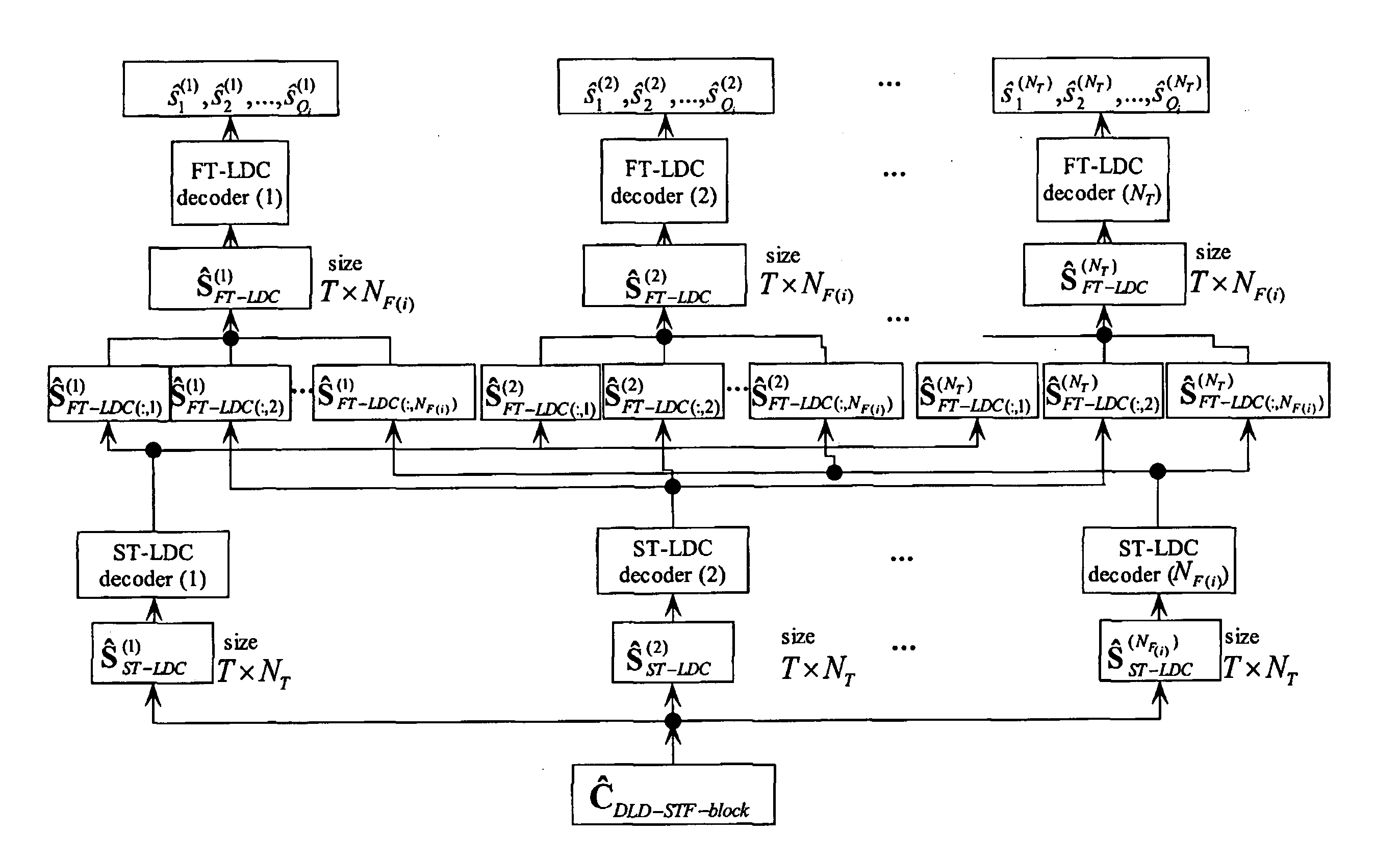
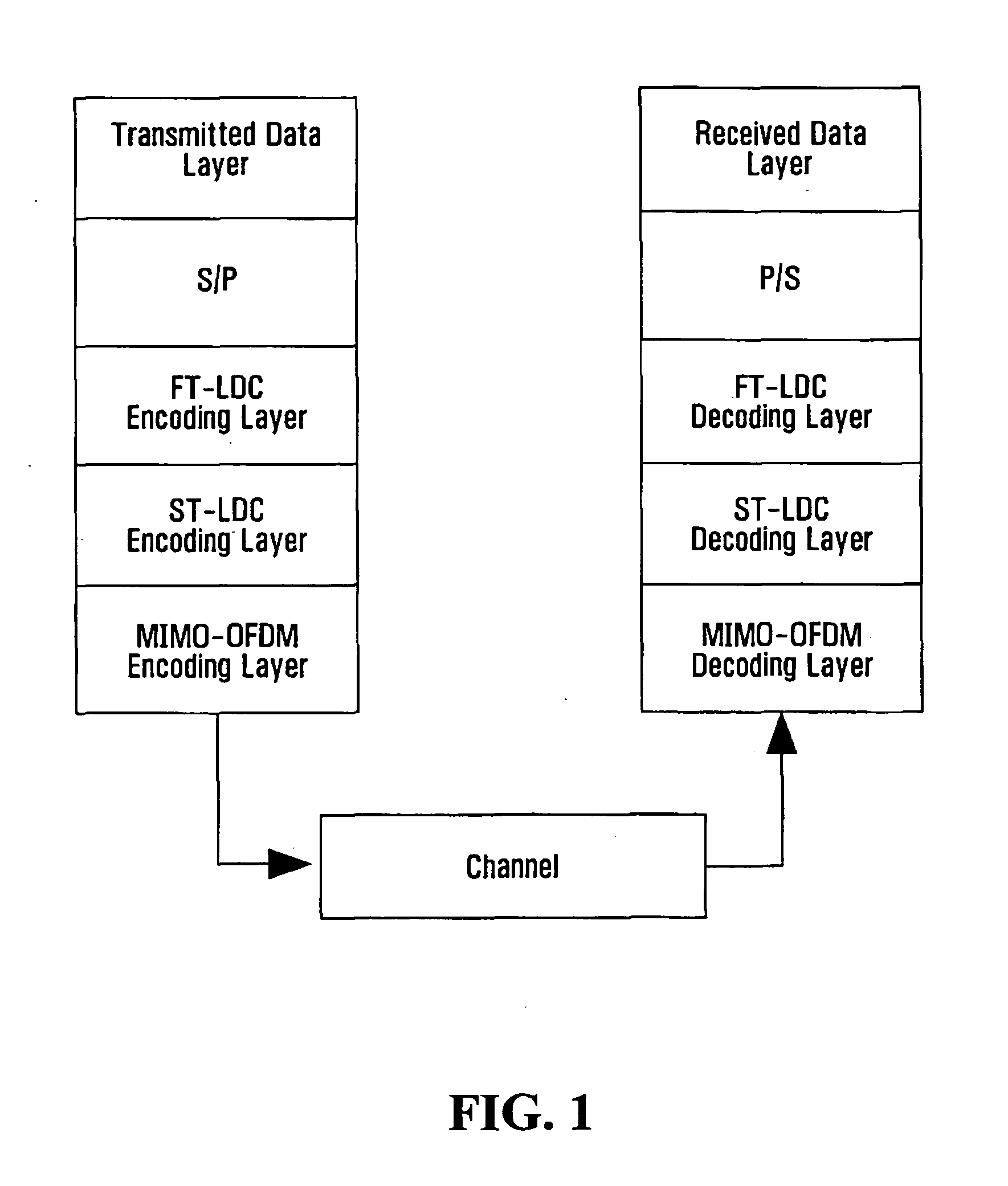
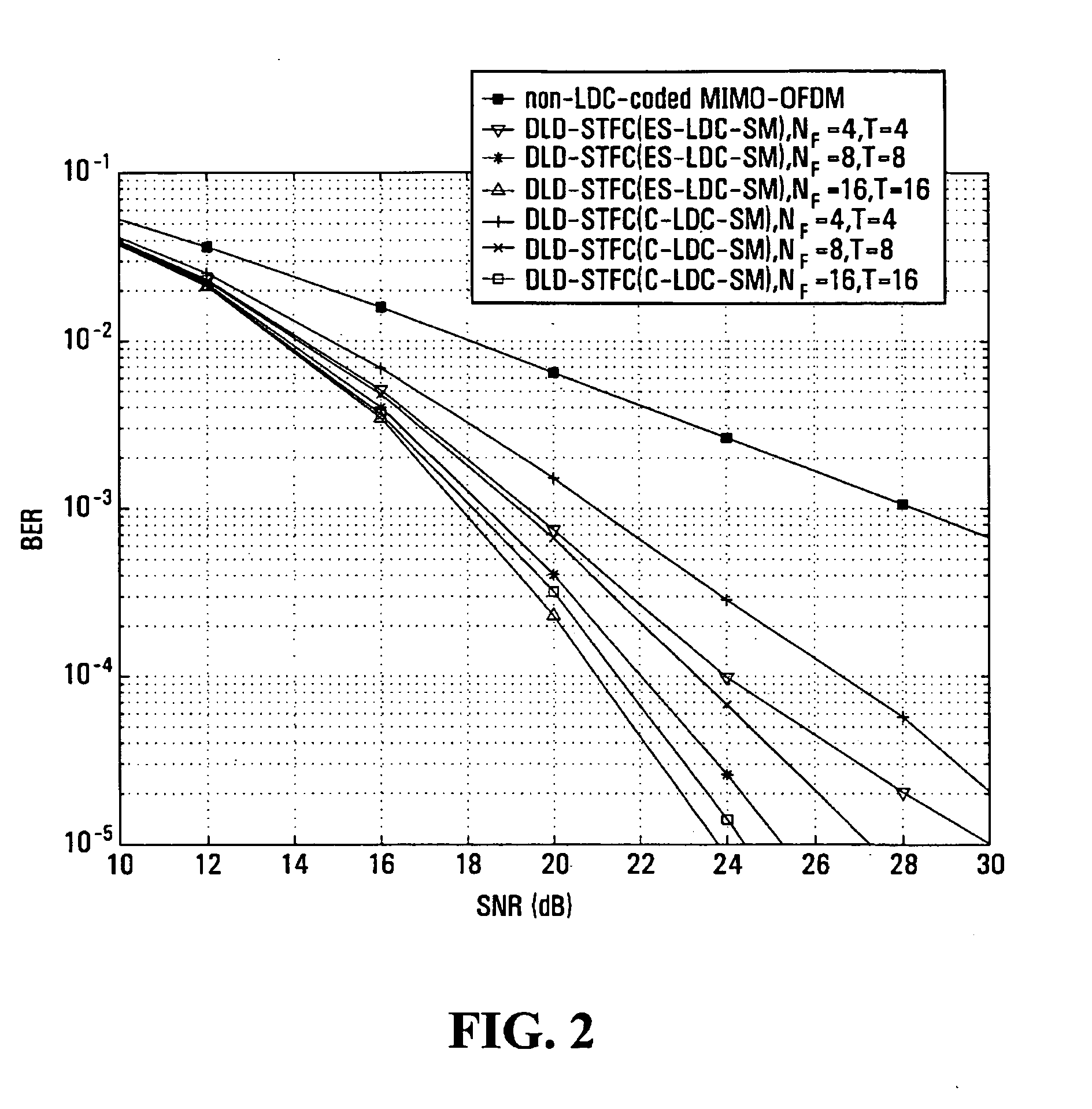
System and method employing linear dispersion over space, time and frequency
InactiveUS20070177688A1Diversity/multi-antenna systemsForward error control useLinear dispersionTwo-vector
Systems and methods for performing space time coding are provided. Two vector→matrix encoding operations are performed in sequence to produce a three dimensional result containing a respective symbol for each of a plurality of frequencies, for each of a plurality of transmit durations, and for each of a plurality of transmitter outputs. The two vector→matrix encoding operations may be for encoding in a) time-space dimensions and b) time-frequency dimensions sequentially or vice versa.
