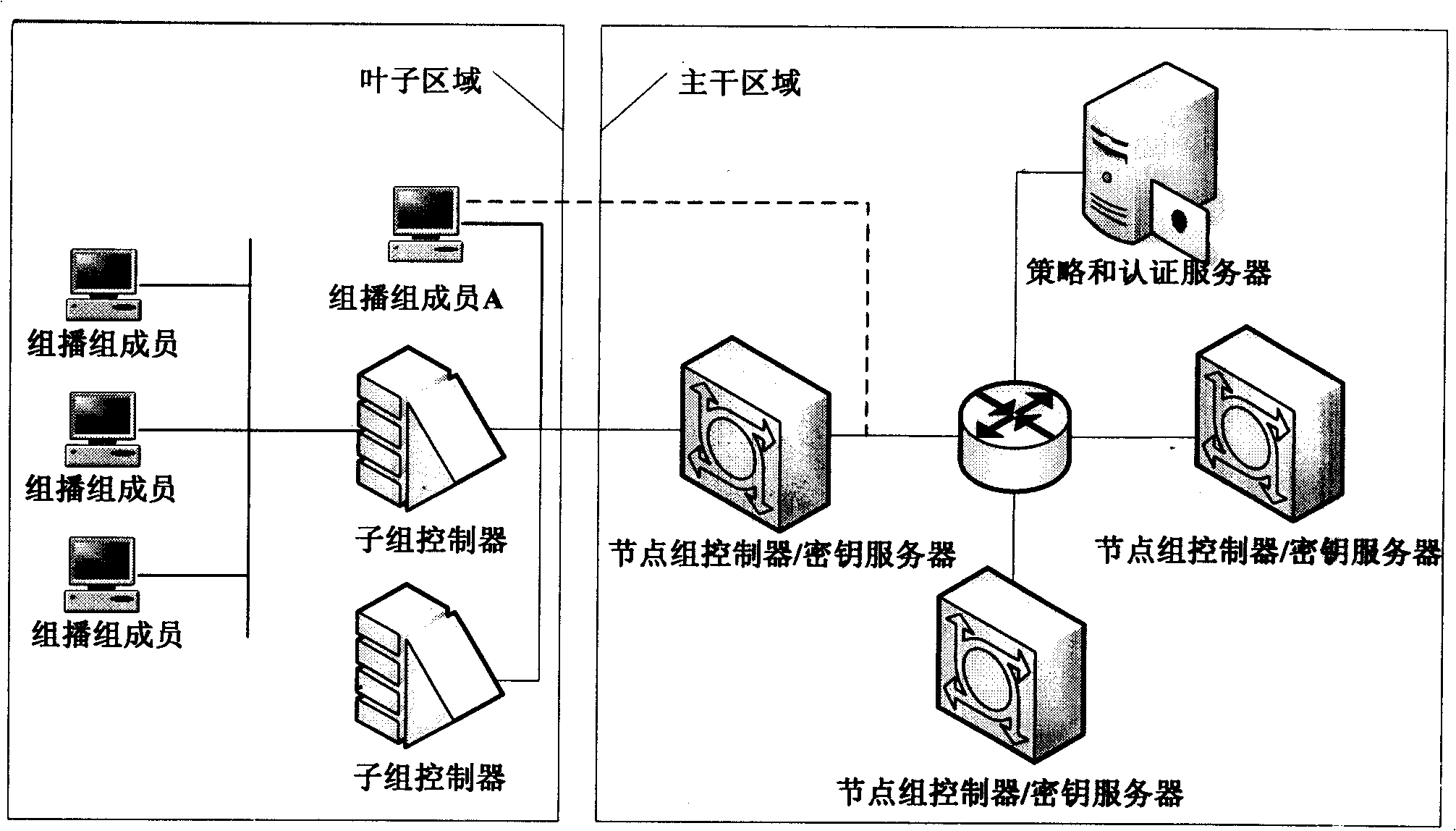
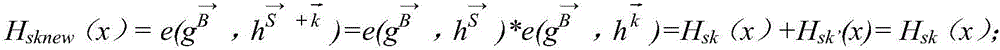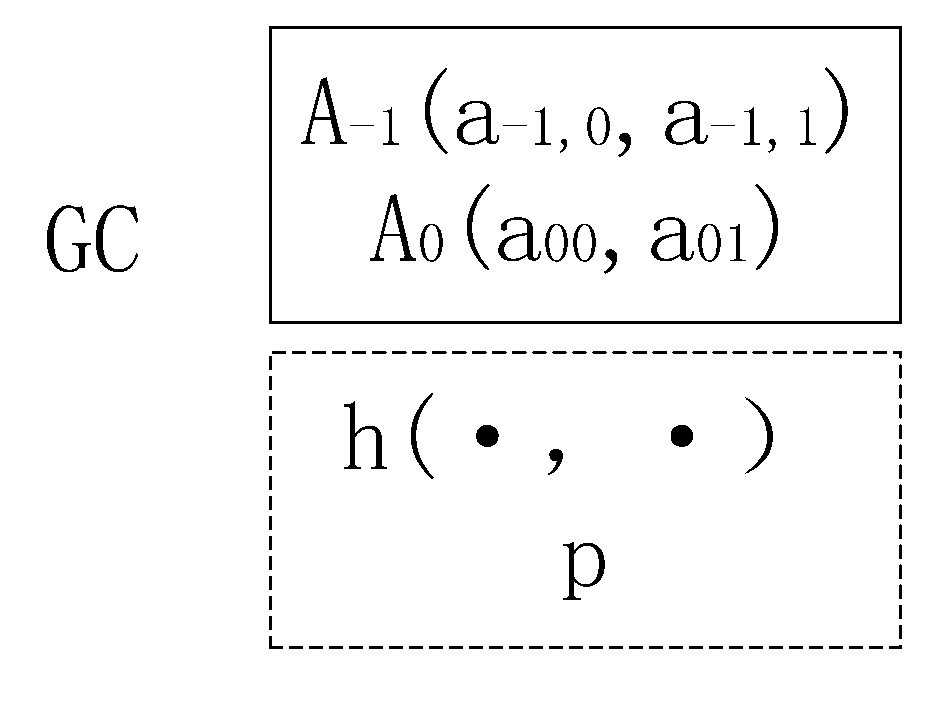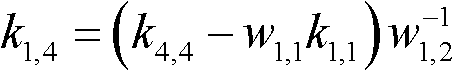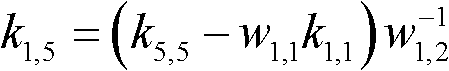Patents
Literature
80 results about "Group key management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
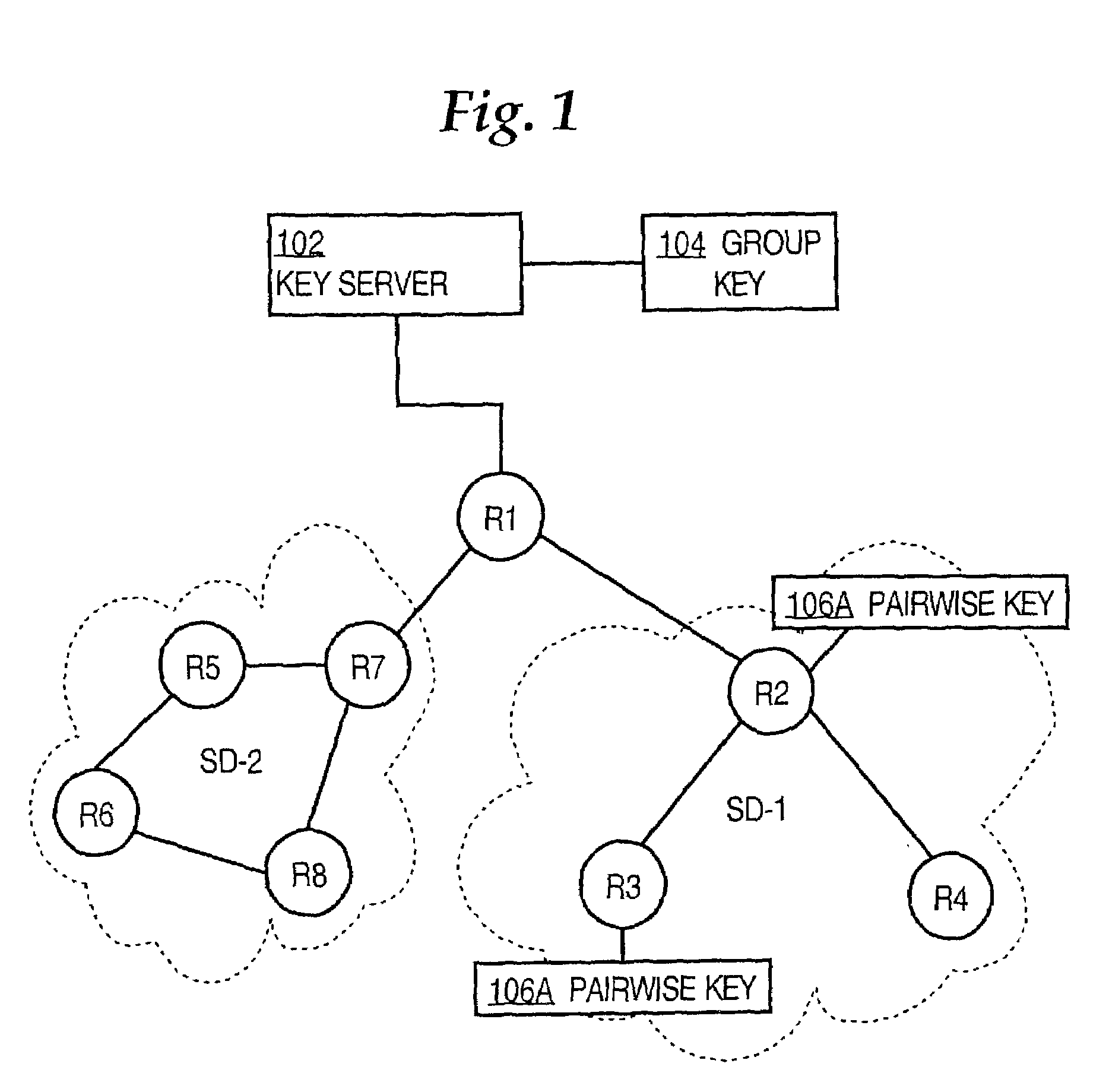
Method and apparatus for generating pairwise cryptographic transforms based on group keys
ActiveUS7234058B1Key distribution for secure communicationDigital data processing detailsPairwise keyComputer security
Group key management techniques are applied to generating pair-wise keys for point-to-point secure communication applications. Nodes participating in a secure communication group each receive a group key and associated policy information. When a first node wishes to establish a secure point-to-point connection to a second node, the first node derives a pairwise key from the group key and policy information, for example, by hashing the group key and information identifying the two nodes. As a result, a pairwise key is generated without exchanging negotiation messages among the two nodes and without expensive asymmetric cryptographic computation approaches.
Owner:CISCO TECH INC
Extending credential type to group key management interoperability protocol (KMIP) clients
A key management protocol (such as KMIP) is extended to provide an extended credential type to pass information from clients to the server to enable the server to deduce pre-provisioned cryptographic materials for the individual clients. Preferably, KMIP client code communicates device information to a key management server in a value in the headers of KMIP requests that flow to the server. In this manner, KMIP requests are associated with pre-provisioned cryptographic materials for particular devices or device groups.
Owner:IBM CORP
Rekeying in secure mobile multicast communications
InactiveUS20070143600A1Easy to calculateReduce the impactKey distribution for secure communicationKey serverGroup controller
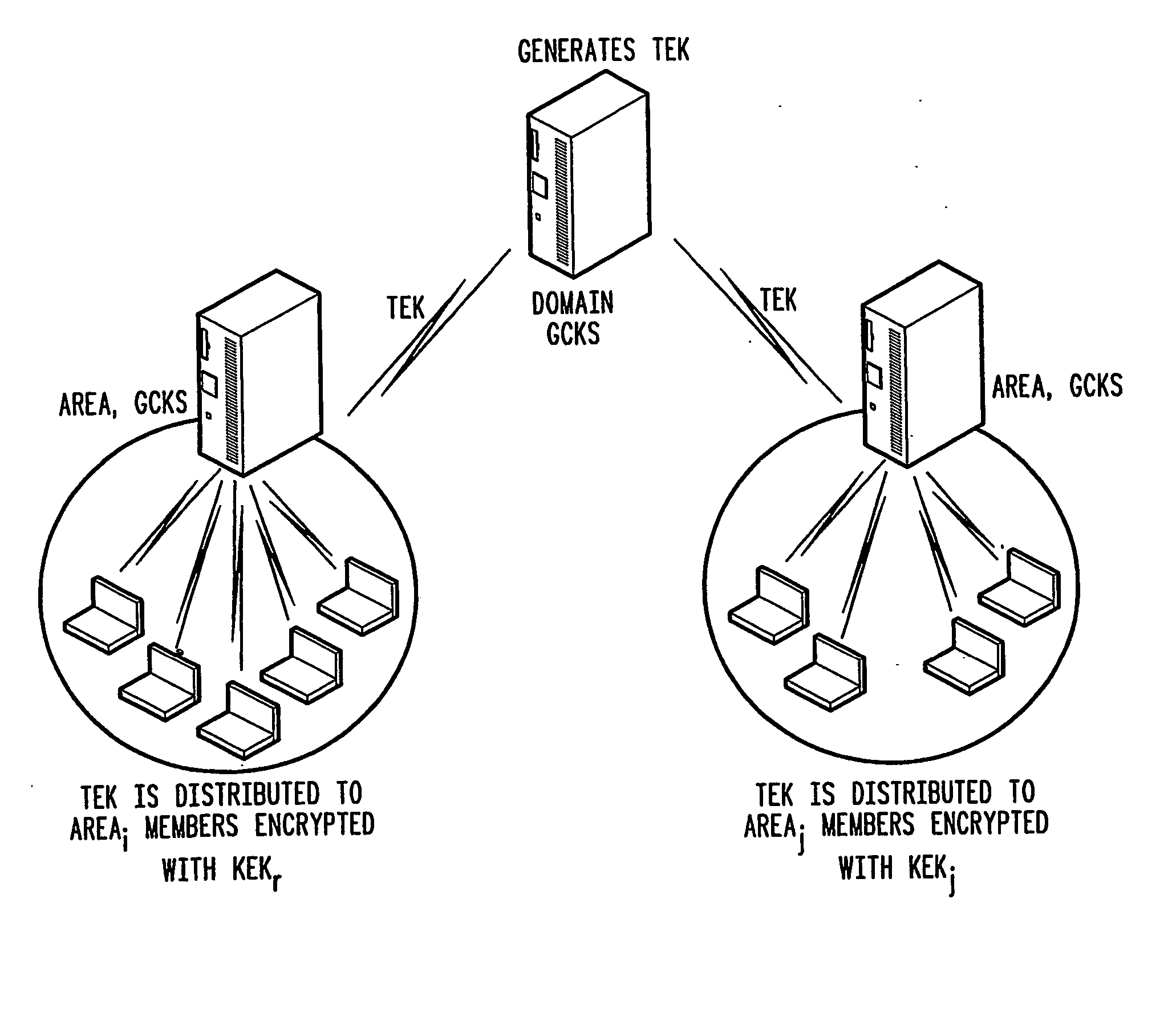
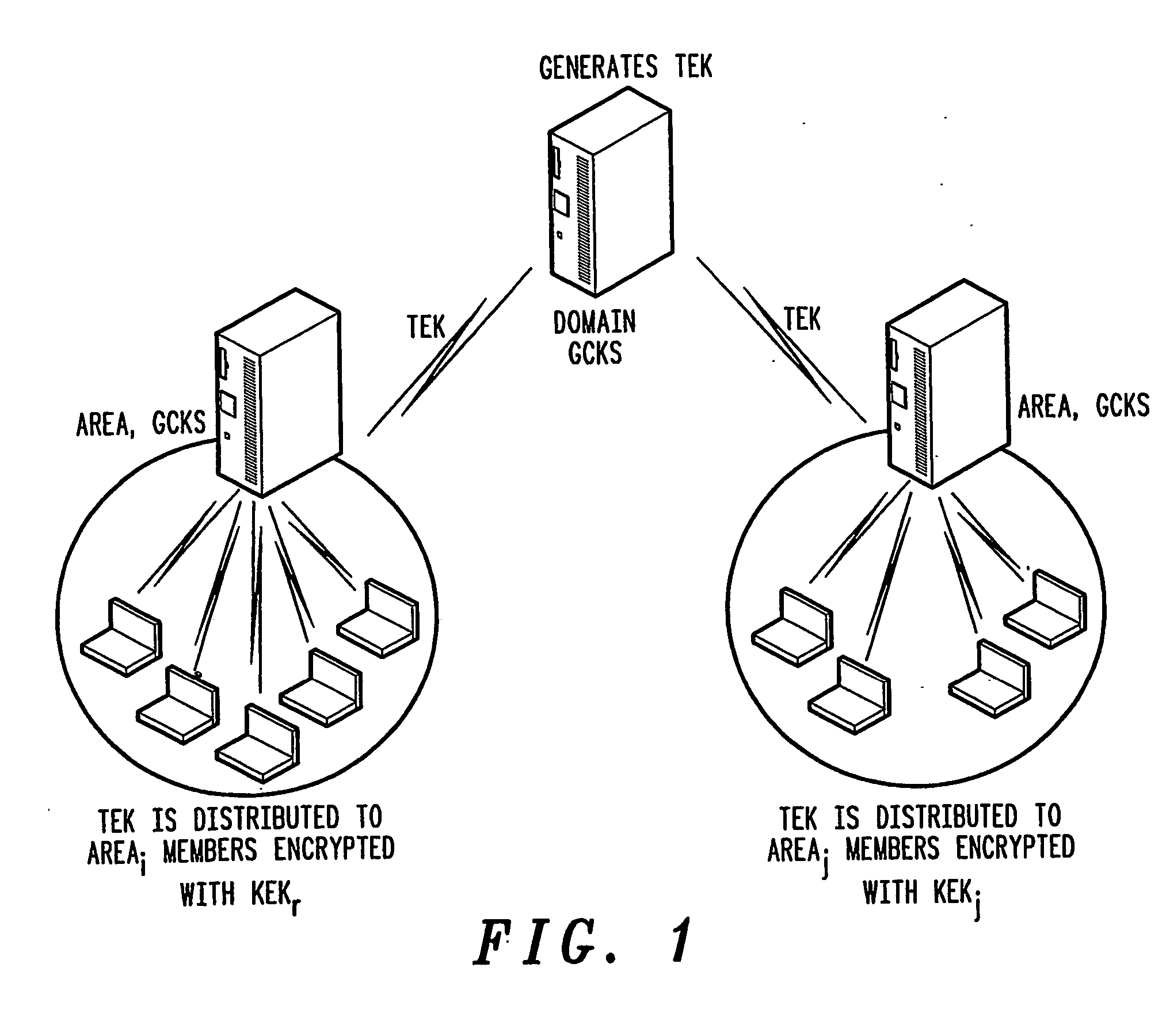
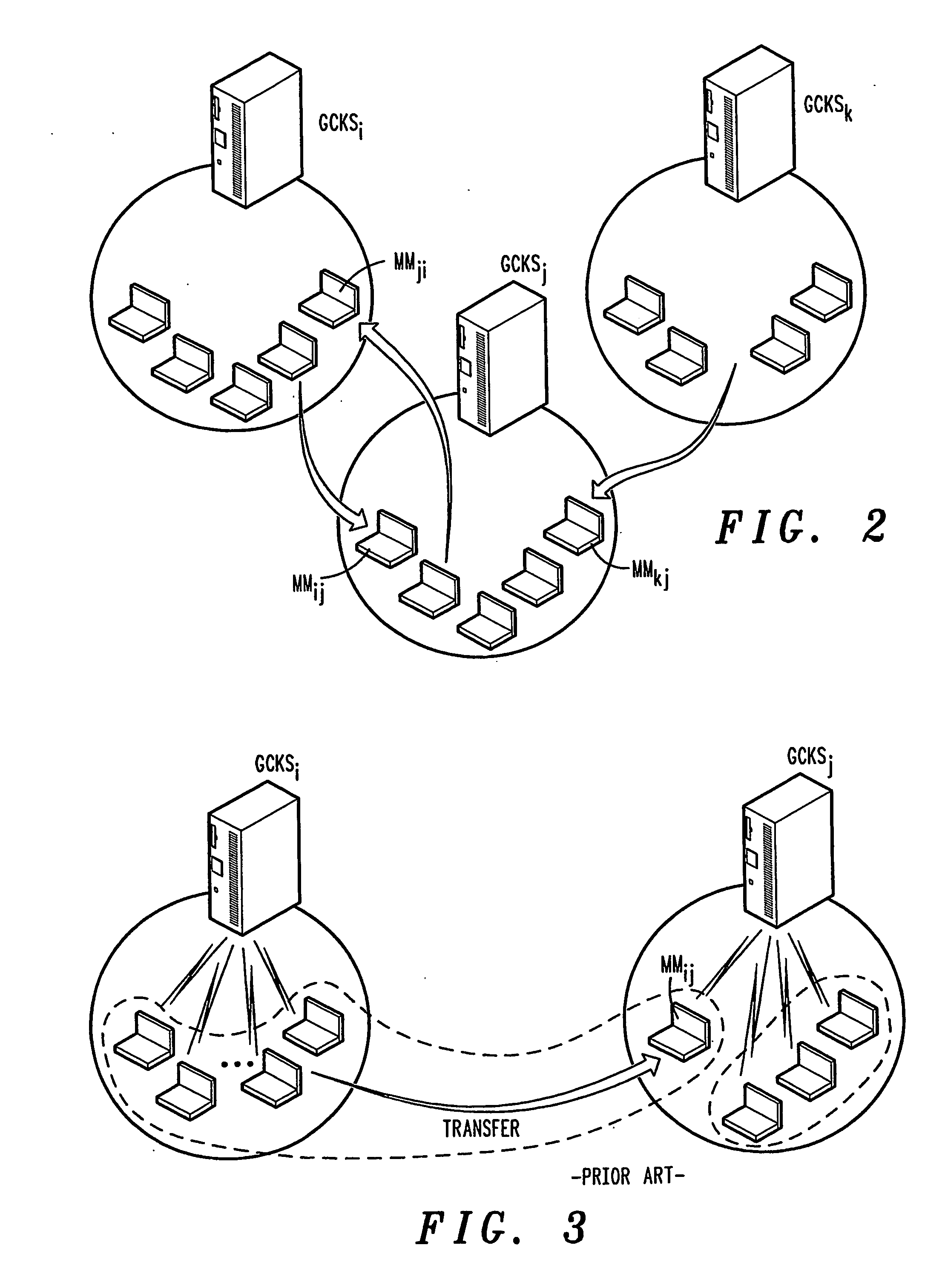
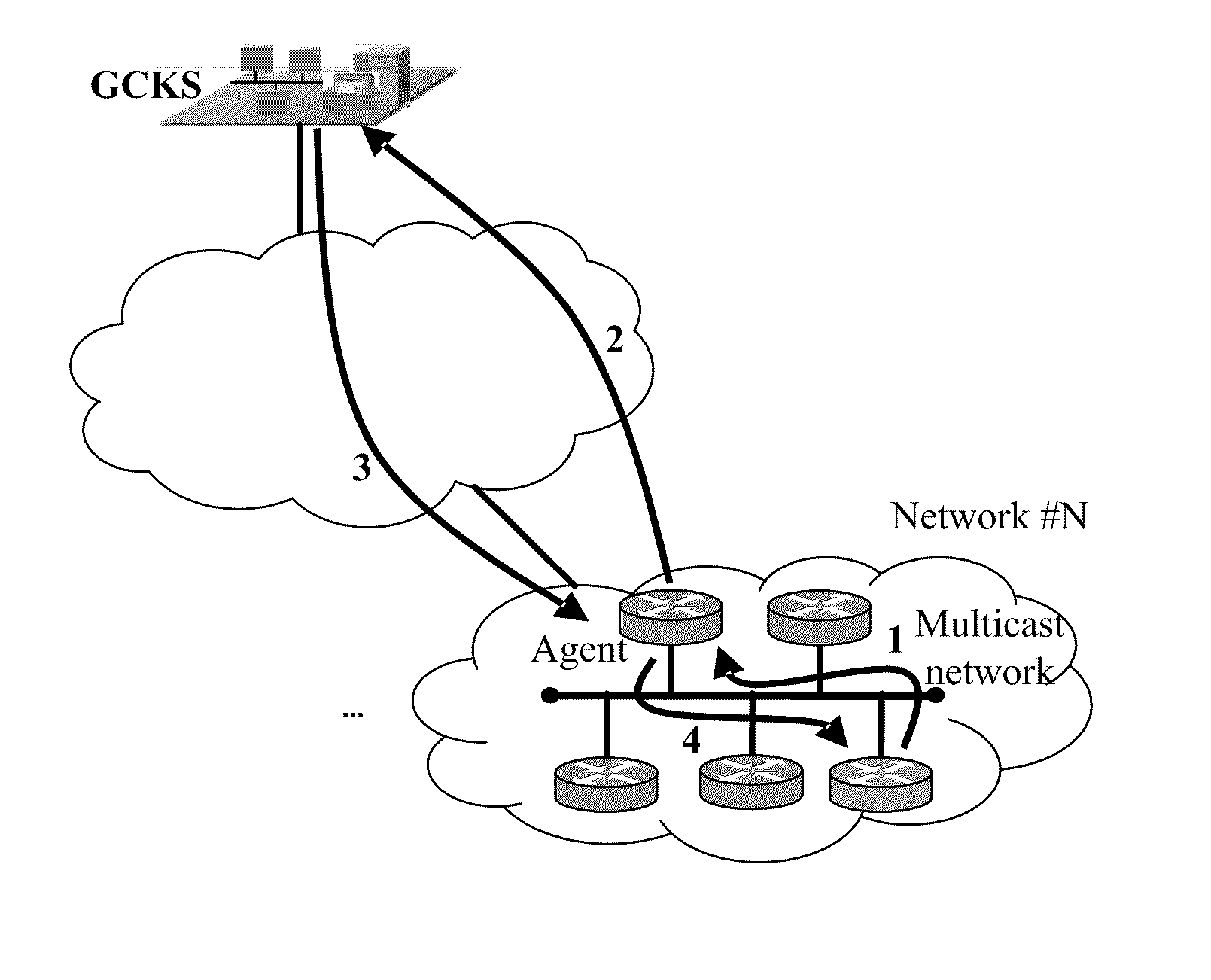
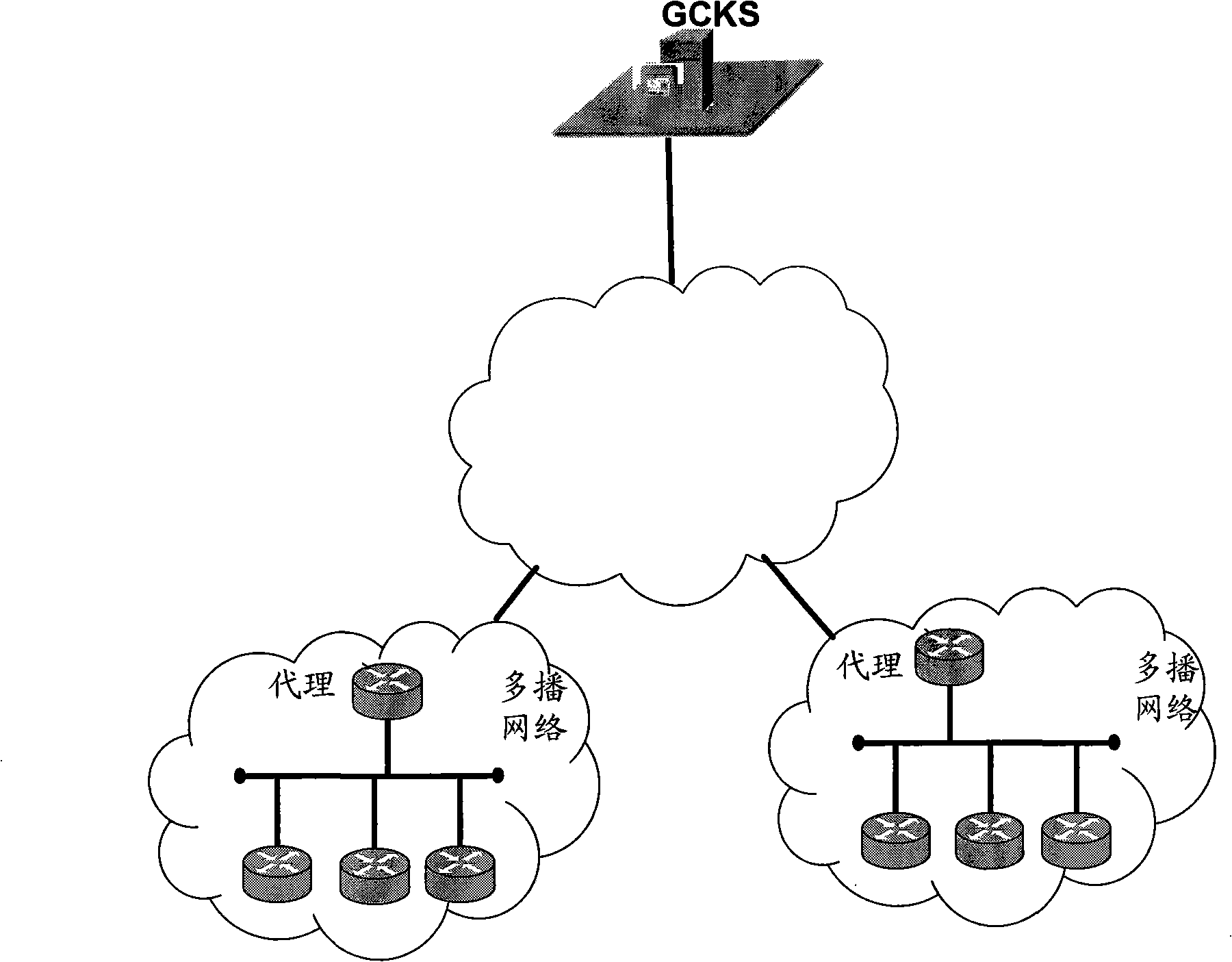
A method of inter-area rekeying of encryption keys in secure mobile muiticast communications, in which a Domain Group Controller Key Server (Domain GCKS) distributes Traffic Encryption Keys (TEK) to a plurality of local Group Controller Key Servers (local GCKS), and said local Group Controller Key Servers forward said Traffic Encryption Keys, encrypted using Key Encryption Keys (KEKi, KEKj) that are specific to the respective local Group Controller Key Server (local GCKSi, GCKSj), to group members, said local Group Controller Key Servers (GCKSi, GCKSj) constituting Extra Key Owner Lists (EKOLi, EKOLj) for group key management areas (areai, areaj) that distinguish group members (MMi, MMj) possessing Key Encryption Keys (KEKi, KEKj) and situated in the corresponding group key management area (areai, areaj) from group members (MMij) possessing Key Encryption Keys (KEKi) that were situated in the corresponding group key management area (areai) but are visiting another area (areaj).
Owner:MOTOROLA INC
Methods, Systems, and Apparatuses for Optimal Group Key Management for Secure Multicast Communication
InactiveUS20120257756A1Constant message sizeImmune to collusion attackKey distribution for secure communicationGroup controllerSecure multicast
Apparatuses, systems, and methods for optimal group key (OGK) management that may achieve non-colluding and / or the storage-communication optimality are disclosed. In some embodiments, a group controller (GC) is responsible for key generation and distribution and the group data are encrypted by a group key. When joining the group, in some embodiments, each group member (GM) is assigned a unique n-bit ID and a set of secrets, in which each bit is one-to-one mapped to a unique secret. Whenever GMs are revoked from the group, in some embodiments, the GC will multicast an encrypted key-update message. Only the remaining GMs may be able to recover the message and update GK as well as their private keys. The disclosed OGK scheme can achieve storage-communication optimality with constant message size and immune to collusion attack and also may outperform existing group key management schemes in terms of communication and storage efficiency.
