Distributed group key management scheme for secure many-to-many communication
A technology of secure communication and key management system, applied in the field of secure communication systems, and can solve problems such as fragility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
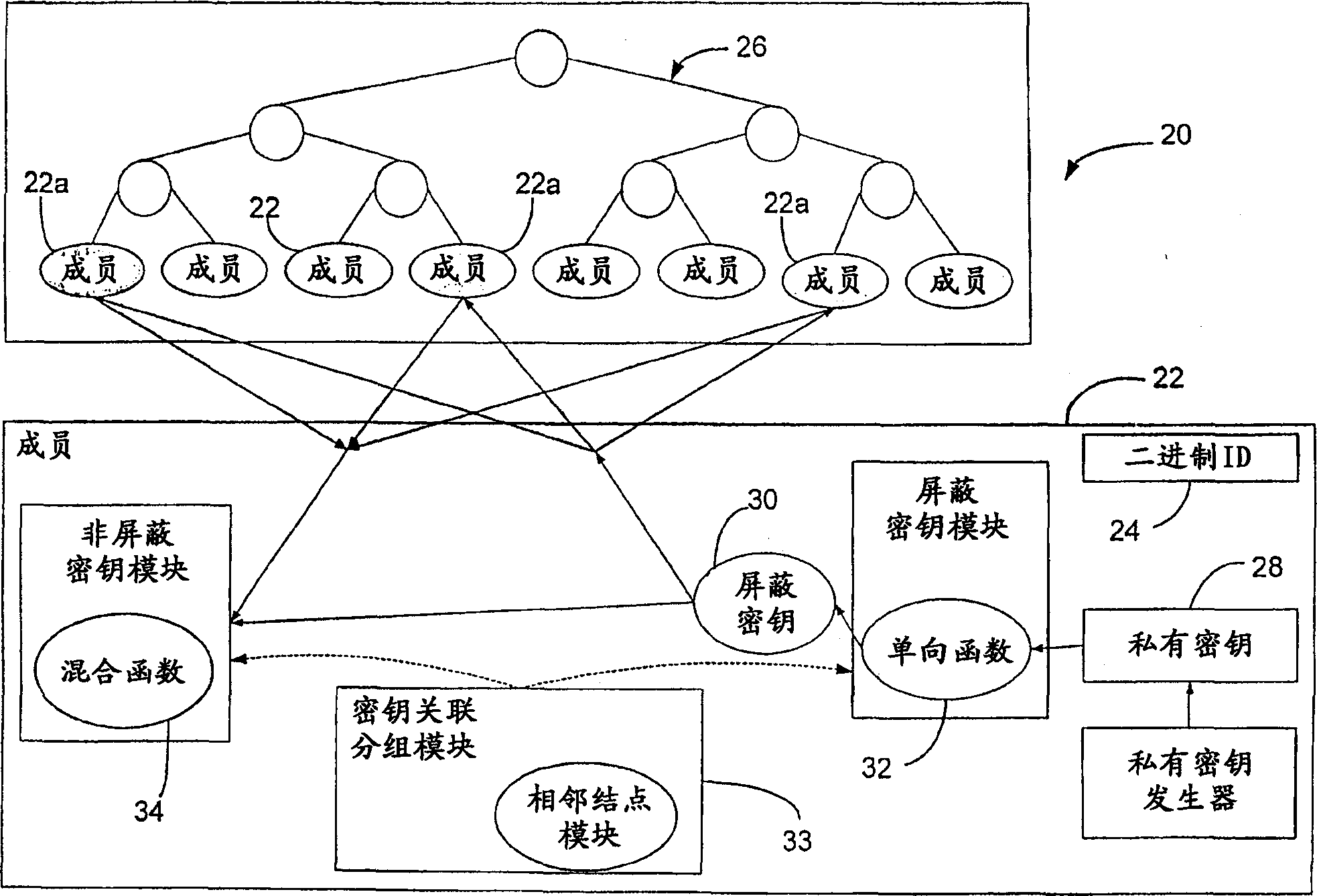
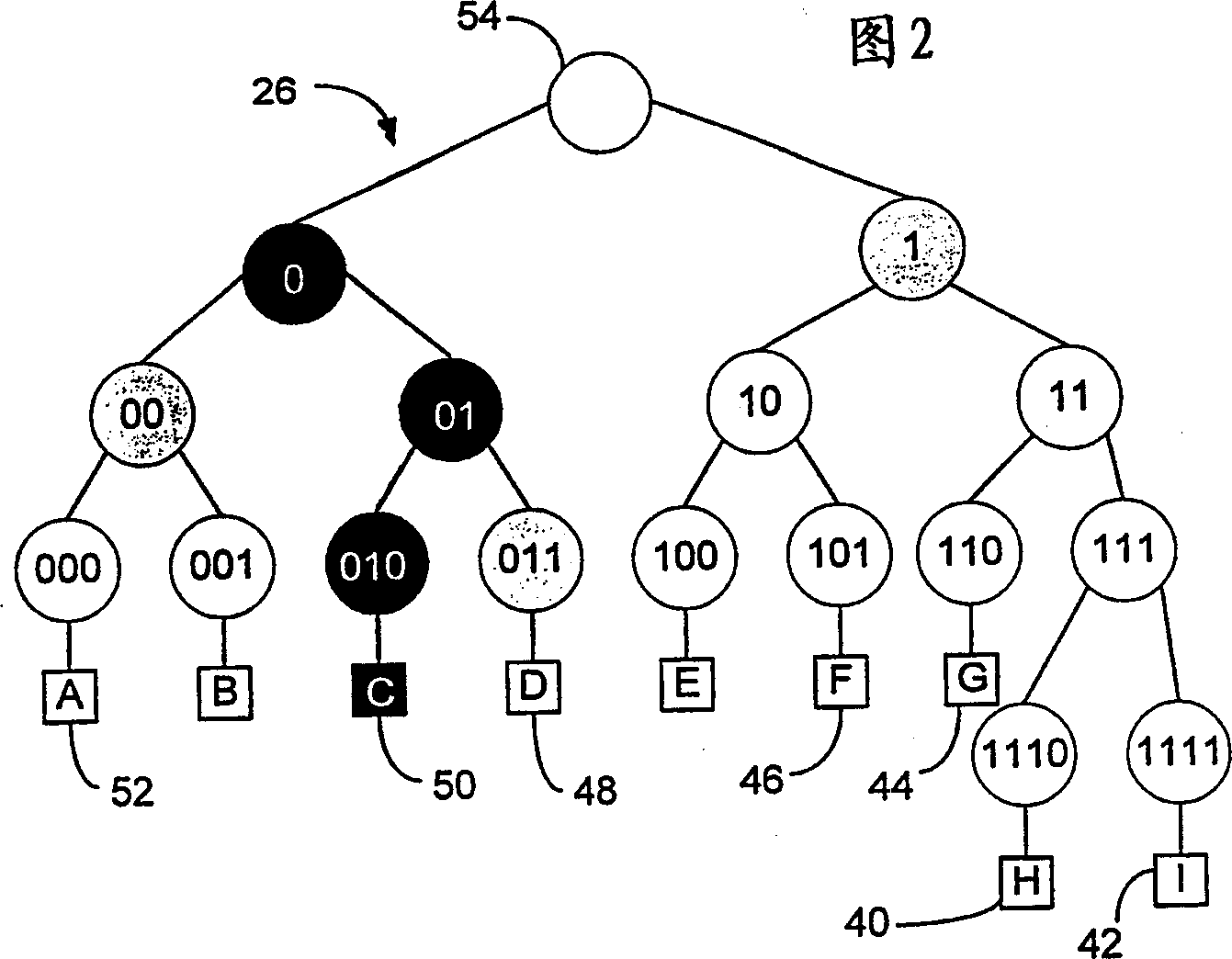
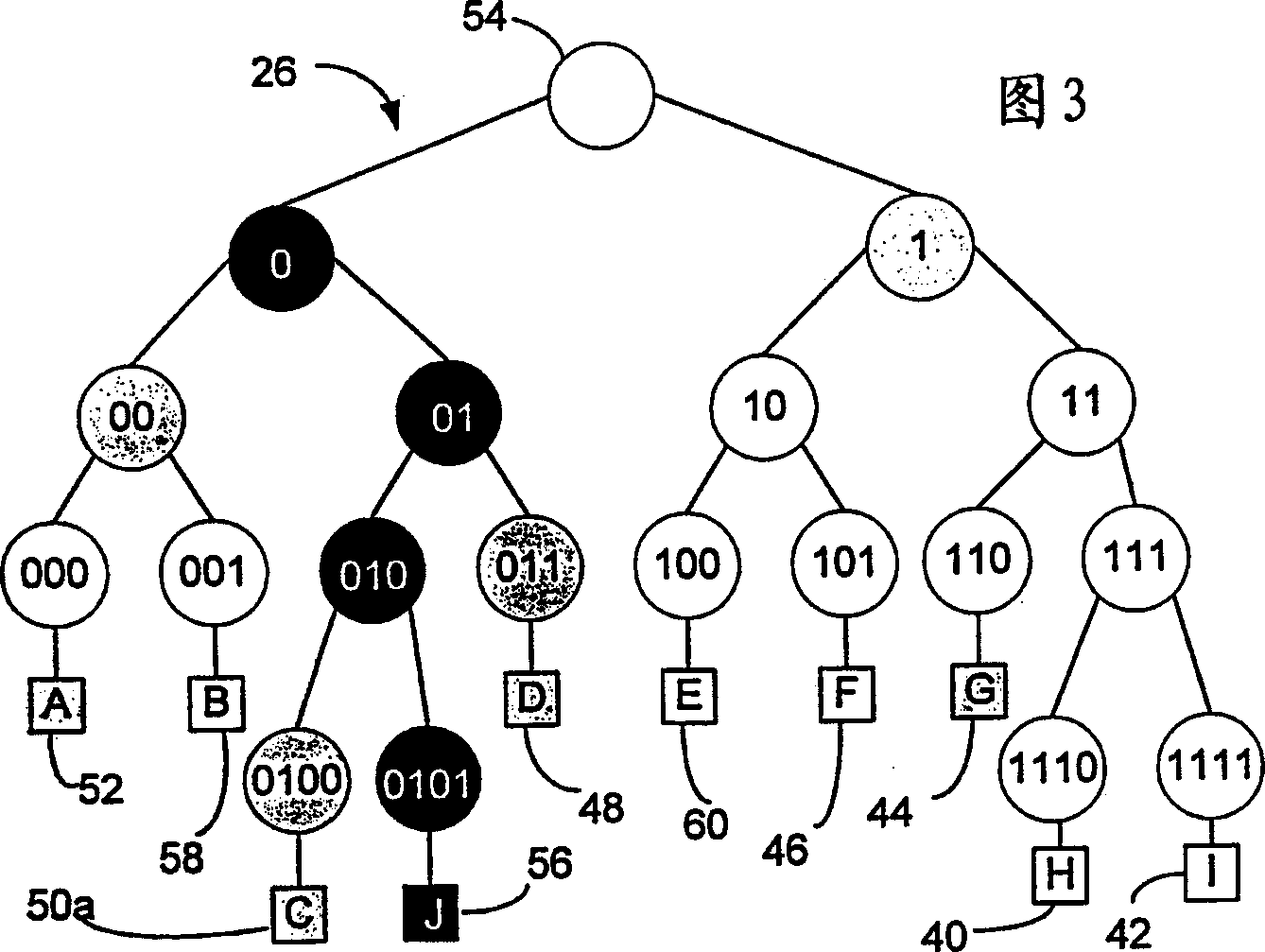
[0021] refer to figure 1 , which illustrates a scalable secure multicast protocol supporting many-to-many communications based on the principles of the present invention. An embodiment of the present invention is a communication system 20 that uses a distribution tree-based key management scheme (DTKM) for secure many-to-many packet communication. System 20 is scalable and members 22 are trusted equally. System 20 equally distributes group control responsibilities and key distribution tasks among members.
[0022] Each member 22 is assigned a binary ID and these IDs are used to define key associations for each member 22 . Members of the key association group 22a contact each other to report membership changes and exchange keys. Members 22 are equally trusted and can all be senders. Prospective members can contact any active member to join the group. The active member verifies the new member's certificate and assigns it a unique binary ID 24 . ID assignment is done locall...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com