Owner:QUEENS UNIV OF KINGSTON
Coding and decoding methods of ode of tail-biting staircase codes
ActiveCN105429646AGuaranteed error correction performanceTroubleshoot issues where uncorrected errors are affecting overall performanceError correction/detection using convolutional codesError correction/detection by combining multiple code structuresComputer architectureBlock code
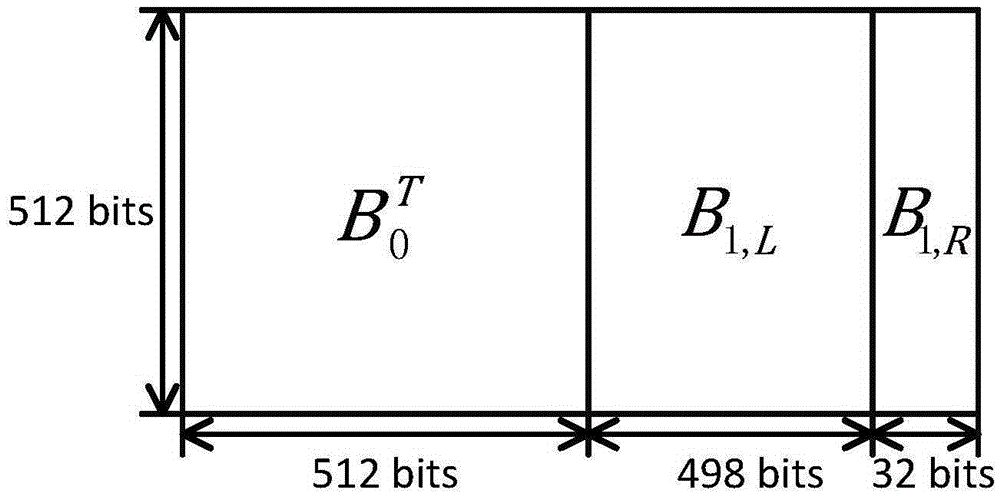
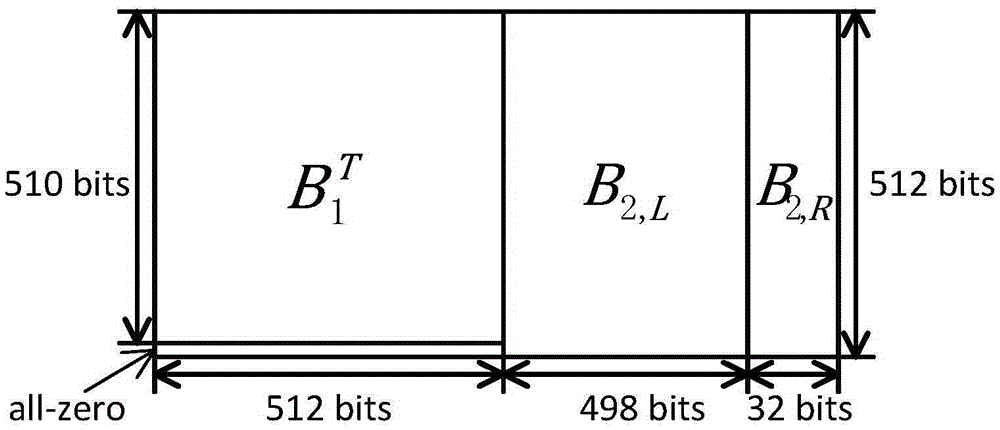
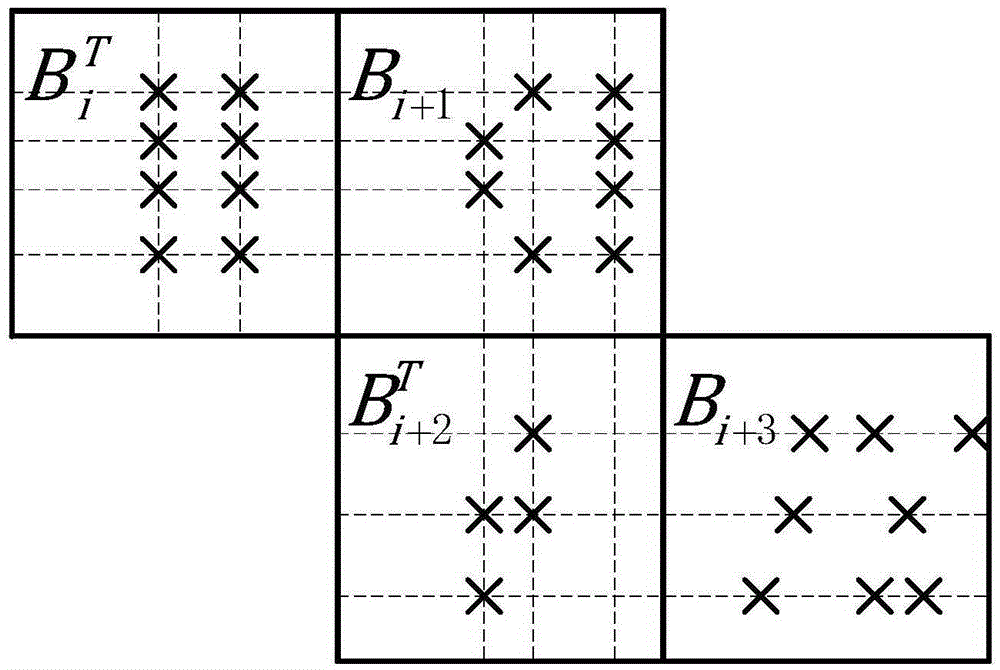
The invention relates to a tail-biting staircase code coding method. The tail-biting staircase code coding method comprises the following steps: 1) selecting an (n, k) linear block code as a component code, wherein n represents a code length, n belongs to (500, 5000), and k represents an information length before coding; and 2) grounding received information according to a mode in staircase codes, constructing a matrix B<1>, B<2>, B<3>, ..., B<n>, adding a full-zero matrix participating the coding to a lower part of B<1>, coding the residual matrix using the component code then, generating a check bit matrix while the coding, completing end-to-end connection of codes of a final matrix and a first matrix in a group then, finally replacing the full-zero matrix complemented in the B<1> with the check bit matrix, and completing the coding. The coding method is advantageous in that, through adoption of the novel coding scheme, the novel tail-biting staircase codes have a characteristic of the block code, coding processes between groups are mutually independent, information of each matrix in the groups is still contained in the two component codes, and error correction performance is guaranteed.
Owner:NANJING UNIV
Freezing a subject's contextualization of a proposition considered in a quantum representation by using a Quantum Zeno effect
The present invention concerns methods and apparatus for using a Quantum Zeno type effect to arrest the evolution or freeze a contextualization adopted by a subject in contextualizing an underlying proposition that typically revolves about an item. The subject is understood to be any sentient being, e.g., a human being that uses the known contextualization modulo the underlying proposition and also exhibits a known initial measurable indication in response to the underlying proposition. Measurable indications can take on the form of responses, actions, behaviors or any measurable aspects that can be collected from the subject in response to the underlying propositions. In the quantum representation as adopted herein, the matrix encoding the contextualization exhibited by the subject is a quantum mechanical operator and the initial measurable indication corresponds to one of its eigenvalues.
Owner:INVENT LY LLC
Strengthening parity check bit protection for array-like LDPC codes
InactiveUS20080235559A1Error detection/correctionError correction/detection using multiple parity bitsTheoretical computer scienceParity-check matrix
An LDPC parity check matrix originated using an array code provides more protection against errors for parity bits 1 through 1-p, which can, during decoding, allow faster convergence to a higher LLR value for those bits as well as higher overall reliability of other parity check bits. The present parity check matrix provides an upper triangular sub-matrix (H1) for the parity check bits, where column weights for parity bits 1 through p-1 can be greater than 1. Aspects include encoders to encode user bits using the parity check matrix, decoders to decode based on the parity check matrix, systems comprising encoders and / or decoders, encoder and decoder methods; as well as computer readable media comprising programs for implementing such methods.
Owner:QUANTUM CORP
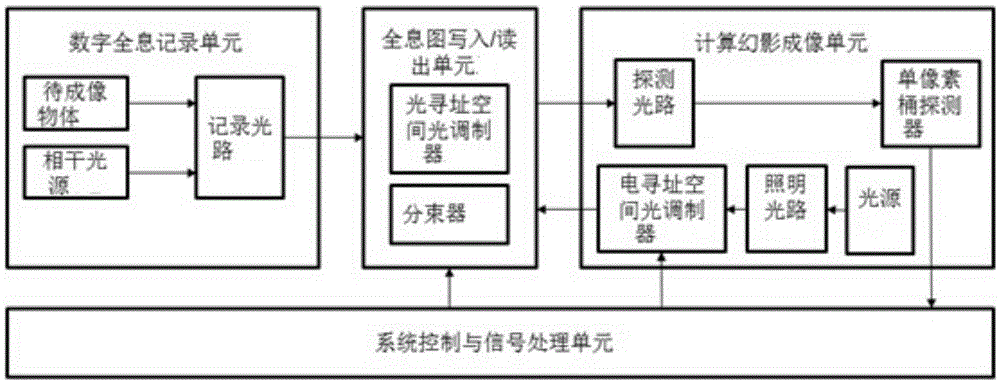
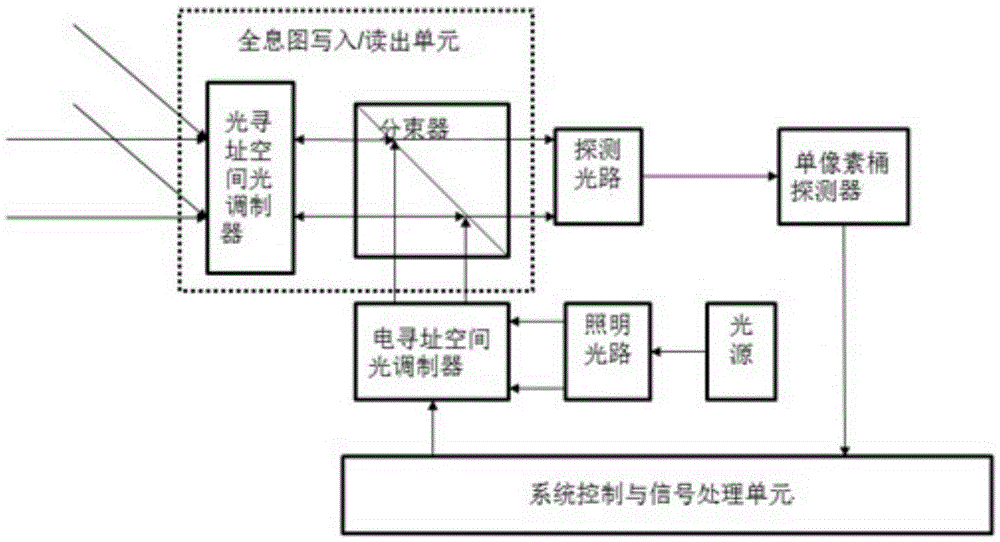
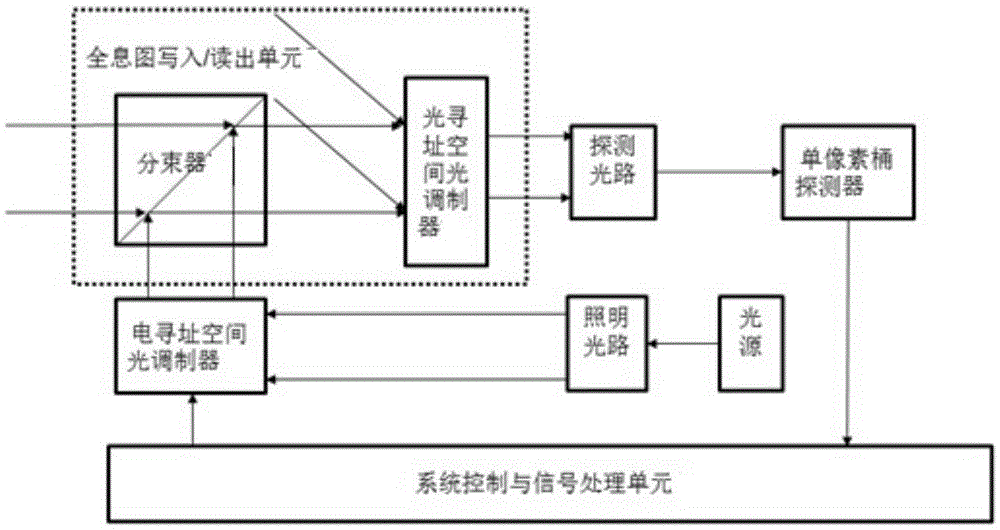
Digital holography ghost imaging system by adopting single-pixel or bucket detector and working method thereof
The invention relates to a digital holography ghost imaging system by adopting a single-pixel or bucket detector and a working method thereof. The system comprises a digital holography recording unit, a hologram writing / reading unit, a computational ghost imaging unit and a system control and signal processing unit, wherein the digital holography recording unit generates a hologram of a target object and the hologram serves as writing light to be written in the hologram writing / reading unit; and the computational ghost imaging unit generates structured light which can be dynamically refreshed and carries reference matrix encoding information, and the structured light serves as reading light to read the hologram, and the hologram is received by the single-pixel or bucket detector. The method of the invention combines the ghost imaging and the digital holography, and the problems that the size of the target surface of a plane array photoelectric detector and the resolution are insufficient and plane array photoelectric detectors of certain wave bands are hard to make as a result of limitations such as the material and the technology in the digital holography technology applications can be solved.