Owner:ARIZONA STATE UNIVERSITY
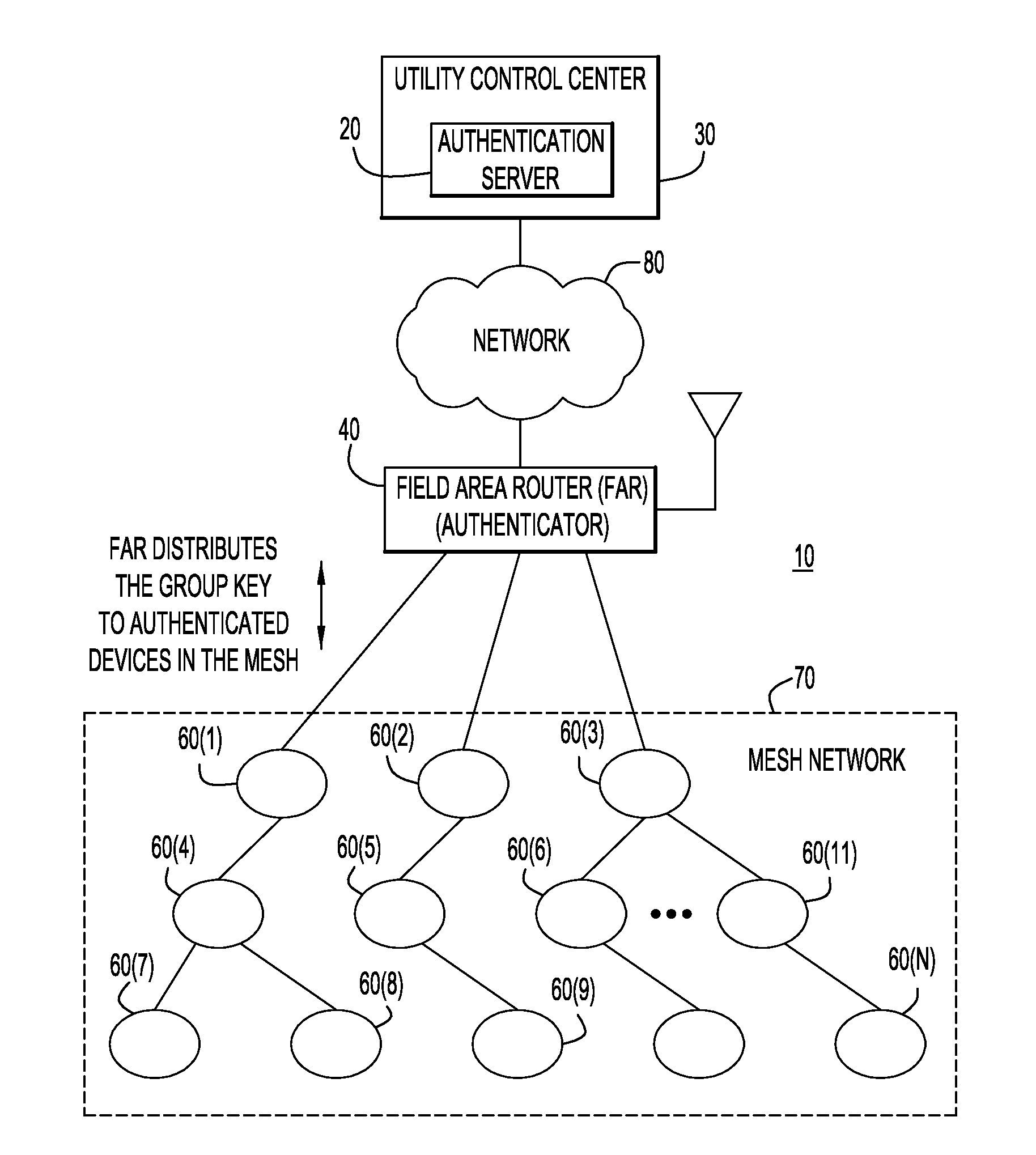
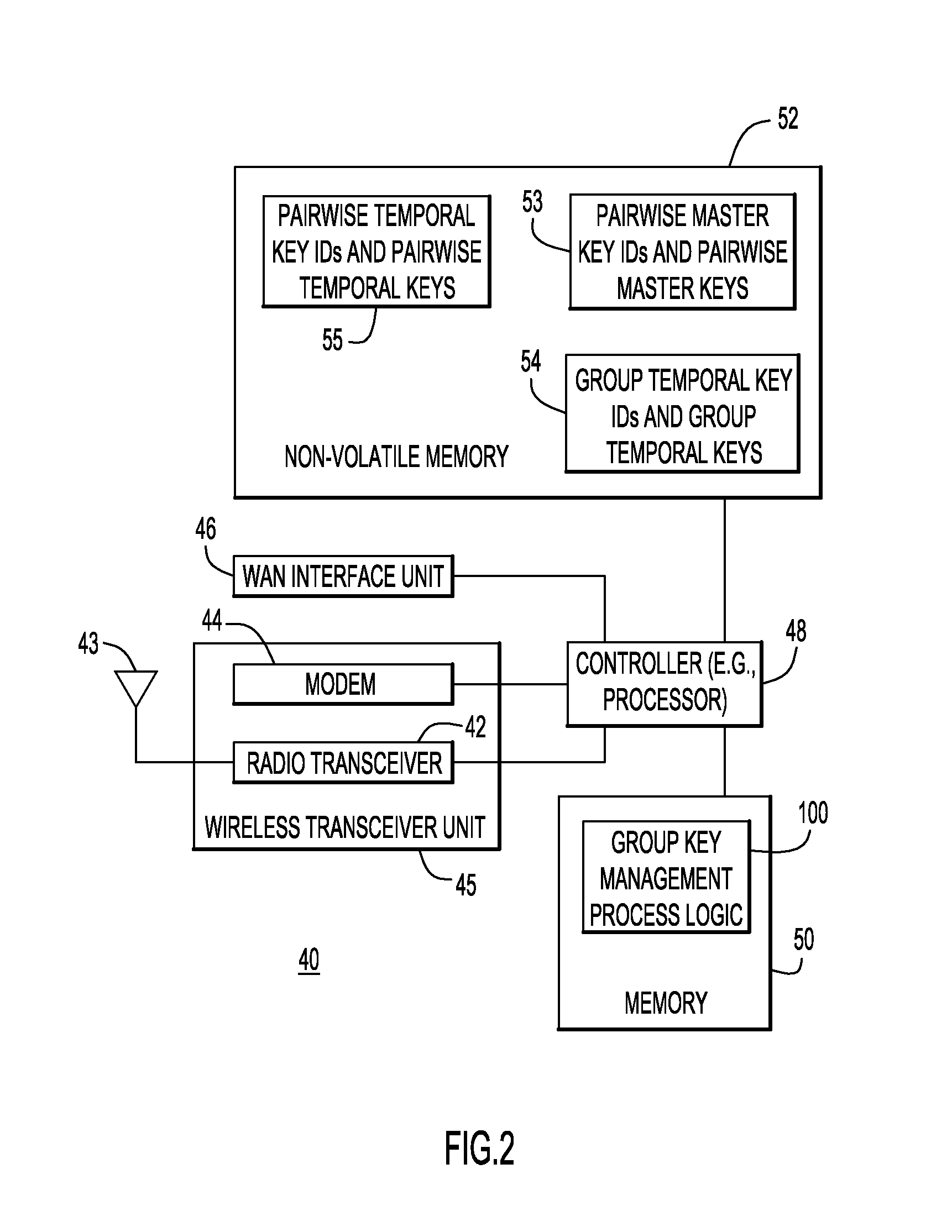
Group Key Management and Authentication Schemes for Mesh Networks
ActiveUS20130036305A1Multiple keys/algorithms usageUser identity/authority verificationSecure communicationMaster key
According to one embodiment, techniques are provided to enable secure communication among devices in a mesh network using a group temporal key. An authenticator device associated with a mesh network stores a pairwise master key for each of a plurality of devices in a mesh network upon authentication of the respective devices. Using the pairwise master key, the authenticator device initiates a handshake procedure with a particular device in the mesh network to mutually derive a pairwise temporal key from the pairwise master key. The authenticator device encrypts and signs a group temporal key using the pairwise temporal key for the particular device and sends the group temporal key encrypted and signed with the pairwise temporal key to the particular device.
Owner:CISCO TECH INC
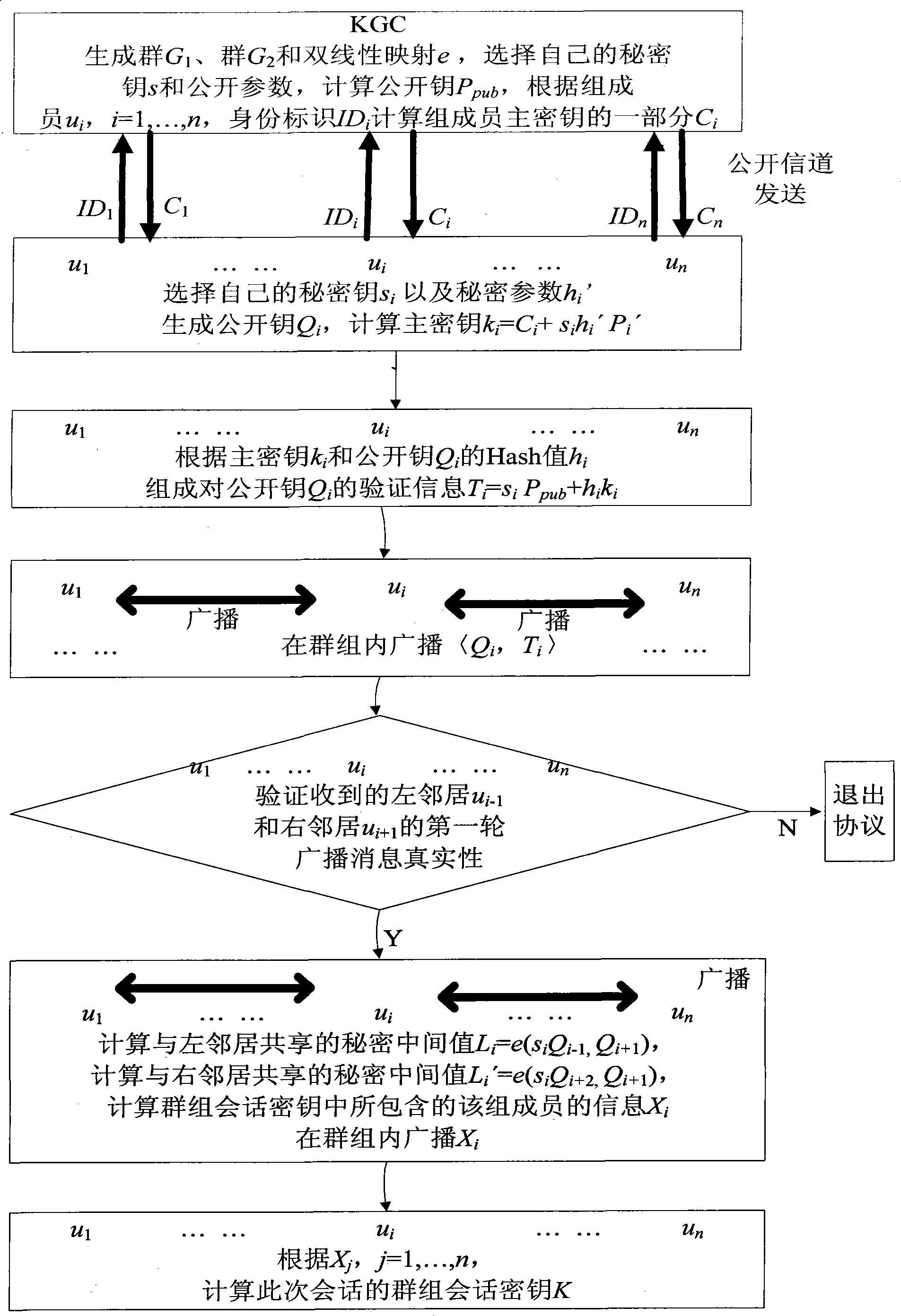
Authentication group key management method based on identity
InactiveCN101431414AAvoid hostingSolve tough problemsKey distribution for secure communicationUser identity/authority verificationGroup sessionKey escrow
The present invention discloses a identity-based authentication group key management method which comprises the following steps: embedding ID into key with bilinear pairing in elliptic curve; generating Ci as part of main key ui according to the secret key and ID of group member ui by key generating center, and transmitting the Ci to ui through overt channel; generating main key according to Ci and its own secret key by each group member ui; calculating overt key verification information according to Hash value of main key and over key by each group member, and broadcasting the link between over key and verification information inside the group; calculating the secret value sharing with left and right neighbors when the received information is verified to be true by each group member, and calculating the group member information Xi included in group session key according to the secret value, and then broadcasting the Xi inside the group; calculating group session key K according to all Xj, j=1, ...,n, by each group member. The invention has the advantages of no key escrow and no need of secure channel, which can be applied in coordination and distributed network as secure reliable group communication.
Owner:XIDIAN UNIV
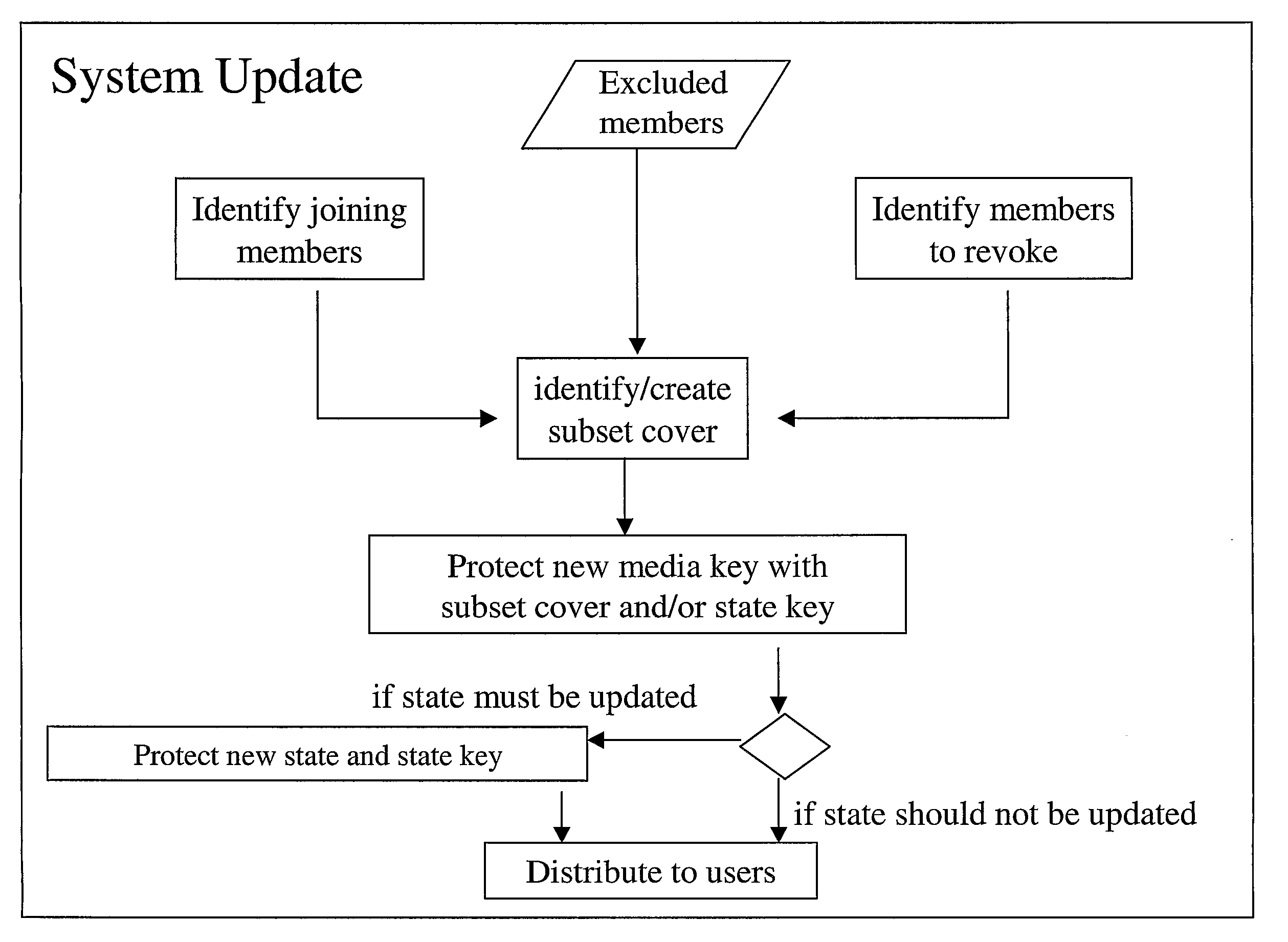
Key Distribution in Systems for Selective Access to Information
InactiveUS20080101611A1Small sizeAcceptable security levelKey distribution for secure communicationDigital data processing detailsInternet privacyKey distribution
A combination of stateless and state-full techniques enable reduced overall key management messages. A set of encryption keys is created based on a stateless subset cover scheme, where each user is associated with a leaf in the subset cover scheme. A state key and a corresponding state representing a subset of users that have the state key and a subset of users that do not have the state key is established, and a subset cover based on information representative of the established state is determined. Finally, a group key management message can be determined at least partly based on the calculated subset cover. The introduced state opens up for efficient subset cover calculation, reducing the size of the key management message.
