Segmented key authentication system
A technology of authentication system and authentication data, applied in the field of authentication system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] The following embodiments are examples. Although the description refers to one or more embodiments, this does not imply that each reference refers to the same embodiment, or that a feature applies to only one embodiment. Simple features of different implementations may also be combined to provide other implementations. In respect of the drawings, for purposes of illustration and clarity, scale and proportion have not been strictly adhered to.
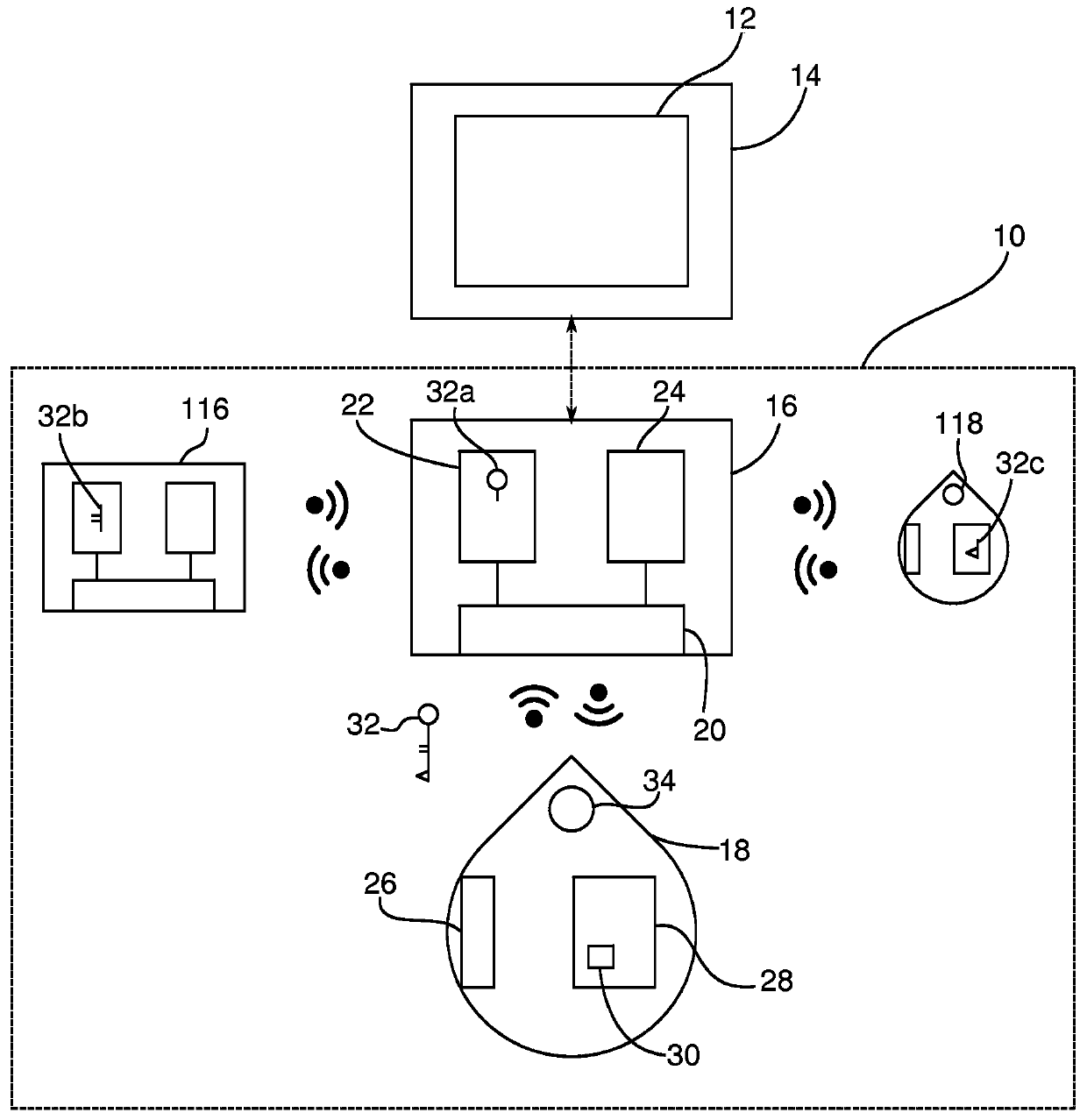
[0064] figure 1 An authentication system 10 according to an embodiment of the present invention is schematically represented. Authentication system 10 enables control of access to applications 12 accessible via computer 14 . The authentication system includes a master mobile device 16 and a master token 18 . The master mobile device includes a near field communication module 20 , a non-volatile memory 22 and a volatile memory 24 .
[0065] The master token 18 also includes a near field communication module 26 and a non-volat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com