Owner:SHANDONG UNIV
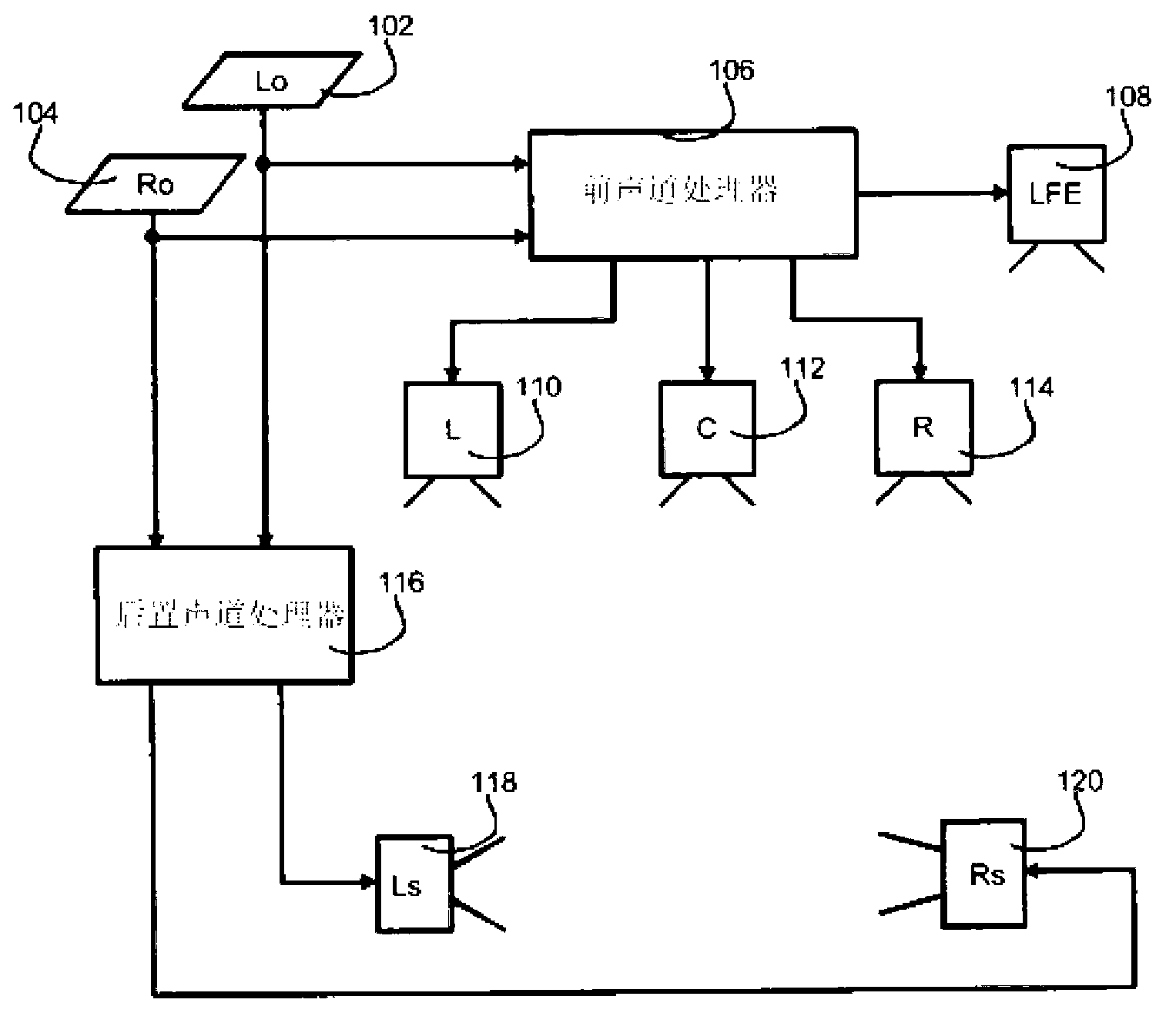
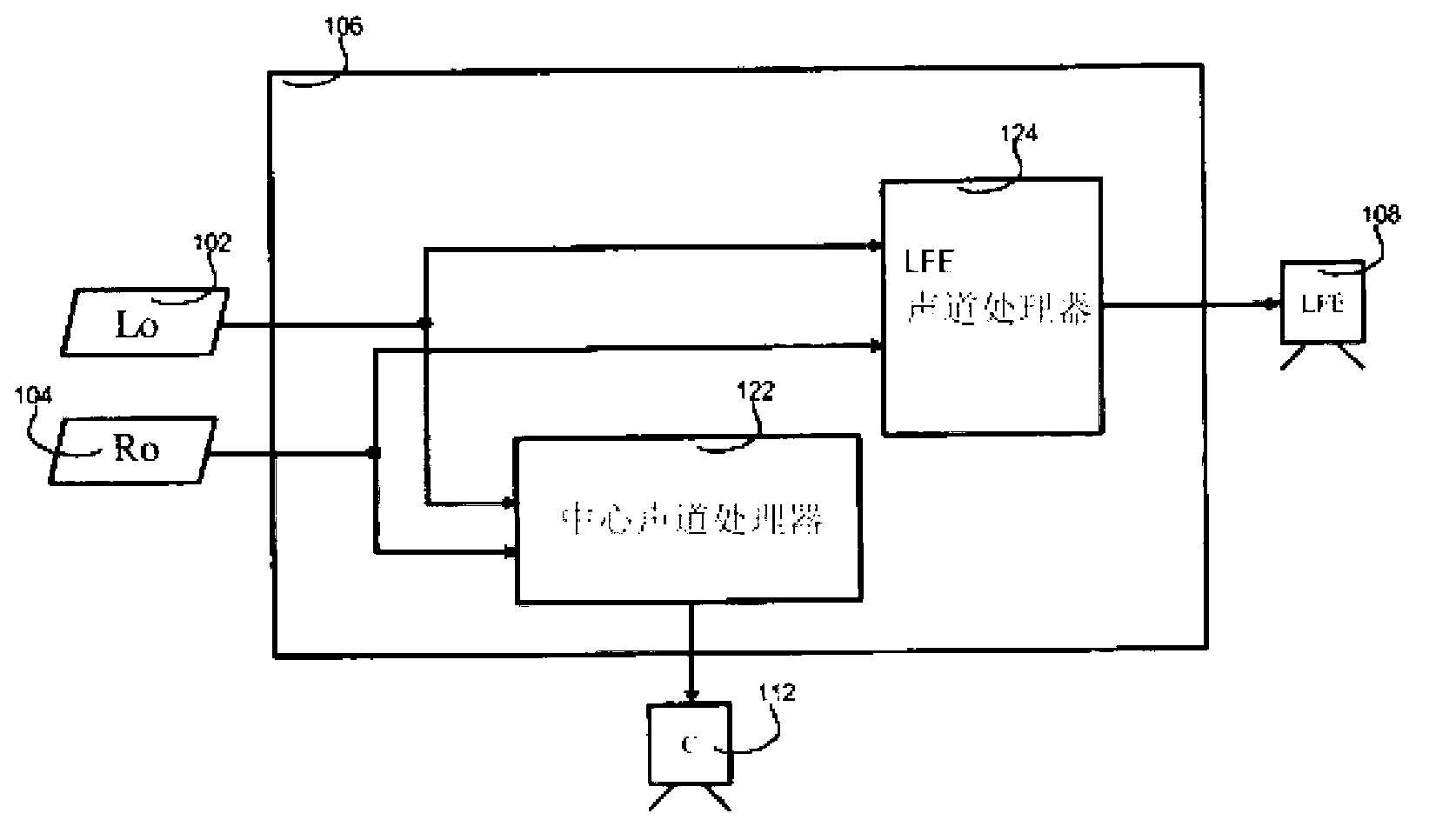
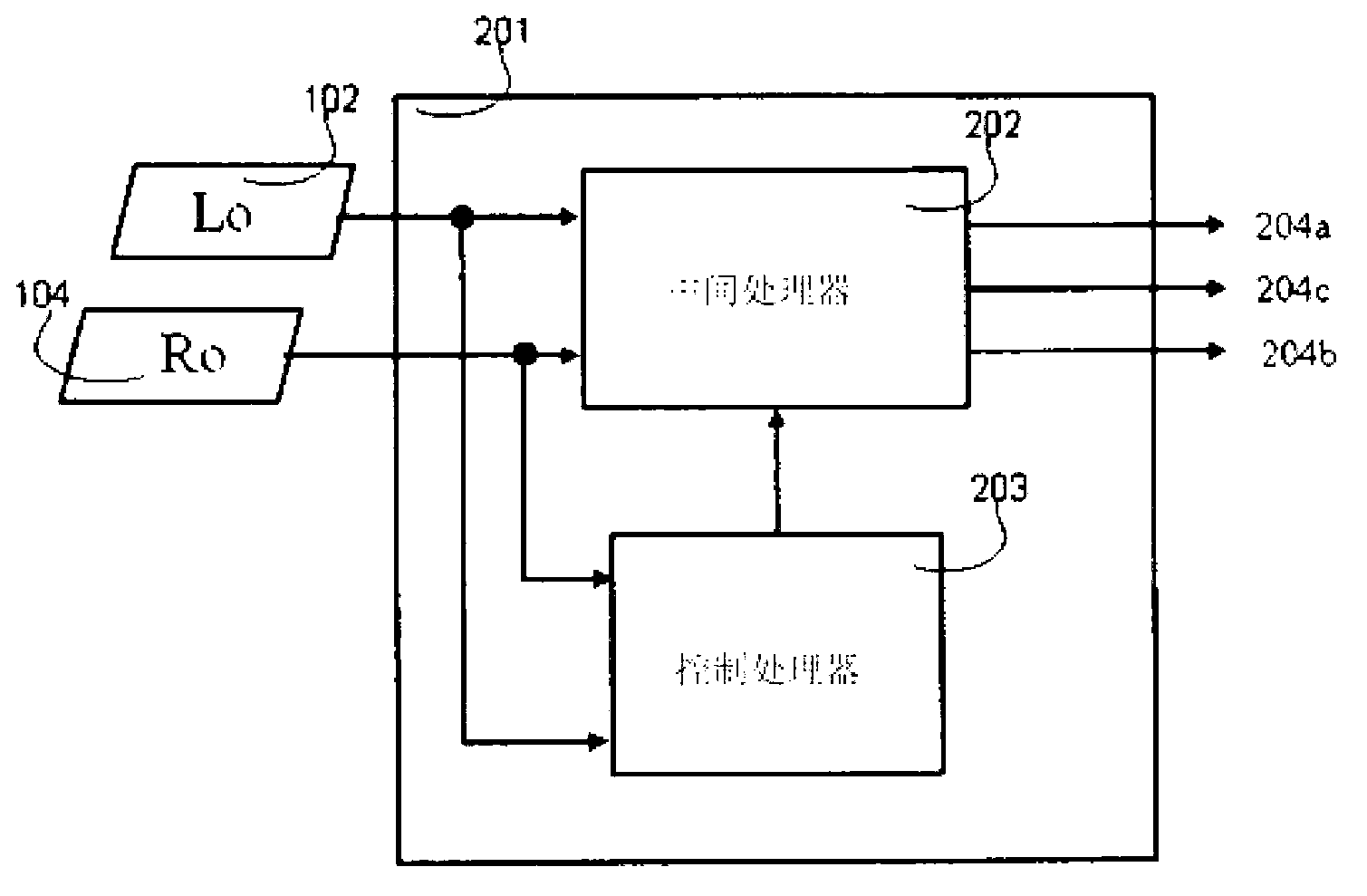
Upmixing method and system for multichannel audio reproduction
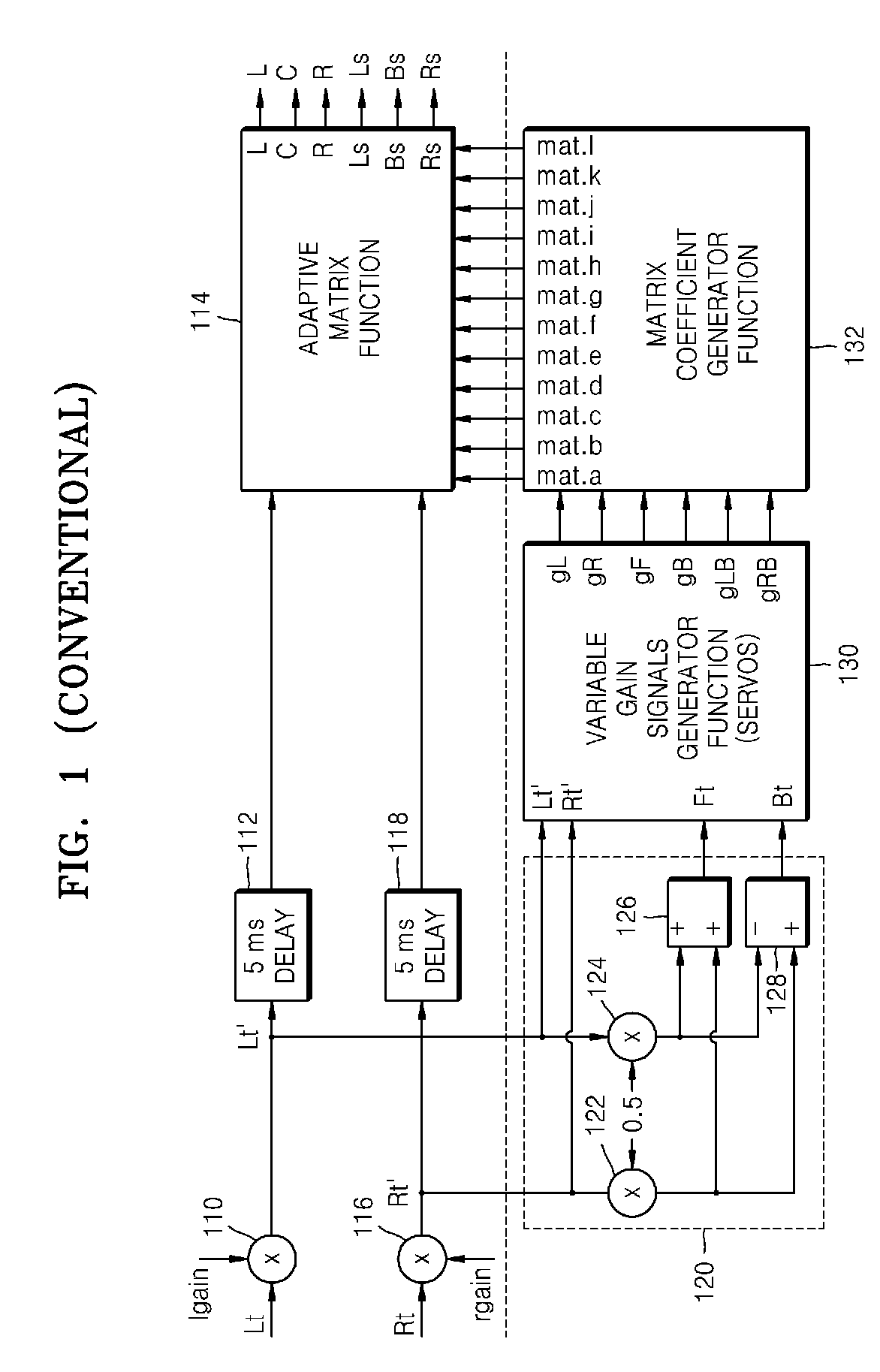
An audio signal enhancing device, and a corresponding method of enhancing stereophonic signals, is provided which generates an enhanced signal with improved spatial sound image quality for upmixing a stereophonic input signal. When used in combination with a centre channel processor or LFE processor, an improved processing of the input signals is provided resulting in final centre channel and at least one LFE sub-woofer channel wherein the problems and disadvantages of the prior art are resolved. The result is a centre and LFE signal that contains a stable, non time-smeared image with a high quality natural-sounding fidelity. These advantages are achieved especially for time-delayed or phase-panned stereo input signals, independently of whether they are matrix encoded or non-matrix encoded input signals.
Owner:DOLBY INTERNATIONAL AB
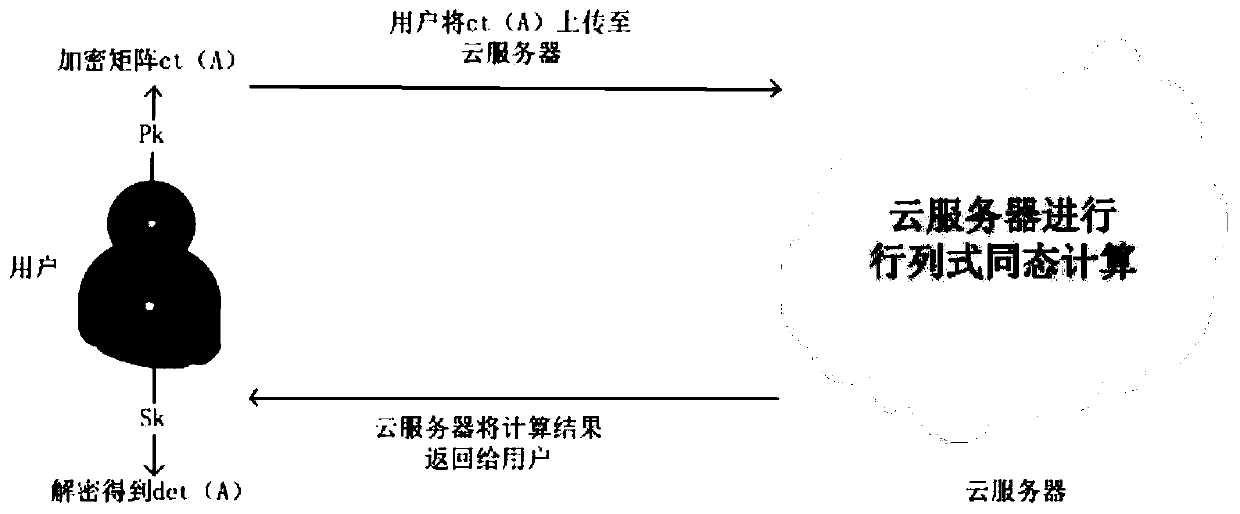
Homomorphic encryption matrix determinant security outsourcing method based on cloud computing
ActiveCN110324135AReduce the amount of calculationReduce the number of operationsCommunication with homomorphic encryptionComplex mathematical operationsCiphertextWorkload
The invention discloses a homomorphic encryption matrix determinant security outsourcing method based on cloud computing, which is characterized in that the whole matrix is encoded and encrypted intoa ciphertext by applying matrix encoding technology, and efficient matrix determinant security outsourcing computation is realized in combination with a division-free determinant computation method. The method comprises a data encryption / decryption method and a homomorphic calculation method. A client side executes the encryption method, codes, encrypts and uploads the matrix to a cloud server. Acloud server side executes a homomorphic calculation method, carries out ciphertext operation under the condition of not decrypting, and returns a calculation result to the client side in a ciphertextform. Finally, the client side executes the decryption module to obtain the determinant value of the matrix. Most calculation is carried out at the cloud server side, so that calculation workload ofthe client side is greatly reduced.