Owner:TELEFON AB LM ERICSSON (PUBL)
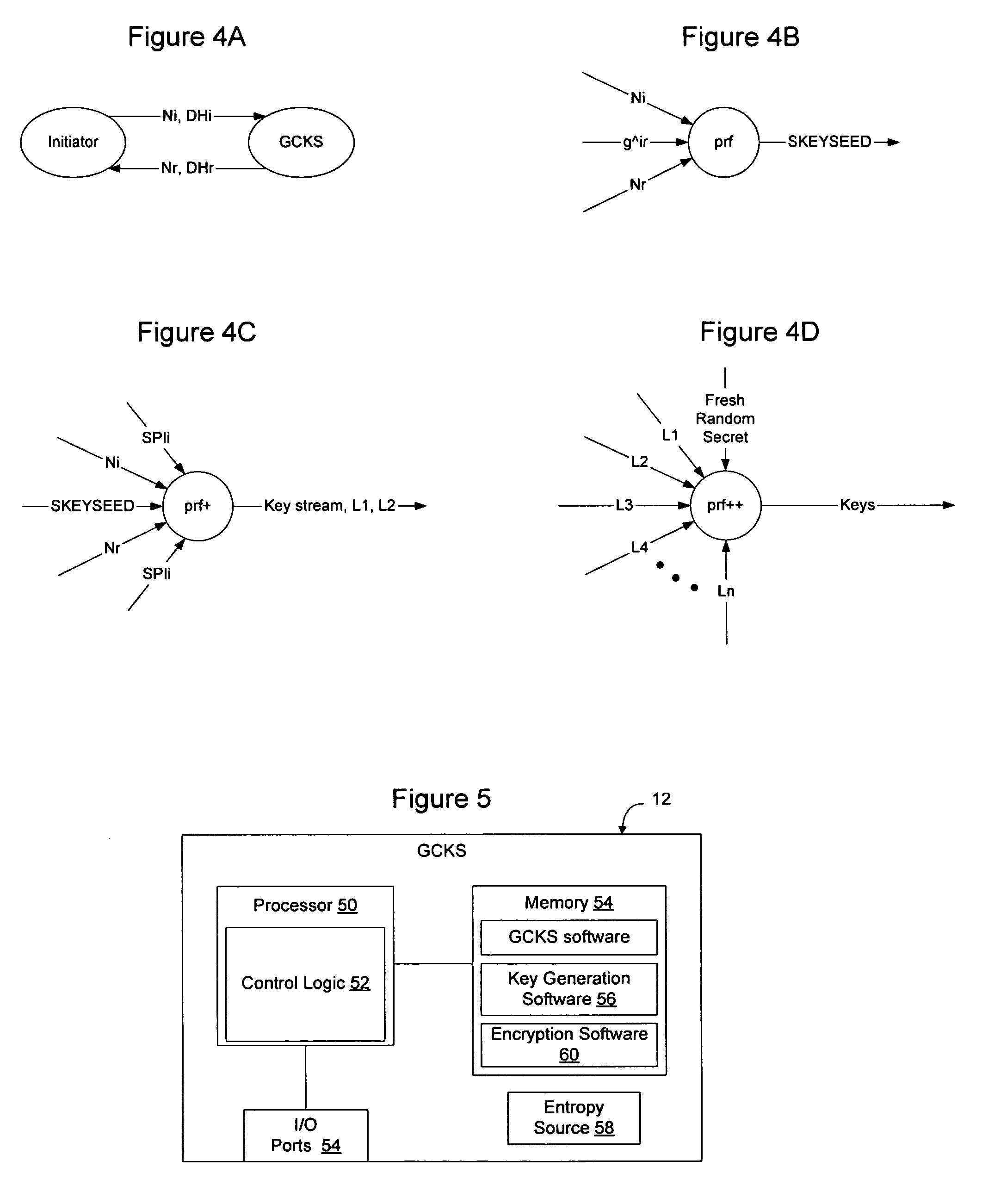
Method and apparatus for generating large numbers of encryption keys
InactiveUS20060062384A1High strengthKey distribution for secure communicationData stream serial/continuous modificationKey exchangeComputer science
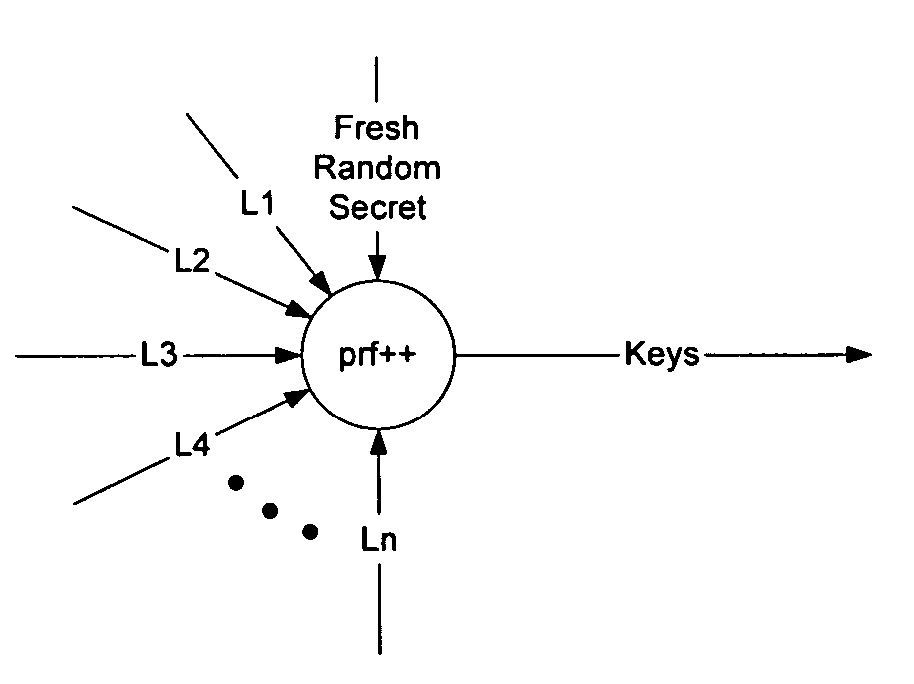
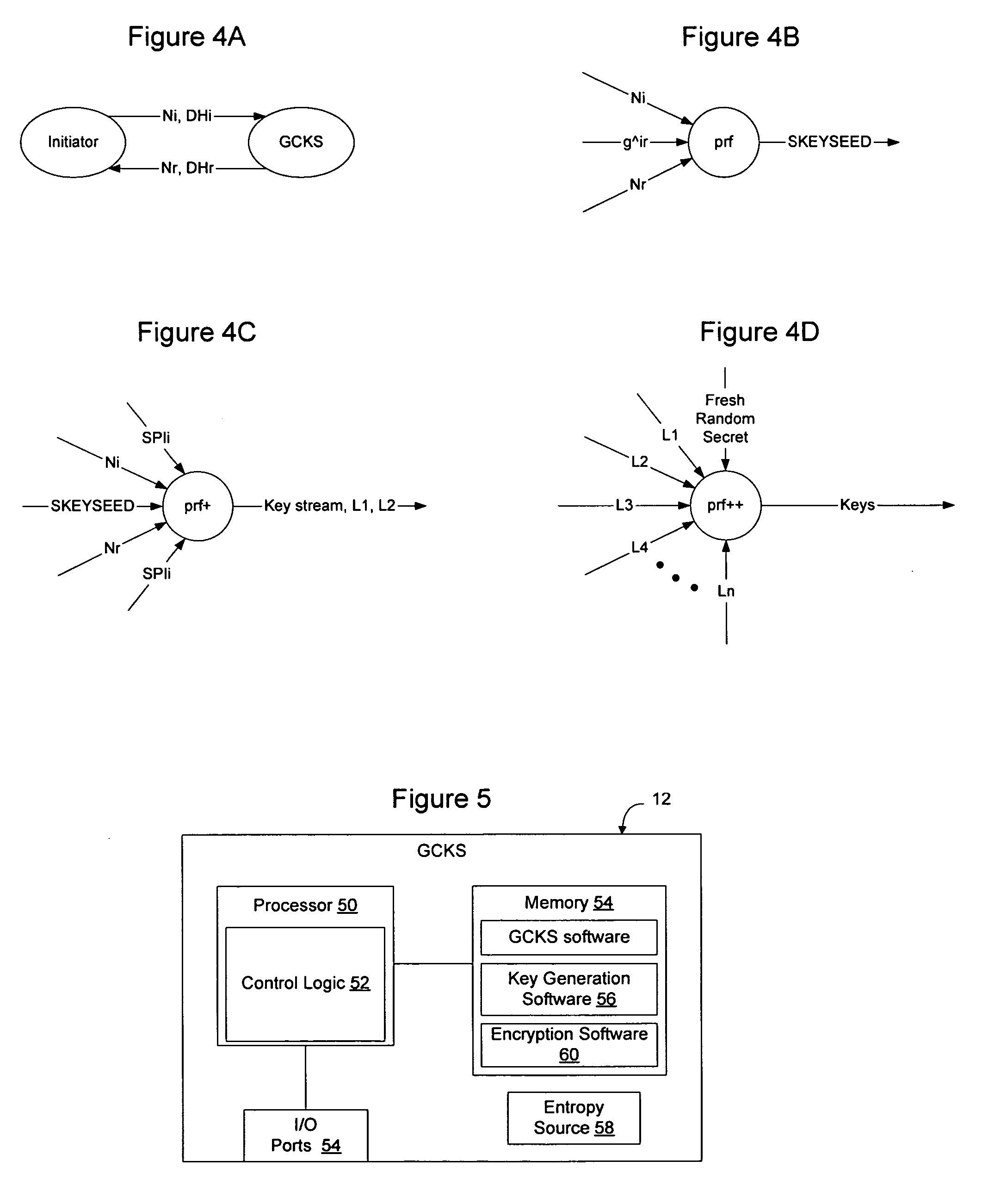
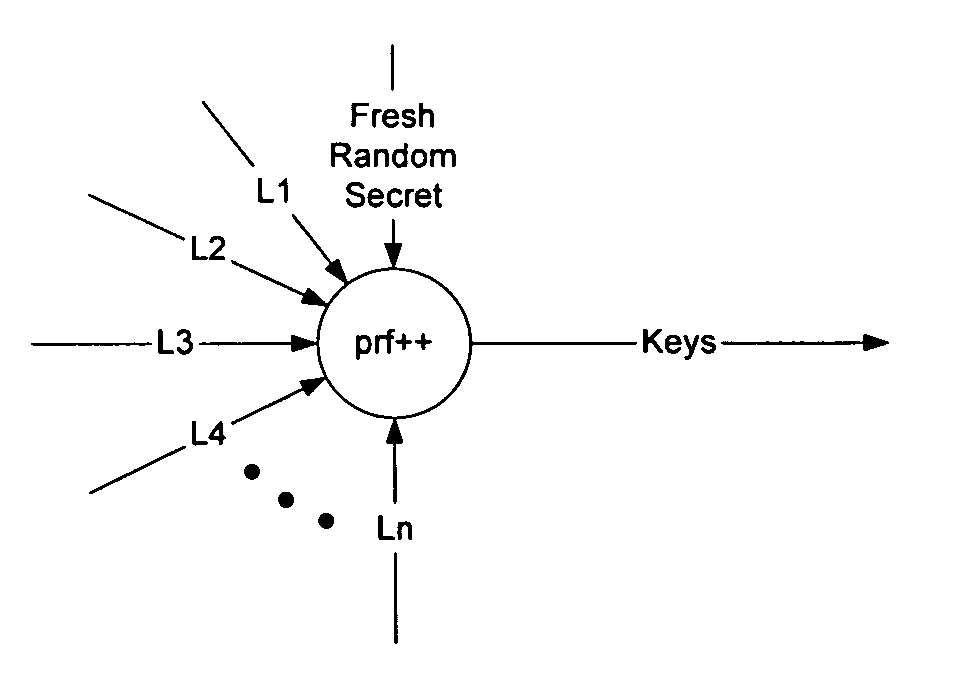
Entropy obtained from a series of key generation exchanges may be combined with entropy from a strong entropy source to allow the strong entropy to be stretched to generate a larger number of keys for use on a communication network, without requiring additional information from the group members and without requiring the entropy source to be increased in size or in number. In one embodiment, nonces exchanged during an initial key exchange are used to generate additional key material that is then fed, together with a fresh random secret, to another pseudo-random function to generate an additional key stream. The fresh ransom secret may be generated at the GCKS from a physical entropy source or other entropy source, and may be changed at will by the GCKS to further increase the strength of the keys. The methods are particularly useful for group key management where a large number of keys are required to be generated in a short time frame.
Owner:RPX CLEARINGHOUSE
Distributing system, method and device for group key control message
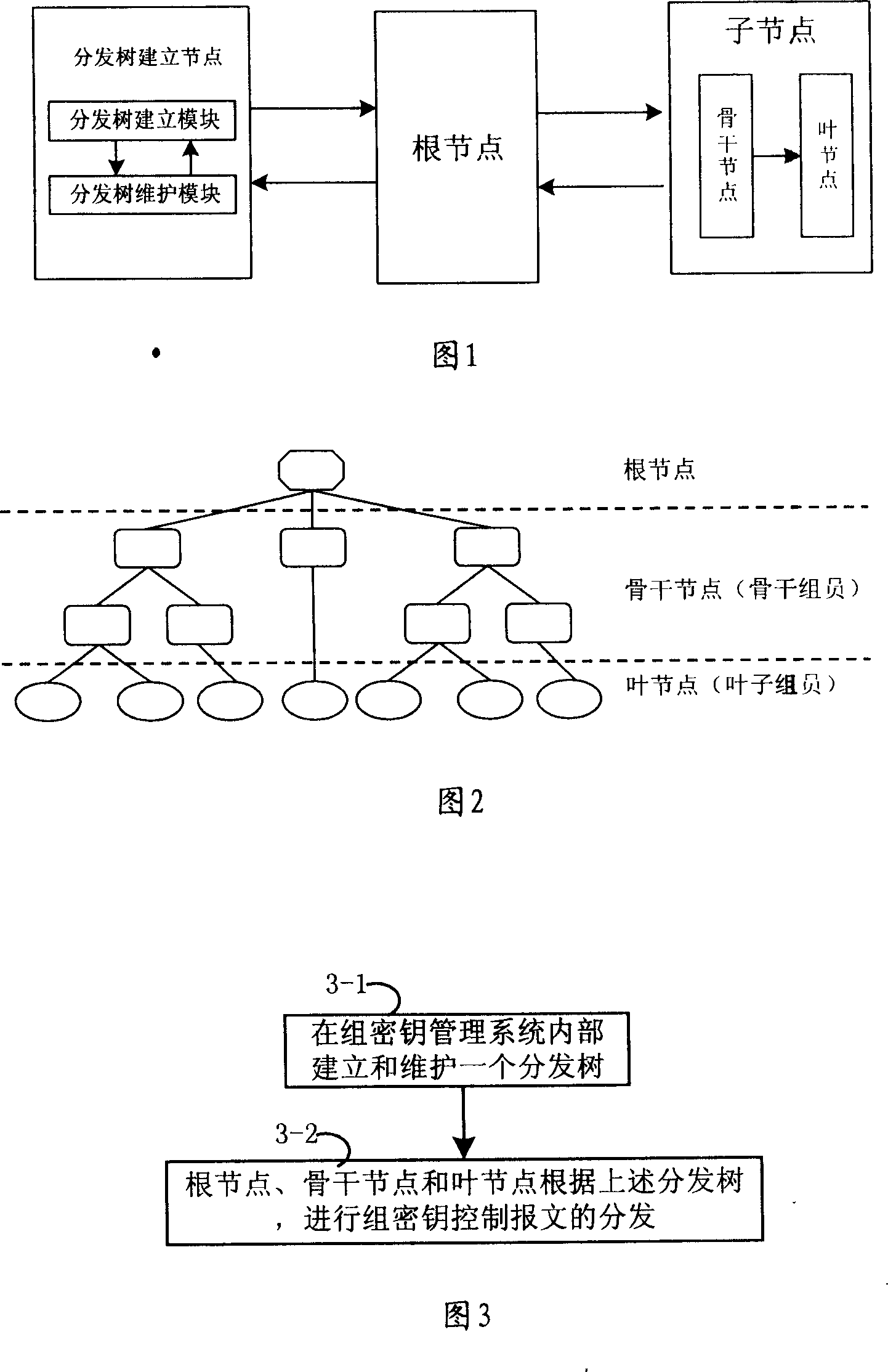
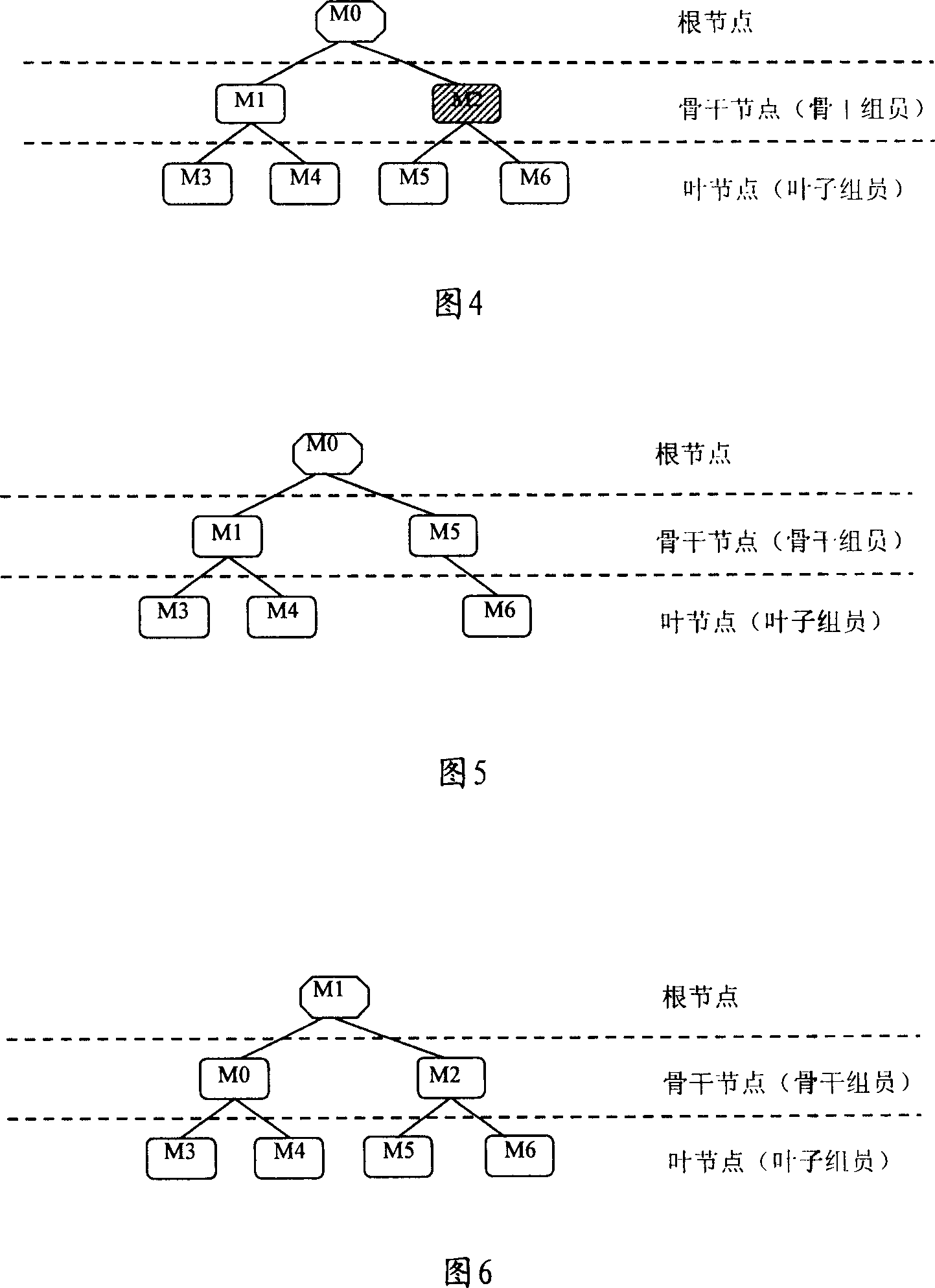
InactiveCN101022333AImprove usabilityImprove acceleration performanceKey distribution for secure communicationPublic key for secure communicationDistribution treeComputer hardware
A method for distributing composite cipher key control message includes setting up distribution tree of composite cipher key control message in composite cipher key management unit, down-sending composite cipher key control message to sub-node by root-node according to distribution tree, carrying out relevant retransmission or local treatment on received composite cipher key control message by sub-node. The system and device used for realizing said method are also disclosed.
Owner:HUAWEI TECH CO LTD
Key managing project for virtual organization under gridding computer environment
InactiveCN1801696AEasy to implement authenticationResistance to security risksKey distribution for secure communicationComputer scienceVirtual organization
The key management scheme for virtual organization in grid computation environment comprises: generating and updating the key; communicating and identifying based on threshold scheme. Based on schemes of centralization and distribution, it provides a new layer-cluster key management frame to solve the security problem and improve execution efficiency.