Owner:ZHEJIANG SCI-TECH UNIV
Wireless communication system, wireless communication apparatus and wireless communication method, encoding apparatus and encoding method, and computer program
InactiveUS20100020891A1Improve transmission performanceSecret communicationChannel estimationCommunications systemDecomposition
A wireless communication apparatus includes: plural antennas; a channel matrix acquiring unit acquiring a channel matrix for each sub-carrier; a channel matrix encoding unit encoding the acquired channel matrix of each sub-carrier, by decomposition from signals in fixed-point representation into data and amplitude parts with a predetermined bit width; and a channel matrix information delivery unit delivering the encoded channel matrix information to a communication party. The encoding unit retrieves a first maximum value as the maximum of channel matrix elements in all sub-carriers, in plural levels, and determines an amplitude part and a normalization coefficient for normalizing channel matrix elements to a data part having the predetermined bit width, based on a ratio between a second maximum value as the maximum of channel matrix elements with respect to each sub-carrier and the first maximum value, and multiples channel matrix elements by the normalization coefficient to obtain a data part.
Owner:SONY CORP
Tool magazine central management system for automatic production line and application method thereof
InactiveCN102581676AImprove clamping efficiencyEasy to managePositioning apparatusMetal-working holdersProduction lineSystems management
The invention provides a tool magazine central management system for an automatic production line and an application method of the tool magazine central management system. The system comprises a tool magazine integrally provided with various tools, multiple lathes respective for processing in special processes, a tool conveying device for connecting the tool magazine with multiple lathes, a controller for obtaining request information from the lathe and controlling to convey the tools from the tool magazine to the lathe by the cutter conveying device, and multiple exchanging operating platforms for shifting among different lathes. In the management system provided by the invention, the tools for all the lathes on the production line are collected into a tool magazine in order to achieve convenient management; the clamping efficiency of the tool can be raised by the streamlined exchanging operating platforms; and the lathes, the tool magazine and the exchanging operating platforms are managed in a centralized manner by a matrix encoding management mode, thus improving the efficiency on system management as well as improving the reliability of each link.
Owner:SANY GRP
A method and apparatus for encoding and decoding data using low density parity check code in a wireless communication system
A method of encoding data using low density parity check (LDPC) code defined by a mxn parity check matrix is disclosed. More specifically, the method includes encoding input source data using the parity check matrix, wherein the parity check matrix comprises a plurality of zxz sub-matrices of which row weights and column weights are ''0'' or ''1 ''.
Owner:LG ELECTRONICS INC
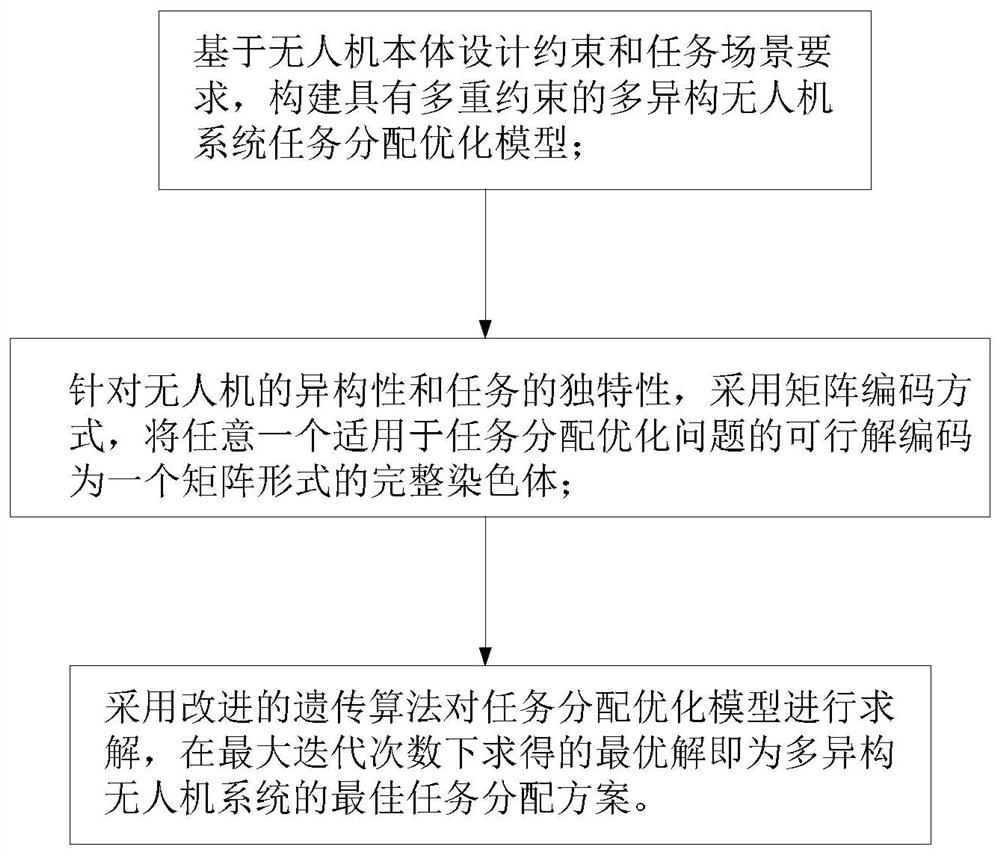
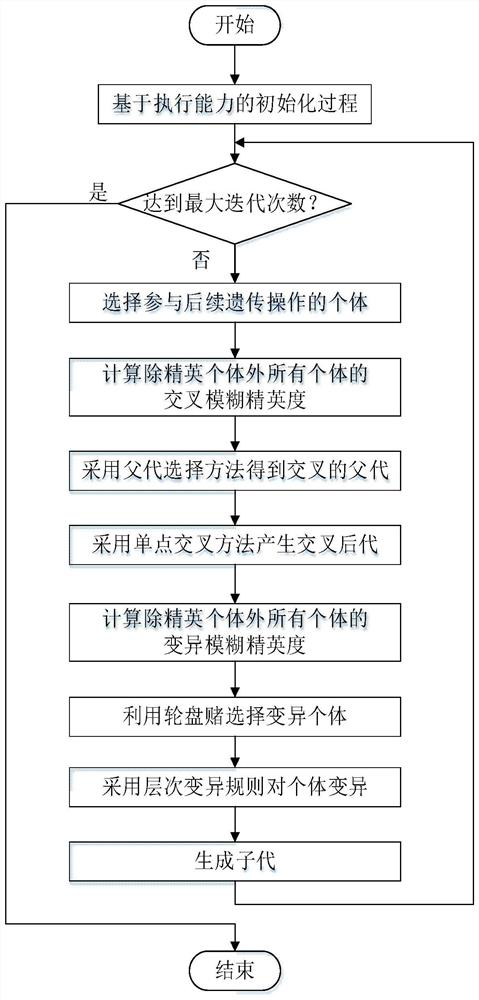
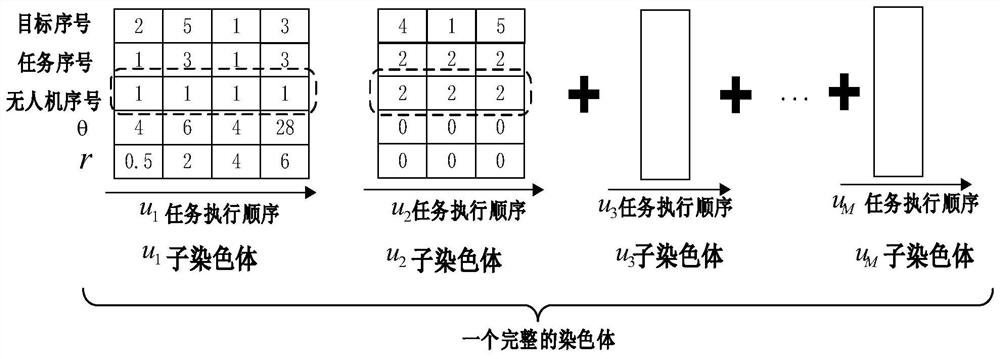
Multi-heterogeneous unmanned aerial vehicle task allocation method based on improved genetic algorithm
ActiveCN111860984AFast convergenceImprove work efficiencyInternal combustion piston enginesForecastingAlgorithmGenetics algorithms
The invention discloses a multi-heterogeneous unmanned aerial vehicle task allocation method based on an improved genetic algorithm, and belongs to the technical field of unmanned aerial vehicles. Themethod is characterized by establishing a task allocation optimization model by comprehensively considering multiple constraints such as resource consumption, task completion effect and load balancing, resource limitation and task priority; and encoding each feasible task allocation scheme into a complete chromosome by adopting a matrix encoding mode. Aiming at the problems that an existing genetic algorithm is insufficient in solving precision and too slow in solving speed, the concept of fuzzy elitibility is provided, all genetic operations are improved on the basis, the built optimizationmodel is solved through the improved genetic algorithm, and an optimal task allocation scheme is obtained within limited iteration times. The method has good universality in the field of multi-agent cooperative control, has the advantages of high solving speed and high solving precision, and can effectively solve the task allocation problem of a multi-heterogeneous unmanned aerial vehicle system with multiple constraints.
Owner:河北梓墨电子科技有限公司
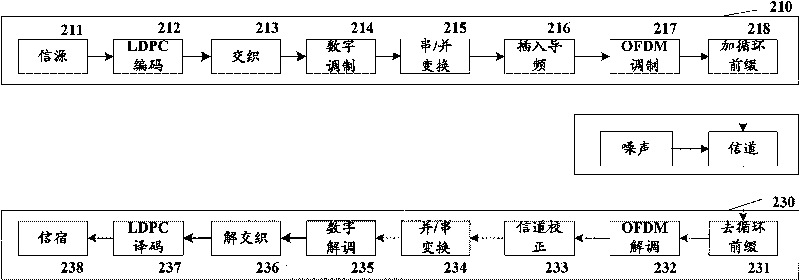
QC-LDPC codes and system and method applied thereof
InactiveCN101753263ASimple structureGood error correction performanceError preventionMulti-frequency code systemsEngineeringLow density
The invention provides QC-LDPC codes and a system and a method applied thereof. The system comprises a transmitting system and a receiving system. The transmitting system conducts quasi-cycle low-density parity check (QC-LDPC) matrix coding to input information, orthogonal frequency division multiplexing modulation is conducted to the QC-LDPC coded information and modulating signals are transmitted through a transmitter. The receiving system receives signals transmitted by the transmitting system, demodulation is conducted to orthogonal frequency division multiplexing signals first and then QC-LDPC matrix decoding is conducted to obtain the transmitted information data. The invention has the advantages that the structure of the system is simple, the error code correction performance is high, the system can adapt to the high-speed data transmission technology in the multi-path environment and frequency selectivity fading channel and the mobile receiving function is improved.
Owner:ACAD OF BROADCASTING SCI SARFT
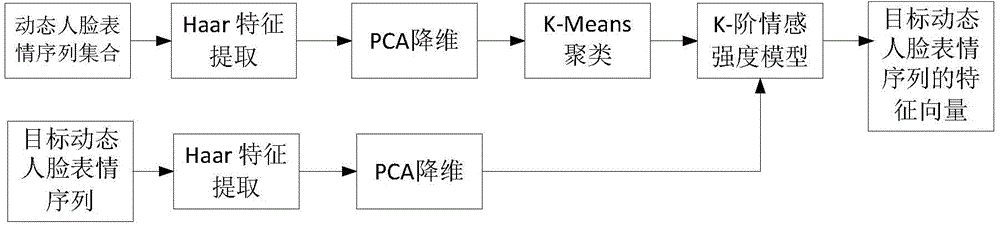
Feature representation method based on dynamic facial expression sequence and K-order emotional intensity model
InactiveCN104156708AReduce computational complexityReduce feature dimensionCharacter and pattern recognitionComputation complexityDimensionality reduction
The invention discloses a feature representation method based on a dynamic facial expression sequence and a K-order emotional intensity model. The method is characterized in that the method comprises the steps of (1) extracting a Haar feature in a dynamic facial expression sequence set and carrying out feature dimensionality reduction by using PCA, (2) taking each column of a feature matrix which is subjected to dimensionality reduction as a clustering sample and carrying out K-Means clustering, obtaining the mean and variance of all features in each class, constructing the normal distribution of each class, and generating a K-order emotional intensity model, (3) extracting the Haar feature in a dynamic facial expression sequence to be extracted and then carrying out feature dimensionality reduction by using the PCA, (4) inputting the feature which is subjected to the dimensionality reduction into the K-order emotional intensity model and obtaining an output matrix, and (5) encoding the output matrix to obtain an encoding result which is the feature representation of dynamic facial expression sequence to be extracted. According to the method, the feature dimensionality and computation complexity can be effectively reduced, and the real-time performance of feature extraction is improved.
Owner:HEFEI UNIV OF TECH
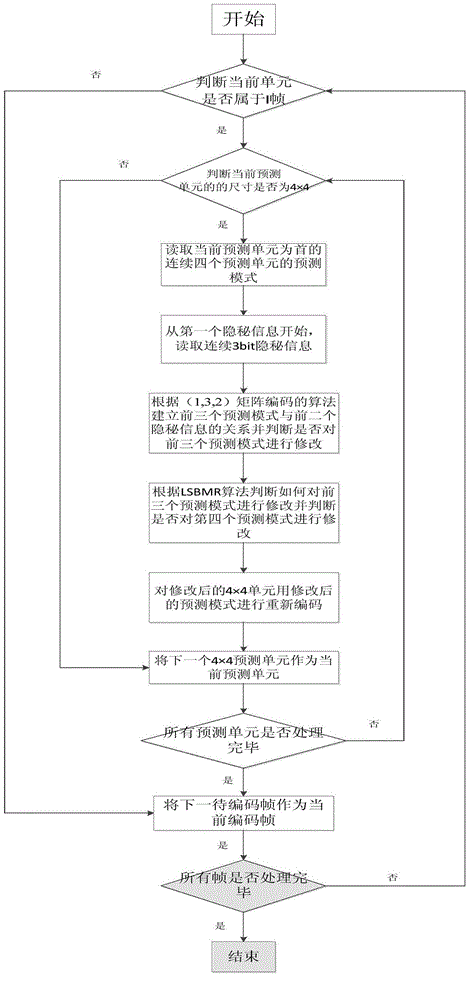
Hamming code plus one-based information hiding method of HEVC video
ActiveCN104902281AGuarantee subjective and objective qualityReduce the impact of quality degradationDigital video signal modificationHamming codeVideo bitstream
The invention discloses a hamming code plus one-based information hiding method of an HEVC video. The method comprises the steps as follows: using a (1, 3,2 ) matrix encoding algorithm in steganography code to combine with an LSBMR algorithm to form a hamming code plus one algorithm, modifying a prediction mode according to three-bit secret information to be embedded to finish information embedding, embedding the three-bit secret information in four continuous 4X4 intra-frame luminance blocks. The hamming code plus one-based information hiding method of the invention not only ensures hiding capacity, but also reduces the impact that the video quality is reduced because of modifying the prediction mode to ensure the subjective and objective quality of the video well, and greatly reduces the impact of embedded secret information to a video bitstream. By analyzing an HEVC coding and decoding structure, modulating the predication node in an intra-frame prediction coding process as the predication node which meets an embedding condition and whose rate-distortion cost is the smallest in terms of a predication unit whose size is 4 plus 4, and using a Lagrange rate-distortion mode to adaptively select the type of the prediction unit of the coding unit, the secret information hiding manner could well ensure the subjective and objective quality of the video.
Owner:NINGBO UNIV
Method for encoding/decoding signals with multiple descriptions vector and matrix
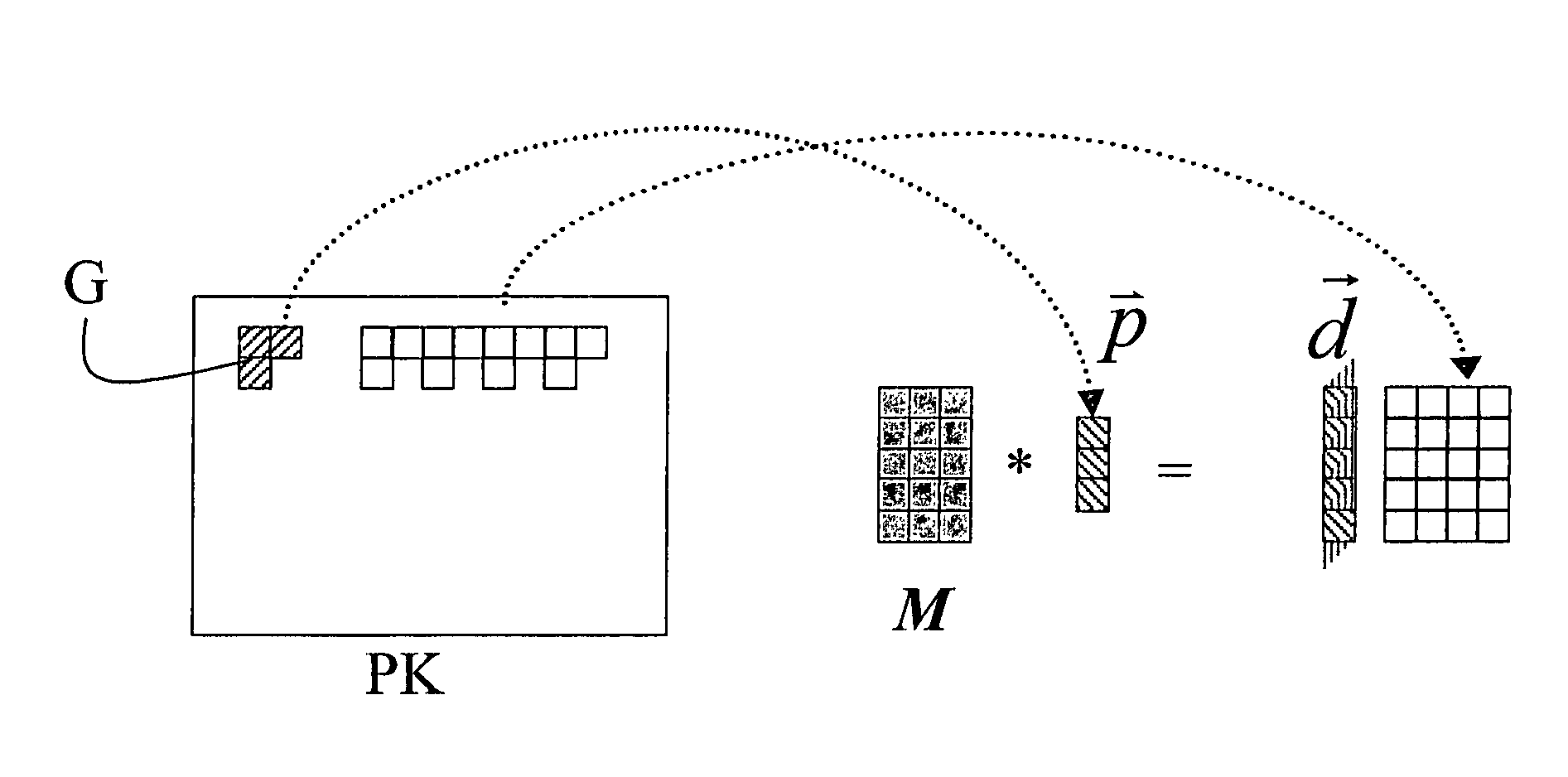
ActiveUS7961790B2Easy to implementColor television with pulse code modulationColor television with bandwidth reductionAlgorithmMultiple description
The method for encoding and / or decoding video signals, includes the operations of generating at a transmitter side a multiple descriptions vector associated to a pixel values vector of the video signals and decoding at a receiver side available descriptions vector for reconstructing the pixel values vector. The operation of generating a multiple descriptions vector includes the steps of obtaining the pixel values vector by selecting a group of pixels in a picture of the video signal and applying an encoding matrix to the pixel values vector. The decoding operation includes the step of applying a decoding matrix that is in an inverse relationship with the encoding matrix to the available descriptions vector to obtain the pixel values vector.
Owner:STMICROELECTRONICS SRL
Construction method for multi-code low density verification LDPC code with fixed code length
ActiveCN105577194ASimple structureEasy to implementError correction/detection using multiple parity bitsCode conversionTheoretical computer scienceLow density
The invention discloses a construction method for a multi-code rate low density verification LDPC code with a fixed code length, comprising steps of determining the number N of columns of a circulation coefficient array C according to a maximum bitrate of the multi-rate LDPC code to be constructed, choosing a prime number P greater than the column number N, determining the size L of a circulation replacement array and the code length n, constructing a limited domain according to the prime number, choosing a primitive element alpha on a limited domain to determine the circulation coefficient array Ck, utilizing an optimized algorithm to determine that the R is equal to three mask matrixes Bk of the LDPC code with various rate Rk, determining a basic matrix Dk of each code rate according to the circulation coefficient matrix Ck and the mask matrix Bk of each code rate, determining a check matrix Hk of the LDPC code of each code rate according to the basic matrix, and finally obtaining a group of check matrixes of the multi-rate LDPC code. Compared with the prior art, the code length of the constructed multi-rate LDPC code is fixed, and the invention can directly use the check matrix to perform coding, is easy to realize the hardware and is applicable to the satellite communication system and the cellular system.
Owner:XIDIAN UNIV
System and method for reducing frenquency breadth need of transmitting graph data
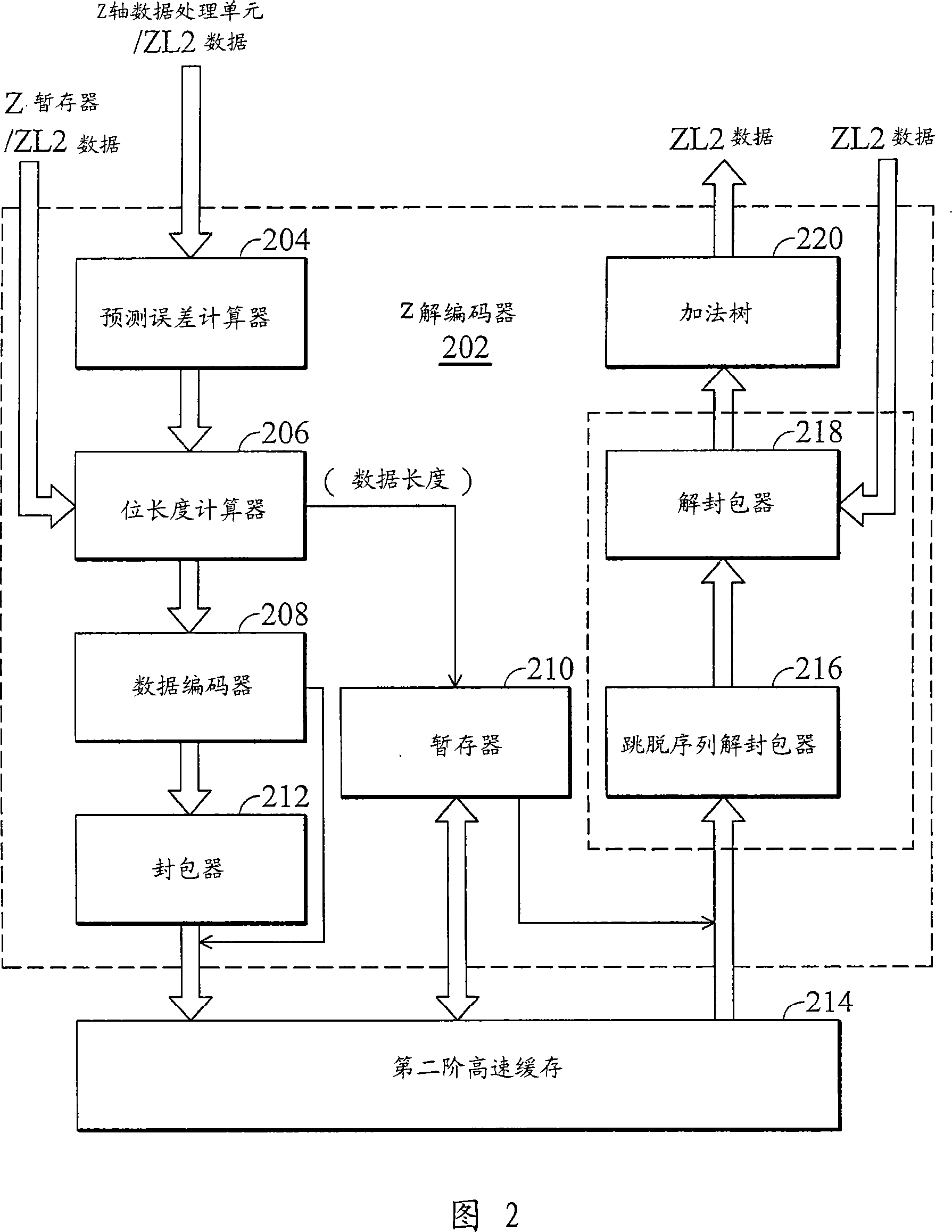
Various embodiments for reducing external bandwidth requirements for transferring graphics data are included. One embodiment includes a system for reducing the external bandwidth requirements for transferring graphics data comprising a prediction error calculator configured to generate a prediction error matrix for a pixel tile of z-coordinate data, a bit length calculator configured to calculate the number of bits needed to store the prediction error matrix, a data encoder configured to encode the prediction error matrix into a compressed block and a packer configured to shift the compressed block in a single operation to an external memory location.