Owner:NANJING UNIV OF POSTS & TELECOMM
System and method for implementing security of multi-party-communication
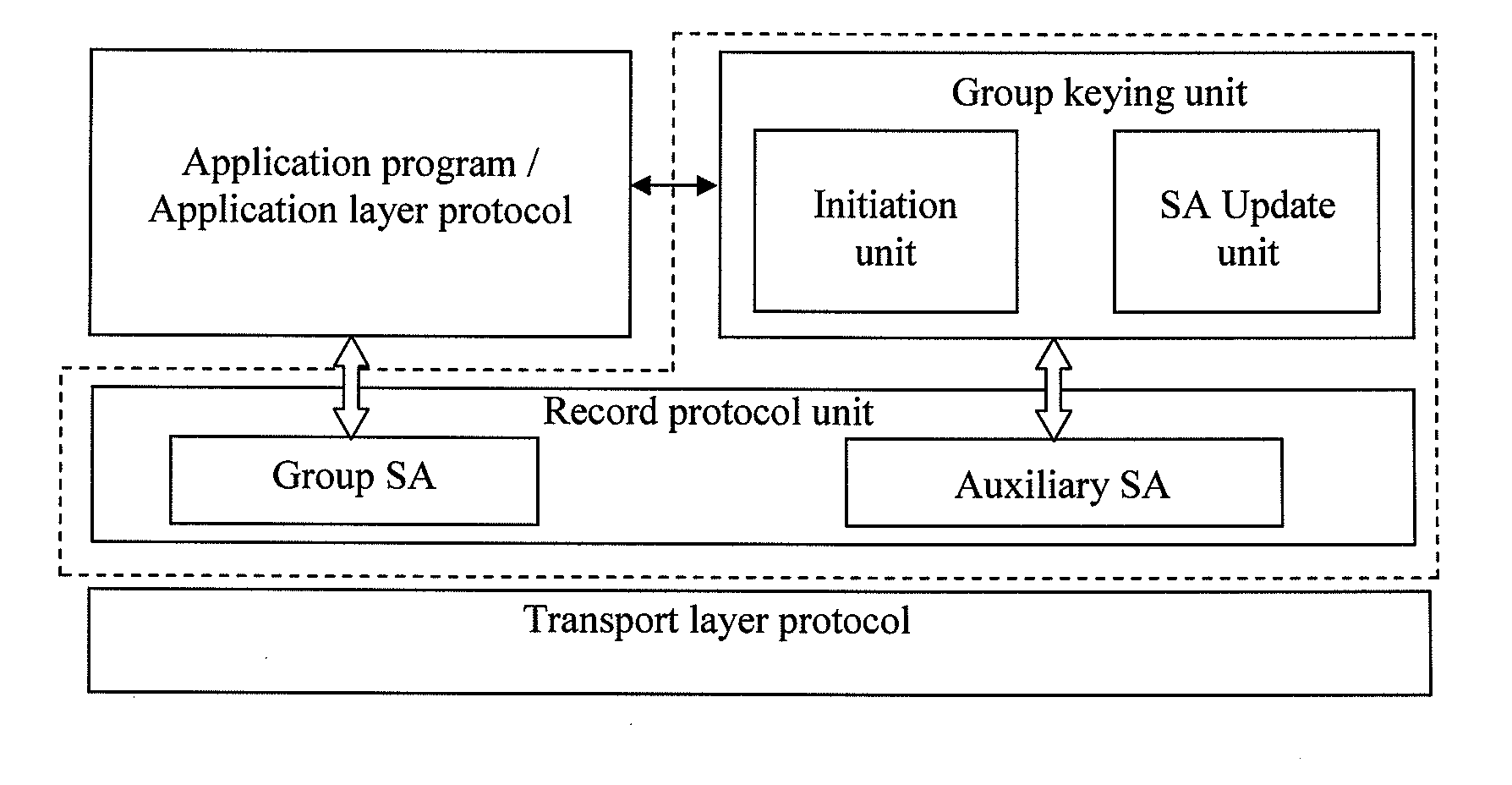
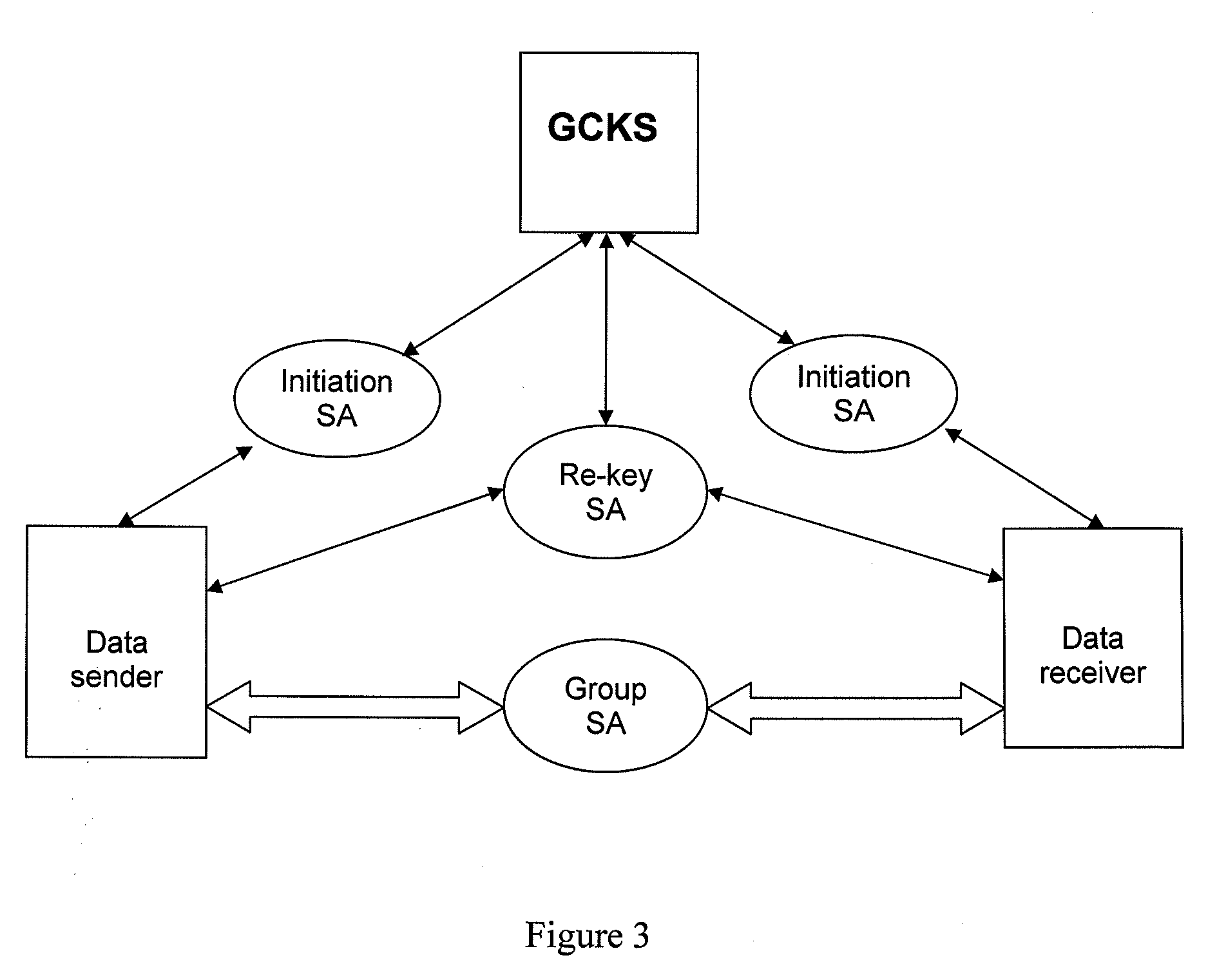
ActiveUS20090150668A1Implement securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesGroup controllerSecurity association
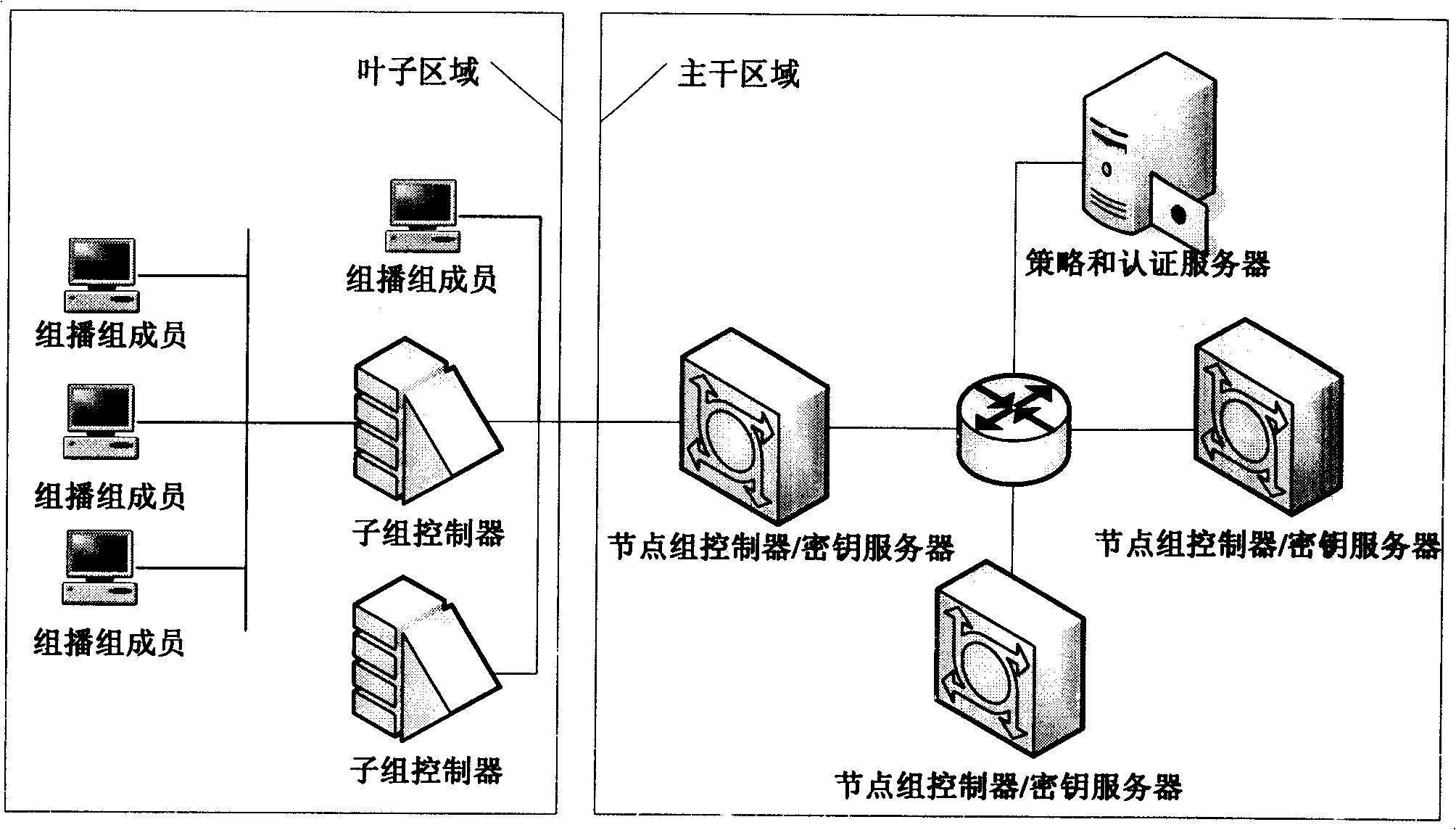
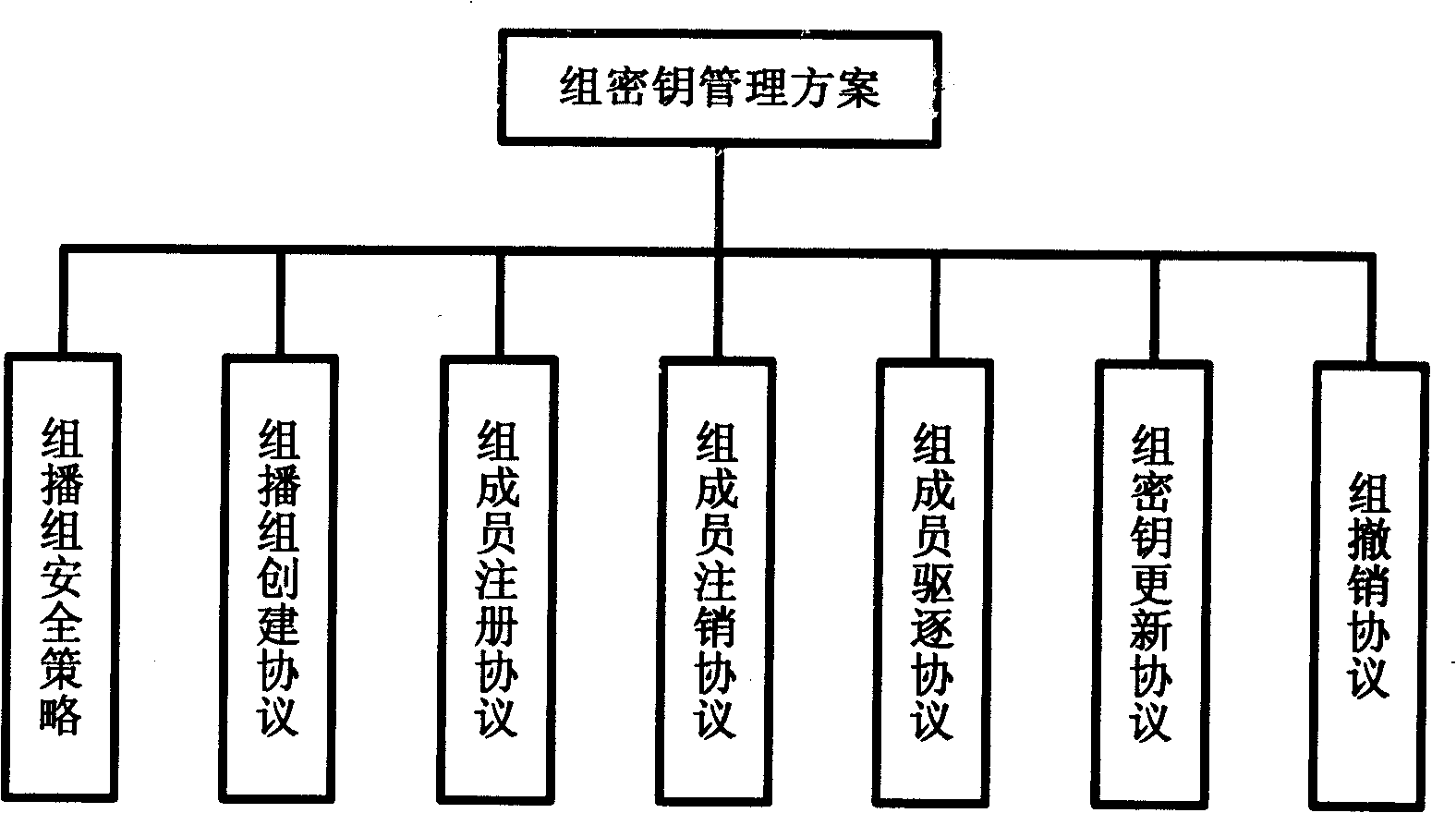
A system and method for implementing security of multi-party communication is disclosed in the disclosure. The system mainly includes a group key management unit and a record protocol unit. The method mainly includes when the system runs in the centralized group key management mode, the Group Controller and Key Server (GCKS) establishes and stores a Group Security Association, the GCKS negotiates with the group members to establish an Initiation Security Association, under the protection of the Initiation Security Association, the group members obtain the Group Security Association from GCKS. When the system runs in the distributed group key management mode, a Group Security Association is established by all the group members together at the beginning of the group communication. The system runs in the application process space and can provide an application program (or application protocol) with the function of the group key management and data security of the multi-party communication in the form of the standard Application Programming Interface (API).
Owner:HUAWEI TECH CO LTD
Method, system and device for realizing multi-party communication security
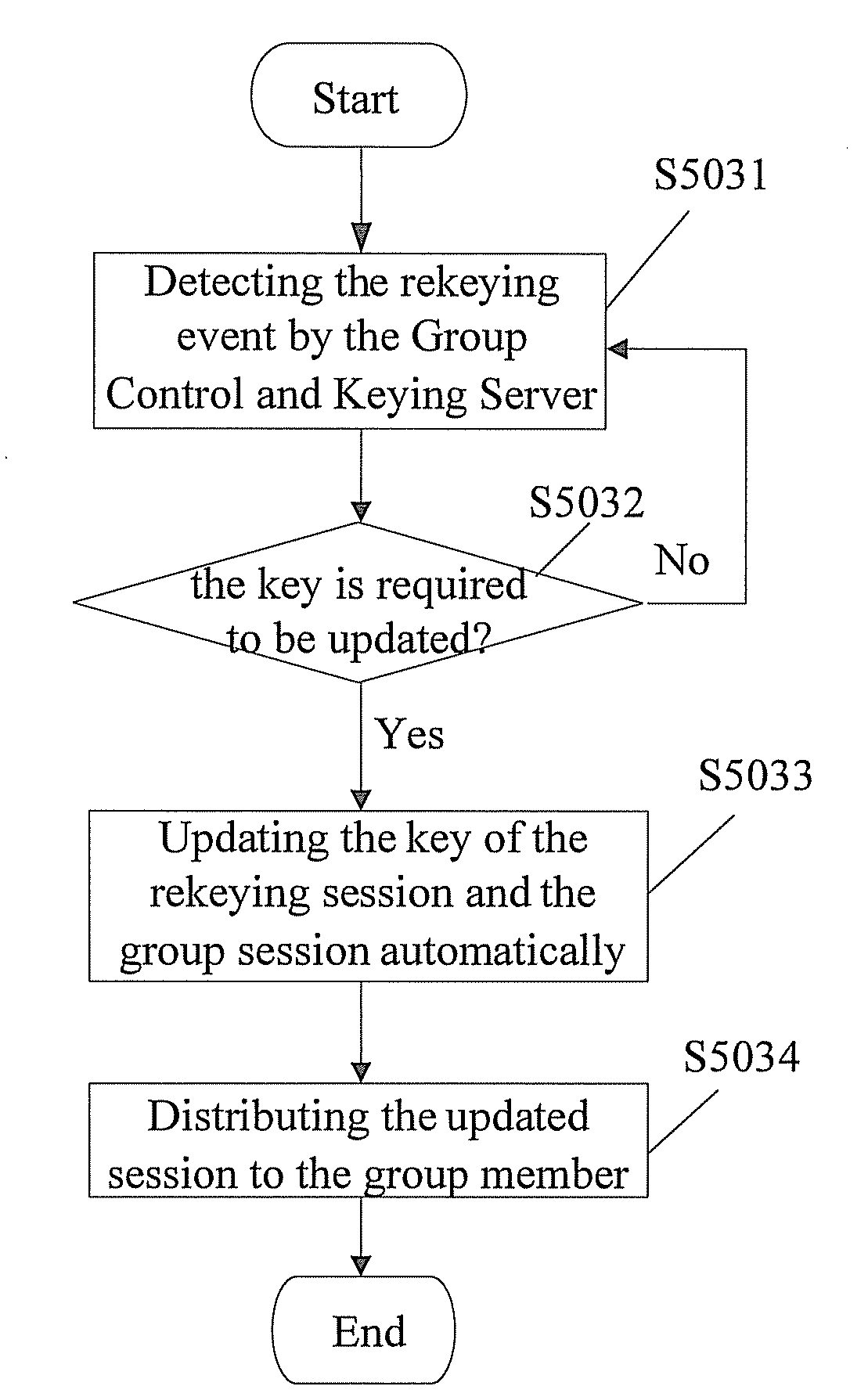
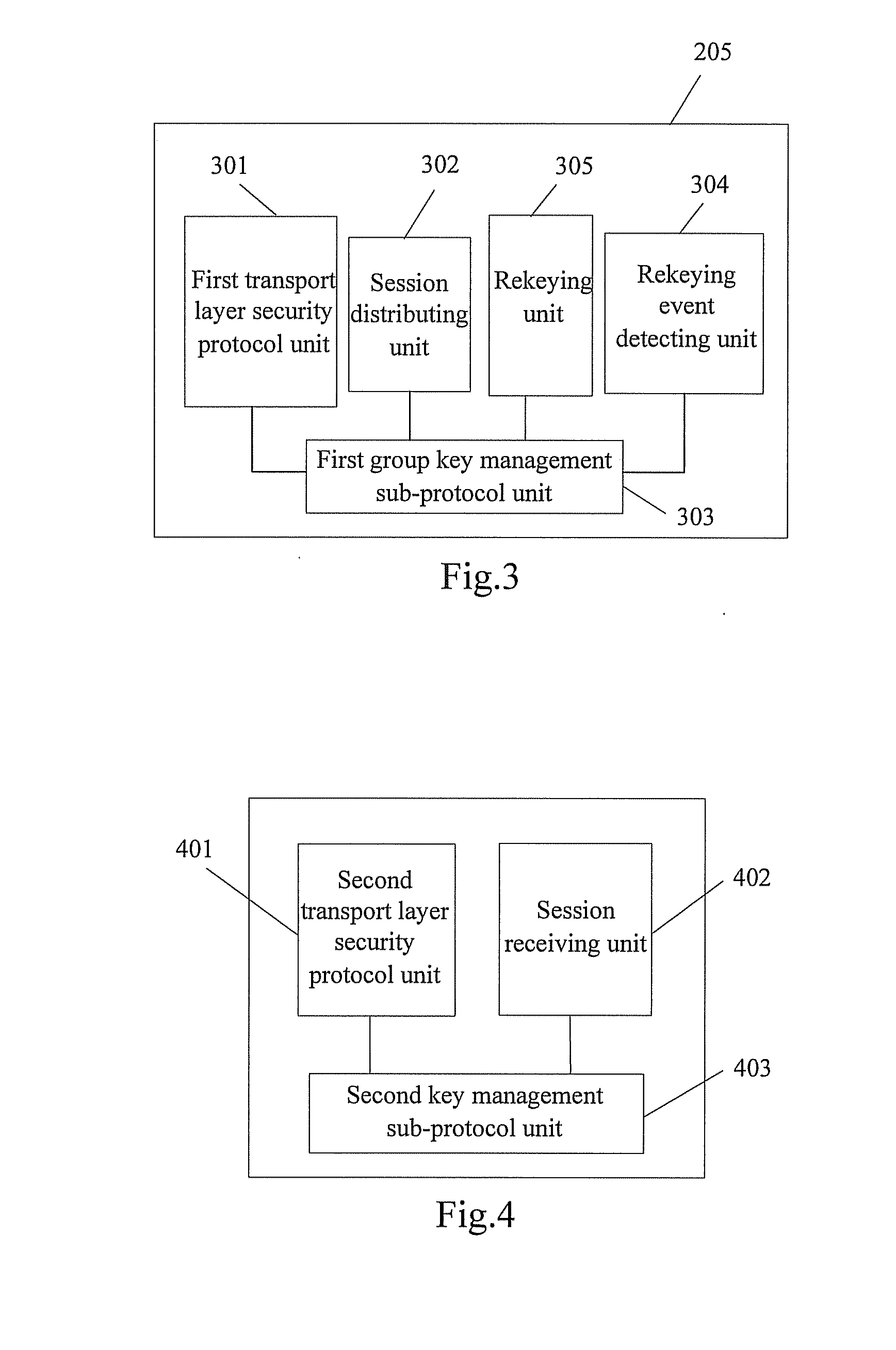
InactiveUS20090271612A1Improve deployabilityImprove portabilityKey distribution for secure communicationUser identity/authority verificationCommunications securityKey server
A method for realizing multi-party communication security includes: performing identification authentication and negotiating to create an initiation session through running the transport layer security protocol or datagram transport layer security protocol by a Group Control and Keying Server and a group member device; distributing a group session and a rekeying session to the group member device through running a group key management sub-protocol on the Group Control and Keying Server and the group member devices; rekeying through running the group key management sub-protocol on the Group Control and Keying Server and the group member devices, when a rekeying event is detected by the Group Control and Keying Server. A relevant multi-party communication security system and a device are further provided in the present invention.