Owner:VIA TECH INC
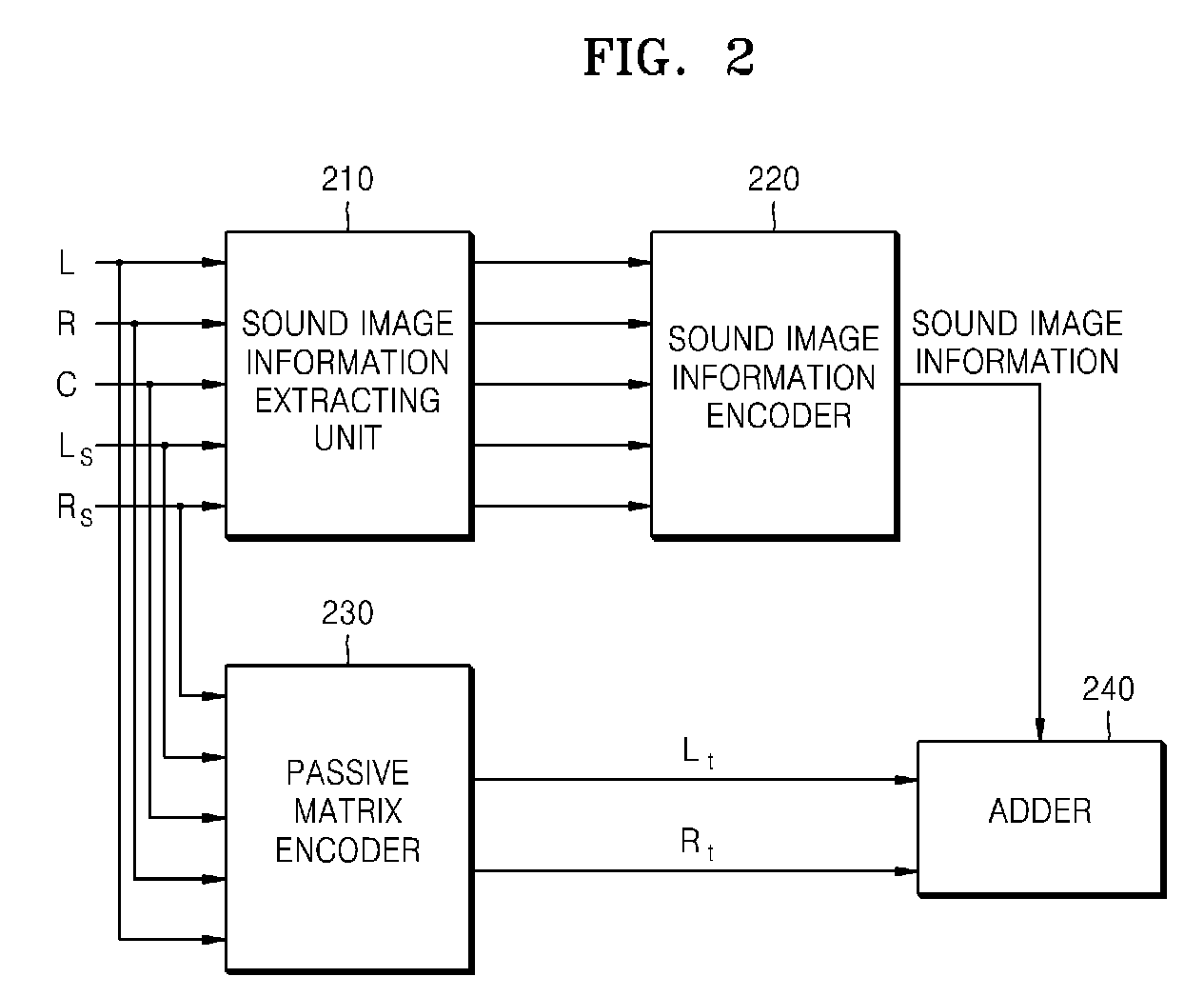
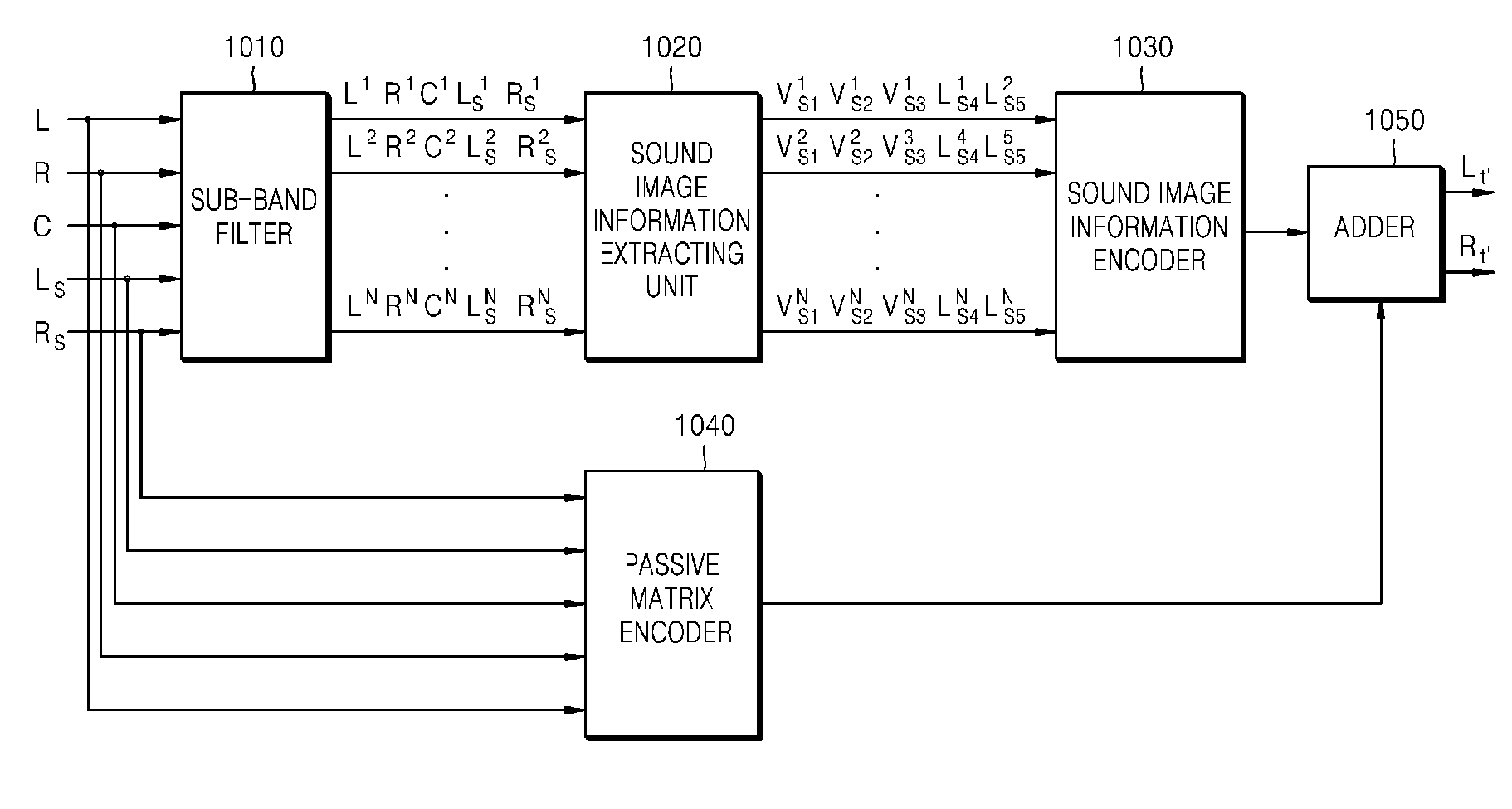
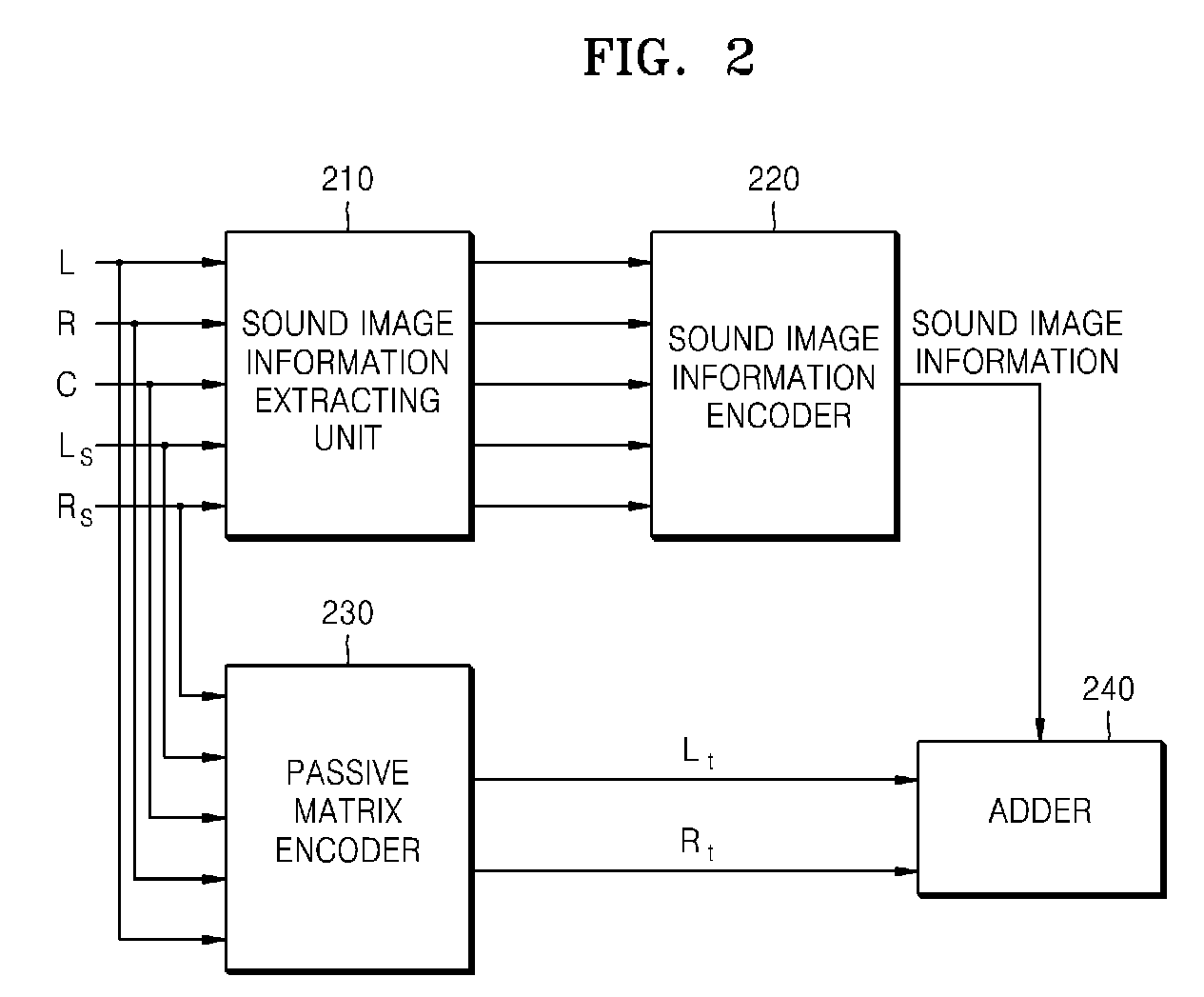
Method and apparatus of audio matrix encoding/decoding
InactiveUS20090164225A1Restoring movementEnhance channel separationGain controlSpeech analysisSound imageVocal tract
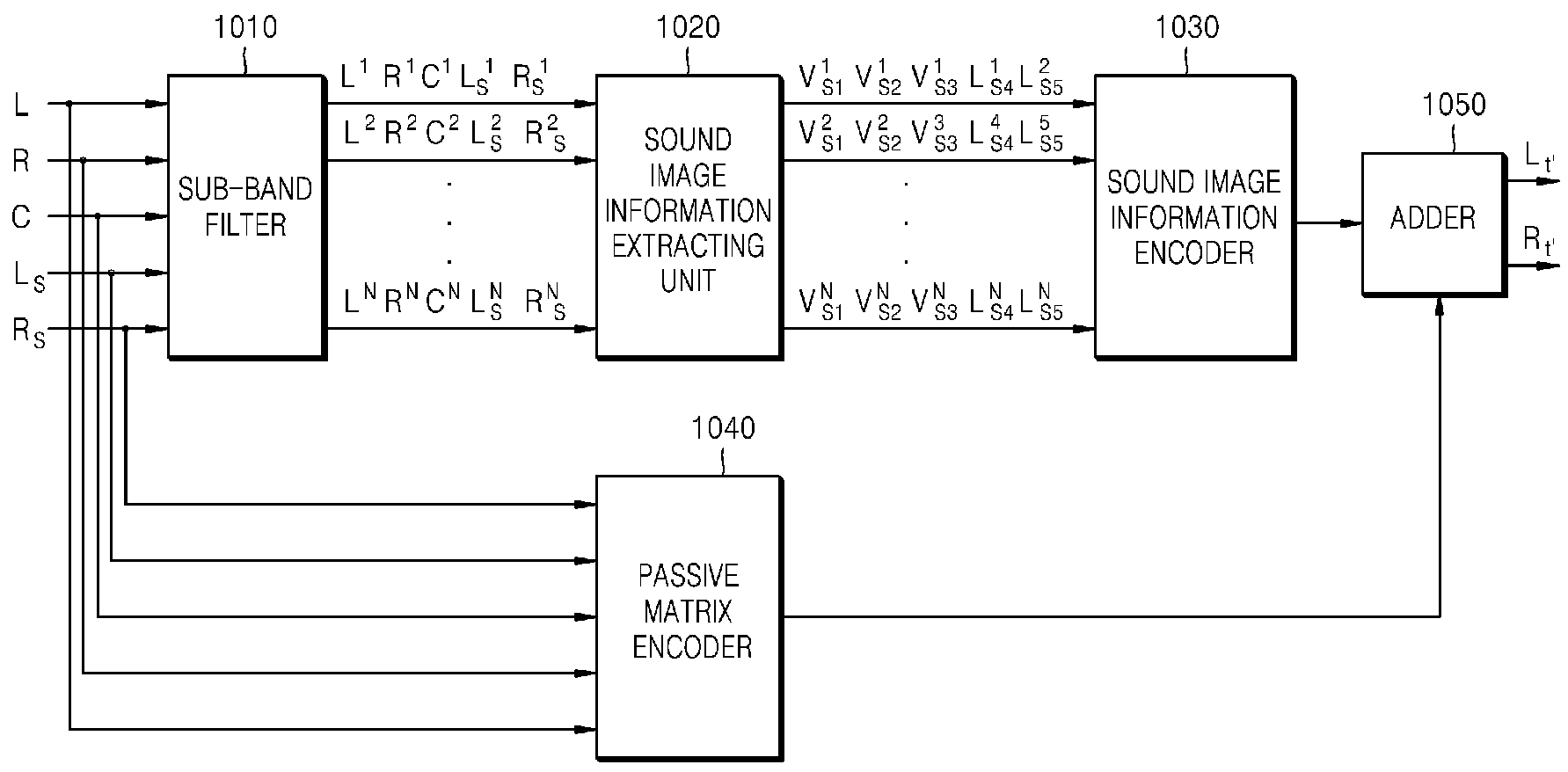
A method to audio matrix encode / decode, which encode and decode audio signals of two or more channels into an audio signal of one or more channel while preserving the direction of a sound image includes extracting pieces of sound image information from audio signals of multi channels, encoding and allocating the extracted sound image information to an inaudible frequency domain except an audible frequency domain, and adding the sound image information allocated to the inaudible frequency domain and matrix-encoded stereo signals of the audible frequency domain.
Owner:SAMSUNG ELECTRONICS CO LTD
Calibration plate and calibration method
PendingCN112184825AAvoid the problem of reading data errorsProblems causing read data errorsImage analysisGraphicsCode generation
The invention discloses a calibration plate and a calibration method using the calibration plate. The calibration plate comprises: a substrate; a feature pattern which is printed on the surface of thesubstrate and is provided with a plurality of feature points; a positioning reference pattern unit printed on the substrate and surrounded by the feature pattern, wherein the positioning reference pattern unit comprises a static area; a orientation frame which is embedded in the static area; a central block which is positioned in the center of the inner region of the orientation frame and is positioned at any feature point in the feature pattern; and a coding matrix which is positioned in the internal region of the orientation frame and records the set coordinates of the central block. According to the calibration board and the calibration method, the positioning reference graphic unit containing the direction information and the index coordinate information is embedded into the characteristic pattern of the calibration board, the calibration board adopting a two-dimensional code for calibration is replaced, and the cost required by adopting two-dimensional code generation software issaved.