Owner:HUAWEI TECH CO LTD
Method of Managing a Mobile Multicast Key Using a Foreign Group Key
InactiveUS20080123856A1Address security threatsSecurity arrangementSecuring communicationSecure communicationMicrowave
The present invention relates to a method of managing a mobile multicast key using a foreign key. More specifically, the present invention relates to a method of managing a mobile multicast key using a foreign key for secure communication between a mobile terminal and a secure relay server in the region where microwaves from plural access points overlap.A method of managing a mobile multicast key using a foreign key according to the present invention has an advantage that multicast secure relay servers perform delegated authentication in advance in a region where microwaves overlap, thus reducing a delay time for authentication in a mobile terminal.And it has an advantage that it can minimize an effect from changes in group keys that user's movement make, by using a primary group key and a foreign key. This results in a reduction of an overhead from update of a group key while moving, and accordingly a reduction of a delay time.In addition, it has an advantage that it centralizes functions of key management to a secure relay server, thus overcoming the limitations on processing ability or network bandwidth of a mobile terminal.
Owner:KOREA INTERNET & SECURITY AGENCY
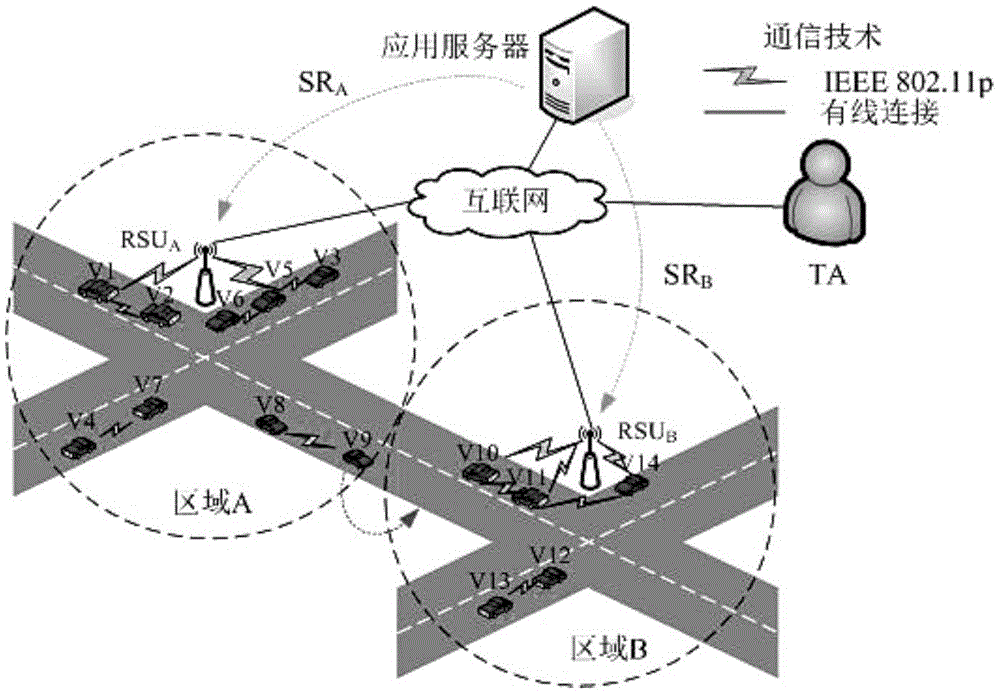
Internet of vehicles group key management method oriented to multiple services and privacy protection
ActiveCN105554105ASolve the problem of multiple groups ordering multiple servicesProtect identity privacyTransmissionComputer networkPrivacy protection
The invention discloses an Internet of vehicles group key management method oriented to multiple services and privacy protection. The method sequentially comprises the following steps: (1) establishing a two-layer network model of Internet of vehicles (colons are deleted); (2) describing a scene in which multiple groups subscribe multiple services in the Internet of vehicles based on the network model in the step (1); (3) protecting identity privacy of vehicles through a pseudonym mechanism, wherein TA can reveal real identities of the vehicles when service disputes occur; (4) using key update slot KUS by a TEK update strategy; and (5) after turnover of the vehicles, performing TEK update in a target region to ensure backward security, and performing TEK update in an original region to ensure forward security. Through adoption of the method, the identity privacy of the vehicles, non-repudiation of vehicle subscription services and service continuity during inter-regional turnover of the vehicles can be ensured.
Owner:ANHUI UNIVERSITY
Methods, systems, and apparatuses for optimal group key management for secure multicast communication
InactiveUS8837738B2Storage-communication optimalityConstant sizeKey distribution for secure communicationGroup controllerSecure multicast
Apparatuses, systems, and methods for optimal group key (OGK) management that may achieve non-colluding and / or the storage-communication optimality are disclosed. In some embodiments, a group controller (GC) is responsible for key generation and distribution and the group data are encrypted by a group key. When joining the group, in some embodiments, each group member (GM) is assigned a unique n-bit ID and a set of secrets, in which each bit is one-to-one mapped to a unique secret. Whenever GMs are revoked from the group, in some embodiments, the GC will multicast an encrypted key-update message. Only the remaining GMs may be able to recover the message and update GK as well as their private keys. The disclosed OGK scheme can achieve storage-communication optimality with constant message size and immune to collusion attack and also may outperform existing group key management schemes in terms of communication and storage efficiency.
Owner:ARIZONA STATE UNIVERSITY
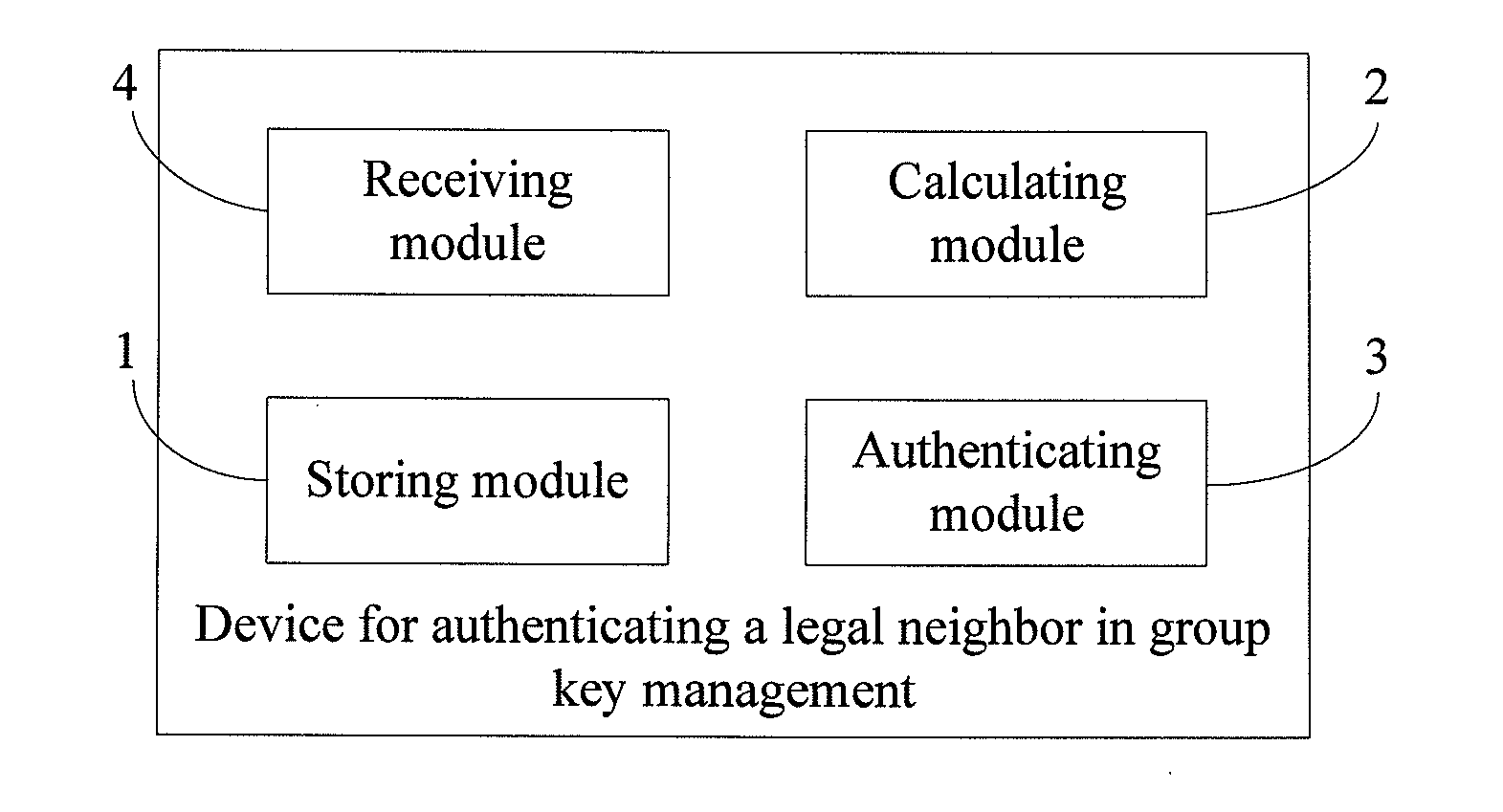
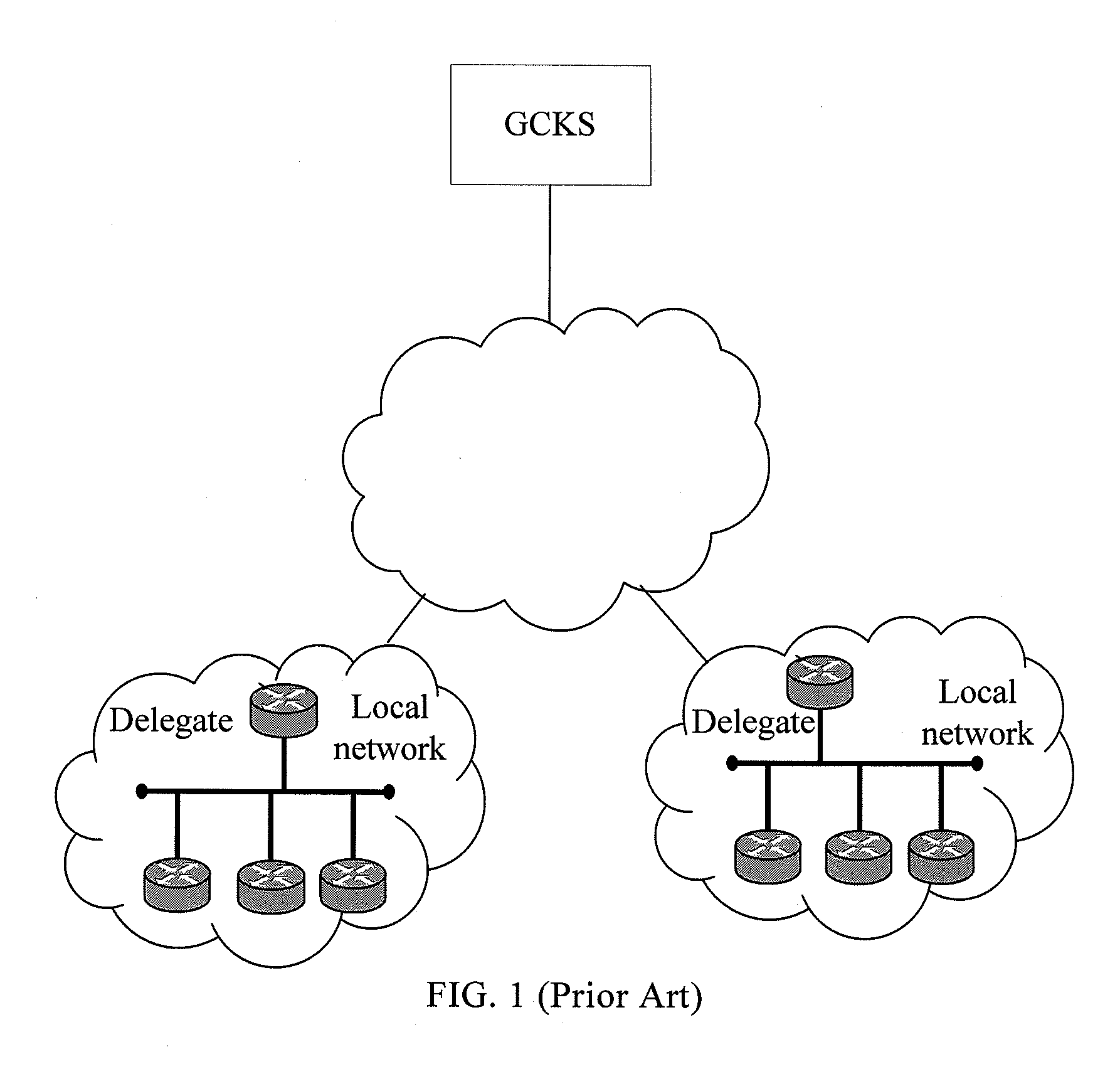
Legal neighbor authentication method and device in group key management
InactiveCN101399661AKey distribution for secure communicationData switching networksAuthentication informationGroup key management
Owner:HUAWEI TECH CO LTD
Distributed group key management scheme for secure many-to-many communication
InactiveCN1363160ASpecial service provision for substationKey distribution for secure communicationDistribution treeBinary tree
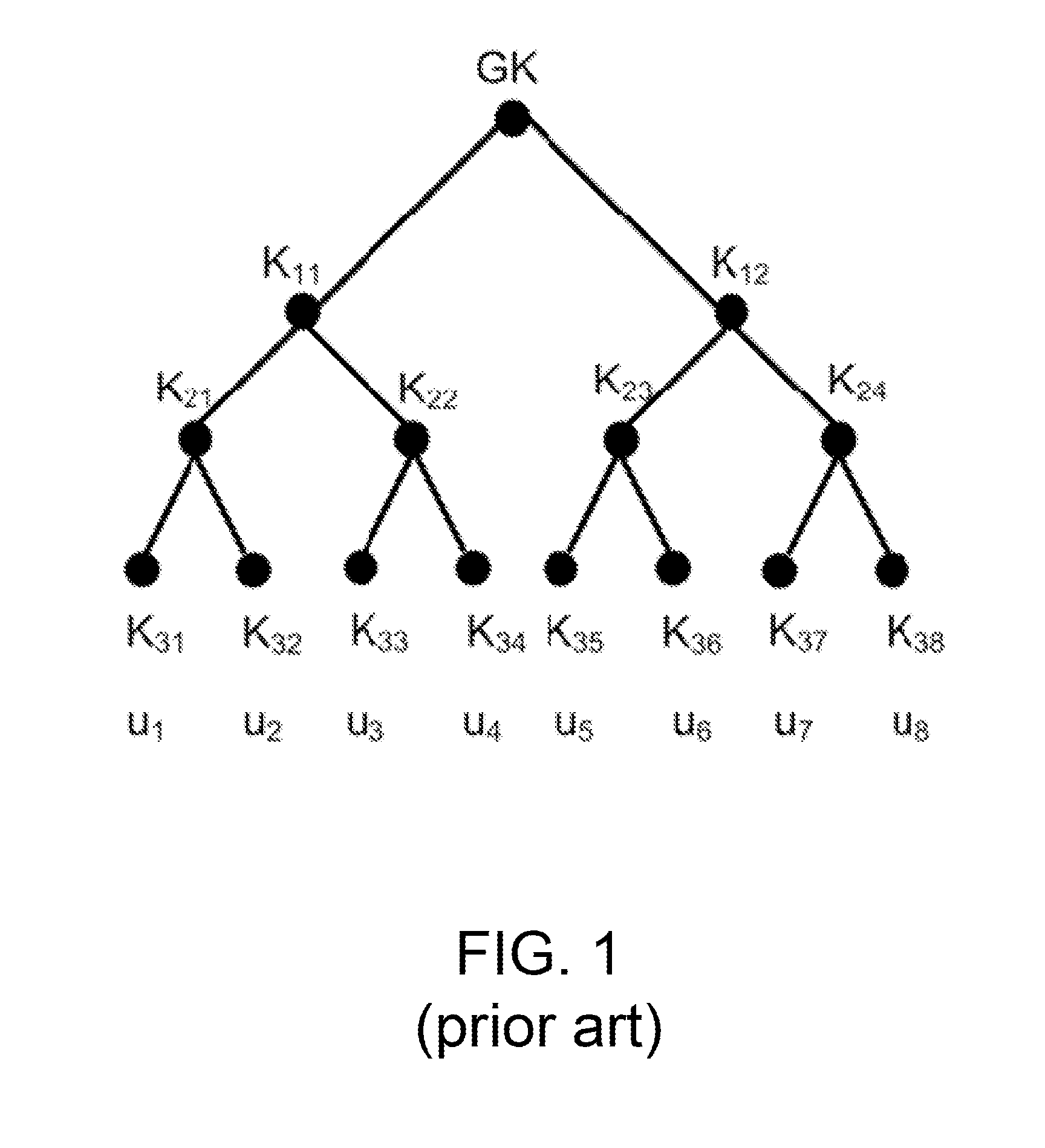
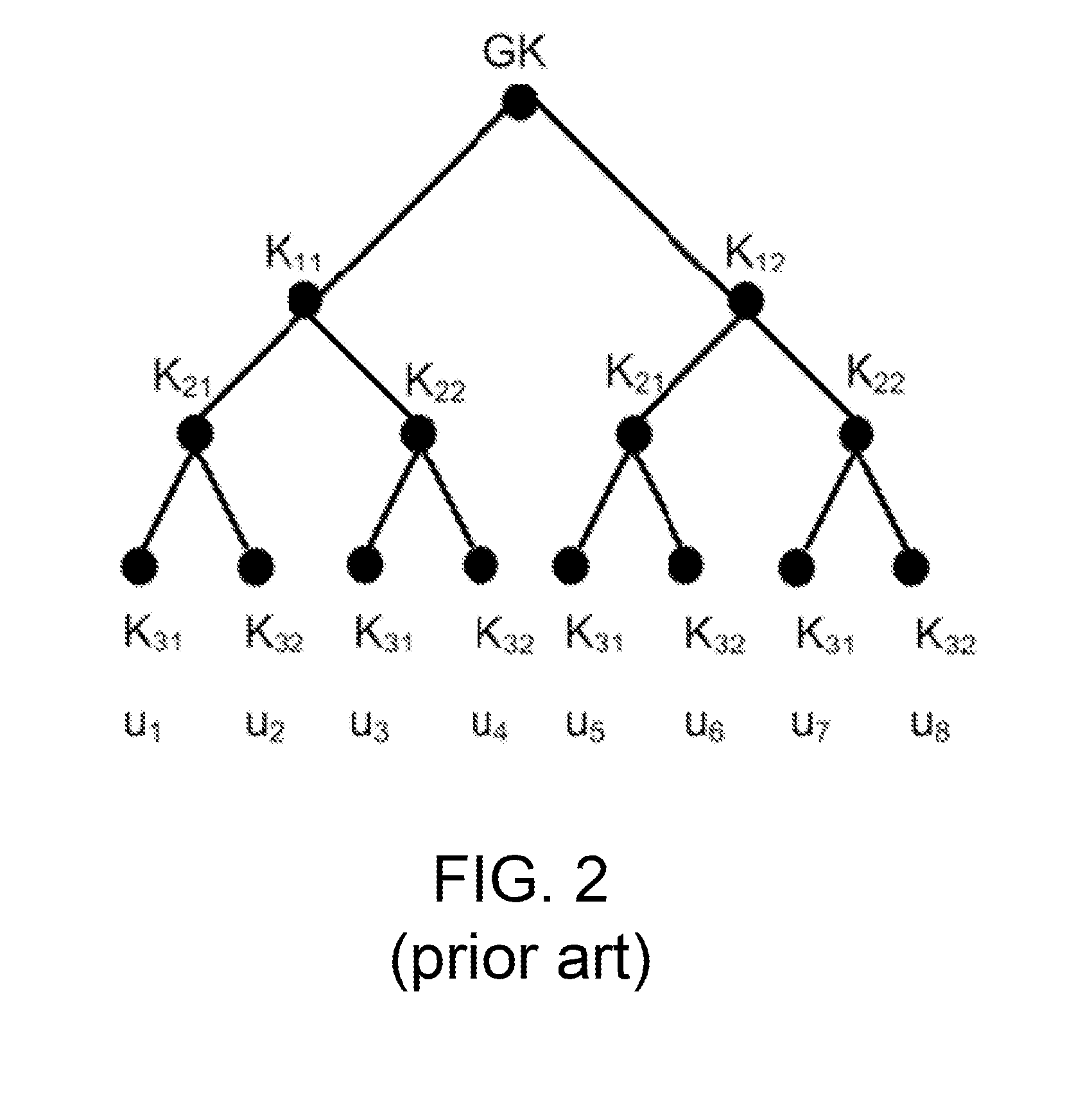
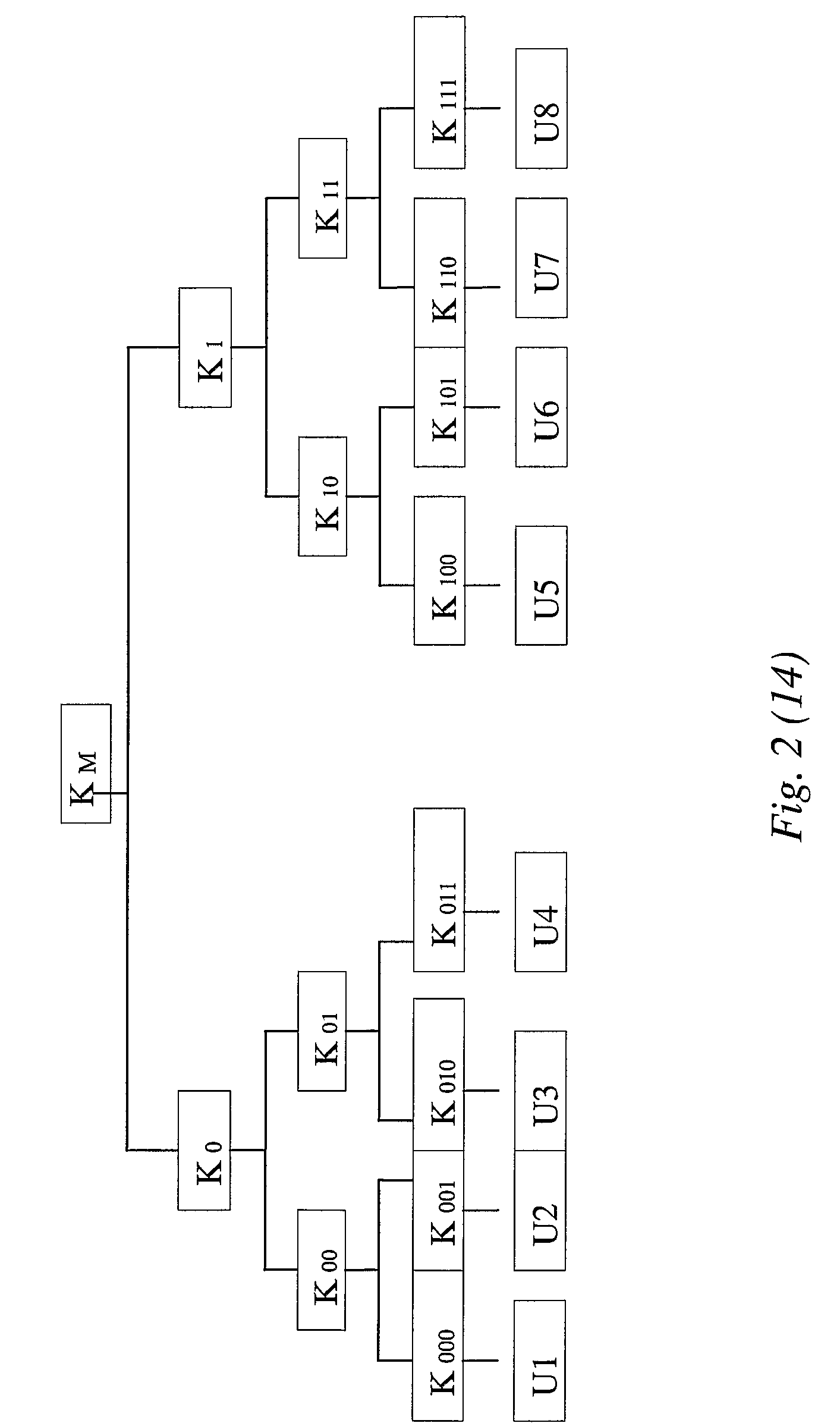
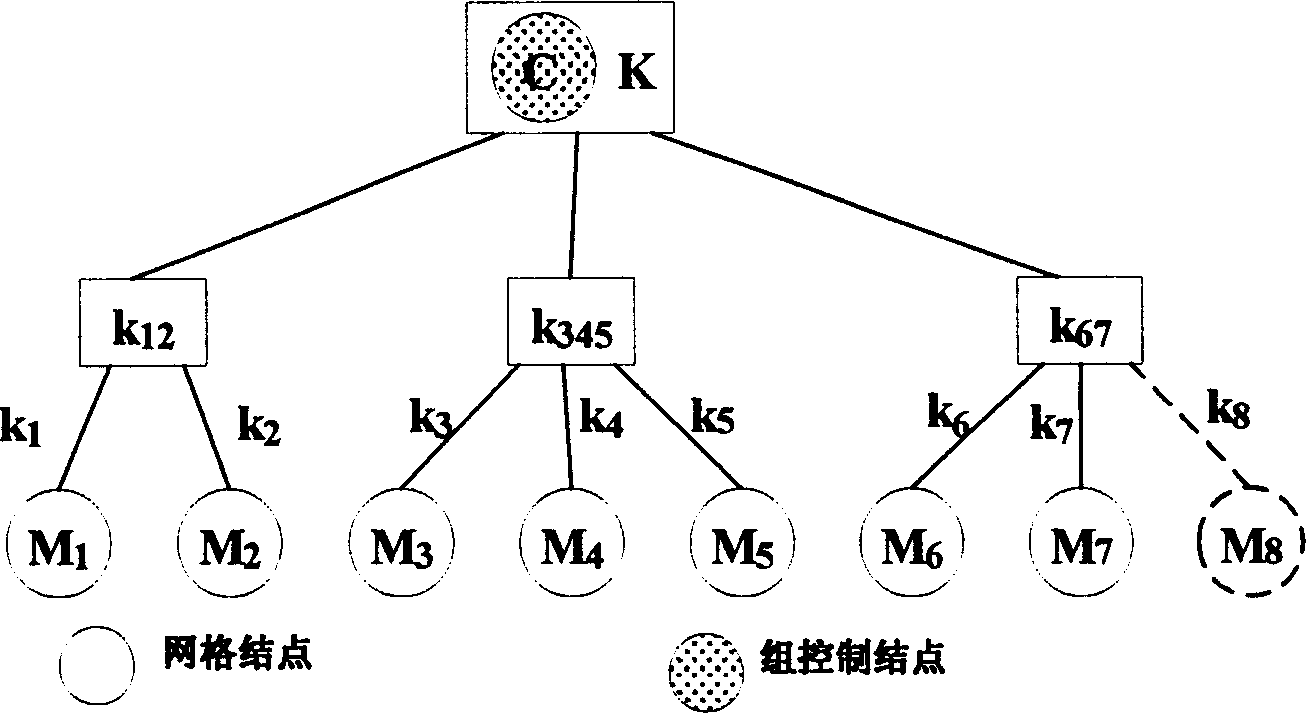
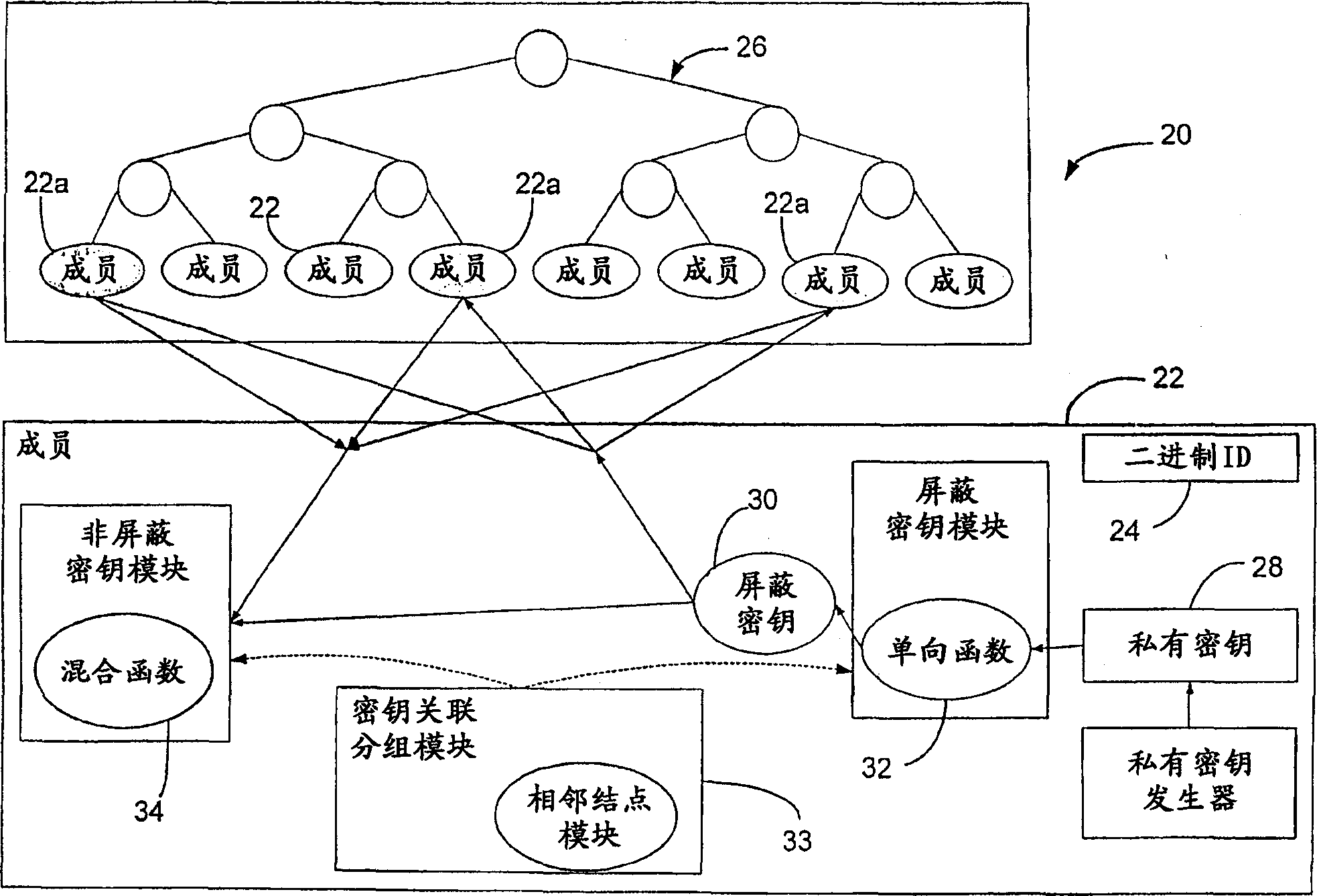
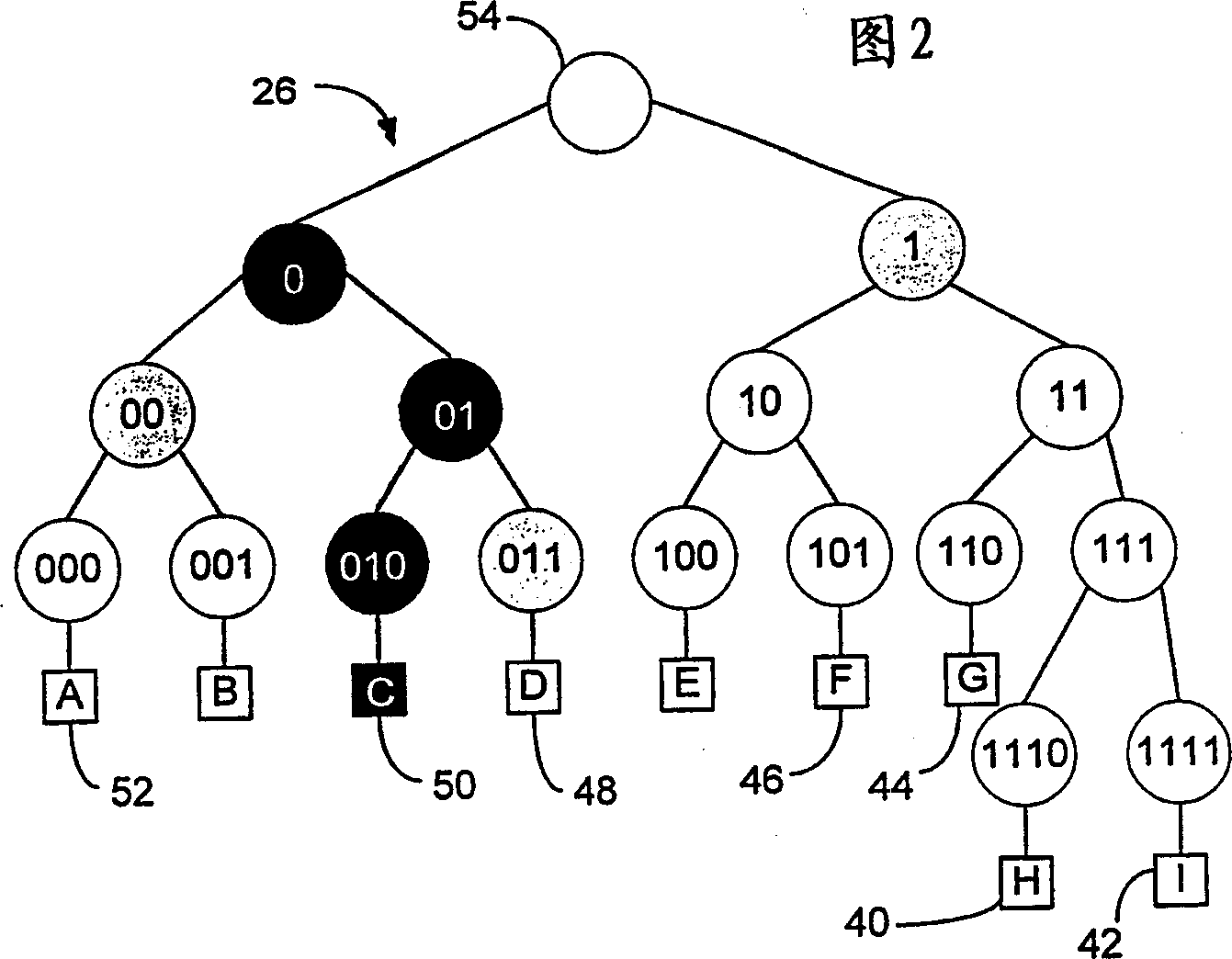
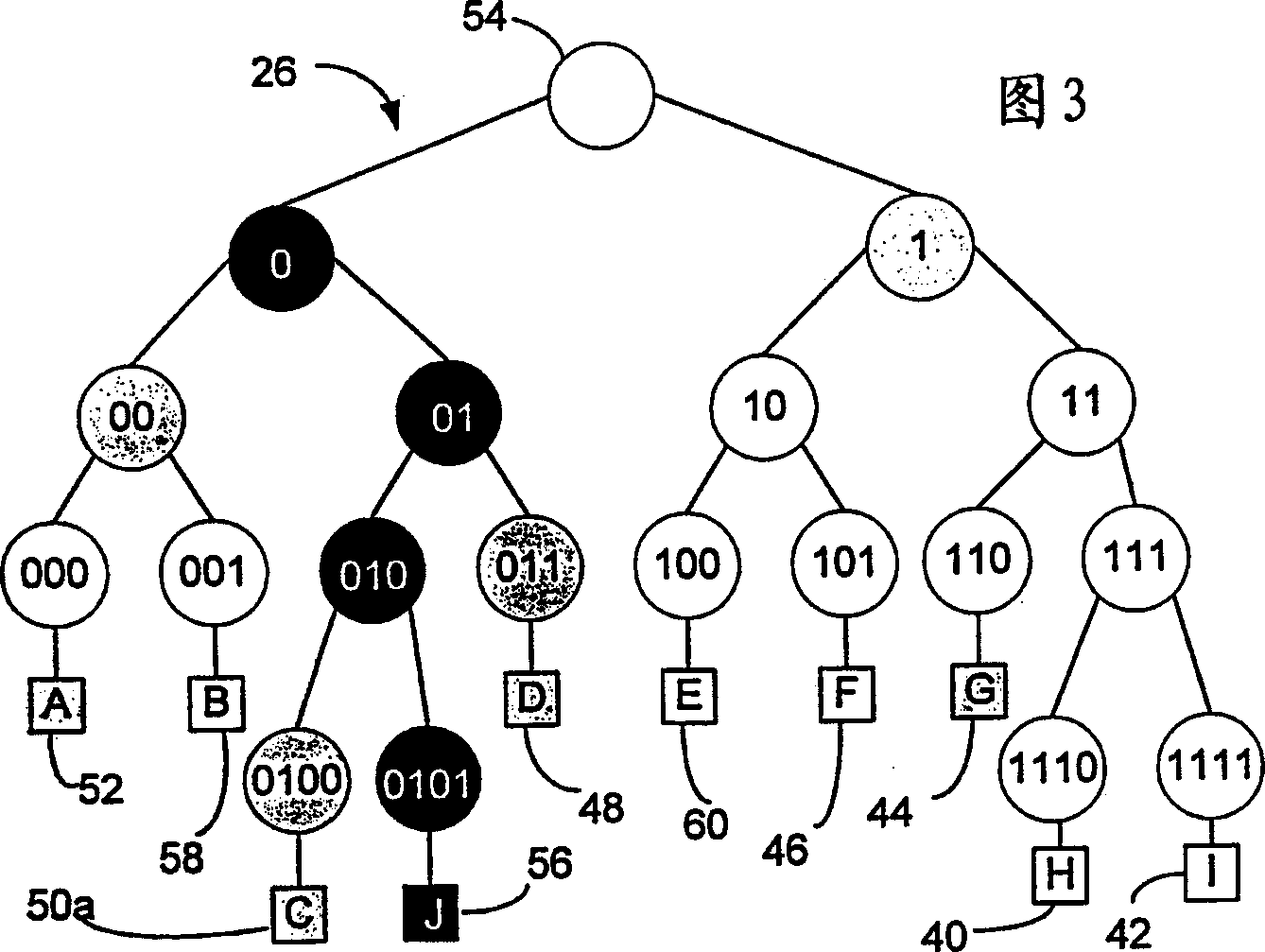
A group key management system and method for providing secure many-to-many communication is presented. The system employs a binary distribution tree structure. The binary tree includes a first internal node having a first branch and a second branch depending therefrom. Each of the branches includes a first member assigned to a corresponding leaf node. The first member has a unique binary ID that is associated with the corresponding leaf node to which the first member is assigned. A first secret key of the first member is operable for encrypting data to be sent to other members. The first member is associated with a key association group that is comprised of other members. The other members have blinded keys. A blinded key derived from the first secret key of the first member is transmitted to the key association group. Wherein, the first member uses the blinded keys received from the key association group and the first secret key to calculate an unblinded key of the first internal node. The unblinded key is used for encrypting data that is communicated between members located on branches depending from the first internal node.
Owner:PANASONIC CORP
Group key management method supporting user identity authentication
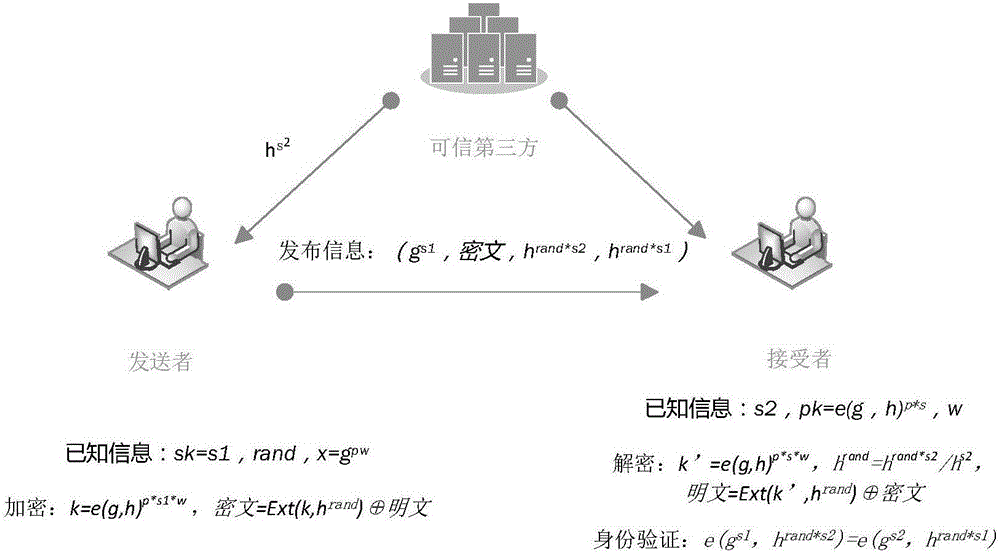
ActiveCN106301788ARelieve pressureReduce the possibility of leaksKey distribution for secure communicationPublic key for secure communicationPaired DataUser authentication
The invention discloses a group key management method supporting user identity authentication. The method comprises steps that comprises steps that an information sender, an information receiver and a trusted third party participating in identity verification and key management are included; the trusted third party is responsible for establishing an integral key system and managing the identity information of users; the information sender is used for acquiring an identity voucher disclosed by the data receiver from the trusted third party, carrying out encryption in combination with the private key pair data, utilizing the private information to realize data signature and then sending the data after signature to a whole multicast system, and the information receiver is used for carrying out decryption and source verification through utilizing a public key and the private key data. Compared with a traditional key scheme, key management pressure and key leakage possibility are greatly reduced.
Owner:WUHAN UNIV
Method, apparatus and system for registering new member in group key management
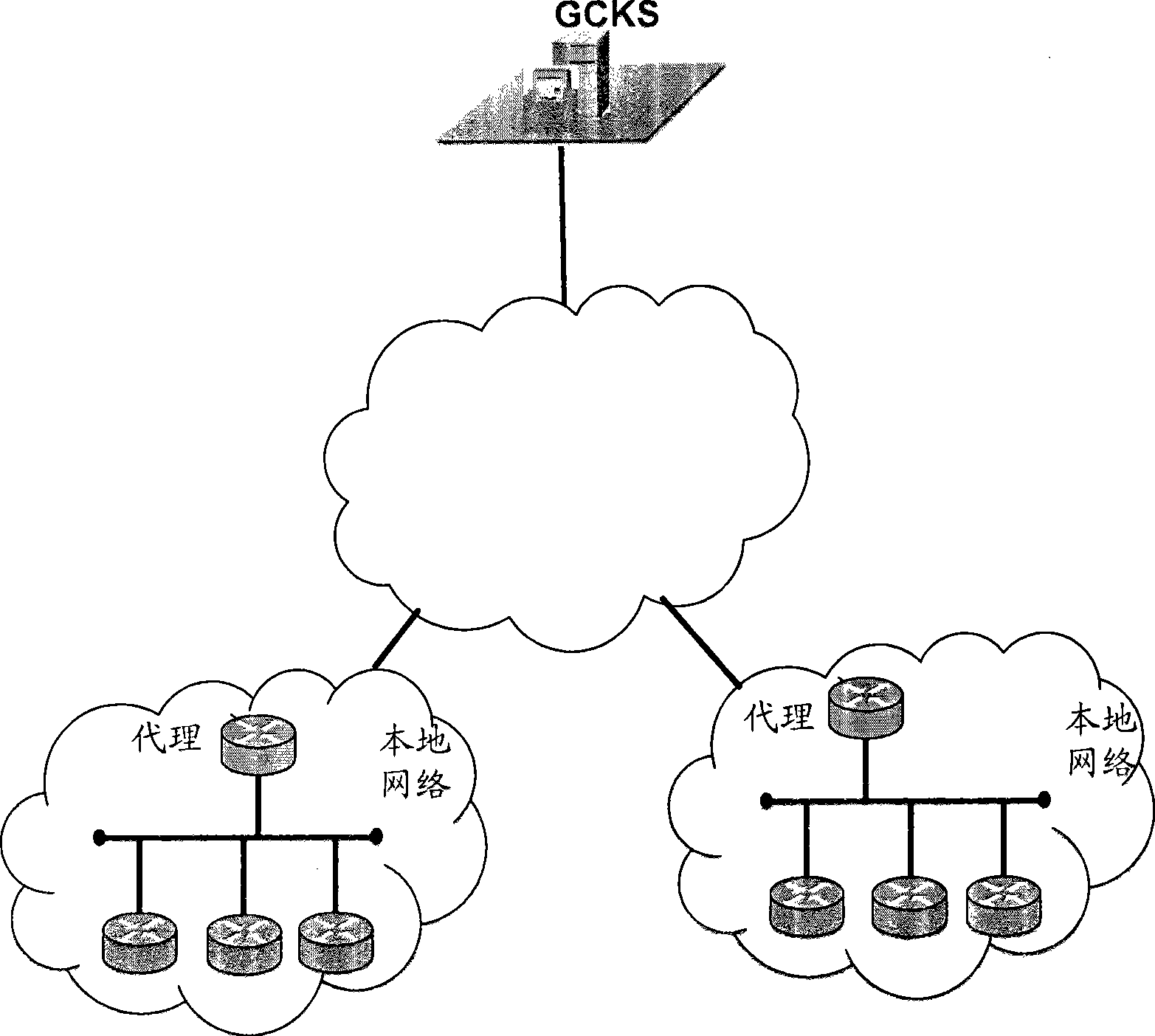
InactiveUS20100122084A1Implement automatic registrationSecuring communicationGroup controllerReal-time computing
A method for registering a new member in group key management is disclosed. An agent is deployed on the local network that requires the automatic group key management service; the agent receives an original registration request message sent by a new member in the local network, encapsulates the original registration request message and an information indicating the new member into a first request message, and sends the first request message to a Group Controller Key Server (GCKS); and the agent receives a first response message returned by the GCKS, extracts the information indicating the new member and the original response message carrying the processing result of request from the first response message, and sends the original response message to the new member according to the information indicating the new member. Apparatuses and system for registering a new member in group key management are also disclosed. According to the present invention, a new member that joins a network can be registered automatically.