Owner:HANGZHOU HIKROBOT TECH CO LTD
Method and apparatus of audio matrix encoding/decoding
InactiveUS8407059B2Effectively restore movementEasy to separateGain controlSpeech analysisSound imageVocal tract
A method to audio matrix encode / decode, which encode and decode audio signals of two or more channels into an audio signal of one or more channel while preserving the direction of a sound image includes extracting pieces of sound image information from audio signals of multi channels, encoding and allocating the extracted sound image information to an inaudible frequency domain except an audible frequency domain, and adding the sound image information allocated to the inaudible frequency domain and matrix-encoded stereo signals of the audible frequency domain.
Owner:SAMSUNG ELECTRONICS CO LTD
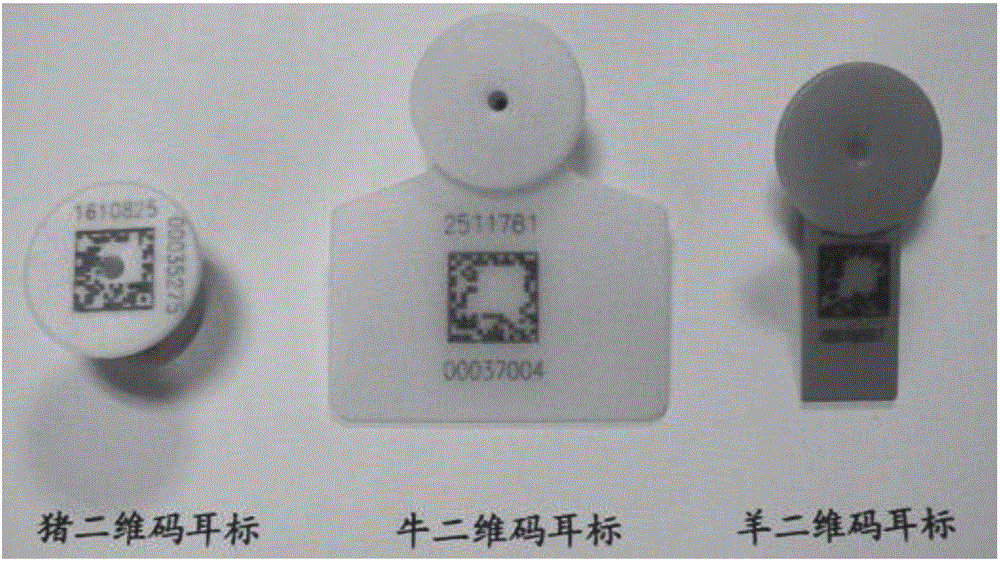
Animal ear tag matrix encoding identification method and device
InactiveCN106709487AAchieve readingRealize point-and-shootCharacter and pattern recognitionAnimal husbandryEar tagMatrix encoding
The invention discloses an animal ear tag matrix encoding identification method and device, and relates to the technical field of computers. The method comprises the following steps of: obtaining an image of an encoding region of animal tags; carrying out white-black binary processing on the image of the encoding region; determining the number of lines and number of rows of an encoding matrix in the encoding area after the binary processing by utilizing a protection segmentation algorithm; carrying out grid generation on the encoding region according to the determined number of lines and number of rows; and decoding the encoding matrix according to pixel values of pixel points in each grid, and identifying information of animals included in the encoding matrix. According to the method, the images of the encoding region of the animal tags is acquired, and the encoding matrix of the encoding region is divided and decoded by utilizing the projection segmentation method, so that the reading of animal tag matrix codes is realized; and the method is strong in university, is suitable for various devices capable of acquiring and processing images, is simple and convenient to apply, and can carry out real-time decoding to realize decoding during shooting.
Owner:ZHENGJIANG PUBLIC INFORMATION
SPDMD-based power system oscillation mode and modal identification method
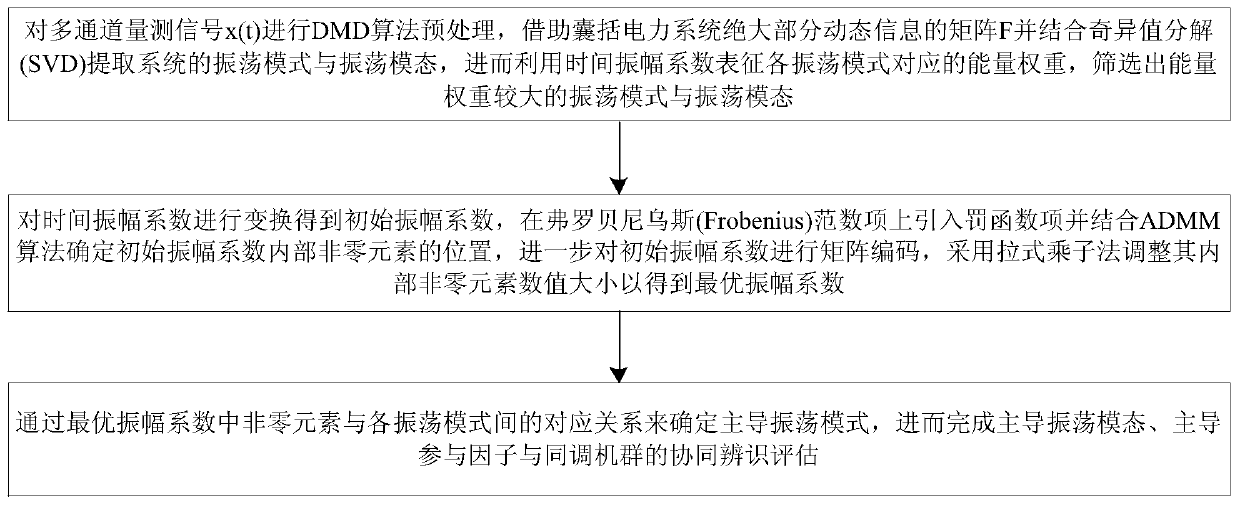
ActiveCN110311392ARich oscillation informationImprove real-time monitoring capabilitiesPower oscillations reduction/preventionData sequencesComputer science
The invention discloses a SPDMD-based power system oscillation mode and modal identification method comprising the steps: the energy weight corresponding to each oscillation mode is represented by thetime amplitude coefficient and the oscillation mode and the oscillation modal of high weight are selected out; a matrix formed by the previous N-1 columns of measurement data sequences is converted to calculate the initial amplitude coefficient, the penalty function term is introduced into the Frobenius norm term and the position of the non-zero elements in the initial amplitude coefficient is determined by ADMM, matrix encoding is performed on the initial amplitude coefficient and the value size of the non-zero elements in the initial amplitude coefficient is adjusted by using a pull multiplier method so as to obtain the optimal amplitude coefficient; and the dominant oscillation mode is determined by the correspondence between the non-zero elements in the optimal amplitude coefficient and each oscillation mode, and the collaborative identification and evaluation of the dominant oscillation mode, the dominant participation factor and the homology cluster are completed. The oscillation mode and modal identification of the power system can be realized, and the defect that the DMD algorithm cannot determine the number of the dominant oscillation mode can be overcome.
Owner:NORTHEAST DIANLI UNIVERSITY
Image steganography method and system for automatically learning distortion based on GAN network structure
ActiveCN112767226ANarrow down the search spaceReduce training timeInternal combustion piston enginesImage codingPattern recognitionGenerative adversarial network
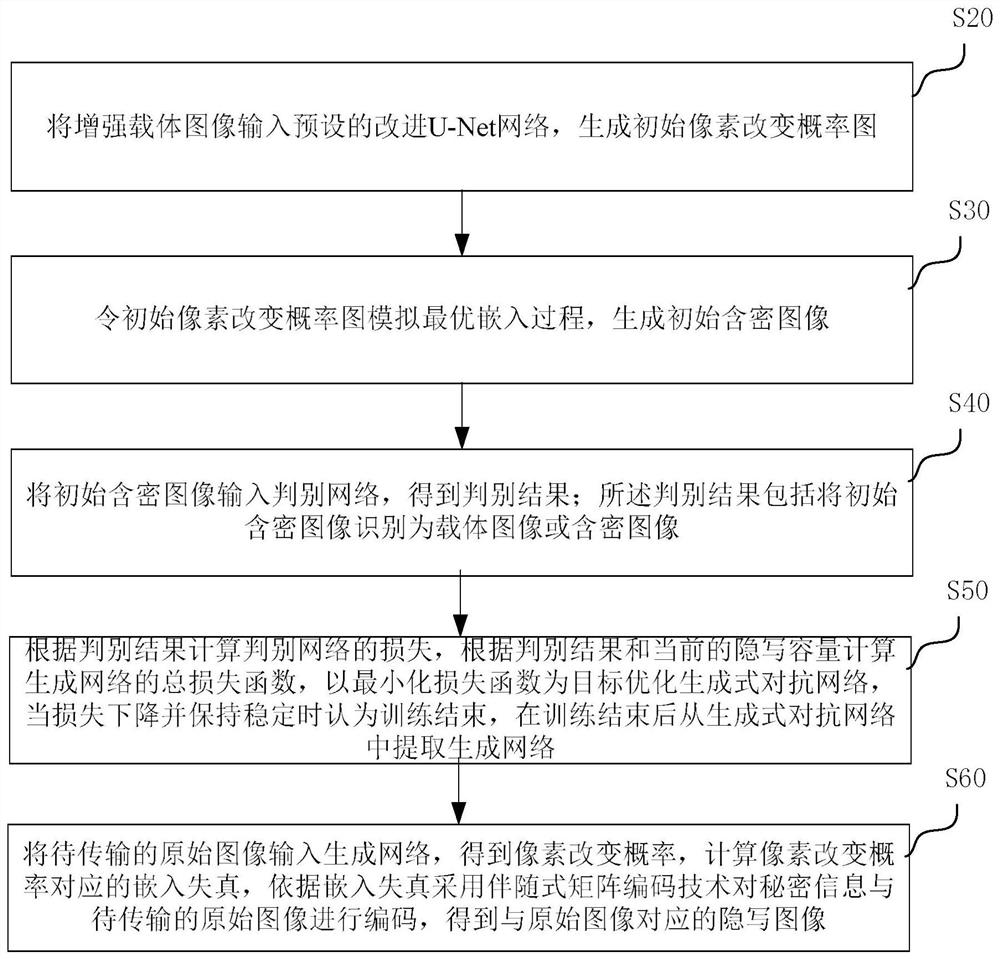
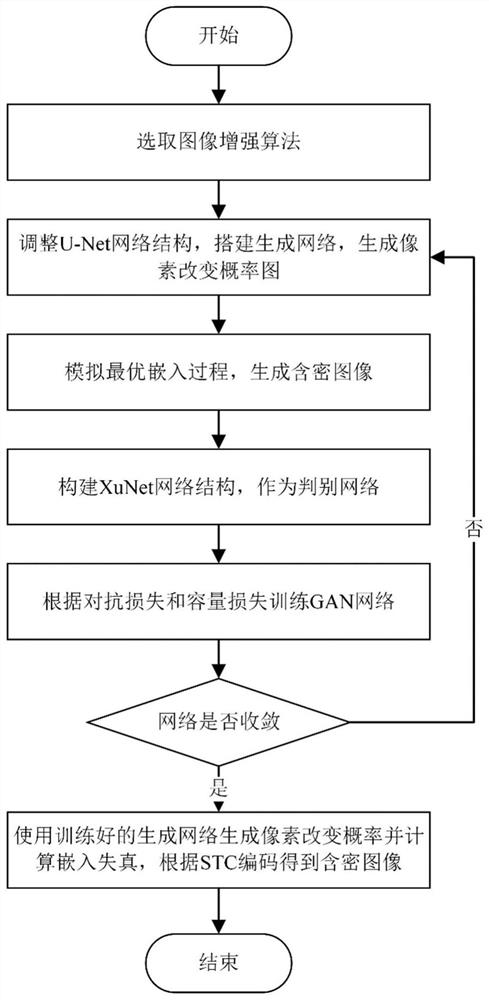
The invention discloses an image steganography method and system for automatically learning distortion based on a GAN network structure, and the method comprises the steps: inputting an enhanced carrier image into a preset improved U-Net network, sequentially generating an initial pixel change probability graph and an initial secret-containing image, inputting the initial secret-containing image into a discrimination network, and obtaining a discrimination result, calculating the loss of the discrimination network according to the discrimination result, calculating a total loss function of the generative network according to the discrimination result and the current steganography capacity, optimizing the generative adversarial network by taking minimization of the loss function as a target, when the loss is reduced and kept stable, considering that the training is ended, extracting the generative network from the generative adversarial network after the training is ended, and inputting a to-be-transmitted original image into the generative network to obtain a pixel change probability, calculating embedded distortion corresponding to the pixel change probability, and coding the secret information and the to-be-transmitted original image by adopting a syndrome matrix coding technology according to the embedded distortion to obtain a steganographic image corresponding to the original image.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
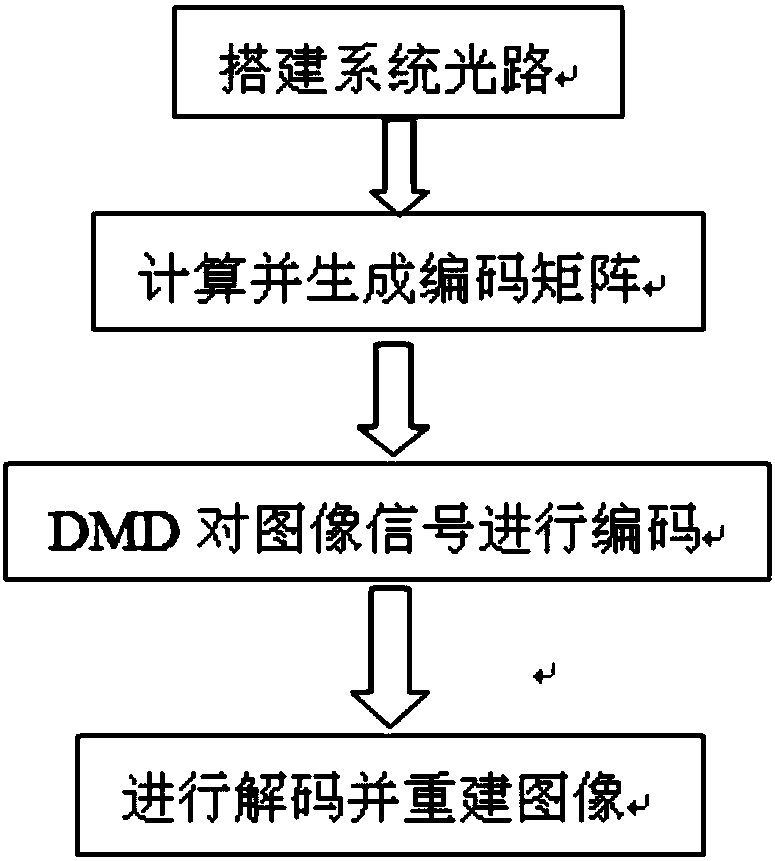
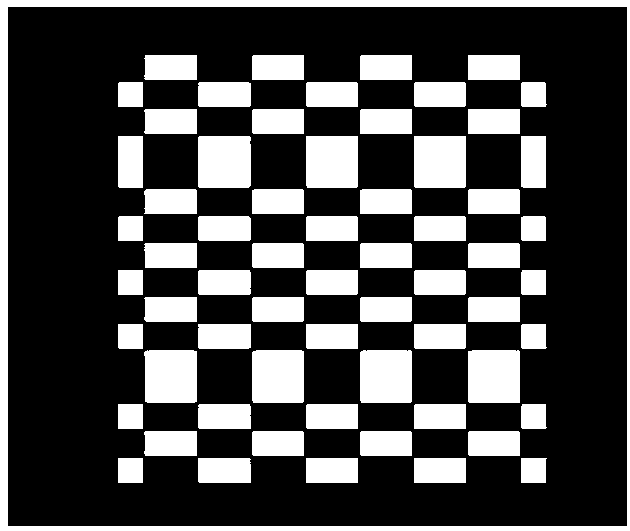
Full Hadamard matrix coding imaging method
ActiveCN108616686AUnrealizableTurn up the signal-to-noise ratioTelevision system detailsColor television detailsSignal-to-noise ratio (imaging)Algorithm
The invention provides a full Hadamard matrix coding imaging method. Two elements such as +1 and -1 in a Hadamard matrix are respectively extracted through matrix operations, the Hadamard matrix is divided into a Hadamard positive matrix and a Hadamard negative matrix which can be realized in an optical path, and image signals are coded by using the Hadamard positive matrix and the Hadamard negative matrix; and subtraction is performed between a measured value obtained by the coding of the Hadamard positive matrix and a measured value obtained by the coding of the Hadamard negative matrix in decoding, and then an image is reconstructed through matrix operations. The method realizes the Hadamard matrix in optical path modulation and greatly improves the imaging sensitivity and signal-to-noise ratio.
Owner:NANJING UNIV OF SCI & TECH
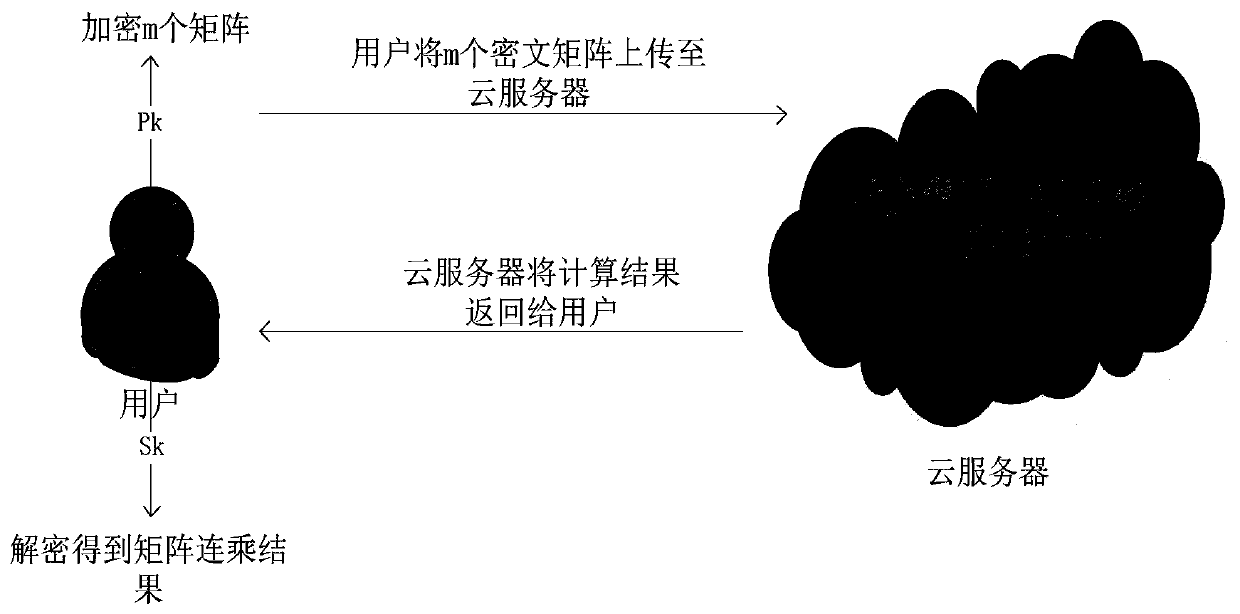
Homomorphic encryption matrix continuous multiplication safety outsourcing method based on cloud computing
ActiveCN111064558AImprove computing efficiencyReduce the amount of calculationCommunication with homomorphic encryptionComplex mathematical operationsCiphertextParallel computing
The invention discloses a homomorphic encryption matrix continuous multiplication safety outsourcing method based on cloud computing, and belongs to the technical field of homomorphic encryption. Themethod comprises the following steps that: encryption is performed at a client, encoding and encrypting is carried out on a matrix and the matrix is uploaded to a cloud server; the cloud server executes homomorphic calculation, carries out ciphertext matrix continuous multiplication operation under the condition that decryption is not carried out, and returns a calculation result to the client side in a ciphertext form; and finally, the client executes a decryption module to obtain a value of matrix continuous multiplication. The matrix continuous multiplication calculation task can be outsourced to the cloud server under the condition that matrix elements, namely client private data, are not leaked, so that the security of client data is protected, and the calculation amount of the clientis reduced. The matrix is encoded into a ciphertext for operation, so that the space complexity is remarkably reduced, the ciphertext operation frequency is reduced, and the purpose of improving theefficiency is achieved.
Owner:ZHEJIANG SCI-TECH UNIV
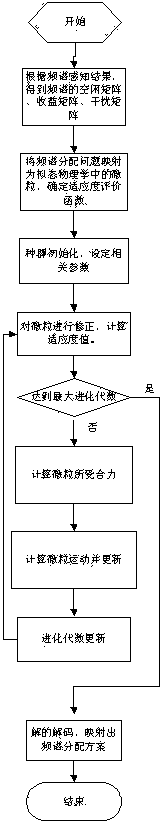
Artificial physics optimization cognitive radio network spectrum distribution method
InactiveCN104168572AFew parametersFast convergenceBiological modelsNetwork planningDistribution matrixFrequency spectrum
The invention relates to an artificial physics optimization cognitive radio network spectrum distribution method for solving the problem that the spectrum distribution efficiency is low in the prior art. The realization steps are: (1) obtaining an idle matrix, an income matrix, and a disturbance matrix of the spectrum, (2) mapping a spectrum distribution matrix encoding as a particle in the artificial physic optimization and determining a fitness evaluation function, (3) initializing population and setting related parameters, (4) correcting particles and calculating fitness value, (5) determining whether latest evolution generations is achieved, if yes, mapping the optimal particle encoding as a spectrum distribution matrix type to obtain the optimal spectrum distribution matrix, if not, switching to the step (6) to calculate the composite force of each particle, (7) calculating the particle motion and updating, and (8) switching to the step (4) if the evolution generations is increased. The artificial physic method adopted by the invention has advantages of less in parameters and quick in rate of convergence, and can better realize the maximum of the network income.
Owner:TIANJIN POLYTECHNIC UNIV +5
Error compensation method of absolute code disc in matrix encoding manner
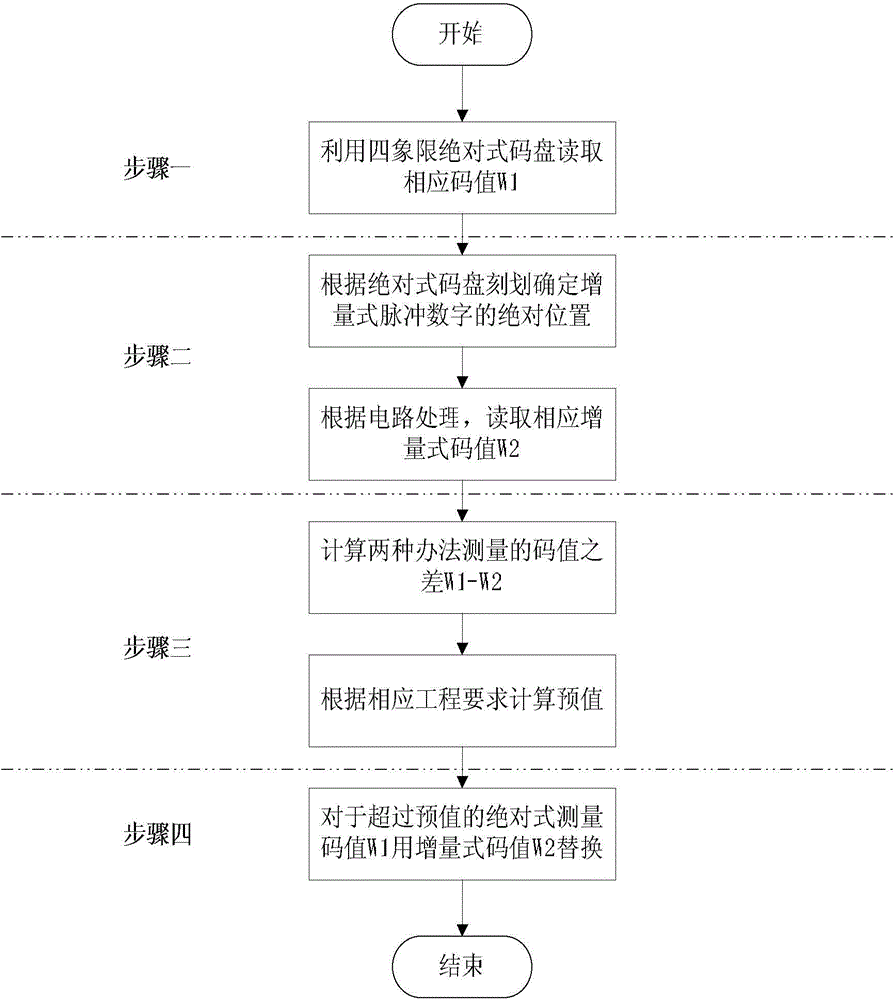
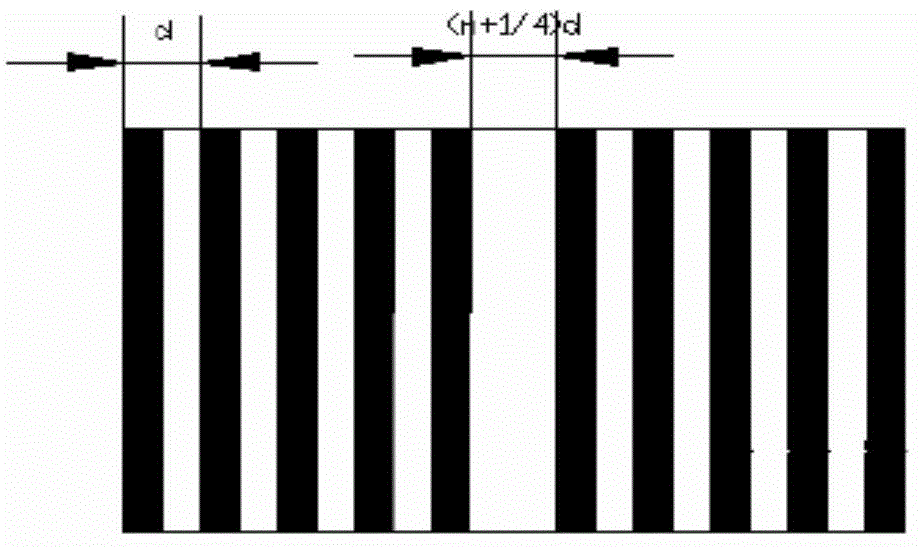
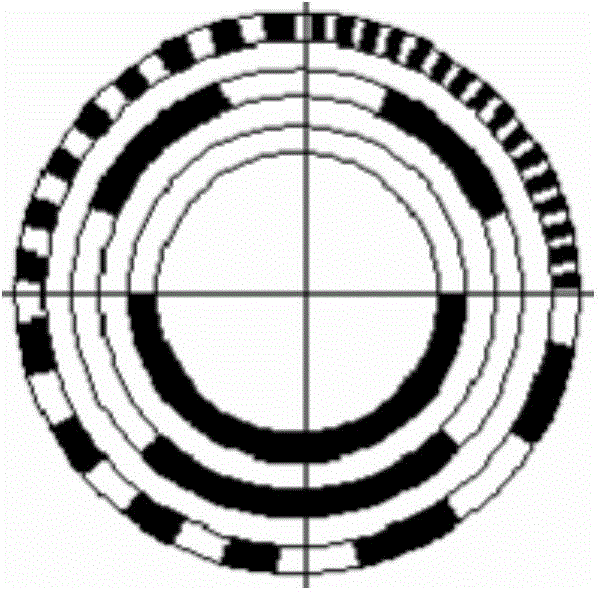
ActiveCN104655156AImprove bit error handling capabilityIncrease the counting circuit structureMitigation of undesired influencesFour quadrantsAutomatic control
The invention provides an error compensation method of an absolute code disc in a matrix encoding manner, and relates to the fields of photoelectric measurement and automatic control. The error compensation method disclosed by the invention solves the problem that the absolute code disc is insufficient in the capability of processing error codes. The error compensation method comprises the following steps: 1, reading a corresponding code value by utilizing a four-quadrant absolute code disc; 2, adopting a reading head of which the outermost circle has a difference of 90 degrees, and reading a value of an incremental code disc through a processing circuit of the incremental code disc; 3, setting a threshold, and calculating the difference of the two code values; 4, replacing the absolute code value exceeding the preset threshold with the corresponding incremental code value. According to the error compensation method disclosed by the invention, a real-time detection method is adopted, the original structure of the matrix encoding disc is utilized, and only a counting circuit structure of the incremental code disc is additionally added, so that the jump variation of the code value due to various factors can be compensated, the advantages of an absolute manner and an incremental manner are merged, the contradiction of the decoding of high code values and the size of the code disc is solved in a certain extent, and the added circuit is simple and reliable, and is convenient to maintain.
Owner:严格集团股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com