Owner:HUAWEI TECH CO LTD
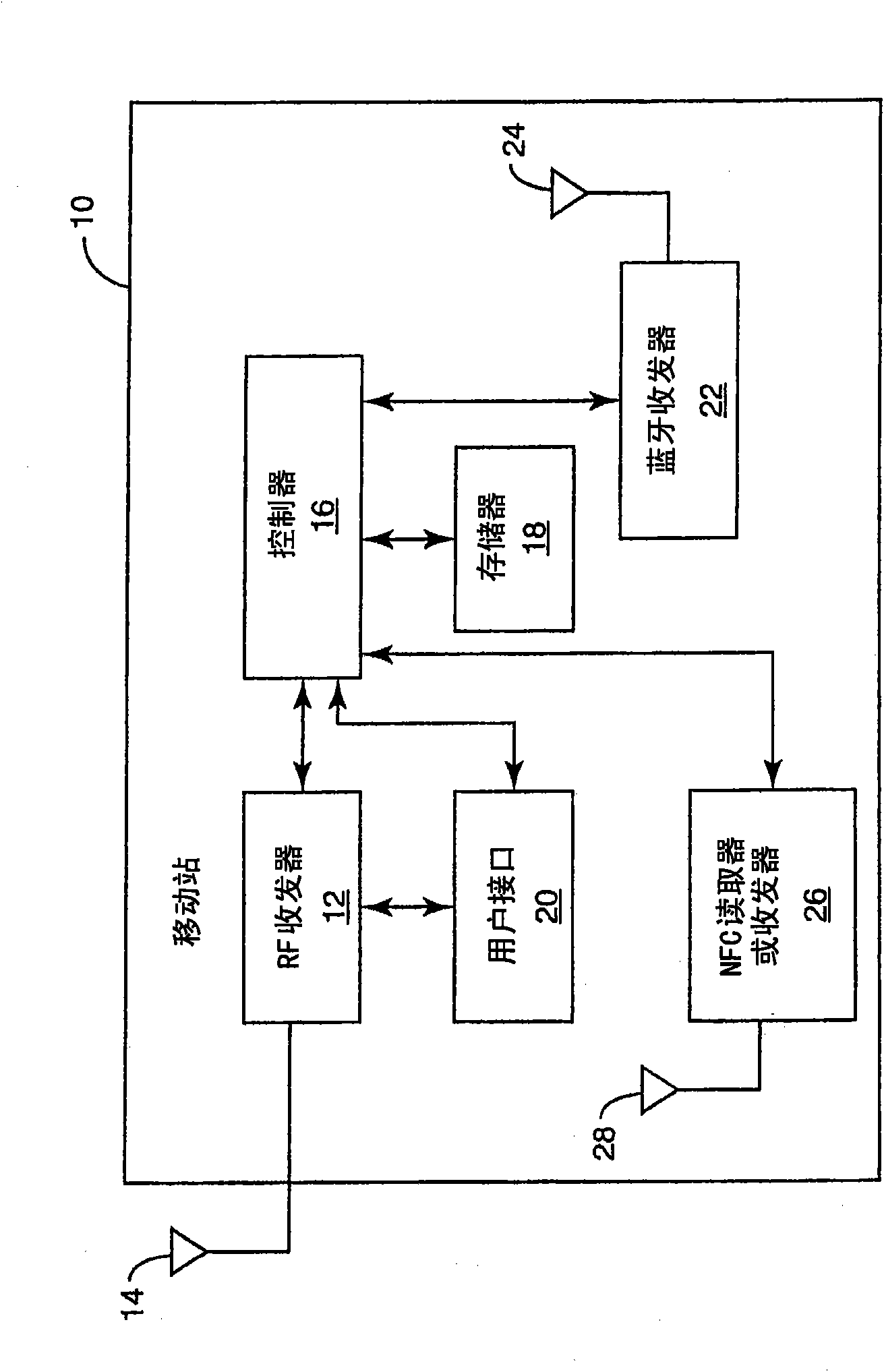
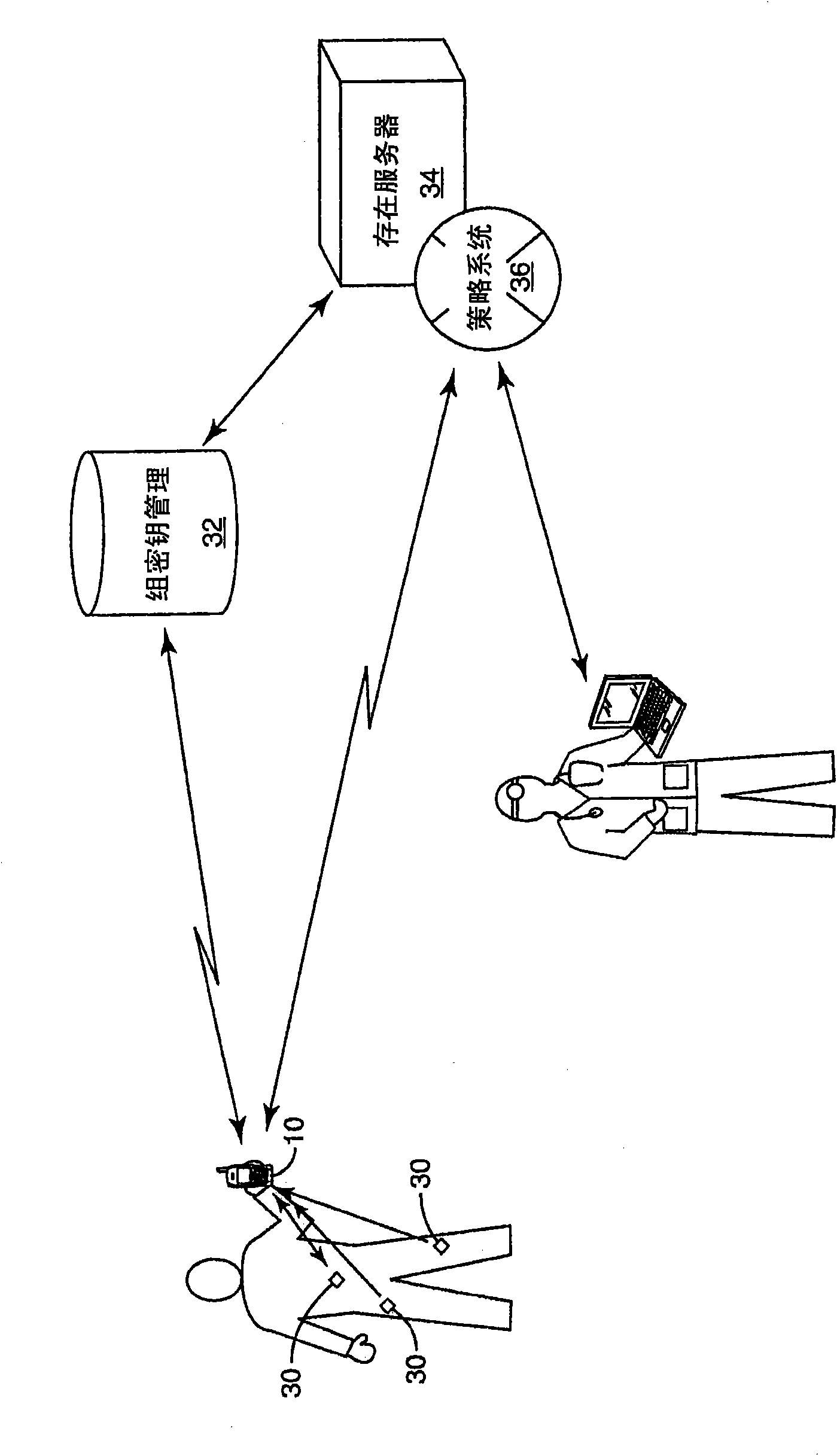
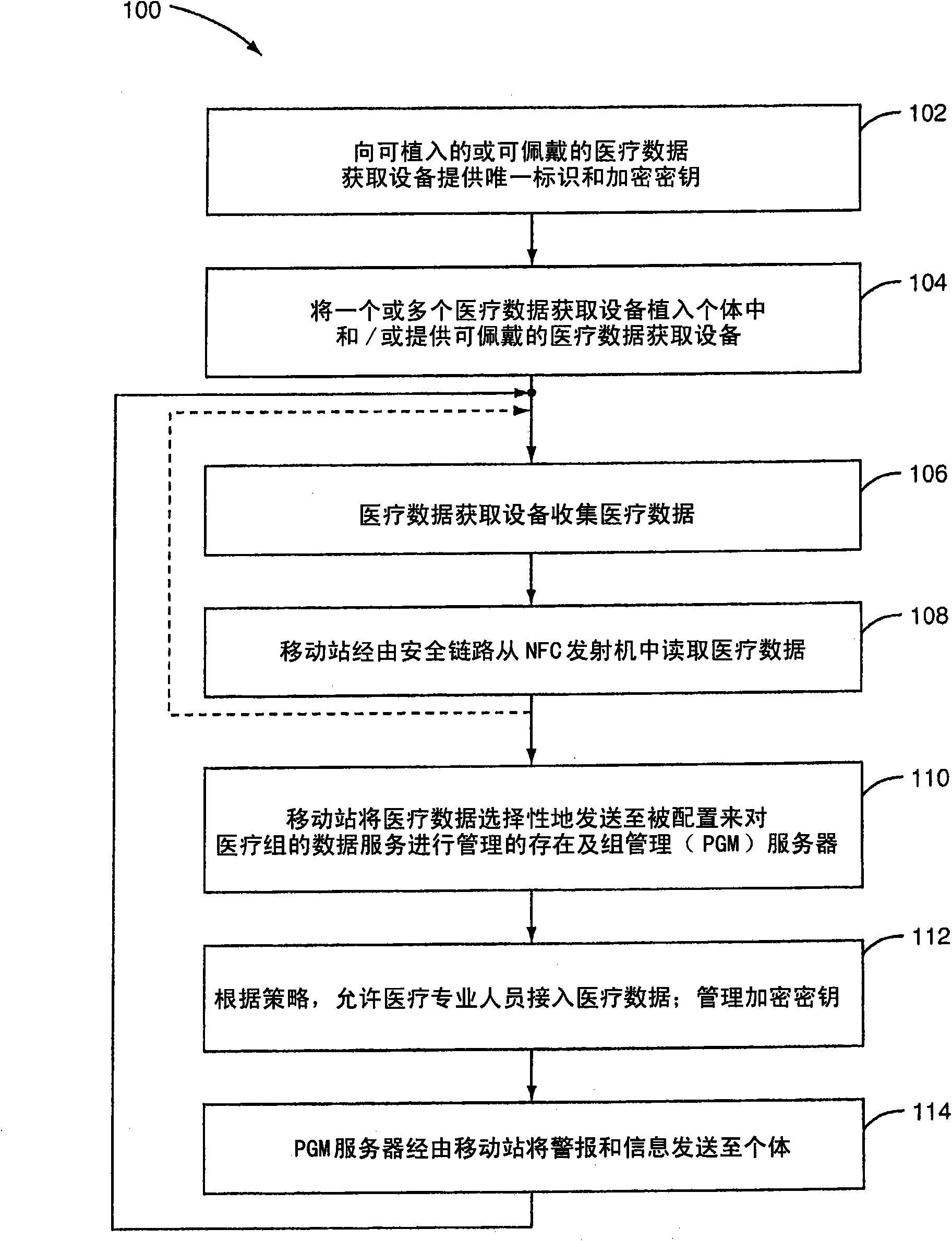
Nfc communications for implanted medical data acquisition devices
Implantable and / or wearable medical data acquisition devices (30) associated with an individual, each having NFC communication capability, collect medical data. Each device has a unique identifier. The medical data are read from the devices via a secure link by an NFC reader or transceiver in a wireless communication system mobile station (10) having a unique identifier. The medical data are selectively transmitted via a secure link from the mobile station to a Presence and Group Management (PGM) server (32, 34) configured to manage data services for medical groups. Secure access to the medical data by medical professionals is restricted accordingto a policy system (36). Encryption keys are managed on a group basis by a group key management server (32), assigning the medical data acquisition devices (30) and mobile station (10) to groups based ontheir unique identifiers. The PGM server (32, 34) may send alerts and / or information to the user via the mobile station (10).
Owner:TELEFON AB LM ERICSSON (PUBL)
A method, system and device for securing multi-party communication
InactiveCN101127595AVersatileMulti-party communication security implementationKey distribution for secure communicationSynchronising transmission/receiving encryption devicesGroup sessionCryptographic protocol
Owner:HUAWEI TECH CO LTD
Method and apparatus for generating large numbers of encryption keys
InactiveUS8594323B2High strengthKey distribution for secure communicationData stream serial/continuous modificationKey exchangeKey generation
Owner:RPX CLEARINGHOUSE
Safety multicast method based on protocol of conversation initialization
InactiveCN1874224ASolve the requestSolve the statistical billing abilityUser identity/authority verificationSecure communicationMethod selection
The safe multicast method is a first method of using the protocol of conversation initialization to implement operation of safe multicast. The method presents a set of scheme for solving issue of safe multicast including access control of multicast source, access control for receiver, management of group key, authentication of multicast source, service statistics, and charging capability. The method includes procedures: using route in network to encrypt data of multicast to guarantee access control of service, and safe comm.; method for authenticating multicast source in two stages is adopted; when IGMP / MLD adapter layer implements the method, working mode of traditional multicast route system does not need to be changed; three expansion techniques including cluster of regional multicast control server, regional physical and logical segmentations. The expansibility is suitable to large-scale network environment, and concurrent use. The invention does not change core network.
Owner:SOUTHEAST UNIV
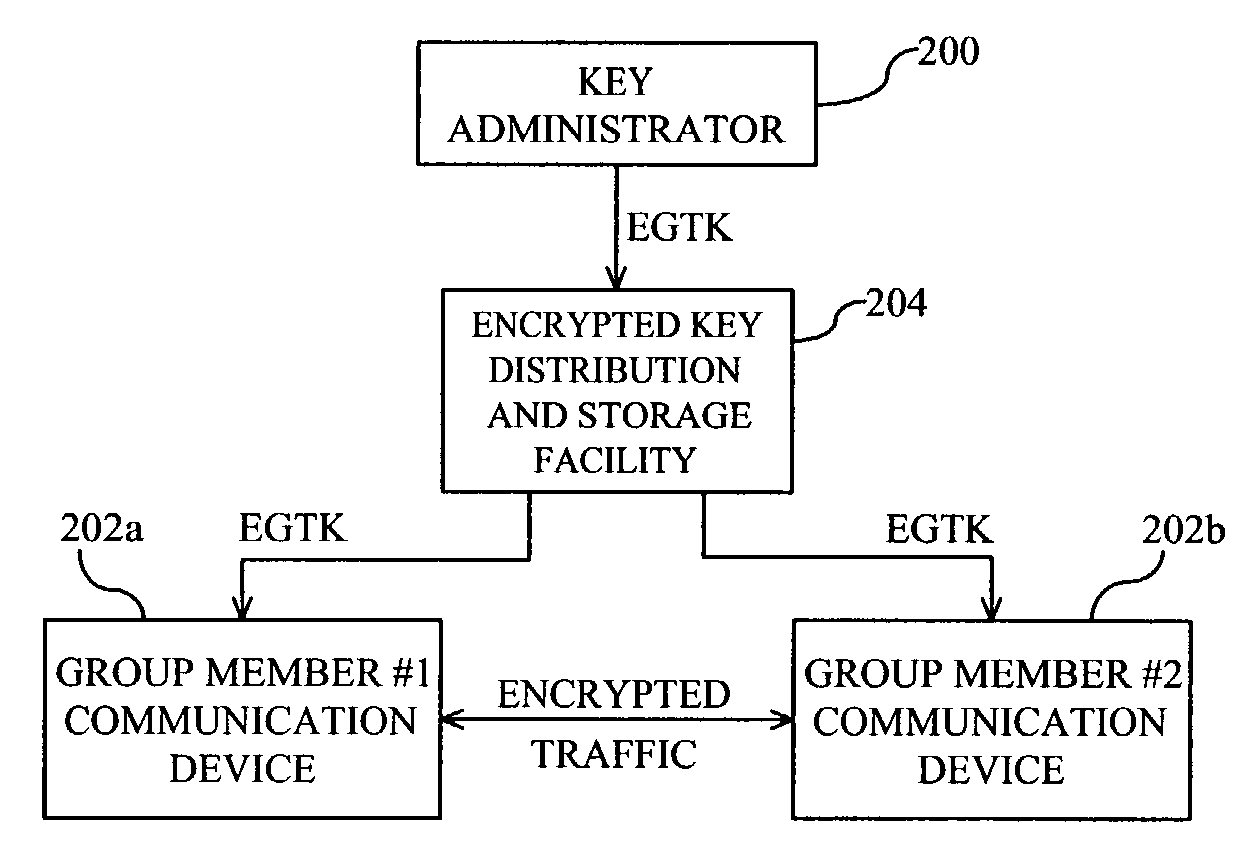
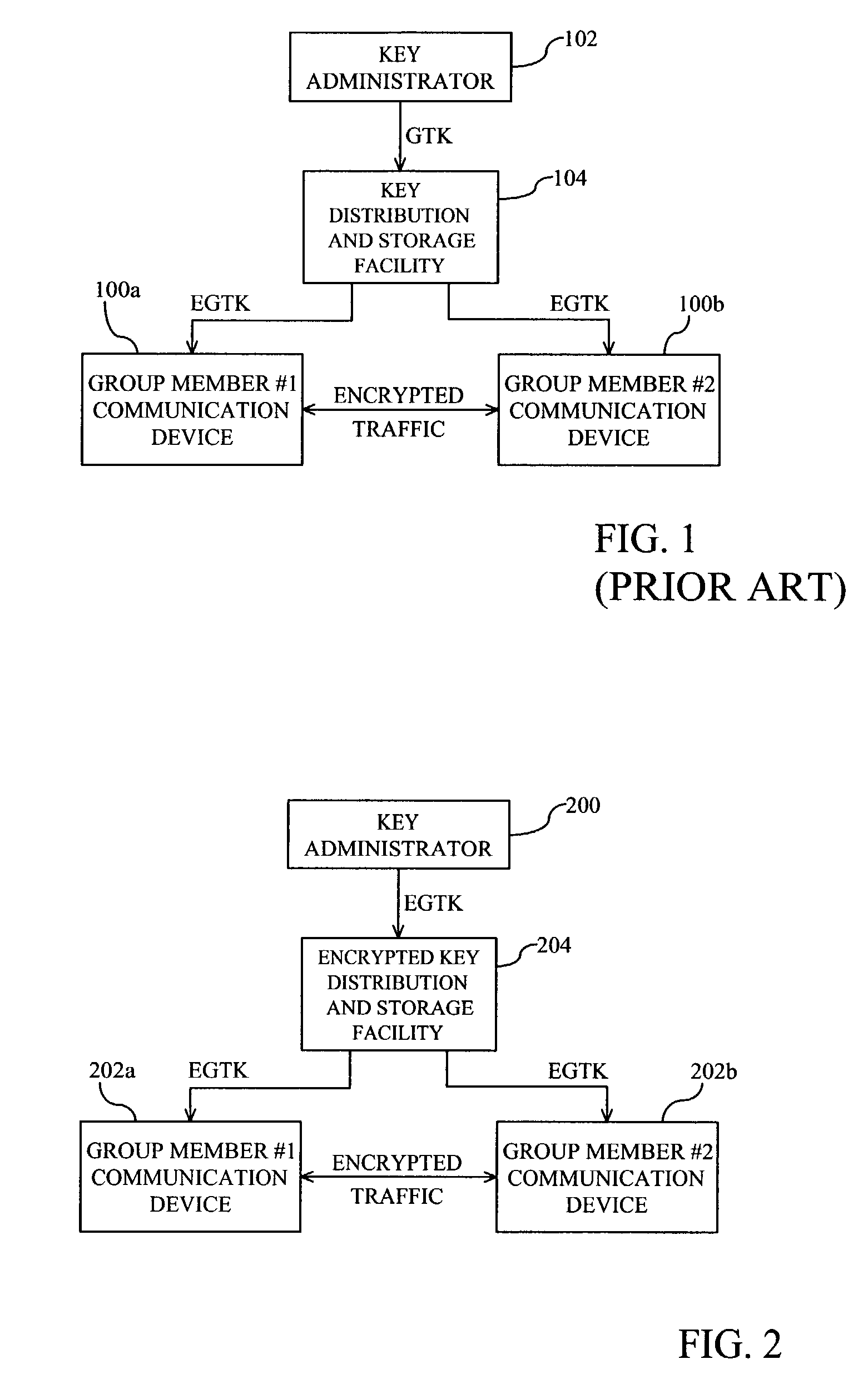
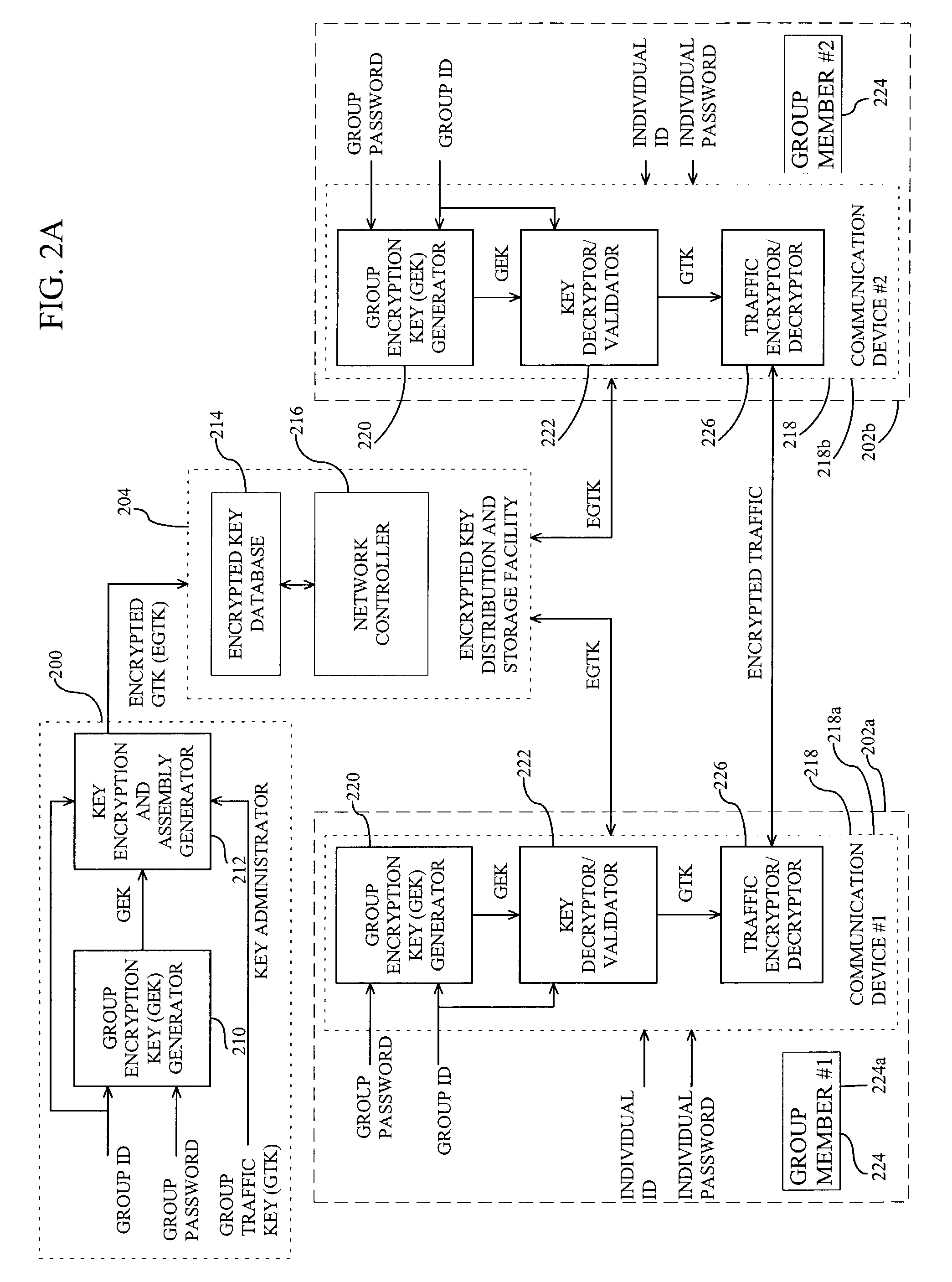
Secure encryption key distribution
ActiveUS7599496B2Improve integritySecure distributionKey distribution for secure communicationCommunications systemKey distribution
A method for distributing encryption keys for use in communication systems such as trunked radio communication systems. Group traffic keys are encrypted at a key administrator and passed to a distribution facility for storage and distribution. The distribution facility passes the encrypted group traffic key to communication devices where the group traffic keys are decrypted and used to encrypt / decrypt traffic.
Owner:EAGLE TECH LLC
Secure group key management approach based upon N-dimensional hypersphere
InactiveUS20110058668A1Reduce user storage userReduce user user computationSecuring communicationHypersphereData mining
This invention publishes a secure group key management approach based upon N-dimensional hypersphere. After initialization, the GC admits the new members and assigns identifiers to them when there are new members joining the group, and deletes the leaving members' private information when there are members leaving the group. If a lot of members join and other members leave the group at the same time, the GC deletes the leaving members' private information, admits the new members, assigns indemnifiers to the new members, and then chooses mapping parameters, mapping each member's and its private information to the points in a multi-dimensional space. The GC calculates the central point of the hypersphere, and publishes the central point, the mapping parameter and the identifiers of leaving members if there are members leave. The group members calculate the mapping points, and then calculate the group keys. The invention can effectively reduce user storage, user computation, and amount of update information while re-keying. The independence of the group keys can be kept.
Owner:SOUTH CHINA UNIV OF TECH
Method, apparatus and system for implementing new member register of group key management
InactiveCN101355425AImplement automatic registrationUser identity/authority verificationData switching networksGroup controllerGroup key management
The invention discloses a method for realizing the registration of new members in group encryption key management, wherein an agent is deployed on a local network needing automatic group encryption key management service; the method also comprises the following steps: the agent receives an original registration request message sent by a new member of the local network; the original registration request message and the marker information of the new member are encapsulated in the request message and sent to a group controller and an encryption key management server GCKS; and the agent receives a response message returned by the GCKS, extracts the marker information of the new member and the original response message carried with a request processing result from the response message, and sends the original response message to the new member according to the marker information of the new member. The invention also discloses a device and a system for realizing the registration of the new members in the group encryption key management. The method, the device and the system are applied to realize automatic registration of the new members in the group encryption key management.
Owner:HUAWEI TECH CO LTD
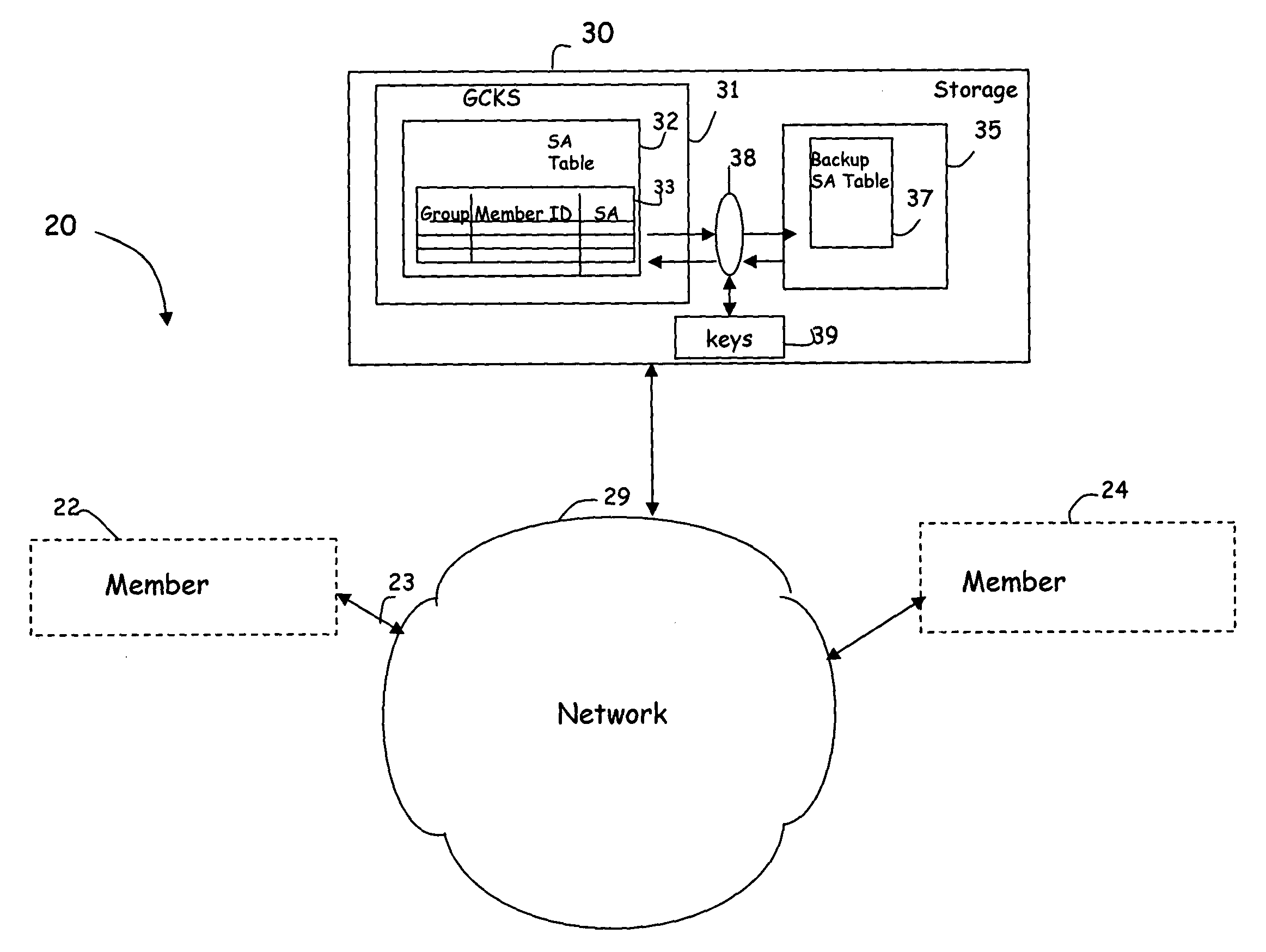
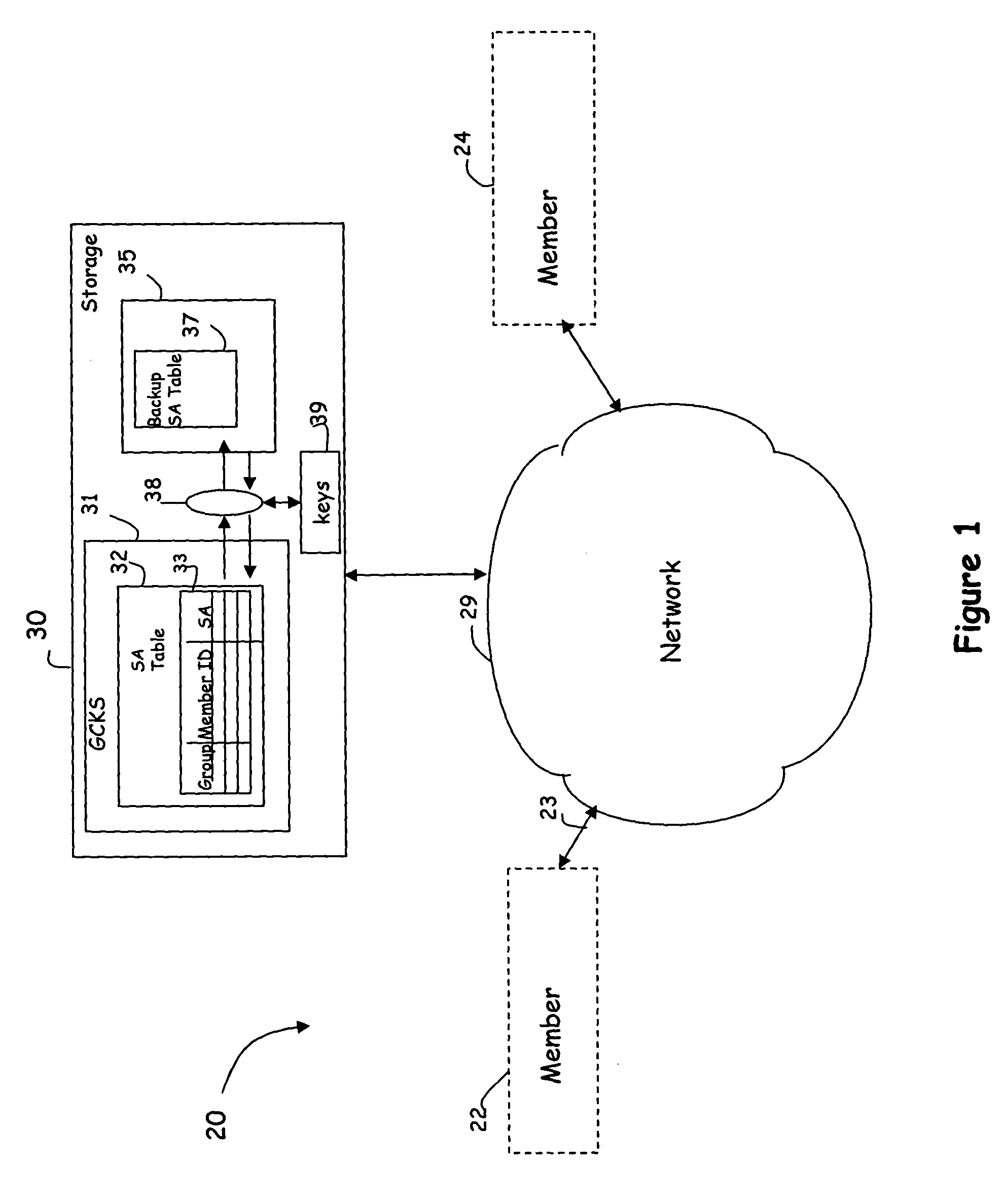
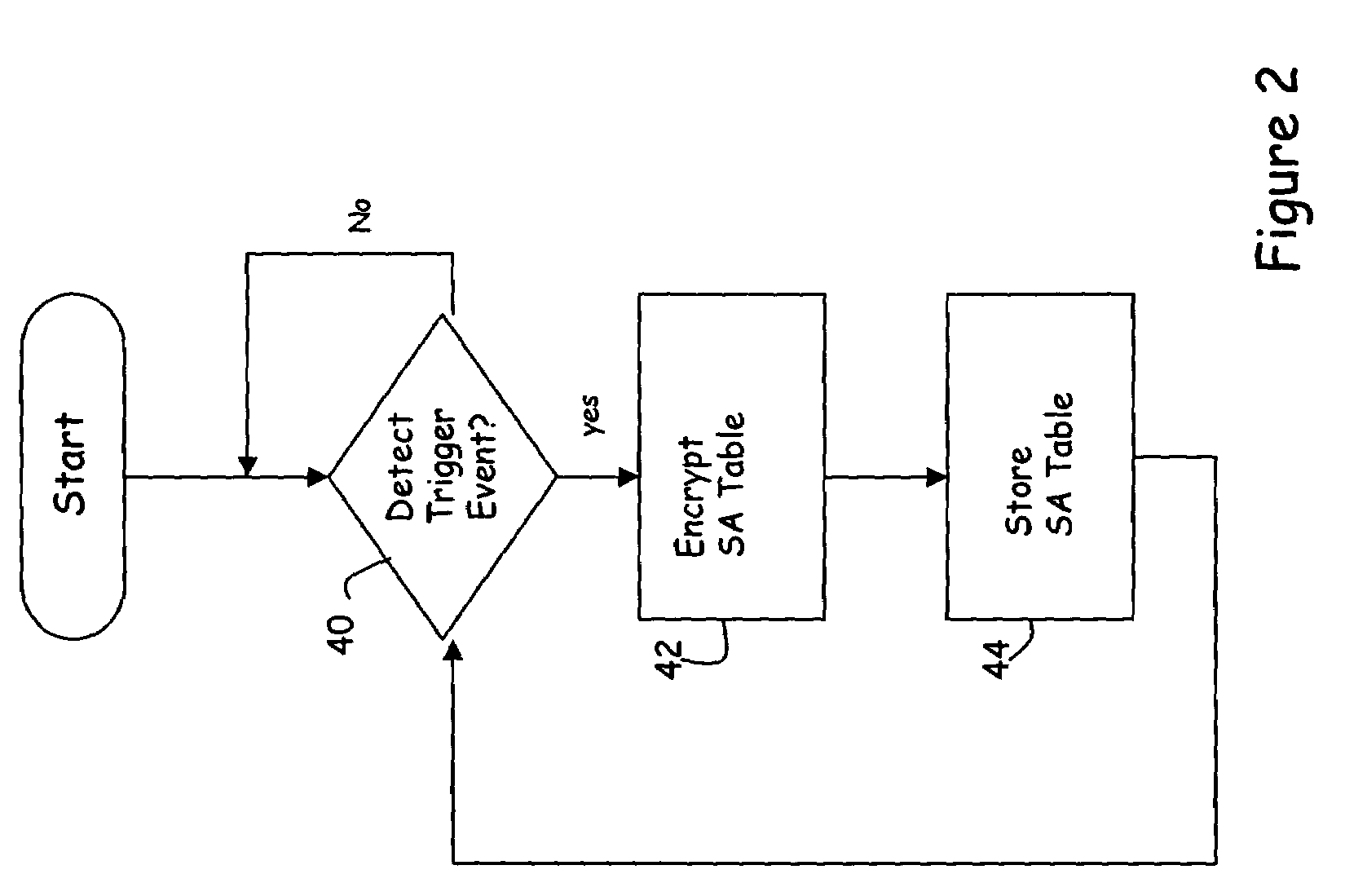
Security association storage and recovery in group key management
InactiveUS7395423B1Secure performanceLoss of performanceSecuring communicationSecurity associationNon-volatile memory
A method for preserving security associations between at least two entities includes the steps of maintaining a security association relating to communication between the at least two entities in a table, and periodically storing the security association in non-volatile storage. With such an arrangement, in the event that data within the table become corrupted, it can be retrieved from storage. Because the key data is stored, performance losses due to re-establishing the secure group are minimized. In one embodiment, the security association is advantageously encrypted prior to storage to further secure the security associations for each member.
Owner:RPX CLEARINGHOUSE
Graded group key management method based on line geometry
InactiveCN101848082AAvoid security impactReduce the likelihood of an attackKey distribution for secure communicationGroup controllerPrivate network
The present invention discloses a graded group key management method based on line geometry, which comprises the following steps: step 1. a central controller selects a finite field F, a mapping F and a constant for the use of groups and a N-dimension private vector for each sub-group; step 2. the central controller selects a mapping parameter r and maps the private vectors into a group of new vectors in a vector space; step 3. the central controller selects a sub-group key for each sub-group, constructs n linear equations and solves the linear equations, wherein the solutions of the linear equations are public vectors and n groups of public vectors form a public matrix; and the central controller further sends the public matrix and the mapping parameter r to all sub-group controllers via a public channel broadcast or multicast; and step 4. the sub-group controllers calculate confidential vector thereof and carry out a linear conversion on the confidential vector and the public matrix to obtain a group of key vectors. The graded group key management method is simple and flexible and is capable of avoiding violent attacks.
Owner:SOUTH CHINA UNIV OF TECH
Method and device for authenticating legal neighbor in group key management
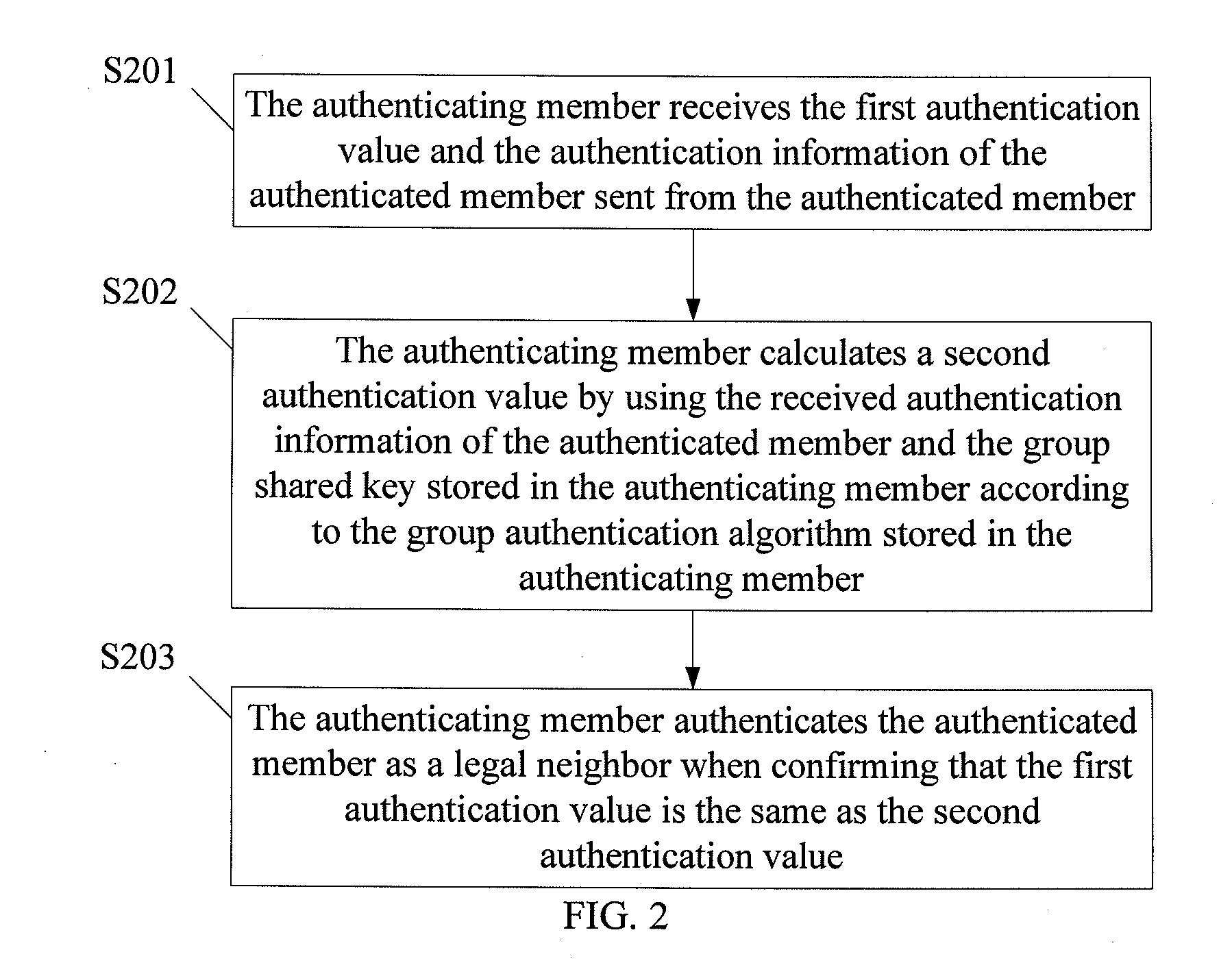
InactiveUS20100185850A1Good flexibilityKey distribution for secure communicationUser identity/authority verificationAuthentication informationGroup key management
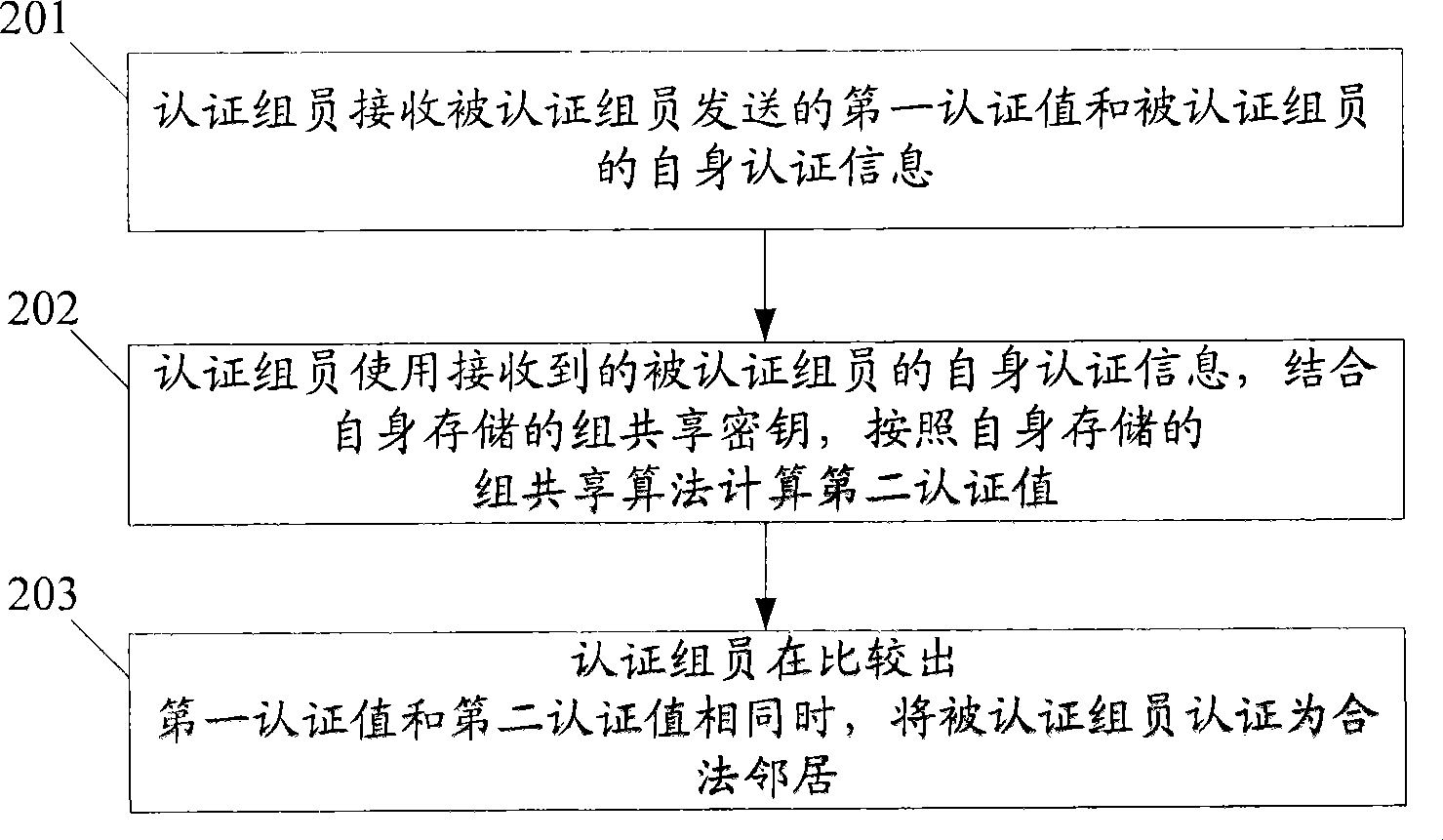
Method and device for authenticating a legal neighbor in group key management (GKM) are disclosed. The method includes: members on a local network that needs the automatic GKM service store a group shared key and a group authentication algorithm; an authenticating member receives a first authentication value and authentication information of an authenticated member sent from the authenticated member, where the first authentication value is calculated by the authenticated member by using the group shared key and the authentication information of the authenticated member according to the group authentication algorithm; the authenticating member calculates a second authentication value by using the authentication information of the authenticated member and the group shared key according to the group authentication algorithm; the authenticating member authenticates the authenticated member as a legal neighbor when confirming that the first authentication value is the same as the second authentication value.
Owner:HUAWEI TECH CO LTD
Design of large-scale dynamic multicasting security system framework
InactiveCN101286838AMeet performance requirementsMeet application requirementsSpecial service provision for substationKey distribution for secure communicationViewpointsSecure multicast
The invention relates to a dynamic secure multicast system architecture in large-scale network environment, which is characterized in that a new set of dynamic secure multicast system architecture is designed; the dynamic secure multicast system architecture divides whole multicast into different areas, only updates the encryption key of a group after the members of each group are changed, avoids system expense brought by the update of the encryption key of whole group caused by frequent changes of group members, realizes the flexible extension mechanism with respect to the encryption key management and data distribution of each subarea, realizes the safe certification mechanism based on Kerberos, so as to carry out management of multicast from the viewpoints of controlling safety and data safety. According to the characteristics and requirements of IPv6 protocol, a set of relatively complete group encryption key management mechanism is realized to be applicable to the requirement for safety and practicability of most multicasts in China Education and Research NET of second generation (CERNET2) and similar network environments.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com